Boosted Reptile Search Algorithm for Engineering and Optimization Problems
Abstract
1. Introduction
Paper Contribution
- We propose a boosted version of the reptile search algorithm (RSA), called RSRFT, to address IDS problems in IoT and cloud environments, as well as complex and multidimensional engineering problems
- We employed the operators of the red fox optimization and triangular mutation operator to boost the performance of the RSA.
- We applied the RSRFT technique to solve different and complex engineering problems. We conducted a set of comparisons with other efficient techniques to verify the quality of RSRFT.
2. Background
2.1. The Reptile Search Algorithm
2.1.1. Exploration Search
2.1.2. Exploitation Search
2.2. Red Fox Algorithm
2.3. Triangular Mutation Operator
3. Proposed RSRFT Method
3.1. Initial Phase
3.2. Updating Phase
3.3. Terminal Phase
| Algorithm 1 The RSRFT method. |
|
4. Experimental Results and Discussion
4.1. Series of Analysis 1: Engineering Problems
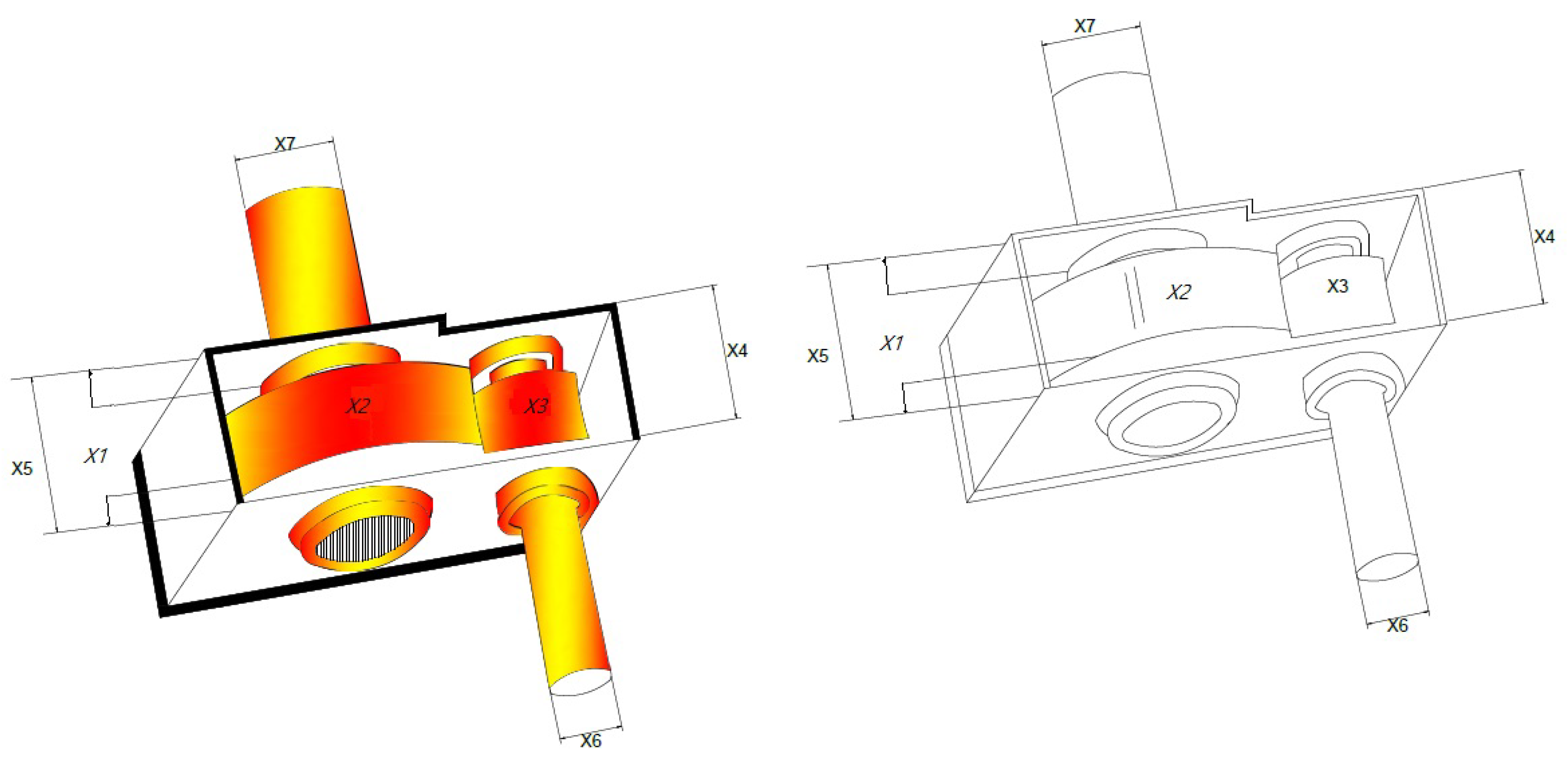
4.1.1. Welded Beam Design Problem
4.1.2. Tension/Compression Spring Design Problem
4.1.3. Pressure Vessel Design Problem
4.1.4. Three-Bar Truss Design Problem Design
4.1.5. Speed Reducer Problem
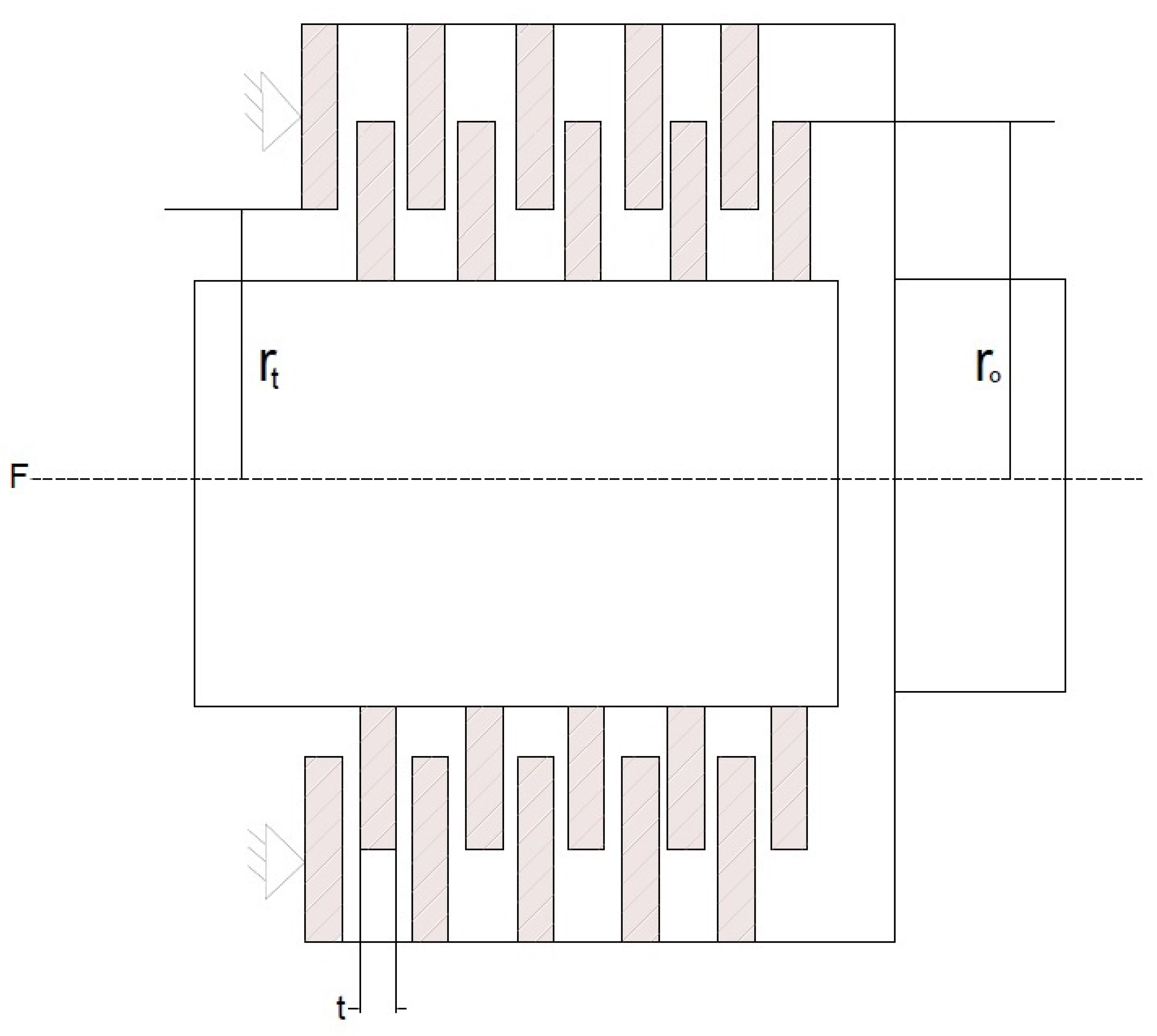
4.1.6. Multiple Disc Clutch Brake Problem
4.2. Series of Analysis 2: RSRFT for Security in the IoT
4.2.1. Dataset Description
4.2.2. Evaluation Criteria and Experimental Setup
- : This stands for the rate of the correct detection of intrusions in the IoT environment. can be formulated aswhere is the total number of runs. FN, TN, TP, and FP refer to false negative, true negative, true positive, and false positive, respectively.
