Abstract
A smart city is where existing facilities and services are enhanced by digital technology to benefit people and companies. The most critical infrastructures in this city are interconnected. Increased data exchange across municipal domains aims to manage the essential assets, leading to more automation in city governance and optimization of the dynamic offered services. However, no clear guideline or standard exists for modeling these data flows. As a result, operators, municipalities, policymakers, manufacturers, solution providers, and vendors are forced to accept systems with limited scalability and varying needs. Nonetheless, it is critical to raise awareness about smart-city cybersecurity and implement suitable measures to safeguard citizens’ privacy and security because cyber threats seem to be well-organized, diverse, and sophisticated. This study aims to present an overview of cyber threats, attacks, and countermeasures on the primary domains of smart cities (smart government, smart mobility, smart environment, smart living, smart healthcare, smart economy, and smart people). It aims to present information extracted from the state of the art so policymakers can perceive the critical situation and simultaneously be a valuable resource for the scientific community. It also seeks to offer a structural reference model that may guide the architectural design and implementation of infrastructure upgrades linked to smart city networks.
1. Introduction
The smart city [1] is an ecosystem that offers various e-government services, ensuring the seamless access of participating citizens to these services. At the same time, through an integrated analysis program of the information collected, it promotes the optimal use of available resources, the improvement of urban space, and its other administrative services. A city can be considered smart when traditional infrastructure and investment in human resources support sustainable economic development and high quality of life based on integrated control technology (\) . In this spirit, a smart city can connect its built environment, which is also its natural capital, with society, businesses, and human resources to develop better services and infrastructure for its perpetual sustainability [2].
As said, the role of ICT is to provide intelligent management tools that will unite and strengthen the networks of people, infrastructure, companies, and generally available resources with the aim of sustainable economic development, high quality of life, and general well-being for the vast majority of citizens. Therefore, a smart city is a city that tries to face and solve public issues with the help of technology but based on a participatory process between multiple stakeholders, with the prudent management of natural reseizures above all, through the participatory action and active participation of citizens, preventing and many times eliminating social exclusion. Thus, smart cities ensure a networked urban society which enjoys the benefits of the intelligent management of its affairs with minimal financial, administrative, and social costs [3].
Here, it is also important to mention that a city cannot be considered smart if useful, up-to-date, and essential data are not collected, allowing all city entities, from competent bodies to each citizen, to make smart decisions. Critical data offer convenience, economy, optimal services, and better and more thoughtful design in a sustainable scheme, where problems are not simply solved. Still, based on the stored historical data, their hidden knowledge can reveal trends, allowing relevant agencies to implement preventive policies to avoid complex situations. As a result, in addition to the direct benefits that any city entity may receive, these essential data can also provide indirect benefits. For example, companies can use academic institutions and research bodies in environmental, social, economic, or transportation studies for appropriate adaptation. Additionally, their products or services can be used by non-profit and non-governmental organizations to carry out more effective work [4].
Many urban areas, including energy supply, transportation systems, and telecommunications infrastructure, have started to include parts of a “smart grid”—or a network of linked sensors inside the city with many advantages. On the other hand, increased connection brings potentially severe cyber security concerns that have yet to be fully identified and managed [5].
Based on the above, information security is critical in intelligent cities to ensure higher confidentiality, availability, and integrity levels. Additionally, it ensures the stability that national services and organizations require to support sustainable and livable intelligent environments. Although smart cities are intended to boost productivity and efficiency, they may pose severe hazards to inhabitants and authorities if cyber security is not prioritized.
For example, the internet of things (IoT) growth reveals new vulnerabilities for intruders and other hostile actors to exploit. There are many possible vulnerabilities and techniques with billions of linked “things” installed in smart cities throughout the globe [6].
Summarizing, the following are the most significant security challenges for smart city environments [7]:
- A large and complex attack surface: As cities become more intelligent, they will incorporate more systems and “systems of systems,” increasing the risk and impact of an attack and necessitating better control and visibility. Furthermore, the integration of vendor solutions increases the complexity of intelligent city systems, particularly during rapid technological transformations.
- Inadequate oversight and organization: Complex systems will necessitate more robust management and governance capabilities. Keeping leadership fully informed of complex occurrences will require additional resources and capabilities.
In the face of a constantly developing cyber threat scenario, the research community must supply threat information, prevention, and reaction, as smart cities will give enter-prizes unparalleled economic potential. However, because of the significant increase in interconnected devices, cyber threat actors will be presented with an unprecedented attack surface. Securing smart cities must be a collaborative project involving local administrations and private sector organizations with an immediate stake in the city’s stable function. Additionally, ensuring that smart cities are cyber-safe will need identifying and prioritizing critical assets and behavior-based security—creating a baseline for the routine functioning of vital support. It should be emphasized that a Smart City’s smartness is measured by seven aspects in which the city should excel smart government, smart mobility, smart environment, smart living, smart healthcare, smart economy and smart people [1]. These critical assets must guarantee that all sections of the city conform to minimal benchmarks, a policy of quick component replacement in case of breach or failure, and a safe segment of critical private assets from the public network. In this sense, this research aims to identify the cyber threats, attacks, and countermeasures based on the seven primary domains of smart cities listed above.
The following is the structure of the study: The next section, Section 2, provides an in-depth description of the primary threat’s attacks and countermeasures that are present in the seven domains of the smart city networks, how they function, and the associated effective solutions that have been proposed in the most recent literature. Section 3 presents some concrete recommendations, and Section 4 summarizes the primary findings from the investigation, makes the conclusions and discusses potential avenues for further study.
2. Literature Review
Improving residents’ living standards is the primary goal of constructing smart cities. From this point of view, a smart city utilizes its resources more effectively and produces an intelligent ecosystem using the capabilities of digital technology. It requires more inventive urban transport networks, better water supply and waste-disposal facilities, and more efficient methods to light and heat buildings in living places. It also involves more creative ways to deliver democracy and decision participation to citizens. It also means having a clean and safe environment with accessible public areas and user-friendly financial services that cater to the population’s requirements without restrictions or exclusions. It should be emphasized that this connection is achieved with the optimal use of ICT, making smart citizens of a smart city [2,5].
This study presents an overview of the most dangerous cyber threats, attacks, and countermeasures to smart city networks based on the seven primary domains of smart cities [8]. In this context, the paper examines indicative but very characteristic cases of cyber threats related to these categories and the countermeasures proposed in the recent literature.
2.1. Smart Government
Smart governance [9] encompasses services that reflect political participation and opportunities for citizens’ social inclusion in the administration’s operation. It also encourages the most efficient administration at the lowest possible cost, in which human and available resources are fully utilized. Additional training opportunities are also provided, and the processing of bureaucratic tasks is promoted digitally, removing the citizen from an unfair waste of time [10]. Furthermore, smart governance empowers citizens to participate in public decision making and city planning, increasing efficiency and information transparency.
It is necessary to have policy guidelines in place in smart cities to guarantee the smoothness, security, integrity, and secrecy of smart governance [11]. The use of technology in smart governance must comply with a nation’s laws to be considered legitimate.
The city’s governance services are becoming smarter and more complex [12], but these users must be prepared to confront cyberspace security using more sophisticated technology and infrastructure [13]. Governance service providers are facing growing problems in adopting a culture of security and information confidentiality as a critical component of their services [14,15].
2.1.1. Cyber Threats or Attacks
These difficulties will endure as long as regulatory oversight and information security risks exist. Improving the information security culture inside these firms will most certainly aid in the safety of governance information, transactions, and personal information and the continuing performance of essential governance processes [16]. For example, risk identification and mitigation must occur at intersections and in separate domains in the governance system. The designation from the inter-sector dimension considers the linkages of the national or municipal sector and the interdependence of the other domestic and foreign sectors. Furthermore, the intersectoral extent indicates how risk is distributed throughout interrelated systems (contagion risk) because of parallels in concentration risk and connectivity. Meanwhile, the inter-time dimension specifies how hazards in the planned system rise over time, primarily risk caused by procedural behavior shifting from one sector to another [17].
In a smart governance scenario (as depicted in Figure 1), municipal authorities and local administrations strive to structure and arrange city-wide interventions across various IoT systems/applications to build an all-in-one and coordinated IoT ecosystem for the full smart city [18]. However, the administration of a whole smart city requires a significant degree of responsibility for the many tasks to be completed, such as managing IoT systems (e.g., credential access and control of sensitive data). In addition, technology is necessary to handle these IoT systems in a coordinated and well-managed manner. The technical background required to carry out know-how is not recognized by city authorities but by professionals in the field [14].
Figure 1.
