Early Forest Fire Detection Using a Protocol for Energy-Efficient Clustering with Weighted-Based Optimization in Wireless Sensor Networks
Abstract
1. Introduction
- Reasonable packet data transmission rate and energy-efficient for the WSN nodes using a novel clustering routing algorithm have been developed in this paper;
- We develop a new function that considers energy efficiency through a cluster formation process to make the CH excerption process better;
- Surpassing existing systems in terms of their energy consumption, the number of live nodes, packet delivery rate, and among other metrics too;
- To better comprehend the protocols and related approaches used by WSNs, we provide a thorough analysis and evaluation of the relevant literature based on clustering parameters.
2. Background
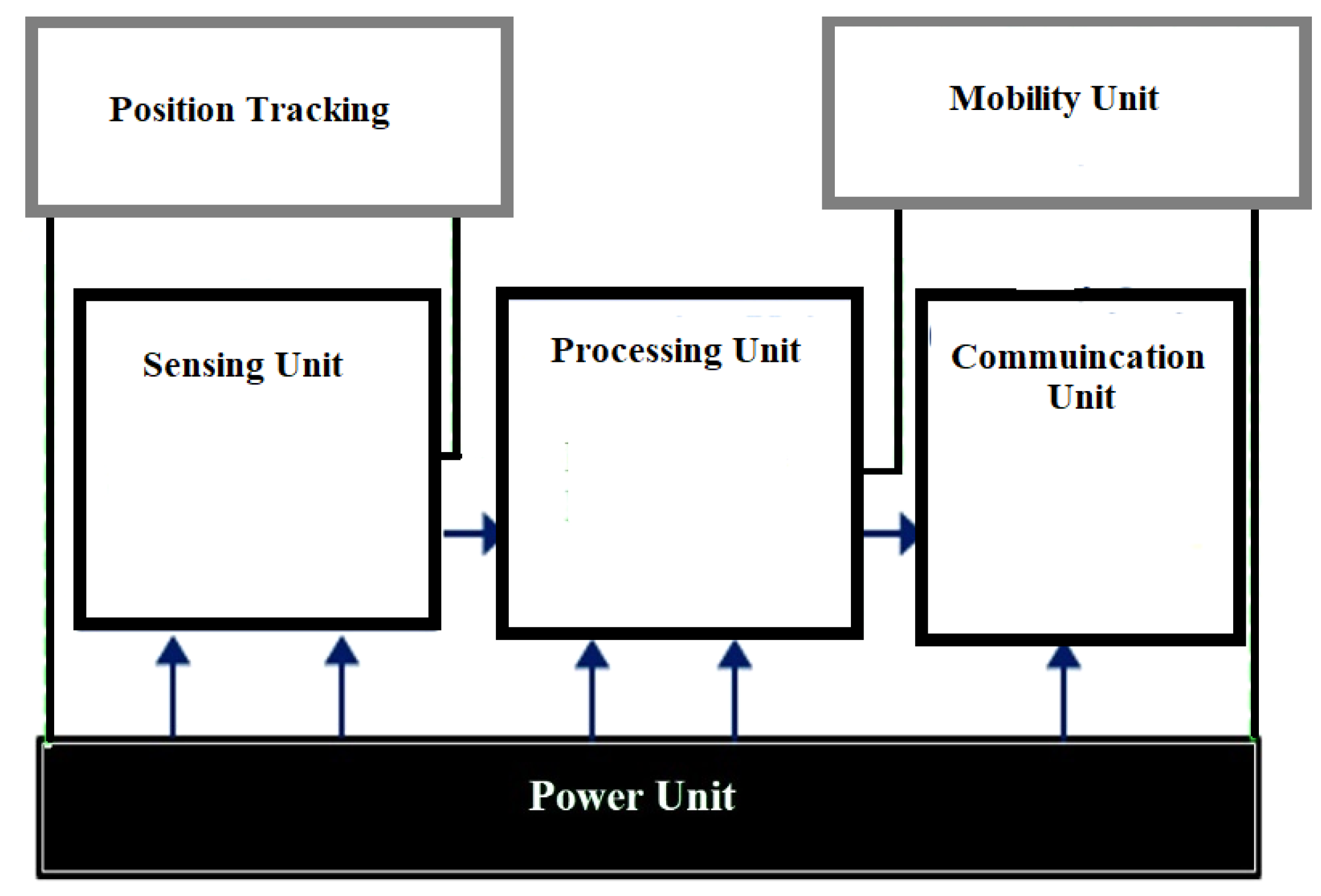
2.1. Wireless Sensors Network (WSN)
2.2. Why WSN Is Important in Forest Fire Detection
2.3. Author Contribution
- In subsequent rounds, we will choose the CH without considering the excess energy of the sensor nodes;
- Therefore, a sensor node with low residual energy will pass away rapidly if it is picked to be the CH;
- Due to this, the network’s resilience is diminished and its lifetime is shortened;
- Since they are placed near the edge of the clusters, the CHs would lose more energy, which would hurt the overall performance of the network;
- When it comes to data transmission, CHs that are further away from the BS use up more energy than CHs that are positioned closer to the BS. Due to this, the lifespan of the network may be reduced.
- Create a clustering protocol using weighted parameters. Review the state-of-the-art WSN clustering;
- Extensive comparison and assessment of the offered algorithms based on the parameters;
- Compared to state-of-the-art algorithms, the proposed one has significantly lower energy requirements while maintaining or improving performance.
3. Literature Review
4. Proposed Algorithm EEWBP
4.1. Energy Model
4.2. Network Model
- In our setup, low energy SNs and high energy SNs are the two types of accessible SNs. Both types of nodes are static (plain nodes);
- The sink or BS is stationary and intended to be known by other SNs in the center of the field under surveillance;
- The networks have the same type of sensor nodes and communication capabilities, where in all SNs are similar;
- A unique identification number is issued to each SN;
- There is always a limited sensing range for each SN. It is assumed that the SN is in the middle [3] of the disc and that the SNs can interact with other’s nodes through changing power levels, depending on their distance from their neighbors;
- A sensor node’s transmission range is described in 2-D space as the disc-sensing model and all SNs in the area of its transmission range can acquire the data supplied from each SN [3];
- The range of transmission is at least twice that of the sensor range [4], e.g., Trange = 2 × R sensor, where the range of transmission and sensor range are indicated as Transmission Range (Trange) and Range of Sensor (RS);
- The connection between wireless sensor nodes is symmetrical and bidirectional and the coordinates of them are known to other SNs.