- : This can also be referred to as the true positive rate, and it describes the percentage of correctly predicted positive intrusions. is computed as
- : This describes the ratio of true detections among all correct detection samples, and it is formulated as
4.2.3. Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| Acronyms | |
| IDS | Intrusion detection system |
| IoT | Internet of Things |
| MH | Metaheuristic |
| RFO | Red fox algorithm |
| RSA | Reptile search algorithm |
| TMO | Triangular mutation operator |
| Variables | |
| Combination vector triangle | |
| Hunting operator | |
| Best solution | |
| M() | Mean value of X |
| N | Number of solutions |
| t | Iteration |
| X | Population |
| Value of randomly selected solution | |
References
- Sarkar, A.; Guchhait, R.; Sarkar, B. Application of the artificial neural network with multithreading within an inventory model under uncertainty and inflation. Int. J. Fuzzy Syst. 2022, 24, 2318–2332. [Google Scholar]
- Sarkar, B.; Takeyeva, D.; Guchhait, R.; Sarkar, M. Optimized radio-frequency identification system for different warehouse shapes. Knowl.-Based Syst. 2022, 258, 109811. [Google Scholar]
- Houssein, E.H.; Çelik, E.; Mahdy, M.A.; Ghoniem, R.M. Self-adaptive Equilibrium Optimizer for solving global, combinatorial, engineering, and Multi-Objective problems. Expert Syst. Appl. 2022, 195, 116552. [Google Scholar]
- Abualigah, L.; Ewees, A.A.; Al-qaness, M.A.; Elaziz, M.A.; Yousri, D.; Ibrahim, R.A.; Altalhi, M. Boosting arithmetic optimization algorithm by sine cosine algorithm and levy flight distribution for solving engineering optimization problems. Neural Comput. Appl. 2022, 34, 8823–8852. [Google Scholar]
- Al-Qaness, M.A.; Helmi, A.M.; Dahou, A.; Elaziz, M.A. The applications of metaheuristics for human activity recognition and fall detection using wearable sensors: A comprehensive analysis. Biosensors 2022, 12, 821. [Google Scholar] [PubMed]
- Al-Qaness, M.A.; Ewees, A.A.; Abualigah, L.; AlRassas, A.M.; Thanh, H.V.; Abd Elaziz, M. Evaluating the Applications of Dendritic Neuron Model with Metaheuristic Optimization Algorithms for Crude-Oil-Production Forecasting. Entropy 2022, 24, 1674. [Google Scholar] [PubMed]
- Whitley, D. A genetic algorithm tutorial. Stat. Comput. 1994, 4, 65–85. [Google Scholar]
- Dorigo, M.; Di Caro, G. Ant colony optimization: A new meta-heuristic. In Proceedings of the 1999 Congress on Evolutionary Computation-CEC99 (Cat. No. 99TH8406), Washington, DC, USA, 6–9 July 1999; Volume 2, pp. 1470–1477. [Google Scholar]
- Kennedy, J.; Eberhart, R. Particle swarm optimization. In Proceedings of the ICNN’95-International Conference on Neural Networks, Perth, WA, Australia, 27 November–1 December 1995; Volume 4, pp. 1942–1948. [Google Scholar]
- Yang, X.S.; Slowik, A. Firefly algorithm. In Swarm Intelligence Algorithms; CRC Press: Boca Raton, FL, USA, 2020; pp. 163–174. [Google Scholar]
- Mirjalili, S. SCA: A sine cosine algorithm for solving optimization problems. Knowl.-Based Syst. 2016, 96, 120–133. [Google Scholar]
- Mirjalili, S.; Mirjalili, S.M.; Hatamlou, A. Multi-verse optimizer: A nature-inspired algorithm for global optimization. Neural Comput. Appl. 2016, 27, 495–513. [Google Scholar]
- Heidari, A.A.; Mirjalili, S.; Faris, H.; Aljarah, I.; Mafarja, M.; Chen, H. Harris hawks optimization: Algorithm and applications. Future Gener. Comput. Syst. 2019, 97, 849–872. [Google Scholar]
- Faramarzi, A.; Heidarinejad, M.; Mirjalili, S.; Gandomi, A.H. Marine Predators Algorithm: A nature-inspired metaheuristic. Expert Syst. Appl. 2020, 152, 113377. [Google Scholar]
- Abualigah, L.; Yousri, D.; Abd Elaziz, M.; Ewees, A.A.; Al-Qaness, M.A.; Gandomi, A.H. Aquila optimizer: A novel meta-heuristic optimization algorithm. Comput. Ind. Eng. 2021, 157, 107250. [Google Scholar]
