Exploring the Frontiers of Cybersecurity Behavior: A Systematic Review of Studies and Theories
Abstract
1. Introduction
2. Background
2.1. Cybersecurity Behavior
2.2. Related Work
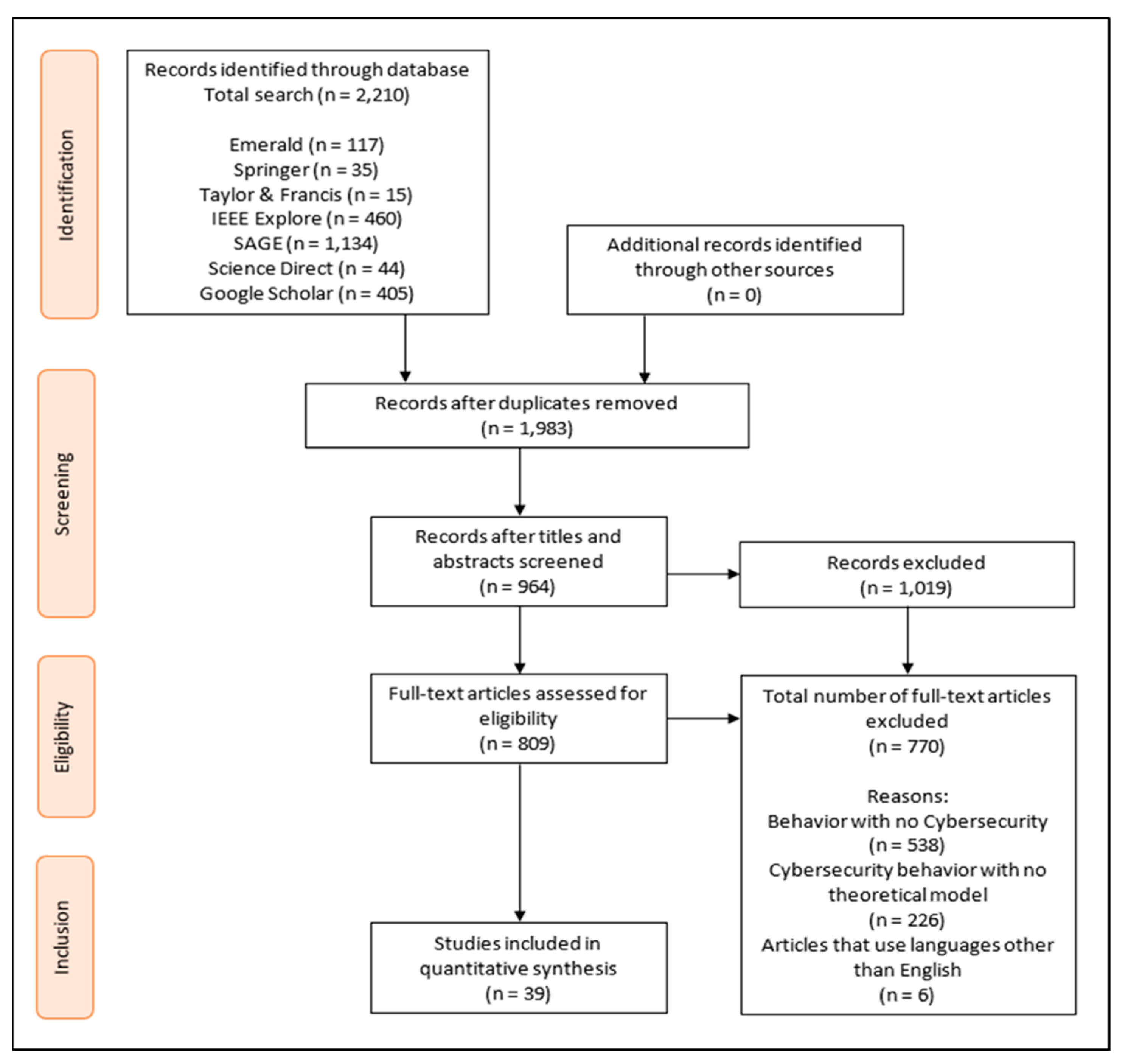
3. Method
3.1. Inclusion and Exclusion Criteria
3.2. Data Sources and Search Strategies
3.3. Data Coding and Analysis
4. Results
4.1. Prominent Theories and Models in Cybersecurity Behavior
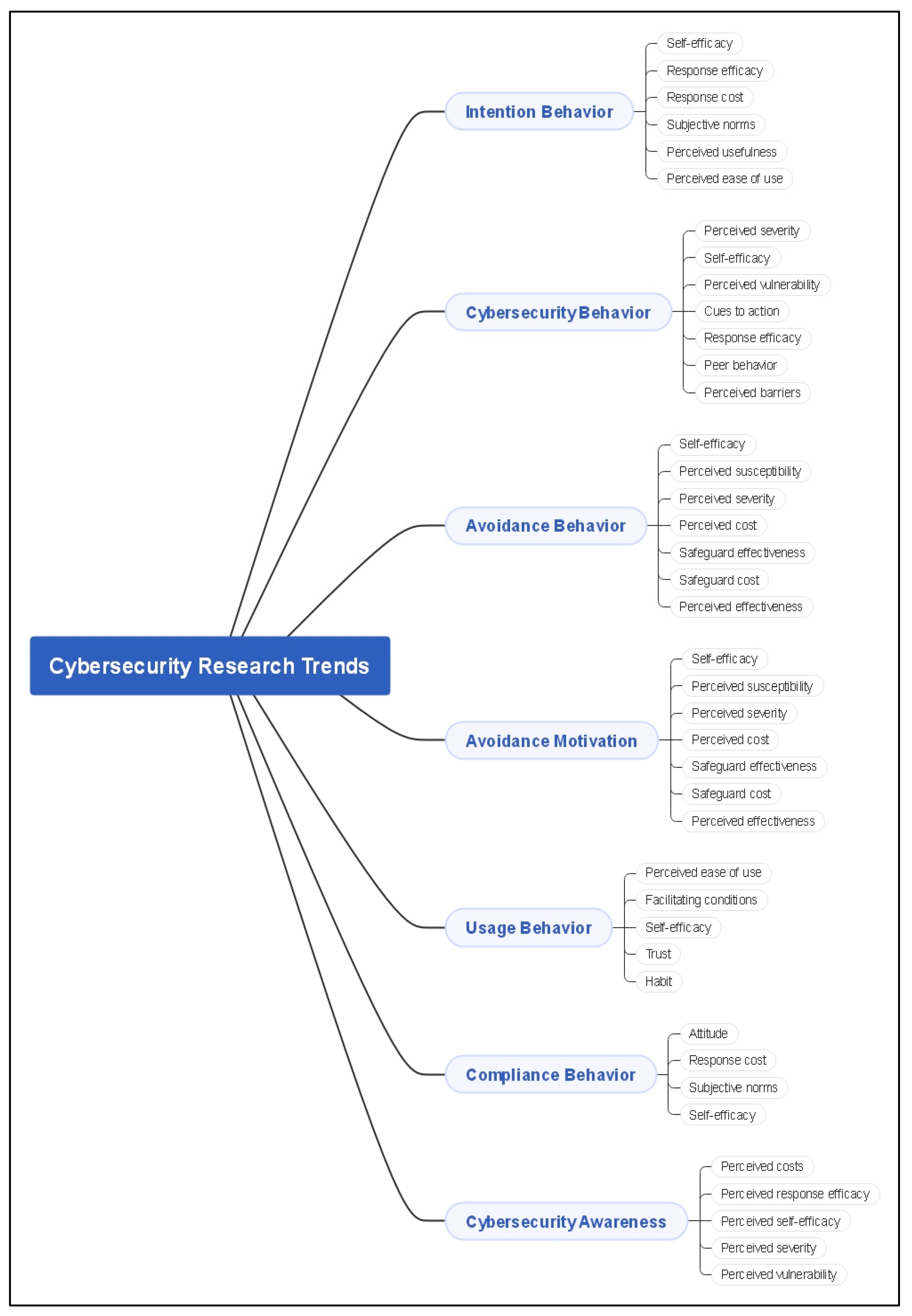
4.2. Common Research Themes
4.3. External Factors Affecting Cybersecurity
4.4. Relationship between Cybersecurity Research Themes and External Factors
4.5. Dominant Technologies and Services in Cybersecurity
4.6. Leading Research Methods
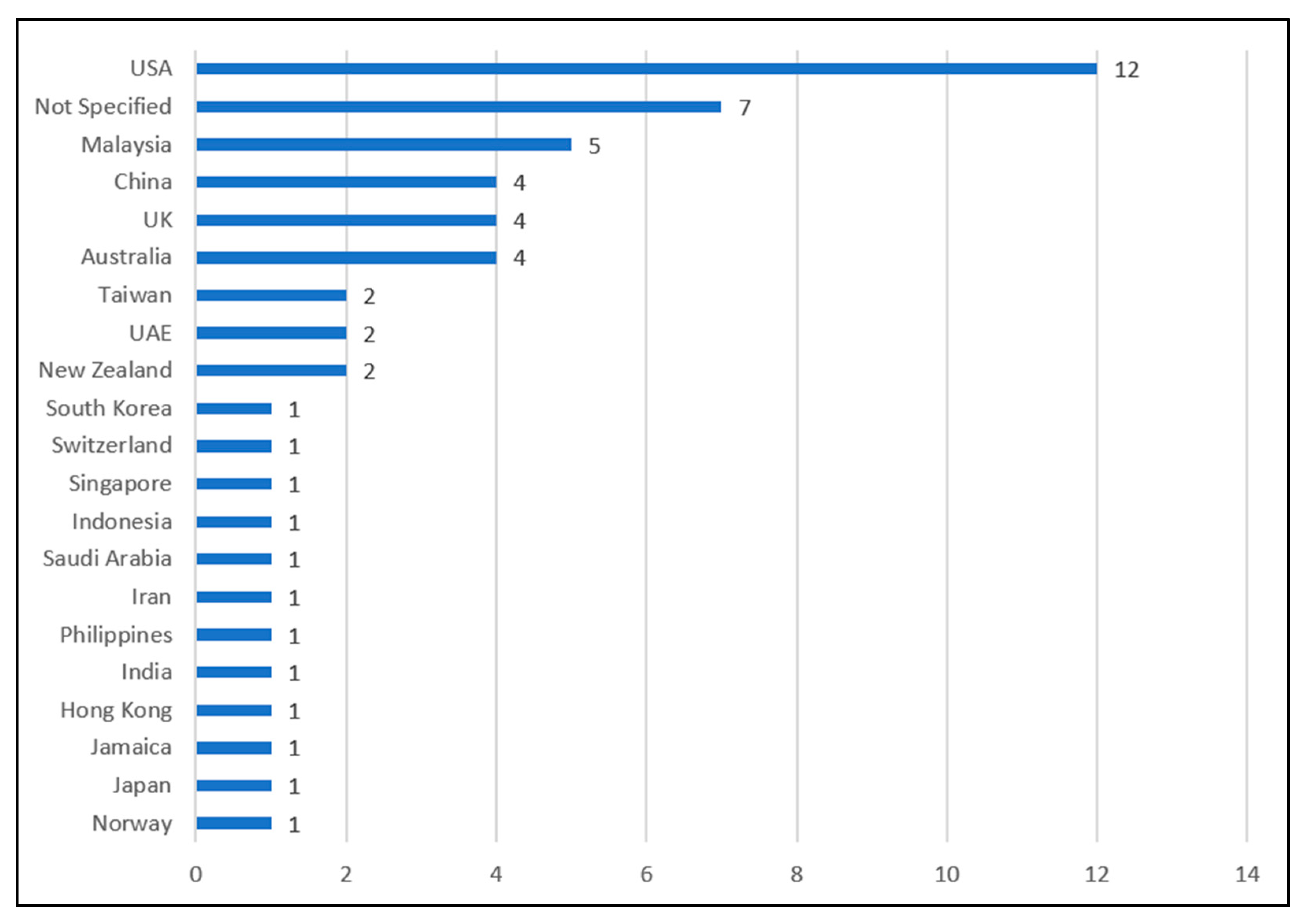
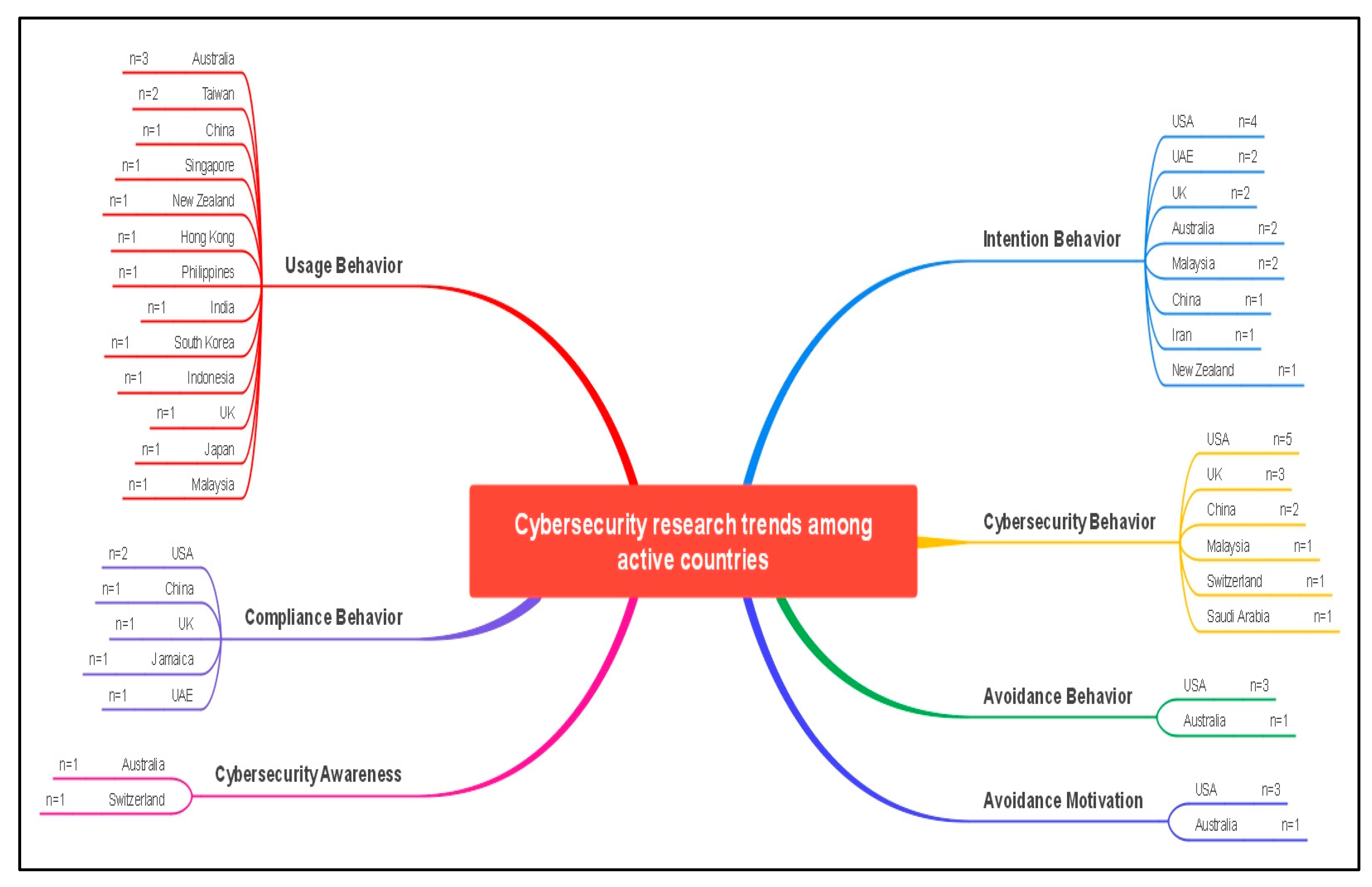
4.7. Active Countries in Cybersecurity Behavior Research
4.8. Relationship between Cybersecurity Research Themes and Study Regions
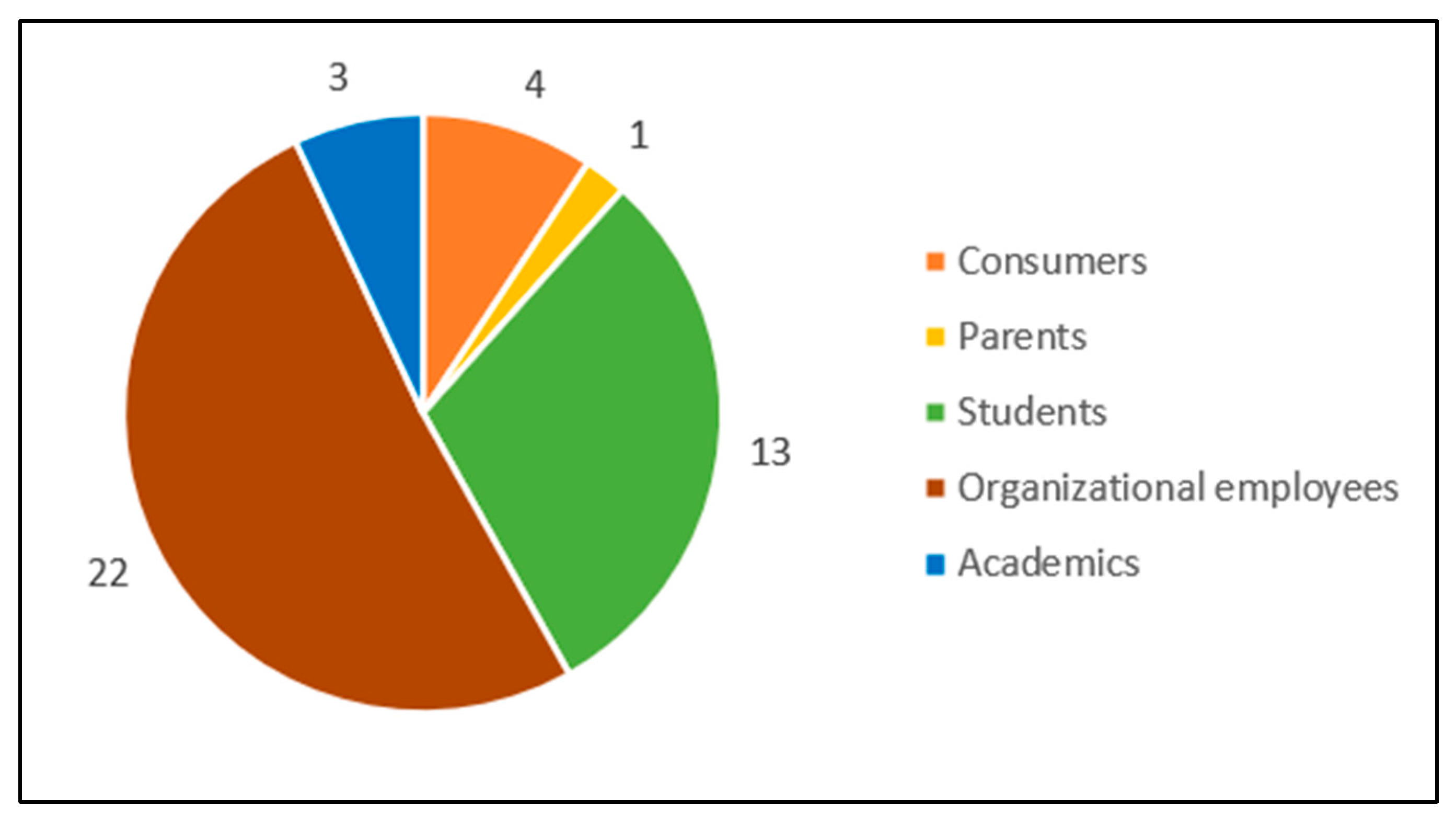
4.9. Main Participants in Cybersecurity Behavior Research
5. Discussion
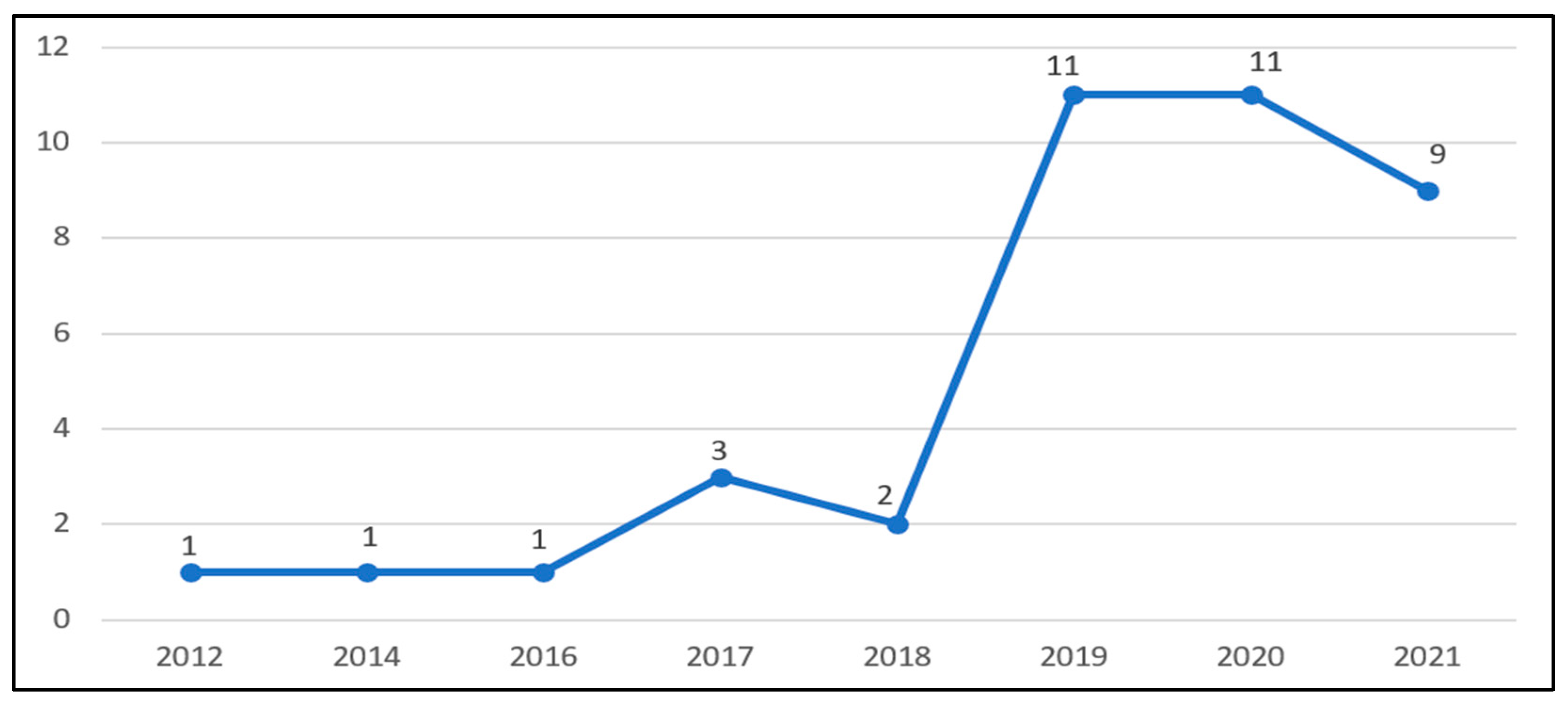
5.1. Rapid Growth in Cybersecurity Behavior Research
5.2. Analysis of Theories and Models in Cybersecurity Behavior
5.3. Cybersecurity Research Themes and Key Factors
5.4. Cybersecurity Research Trends in Diverse Cultural and Socioeconomic Settings
5.5. Research Methodologies in Cybersecurity Behavior
5.6. Participants in Cybersecurity Behavior Research
6. Conclusions and Future Research Agendas
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| # | Source | Year | Theoretical Model | Independent Variables | Dependent Variables | Technology/Service | Methodology | Participants | Country |
|---|---|---|---|---|---|---|---|---|---|
| S01 | [83] | 2021 | Technology Threat Avoidance Theory | “Perceived susceptibility”, “Perceived severity”, “Perceived effectiveness”, “Perceived cost”, and “Self-efficacy” | “Avoidance Motivation” and “Avoidance Behavior” | Internet threats | Quantitative (survey) | Organizational employees | USA |
| S02 | [114] | 2019 | Social Cognitive Theory | “Information security policy”, “Subjective norm”, “Perceived inconvenience”, “Self-efficacy”, “Outcome expectation”, and “Information security monitoring” | Assurance Behavior | Information system | Mixed method (survey and focus group) | Organizational employees | Malaysia |
| S03 | [91] | 2019 | Coping Theory | “Perceived externality” and “Triage” | “Procrastination”, “Psychological detachment”, and “Cybersecurity Behavior” | Information system | Quantitative (survey) | Organizational employees | China |
| S04 | [88] | 2020 | Job Demands-Resources Model | “Continuity demand”, “Mandatory demand”, “Trust enhancement”, and “Professional development” | “Perseverance of effort” and “Intention Behavior” | Information system | Quantitative (survey) | Organizational employees | Not Specified |
| S05 | [100] | 2021 | Compliance Theory and Control Theory | “Reward expectancy”, “Punishment expectancy”, and “Organizational commitment” | “Compliance Behavior” | Not Specified | Quantitative (survey) | Organizational employees | China |
| S06 | [87] | 2021 | Decision-making Theory | “Punishment likelihood”, “Reward likelihood”, and “Neutralization scenarios” | “Intention Behavior” | Information system | Quantitative (survey) | Students | USA |
| S07 | [115] | 2018 | Innovation Diffusion Theory | “Compatibility”, “Ease of use”, “images”, “intention”, “Relative advantage”, “Results demonstrability”, “Trialability”, “Visibility”, and “Voluntariness” | “Intention Behavior” | Internet security software | Quantitative (survey) | Students | Malaysia |
| S08 | [61] | 2019 | Theory of Planned Behavior | “Perceived price level”, “Information security awareness”, “Subjective norms”, and “Perceived behavioral control” | “Attitude” and “Intention Behavior” | Anti-malware software | Quantitative (survey) | Students | Malaysia |