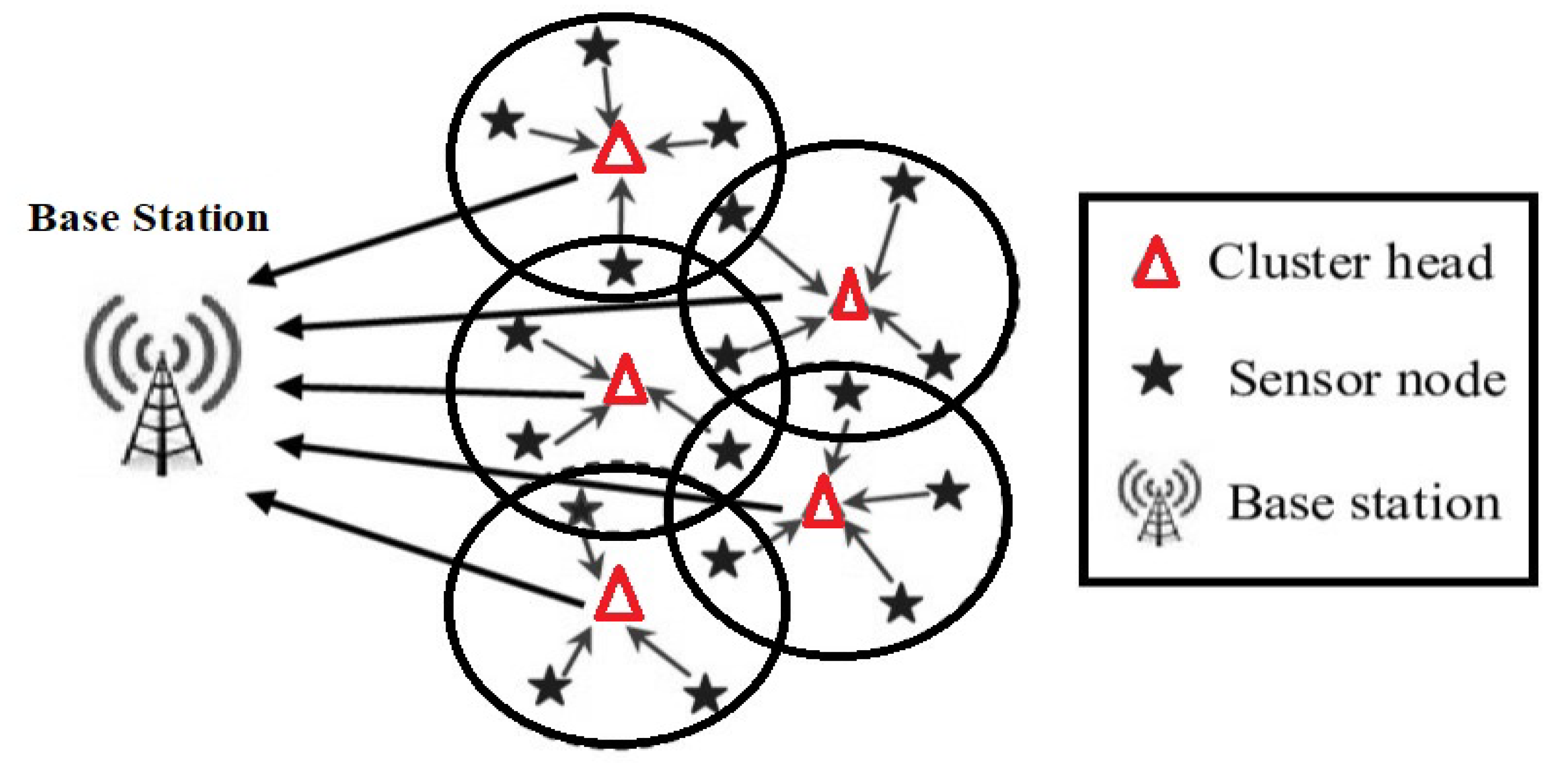
4.3. Network Operation
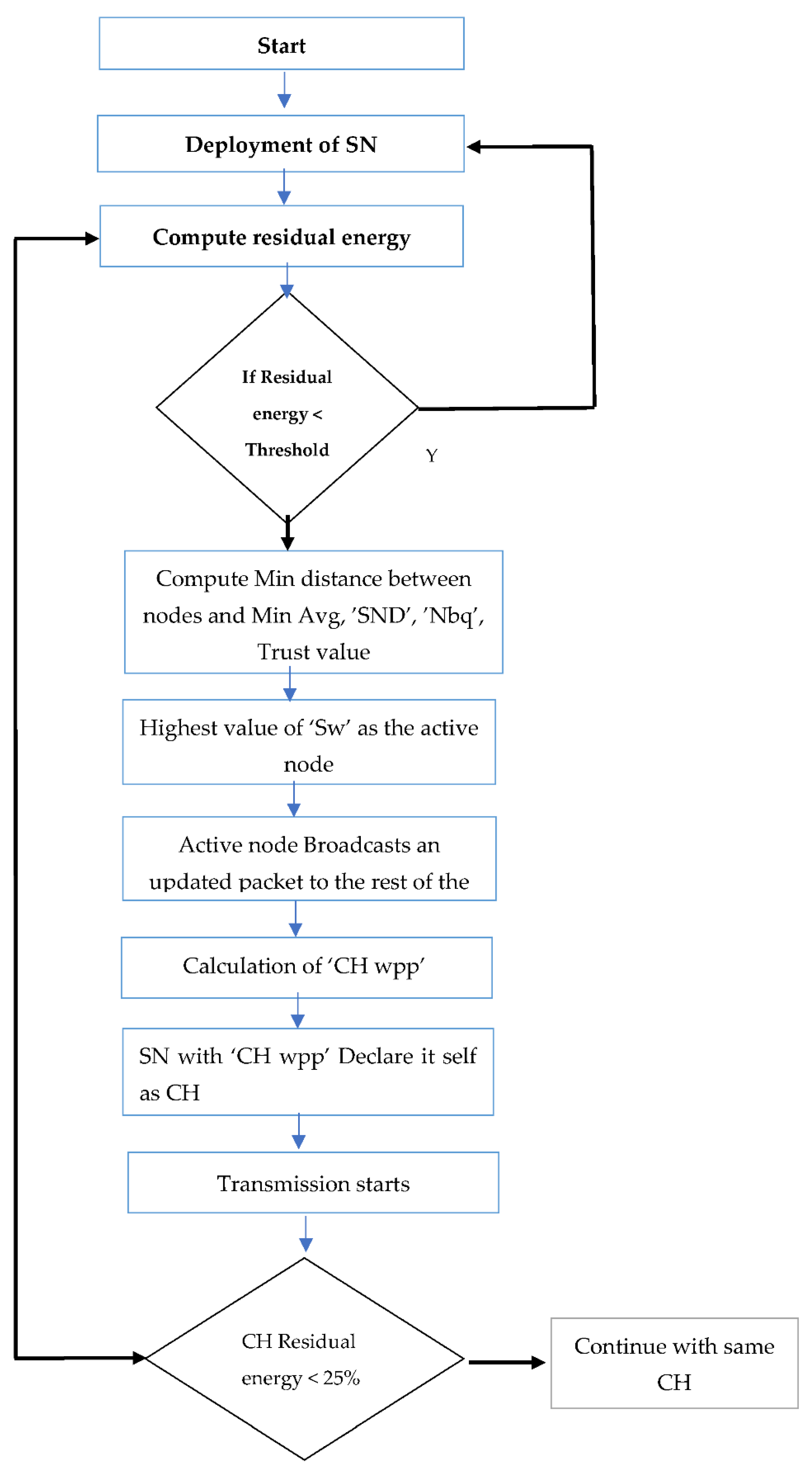
4.3.1. Cluster Formation Phase
- Dismantle SNs to cover the entire required region;
- Computation of residual energy Re of each node is done in the starting and if it is less than the threshold value, then it is skipped from the current round and can participate only in the next round of communication;Residual energy = initial energy − current energy
- Calculation of all the minimum distances between each node to the sink as denoted by Dist(i,j). To calculate distance among every node to CH and between CH to BS, we use a Basic Equation (5) known as three-dimensional Cartesian space, in which two locations have three coordinates each. In order to determine the distance spanning between two points, A(x1, y1, z1) and B(x2, y2, z2), use the formula:where ;
- Calculation of each sensor node’s net weight using a weighted-sum equation (Sw)The values of x1, x2, x3, and x4 are 0.6, 0.3, 0.2, and 0.1 for particular application;
- Identification of the SN with the highest value of ‘Sw’ as the active node for a certain region;
- Each active node inside its sensing network radius broadcasts an updated packet to the rest of the network;
- Calculation of ‘CH wpp’ (CH weighted-sum) using the determined ‘Sw’ of the sensor node and the distance between it and the sink;
- Nodes with the lowest ‘CH wpp’ values are picked as candidates for CH for the specified active nodes;
- Each selected CH broadcasts an updated packet inside the cluster radius;
- If residual energy of CH is less than 25% then again CH re-selection process is repeated.
| Algorithm 1 CH selection and Cluster Establishment |
| Start |
| 1: For every SN in network deployed on space; |
| 2: Calculate residual energy Re of every node |
| 3: If (Re < threshold) |
| 4: Skip the node for current round |
| 5: Calculate of all the minimum distances between each node to the sink Dist(i,j). |
| 6: Calculate each sensor node’s net weight using a weighted-sum equation including Min Avg flying speed, ’SND(degree of a sensor node), nbq(number of neighbors), and Trust value |
| 7: Highest value of weighted-sum of a SN is denoted as active node |
| 8: Each active node inside its sensing network radius, Transmit an updated packet to the rest of the network. |
| 9: Calculate the ‘CH wpp’ (CH weighted-sum) using weighted-sum of the sensor node and the distance between it and the sink. |
| 10: Nodes with the lowest ‘CH wpp’, Declare (Itself as CH); |
| 11: Each selected CH Transmit an updated packet inside the cluster radius |
| 12: End If |
| End |
- Residual energy, abbreviated as “Re”, is the first performance measure for weight value. Each simulation cycle ends with some leftover energy from the SN, which is known as residual energy. The larger the residual energy of the SN, the more likely it is to become an active node;
- The next performance measure for the weight value is Average flying speed. Every node distance covered is divided by the time taken, which is considered flying speed. Then, the average of all nodes is considered as Avg flying speed. If a node’s flying speed is less than Avg flying speed, it is disqualified;
- The ‘SND’ denotes the degree of a sensor node, which is the third performance criteria for weight value. SND refers to the number of sites in SNi’s sensing range that are reached. Initiation probability is higher for SNs to become active as it covers many locations;
- The next functioning parameter for weight value is a number of neighbors i.e., ‘Nbq’. Number of neighbors is delineated as several other SNs within its cluster range;
- Sending and receiving packets from one SN n to another SN m might take some delay;
- average, is the average delay of packets sent SN n to another SN m;
- α is the threshold constant which can range from 0 to 2. Therefore, Direct Trust can be calculated as shown in (8):
- Tpf is the Total packets requested by SN n to be sent to SN n in the situation when n ≠ m and m is a neighbor of n;
- Tpr is the number of packets sent by SN n to SN m.