- Abualigah, L.; Diabat, A.; Mirjalili, S.; Abd Elaziz, M.; Gandomi, A.H. The arithmetic optimization algorithm. Comput. Methods Appl. Mech. Eng. 2021, 376, 113609. [Google Scholar]
- Abualigah, L.; Abd Elaziz, M.; Sumari, P.; Geem, Z.W.; Gandomi, A.H. Reptile Search Algorithm (RSA): A nature-inspired meta-heuristic optimizer. Expert Syst. Appl. 2022, 191, 116158. [Google Scholar]
- Bo, Q.; Cheng, W.; Khishe, M. Evolving chimp optimization algorithm by weighted opposition-based technique and greedy search for multimodal engineering problems. Appl. Soft Comput. 2023, 132, 109869. [Google Scholar]
- Shen, Y.; Zhang, C.; Gharehchopogh, F.S.; Mirjalili, S. An Improved Whale Optimization Algorithm based on Multi-Population Evolution for Global Optimization and Engineering Design problems. Expert Syst. Appl. 2023, 215, 119269. [Google Scholar]
- Yang, X.; Wang, R.; Zhao, D.; Yu, F.; Huang, C.; Heidari, A.A.; Cai, Z.; Bourouis, S.; Algarni, A.D.; Chen, H. An adaptive quadratic interpolation and rounding mechanism sine cosine algorithm with application to constrained engineering optimization problems. Expert Syst. Appl. 2023, 213, 119041. [Google Scholar]
- Hong, J.; Shen, B.; Xue, J.; Pan, A. A vector-encirclement-model-based sparrow search algorithm for engineering optimization and numerical optimization problems. Appl. Soft Comput. 2022, 131, 109777. [Google Scholar]
- Zhao, X.; Fang, Y.; Ma, S.; Liu, Z. Multi-swarm improved moth–flame optimization algorithm with chaotic grouping and Gaussian mutation for solving engineering optimization problems. Expert Syst. Appl. 2022, 204, 117562. [Google Scholar]
- Peng, H.; Xiao, W.; Han, Y.; Jiang, A.; Xu, Z.; Li, M.; Wu, Z. Multi-strategy firefly algorithm with selective ensemble for complex engineering optimization problems. Appl. Soft Comput. 2022, 120, 108634. [Google Scholar]
- Zhang, Y.J.; Wang, Y.F.; Yan, Y.X.; Zhao, J.; Gao, Z.M. LMRAOA: An improved arithmetic optimization algorithm with multi-leader and high-speed jumping based on opposition-based learning solving engineering and numerical problems. Alex. Eng. J. 2022, 61, 12367–12403. [Google Scholar]
- Al-qaness, M.A.; Ewees, A.A.; Elaziz, M.A.; Samak, A.H. Wind Power Forecasting Using Optimized Dendritic Neural Model Based on Seagull Optimization Algorithm and Aquila Optimizer. Energies 2022, 15, 9261. [Google Scholar]
- Al-qaness, M.A.; Ewees, A.A.; Thanh, H.V.; AlRassas, A.M.; Dahou, A.; Elaziz, M.A. Predicting CO2 trapping in deep saline aquifers using optimized long short-term memory. Environ. Sci. Pollut. Res. 2022, 1–15. [Google Scholar] [CrossRef]
- Al-qaness, M.A.; Ewees, A.A.; Thanh, H.V.; AlRassas, A.M.; Abd Elaziz, M. An optimized neuro-fuzzy system using advance nature-inspired Aquila and Salp swarm algorithms for smart predictive residual and solubility carbon trapping efficiency in underground storage formations. J. Energy Storage 2022, 56, 106150. [Google Scholar]
- Lin, Y.; Bian, X.Y.; Dong, Z.R. A discrete hybrid algorithm based on Differential Evolution and Cuckoo Search for optimizing the layout of ship pipe route. Ocean. Eng. 2022, 261, 112164. [Google Scholar]
- Zhong, X.; You, Z.; Cheng, P. A hybrid optimization algorithm and its application in flight trajectory prediction. Expert Syst. Appl. 2023, 213, 119082. [Google Scholar]
- Balyan, A.K.; Ahuja, S.; Lilhore, U.K.; Sharma, S.K.; Manoharan, P.; Algarni, A.D.; Elmannai, H.; Raahemifar, K. A hybrid intrusion detection model using ega-pso and improved random forest method. Sensors 2022, 22, 5986. [Google Scholar] [PubMed]
- Bu, S.J.; Kang, H.B.; Cho, S.B. Ensemble of Deep Convolutional Learning Classifier System Based on Genetic Algorithm for Database Intrusion Detection. Electronics 2022, 11, 745. [Google Scholar]
