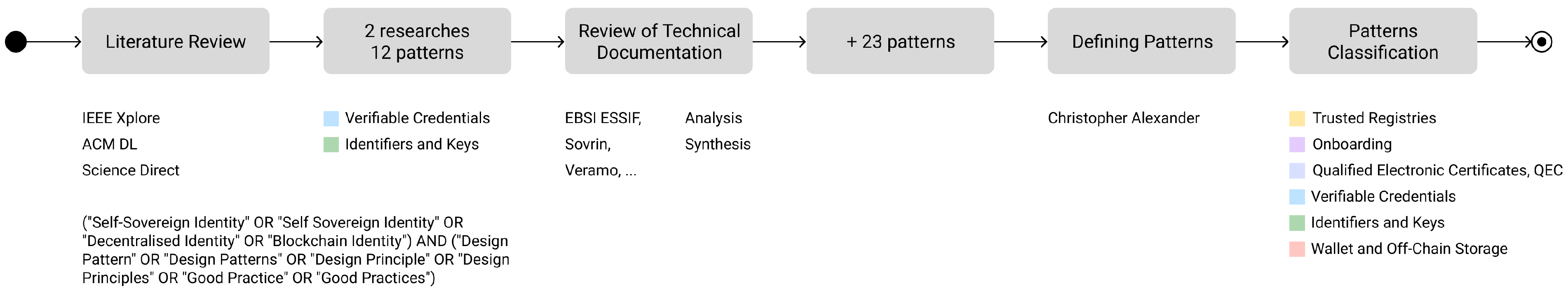
3.3. Patterns and Their Classification
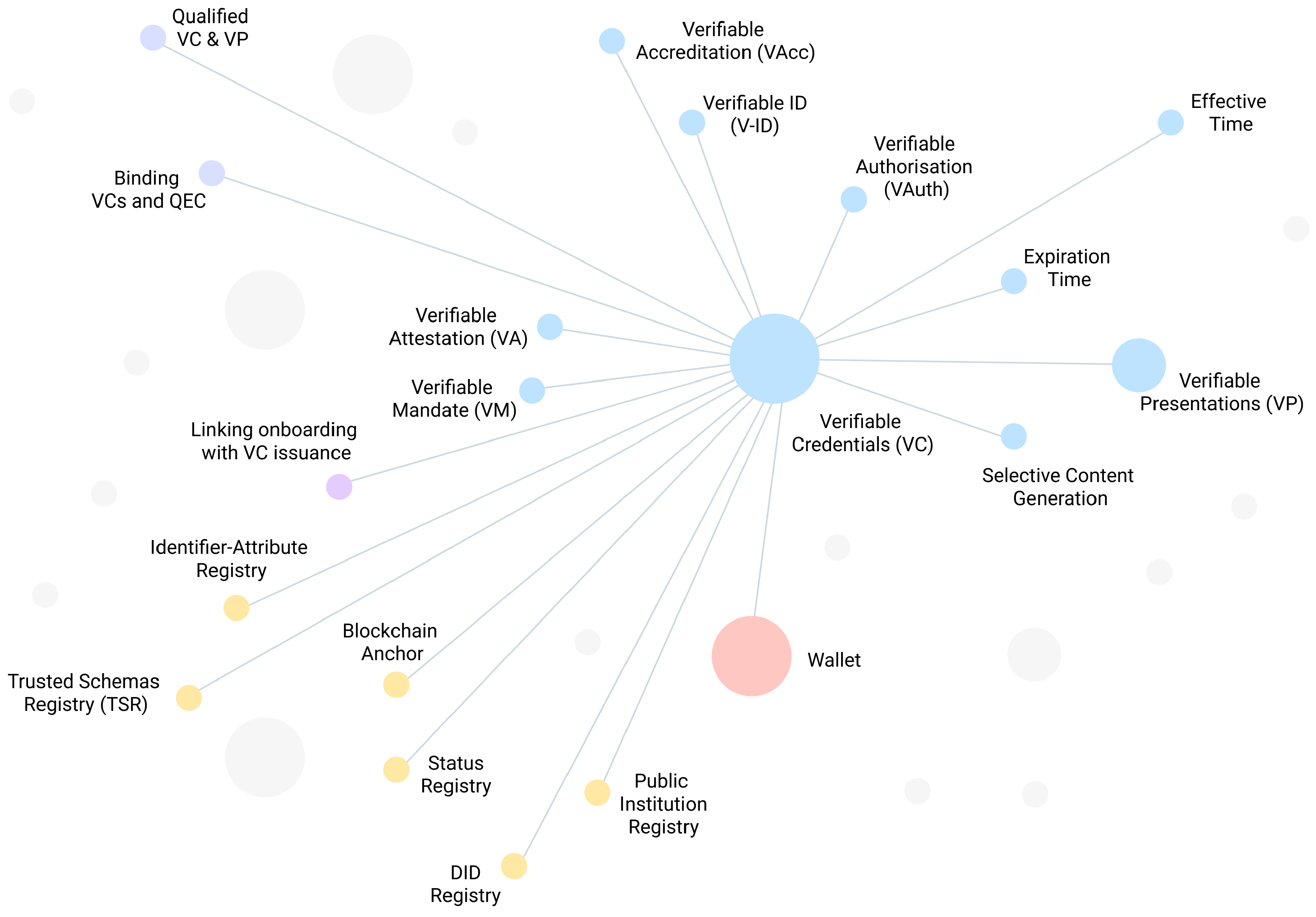
In this section we present an extended SSI pattern collection consisting of 35 design patterns, whereby each is summarised in
Table 1,
Table 2,
Table 3,
Table 4,
Table 5 and
Table 6. Additionally, we also analysed and classified the synthesised patterns into six representative categories, namely, (1)
Trusted Registries, (2)
Onboarding, (3)
Verifiable Credentials and Presentations, (4)
Decentralised Identifiers and Cryptographic Keys, (5)
Qualified Electronic Certificates, and (6)
Wallet and Off-Chain Storage. The objective of the categorisation was to generalise the patterns and group them in order to enable a better understanding of patterns, i.e., how these complement each other, or how these are connected to each other.
In the context of research, each pattern was defined according to the Alexander template [
17]. Due to the length of our output, only summaries of the patterns are presented below, with the complete documentation available at [
30].
Moreover, to present and visualise better where the summarised patterns come into play and can be applied, we also connected these with the life-cycle states and transitions of main SSI objects depicted in
Figure 4.
The category
Trusted Registries (
Table 1) combines patterns that enable the establishment of trust between different entities, i.e., holder, issuer and verifier, in a decentralised identity ecosystem, which is crucial in digital interactions. It represents one of the key elements for removing centralised intermediaries (i.e., identity providers, certification authorities, etc.) in the verification process, as it allows verifiers to verify the received proofs, i.e., verifiable presentations, without the involvement of credential issuers. It includes patterns that address various aspects of building trust, namely, (1.1)
Public Institution Registry, (1.2)
Trusted Schemas Registry, (1.3)
Status Registry, (1.4)
DID Registry or Identifier Registry, (1.5)
Identifier-Attribute Registry, (1.6)
Blockchain Anchor.
(1.1) The
Public Institution Registry maintains a publicly accessible list of (public) institutions/organisations/businesses and their information. It allows verification of their identity, accreditations, and authorisations. It enables verifiers to verify the credential issuer and its publicly available data, to ensure that the issuer has the required accreditations for the issuance of a particular type of credential at the time of issuance. This is crucial, especially when dealing with unknown issuers, as verifiers have to trust issuers to be able to trust the credibility of the data. (1.2) The