4.3.2. Data Transmission Phase
5. Performance Analysis
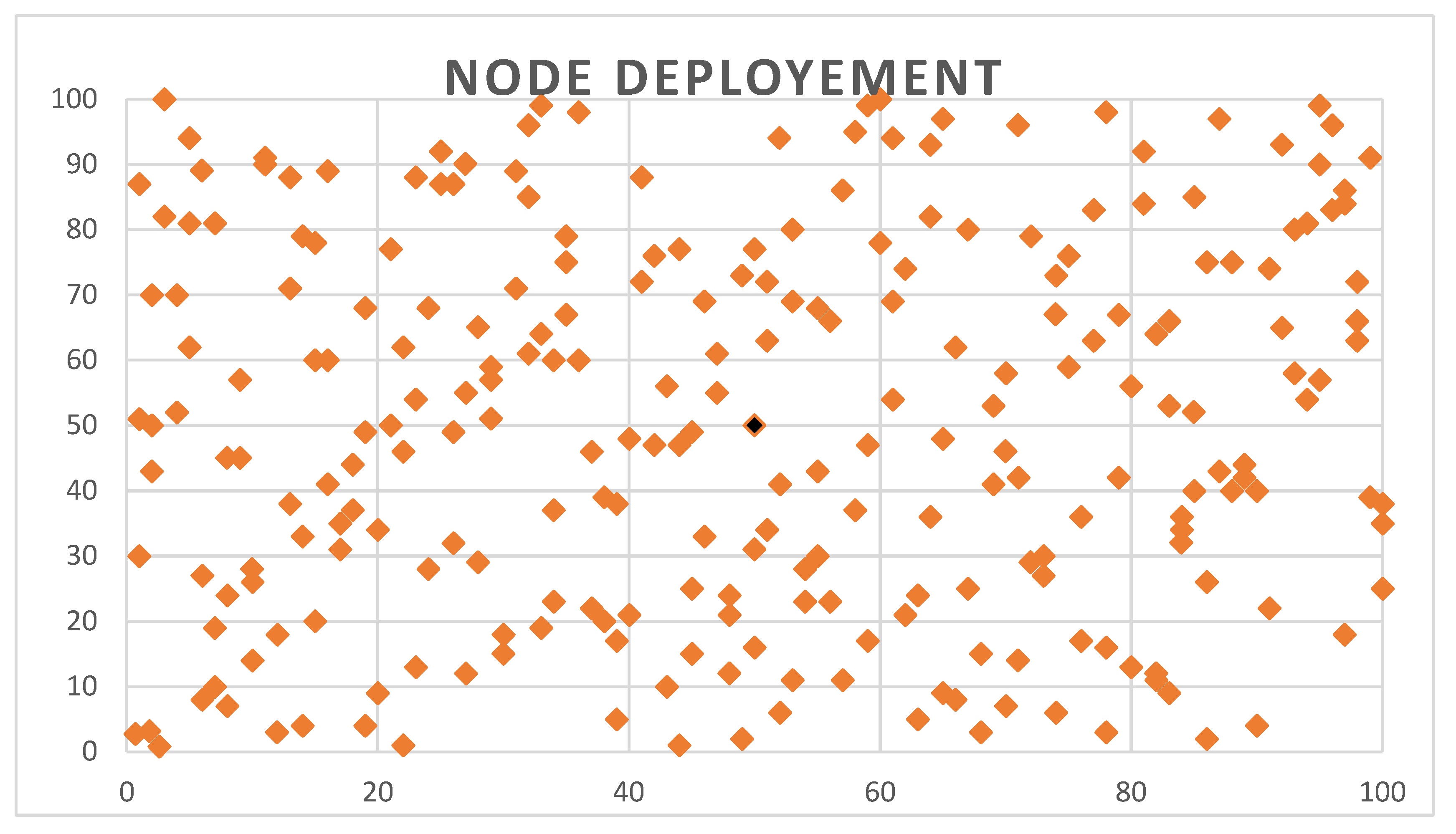
5.1. Deployment of Nodes
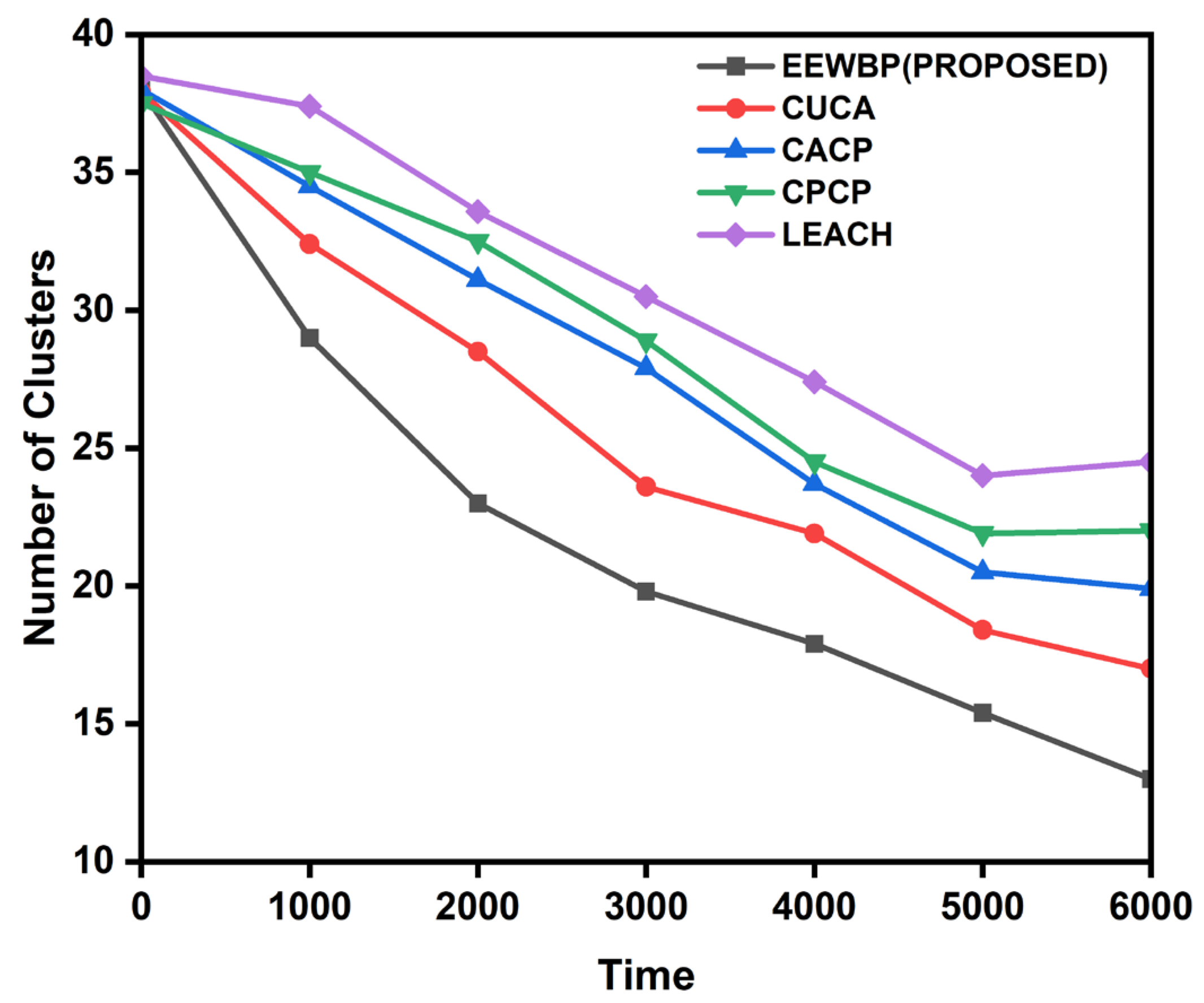
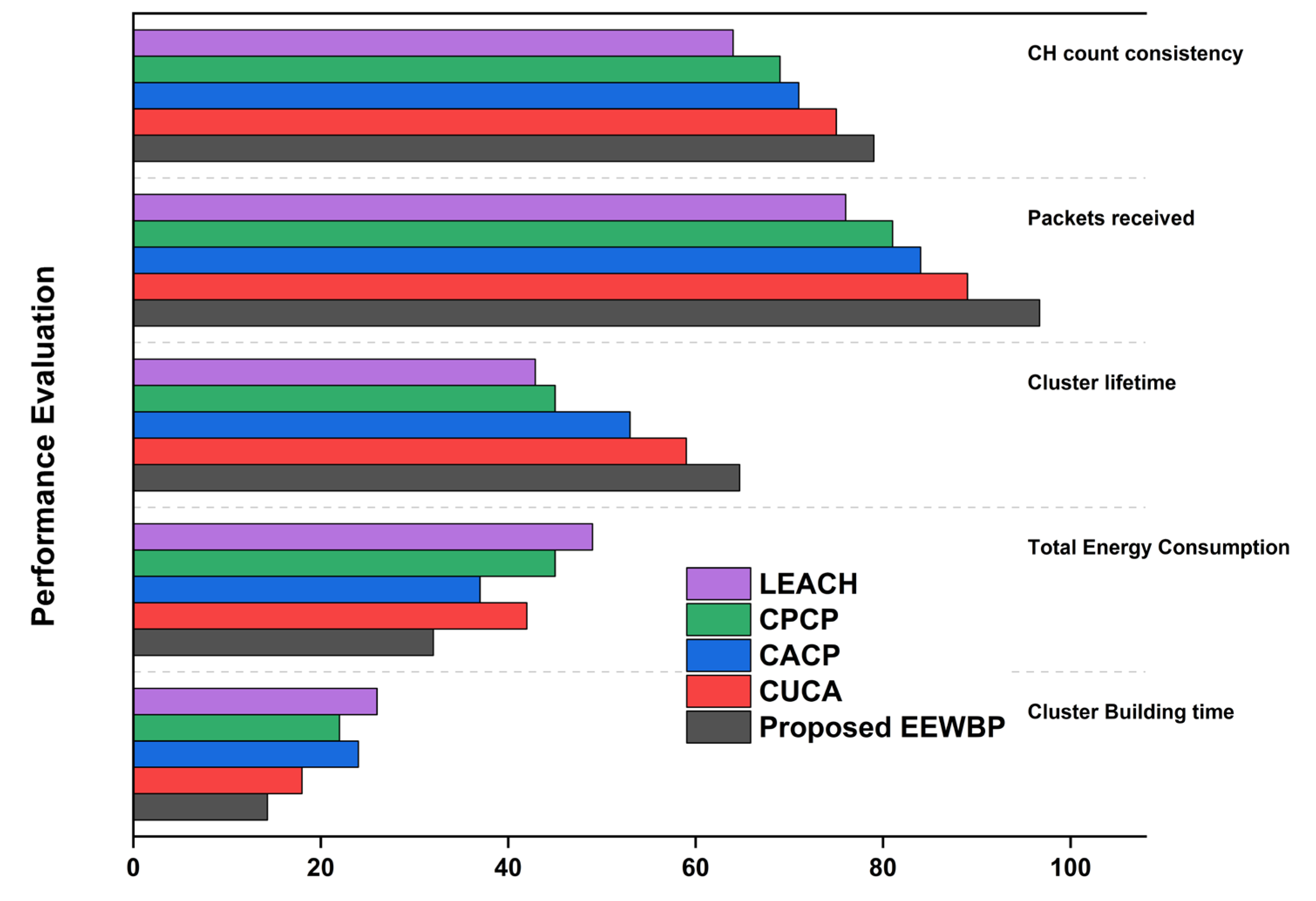
5.2. Number of Clusters
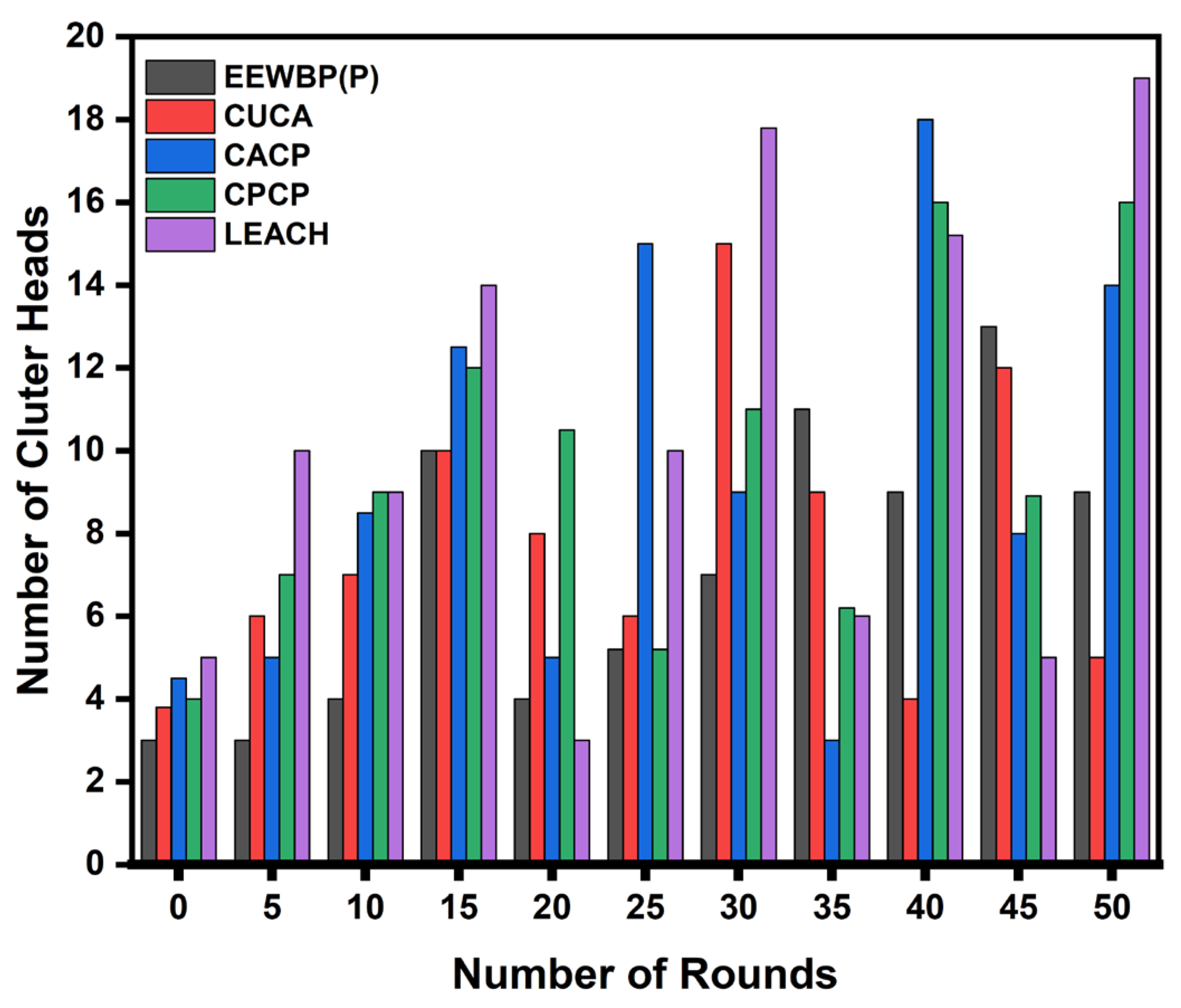
5.3. Consistency in Number of CH
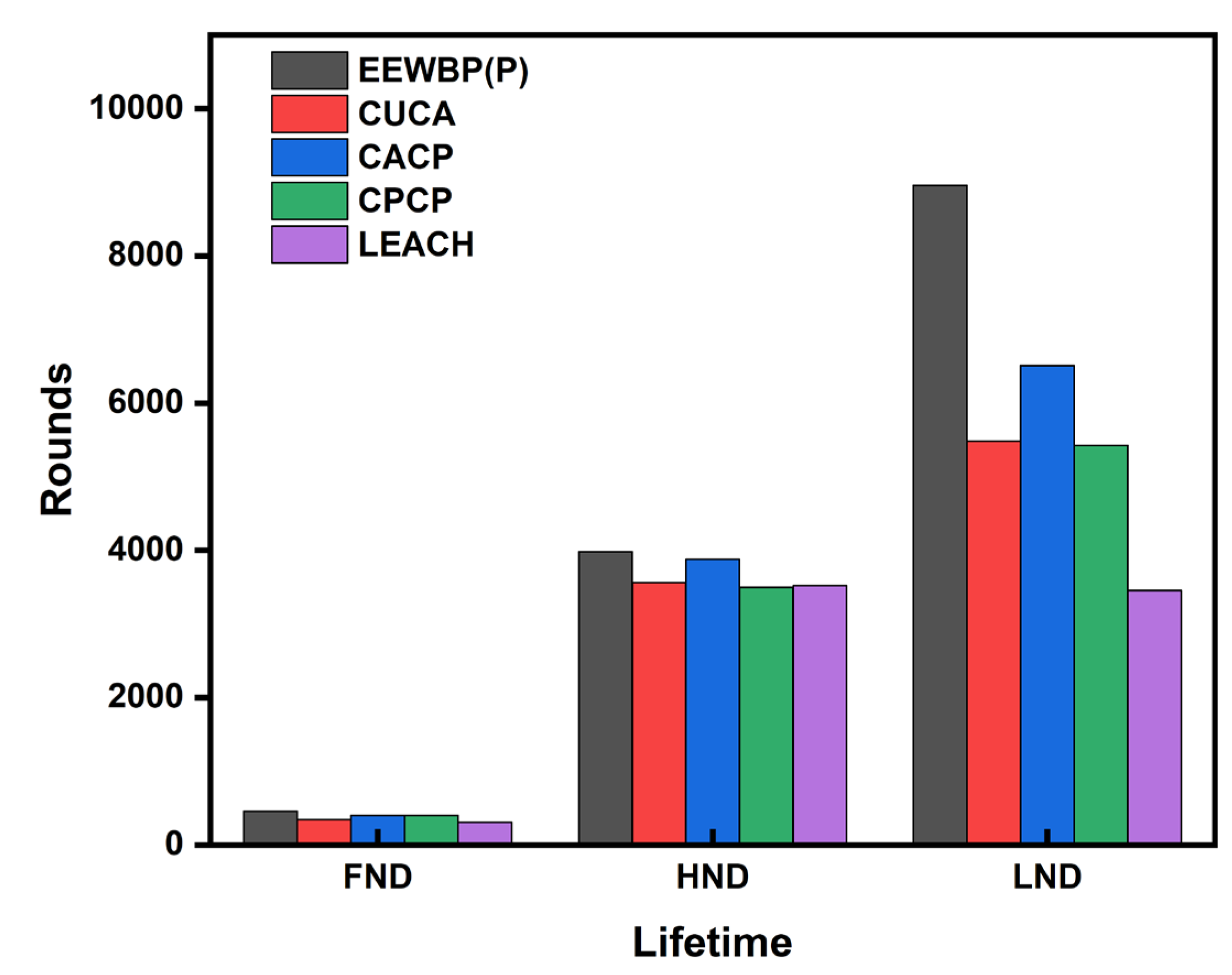
5.4. Cluster Lifetime
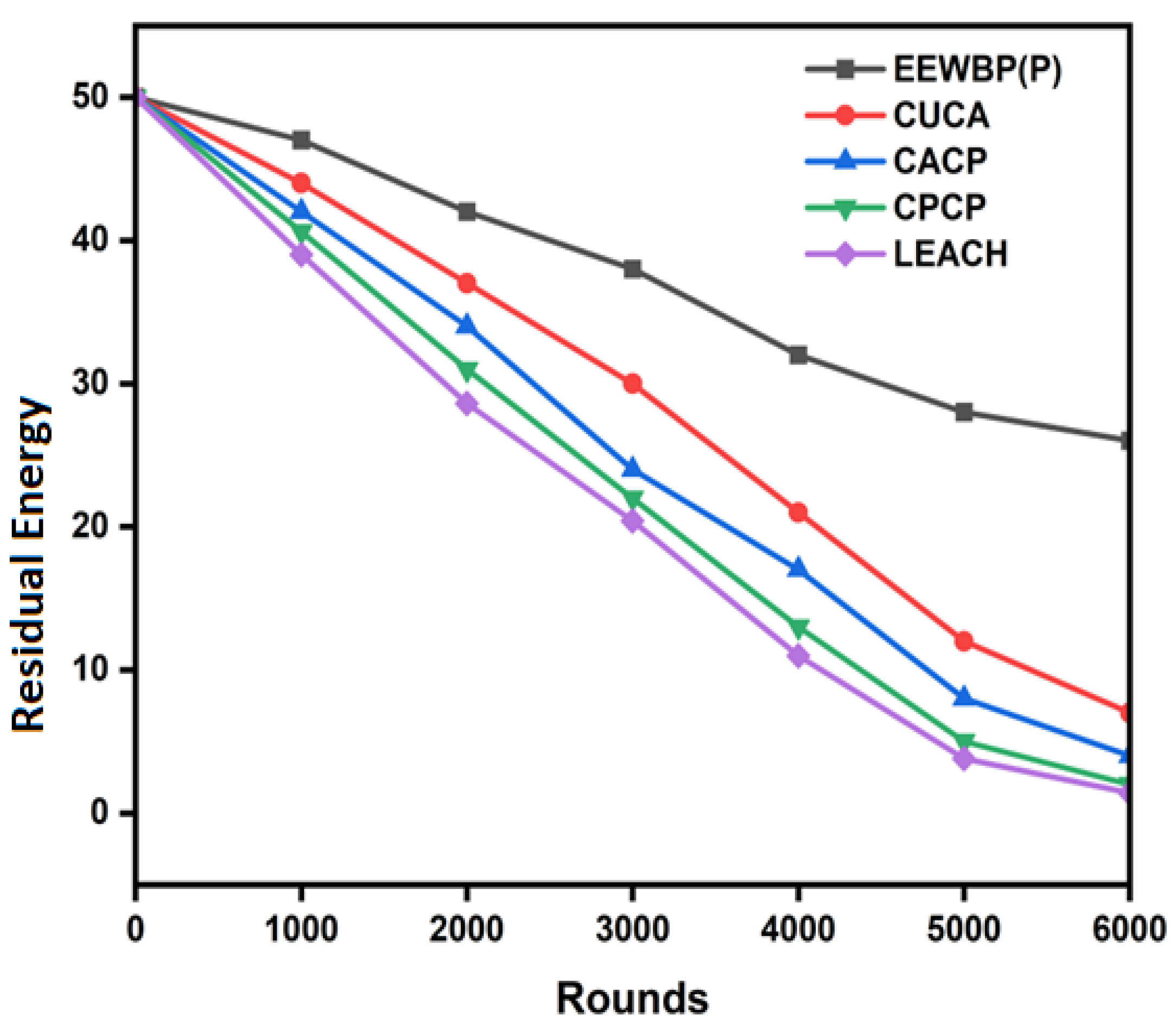
5.5. Residual Energy
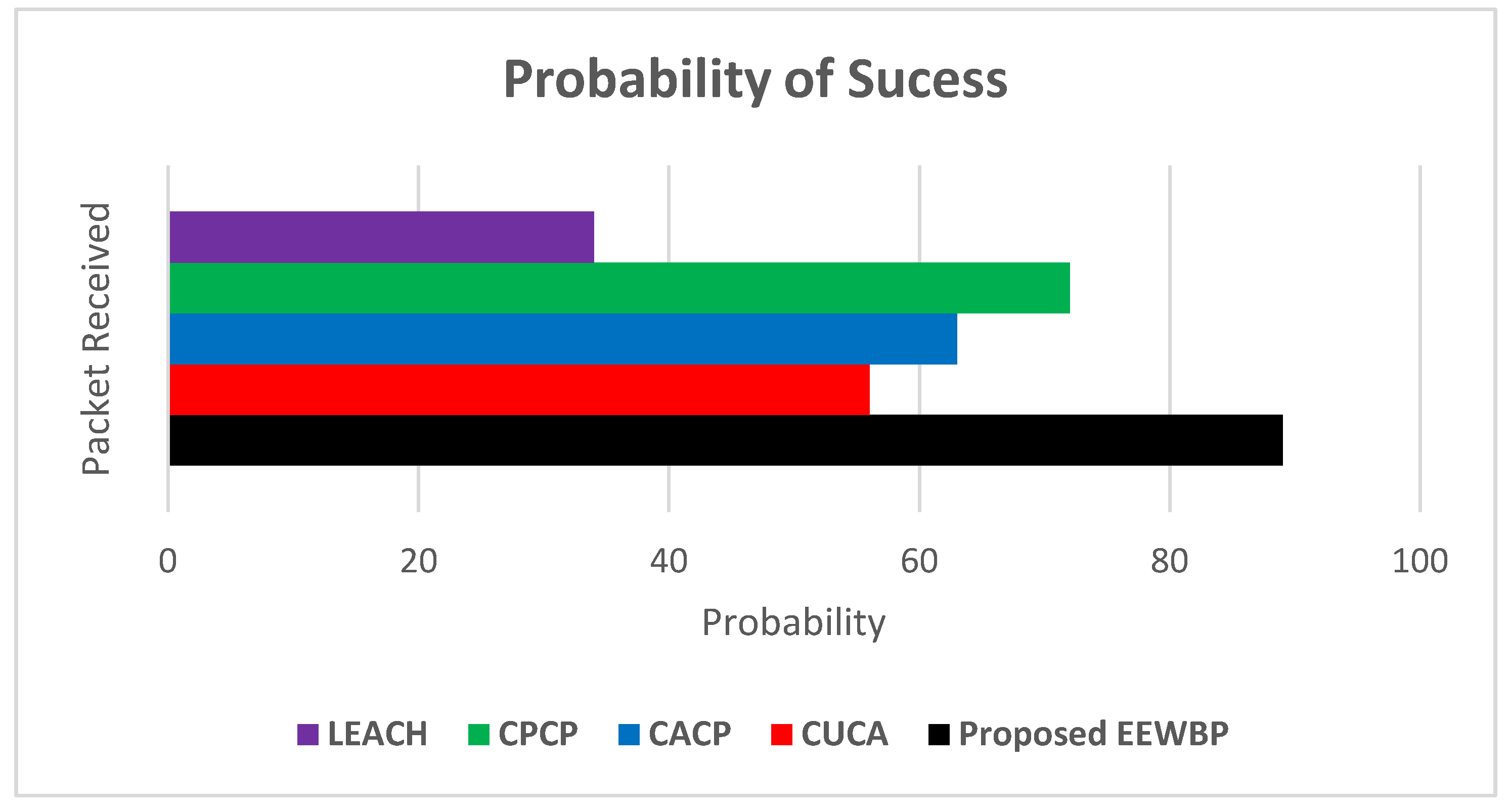
5.6. Probability of Successful Information Delivery
6. Discussion and Analysis of Results
7. Conclusions and Future Scope
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Heinzelman, W.; Chandrakasan, A.; Balakrishnan, H. Energy-Efficient Communication Protocols for Wireless Microsensor Networks. In Proceedings of the 33rd Hawaaian International Conference on Systems Science (HICSS), Maui, HI, USA, 7 January 2000. [Google Scholar]
- Heinzelman, W.; Chandrakasan, A.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Li, D.; Liu, H. Sensor Coverage in Wireless Sensor Networks. In Wireless Networks: Research, Technology and Applications; NOVA Science Publishers, Incorporated: Hauppauge, NY, USA, 2009; pp. 3–31. [Google Scholar]
- Amgoth, T.; Jana, P.K. Energy and Coverage-Aware Routing Algorithm for Wireless Sensor Networks. Wirel. Pers. Commun. 2014, 81, 531–545. [Google Scholar] [CrossRef]
- Kaur, A.; Grover, A. LEACH and Extended LEACH Protocols in Wireless Sensor Network-A Survey. Int. J. Comput. Appl. 2015, 116, 1–5. [Google Scholar] [CrossRef]
- Soro, S.; Heinzelman, W.B. Cluster head election techniques for coverage preservation in wireless sensor networks. Ad Hoc Netw. 2009, 7, 955–972. [Google Scholar] [CrossRef]
- Sahoo, B.M.; Amgoth, T.; Pandey, H.M. Particle swarm optimization based energy efficient clustering and sink mobility in heterogeneous wireless sensor network. Ad Hoc Netw. 2020, 106, 102237. [Google Scholar] [CrossRef]
- Tao, Y.; Zhang, Y.; Ji, Y. Flow-balanced Routing for Multi-hop Clustered Wireless Sensor Networks. Ad Hoc Netw. 2012, 11, 541–554. [Google Scholar] [CrossRef]
- Liu, Z.; Zheng, Q.; Xue, L.; Guan, X. A distributed energy-efficient clustering algorithm with improved coverage in wireless sensor networks. Future Gener. Comput. Syst. 2012, 28, 780–790. [Google Scholar] [CrossRef]
- Mazumdar, N.; Om, H. Coverage-aware Unequal Clustering Algorithm for Wireless Sensor Networks. Procedia Comput. Sci. 2015, 57, 660–669. [Google Scholar] [CrossRef]
- Gu, X.; Yu, J.; Yu, D.; Wang, G.; Lv, Y. ECDC: An energy and coverage-aware distributed clustering protocol for wireless sensor networks. Comput. Electr. Eng. 2014, 40, 384–398. [Google Scholar] [CrossRef]
- Gupta, N.; Maashi, M.S.; Tanwar, S.; Badotra, S.; Aljebreen, M.; Bharany, S. A Comparative Study of Software Defined Networking Controllers Using Mininet. Electronics 2022, 11, 2715. [Google Scholar] [CrossRef]
- Karthik, P.; Shanthibala, P.; Bhardwaj, A.; Bharany, S.; Yu, H.; Zikria, Y.B. A novel subset-based polynomial design for enhancing the security of short message-digest with inflated avalanche and random responses. J. King Saud Univ. Comput. Inf. Sci. 2023, 35, 310–323. [Google Scholar] [CrossRef]
- Gandhi, J.R.; Jhaveri, R.H. Addressing Packet Forwarding Misbehaviour Using Trust-Based Approach in Ad-hoc Networks: A survey. In Proceedings of the 2015 International Conference on Signal Processing and Communication Engineering Systems, Guntur, India, 2–3 January 2015. [Google Scholar]