| S09 | [70] | 2017 | Protection Motivation Theory and Threat Avoidance Motivation | “Attitude to personal data”, “Perceived risk”, and “Perceived ease of use” | “Perceived usefulness”, “Intention Behavior”, and “Cybersecurity Behavior” | Social networking sites | Mixed method (survey and focus group) | Consumers | Not Specified |
| S10 | [55] | 2019 | Protection Motivation Theory and Threat Avoidance Motivation | “Self-efficacy”, “Security breach concern level”, “Perceived risk”, “Domain knowledge”, “System characteristics”, “Perceived ease of use”, “Perceived usefulness”, “Value for personalization” and “Attitude to personal data” | “Intention Behavior”, “Cybersecurity Behavior”, “Usage Behavior”, “Value for personalization”, and “Attitude” | Web browser | Quantitative (survey) | Students and academics | China and U.K. |
| S11 | [54] | 2020 | Technology Threat Avoidance Theory | “Fear”, “Safeguard effectiveness”, “Safeguard cost”, “Self-efficacy”, “Perceived severity”, “Perceived susceptibility”, and “Decision-making style” | “Avoidance Motivation” and “Avoidance Behavior” | Game | Quantitative (survey) | Students | Australia |
| S12 | [89] | 2020 | Unified Theory of Acceptance and Usage of Technology | “Performance expectancy”, “Effort expectancy”, “Facilitating conditions”, “Hedonic motivation”, “Social influence”, “Habit”, and “Gamification feature” | “Intention Behavior” and “Usage Behavior” | Game | Quantitative (survey) | Students | Australia |
| S13 | [80] | 2019 | Protection Motivation Theory | “Perceived vulnerability”, “Perceived severity”, “Perceived self-efficacy”, “Perceived response efficacy”, “Perceived costs”, “Organizational determinants”, “Social determinants”, and “Personal determinants” | “Cybersecurity Awareness” and “Cybersecurity Behavior” | Computer | Quantitative (survey) | Organizational employees | Switzerland |
| S14 | [101] | 2020 | Knowledge, Attitude, and Behavior Model | “Greater employment level”, “Grater perception of personal risk”, “Grater dread and unfamiliarity of InfoSec risks”, and “Greater organizational commitment” | “Cybersecurity Awareness” | Internet of Things | Quantitative (survey) | Organizational employees | Australia |
| S15 | [116] | 2019 | Theory of Social Preferences | “Cyber attack experience”, “Perceived cybersecurity risk”, “Perceived cybersecurity value”, and “Social preferences” | “Cooperate Intention” | Ecosystem | Quantitative (survey) | Organizational employees | Norway |
| S16 | [117] | 2020 | Theory of Planned Behavior and Threat Avoidance Motivation | “Subjective norm”, “Attitude”, “Hardness”, “Habit”, “Perceived severity”, and “Perceived vulnerability” | “Compliance Intention” | Not Specified | Quantitative (survey) | Organizational employees | USA |
| S17 | [60] | 2020 | Protection Motivation Theory, Theory of Planned Behavior, and General Deterrence Theory | “Perceived vulnerability”, “Perceived severity”, “Rewards”, “Perceived shame”, “Response efficacy”, “Self-efficacy”, “Response cost”, “Habit”, “Subjective norms”, “Procedural countermeasures”, “Preventive countermeasures”, and “Detective countermeasures” | “Intention Behavior” | Quantitative (survey) | Organizational employees | New Zealand | |
| S18 | [92] | 2020 | Technology Threat Avoidance Theory and Protection Motivation Theory | “Security intention”, “Self-efficacy”, and “Psychological ownership” | “Cybersecurity Behavior” | Smartphone | Quantitative (Survey) | Organizational employees | Not Specified |
| S19 | [90] | 2021 | Big Five Model | “Risk-taking” and “Decision-making styles” | “Intention Behavior” | Game | Quantitative (Survey) | Students and academics | Iran |
| S20 | [118] | 2014 | Protection Motivation Theory | “Explicit cybersecurity policy” | “Peer Behavior” and “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | USA |
| S21 | [119] | 2017 | Protection Motivation Theory | “Computer skills”, “Information seeking skills”, “Experience with cybersecurity practice”, “Perceived susceptibility”, “Perceived severity”, “Self-efficacy”, “Perceived barriers”, “Perceived benefits”, “Response efficacy”, “Cues to action”, and “Peer behavior” | “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | Not Specified |