- Fatani, A.; Dahou, A.; Al-Qaness, M.A.; Lu, S.; Abd Elaziz, M. Advanced feature extraction and selection approach using deep learning and Aquila optimizer for IoT intrusion detection system. Sensors 2022, 22, 140. [Google Scholar]
- Mansour, R.F. Blockchain assisted clustering with Intrusion Detection System for Industrial Internet of Things environment. Expert Syst. Appl. 2022, 207, 117995. [Google Scholar]
- Dahou, A.; Abd Elaziz, M.; Chelloug, S.A.; Awadallah, M.A.; Al-Betar, M.A.; Al-qaness, M.A.; Forestiero, A. Intrusion Detection System for IoT Based on Deep Learning and Modified Reptile Search Algorithm. Comput. Intell. Neurosci. 2022, 2022, 6473507. [Google Scholar]
- Elgamal, Z.; Sabri, A.Q.M.; Tubishat, M.; Tbaishat, D.; Makhadmeh, S.N.; Alomari, O.A. Improved Reptile Search Optimization Algorithm using Chaotic map and Simulated Annealing for Feature Selection in Medical Filed. IEEE Access 2022, 10, 51428–51446. [Google Scholar] [CrossRef]
- Chauhan, S.; Vashishtha, G.; Kumar, A. Approximating parameters of photovoltaic models using an amended reptile search algorithm. J. Ambient. Intell. Humaniz. Comput. 2022, 1–16. [Google Scholar] [CrossRef]
- Połap, D.; Woźniak, M. Red fox optimization algorithm. Expert Syst. Appl. 2021, 166, 114107. [Google Scholar]
- Khorami, E.; Mahdi Babaei, F.; Azadeh, A. Optimal diagnosis of COVID-19 based on convolutional neural network and red Fox optimization algorithm. Comput. Intell. Neurosci. 2021, 2021, 4454507. [Google Scholar] [PubMed]
- Natarajan, R.; Megharaj, G.; Marchewka, A.; Divakarachari, P.B.; Hans, M.R. Energy and Distance Based Multi-Objective Red Fox Optimization Algorithm in Wireless Sensor Network. Sensors 2022, 22, 3761. [Google Scholar]
- Zaborski, M.; Woźniak, M.; Mańdziuk, J. Multidimensional Red Fox meta-heuristic for complex optimization. Appl. Soft Comput. 2022, 131, 109774. [Google Scholar]
- Mirjalili, S.; Lewis, A. The whale optimization algorithm. Adv. Eng. Softw. 2016, 95, 51–67. [Google Scholar]
- Krohling, R.A.; dos Santos Coelho, L. Coevolutionary particle swarm optimization using Gaussian distribution for solving constrained optimization problems. IEEE Trans. Syst. Man Cybern. Part B (Cybern.) 2006, 36, 1407–1416. [Google Scholar]
- Awad, N.H.; Ali, M.Z.; Suganthan, P.N. Ensemble sinusoidal differential covariance matrix adaptation with Euclidean neighborhood for solving CEC2017 benchmark problems. In Proceedings of the 2017 IEEE Congress on Evolutionary Computation (CEC), San Sebastián, Spain, 5–8 June 2017; pp. 372–379. [Google Scholar]
- Huang, F.z.; Wang, L.; He, Q. An effective co-evolutionary differential evolution for constrained optimization. Appl. Math. Comput. 2007, 186, 340–356. [Google Scholar]
- Ragsdell, K.; Phillips, D. Optimal design of a class of welded structures using geometric programming. J. Manuf. Sci. Eng. 1976, 38, 1021–1025. [Google Scholar]
- Rashedi, E.; Nezamabadi-Pour, H.; Saryazdi, S. GSA: A gravitational search algorithm. Inf. Sci. 2009, 179, 2232–2248. [Google Scholar]
- Deb, K. Optimal design of a welded beam via genetic algorithms. AIAA J. 1991, 29, 2013–2015. [Google Scholar]
- Lee, K.S.; Geem, Z.W. A new meta-heuristic algorithm for continuous engineering optimization: Harmony search theory and practice. Comput. Methods Appl. Mech. Eng. 2005, 194, 3902–3933. [Google Scholar]
- Mohamed, A.W.; Hadi, A.A.; Fattouh, A.M.; Jambi, K.M. LSHADE with semi-parameter adaptation hybrid with CMA-ES for solving CEC 2017 benchmark problems. In Proceedings of the 2017 IEEE Congress on Evolutionary Computation (CEC), San Sebastián, Spain, 5–8 June 2017; pp. 145–152. [Google Scholar]
- Ewees, A.A.; Abd Elaziz, M.; Houssein, E.H. Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst. Appl. 2018, 112, 156–172. [Google Scholar]
- Kaveh, A.; Khayatazad, M. A new meta-heuristic method: Ray optimization. Comput. Struct. 2012, 112, 283–294. [Google Scholar]