Smart governance scenario.
As a result, municipal governments need ICT-based solutions that offer the elements necessary for the smart governance of the smart city, emphasizing the following desirable features [10,11,17]:
- Permission hierarchy model. Upper-tier authorities need a multilevel governance solution to distribute and transfer authority and duties across various levels of government (top-down governance) [19].
- Keeping track of duties. Because of the variety of IoT systems and functions supplied in a smart city, the various authorities must administer a role-based access control system to allocate and monitor duties.
- Inclusion. An integrated strategy to accommodate heterogeneity within the same ICT-based solution is required to facilitate data interchange—third-party API (application programming interface) deployment, sharing credentials and permissions, and so forth.
- Support for new systems. A suitable solution that allows the integration of new IoT systems over time, independent of the technology on which they are based, is necessary for a dynamic smart municipal, integrating the latest IoT system into the ICT-based solution offered by the city authorities.
- Safety and privacy. It is critical to include security methods in the elements outlined above. For example, only authorized and authenticated users may manage permissions using well-tested and robust processes.
Several ICT-based solutions are needed to address these aspects. For different entities to cover these features, a common infrastructure that provides ICT-based tools and mechanisms is required, ensuring that the same rules and regulations guide IoT systems that belong to a smart city in terms of smart governance [20].
From this perspective, governance systems must be based on ISO 27001:2013, a global standard for designing and evaluating an information security management system. This is important for any governance transaction service provider because transactions as part of a governance process must be secure and easy to complete. Other references that are often used for security requirements in technology-based services include the following [21,22]:
- COBIT—The Board of Standards Audit and Information Systems Control (ISACA) publishes the Control of Information and Related Technologies (COBIT), which offers a control framework for corporate governance and IT governance.
- ISO/IEC 15408—These assessment criteria were established and are aligned with the national security standards.
- ITIL (or ISO/IEC 20000 series)—This publication presents a collection of best practices in IT services management (ITSM), focusing on the IT service process and emphasizing the user’s important role.
- The ISO/IEC 27001—This certificate is often the most basic information technology standard and determines which other security standards must also comply by a government organization. For example, if a governance domain offers payment services, it must meet, if not exceed, the Payment Card Industry Data Security Standard (PCI DSS).
2.1.2. Countermeasures
This paper [4] shows how proper smart governance and security framework on which a built adequate security infrastructure could simplify and speed up the certification process and simultaneously reduce the certification cost.
However, the link between smart governance and data security is quite complex [23]. Information security risks and data challenges, such as data transfer, processing, information management, network security, and equipment access are significant. The goal is to improve the smart governance operation environment and big data security by studying and improving relevant laws and regulations, strengthening access control processing, improving system protection levels, strengthening the integration of new technologies, and improving network intrusion detection systems and identity security verification mechanisms [24].
Only authorized users should be able to access smart governance services, so authentication must be more secure. This research proposes a three-factor authentication scheme for e-governance applications to address the shortcomings of previous approaches. Lightweight XOR, one-way, and perceptual hash are used for permission. User identity, passwords, and biometrics improve scalability and security. The suggested approach has been verified using the popular Automated Validation of Internet Security Protocols and Applications tool. According to the security study [22], the system is resistant to numerous threats.
In this direction, the authors of this article [25] provide a smart data sharing architecture for a smart city environment based on smart contracts and blockchains. The suggested approach combines data access control and auditing to protect data exchange among stakeholders. PoT is a complex security solution. The proposed consensus technique uses a multidimensional trust model to determine smart service provider trustworthiness. The suggested solution complies with privacy laws and regulations, including GDPR duties.
Additionally, to protect the privacy of this sensitive information, unique software tools and cryptographic security protocols must be employed using the user’s settings [16,26]. Hardware devices must be put inside the linked system to improve these security settings. Because the government is the critical player in delivering electronic services under its authority, this study has previously presented a citizen-centric multidimensional smart-card-based e-governance system [13]. The authors of [14] created a cloud architecture as an interconnected governance model to handle a large volume of sensitive information. The new model’s viability is shown via cloud banking transactions via a linked governance environment.
On the other hand, there are several practical proposals for this avenue: the authors of this study [15] propose an architecture for the smart governance of heterogeneous IoT solutions inside smart cities, which includes aspects such as power distribution, security limitations, and scalability, among others. It is a modified version of the fundamental architectural paradigm of smart government systems. It relies on digital objects to represent, store, and interact with physical and digital materials. It also uses open-source technologies to create the architectural concept and manage digital objects.
Following the proposed transparent and open adjudication procedure, local officials may assign, for example, the administration of the city’s smart lighting system. This is done by defining and creating new digital objects as part of the smart city infrastructure for these new actors: (55555/city/company for the company and 55555/users/manager for the company manager or representative) and granting permissions to the manager to handle all smart lighting infrastructure. Similarly, the manager may authorize other members of the institution, such as the IoT system manager (55555/users/iotmanager), to assign tasks to trusted employers.
Adopting this multi-level smart governance architecture also addresses one of the most challenging difficulties in any IoT-based solution: naming (devices or IoT settings). Because of the handle system and its global infrastructure, each infrastructure installed following the concept functions as an independent node in a well-structured network that functions as a domain name system (DNS). In this approach, any IoT material and smart-governance-related element may be accessible from anywhere, including external ecosystems, such as other companies, municipal authorities, and smart cities.
Remote e-voting is unquestionably the apex of e-governance in a prosperous smart city. Remote e-voting is convenient and gives voters simple access. On the other hand, it makes it simpler for election officials to tally ballots and compile reports. Nonetheless, there has been increased criticism of the security and integrity of remote e-voting systems. Concerns have also been expressed concerning the systems’ ability to guard against cyber threats. A functional remote e-voting system must fulfil a set of regulatory requirements. This study [27] examined the design criteria for remote e-voting systems as mentioned in the existing literature. The authors investigated whether the current public infrastructure can support an efficient remote e-voting system that fulfils the design criteria. They discovered that the present technological infrastructure is insufficient to enable efficient remote e-voting systems since the technologies that must be installed to meet design criteria are vulnerable to various cyber assaults.
Decentralized e-voting systems make transparency and dependability difficult to ensure. Additionally suspicious are the following: protecting the votes’ privacy, secrecy, and integrity. Blockchain technology has ushered in a new digital age. Blockchain’s immutability and decentralized design make it ideal for e-voting. It ensures election authenticity, integrity, transparency, secrecy, and non-repudiation. This article assessed blockchain’s potential for electronic voting. The authors solved all constraints in the current e-voting system. They created a small-scale e-voting system as a smart contract using solidity language, which includes hosting the election, certifying voters, and counting votes. The study [24] also demonstrated how zero-knowledge proof might aid in developing safe, privacy-preserving E-voting systems.
However, implementing blockchain technology in voting systems causes severe delays in transaction execution. The software solution is only available to a small group of professionals, which does not inspire trust among voters. This study [28] suggests a novel strategy based on freely accessible verification of all means and procedures that may generate doubt about the accuracy of the vote count or the secrecy of their results. Specifically, the authors presented an e-voting system in which an audit of all the hardware and software of a server that conducts operations linked to potential misuse is performed to assure confidence. The mechanism guards against illegal influence on votes via bribery or other forms of pressure. It also monitors all employee operations to control the server’s functioning from its inception until the election’s conclusion. Simultaneously, the number of auditors is not restricted, and the verification method is streamlined by using extra software and hardware. Auditors’ responsibilities include copying and comparing files. All e-voting system solutions, including audits, are easy to grasp and inexpensive.
2.2. Smart Mobility
Smart mobility aims to make transportation systems “smarter.” Smart transportation networks, in particular, can better serve the public by improving the safety, speed, and reliability for local and international accessibility [29]. Information and communication technologies from modern and sustainable transportation systems help consumers plan their schedules and find the cheapest and fastest routes using transportation-oriented mobile applications [30]. Driver’s passports, license recognition systems, car parking searching, and prediction are typical applications in smart mobility facilities [31].