| S22 | [97] | 2019 | 6-T Internet attitude model | “Social networking sites”, “Communication”, “Video-watching”, “Game-playing”, “Photo-sharing”, “Academy”, “Recreational info. searching”, “Friends making”, “Transaction”, “Individual factors”, and “Parental factors” | “Usage Behavior” | Smartphone | Quantitative (Survey) | Students and parents | Taiwan |
| S23 | [12] | 2021 | Protection Motivation Theory | “Situational support”, “Self-efficacy”, and “Response efficacy” | “Behavioral comprehensiveness” and “Behavioral habits” | Not Specified | Quantitative (Survey) | Students | China |
| S24 | [71] | 2021 | Theory of Planned Behavior | “Agreeableness”, “Conscientiousness”, “Extraversion”, “Neuroticism”, and “Openness” | “Intention Behavior” and “Cybersecurity Awareness” | Social networking sites | Quantitative (Survey) | Consumers | Not Specified |
| S25 | [81] | 2021 | Protection Motivation Theory, Theory of Reasoned Action, and General Deterrence Theory | “National smartphone cybersecurity policies”, “Response cost”, “Top management participation”, “Technology (smartphone-specific) security threats”, “Attitude”, “Self-efficacy”, “Subjective norms”, “Perceived risk vulnerability”, “Perceived response efficacy”, “Perceived severity of sanction”, and “Perceived certainty of sanction” | “Intention Behavior” and “Compliance Behavior” | Smartphone | Quantitative (Survey) | Organizational employees | U.K., USA, and UAE |
| S26 | [64] | 2019 | Protection Motivation Theory | “Peer behavior”, “Cues to action”, “Prior experience with information security practice”, “Perceived severity”, “Perceived vulnerability”, “Perceived barriers”, “Response efficacy”, and “Self-efficacy” | “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | USA |
| S27 | [94] | 2019 | Technology Threat Avoidance Theory and Regret Theory | “Anti-Phishing self-efficacy” and “Anticipated regret” | “Avoidance Motivation” and “Avoidance Behavior” | Smartphone | Quantitative (Survey) | Consumers | Not Specified |
| S28 | [82] | 2020 | Protection Motivation Theory and General Deterrence Theory | “Self-efficacy”, “Perceived severity of sanction”, “Perceived risk vulnerability”, “Response cost”, “Perceived certainty of sanction”, “Severity of the adverse consequences”, “Response efficacy”, “Uncertainty avoidance”, “Power distance”, “Individualism vs. collection”, and “Masculinity vs. femininity” | “Intention Behavior” | Smartphone | Quantitative (Survey) | Organizational employees | USA and UAE |
| S29 | [56] | 2018 | Protection Motivation Theory | “Severity”, “Susceptibility”, “Self-efficacy”, “Response efficacy”, “Response costs”, “Experience”, “Workplace information sensitivity appraisal”, “Responsibility”, “Psychological ownership”, and “Organisational citizenship behaviors” | “Intention Behavior” | Malware | Quantitative (Survey) | Organizational employees | Not Specified |
| S30 | [99] | 2020 | Individual cybersecurity compliance behavior model and Donalds and Osei-Bryson model | “Dominant decision style”, “General security orientation”, “General security awareness”, “Dominant orientation”, and “Security self-efficacy” | “Compliance Behavior” | Not Specified | Quantitative (Survey) | Students and academics | Jamaica |
| S31 | [120] | 2021 | Protection Motivation Theory | “Perceived severity”, “Perceived vulnerability”, “Perceived barriers”, “Response efficacy”, and “Security self-efficacy” | “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | Saudi Arabia |
| S32 | [58] | 2020 | Technology Threat Avoidance Theory | “Perceived susceptibility”, “Perceived severity”, “Perceived effectiveness”, “Perceived cost”, and “Self-efficacy” | “Avoidance Motivation”, “Avoidance Behavior”, and “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | USA |
| S33 | [93] | 2017 | Actor-network Theory | “Familiarity” and “Internet experience proxies” | “Cybersecurity Behavior” | Internet threats | Quantitative (Survey) | Students | U.K. and USA |