Trusted Schemas Registry pattern is paramount for ensuring semantic interoperability between various systems, alignment with domain-specific requirements, and providing quality data objects. It provides a publicly available registry containing data schemas of data objects, and facilitates digital interactions and data exchange between different systems. We refer to data objects as any type of VCs or DIDs, e.g., a verifiable attestation as a subtype of VC, which attest that an individual has a formal higher education (HE) diploma, whereby this diploma is defined with a VC through the official schema for HE diplomas. The schema is, thus, based on the official template for defining formal diplomas, whereby there could be several different HE diploma schemas, depending on the regulation, legislation, country, membership, etc. To establish trust, entities must be able to verify that data objects are structured correctly and approved by relevant authorities. Moreover, without predefined schemas, an unregulated explosion of data objects may occur. (1.3) The
Status Registry contains a status list with information on credential’s validity. Most credentials require the possibility of revocation, suspension, or other means for terminating the validity before the credential’s expiration date for various reasons. Identity and other identity attributes are a dynamic concept, so some of the information in the issued credentials may change; there may be errors in the issuance of the credential, devices, or private key(s) may be lost, or the credential may be misused. Thus, issuers must be able to revoke or suspend credentials, while verifiers must have the means to check the validity of presented credentials without contacting the issuers. (1.4) The
DID Registry or Identifier Registry pattern serves as a decentralised public-key infrastructure (DPKI), and provides a binding between the entity’s identifier(s) and associated public key(s), service endpoint, and other metadata. It is essential for providing a means for discovery, identification, and authentication, and provides trust and integrity. To ensure compliance with the GDPR and prevent disclosure of identity, the Registry should not contain any personally identifiable information of a natural person, since, in the majority of cases, decentralised storage or ledgers will be used for the registries. (1.5) The
Identifier-Attribute Registry maintains mappings between an identifier and the correlated data or its location (off-chain storage URI). The identity data of a natural person should never be stored on-chain due to privacy and security reasons. On the other hand, there may be limitations to the storage capacity of blockchain. Thus, data can be stored off-chain on decentralised file systems such as IPFS, Ceramic Network, etc., and referenced on-chain [
14]. (1.6) The
Blockchain Anchor pattern can be used to preserve the integrity of off-chain stored data and maintain the entity’s privacy. Instead of storing everything on-chain, only hashed values of off-chain data can be anchored on the blockchain. The pattern solves problems related to blockchain storage capacity limitations and GDPR implications, as personally identifiable information should never be stored on-chain and takes into account transaction fees [