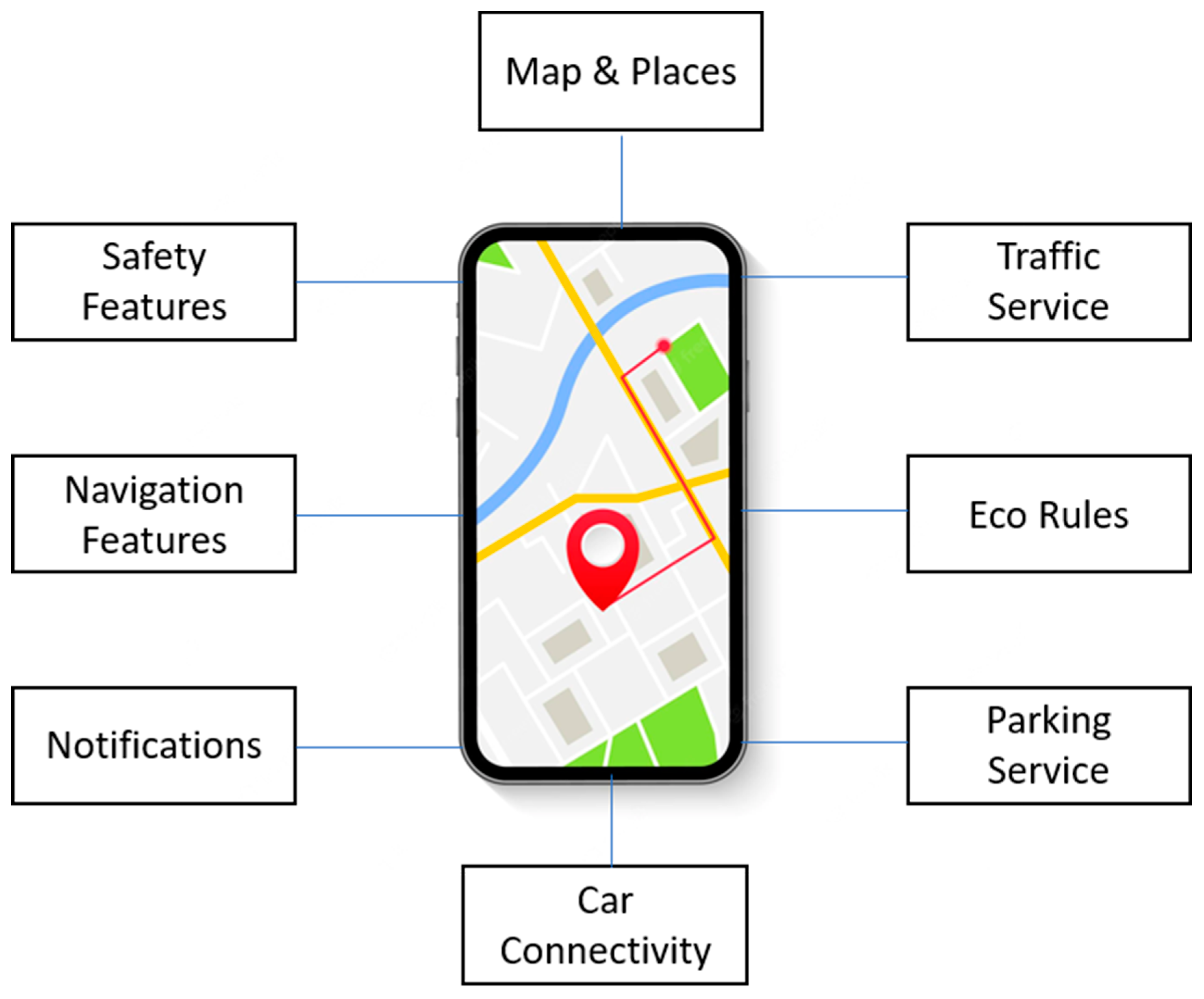
A depiction of a smart mobility platform is presented in Figure 2.
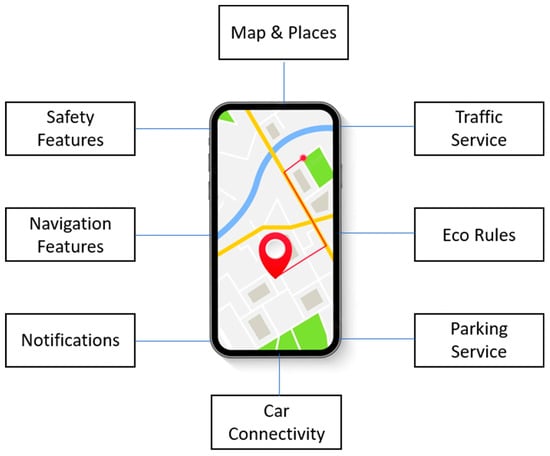
Figure 2.
Smart mobility application.
Traffic safety is a significant concern in crowded cities that harms residents [32]. In this regard, IoT can be more proactive in detecting human errors and reducing traffic accidents. In the literature, for example, particular research gives valuable insights into allowing smart mobility systems. In [33], an IoT-based system was created by combining internet platforms and low-cost antenna technologies. The suggested research in [34] demonstrates the viability of monitoring road safety using developments in IoT. It offers a low-cost IoT framework for assessing the safety of a road network. In addition, Ref. [35] presents an overview of the key IoT technologies suggested for smart mobility in smart city scenarios.
Furthermore, IoT-based solutions must be employed for various applications and modes of transportation, such as smart traffic, parking, and mobility, to create safer and cleaner streets. For instance, in [36], an intelligent transportation system was designed to recognize, locate, track, and monitor buses through exchanging information and communication. This system is based on the IoT, radio frequency identification (RFID), general packet radio services (GPRSs), geographic information system (GIS), and global positioning system (GPS), among other technologies. Another project that is mentioned in [37] aims to construct a prototype for intelligent transportation that makes use of a GPS, near field communication (NFC), and temperature and humidity sensors to monitor automobiles and commuter information and the atmosphere inside buses. The [38] research suggests a real-time traffic-monitoring system to solve the issues associated with traffic management and monitoring. The study used the information gathered from real-time traffic monitoring to determine roadway problems. In addition, Ref. [39] creates an intelligent transportation system application that uses internet-of-things platforms, Intel Edison, and Raspberry Pi. It has been proposed that information on traffic conditions may be distributed via standard instant messaging services, such as WhatsApp.
2.2.1. Cyber Threats or Attacks
As the above research indicates, selecting IoT technology is critical for creating smart mobility systems [40,41]. However, the security provided by IoT devices is not guaranteed. The devices have the propensity to have little computing power, and their hardware restrictions prevent them from having built-in security mechanisms. This makes the devices susceptible to vulnerabilities [42,43,44]. The IoT devices in a smart city’s ecosystem control critical transportation infrastructures, so they need strict secure guarantees. In this point of view, a “Cybersecurity via Determinism” paradigm for the next-generation “Industrial and Tactile Deterministic IoT” is presented in this study [45]. Specifically, in layer 3, there is a new addition of a forwarding sub-layer called deterministic packet switches (D-switches), which are straightforward and safe. This sub-layer supports many deterministic software-defined wide area networks (SD-WANs) in addition to three new tools that may be used to improve online safety: access control, rate control, and isolation control. A software-defined networking (SDN) control plane will set up each D-switch with several deterministic schedules to support D-flows. The control plane of a SDN can insert millions of deterministic virtual private networks (Dvpns) into layer 3. This paradigm has a number of advantages, including the following:
- All congestion, interference, and distributed denial-of-service (DDOS) assaults are eliminated.
- The size of the buffers in D-switches is cut in half.
- Delays in end-to-end IoT communications are brought down significantly.
- The D-switches do not require gigabytes of memory to store large IP routing tables.
- Hardware support is provided in layer 3 for the US NIST Zero Trust Architecture.
- Packets within a DVPN can be entirely encrypted using quantum-safe encryption, which is resistant to attacks by quantum computers using existing quantum algorithms.
- The likelihood of an undiscovered cyberattack against a DVPN may be arbitrarily tiny using lengthy quantum-safe encryption keys.
- Savings can approach thousands of dollars annually via decreased capital, energy, and operating expenses.
Because of this, the attack surface is substantially smaller, meaning there are fewer packets to assault; thus, the danger posed by this attack is significantly decreased. In addition, using encrypted packets for signals eliminates any possibility that a rogue control-plane packet may get past the authorization check [45].
2.2.2. Countermeasures
To provide safety and information-related applications on the road, the vehicular ad hoc network (Vanet) has recently received considerable attention in the smart transportation domain. Vanet delivers an infrastructure where vehicles moving on the road can use communications to report traffic congestion, accidents, and road surface conditions to other cars. Although Vanet is an excellent cyber–physical system [46], it has several security and privacy problems, particularly location privacy. To be applied, they must enhance the Vanets applications to preserve the identity and location privacy of cars. However, since a hostile vehicle cannot be followed using a complete privacy-preservation strategy in a cyber security scenario, most users would expect a conditional privacy-preservation approach to safeguarding systems. Group signatures may be used to provide conditional privacy preservation. However, the calculation costs are relatively high. Unlikable pseudo-ID techniques may also produce dependent privacy preservation. However, revoking a malicious vehicle would result in a lengthy revocation list. Unfortunately, any proposed method for verified cater evocation does not enable forward unlikability. Forward unlikability is a challenging criterion for Vanet systems. If a car is hacked and turns malevolent, the vehicle’s license should be cancelled immediately. However, the vehicle’s previous communications and positions (from before it was hacked) should be safeguarded and unlikable. To address these issues, the authors of this research study [47] provide a lightweight conditional privacy-preservation system that leverages basic hash-chain algorithms to allow accurate identity monitoring by a trusted authority and quick local revocation verification on the road. In Vanet systems, the suggested protocol addresses location privacy, conditional privacy preservation, and forward unlikability.