| S34 | [72] | 2020 | Protection Motivation Theory and Affect heuristic model | “Affect”, “Perceived risk”, and “Perceived benefit” | “Cybersecurity Behavior” | Social networking sites | Quantitative (Survey) | Consumers | U.K. |
| S35 | [63] | 2019 | Protection Motivation Theory and Health Belief Model | “Perceived vulnerability”, “Prior experience with computer security”, “Perceived severity”, “Security self-efficacy”, “Response efficacy”, “Cues to action”, “Peer behavior”, “Computer skills”, and “Familiarity with cyber threats” | “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Students | Malaysia |
| S36 | [59] | 2016 | Technology Threat Avoidance Theory | “Perceived susceptibility”, “Perceived severity”, “Perceived threat”, “Safeguard effectiveness”, “Safeguard cost”, and “Self-efficacy” | “Avoidance Motivation” and “Avoidance Behavior” | Malware | Quantitative (Survey) | Students | USA |
| S37 | [84] | 2019 | Protection Motivation Theory and Health Belief Model | “Computer skills”, “Experience with cybersecurity practice”, “Perceived vulnerability”, “Perceived severity”, “Self-efficacy”, “Perceived barriers”, “Perceived benefits”, “Response efficacy”, “Cues to action”, and “Peer behavior” | “Cybersecurity Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | USA |
| S38 | [121] | 2012 | Protection Motivation Theory and General Deterrence Theory | “Threat severity”, “Threat vulnerability”, “Self-efficacy”, “Response efficacy”, “Response cost”, “Sanction severity”, “Sanction certainty”, “Agreeableness”, “Conscientiousness”, “Extraversion”, “Neuroticism”, and “Openness” | “Intention Behavior” | Not Specified | Quantitative (Survey) | Organizational employees | USA |
| S39 | [98] | 2021 | Not Specified | “Human Intention and Perception”, “Perceived Trust and beliefs”, “Perceived e-mail security”, “Perceived Privacy”, and “Information Sharing” | “Usage Behavior” | Quantitative (Survey) | Organizational employees | Japan, South Korea, India, Australia, Hong Kong, Taiwan, Singapore, New Zealand, Malaysia, Indonesia, and the Philippines |
References
- Seki, T.; Çimen, F.; Dilmaç, B. The Effect of Emotional Intelligence on Cyber Security: The Mediator Role of Mindfulness. Bartın Univ. J. Fac. Educ. 2023, 12, 190–199. [Google Scholar] [CrossRef]
- González-Manzano, L.; de Fuentes, J.M. Design recommendations for online cybersecurity courses. Comput. Secur. 2019, 80, 238–256. [Google Scholar] [CrossRef]
- NIST. NIST Special Publication 800-181: National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017. [Google Scholar]
- Donalds, C.; Osei-Bryson, K.M. Toward a cybercrime classification ontology: A knowledge-based approach. Comput. Hum. Behav. 2019, 92, 403–418. [Google Scholar] [CrossRef]
- NIST. Cyber Attack—Glossary; CSRC: Gaithersburg, MD, USA, 2012. [Google Scholar]
- Lewis, J.A. Assessing the Risks of Cyber Terrorism, Cyber War and Other Cyber Threats; Center for Strategic & International Studies: Washington, DC, USA, 2002. [Google Scholar]
- Almomani, O.; Almaiah, M.A.; Alsaaidah, A.; Smadi, S.; Mohammad, A.H.; Althunibat, A. Machine Learning Classifiers for Network Intrusion Detection System: Comparative Study. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14–15 July 2021; pp. 440–445. [Google Scholar] [CrossRef]
- Mohammad, A.H. Intrusion Detection Using a New Hybrid Feature Selection Model. Intell. Autom. Soft Comput. 2021, 30, 65–80. [Google Scholar] [CrossRef]
- Von Solms, R.; Van Niekerk, J. From information security to cyber security. Comput. Secur. 2013, 38, 97–102. [Google Scholar] [CrossRef]
- Smadia, S.; Almomanib, O.; Mohammadc, A.; Alauthmand, M.; Saaidahe, A. VPN Encrypted Traffic classification using XGBoost. Int. J. Emerg. Trends Eng. Res. 2021, 9, 960–966. [Google Scholar]
- Cybersecurity Education Guides. Cybersecurity Industries and Domains|Careers and Jobs. Available online: https://www.cybersecurityeducationguides.org/industries-and-domains/ (accessed on 19 March 2023).