14].
Table 1.
SSI design patterns, classified into the Trusted Registries category.
Table 1.
SSI design patterns, classified into the Trusted Registries category.
| Design Pattern | Summary |
|---|
| Public Institution Registry | A register containing information about public entities such as companies, organisations, and institutions, their accreditations, authorisations, etc. [31]. |
| Trusted Schemas Registry | A registry that contains data schemas (templates) of data objects (DIDs, VCs, semantic context) and allows their reuse [32]. |
| Status Registry | The registry contains information required for the verification of (i) verifiable credentials, or (ii) verifiable presentation validity [33]. |
| DID Registry | A registry for the storage of public DIDs that provides a binding between an entity’s identifier(s), public key(s), and other metadata such as service endpoints, etc. Thus, it serves as a decentralised public-key infrastructure (DPKI) [33]. |
| Identifier-Attribute Registry | A registry that maintains a mapping between an identifier and the location, i.e., the address of identity attributes for off-chain storage (e.g., a name and profile picture of an entity) [2,14]. |
| Blockchain Anchor | A registry for storing evidence in the form of hashed data values. Instead of recording all the data on-chain, only a hashed value of the data is recorded on-chain, which can be used for verifying the authenticity of data stored outside the blockchain [2,14]. |
The
Onboarding category (
Table 2) includes two patterns, (2.1)
Onboarding or DID Registration, and (2.2)
Linking onboarding with credential issuance, to interact with other entities within decentralised identity ecosystem and identity management frameworks such as those of EBSI, which is also utilising its own permissioned ledger, where a public entity must first (2.1)
onboard/register through an onboarding service to obtain writing and updating permissions, and store at least one DID and correlated public key on the DID Registry. However,
onboarding should be linked with VC issuance, as it requires identification, and regulations demand sufficient justification when requesting and processing personal data. The mere reason for identification is not sufficient. On the other hand,
linking VC issuance with the DID registration process provides an adequate justification. Moreover, entities usually do not have a profound interest in merely registering DIDs, but have an interest in collecting their data (VCs), building a digital identity and acquiring access to the services. Therefore, isolated DID registration is unreasonable.
Table 2.
SSI design patterns, classified into the Onboarding category.
Table 2.
SSI design patterns, classified into the Onboarding category.