In addition, novel security techniques are presented in this study [48] to enable safe certificate revocation, which is regarded as one of the most demanding design challenges in Vanet networks. Each vehicle that receives a message from another vehicle verifies the sender’s certificate. The recipient verifies the sender’s certificate. When a sender’s certificate is invalid, the recipient ignores the message. If the sender lacks credentials, the receiver will report him to the road side unit and review the message. If the information is correct, the road side unit (RSU) will issue a valid certificate. The road side unit will issue an invalid certificate and add the vehicle to the revocation list otherwise. The RSU replaces a misbehaving car’s valid certificate with an invalid certificate to indicate it should be avoided. Multiple vehicles report to the road side unit that a car has a valid certificate and is broadcasting incorrect data.
This research paper [49] presents a catalogue of potential solutions, each of which, if put into practice, can dramatically cut the risk of cyberattacks on the communication systems of connected cars in a vanet infrastructure. Five degrees of security architectures may be chosen from the defense options that users can apply. However, cyber attackers have a large terrain of assaults and objectives, and the variations between innocuous and damaging are recorded in terms of the number of people killed and the amount of damage done to transportation infrastructure.
Cryptography, zero-knowledge between communication vehicles, and authentication methods with or without a trusted third party are all necessary breakthroughs; in reality, they are inadequate [50,51,52], especially today, when more and more automated vehicles are being put onto the roads, which need to cohabit with other types of motorized and non-motorized traffic participants efficiently and safely. Autonomous cars do, however, run the risk of traditional cyberattacks on the information and operation of the vehicle, as well as a new breed of attacks surrounding things, such as ransomware, IoT attacks, and DDoS attacks (connected vehicles drafted into Botnet Armies). Because of their interconnected nature, security risks are associated with the networks to which they are connected. This is true regardless of the financial networks that process payments, roadside sensor networks, electricity infrastructure, or traffic control features. The authors of this paper [53] propose a method for designing safe and secure mixed traffic systems, including automated vehicles and non-automated road users, such as pedestrians, bicyclists, and conventional vehicles. This will allow the authors to model safe and secure cooperating automated vehicles and road infrastructure. In addition, this method will enable the design of safer and more secure automated vehicles and road infrastructure. The applicability of the suggested approach is shown with the help of a typical scenario involving the interaction of an automated vehicle with pedestrians at an intersection that does not have traffic signals.
The development of connected vehicles, which produce dynamic data through wireless communications, has made it possible to automate vehicles to operate more effectively. This is especially true in traffic signal control, which serves as the structural foundation for the scheduling of traffic flow. On the other hand, wireless communication channels are susceptible to cyberattacks and may constitute a significant risk to dynamic traffic signal control systems. Attackers might manipulate the usual traffic flow to bring up extreme traffic congestion. The authors of this work use deep reinforcement learning to create an intelligent Sybil attack on a traffic intersection. In this attack, connected vehicles with fake identities are optimally placed to change traffic signal timings by corrupting traffic data. This work aims to highlight and exploit existing vulnerabilities in traffic signal control systems. The findings indicate that this attack causes a sizeable increase in the time it takes for vehicles to complete their journeys and results in catastrophic traffic congestion, mainly if carried out for an extended period. This will lead to several serious issues, including increased fuel consumption and air pollution in cities with a high population density. In the face of such sophisticated assaults, the design assumptions behind present traffic signal control systems have become increasingly suspect [54].
The authors of this research paper [55] establish an assessment methodology for cyber attacks on autonomous cars using preexisting traffic flow models as the basis for their work. They consider the percentage of cyber-attacked cars, the intensity and range of cyber attacks, and transportation demand. Efficiency, safety, emissions, and fuel consumption are used to evaluate the transportation system’s performance. Simulations show that as the number of cyber-attacked vehicles and the severity of attacks increase, the negative impact on traffic flow grows. This reduces capacity and increases rear-end collision risk, air pollution, fuel consumption, etc. Cyberattacks on location rather than speed may cause accidents and reduce traffic efficiency. Position-attacked traffic systems consume more energy and produce more pollution. This research can be used to project future cyberattack traffic, evaluate transportation systems, and manage automated highway systems from a network security perspective.
However, as is easily understood, the big problem in smart mobility is the cyber issues of mass transportation in which many people are carried within a single vehicle. Specifically, the most serious difficulty is the cyber security of public transit [56,57]. Trains, for example, are the most often used mode of transportation in a modern city, with millions of daily passengers, as opposed to car transportation. Because of system and infrastructure digitalization, the automation of railway processes, mass transit concerns, and expanding linkages with external and multimodal systems, the railway industry is experiencing a significant change in its operations, procedures, and infrastructure. Cybercriminals may target ticket vending machines, passenger information screens, and the Wi-Fi infrastructure. These systems are becoming more vulnerable to cyber attacks as they transition from bespoke stand-alone systems to open-platform, standardized equipment built with commercial off-the-shelf components and increased use of networked control and automation systems accessible remotely via public and private networks. Many signals transmitted and received over insecure communication links are critical to railway operations. Constant monitoring, immediate notice of any departure from ordinary circumstances, and decisive measures to resolve the issue allow for effective risk reduction and business continuity. Furthermore, uninterrupted and safe traffic operation depends on recognizing and addressing threats to telecom, train management, and signaling systems as soon as possible. Complete visibility and the capacity to identify and mitigate hazards as they emerge give a route to reducing uncertainty and operational interruptions [58,59].
Though various studies on critical infrastructures have been conducted from the aspect of cyber security, there has been little research conducted from the standpoint of cyber–physical security in application areas such as the railway infrastructure. This is the first complete empirical evaluation of the cyber–physical vulnerability of communication-based train control systems [60]. The writers carefully analyze communication-based train control and the cyber–physical vulnerabilities that may seize control of the train. They discover that a man-in-the-middle assault combined with knowledge of railroad signaling may result in substantial train crashes. They propose a countermeasure for communication-based train control resilience to overcome the issue and meet these difficulties. The primary idea behind this countermeasure design is to create a subsystem with a host that the attacker cannot reach. The cable links the subsystem to the SDN switch. The SDN controller, on the other hand, logically disconnects the link between the SDN switch and the subsystem. The subsystem stays undiscovered due to the logical separation while the attacker seeks victims.
Consequently, during a man-in-the-middle attack, the subsystem may go undiscovered. For the subsystem to warn the automated railway protection system of the attack scenario, the SDN switch should detect ARP spoofing. The SDN switch continuously monitors ARP messages and creates an IP-MAC list for ARP messages across the structure’s SDN switches. They validate their findings by developing a realistic communication-based train control testbed environment that yields promising outcomes.
In addition, this research [61] looks at the security of railway control equipment against cyber or physical attacks. The authors offer a cyber–physical authentication approach that combines an add-on security module with a cyber security protocol for device authentication and data transmission. A ‘hot swappable’ bump-in-the-wire security module adds cryptographic capabilities to current control devices. The suggested system offered tamper resistance by encapsulating the hardware in a tampered-detection box and using tamper-resistant hardware to secure the cryptographic key. The device authentication protocol secures server-to-control-device communication. Setup, first handshake, acknowledgement/critical exchange, and data transmission make up the protocol. Due to storage needs, the first handshake used RSA signatures, and the data transmission phase used AES with a 256-bit session key. Tests show that overall overhead has a minor impact on the railway’s control device.
The authors offer a set of actions for enhancing cyber security and the information power of railway management systems, with the instruments of risk engineering and the knowledge gained from the information technologies serving as the foundation for their recommendations. The criteria for the railway management system are outlined in detail in work [56], which also provides a summary of the requirements that must be met for the smart city concept. Additionally, in this paper [62], the authors provide the bases for a combined safety and security risk assessment and analysis approach. This approach reconciles the risk analysis processes used in both safety and security by making relevant connections at different stages of the two methods and by adding cross-cutting steps common to both safety and cybersecurity.