- Hong, Y.; Furnell, S. Understanding cybersecurity behavioral habits: Insights from situational support. J. Inf. Secur. Appl. 2021, 57, 102710. [Google Scholar] [CrossRef]
- Reeves, A.; Calic, D.; Delfabbro, P. “Get a red-hot poker and open up my eyes, it’s so boring”1: Employee perceptions of cybersecurity training. Comput. Secur. 2021, 106, 102281. [Google Scholar] [CrossRef]
- Al-Emran, M.; Griffy-Brown, C. The role of technology adoption in sustainable development: Overview, opportunities, challenges, and future research agendas. Technol. Soc. 2023, 73, 102240. [Google Scholar] [CrossRef]
- Chowdhury, N.H.; Adam, M.T.P.; Teubner, T. Time pressure in human cybersecurity behavior: Theoretical framework and countermeasures. Comput. Secur. 2020, 97, 101931. [Google Scholar] [CrossRef]
- Mashiane, T.; Kritzinger, E. Cybersecurity Behaviour: A Conceptual Taxonomy. In Information Security Theory and Practice; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Cham, Switzerland, 2019; Volume 11469, pp. 147–156. [Google Scholar]
- Zwilling, M.; Klien, G.; Lesjak, D.; Wiechetek, Ł.; Cetin, F.; Basim, H.N. Cyber Security Awareness, Knowledge and Behavior: A Comparative Study. J. Comput. Inf. Syst. 2022, 62, 82–97. [Google Scholar] [CrossRef]
- Rogers, R.W. Cognitive and physiological processes in fear appeals and attitude change: A revised theory of protection motivation. In Social Psychophysiology: A Sourcebook; Guilford Press: New York, NY, USA, 1983; pp. 153–176. [Google Scholar]
- Ajzen, I. The theory of planned behavior. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Khando, K.; Gao, S.; Islam, S.M.; Salman, A. Enhancing employees information security awareness in private and public organisations: A systematic literature review. Comput. Secur. 2021, 106, 102267. [Google Scholar] [CrossRef]
- Svabensky, V.; Vykopal, J.; Celeda, P. What Are Cybersecurity Education Papers About? A Systematic Literature Review of SIGCSE and ITiCSE Conferences. In Proceedings of the 51st ACM Technical Symposium on Computer Science Education, SIGCSE 2020, Portland, OR, USA, 11–14 March 2020; pp. 2–8. [Google Scholar] [CrossRef]
- Fujs, D.; Mihelič, A.; Vrhovec, S.L.R. The power of interpretation: Qualitative methods in cybersecurity research. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; ACM: New York, NY, USA, 2019. [Google Scholar]
- AlShamsi, M.; Al-Emran, M.; Shaalan, K. A Systematic Review on Blockchain Adoption. Appl. Sci. 2022, 12, 4245. [Google Scholar] [CrossRef]
- Al-Qaysi, N.; Mohamad-Nordin, N.; Al-Emran, M. Factors Affecting the Adoption of Social Media in Higher Education: A Systematic Review of the Technology Acceptance Model. In Recent Advances in Intelligent Systems and Smart Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 571–584. [Google Scholar]
- Alqudah, A.A.; Al-Emran, M.; Shaalan, K. Technology Acceptance in Healthcare: A Systematic Review. Appl. Sci. 2021, 11, 10537. [Google Scholar] [CrossRef]
- Alsharida, R.A.; Hammood, M.M.; Al-Emran, M. Mobile Learning Adoption: A Systematic Review of the Technology Acceptance Model from 2017 to 2020. Int. J. Emerg. Technol. Learn. 2021, 15, 147–162. [Google Scholar] [CrossRef]
- Baraković, S.; Husić, J.B. The Importance of Security Matters for Quality of Experience in Mobile Web Context. Int. J. Hum.–Comput. Interact. 2022, 39, 1712–1722. [Google Scholar] [CrossRef]
- Rahman, T.; Rohan, R.; Pal, D.; Kanthamanon, P. Human Factors in Cybersecurity: A Scoping Review. In Proceedings of the 12th International Conference on Advances in Information Technology, Bangkok, Thailand, 29 June 2021–1 July 2021; ACM: New York, NY, USA, 2021. [Google Scholar] [CrossRef]
- Mc Mahon, C. In Defence of the Human Factor. Front. Psychol. 2020, 11, 2–5. [Google Scholar] [CrossRef]
- Maalem Lahcen, R.A.; Caulkins, B.; Mohapatra, R.; Kumar, M. Review and insight on the behavioral aspects of cybersecurity. Cybersecurity 2020, 3, 10. [Google Scholar] [CrossRef]
- Alshaikh, M. Developing cybersecurity culture to influence employee behavior: A practice perspective. Comput. Secur. 2020, 98, 102003. [Google Scholar] [CrossRef]
- Edkrantz, M.; Truve, S.; Said, A. Predicting Vulnerability Exploits in the Wild. In Proceedings of the 2nd International Conference on Cyber Security and Cloud Computing, New York, NY, USA, 3–5 November 2015; pp. 513–514. [Google Scholar] [CrossRef]
- Klimburg-Witjes, N.; Wentland, A. Hacking Humans? Social Engineering and the Construction of the “Deficient User” in Cybersecurity Discourses. Sci. Technol. Hum. Values 2021, 46, 1316–1339. [Google Scholar] [CrossRef]
- Quayyum, F.; Cruzes, D.S.; Jaccheri, L. Cybersecurity awareness for children: A systematic literature review. Int. J. Child-Comput. Interact. 2021, 30, 100343. [Google Scholar] [CrossRef]
- Herath, T.B.G.; Khanna, P.; Ahmed, M. Cybersecurity Practices for Social Media Users: A Systematic Literature Review. J. Cybersecur. Priv. 2022, 2, 1. [Google Scholar] [CrossRef]
- Coventry, L.; Branley, D. Cybersecurity in healthcare: A narrative review of trends, threats and ways forward. Maturitas 2018, 113, 48–52. [Google Scholar] [CrossRef]
- Nifakos, S.; Chandramouli, K.; Nikolaou, C.K.; Papachristou, P.; Koch, S.; Panaousis, E.; Bonacina, S. Influence of Human Factors on Cyber Security within Healthcare Organisations: A Systematic Review. Sensors 2021, 21, 5119. [Google Scholar] [CrossRef]
- Khan, N.F.; Yaqoob, A.; Khan, M.S.; Ikram, N. The cybersecurity behavioral research: A tertiary study. Comput. Secur. 2022, 120, 102826. [Google Scholar] [CrossRef]
- Chowdhury, N.H.; Adam, M.T.P.; Skinner, G. The impact of time pressure on cybersecurity behaviour: A systematic literature review. Behav. Inf. Technol. 2019, 38, 1290–1308. [Google Scholar] [CrossRef]
- Sulaiman, N.S.; Fauzi, M.A.; Wider, W.; Rajadurai, J.; Hussain, S.; Harun, S.A. Cyber–Information Security Compliance and Violation Behaviour in Organisations: A Systematic Review. Soc. Sci. 2022, 11, 386. [Google Scholar] [CrossRef]
- Jeong, J.; Mihelcic, J.; Oliver, G.; Rudolph, C. Towards an improved understanding of human factors in cybersecurity. In Proceedings of the 5th International Conference on Collaboration and Internet Computing (CIC), Los Angeles, CA, USA, 12–14 December 2019; pp. 338–345. [Google Scholar] [CrossRef]
- Hakami, M.; Alshaikh, M. Identifying Strategies to Address Human Cybersecurity Behavior: A Review Study. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2022, 22, 299–309. [Google Scholar]
- Kalhoro, S.; Rehman, M.; Ponnusamy, V.A.P.; Shaikh, F. Extracting Key Factors of Cyber Hygiene Behaviour among Software Engineers: A Systematic Literature Review. IEEE Access 2021, 9, 99339–99363. [Google Scholar] [CrossRef]
- Kuppusamy, P.; Samy, G.N.; Maarop, N.; Shanmugam, B.; Perumal, S. Information Security Policy Compliance Behavior Models, Theories, and Influencing Factors: A Systematic Literature Review. J. Theor. Appl. Inf. Technol. 2022, 100, 1536–1557. [Google Scholar]
- Alnifie, K.M.; Kim, C. Appraising the Manifestation of Optimism Bias and Its Impact on Human Perception of Cyber Security: A Meta Analysis. J. Inf. Secur. 2023, 14, 93–110. [Google Scholar] [CrossRef]
- Chang, V.; Golightly, L.; Xu, Q.A.; Boonmee, T.; Liu, B.S. Cybersecurity for children: An investigation into the application of social media. Enterp. Inf. Syst. 2023, 17, 2188122. [Google Scholar] [CrossRef]
- Kannelønning, K.; Katsikas, S.K. A systematic literature review of how cybersecurity-related behavior has been assessed. Inf. Comput. Secur. 2023. [Google Scholar] [CrossRef]
- Al-Saedi, K.; Al-Emran, M. A Systematic Review of Mobile Payment Studies from the Lens of the UTAUT Model. In Recent Advances in Technology Acceptance Models and Theories; Springer: Cham, Switzerland, 2021; Volume 335, pp. 79–106. [Google Scholar]
- Marangunić, N.; Granić, A. Technology acceptance model: A literature review from 1986 to 2013. Univers. Access Inf. Soc. 2015, 14, 81–95. [Google Scholar] [CrossRef]
- Fatehah, M.; Mezhuyev, V.; Al-Emran, M. A Systematic Review of Metamodelling in Software Engineering. In Recent Advances in Intelligent Systems and Smart Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 3–27. [Google Scholar]
- Al-Qaysi, N.; Granić, A.; Al-Emran, M.; Ramayah, T.; Garces, E.; Daim, T.U. Social media adoption in education: A systematic review of disciplines, applications, and influential factors. Technol. Soc. 2023, 73, 102249. [Google Scholar] [CrossRef]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; Software Engineering Group, School of Computer Science and Mathematics, Keele University: Newcastle, UK, 2007; pp. 1–57. [Google Scholar]