| Design Pattern | Summary |
|---|
| Onboarding or DID Registration | Provision of an entity onboarding service to register identifiers in the DID registry (required when using private and consortium blockchains) [34]. |
| Linking onboarding with VC issuance | The onboarding or registration of DIDs should be linked to verifiable credential issuance. Onboarding requires identity verification, which must be substantiated [35]. |
Category
Verifiable Credentials and Presentations (
Table 3) includes patterns that support data exchange through the VC data format. Patterns (3.1)
Verifiable ID (V-ID), (3.2)
Verifiable Attestation (VA), (3.3)
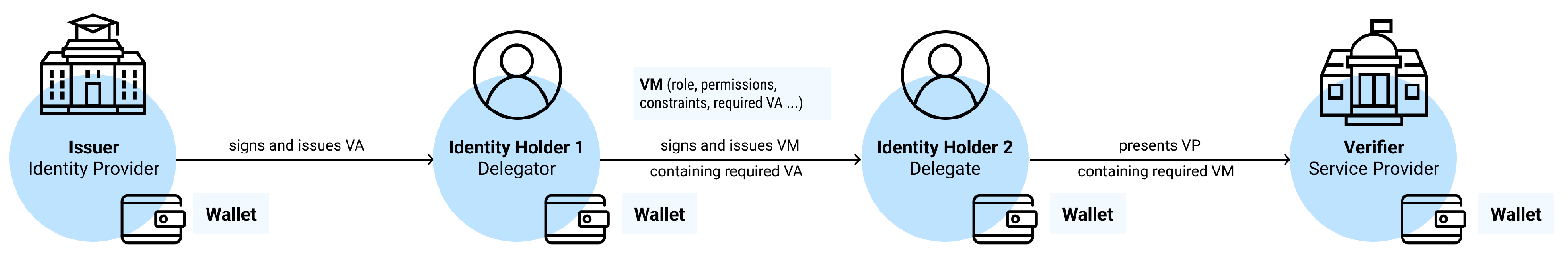
Verifiable Mandate (VM), (3.4)
Verifiable Accreditation (VAcc), and (3.5)
Verifiable Authorisation (VAuth) support different scenarios and use cases. Although they are all technically the same VC generic data format they provide an important distinction, as different scenarios have various purposes and (functional/legal) requirements regarding the level of assurance (LoA), which has implications for the credential issuance process and the attributes contained, etc. Each of the data formats thus has its complex issuance and verification requirements in technical, as well as organisational/management, terms.
(3.1) A V-ID should be used for identification and authentication purposes, e.g., a natural person receives a signed VC of type V-ID from his/her administrative unit, which acts as a digital ID card, holding the minimally required information for an ID card, defined through a specific schema ((1.2) Trusted Schemas Registry). It should be noted that, due to various regulations and legislations, different administrative units can have different templates, and, thus, schemas for the same generalised ID card. Additionally, V-IDs are not only bound to formal documents, but can also be applied to less formal or informal ones, e.g., student cards, library cards, etc. (3.2) A VA should be used for proving certain attributes/properties and permits/attestation/authorisation to access services. Examples of such attestations are, again, more formal documents such as diplomas or driving licences, proving the holder has finished some form of education or has gained some knowledge and thus has gained some rights, such as applying to a specific job posting or driving a car. However, the attestations can also be less formal or informal, such as proof of attending an event, proof of achieving first place at a sports competition, etc. As with the V-ID, each of the aforementioned scenarios or use cases for VA could have its own schema defined (i.e., not mandatory). (3.3) A VM should be used for transferring authority and/or access from one entity to another. An example of such a mandate is indirect identity controls, such as those of delegation, as well as guardianship and/or controllership. Each of these use cases has its own complexity and rules. The former are classical power of attorney rights, while the latter are use cases where parents or custodians are acting in the name of their children, and entities such as IoT devices are acting in the name of their owners/controllers. (3.4) VAcc should be used for proving needed accreditations that ensure compliance with the standards and requirements, and (3.5). An example of such is formal accreditation for higher education institutions received from Ministries, which gives them the right to issue formal diplomas. Lastly, (3.5) VAuth should be used as authorisation proof for accessing permissioned ledgers. These VC data formats play the role of an access token for accessing services, or, in this case, a permissioned ledger. An example of such is seen in the EBSI onboarding processes.