- Khayat, G.; Maalouf, H. Trust in Real-Time Distributed Database Systems. In Proceedings of the Third International Conference on Electrial and Electronic Engineering, Telecommunication Engineering and Mechatronics, Beirut, Lebanon, 26–28 April 2017. [Google Scholar]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Talwar, B.; Arora, A.; Bharany, S. An Energy Efficient Agent Aware Proactive Fault Tolerance for Preventing Deterioration of Virtual Machines Within Cloud Environment. In Proceedings of the 2021 9th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 3–4 September 2021; IEEE: Piscataway, NJ, USA, 2021. [Google Scholar] [CrossRef]
- Mohamadi, H.; Ismail, A.S.; Salleh, S. Solving target coverage problem using cover sets in wireless sensor networks based on learning automata. Wirel. Pers. Commun. 2013, 75, 447–463. [Google Scholar] [CrossRef]
- Wang, B.; Lim, H.B.; Ma, D. A coverage-aware clustering protocol for wireless sensor networks. Comput. Netw. 2012, 56, 1599–1611. [Google Scholar] [CrossRef]
- Alotaibi, Y. Automated Business Process Modelling for Analyzing Sustainable System Requirements Engineering. In Proceedings of the 2020 6th International Conference on Information Management (ICIM), London, UK, 27–29 March 2020; pp. 157–161. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S. Intelligent Green Internet of Things: An Investigation. In Machine Learning, Blockchain, and Cyber Security in Smart Environments; Chapman and Hall/CRC: London, UK, 2022; pp. 1–15. [Google Scholar] [CrossRef]
- Enam, R.N.; Ismat, N.; Farooq, F. Connectivity and Coverage Based Grid-Cluster Size Calculation in Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 95, 429–443. [Google Scholar] [CrossRef]
- Shokouhi, A.; Farahnaz, R. A Novel Energy-Aware Target Tracking Method by Reducing Active Nodes in Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 95, 3585–3599. [Google Scholar] [CrossRef]
- Handy, M.J.; Haase, M.; Timmermann, D. Low Energy Adaptive Clustering Hierachy with Deterministic Cluster head Selection. In Proceedings of the Fourth IEEE Conference on Mobile and Wireless Communications Networks, Stockholm, Sweden, 9–11 September 2002; pp. 368–372. [Google Scholar]
- Lewis, S.A.; Furness, R.W. An energy-driven unequal clustering protocol for heterogeneous wireless sensor networks. J. Control Theory Appl. 2011, 9, 133–139. [Google Scholar] [CrossRef]
- Liao, Y.; Qi, H.; Li, W. Load-balanced clustering algorithm with distributed self-organization for wireless sensor networks. IEEE Sens. J. 2012, 13, 1498–1506. [Google Scholar] [CrossRef]
- Dohare, U.; Lobiyal, D.K.; Kumar, S. Energy balanced model for lifetime maximization in randomly distributed wireless sensor networks. Wirel. Pers. Commun. 2014, 78, 407–428. [Google Scholar] [CrossRef]
- Kim, H.-Y.; Kim, J. An energy-efficient balancing scheme in wireless sensor networks. Wirel. Pers. Commun. 2015, 94, 17–29. [Google Scholar] [CrossRef]
- Tian, D.; Avenue, K.E.; Georganas, N.D. A coverage-preserving node scheduling scheme for large wireless sensor networks. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, WSNA’02, Atlanta, GA, USA, 28 September 2002; pp. 32–41. [Google Scholar] [CrossRef]