- Costa, V.; Monteiro, S. Key knowledge management processes for innovation: A systematic literature review. VINE J. Inf. Knowl. Manag. Syst. 2016, 46, 386–410. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Does Decision-Making Style Predict Individuals’ Cybersecurity Avoidance Behaviour? In HCI for Cybersecurity, Privacy and Trust; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; Volume 12210, ISBN 9783030503086. [Google Scholar]
- Addae, J.H.; Sun, X.; Towey, D.; Radenkovic, M. Exploring user behavioral data for adaptive cybersecurity. User Model. User-Adapt. Interact. 2019, 29, 701–750. [Google Scholar] [CrossRef]
- Blythe, J.M.; Coventry, L. Costly but effective: Comparing the factors that influence employee anti-malware behaviours. Comput. Hum. Behav. 2018, 87, 87–97. [Google Scholar] [CrossRef]
- Al-Emran, M.; AlQudah, A.A.; Abbasi, G.A.; Al-Sharafi, M.A.; Iranmanesh, M. Determinants of Using AI-Based Chatbots for Knowledge Sharing: Evidence From PLS-SEM and Fuzzy Sets (fsQCA). IEEE Trans. Eng. Manag. 2023. [Google Scholar] [CrossRef]
- Gillam, A.R.; Foster, W.T. Factors affecting risky cybersecurity behaviors by U.S. workers: An exploratory study. Comput. Hum. Behav. 2020, 108, 106319. [Google Scholar] [CrossRef]
- Young, D.; Carpenter, D.; McLeod, A. Malware Avoidance Motivations and Behaviors: A Technology Threat Avoidance Replication. AIS Trans. Replication Res. 2016, 2, 1–17. [Google Scholar] [CrossRef]
- Shahbaznezhad, H.; Kolini, F.; Rashidirad, M. Employees’ Behavior in Phishing Attacks: What Individual, Organizational, and Technological Factors Matter? J. Comput. Inf. Syst. 2020, 61, 539–550. [Google Scholar] [CrossRef]
- Vafaei-Zadeh, A.; Thurasamy, R.; Hanifah, H. Modeling anti-malware use intention of university students in a developing country using the theory of planned behavior. Kybernetes 2019, 48, 1565–1585. [Google Scholar] [CrossRef]
- Al-Emran, M.; Al-Nuaimi, M.N.; Arpaci, I.; Al-Sharafi, M.A.; Anthony Jnr, B. Towards a wearable education: Understanding the determinants affecting students’ adoption of wearable technologies using machine learning algorithms. Educ. Inf. Technol. 2022, 28, 2727–2746. [Google Scholar] [CrossRef]
- Fatokun, F.B.; Hamid, S.; Norman, A.; Fatokun, J.O. The Impact of Age, Gender, and Educational level on the Cybersecurity Behaviors of Tertiary Institution Students: An Empirical investigation on Malaysian Universities. J. Phys. Conf. Ser. 2019, 1339, 12098. [Google Scholar] [CrossRef]
- Li, L.; He, W.; Xu, L.; Ash, I.; Anwar, M.; Yuan, X. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. Int. J. Inf. Manag. 2019, 45, 13–24. [Google Scholar] [CrossRef]
- Ryle, P.; Yan, J.; Gardiner, L.R. Gramm-Leach-Bliley Gets a Systems Upgrade: What the Ftc’S Proposed Safeguards Rule Changes Mean for Small and Medium American Financial Institutions. EDPACS 2022, 65, 6–17. [Google Scholar] [CrossRef]
- Buzan, T. Tony Buzan|Inventor of Mind Mapping.
- Al-Qaysi, N.; Mohamad-Nordin, N.; Al-Emran, M. What leads to social learning? Students’ attitudes towards using social media applications in Omani higher education. Educ. Inf. Technol. 2020, 25, 2157–2174. [Google Scholar] [CrossRef]
- Al-Qaysi, N.; Mohamad-Nordin, N.; Al-Emran, M.; Al-Sharafi, M.A. Understanding the differences in students’ attitudes towards social media use: A case study from Oman. In Proceedings of the 2019 IEEE Student Conference on Research and Development (SCOReD), Bandar Seri Iskandar, Malaysia, 15–17 October 2019; pp. 176–179. [Google Scholar]
- Jain, A.K.; Sahoo, S.R.; Kaubiyal, J. Online social networks security and privacy: Comprehensive review and analysis. Complex Intell. Syst. 2021, 7, 2157–2177. [Google Scholar] [CrossRef]
- Addae, J.H.; Brown, M.; Sun, X.; Towey, D.; Radenkovic, M. Measuring attitude towards personal data for adaptive cybersecurity. Inf. Comput. Secur. 2017, 25, 560–579. [Google Scholar] [CrossRef]
- Van der Schyff, K.; Flowerday, S. Mediating effects of information security awareness. Comput. Secur. 2021, 106, 102313. [Google Scholar] [CrossRef]
- Van Schaik, P.; Renaud, K.; Wilson, C.; Jansen, J.; Onibokun, J. Risk as affect: The affect heuristic in cybersecurity. Comput. Secur. 2020, 90, 101651. [Google Scholar] [CrossRef]
- Varshney, G.; Misra, M.; Atrey, P. Secure authentication scheme to thwart RT MITM, CR MITM and malicious browser extension based phishing attacks. J. Inf. Secur. Appl. 2018, 42, 1–17. [Google Scholar] [CrossRef]
- Gratian, M.; Bandi, S.; Cukier, M.; Dykstra, J.; Ginther, A. Correlating human traits and cyber security behavior intentions. Comput. Secur. 2018, 73, 345–358. [Google Scholar] [CrossRef]
- Fischer, E.A. Cybersecurity Issues and Challenges: In Brief; Congressional Research Service: Washington, DC, USA, 2016. [Google Scholar]
- Cybint 15 Alarming Cyber Security Facts and Stats. Available online: https://www.cybintsolutions.com/cyber-security-facts-stats/ (accessed on 28 October 2021).
- Proofpoint. An In-Depth Look at User Awareness, Vulnerability and Resilience; Proofpoint: Sunnyvale, CA, USA, 2020. [Google Scholar]
- Katsikeas, S.; Johnson, P.; Ekstedt, M.; Lagerström, R. Research communities in cyber security: A comprehensive literature review. Comput. Sci. Rev. 2021, 42, 100431. [Google Scholar] [CrossRef]
- Al-Emran, M.; Granić, A.; Al-Sharafi, M.A.; Ameen, N.; Sarrab, M. Examining the roles of students’ beliefs and security concerns for using smartwatches in higher education. J. Enterp. Inf. Manag. 2021, 34, 1229–1251. [Google Scholar] [CrossRef]
- Simonet, J.; Teufel, S. The influence of organizational, social and personal factors on cybersecurity awareness and behavior of home computer users. IFIP Adv. Inf. Commun. Technol. 2019, 562, 194–208. [Google Scholar] [CrossRef]
- Ameen, N.; Tarhini, A.; Shah, M.H.; Madichie, N.; Paul, J.; Choudrie, J. Keeping customers’ data secure: A cross-cultural study of cybersecurity compliance among the Gen-Mobile workforce. Comput. Hum. Behav. 2021, 114, 106531. [Google Scholar] [CrossRef]
- Ameen, N.; Tarhini, A.; Shah, M.H.; Madichie, N.O.; Hussain Shah, M.; Madichie, N.O. Employees’ behavioural intention to smartphone security: A gender-based, cross-national study. Comput. Hum. Behav. 2020, 104, 106184. [Google Scholar] [CrossRef]
- Gillam, A.R.; Waite, A.M. Gender differences in predictors of technology threat avoidance. Inf. Comput. Secur. 2021, 29, 393–412. [Google Scholar] [CrossRef]
- Anwar, M.; We, H.; Ash, I.; Yuan, X.; Li, L.; Xu, L. Gender Difference and Employees’ Cybersecurity Behaviors. Comput. Hum. Behav. 2017, 69, 437–443. [Google Scholar] [CrossRef]
- Alsharida, R.A.; Al-rimy, B.A.S.; Al-Emran, M.; Zainal, A. A systematic review of multi perspectives on human cybersecurity behavior. Technol. Soc. 2023, 73, 102258. [Google Scholar] [CrossRef]
- Alshaikh, M.; Adamson, B. From awareness to influence: Toward a model for improving employees’ security behaviour. Pers. Ubiquitous Comput. 2021, 25, 829–841. [Google Scholar] [CrossRef]
- Bansal, G.; Muzatko, S.; Shin, S. Il Information system security policy noncompliance: The role of situation-specific ethical orientation. Inf. Technol. People 2021, 34, 250–296. [Google Scholar] [CrossRef]
- Li, Y.; Pan, T.; Zhang, N. From hindrance to challenge: How employees understand and respond to information security policies. J. Enterp. Inf. Manag. 2020, 33, 191–213. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M.; Alrowaily, M. The Impact of Gamification Factor in the Acceptance of Cybersecurity Awareness Augmented Reality Game (Cybar). In HCI for Cybersecurity, Privacy and Trust; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; Volume 12210, ISBN 9783030503086. [Google Scholar]
- Abroshan, H.; Devos, J.; Poels, G.; Laermans, E. Phishing Happens beyond Technology: The Effects of Human Behaviors and Demographics on Each Step of a Phishing Process. IEEE Access 2021, 9, 44928–44949. [Google Scholar] [CrossRef]
- Xu, Z.; Guo, K. It ain’t my business: A coping perspective on employee effortful security behavior. J. Enterp. Inf. Manag. 2019, 32, 824–842. [Google Scholar] [CrossRef]
- Verkijika, S.F. Employees’ Cybersecurity Behaviour in the Mobile Context: The Role of Self-Efficacy and Psychological Ownership. In Proceedings of the 2nd International Multidisciplinary Information Technology and Engineering Conference (IMITEC), Kimberley, South Africa, 25–27 November 2020. [Google Scholar] [CrossRef]
- Jeske, D.; van Schaik, P. Familiarity with Internet threats: Beyond awareness. Comput. Secur. 2017, 66, 129–141. [Google Scholar] [CrossRef]
- Verkijika, S.F. “If you know what to do, will you take action to avoid mobile phishing attacks”: Self-efficacy, anticipated regret, and gender. Comput. Hum. Behav. 2019, 101, 286–296. [Google Scholar] [CrossRef]
- Packetlabs Cybersecurity Statistics for 2021. Available online: https://www.packetlabs.net/cybersecurity-statistics-2021/ (accessed on 29 October 2021).