The remaining patterns within this category are solving problems related to flexibility, privacy, and data minimisation. (3.6)
Selective Content Generation and (3.7)
Selective Content Disclosure support the creation of customised credentials and presentations, allowing data minimisation by generating (3.6) VCs according to the holders’ specific requirements, or (3.7) VPs according to the verifiers’ requirements. Both enable the holder to disclose the minimum amount of data necessary for a particular interaction by utilising mechanisms such as atomic credentials, selective disclosure signatures, hashed values and zero-knowledge proof (ZKP) [
14]. By utilising selective content disclosure, identity holders can create VPs consisting of only a subset of attributes from one or more credentials that are required for a particular interaction. Moreover, they can provide attributes without actually revealing their value. For example, if an identity holder wants to prove his/her age, he/she can use selective disclosure to share only the year of birth from the driver’s licence, while not revealing the rest of the attributes, such as day and month of birth, address, etc. Additionally, by using ZKP, he/she can prove that, for example, he/she is over 18 years old without revealing the actual date of birth. This is especially useful in situations where identity holders do not trust the verifiers. (3.8)
Time-Constrained Access and (3.9)
One-Off Access patterns provide privacy and flexibility, and allow identity holders to restrict access to shared credentials to (3.8) specific time frames, or (3.9) limit it to one-time access only. This is important, as the holder’s identity data should not be accessed or verified without a legitimate reason after completing the initial identification process [
14]. (3.10)
Expiration Time enhances trust, increases data accuracy, and reduces misuse and/or abuse of credentials. It enables issuers to restrict the effectivity of credentials, as identity is a dynamic concept, meaning the holder’s identity attributes and conditions may change. Therefore, credentials should not be long-term or effective permanently. On the other hand, (3.11)
Effective Time allows differentiation between the time of the issuance and the time when the credential becomes valid.
Table 3.
SSI design patterns, classified into the Verifiable Credentials and Presentations category.
Table 3.
SSI design patterns, classified into the Verifiable Credentials and Presentations category.
| Design Pattern | Summary |
|---|
| Verifiable ID | Use verifiable ID (VI-D) as evidence/proof of an entity’s identity for identification and authentication purposes [36,37,38]. |
| Verifiable Attestation | Use verifiable attestation (VA) as evidence/proof of specific identity attributes or compliance with certain conditions for nonidentification and non-verification-related scenarios [8,39,40,41,42]. |
| Verifiable Mandate | Use a verifiable mandate (VM) as evidence/proof that an entity (delegate) can act on behalf of another entity (delegator) [43,44,45]. |
| Verifiable Accreditation | Use verifiable accreditation (VAcc) as evidence/proof to demonstrate the appropriate/required accreditations of legal entities to perform particular tasks, such as issuance of certain types of credentials [46,47,48,49,50,51]. |
| Verifiable Authorisation | Use verifiable authorisation (VAuth) to authorise entities to interact with permissioned ledgers and access resources/services [52]. |
| Selective Content Generation | Creating a customised credential according to the identity holder’s specific requirements for credential attributes/contents (interaction between the issuer and the identity holder) [2,14]. |
| Selective Content Disclosure | Creating a customised presentation according to the verifier-specific requirements for credential attributes/contents (interaction between the identity holder and the verifier) [2,14,53]. |
| Time-Constrained Access | Generate and forward a time-limited credential link to allow the verifier access only within the specified time window [2,14]. |
| One-Off Access | Generate and forward a time-limited credential link to allow the verifier to access it only once [2,14]. |
| Expiration Time | Include information that restricts the time of the credential validity/usage [8,54]. |
| Effective Time | Differentiate between the issuance date and the date when the credential becomes valid [39,54]. |
The category
Decentralised Identifiers and Cryptographic Key (
Table 4) includes patterns (4.1)
Multiple Registration, (4.2)
Blockchain and Social Media Account Pair, (4.3)
Public DIDs or Anywise DIDs, (4.4)
Pairwise DIDs (and N-wise DIDs), (4.5)
Static DIDs, (4.6)
Dual Resolution or DID Resolution, (4.7)
Delegate List, (4.8)
DID Controller, (4.9)
Master and Sub-Key Generation, and (4.10)
Key Shards patterns, dealing mainly with solving problems connected to identification, authentication, and management of DIDs, DID documents, and cryptographic keys.
Table 4.
SSI design patterns, classified into the Decentralised Identifiers and Cryptographic Keys category.
Table 4.