2.3. Smart Environment
A smart environment can make a significant contribution to the development of a sustainable society. The smart environment combines appealing natural conditions, such as climate, green spaces, and so on, with techniques for limited contamination, optimal resource management, and environmental actions. It is also related to access to services that improve the city’s quality of life and the facilities of public spaces on a broader scale. In addition, it is associated with the city’s cleanliness, the initiatives that give life and movement, and strengthening security in areas, such as local forests, lakes, etc. [63].
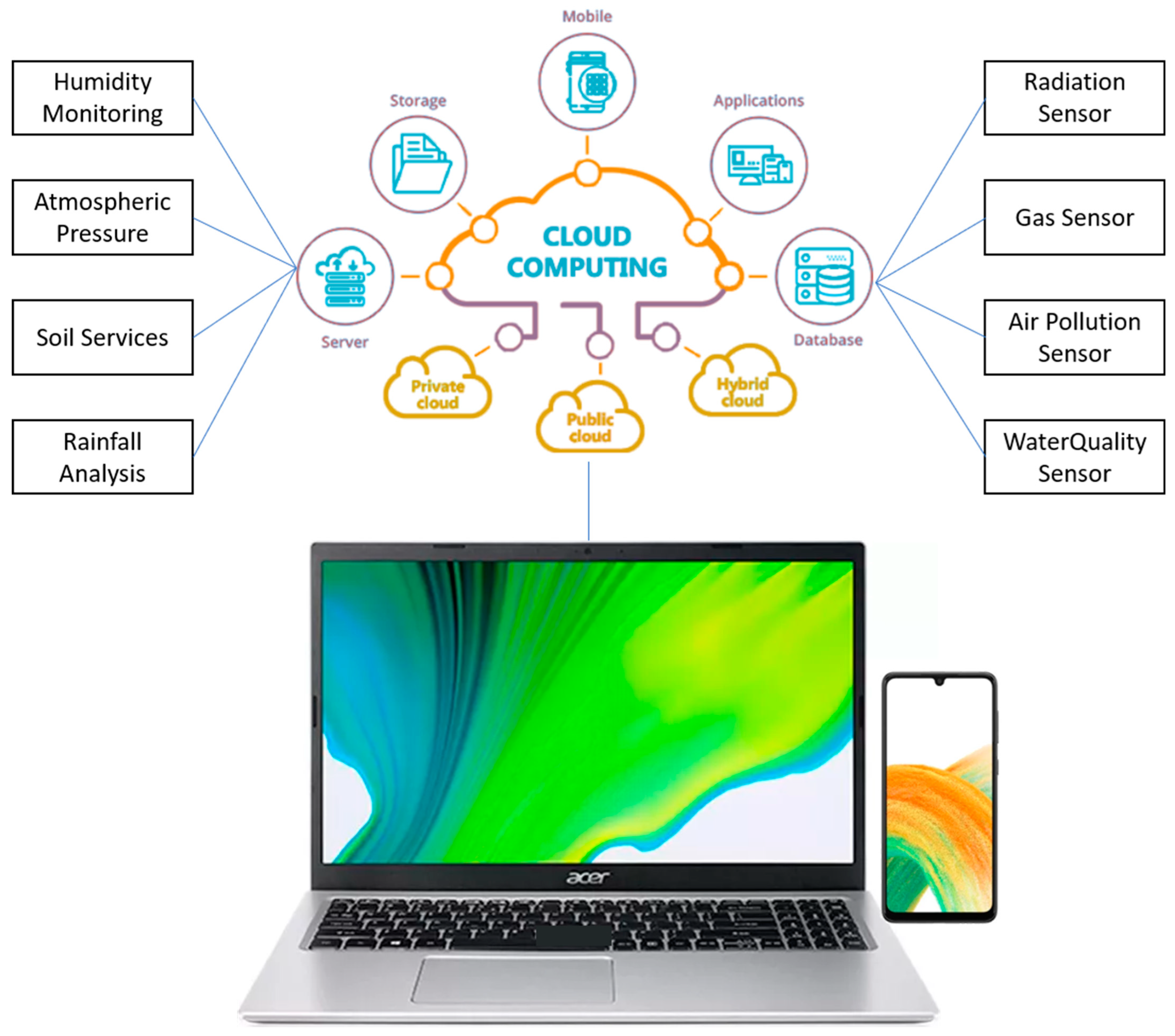
A depiction of a smart environment monitoring application is presented in Figure 3.
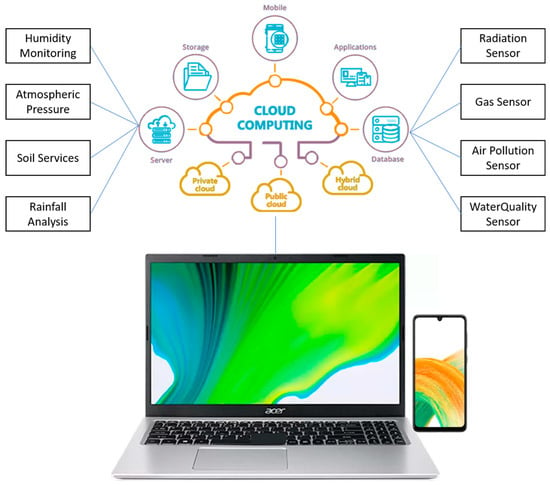
Figure 3.
Smart environment monitoring application [64].
A smart city can monitor energy consumption, air quality, building structural reliability, and traffic congestion and address pollution or waste using technical management tools. Thus, the sustainable and smart city considers using and producing green and renewable energies, more sustainable food production techniques, or the application of innovative technology to improve resource management (fuel, air, water, waste, etc.). Novel environmental wireless sensor networks (WSNs) have the potential to monitor the natural environment and potentially anticipate and detect natural disasters [65,66].
2.3.1. Cyber Threats or Attacks
WSNs are networks of autonomous sensing devices that monitor physical or environmental factors such as temperature, pressure, sound, vibration, motion, or pollution at several places. WSNs are multi-hop ad hoc self-organizing networks in which all nodes interact wirelessly and use multiple routing protocols [67]. It works under circumstances of limited bandwidth and performance. It is scalable and may accept more nodes or devices at any moment. It is also adaptable, allowing for physical divisions, and all nodes may be accessible through a centralized monitoring system [68]. Because it is wireless, it may be used on a big scale and in various environmental applications or sectors. Furthermore, it employs multiple security methods based on the underlying wireless technology, resulting in a dependable network for specific users [69].
Smart cities can save energy and reduce carbon issues using WSNs. Specifically, it can collect environmental factors through many wireless sensors and then return the information to the backend monitoring server. This study [70] presents a WSN using ecological sensors and controllers to adjust the energy consumption of electrical appliances. Because a plethora of wireless nodes are exposed to physical or logical access in remote urban areas, the authors performed a massive simulation of DoS attacks or external damage by human manipulations. The authors used a sophisticated analysis of various packet loss patterns to identify the potential damage and examine the abnormality. After identifying damage by the logical or physical attack, each node is used by the different queue management models to collect environmental data.
It is difficult to approach or work at the WSN since it operates in a complicated setting. Because nodes are open, they are susceptible to numerous assaults. Traditional security systems will also mistake nodes deployed in a complex environment with poor-quality connections or poorer conditions (less energy or a higher workload) for malicious nodes. In WSN, the trust and reputation model may be employed to mitigate the harm caused by malicious nodes. However, trust and reputation models have a sizeable false-positive rate since a node with less reputation is evaluated as undesirable owing to the communication context. This study [71] provides trust and reputation-based harmful node detection techniques with environmental factors to prevent malicious nodes from interfering with or selectively forwarding attack nodes. Machine learning’s linear regression and combining node energy, data volume, number of nearby nodes, node sparsity, and other deterministic characteristics can solve environmental parameters. Using environmental parameters, benchmark trust is estimated. The Gaussian radial basis function is simplified to compare the benchmark and cycle reputation sequences. Environmental settings provide three reputation intervals and an adoption threshold span to detect malicious nodes based on work environment and node statuses. The simulations show that factors increase malicious node detection by 1% and reduce false positives by 1%.
To communicate outside of the wireless communication zone, WSN employs mobile nodes. Wireless ad hoc network routing protocol attacks degrade network performance and dependability. Malicious nodes advertise the shortest route between source and destination in active black hole attacks on wireless networks, resulting in routing table alterations and packet loss. Self-security management is a hot topic in WSN-related environmental applications. For example, this paper [72] provides the grouped black hole attack security model (GBHASM), which prevents grouped hostile nodes from advertising the shortest route between source and destination, preventing routing table alterations and packet loss. The GBHASM proposed is separated into two components. The first module describes how a new node will join the network, while the second handles communication.