- ACSC. ACSC Annual Cyber Threat Report 2020–21. Available online: https://www.cyber.gov.au/acsc/view-all-content/reports-and-statistics/acsc-annual-cyber-threat-report-2020-21 (accessed on 29 October 2021).
- Chou, H.L.; Chou, C. A quantitative analysis of factors related to Taiwan teenagers’ smartphone addiction tendency using a random sample of parent-child dyads. Comput. Hum. Behav. 2019, 99, 335–344. [Google Scholar] [CrossRef]
- Sivarethinamohan, R.; Sujatha, S. Behavioral Intentions towards adoption of Information Protection and Cyber security (Email Security and Online Privacy): SEM model. Turk. J. Comput. Math. Educ. 2021, 12, 56–68. [Google Scholar] [CrossRef]
- Donalds, C.; Osei-Bryson, K.M. Cybersecurity compliance behavior: Exploring the influences of individual decision style and other antecedents. Int. J. Inf. Manag. 2020, 51, 102056. [Google Scholar] [CrossRef]
- Liu, C.; Liang, H.; Wang, N.; Xue, Y. Ensuring employees’ information security policy compliance by carrot and stick: The moderating roles of organizational commitment and gender. Inf. Technol. People 2021, 35, 802–834. [Google Scholar] [CrossRef]
- Reeves, A.; Parsons, K.; Calic, D. Whose risk is it anyway: How do risk perception and organisational commitment affect employee information security awareness? In Proceedings of the International Conference on Human-Computer Interaction, Copenhagen, Denmark, 19–24 July 2020; Springer: Cham, Switzerland, 2020; pp. 232–249. [Google Scholar]
- Sun, H.; Zhang, P. The role of moderating factors in user technology acceptance. Int. J. Hum. Comput. Stud. 2006, 64, 53–78. [Google Scholar] [CrossRef]
- Arpaci, I.; Huang, S.; Al-Emran, M.; Al-Kabi, M.N.; Peng, M. Predicting the COVID-19 infection with fourteen clinical features using machine learning classification algorithms. Multimed. Tools Appl. 2021, 80, 11943–11957. [Google Scholar] [CrossRef]
- Zaza, S.; Al-Emran, M. Mining and exploration of credit cards data in UAE. In Proceedings of the 2015 5th International Conference on e-Learning, ECONF 2015, Manama, Bahrain, 18–20 October 2015; IEEE: New York, NY, USA, 2015; pp. 275–279. [Google Scholar]
- Mijwil, M.M.; Salem, I.E.; Ismaeel, M.M. The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review. Iraqi J. Comput. Sci. Math. 2023, 4, 87–101. [Google Scholar] [CrossRef]
- Pattnaik, N.; Li, S.; Nurse, J.R.C. Perspectives of non-expert users on cyber security and privacy: An analysis of online discussions on twitter. Comput. Secur. 2023, 125, 103008. [Google Scholar] [CrossRef]
- Liu, B.; Wei, L. Unintended effects of open data policy in online behavioral research: An experimental investigation of participants’ privacy concerns and research validity. Comput. Hum. Behav. 2023, 139, 107537. [Google Scholar] [CrossRef]
- Lin, W.; Xu, M.; He, J.; Zhang, W. Privacy, security and resilience in mobile healthcare applications. Enterp. Inf. Syst. 2023, 17, 1–15. [Google Scholar] [CrossRef]
- Huang, Y.; Li, Y.J.; Cai, Z. Security and Privacy in Metaverse: A Comprehensive Survey. Big Data Min. Anal. 2023, 6, 234–247. [Google Scholar] [CrossRef]
- Koohang, A.; Nord, J.; Ooi, K.; Tan, G.; Al-Emran, M.; Aw, E.; Baabdullah, A.; Buhalis, D.; Cham, T.; Dennis, C.; et al. Shaping the Metaverse into Reality: A Holistic Multidisciplinary Understanding of Opportunities, Challenges, and Avenues for Future Investigation. J. Comput. Inf. Syst. 2023, 63, 735–765. [Google Scholar] [CrossRef]
- Hong, W.C.H.; Chi, C.Y.; Liu, J.; Zhang, Y.F.; Lei, V.N.L.; Xu, X.S. The Influence of Social Education Level on Cybersecurity Awareness and Behaviour: A Comparative Study of University Students and Working Graduates. Educ. Inf. Technol. 2023, 28, 439–470. [Google Scholar] [CrossRef]
- Limna, P.; Siripipattanakul, S. The Relationship between Cyber Security Knowledge, Awareness and Behavioural Choice Protection among Mobile Banking Users in Thailand. Int. J. Comput. Sci. Res. 2022, 7, 1–19. [Google Scholar] [CrossRef]
- Rohan, R.; Pal, D.; Hautamäki, J.; Funilkul, S.; Chutimaskul, W.; Thapliyal, H. A systematic literature review of cybersecurity scales assessing information security awareness. Heliyon 2023, 9, e14234. [Google Scholar] [CrossRef]
- Ahmad, Z.; Ong, T.S.; Liew, T.H.; Norhashim, M. Security monitoring and information security assurance behaviour among employees: An empirical analysis. Inf. Comput. Secur. 2019, 27, 165–188. [Google Scholar] [CrossRef]
- Vafaei-Zadeh, A.; Ramayah, T.; Wong, W.P.; Md Hanifah, H. Modelling internet security software usage among undergraduate students: A necessity in an increasingly networked world. VINE J. Inf. Knowl. Manag. Syst. 2018, 48, 2–20. [Google Scholar] [CrossRef]
- Kianpour, M.; Øverby, H.; Kowalski, S.J.; Frantz, C. Social Preferences in Decision Making Under Cybersecurity Risks and Uncertainties. In HCI for Cybersecurity, Privacy and Trust; Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2019; Volume 11594, pp. 149–163. [Google Scholar] [CrossRef]
- Aigbefo, Q.A.; Blount, Y.; Marrone, M. The influence of hardiness and habit on security behaviour intention. Behav. Inf. Technol. 2020, 41, 1151–1170. [Google Scholar] [CrossRef]
- Li, L.; He, W.; Xu, L.; Ivan, A.; Anwar, M.; Yuan, X. Does explicit information security policy affect employees’ cyber security behavior? A pilot study. In Proceedings of the 2nd International Conference on Enterprise Systems, Shanghai, China, 2–3 August 2014; pp. 169–173. [Google Scholar] [CrossRef]
- Anwar, M.; He, W.; Yuan, X. Employment status and cybersecurity behaviors. In Proceedings of the 2016 International Conference on Behavioral, Economic and Socio-Cultural Computing (BESC), Durham, NC, USA, 11–13 November 2016; IEEE: New York, NY, USA, 2016; pp. 1–2. [Google Scholar]
- Alghamdi, M.I. Determining the impact of cyber security awareness on employee behaviour: A case of Saudi Arabia. Mater. Today Proc. 2021. [Google Scholar] [CrossRef]
- McBride, M.; Carter, L.; Warkentin, M. Exploring the Role of Individual Employee Characteristics and Personality on Employee Compliance with Cybersecurity Policies; RTI International: Research Triangle Park, NC, USA, 2012; ISBN 3312021278. [Google Scholar]

| Source | Review Type | Number of Reviewed Studies | Domain | Aim |
|---|---|---|---|---|
| [36] | Narrative review | 1249 | Healthcare | Understanding and identifying the vulnerabilities and cybersecurity threats and their effect on healthcare. |
| [43] | Systematic review | 35 | Software Engineering | Understanding user differences related to good or bad cyber hygiene behavior, and what users can do to support good cyber hygiene. |
| [37] | Systematic review | 70 | Healthcare | Uncovering the prevalent factors affecting a healthcare organization’s cybersecurity posture due to a lack of awareness of the cyber threat to healthcare, identifying healthcare organizations’ cyber defense strategy through studying human behavior, and examining the organization’s risk assessment approach and cybersecurity policies that have been enacted. |
| [41] | Systematic review | 27 | Social Science | Investigating human factors in cybersecurity, which are subjective and often complex. |
| [34] | Taxonomy review | 56 | Global | Reviewing the existing literature on cybersecurity awareness among young people. |
| [39] | Systematic review | 21 | Global | Consolidating a paradigm that examines the influence of temporal constraints on human cybersecurity behaviors. |
| [40] | Systematic review | 60 | Social sciences | Understanding the underlying human behavioral factors influencing cyber-information security compliance from theoretical perspectives. |
| [38] | Systematic review | 107 | Social sciences | Investigating trends in cybersecurity behavioral research by synthesizing secondary literature. |
| [35] | Systematic review | 43 | Computer science | Reviewing research on the recommended cybersecurity practices for social media users from the user’s point of view. |
| [42] | Systematic review | 33 | Computer science | Identifying strategies to address human factors in cybersecurity. |
| [44] | Systematic review | 32 | Computer science | Identifying information security policy compliance behavior factors, models, and theories. |
| [45] | Meta-analysis | 9 | Social science-es | Investigating the impact of cyber optimistic bias on an individual’s security risk perception and its subsequent influence on their decision-making process. |
| [46] | Systematic review | 54 | Computer science | Analyzing teenagers’ behavior and its potential susceptibility to exploitation on social media platforms. |
| [47] | Systematic review | 26 | Social science | Evaluating common approaches utilized in examining cybersecurity-related behavior. |
| This Study | Systematic review | 39 | Global | Conducting a systematic review of cybersecurity behavior from the perspective of IS theories and models to examine the main research themes, influential factors, dominant technologies and services, research methods, active countries, and the interrelationships among these characteristics. |
| Inclusion Criteria | Exclusion Criteria |
|---|---|
| Addresses cybersecurity behavior. | Behavior is covered but not cybersecurity. |
| Discusses a theoretical model. | Cybersecurity behavior is described without presenting a theoretical model. |