- Coello, C.A.C. Use of a self-adaptive penalty approach for engineering optimization problems. Comput. Ind. 2000, 41, 113–127. [Google Scholar]
- Mezura-Montes, E.; Coello, C.A.C. An empirical study about the usefulness of evolution strategies to solve constrained optimization problems. Int. J. Gen. Syst. 2008, 37, 443–473. [Google Scholar]
- Ray, T.; Saini, P. Engineering design optimization using a swarm with an intelligent information sharing among individuals. Eng. Optim. 2001, 33, 735–748. [Google Scholar]
- Belegundu, A.D.; Arora, J.S. A study of mathematical programmingmethods for structural optimization. Part II: Numerical results. Int. J. Numer. Methods Eng. 1985, 21, 1601–1623. [Google Scholar]
- He, Q.; Wang, L. A hybrid particle swarm optimization with a feasibility-based rule for constrained optimization. Appl. Math. Comput. 2007, 186, 1407–1422. [Google Scholar] [CrossRef]
- Kaveh, A.; Talatahari, S. An improved ant colony optimization for constrained engineering design problems. Eng. Comput. 2010, 27, 155–182. [Google Scholar] [CrossRef]
- Liu, H.; Cai, Z.; Wang, Y. Hybridizing particle swarm optimization with differential evolution for constrained numerical and engineering optimization. Appl. Soft Comput. 2010, 10, 629–640. [Google Scholar] [CrossRef]
- Ray, T.; Liew, K.M. Society and civilization: An optimization algorithm based on the simulation of social behavior. IEEE Trans. Evol. Comput. 2003, 7, 386–396. [Google Scholar] [CrossRef]
- Mirjalili, S. Moth-flame optimization algorithm: A novel nature-inspired heuristic paradigm. Knowl.-Based Syst. 2015, 89, 228–249. [Google Scholar] [CrossRef]
- Zhang, M.; Luo, W.; Wang, X. Differential evolution with dynamic stochastic selection for constrained optimization. Inf. Sci. 2008, 178, 3043–3074. [Google Scholar] [CrossRef]
- Mirjalili, S.; Gandomi, A.H.; Mirjalili, S.Z.; Saremi, S.; Faris, H.; Mirjalili, S.M. Salp Swarm Algorithm: A bio-inspired optimizer for engineering design problems. Adv. Eng. Softw. 2017, 114, 163–191. [Google Scholar] [CrossRef]
- Sadollah, A.; Bahreininejad, A.; Eskandar, H.; Hamdi, M. Mine blast algorithm: A new population based algorithm for solving constrained engineering optimization problems. Appl. Soft Comput. 2013, 13, 2592–2612. [Google Scholar] [CrossRef]
- Gandomi, A.H.; Yang, X.S.; Alavi, A.H. Cuckoo search algorithm: A metaheuristic approach to solve structural optimization problems. Eng. Comput. 2013, 29, 17–35. [Google Scholar] [CrossRef]
- YILDIRIM, A.E.; KARCI, A. Application of Three Bar Truss Problem among Engineering Design Optimization Problems using Artificial Atom Algorithm. In Proceedings of the 2018 International Conference on Artificial Intelligence and Data Processing (IDAP), Malatya, Turkey, 28–30 September 2018; pp. 1–5. [Google Scholar]
- Saremi, S.; Mirjalili, S.; Lewis, A. Grasshopper optimisation algorithm: Theory and application. Adv. Eng. Softw. 2017, 105, 30–47. [Google Scholar] [CrossRef]
- Siddall, J.N. Analytical Decision-Making in Engineering Design; Prentice Hall: Upper Saddle River, NJ, USA, 1972. [Google Scholar]
- Akhtar, S.; Tai, K.; Ray, T. A socio-behavioral simulation model for engineering design optimization. Eng. Optim. 2002, 34, 341–354. [Google Scholar] [CrossRef]
- SARUHAN, H.; UYGUR, İ. Design optimization of mechanical systems using genetic algorithms. Sak. Üniv. Fen Bilim. Enst. Derg. 2003, 7, 77–84. [Google Scholar]
- Geem, Z.W.; Kim, J.H.; Loganathan, G.V. A new heuristic optimization algorithm: Harmony search. Simulation 2001, 76, 60–68. [Google Scholar] [CrossRef]
- Mezura-Montes, E.; Coello, C.C.; Landa-Becerra, R. Engineering optimization using simple evolutionary algorithm. In Proceedings of the 15th IEEE International Conference on Tools with Artificial Intelligence, Sacramento, CA, USA, 5 November 2003; pp. 149–156. [Google Scholar]