- Shahraki, A.; Geitle, M.; Haugen, Ø. A comparative node evaluation model for highly heterogeneous massive-scale Internet of Things-Mist networks. Trans. Emerg. Telecommun. Technol. 2020, 31, e3924. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Bhatia, S.; Rahmani, M.K.I.; Shuaib, M.; Lashari, S.A. Energy Efficient Clustering Protocol for FANETS Using Moth Flame Optimization. Sustainability 2022, 14, 6159. [Google Scholar] [CrossRef]
- Darabkh, K.A.; El-Yabroudi, M.Z.; El-Mousa, A.H. BPA-CRP: A balanced power-aware clustering and routing protocol for wireless sensor networks. Ad Hoc Netw. 2018, 82, 155–171. [Google Scholar] [CrossRef]
- Wang, Q.; Lin, D.; Yang, P.; Zhang, Z. An energy-efficient compressive sensing-based clustering routing protocol for wsns. IEEE Sens. J. 2019, 19, 3950–3960. [Google Scholar] [CrossRef]
- Mohapatra, H.; Rath, A.K. Fault Tolerance through Energy Balanced Cluster Formation (EBCF) in WSN. In Proceedings of the Smart Innovations in Communication and Computational Sciences; Springer : Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Lin, D.; Wang, Q. An energy-efficient clustering algorithm combined game theory and dual-Cluster-Head mechanism for WSNs. IEEE Access 2019, 7, 49894–49905. [Google Scholar] [CrossRef]
- Hamzah, A.; Shurman, M.; Al-Jarrah, O.; Taqieddin, E. Energy-efficient fuzzy-logic-based clustering technique for hierarchical routing protocols in wireless sensor networks. Sensors 2019, 19, 561. [Google Scholar] [CrossRef]
- Sohal, A.K.; Sharma, A.K.; Sood, N. Enhancing Coverage Using Weight Based Clustering in Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 98, 3505–3526. [Google Scholar] [CrossRef]
- Khan, A.N.; Cha, Y.-O.; Giddens, H.; Hao, Y. Recent Advances in Organ Specific Wireless Bioelectronic Devices: Perspective on Biotelemetry and Power Transfer Using Antenna Systems. Engineering 2022, 11, 27–41. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Frnda, J.; Shuaib, M.; Khalid, M.I.; Hussain, S.; Iqbal, J.; Ullah, S.S. Wildfire Monitoring Based on Energy Efficient Clustering Approach for FANETS. Drones 2022, 6, 193. [Google Scholar] [CrossRef]
- Bharany, S.; Badotra, S.; Sharma, S.; Rani, S.; Alazab, M.; Jhaveri, R.H.; Gadekallu, T.R. Energy Efficient Fault Tolerance Techniques in Green Cloud Computing: A Systematic Survey and Taxonomy. Sustain. Energy Technol. Assess. 2022, 53, 102613. [Google Scholar] [CrossRef]
- Sadiq, M.T.; Yu, X.; Yuan, Z.; Fan, Z.; Rehman, A.U.; Li, G.; Xiao, G. Motor Imagery EEG Signals Classification Based on Mode Amplitude and Frequency Components Using Empirical Wavelet Transform. IEEE Access 2019, 7, 127678–127692. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Khalaf, O.I.; Abdulsahib, G.M.; Al Humaimeedy, A.S.; Aldhyani, T.H.H.; Maashi, M.; Alkahtani, H. A Systematic Survey on Energy-Efficient Techniques in Sustainable Cloud Computing. Sustainability 2022, 14, 6256. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef] [PubMed]
- Shuaib, M.; Badotra, S.; Khalid, M.I.; Algarni, A.D.; Ullah, S.S.; Bourouis, S.; Iqbal, J.; Bharany, S.; Gundaboina, L. A Novel Optimization for GPU Mining Using Overclocking and Undervolting. Sustainability 2022, 14, 8708. [Google Scholar] [CrossRef]
- Bharany, S.; Kaur, K.; Badotra, S.; Rani, S.; Kavita; Wozniak, M.; Shafi, J.; Ijaz, M.F. Efficient Middleware for the Portability of PaaS Services Consuming Applications among Heterogeneous Clouds. Sensors 2022, 22, 5013. [Google Scholar] [CrossRef]