The joining request is received from the new joining node in the replay. It sends membership acknowledgement and waits for replication approval. If the request is not accepted within a specific time frame, it will be rejected; if approved, the demand for its details will be delivered. The same procedures will be repeated till the process is completed. Information received from a new joining node is recorded in the database, given a new node code, and the updated node code table is propagated on the network. The second model deals with network communication activities. After joining the network, the node sends out queries for the quickest network route. Every node will compare the node code, and if the key matches within a specific time frame, information about the packet will be revealed. Otherwise, the time-to-live package will be sent to the next node.
2.3.2. Countermeasures
Although prevention and monitoring techniques may lower the risk of cyber assaults, the residual risk in vital infrastructures or services might still be unacceptable. Resilience, or a system’s capacity to survive evil occurrences while retaining adequate operation, is a crucial attribute of such systems. While numerous resilience indicators have previously been proposed, there are limited experimental data on the cyber security of CPSs. This study [73] aims to provide a model-free, quantitative, and general-purpose assessment approach for extracting resilience indices from data sources such as system logs and process logs. The authors evaluate four resilience indices from a broad range using an actual wastewater treatment plant model and modeling assaults that interfere with a vital feedback control loop. The findings reveal that although the selected indexes varied in their behavior and susceptibility to certain assaults, they can all summarize and extract valuable information from large system logs. The proposed method includes deriving performance indicators from observable data without understanding the system dynamics.
Waste management and recycling are critical to remaining sustainable and clean in contemporary metropolitan settings. Solid waste management, disposal, and recycling are all difficulties in many major cities across the globe. Combining IoTs with deep learning provides a modular approach for data classification and real-time analysis. This article [74] depicts an effective smart waste management and classification system based on IoT and deep learning. The study proposes a microchip-based trash can with a fast waste collection system. IoT provides real-time data control in the recommended data-monitoring system. Smart trash management and categorization include a convolutional neural-network-based algorithm. This waste-collection facility will use trash classification to increase recycling. This system offers waste collection, management, and categorization.
Modern technologies enable water distribution systems (WDSs) to provide improved water supply, storage, distribution, and recycling services. They help with real-time monitoring, automation, and management. However, the limitations of these technologies expose the WDS to cyber–physical threats. The primary aim of cyber–physical assaults is to interrupt regular operations and tamper with crucial data, negatively influencing the WDS. As a result, it is critical to design and deploys solutions to improve WDS security by detecting and mitigating cyber–physical assaults. The authors of this research [75] thoroughly investigate typical cyber–physical assaults and common detection strategies for the WDS. They contrast assaults and detection approaches, focusing on concepts, methodologies, evaluation findings, benefits, limits, etc.
The increasing number of successful and attempted attacks on critical infrastructures, such as power grids and water treatment plants, has resulted in an urgent need to develop and implement methods for detecting such attacks, which state actors or insiders in the targeted organization frequently carry out. This research [76] aims to provide a case study of an infected wastewater treatment plant (WTP) that used a live memory dump acquisition Imager. The forensic carving procedure is removed in bulk, and features are extracted from the memory dump. In addition, this study [77] emphasizes one method to identify assaults that compromise one or more actuators and sensors in a plant by successfully infiltrating the plant’s communication network or accessing the plant computers directly. This technique, known as distributed attack detection (DAD), may detect assaults in real time by spotting irregularities in the behavior of the physical process in the plant. The use of monitors that are actual implementations of the invariants obtained from the plant architecture is how anomalies are discovered. Each invariant must remain valid during the whole plant operation or while the plant is in a specific condition. A functioning water treatment facility was used in an experiment to evaluate the efficiency of DAD, and it was proven to be successful at detecting sneaky and coordinated assaults. Additionally, this study [78] aims to provide a technique for enhancing operational security in a wastewater treatment plant and to demonstrate how this approach can be used in a particular setting.
The motivation stems from the requirement to comprehensively understand security events or attacks on a network and information about the intensity and propagation pattern. In parallel, this study [73] suggests a cyber-security monitoring system that connects time-series event data, visually [74] depicting security occurrences. It provides a predictive prediction of probable circumstances based on established situations. Furthermore, it may assist business choices by identifying or comprehending the link between computer equipment and their business/information technology services.
In recent years, the smart energy grid has steadily become the usual development trend in the world’s power business. It is an improvement to the old system that incorporates technology and communication into the present grid. This results in a more efficient grid that decreases energy demand peaks and can efficiently integrate renewable resources (at naturally varying levels) into its network. To increase their security, smart grids have included physical control, data encryption, and authentication technologies. However, there is still a shortage of timely and efficient detection tools to keep the grid safe from unwanted breaches. In response to this issue, a machine-learning-based methodology for detecting smart grid DoS assaults was developed in this study [79]. The model initially gathers network data, picks features, uses principal component analysis (PCA) to reduce data dimensionality, and then employs the support vector machine (SVM) algorithm to identify abnormalities. The study exploits the attack vulnerabilities of smart meters and data servers to add data collection and intrusion detection modules between smart meters and data servers, aiming at the design structure of the smart grid. In the smart grid, real-time data capture and detection are possible. When DoS attack activity is recognized, the alarm system is initiated to handle the alert.
Cyber security must be a primary priority for electric power providers installing smart meters and smart grid technologies. Despite the well-known benefits of smart meters, how and to what degree cyber assaults might disrupt smart meter functioning and remote data collecting about power use from client locations is unclear. To answer these issues, this study [80] tested a commercial-grade smart meter in a controlled lab and assessed its operational integrity under cyber-attack situations. In addition, the false data injection attack (FDIA) is a way of disrupting the security of the power system based on meter measurement. FDIA detection researchers are now focused on detecting its existence. FDIA location information is also critical for power system security. Finally, in this study [81], identifying the meter’s FDIA is seen as a multi-label classification task. Each label denotes the current condition of the respective meter. The multi-label decision tree approach is used as the classifier in the ensemble model to discover the precise position of the FDIA. This approach does not need power topology information or statistical knowledge assumptions. The suggested method’s performance is validated by numerical tests using the IEEE-14 bus system.
2.4. Smart Lining
Smart living is intended to optimize and manage facilities. It emphasizes one of the primary goals of the sustainable and smart territory, which is to enhance the quality of life of its residents. The smart living axis is built on three key pillars: civic safety, social cohesion, and tourist attraction.
It is a solution that maximizes the city’s infrastructure while improving people’s quality of life. It allows for real-time control, forecasting, and optimal asset optimization and management. The following are some smart living applications [82]:
- Detectors of fire: It is feasible to monitor, detect, and prevent fires in the urban environment with this 24/7 program. Furthermore, the detection may approach the various sources of fire efficiently to manage the fire more effectively.
- Intelligent video surveillance: to improve public safety and to use predictive analytics to optimize traffic flow and citizen safety.
- Sports facility management: Smart living solutions include controlling capacity and performing centralized administration of sports facilities. It is also beneficial for making judgments based on historical data, identifying deficiencies or requirements, and implementing management and infrastructure upgrades.
- Smart home automation: It monitors and regulates home smart applications such as temperature, humidity, electric equipment, security, and so on in real-time.