- Lu, S.; Kim, H.M. A regularized inexact penalty decomposition algorithm for multidisciplinary design optimization problems with complementarity constraints. J. Mech. Des. 2010, 132, 410051–4100512. [Google Scholar] [CrossRef]
- Stephen, S.; Christu, D.; David, D.C.N. Design Optimization of Weight of Speed Reducer Problem Through Matlab and Simulation Using Ansys. Int. J. Mech. Eng. Technol. 2018, 9, 339–349. [Google Scholar]
- Baykasoğlu, A.; Ozsoydan, F.B. Adaptive firefly algorithm with chaos for mechanical design optimization problems. Appl. Soft Comput. 2015, 36, 152–164. [Google Scholar] [CrossRef]
- Kamboj, V.K.; Nandi, A.; Bhadoria, A.; Sehgal, S. An intensify Harris Hawks optimizer for numerical and engineering optimization problems. Appl. Soft Comput. 2020, 89, 106018. [Google Scholar] [CrossRef]
- Rao, R.V.; Savsani, V.J.; Vakharia, D. Teaching–learning-based optimization: A novel method for constrained mechanical design optimization problems. Comput.-Aided Des. 2011, 43, 303–315. [Google Scholar] [CrossRef]
- Deb, K.; Srinivasan, A. Innovization: Discovery of innovative design principles through multiobjective evolutionary optimization. In Multiobjective Problem Solving from Nature; Springer: Berlin/Heidelberg, Germany, 2008; pp. 243–262. [Google Scholar]
- Eskandar, H.; Sadollah, A.; Bahreininejad, A.; Hamdi, M. Water cycle algorithm—A novel metaheuristic optimization method for solving constrained engineering optimization problems. Comput. Struct. 2012, 110, 151–166. [Google Scholar] [CrossRef]
- Sayed, G.I.; Darwish, A.; Hassanien, A.E. A new chaotic multi-verse optimization algorithm for solving engineering optimization problems. J. Exp. Theor. Artif. Intell. 2018, 30, 293–317. [Google Scholar] [CrossRef]
- Bhesdadiya, R.; Trivedi, I.N.; Jangir, P.; Jangir, N. Moth-flame optimizer method for solving constrained engineering optimization problems. In Advances in Computer and Computational Sciences; Springer: Berlin/Heidelberg, Germany, 2018; pp. 61–68. [Google Scholar]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Security and privacy in the Internet of Things: Current status and open issues. In Proceedings of the 2014 international conference on privacy and security in mobile systems (PRISMS), Aalborg, Denmark, 11–14 May 2014; pp. 1–8. [Google Scholar]
- Fatani, A.; Abd Elaziz, M.; Dahou, A.; Al-Qaness, M.A.; Lu, S. IoT intrusion detection system using deep learning and enhanced transient search optimization. IEEE Access 2021, 9, 123448–123464. [Google Scholar] [CrossRef]
- Yang, X.S. A new metaheuristic bat-inspired algorithm. In Nature Inspired Cooperative Strategies for Optimization (NICSO 2010); Springer: Berlin/Heidelberg, Germany, 2010; pp. 65–74. [Google Scholar]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: Bot-iot dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 2018, 1, 108–116. [Google Scholar]

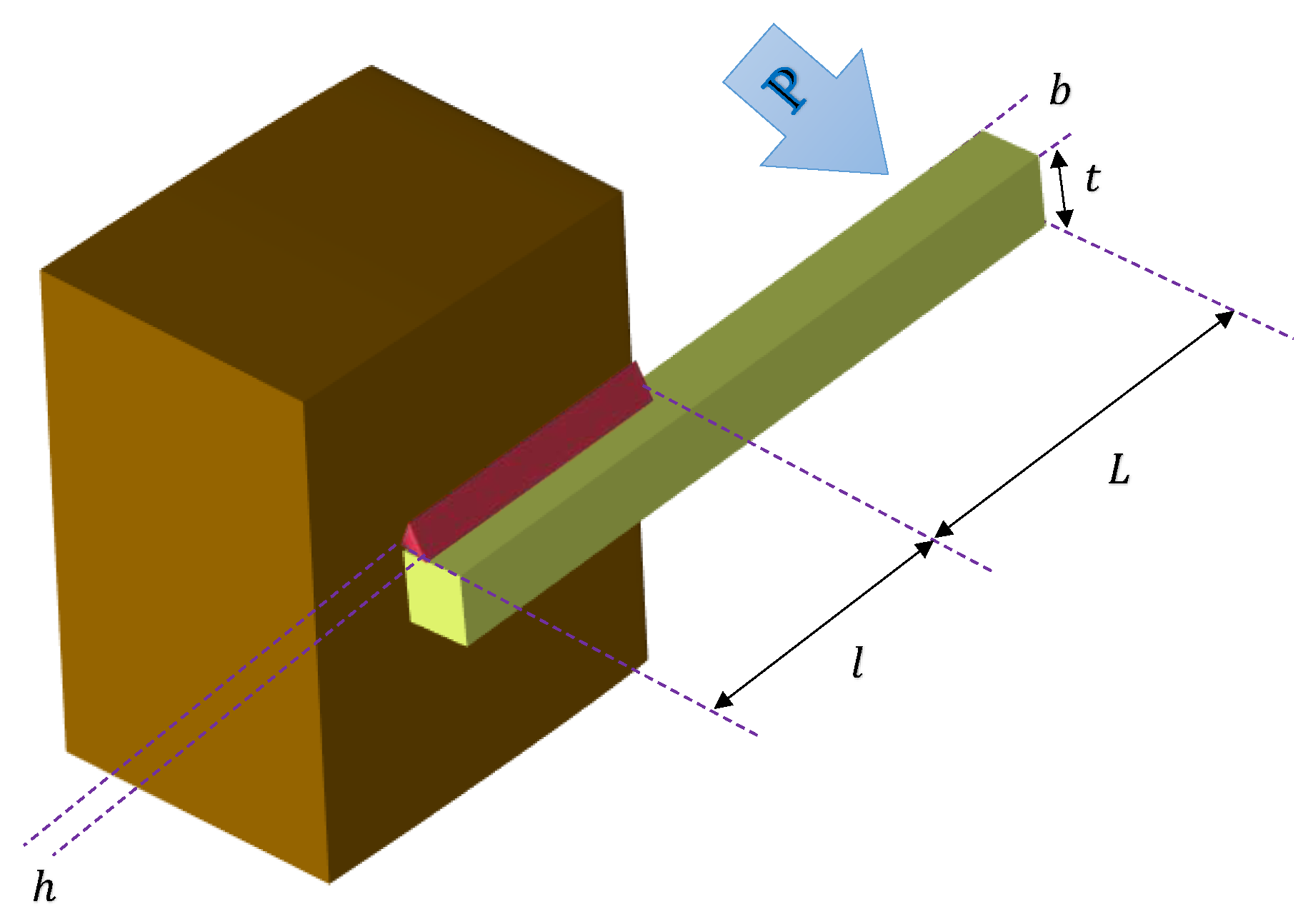
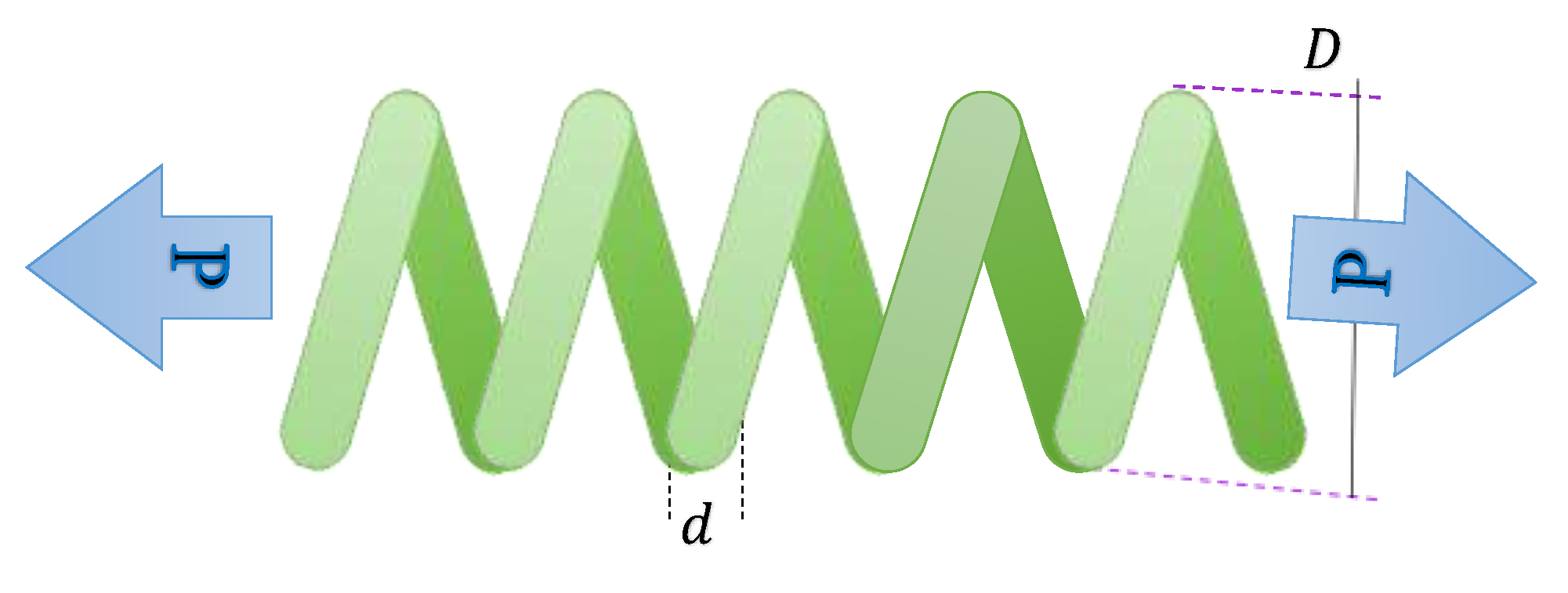
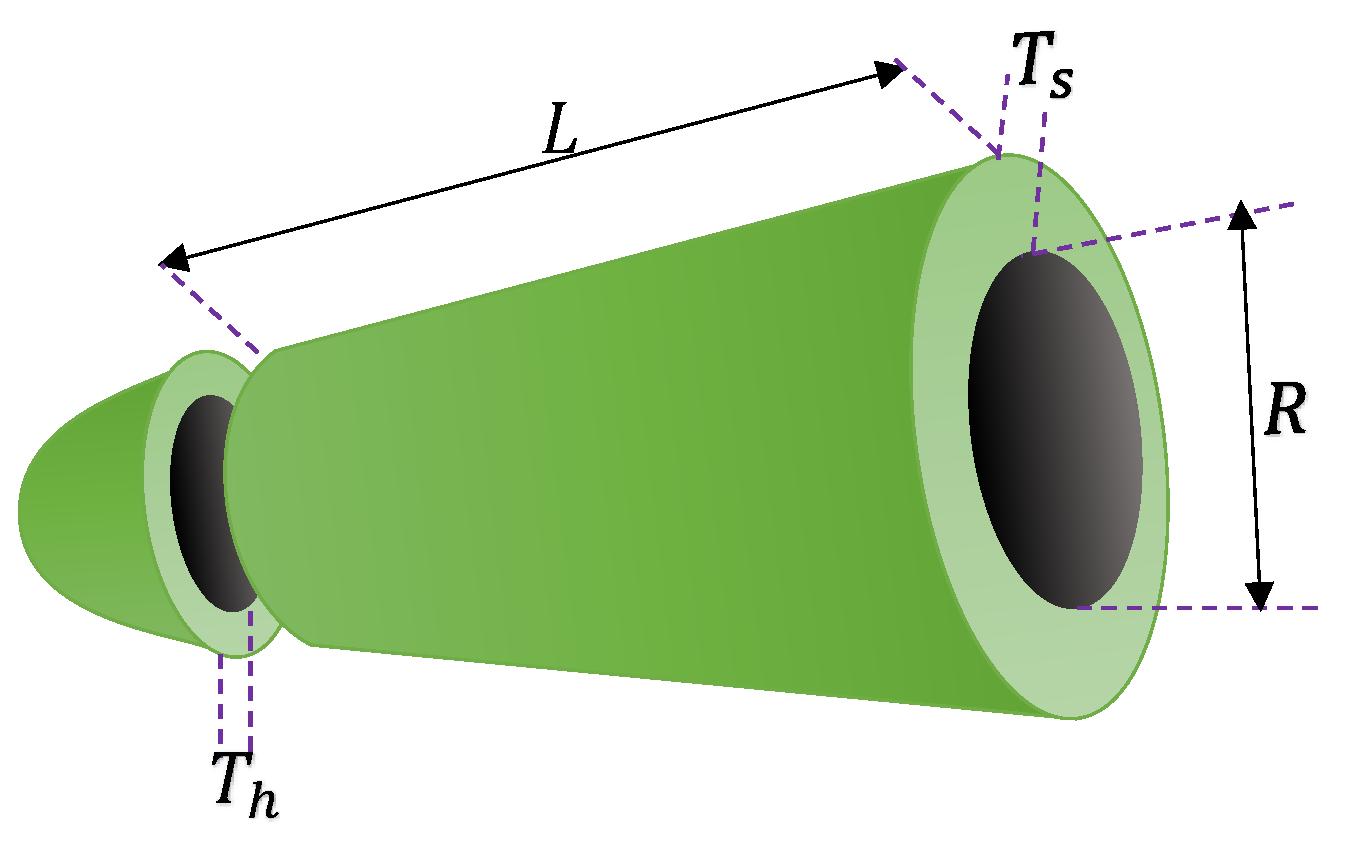
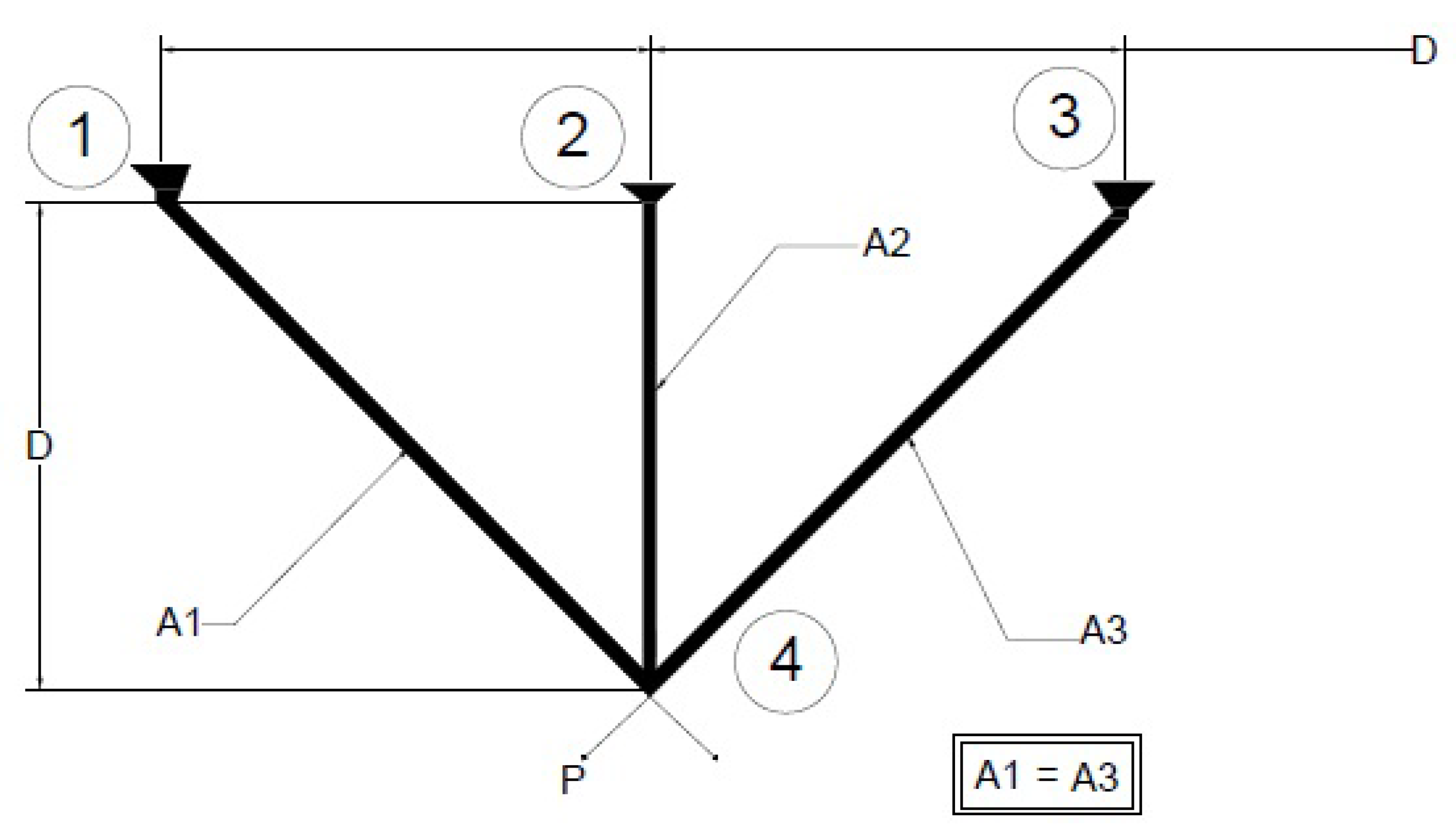
| Algorithm | H | L | t | b | Optimal Objective |
|---|---|---|---|---|---|
| RSRFT | 0.20572 | 3.4704 | 9.0370 | 0.2057 | 1.72489 |
| RFO | 0.21846 | 3.51024 | 8.87254 | 0.22491 | 1.86612 |
| LSHSPCM | |||||
| RSA | 0.14468 | 3.514 | 8.9251 | 0.21162 | 1.6726 |
| LSHcEpS | |||||
| OBLGOA [50] | |||||
| RO [51] | |||||
| HS [48] | |||||
| DAVID [45] | |||||
| SIMPLEX [45] | |||||
| CPSO [42] | |||||
| MVO [12] | |||||
| GA [47] | |||||
| GSA [46] | 10 | ||||
| CSCA [44] | |||||
| WOA [41] |
| Algorithm | d | D | N | Optimal Objective |
|---|---|---|---|---|
| RSRFT | 0.05147146 | 0.3515050 | 11.6013141 | 0.01266617 |
| RFO | 0.052667011 | 0.3806680 | 10.0213925 | 0.0126934 |
| RSA [17] | 0.057814 | 0.58478 | 4.0167 | 0.01176 |
| LSHSPCM | ||||
| LSHcEpS | ||||