SSI design patterns, classified into the Decentralised Identifiers and Cryptographic Keys category.
| Design Pattern | Summary |
|---|
| Multiple Registration | Each entity can create (and register) an unlimited number of unique identifiers (DIDs) and corresponding cryptographic keys for each relationship (i.e., every identity) it has [2,14]. |
| Blockchain and Social Media Account Pair | Establishing a bidirectional link between a social media profile and a blockchain-based identity can increase trust in social networks and the identifier stored on the blockchain [2,14]. |
| Public DIDs or Anywise DIDs | Utilise anywise, public DIDs that require the use of a verifiable data registry (for the execution of CRUD operations) when identifiers need to be available and resolvable by anyone/strangers publicly [7,16,55,56]. |
| Pairwise DIDs (and N-wise DIDs) | Utilise pairwise (and N-wise) private DIDs in personal, confidential interactions between a small number of entities. Such DIDs do not require anchoring to a verifiable data registry, as they are exchanged peer-to-peer [7,57]. |
| Static DIDs | Utilise static DIDs for single, ephemeral interactions that do not require updating and deactivating DID documents [55,56,57,58]. |
| Dual Resolution or DID Resolution | Entities engaged in a mutual interaction have to acquire each other’s DID and resolve it to DID documents to access the information necessary for authentication (e.g., public key) and communication (e.g., service endpoints for provided services) [2,14]. |
| Delegate List | Each entity can maintain a list of delegates or proxies in the DID document who can update a DID document and help recover the identifier in case of lost or compromised keys [2,14]. |
| DID Controller | Entities can designate one or multiple DID controllers (in the DID document) who can control the DID and modify the DID document [7]. |
| Master and Sub Key Generation | Each entity has a master key for managing a set of sub-keys used to sign transactions for different purposes or identity accounts (verification relationships) [2,14]. |
| Key Shards | Entities can split cryptographic keys into several different pieces and recover them with a sufficient number of parts [2,14]. |
(4.1) The
Multiple Registrations pattern enables entities to create and register multiple unique identifiers and correlated cryptographic keys, separate for every relationship they have. Each identifier can be used in different interactions (relationships) to preserve privacy, minimise the possibility of correlation and increase security [
14]. (4.2) The
Blockchain and Social Media Account Pair provides a solution for establishing a bidirectional binding between social media accounts and a decentralised identity, which can enhance the trustworthiness of social media accounts and allows for building a digital reputation [
14]. (4.3)
Public DIDs or Anywise DIDs, (4.4)
Pairwise DIDs (and N-wise DIDs), and (4.5)
Static DIDs allow entities to identify and authenticate. Each pattern supports different types of relationships and their requirements, as some identifiers and interactions should remain private, while others require public availability. Therefore, (4.3)
Public DIDs (e.g., did:ebsi for legal entities, did:ethr, did:sov) should be utilised when DIDs need to be available publicly and resolvable by anyone. (4.4)
Pairwise DIDs (e.g., did:peer) should be used for peer-to-peer, private interactions between a small number of entities, and (4.5)
Static DIDs (e.g., did:key) should be used for single, ephemeral interactions that do not require updating and deactivating DID documents, (4.3) require anchoring DIDs on the VDR, a shared registry that provides a public source of truth and allows arbitrary entities to resolve DIDs to an endpoint and keys. On the other hand, (4.4) and (4.5) are entirely off-chain. Regardless of the type of identifier, entities have to identify and verify each other before engaging in mutual interaction and exchanging information. (4.6)
Dual Resolution or DID Resolution allows them to obtain DIDs and resolve them to DID documents to access the information necessary for authentication (e.g., a public key) and communication purposes (e.g., service endpoints). Each DID is managed by a private key, which is used to prove ownership of the identifier. If the key is lost, stolen, or compromised, patterns (4.7)
Delegate List and (4.10)
Key Shards can be used to retrieve ownership. Both patterns provide approaches for solving problems related to identity recovery, which is crucial for maintaining ownership and control over identifiers, related identity data, and assets in decentralised settings. The
Delegate List allows the identity holder to determine a list of delegates who can help to recover his/her identity if private keys are lost or compromised. The identifier and their keys can be replaced and updated in a DID document after a sufficient number of trustees/delegates vouch for the DID owner. On the other hand, keys can be secured and split into multiple pieces/shards, stored on multiple devices or by multiple trusted entities (i.e., social recovery), and restored by using enough pieces, utilising the
Key Shards pattern [
14]. (4.8) The
DID Controller is related to DID document management, and allows differentiation between a DID subject and the DID controller(s), as, sometimes, the DID subject is not the same as the DID controller (e.g., parents control the identity of their underage children; pet owners control the identifier of their pets, etc.), and some use cases require multiple entities to control a DID (e.g., multiple owners control the organisation identifier) which can be determined in the DID document. Thus, the controller(s) defined in the documents are allowed to make changes to DID document(s), supporting more complex use cases where DID subjects are not capable of controlling their identity (e.g., guardianship as a type of indirect identity control). (4.9) The
Master and Sub-Key Generation pattern can be used to minimise correlation and increase the privacy and security of entities’ identity and their keys. Thus, each entity has multiple keys connected with a particular identity, used for different purposes, meaning that each entity has a master key for managing a set of sub-keys used for signing different types of transactions [
14].