- Sadiq, M.T.; Yu, X.; Yuan, Z.; Zeming, F.; Rehman, A.U.; Ullah, I.; Li, G.; Xiao, G. Motor Imagery EEG Signals Decoding by Multivariate Empirical Wavelet Transform-Based Framework for Robust Brain–Computer Interfaces. IEEE Access 2019, 7, 171431–171451. [Google Scholar] [CrossRef]
- Hussain, W.; Sadiq, M.T.; Siuly, S.; Rehman, A.U. Epileptic seizure detection using 1 D-convolutional long short-term memory neural networks. Appl. Acoust. 2021, 177, 107941. [Google Scholar] [CrossRef]
- Ahmed, A.; Ahmed, Q.Z.; Almogren, A.; Haider, S.K.; Rehman, A.U. Hybrid Precoding Aided Fast Frequency-Hopping for Millimeter-Wave Communication. IEEE Access 2021, 9, 149596–149608. [Google Scholar] [CrossRef]
- Leccese, F.; Cagnetti, M.; Giarnetti, S.; Petritoli, E.; Luisetto, I.; Tuti, S.; Formisano, C. Comparison between routing protocols for wide archeological site. In Proceedings of the 2018 IEEE International Conference on Metrology for Archaeology and Cultural Heritage, MetroArchaeo 2018—Proceedings, Cassino, Italy, 22–24 October 2018; pp. 406–410. [Google Scholar] [CrossRef]
- Rizwan, R.; Arshad, J.; Almogren, A.; Jaffery, M.H.; Yousaf, A.; Khan, A.; Rehman, A.U.; Shafiq, M. Implementation of ANN-Based Embedded Hybrid Power Filter Using HIL-Topology with Real-Time Data Visualization through Node-RED. Energies 2021, 14, 7127. [Google Scholar] [CrossRef]
- Khan, M.D.; Ullah, Z.; Ahmad, A.; Hayat, B.; Almogren, A.; Kim, K.H.; Ilyas, M.; Ali, M. Energy Harvested and Cooperative Enabled Efficient Routing Protocol (EHCRP) for IoT-WBAN. Sensors 2020, 20, 6267. [Google Scholar] [CrossRef]
- Kaur, K.; Bharany, S.; Badotra, S.; Aggarwal, K.; Nayyar, A.; Sharma, S. Energy-efficient polyglot persistence database live migration among heterogeneous clouds. J. Supercomput. 2022, 79, 265–294. [Google Scholar] [CrossRef]
- Rafique, W.; Khan, A.; Almogren, A.; Arshad, J.; Yousaf, A.; Jaffery, M.H.; Rehman, A.U.; Shafiq, M. Adaptive Fuzzy Logic Controller for Harmonics Mitigation Using Particle Swarm Optimization. Comput. Mater. Contin. 2022, 71, 4275–4293. [Google Scholar] [CrossRef]
- Bhardwaj, A.; Kaushik, K.; Bharany, S.; Rehman, A.U.; Hu, Y.-C.; Eldin, E.T.; Ghamry, N.A. IIoT: Traffic Data Flow Analysis and Modeling Experiment for Smart IoT Devices. Sustainability 2022, 14, 14645. [Google Scholar] [CrossRef]
- Leccese, F.; Cagnetti, M.; Tuti, S.; Gabriele, P.; De Francesco, E.; Ðurović-Pejčev, R.; Pecora, A. Modified leach for necropolis scenario. In Proceedings of the IMEKO International Conference on Metrology for Archaeology and Cultural Heritage, MetroArchaeo 2017, Lecce, Italy, 23–25 October 2017; pp. 442–447. [Google Scholar]
- Cagnetti, M.; Leccisi, M.; Leccese, F. Reliability comparison of routing protocols for WSNs in wide agriculture scenarios by means of ηl index. In Proceedings of the SENSORNETS 2020—Proceedings of the 9th International Conference on Sensor Networks, Valletta, Malta, 28–29 February 2020; pp. 169–176. [Google Scholar]
- Leccisi, M.; Cagnetti, M.; Leccese, F.; Spagnolo, G.S. Comparing routing protocols for WSN in agricultural scenario. In Proceedings of the 2021 IEEE International Workshop on Metrology for Agriculture and Forestry, MetroAgriFor, Trento-Bolzano, Italy, 3–5 November 2021; pp. 80–85. [Google Scholar] [CrossRef]
- Cagnetti, M.; Leccisi, M.; Leccese, F. A modified MPRR protocol for WSN in agricultural scenario. In Proceedings of the SENSORNETS 2021—Proceedings of the 10th International Conference on Sensor Networks, Online Streaming, 9–10 February 2021; pp. 143–150. [Google Scholar]