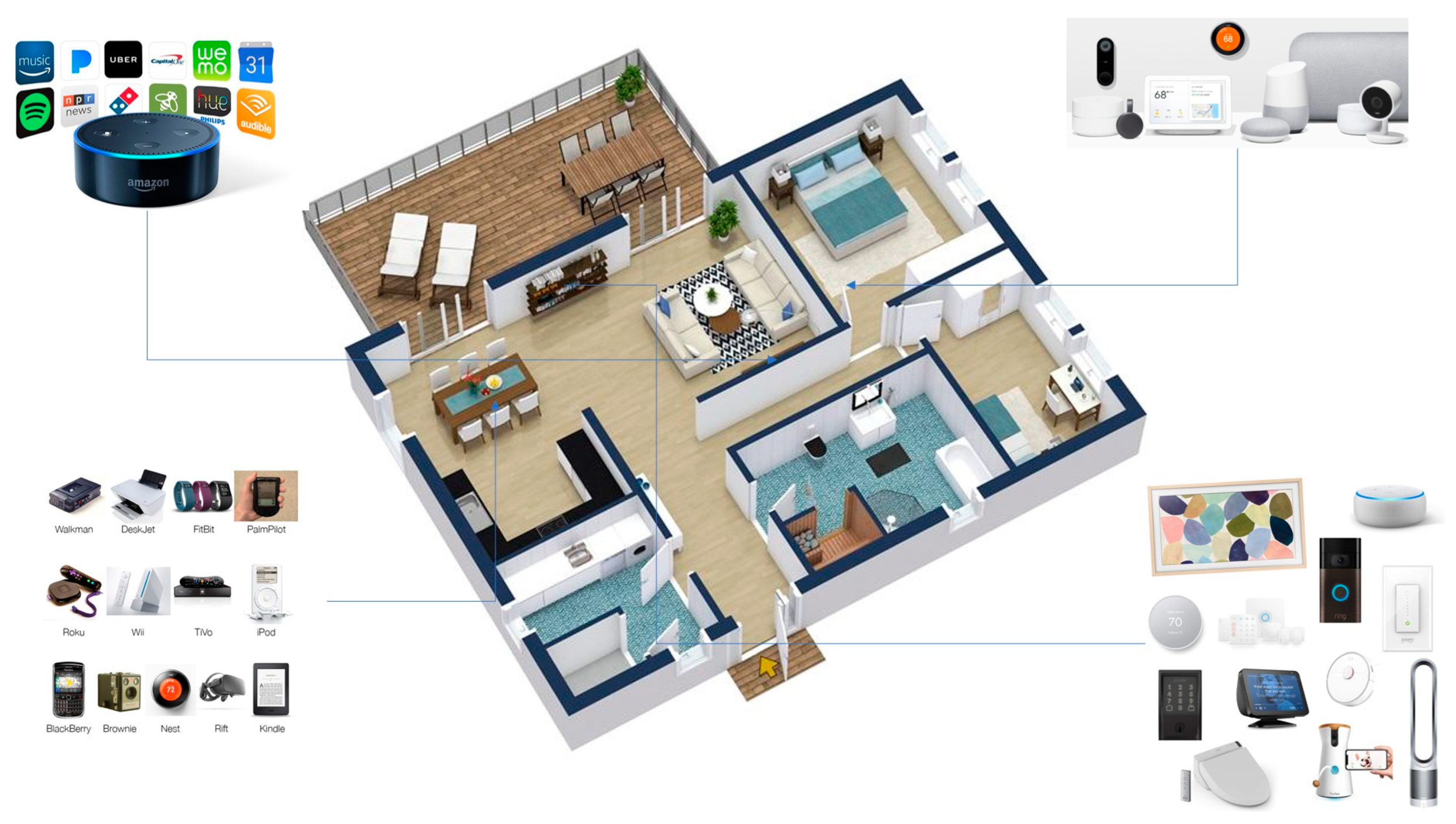
Smart living ICT utilities allow operations to decrease resource overconsumption, such as water and gas while increasing economic development and environmental protection. A depiction of a smart living scenatio is presented in Figure 4.
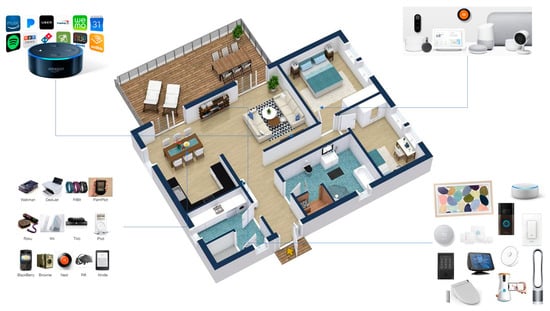
Figure 4.
Smart living Scenario.
2.4.1. Cyber Threats or Attacks
The linked smart house poses a variety of security risks. To begin with, individual smart living gadgets may not be secure. Some IoT home devices are hurried to market, and their security may be compromised. In certain circumstances, user manuals fail to address privacy issues or provide sufficient information to ensure the device’s security. Baby monitors and security cameras, for example, have been hacked, enabling hackers to view inside a home [83].
Intruders may access any data stored on an insecure home network. An intruder may monitor device use to determine when users are away. IoT data are at risk if the main internet account controls the home network. Any flaw could expose email, social media, and bank account information. Insecure IoT devices must not compromise the home network’s security. Many customers control their smart homes via smartphone, making it a valuable database for hackers [84].
As follows from the above, it is critical to describe and comprehend the direction and development required to guarantee that, as smart home systems become more prevalent, the security and functionality of these systems are maintained. Form this spirit, the goal of this study [85] is to identify the hazards associated with smart home systems and research ways to reduce such risks. Additionally, it provides a comprehensive analysis of the techniques currently used by intruders, the reasons for adopting these methods, and what might be done differently to enhance smart home security. This paper [86] also presents and discusses the threats that can affect smart living systems and define the requirement to improve secure communication between smart home devices and applications that remotely control the home devices.
Vulnerabilities in IoT-based systems provide security risks and obstacles for smart applications. One of the most significant impediments to IoT-based systems was identified by the low-level security provided. The smart home environment presents novel security, authentication, access control, and privacy concerns due to its internet-connected, dynamic, and diverse nature. The IoT-based smart environment requires an attack model and a risk management framework to improve information security and integrity. This research [87] provides a finite state automata-based attack model for investigating smart home-based security assaults and assessing their effect using the suggested risk management framework for mitigating IoT smart-home-related attacks. An examination of the typical attack behavior and the risk-management framework demonstrates that the proposed approach is feasible and effective and can be used in many smart home applications.
IoT implementation in the smart home sector is complicated since the devices utilized in such platforms vary in size and computing capacity. The capacity to impose security on such machines depends on how well the authentication procedures are carried out. Against this backdrop, this paper [88] is designed to thoroughly examine possible authentication risks and attacks on IoT, specifically in the smart home sector. The significant concepts offered in this study on potential authentication risks and assaults on IoT in Smart home applications are primarily influenced by a careful literature assessment of relevant work in IoT.
2.4.2. Countermeasures
This research looked at the system architecture of a smart home ecosystem, vulnerabilities, potential assaults, requirements, and post-attack settings [89]. We propose an architecture analysis and design language tool model for the smart home architecture, which is then visualized using a complex graph tool against a security policy. The attack graph highlights the need to address security considerations while creating smart home systems and identifying potential threat landscapes.
This article [86] presents the design and implementation of a safe framework that provides flexibility and security for smart home systems based on CPS and IoT based on the notion that the primary goal of home automation is to control home devices from a single place. As a result, the authors suggest a safe design that protects the system from external internet infections. They address home automation security concerns by installing a secure firewall software solution. A secure firewall identifies and warns the user of specific security vulnerabilities before launching its mitigation technique. Internal security additionally offers encryption for communication and protects the home automation system from unethical acts. This technology (cypher firewall) determines the user privacy problem since it does not allow external threats. Users may monitor smart home activity by attaching static IP addresses to the system. Users may connect to a home coordinator already tied to home automation through cellular internet. Users may turn on/off their TV, door, lights, heat radiator, air conditioning, and water appliances using their connection.
The comparatively inadequate information security of smart home system (SHS) devices may jeopardize consumers’ privacy. The authors of this paper [90] propose a novel block data structure based on homomorphic encryption to record the SHS device information transaction. This study presents a homomorphic consortium blockchain for SHS-Sensitive Data Privacy (HCB-SDPP). To validate SHS operational nodes and transactions, the authors add verification nodes. Using HCB-SDPP, they create a Par-lier-based algorithm for privacy protection. To validate the HCB-SDPP architecture, they encrypt gateway peer data and submit them to the consortium blockchain. They assess data security after homomorphic encryption. The authors target various peers on the consortium blockchain in the experiment using HCB-SDPP. If these nodes are vulnerable, the model is affected. The simulation results suggest that HCB-SDPP protects client privacy better than SHS.
Wireless home alarm systems are becoming more popular, but their security has received little attention. Existing attacks on wireless home alarm systems use networking protocol flaws while ignoring issues caused by the physical components of IoT devices. The authors of this study [91] demonstrate novel event-elimination and event-spoofing attacks against commercial wireless home alarm systems by interfering with the reed switch in practically all COTS alarm sensors in this research. In both assaults, the external adversary controls the state of the reed switch with his magnet to either delete valid alerts or spoof false warnings. The authors also demonstrate a novel battery-depletion assault using programmed electromagnets to quickly and quietly drain the alarm sensor’s battery, intended to last a few years. Extensive tests on a sample ring alarm system indicate the effectiveness of these assaults.