| OBLGOA [50] | ||||
| Belegundu-Arora method [55] | ||||
| GA [52] | ||||
| WOA [41] | ||||
| CPSO [42] | ||||
| ES [53] | ||||
| MVO [12] | ||||
| GSA [41] | ||||
| Ray–Saini method [54] |
| Estimated Values for Parameters | |||||
|---|---|---|---|---|---|
| Method | Optimal Objective | ||||
| RSRFT | 0.81612257 | 0.403409949 | 42.2861349 | 174.325078 | 5953.4364 |
| RFO | 0.81425 | 0.44521 | 42.20231 | 176.62145 | 6113.3195 |
| RSA | 0.8400693 | 0.4189594 | 43.38117 | 161.5556 | 6034.7591 |
| LSHSPCM | |||||
| OBLGOA [50] | |||||
| PSO-DE [58] | |||||
| HPSO [56] | |||||
| ACO [57] | |||||
| CDE [44] | |||||
| ES [53] | |||||
| GA [52] | |||||
| GSA [41] | |||||
| Algorithm | Estimated Values for Parameters | Optimal Weight | |
|---|---|---|---|
| RSRFT | 0.78875052 | 0.4080351 | 263.89584 |
| RFO | 0.75356 | 0.55373 | 268.51195 |
| RSA [17] | 0.78873 | 0.40805 | 263.8928 |
| DEDS [61] | 0.78867513 | 0.40824828 | 263.89584 |
| SSA [62] | 0.78866541 | 0.408275784 | 263.89584 |
| MBA [63] | 0.7885650 | 0.4085597 | 263.89585 |
| PSO-DE [58] | 0.7886751 | 0.4082482 | 263.89584 |
| Ray and Saini [54] | 0.795 | 0.395 | 264.3 |
| CS [64] | 0.78867 | 0.40902 | 263.9716 |
| AAA [65] | 0.7887354 | 0.408078 | 263.895880 |
| GOA [66] | 0.78889755557 | 0.40761957011 | 263.89588149 |
| Method | Estimated Values for Parameters | Optimal Weight | ||||||
|---|---|---|---|---|---|---|---|---|
| RSRFT | 3.5000055 | 0.7 | 17 | 7.305888 | 8.004689 | 3.3502353 | 5.2868060 | 3000.97899 |
| RFO | 3.500001 | 0.7 | 17.00002 | 7.314497 | 8.0294718 | 3.350253 | 5.2867662 | 3001.5811 |
| RSA [17] | 3.50279 | 0.7 | 17 | 7.30812 | 7.74715 | 3.35067 | 5.28675 | 2996.5157 |
| GA [69] | 3.510253 | 0.7 | 17 | 8.35 | 7.8 | 3.362201 | 5.287723 | 3067.561 |
| GSA [46] | 3.600000 | 0.7 | 17 | 8.3 | 7.8 | 3.369658 | 5.289224 | 3051.120 |
| HS [70] | 3.520124 | 0.7 | 17 | 8.37 | 7.8 | 3.366970 | 5.288719 | 3029.002 |
| SES [71] | 3.506163 | 0.700831 | 17 | 7.460181 | 7.962143 | 3.362900 | 5.308949 | 3025.005127 |
| MDA [72] | 3.5 | 0.7 | 17 | 7.3 | 7.670396 | 3.542421 | 5.245814 | 3019.583365 |
| SBSM [68] | 3.506122 | 0.700006 | 17 | 7.549126 | 7.859330 | 3.365576 | 5.289773 | 3008.08 |
| SCA [11] | 3.508755 | 0.7 | 17 | 7.3 | 7.8 | 3.461020 | 5.289213 | 3030.563 |
| CS [64] | 3.5015 | 0.7000 | 17 | 7.6050 | 7.8181 | 3.3520 | 5.2875 | 3000.9810 |
| PSO [73] | 3.5001 | 0.7000 | 17.0002 | 7.5177 | 7.7832 | 3.3508 | 5.2867 | 3145.922 |
| FA [74] | 3.507495 | 0.7001 | 17 | 7.719674 | 8.080854 | 3.351512 | 5.287051 | 3010.137492 |
| hHHO-SCA [75] | 3.506119 | 0.7 | 17 | 7.3 | 7.99141 | 3.452569 | 5.286749 | 3029.873076 |
| Method | Estimated Values for Parameters | Optimal Weight | ||||
|---|---|---|---|---|---|---|
| RSRFT | 69.003908 | 89.003914 | 1 | 789.52330 | 2.965888 | 0.307109 |
| RFO | 72 | 93 | 762 | 2 | 1 | 0.25359 |
| RSA [17] | 70.0347 | 90.0349 | 1.0000 | 801.7285 | 2.9740 | 0.31176 |
| TLBO [76] | 70 | 90 | 1 | 810 | 3 | 0.313656611 |
| NSGA-II [77] | 70 | 90 | 1.5 | 1000 | 3 | 0.470400 |
| WCA [78] | 70 | 90 | 1 | 910 | 3 | 0.313656 |
| MVO [79] | 70 | 90 | 1 | 910 | 3 | 0.313656 |
| CMVO [79] | 70 | 90 | 1 | 910 | 3 | 0.313656 |
| MFO [80] | 70 | 90 | 1 | 910 | 3 | 0.313656 |
| Target Class | KDDCup-99 | NSL-KDD | Target Class | Bot-IoT | Target Class | CICIDS-2017 | ||||
|---|---|---|---|---|---|---|---|---|---|---|
| Train | Test | Train | Test | Train | Test | Train | Test | |||
| Normal | 97,278 | 60,593 | 67,343 | 9710 | Normal | 370 | 107 | Benign | 727,397 | 163,572 |
| DoS | 391,458 | 229,853 | 45,927 | 7458 | DoS | 1,320,148 | 385,309 | DDoS | 112,901 | 25,388 |
| Probe | 4107 | 4166 | 11,656 | 2422 | DDoS | 1,541,315 | 330,112 | FTP-Patator SSH-Patator | 6997 5201 | 1574 1169 |
| R2L | 1126 | 16,189 | 995 | 2887 | Reconnaissance | 72,919 | 18,163 | PortScan Brute Force | 140,043 1329 | 31,492 299 |