- Awotunde, J.B.; Adeniyi, A.E.; Abiodun, K.M.; Ajamu, G.J.; Matiluko, O.E. Application of cloud and IoT technologies in battling the COVID-19 pandemic. In Machine Learning for Critical Internet of Medical Things: Applications and Use Cases; Springer International Publishing: Cham, Switzerland, 2022; pp. 1–29. [Google Scholar]
- Adeniyi, A.E.; Misra, S.; Daniel, E.; Bokolo, A., Jr. Computational complexity of modified blowfish cryptographic algorithm on video data. Algorithms 2022, 15, 373. [Google Scholar] [CrossRef]
- Adeniyi, E.A.; Falola, P.B.; Maashi, M.S.; Aljebreen, M.; Bharany, S. Secure sensitive data sharing using RSA and ElGamal cryptographic algorithms with hash functions. Information 2022, 13, 442. [Google Scholar] [CrossRef]
- Zhang, J.; Gao, W.; Chuai, G.; Zhou, Z. An Energy-Effective and QoS-Guaranteed Transmission Scheme in UAV-Assisted Heterogeneous Network. Drones 2023, 7, 141. [Google Scholar] [CrossRef]
- Yu, J.; Cheng, T.; Cai, N.; Zhou, X.-G.; Diao, Z.; Wang, T.; Du, S.; Liang, D.; Zhang, D. Wheat Lodging Segmentation Based on Lstm_PSPNet Deep Learning Network. Drones 2023, 7, 143. [Google Scholar] [CrossRef]
- Kim, B.; Jang, J.; Jung, J.; Han, J.; Heo, J.; Min, H. A Computation Offloading Scheme for UAV-Edge Cloud Computing Environments Considering Energy Consumption Fairness. Drones 2023, 7, 139. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Alsharabi, N.; Eldin, E.T.; Ghamry, N.A. Energy-efficient clustering protocol for underwater wireless sensor networks using optimized glowworm swarm optimization. Front. Mar. Sci. 2023, 10, 99. [Google Scholar] [CrossRef]
| Protocol | Published Year | Type of Mode | Approach | Sensing Model | Drawbacks |
|---|---|---|---|---|---|
| LEACH [1] | 2000 | Homogenous | Centralized | Disc | CH nodes are distributed in a non-uniform manner. CH is chosen at random and in each cluster, the nodes are not spread uniformly. |
| I-LEACH [5] | 2015 | Homogenous | Centralized | Disc | Unlike nodes that receive distinct data, CH combines collected data to cut data transmission costs. |
| CPCP [6] | 2009 | Homogenous | Distributed | Disc | Sensor node computation load is high. |
| CACP [19] | 2012 | Homogenous | Distributed | Hexagonal | Death of CHs owing to direct transmission of aggregate data. Useful for small networks only. |
| LEACH-C [7] | 2020 | Homogenous | Distributed | Disc | The position of nodes is required every time. Transmission with a single hop adds an additional overhead to the sink when centralization is used. |
| FBR [8] | 2013 | Homogenous | Centralized | Disc | No change in sensor load when communication overhead rises. |
| DEECIC [9] | 2012 | Homogenous | Distributed | Disc | Clustering algorithms that are more energy-efficient than those that are more coverage efficient. |
| ECDC [11] | 2014 | Heterogeneous | Distributed | Disc | Routing requires retransmission of control packets, consuming additional energy. |
| CUCA [15] | 2017 | Homogenous | Distributed | Disc | Useful for small networks only. |
| DECAR [12] | 2014 | Homogenous | Distributed | Disc | Send aggregate data to sink is not possible in a huge network. |
| Protocol | Energy-efficient | Position of Base Station | Number of Cluster Nodes | Number of CH | Cluster Method | Mobility |
|---|---|---|---|---|---|---|