Patterns within the
Qualified Electronic Certificates (QEC) category (
Table 5) can provide legal value, as they bind SSI objects (VCs and DIDs) with the QEC issued by a duly accredited trust service provider. The binding can, therefore, provide the highest legal guarantee, instil trust in the entity’s identity, and assure the integrity of signed documents and their enforceability. This is crucial, because some transactions require a higher LoA to establish sufficient trust. Therefore, some credentials and presentations require a regulatory-supported legal value.
Table 5.
SSI design patterns, classified into the Qualified Electronic Certificates (QEC) category.
Table 5.
SSI design patterns, classified into the Qualified Electronic Certificates (QEC) category.
| Design Pattern | Summary |
|---|
| Qualified Verifiable Credentials | Signing verifiable credentials (and presentations) with qualified digital signatures or seals (eSignature, eSeal) and adding legal value to credentials [59,60]. |
| Binding VCs and QEC | Linking verifiable credentials with qualified electronic certificates [59,60]. |
| Binding DIDs and QEC | Linking decentralised identifiers with qualified electronic certificates, either by enriching the DID document or using trusted registries [61]. |
VCs can be signed by DIDs’ corresponding private keys. However, currently, there is no binding between the DID and real-world natural or legal persons, and no law confers binding between legal value to credentials. Thus, (5.1) Qualified Verifiable Credentials enables entities to sign/seal VCs and VPs with QEC private keys that have a legally binding value/effect. Decentralised digital identity can be linked with a real-world identity by establishing binding with a QEC, either through VCs or DIDs. (5.2) Binding VCs and QECs require issuing verifiable credentials that demand identification and authentication before VC issuance, and they contain information about an entity and can provide substantial proof and evidence. (5.3) Binding DIDs and QECs allows entities, i.e., verifiers, to retrieve qualified certificates and verify them against a trusted list. Thus, verifiers can check reliably which entity is behind a particular DID. DIDs can be linked with QECs using different approaches, either by enriching DID documents or by utilising trusted registries. However, it should be noted that trusted registries should not link natural person identifiers with public certificates, to avoid revealing their identity and comply with GDPR.
Last but not least, the Wallet and Off-Chain Storage category encloses (6.1) Hot and Cold Wallet Storage, (6.2) Local (Private) Storage, and (6.3) External (Remote) Cloud Storage patterns.
Identity wallets provide a means for digital identification, authentication, and authorisation. They serve as a tool for creating and managing identifiers and associated cryptographic keys, as well as for obtaining, storing, and distributing credentials and other personal data, which have to be stored securely and under the complete control of the identity holder. Patterns (6.2) and (6.3) provide storage for identifiers, keys, credentials and other personal data completely off-chain, either locally on the identity holder’s device (smartphone, tablet, computer, etc.), or in remote locations in the cloud where they can be accessible to their holders or wallet controllers. Thereby, trusted cloud-based data storage can be used to avoid the availability and accessibility challenges of local storage.
Table 6.
SSI design patterns, classified into the Wallet and Off-Chain Storage category.
Table 6.
SSI design patterns, classified into the Wallet and Off-Chain Storage category.
| Design Pattern | Summary |
|---|
| Hot and Cold Wallet Storage | Each entity can store keys in two wallets. It stores frequently used keys in a hot wallet with an internet connection and rarely used keys in a cold wallet without an internet connection [2,14]. |
| Local (Private) Storage | Local (off-chain) storage of identifiers, keys, verifiable credentials, and other personal data that can be accessed only by an identity holder or wallet controller [62,63]. |
| External/Remote (Cloud) Storage | External (off-chain) cloud storage for storing identifiers, keys, verifiable credentials, and other personal data [62]. |
(6.1)
Hot and cold wallet storage provides an additional security layer, and can be used for recovery purposes. It allows each entity to maintain keys in two wallets, i.e., hot and cold wallets, providing online storage for frequently used keys and offline storage for infrequently used keys, respectively [
14].