| U2R | 52 | 228 | 52 | 67 | Theft | 65 | 14 | SQL Injection XSS | 19 575 | 4 129 |
| Train | Test | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Precision | F1-Measure | Recall | Accuracy | Precision | F1-Measure | Recall | ||
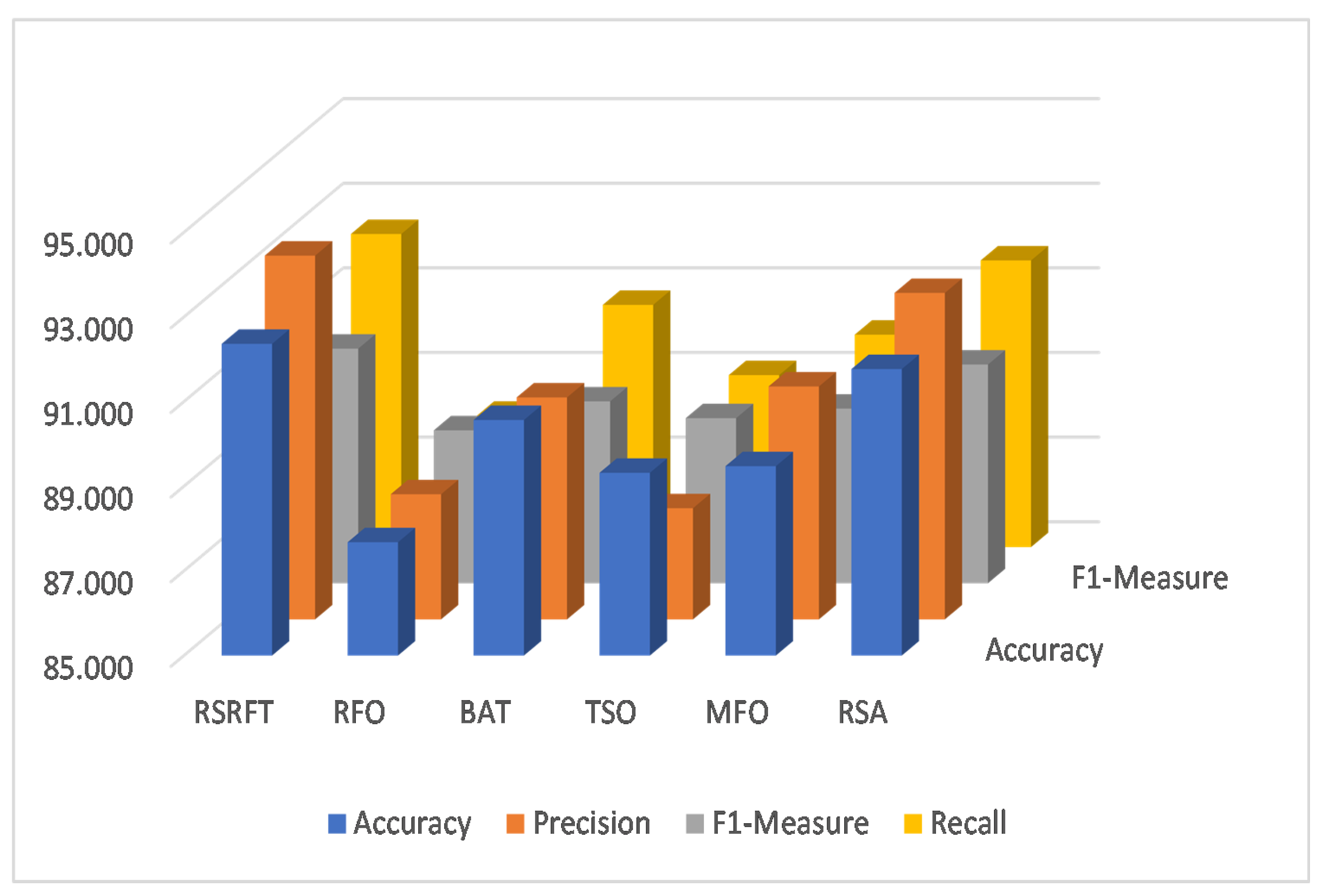
| KDD99 | RSRFT | 99.946 | 99.483 | 99.943 | 99.923 | 93.615 | 92.649 | 90.380 | 93.495 |
| RFO | 92.275 | 92.414 | 97.304 | 93.126 | 84.375 | 82.501 | 87.351 | 85.225 | |
| BAT | 98.007 | 94.847 | 97.337 | 98.247 | 90.347 | 89.134 | 90.093 | 90.587 | |
| TSO | 95.439 | 91.027 | 97.437 | 94.919 | 87.536 | 80.791 | 87.479 | 87.016 | |
| MFO | 96.073 | 97.631 | 98.371 | 97.123 | 88.175 | 87.763 | 88.420 | 89.225 | |
| RSA | 99.910 | 99.909 | 99.906 | 99.910 | 92.040 | 89.684 | 89.985 | 92.040 | |
| NSL-KDD | RSRFT | 99.382 | 99.545 | 99.548 | 99.301 | 76.407 | 82.371 | 72.731 | 77.107 |
| RFO | 91.947 | 92.080 | 96.968 | 92.797 | 67.951 | 71.131 | 68.907 | 68.801 | |
| BAT | 97.669 | 94.501 | 96.989 | 97.909 | 73.671 | 73.501 | 68.905 | 73.911 | |
| TSO | 95.078 | 90.657 | 97.067 | 94.558 | 71.330 | 71.298 | 69.697 | 70.810 | |
| MFO | 95.745 | 97.297 | 98.035 | 96.795 | 71.626 | 76.122 | 69.844 | 72.676 | |
| RSA | 99.201 | 99.158 | 99.148 | 99.201 | 76.107 | 82.171 | 71.731 | 76.107 | |
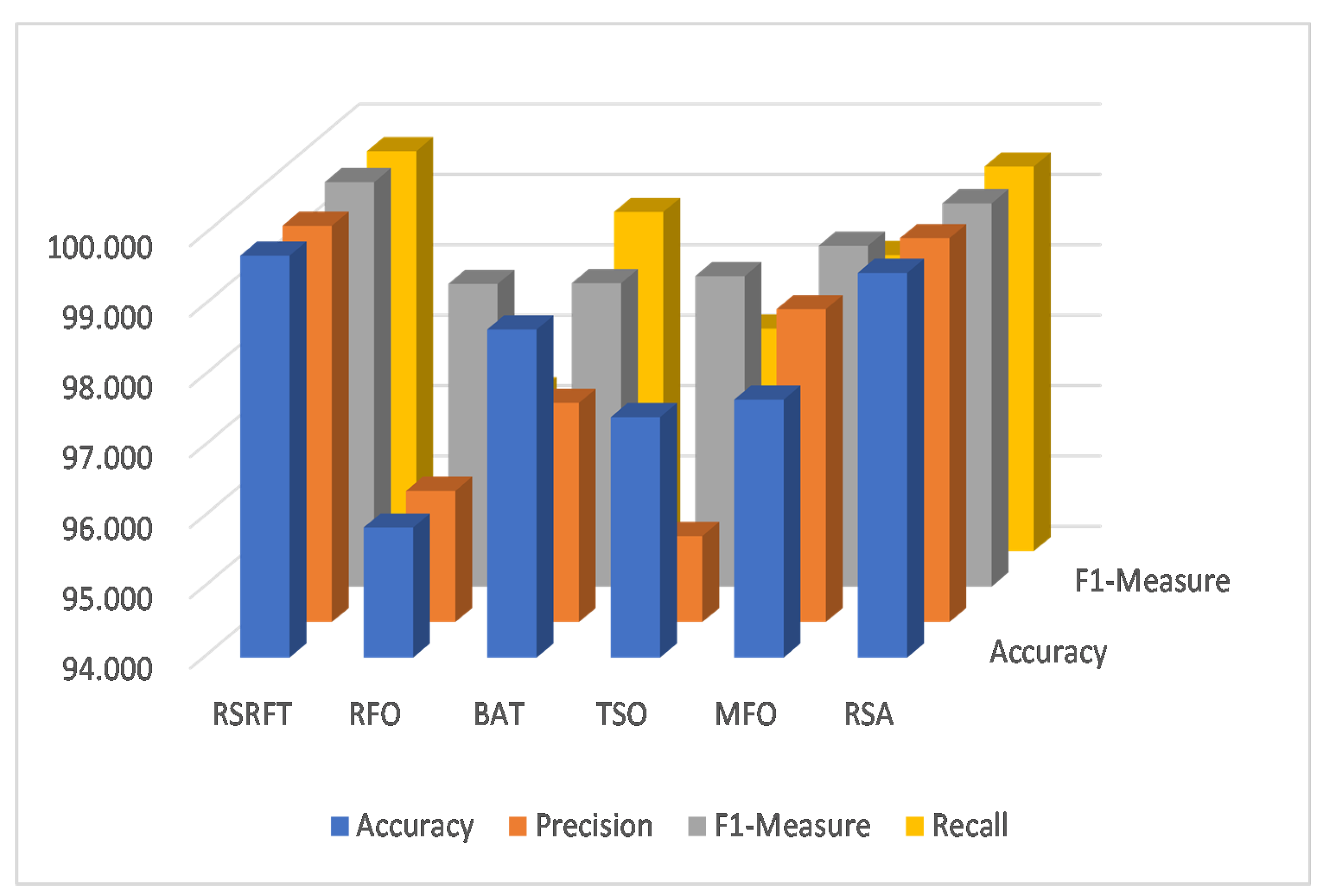
| BIoT | RSRFT | 99.568 | 99.568 | 99.568 | 99.568 | 99.512 | 99.420 | 99.080 | 99.064 |
| RFO | 99.472 | 99.472 | 99.472 | 99.472 | 98.956 | 98.957 | 99.005 | 98.964 | |
| BAT | 99.475 | 99.475 | 99.474 | 99.475 | 99.019 | 98.987 | 99.012 | 99.021 | |
| TSO | 99.460 | 99.459 | 99.459 | 99.460 | 98.986 | 98.941 | 99.005 | 98.981 | |
| MFO | 99.480 | 99.480 | 99.480 | 99.480 | 98.998 | 99.013 | 99.020 | 99.009 | |
| RSA | 98.829 | 98.829 | 98.829 | 98.829 | 99.020 | 99.098 | 99.070 | 99.038 | |
| CIC2017 | RSRFT | 99.941 | 99.920 | 99.918 | 99.931 | 99.931 | 99.947 | 99.983 | 99.931 |
| RFO | 99.690 | 99.490 | 99.450 | 99.690 | 99.430 | 99.240 | 99.190 | 99.430 | |
| BAT | 99.490 | 99.630 | 99.440 | 99.640 | 99.230 | 99.360 | 99.180 | 99.380 | |
| TSO | 99.680 | 99.750 | 99.680 | 99.710 | 99.420 | 99.480 | 99.420 | 99.450 | |
| MFO | 99.360 | 99.370 | 99.480 | 99.430 | 99.100 | 99.120 | 99.220 | 99.170 | |
| RSA | 99.911 | 99.910 | 99.889 | 99.911 | 99.911 | 99.907 | 99.888 | 99.911 | |
| p-Value | RSRFT | RFO | BAT | TSO | MFO | RSA | ||
|---|---|---|---|---|---|---|---|---|
| Training | Accuracy | 0.046 | 6 | 2.25 | 3.5 | 2.25 | 3 | 4 |
| Precision | 0.0543 | 5.75 | 2.25 | 3.25 | 2 | 3.5 | 4.25 | |
| F1-Measure | 0.0208 | 6 | 1.75 | 2.25 | 3 | 4 | 4 | |
| Recall | 0.0435 | 6 | 2 | 3.5 | 2.5 | 3 | 4 | |
| Testing | Accuracy | 0.0064 | 6 | 1.75 | 3.5 | 2.25 | 2.5 | 5 |
| Precision | 0.0064 | 6 | 1.75 | 3.25 | 2 | 3 | 5 | |
| F1-Measure | 0.0101 | 6 | 1.625 | 2.5 | 2.625 | 3.5 | 4.75 | |
| Recall | 0.0054 | 6 | 1.5 | 3.5 | 2.5 | 2.5 | 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abd Elaziz, M.; Chelloug, S.; Alduailij, M.; Al-qaness, M.A.A. Boosted Reptile Search Algorithm for Engineering and Optimization Problems. Appl. Sci. 2023, 13, 3206. https://doi.org/10.3390/app13053206
Abd Elaziz M, Chelloug S, Alduailij M, Al-qaness MAA. Boosted Reptile Search Algorithm for Engineering and Optimization Problems. Applied Sciences. 2023; 13(5):3206. https://doi.org/10.3390/app13053206
Chicago/Turabian StyleAbd Elaziz, Mohamed, Samia Chelloug, Mai Alduailij, and Mohammed A. A. Al-qaness. 2023. "Boosted Reptile Search Algorithm for Engineering and Optimization Problems" Applied Sciences 13, no. 5: 3206. https://doi.org/10.3390/app13053206
APA StyleAbd Elaziz, M., Chelloug, S., Alduailij, M., & Al-qaness, M. A. A. (2023). Boosted Reptile Search Algorithm for Engineering and Optimization Problems. Applied Sciences, 13(5), 3206. https://doi.org/10.3390/app13053206