| LEACH [1] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| I-LEACH [5] | Yes | Outside | Unpredictable | Certain | Distributed | Static |
| CPCP [6] | Yes | Centre | Unpredictable | Uncertain | Distributed | Static |
| CACP [19] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| LEACH-C [7] | Yes | Outside | Unpredictable | Certain | Centralized | Static |
| FBR [8] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| DEECIC [9] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| ECDC [11] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| CUCA [15] | Yes | Outside | Unpredictable | Uncertain | Distributed | Static |
| DECAR [12] | Yes | Inside | Unpredictable | Uncertain | Distributed | Static |
| Protocol | Network Size in m2 | Number of Nodes | Location Aware | Deployment Model | Coverage Type | Residuary Energy Involved |
|---|---|---|---|---|---|---|
| LEACH [1] | 100 × 100 | 100 | Yes | Random | No | No |
| I-LEACH [5] | 100 × 100 | 100 | Yes | Random | No | Yes |
| CPCP [6] | 200 × 200 | 400 | Yes | Random and non-uniform | Area | No |
| CACP [19] | 120 × 120 | 1000 | Yes | Random and uniform | Area | Yes |
| LEACH-C [7] | 100 × 100 | 100 | Yes | Random | Yes | Yes |
| FBR [8] | 150 × 150 | 1000 | Yes | Random | No | |
| DEECIC [9] | 100 × 100 | 100 | No | Random | Bounded Area | Yes |
| ECDC [11] | 200 × 200 | 100–200 | Yes | Random and non-uniform | Area and point | Yes |
| CUCA [15] | 40 × 40 | 60–100 | Yes | Not discussed | Area | No |
| DECAR [12] | 40 × 40 | 100 | Yes | Random and Grid | Area | Yes |
| Parameter | Default Value | Parameter | Default Value |
|---|---|---|---|
| Monitoring area | 100 m × 100 m | Amplifier constant [1,2] | 10 pJ/bit/m2 |
| Network node count | 200 | CH energy threshold [2] | 10–4 J |
| Shortest possible path between nodes | 2 m | Size of packet [2] | 30 bytes |
| Number of simulations performed | 100 | Rate of packets [2] | 1 packet/s |
| Simulation clock time | 120 s | Detection distance [2] | 10 m |
| Position of BS | (50, 50) | Size of a cluster [2] | 25 m |
| Initial energy | 0.5 J | Energy used to send each bit | 50 × 0.000000001 |
| Transmission scope | 40 m | Energy used to receive | 50 × 0.000000001 |
| Chance of a node becoming a CH | 0.1 | Tx/Rx electronics constant [2] | 50 nJ/bit |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kaur, P.; Kaur, K.; Singh, K.; Kim, S. Early Forest Fire Detection Using a Protocol for Energy-Efficient Clustering with Weighted-Based Optimization in Wireless Sensor Networks. Appl. Sci. 2023, 13, 3048. https://doi.org/10.3390/app13053048
Kaur P, Kaur K, Singh K, Kim S. Early Forest Fire Detection Using a Protocol for Energy-Efficient Clustering with Weighted-Based Optimization in Wireless Sensor Networks. Applied Sciences. 2023; 13(5):3048. https://doi.org/10.3390/app13053048
Chicago/Turabian StyleKaur, Puneet, Kiranbir Kaur, Kuldeep Singh, and SeongKi Kim. 2023. "Early Forest Fire Detection Using a Protocol for Energy-Efficient Clustering with Weighted-Based Optimization in Wireless Sensor Networks" Applied Sciences 13, no. 5: 3048. https://doi.org/10.3390/app13053048
APA StyleKaur, P., Kaur, K., Singh, K., & Kim, S. (2023). Early Forest Fire Detection Using a Protocol for Energy-Efficient Clustering with Weighted-Based Optimization in Wireless Sensor Networks. Applied Sciences, 13(5), 3048. https://doi.org/10.3390/app13053048