| Should be written in English. | Articles written in a language other than English. |
| Theories and Models | Frequency |
|---|---|
| Protection Motivation Theory | 17 |
| Technology Threat Avoidance Theory | 6 |
| General Deterrence Theory | 4 |
| Theory of Planned Behavior | 4 |
| Threat Avoidance Motivation | 3 |
| Health Belief Model | 2 |
| Control Theory | 1 |
| Theory of Reasoned Action | 1 |
| Decision-making Theory | 1 |
| Compliance Theory | 1 |
| Donalds and Osei-Bryson Model | 1 |
| Knowledge, Attitude, and Behavior Model | 1 |
| Actor-network Theory | 1 |
| Regret Theory | 1 |
| Affect Heuristic Model | 1 |
| Theory of Social Preferences | 1 |
| Big Five Model | 1 |
| Social Cognitive Theory | 1 |
| 6-T Internet Attitude Model | 1 |
| Coping Theory | 1 |
| Job Demands-Resources Model | 1 |
| Unified Theory of Acceptance and Usage of Technology | 1 |
| Individual Cybersecurity Compliance Behavior Model | 1 |
| Innovation Diffusion Theory | 1 |
| Theories/Models | Strengths | Limitations |
|---|---|---|
| Protection Motivation Theory (PMT) | PMT explains how people respond to fear appeals. It considers two elements related to protection motivation: threat appraisal and coping appraisal [54]. Cybersecurity behavior studies have shown that PMT effectively changes behavior [55]. | PMT fails to consider environmental elements, which affect behavior. For example, it does not consider the effect of social norms. Additionally, it does not consider cognitive variables influencing decision making. For instance, it does not consider the role of experience in behavior [56]. PMT also lacks consideration of individual differences [18]. PMT assumes everyone responds to threats similarly, but this is not always true. This is because individuals have different perceptions of what is threatening, and their reactions may vary based on their past experiences, beliefs, and attitudes. |
| Technology Threat Avoidance Theory (TTAT) | TTAT adopts a broad perspective in explaining the users’ awareness of technology threats and their motivation to avoid them [57]. In addition to threat and coping appraisal, it considers elements related to coping. More importantly, it includes factors related to risk tolerance and social influence [58]. It has been found to be a valid framework for examining users’ cybersecurity behavior toward malware [59]. | TTAT does not cover individual threat motivations adequately [58]. Individual characteristics, such as the propensity for risk and impulsivity, influence people’s actions. Its broad nature also makes implementing it in practical settings difficult. Additionally, TTAT focuses mainly on technical measures to prevent cyber threats and overlooks other critical aspects of cybersecurity, such as policy, governance, and organizational culture. |
| General Deterrence Theory (GDT) | GDT adopts a rational approach to deterring negative behavior by using countermeasures, such as sanctions and other disincentives [60]. Increasing the perception that offenders will be caught and punished can promote positive behavior. | GDT fails to consider that negative actions are often irrational. In addition to personal factors, other environmental variables can influence an individual to engage in harmful behavior [60]. Offenders might feel that they can get away by committing an offense. This is particularly common in cybersecurity, as attackers can remain anonymous. Similarly, if the sanction is minor, attackers can agree to bear the risk. |
| Theory of Planned Behavior (TPB) | TPB considers the role of subjective norms in influencing the initiation and maintenance of behavior [61]. It also considers the role of perceived behavioral control and attitudes in affecting the intention to use technology [62]. This theory has also been used to model behavior in cybersecurity [61]. | While the TPB considers the availability of the resources needed to perform the required behavior [61], it fails to consider personal factors that influence motivation and intention. Although the theory considers normative influences, it fails to consider environmental factors. It posits that the decision-making process is linear, which might not be the case in all situations. The TPB assumes that attitudes and intentions are the primary determinants of behavior [19]. However, there may be a significant gap between individuals’ attitudes and actual behavior, particularly in examining cybersecurity behavior. Additionally, the TPB assumes that individuals have control over their behavior. However, in cybersecurity behavior, individuals may not have complete control over their actions due to other factors, such as technical constraints or external threats. |
| Threat Avoidance Motivation (TAM) | TAM posits that the motivation to avoid a threat is premised on perceived vulnerability and severity [55]. Its main strength is that it offers a framework for describing how individuals avoid threats. It also adopts a rational approach to explaining the behavior of people. | The theory adopts a narrow approach to explaining the motivation to avoid threats. Another limitation of the theory is that it may be based on an incomplete or inaccurate understanding of the existing threats. This can result in individuals focusing on the wrong threats or failing to prepare for potential attacks adequately. The theory can also be challenging to evaluate cybersecurity behavior in organizations with large and complex security environments. This is due to the limitations of effective threat avoidance strategies. In general, it has not been examined sufficiently in cybersecurity behavior research. |
| Health Belief Model (HBM) | HBM considers cognitive elements that influence behavior. This is based on four factors: susceptibility, benefits, severity, and barriers [63]. This broad examination of an individual’s beliefs enables the adoption of holistic strategies for changing behavior. HBM can be leveraged to promote positive cybersecurity behavior. | HBM is a psychological model, which means that other external factors influencing behavior, such as economic and environmental factors, are not considered. Additionally, it does not explain routine factors that routinely influence decision making. It also lacks an explanation of the beliefs and attitudes affecting behavior. It does not account for peer pressure and social norms controlling behavior. |
| Research Themes | Frequency |
|---|---|
| Intention behavior | 14 |
| Cybersecurity behavior | 14 |
| Avoidance behavior | 5 |
| Avoidance motivation | 5 |
| Usage behavior | 4 |
| Compliance behavior | 3 |
| Cybersecurity awareness | 3 |
| Attitude | 2 |
| Procrastination | 1 |
| Perceived usefulness | 1 |
| Value for personalization | 1 |
| Assurance behavior | 1 |
| Perseverance of effort | 1 |
| Behavioral comprehensiveness | 1 |
| Cooperate intention | 1 |
| Psychological detachment | 1 |
| Behavioral habits | 1 |
| Compliance intention | 1 |
| Peer behavior | 1 |
| External Factors | Frequency |
|---|---|
| Self-efficacy | 16 |
| Perceived severity | 12 |
| Response efficacy | 10 |
| Perceived vulnerability | 7 |
| Perceived susceptibility | 5 |
| Response costs | 5 |
| Subjective norm | 5 |
| Cues to action | 4 |
| Peer behavior | 4 |
| Perceived barriers | 4 |
| Perceived risk | 3 |
| Perceived benefit | 3 |
| Habit | 3 |
| Security self-efficacy | 3 |
| Computer skills | 3 |
| Perceived cost | 3 |
| Severity | 2 |
| Perceived certainty of sanction | 2 |
| Psychological ownership | 2 |
| Perceived response efficacy | 2 |
| Safeguard cost | 2 |
| Neuroticism | 2 |
| Perceived effectiveness | 2 |
| Perceived risk vulnerability | 2 |
| Agreeableness | 2 |
| Openness | 2 |
| Risk-taking | 2 |
| Perceived severity of sanction | 2 |
| Safeguard effectiveness | 2 |
| Extraversion | 2 |
| Conscientiousness | 2 |
| Perceived usefulness | 2 |
| Familiarity | 2 |
| Perceived ease of use | 2 |
| Decision-making style | 2 |
| Technologies and Services | Frequency |
|---|---|
| Not specified | 12 |
| Smartphones | 5 |
| Information systems | 4 |
| Games | 3 |
| Social networking sites | 3 |
| Internet threats | 2 |
| 2 | |
| Malware | 2 |
| Computer | 1 |
| Ecosystem | 1 |
| Web browser | 1 |
| Internet security software | 1 |
| Anti-malware software | 1 |
| Internet of Things | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almansoori, A.; Al-Emran, M.; Shaalan, K. Exploring the Frontiers of Cybersecurity Behavior: A Systematic Review of Studies and Theories. Appl. Sci. 2023, 13, 5700. https://doi.org/10.3390/app13095700
Almansoori A, Al-Emran M, Shaalan K. Exploring the Frontiers of Cybersecurity Behavior: A Systematic Review of Studies and Theories. Applied Sciences. 2023; 13(9):5700. https://doi.org/10.3390/app13095700
Chicago/Turabian StyleAlmansoori, Afrah, Mostafa Al-Emran, and Khaled Shaalan. 2023. "Exploring the Frontiers of Cybersecurity Behavior: A Systematic Review of Studies and Theories" Applied Sciences 13, no. 9: 5700. https://doi.org/10.3390/app13095700
APA StyleAlmansoori, A., Al-Emran, M., & Shaalan, K. (2023). Exploring the Frontiers of Cybersecurity Behavior: A Systematic Review of Studies and Theories. Applied Sciences, 13(9), 5700. https://doi.org/10.3390/app13095700