On the other hand, several inspired smart living applications fulfil privacy and security standards [83]. The primary purpose of this proposed project is to use new IoT technologies to enable the senior population to self-manage their health and remain active, healthy, and independent for as long as feasible in a smart and safe living environment. An open-source, comprehensive IoT ecosystem is proposed. It includes the following processes: data gathering, data transportation, data integration, processing, manipulation, computing, visualization, data intelligence and exploitation, data sharing, and data storage. This unique cloud-based IoT ecosystem serves as a one-stop-shop for integrated smart IoT-enabled services to assist elderly persons (65 and older) who live alone at home (or in care homes). Another breakthrough is this system’s design and implementation of an integrated IoT gateway for wellness wearable and home automation system sensors with diverse connection protocols. The smart living system and services address smart health and care, smart quality of life, and the social community. The system is developed using the user-centered design process to enable active user interaction throughout the project lifecycle and relevant standards and compliances (e.g., security, trust, and privacy) that are followed to increase user-friendly adoption.
Access-control rules in smart buildings are becoming more dependent on context, such as who is taking action, if there is an emergency, or whether an adult is around. The extensive literature on context sensing might be used to provide contextual access control, but it mostly overlooks threats, adversaries, and privacy. The authors of this work [92] reassess the literature on home context sensing from the standpoints of security and confidentiality. They describe a unique threat model in smart homes focusing on non-technical adversaries’ capabilities. In this model, replay, mimicry, and shoulder-surfing assaults are significantly more common. They also synthesize circumstances pertinent to home access control, matching them to existing sensors. They then organize the sensing literature to provide a decision framework for home context sensing that considers security, privacy, and usability. Using their approach, they discover that present sensors do not adequately reduce potential hazards in houses. Some sensors are vulnerable to primary threats, such as physical denial-of-service attacks, making it simple to circumvent restrictions based on the lack of a characteristic. Many sensors capture more data than necessary and are useless for all user groups or scenarios.
Simultaneous advances in the internet of things and machine learning have resulted in exciting multidisciplinary applications, such as classification tasks based on data provided by smart devices for different applications, such as resource allocation, security, and activity categorization. However, such applications may be vulnerable to adversarial scenarios. The authors of this research [93] create a white-box adversarial attack technique to produce adversarial instances for data acquired from smart meters placed in residential homes and show that their statistical features are indistinguishable from actual data points. Adversarial machine learning, a method that uses false data to trick algorithms, is a developing danger in AI and machine learning research. The most typical reason is to cause a machine-learning model to malfunction [94]. An adversarial attack might include training a model with erroneous or misleading data or injecting deliberately crafted data to confuse an already trained model. The attack technique focuses primarily on deep learning-based models used in smart home device categorization. Because the adversarial data points are statistically indistinguishable from the actual data points, non-machine-learning-based solutions may be unable to address the issue given by hostile instances. The suggested strategies’ efficacy is proved using the publicly accessible United Kingdom-Domestic Appliance-Level Electricity smart-meter dataset.
2.5. Smart Healthcare
Quality, results, and value are the outcomes of technological advancement in the health industry. Patients need excellent and personalized services [95,96]. Thus, it is critical to invest in this area. Digital healthcare is a movement that entails leveraging new technology to increase support while keeping costs as low as feasible [97,98].
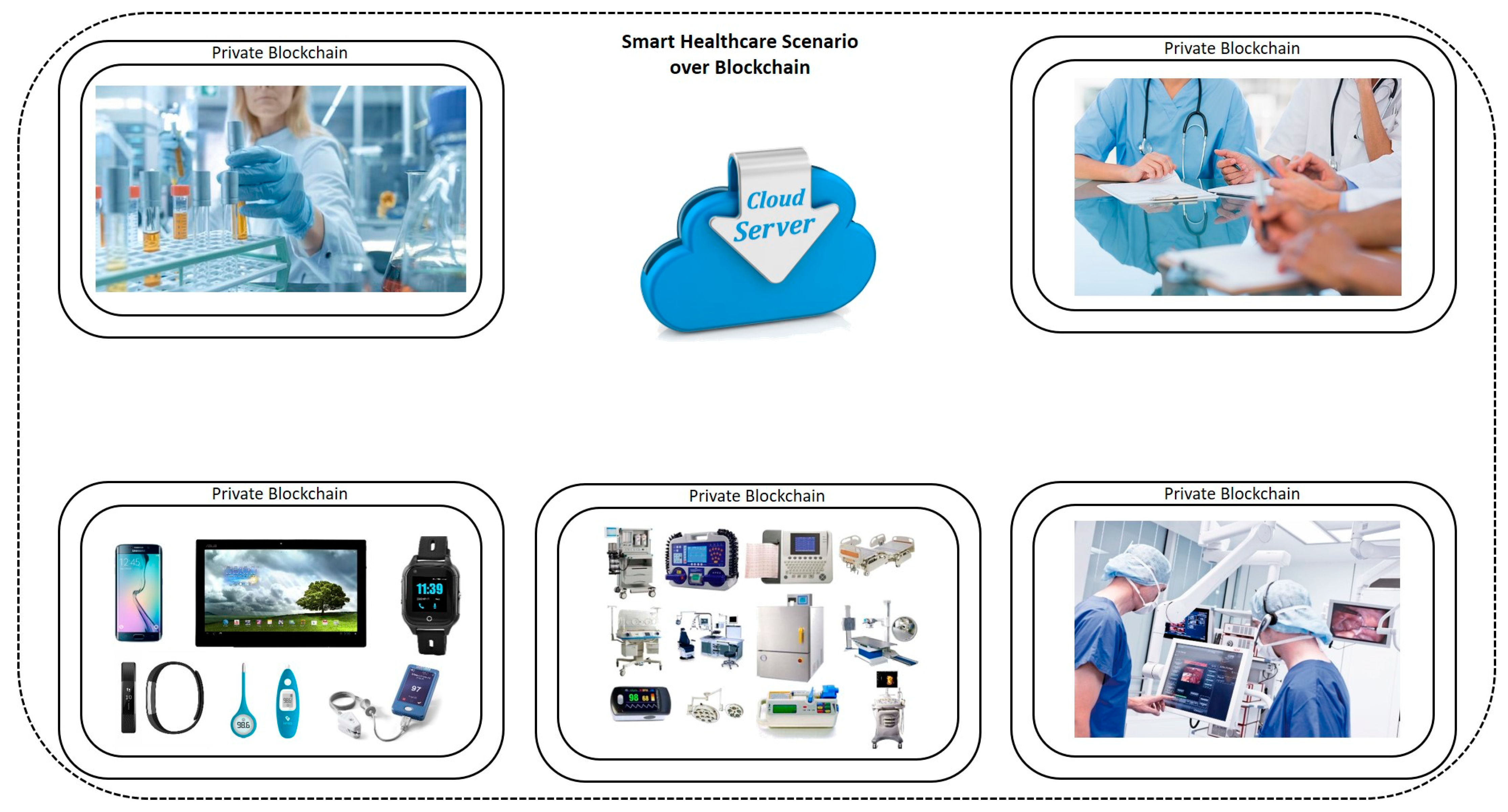
A depiction of a smart healthcare scenario over blockchain is presented in Figure 5.

Figure 5.
Smart healthcare scenario over blockchain.
Smart healthcare entails the adoption of new goods and technology for diagnosis and treatment, a more considerable interchange of information across parties, a more active role for patients during treatment, and improved clinical data management [99,100]. Human and non-human players in smart healthcare include physicians, patients, hospitals, and research organizations. Smart healthcare strives to make patient care safer, better, and more manageable. IoT connection is transforming healthcare by linking patients and healthcare professionals in novel ways [101]. Wearables, skin sensors, home-monitoring tools, and other IoT-connected gadgets allow deeper medical insights into symptoms and health patterns, new degrees of remote care, and more control over patients’ care and treatment. Like those used in other IoT-connected applications, sensors are critical in gathering and analyzing real-time patient data. Artificial intelligence (AI), the IoT, the medical internet of things (MIoT), edge computing, cloud computing, big data, and next-generation wireless communication technology are at their heart [102]. This allows healthcare practitioners to spend more time with patients and treating diseases and less on logistics.
2.5.1. Cyber Threats or Attacks
Smart health is an important field that continually analyzes patients’ health, alternative treatments, and cutting-edge disease-fighting technology. The purpose of smart health is to provide individuals with medical services at any time and from any place. Smart health monitoring devices are often connected through wireless networks, which are vulnerable to cyber threats. However, various risks may endanger these health monitoring applications and systems [103,104]. These include denial-of-service (DoS) attacks, fingerprint and timing-based eavesdropping, router attacks, select and forwarding attacks, sensor attacks, and replay attacks [105,106]. In this paper [107], the authors investigate the consequences of these attacks on health monitoring systems and recommend some interventions based on their research findings.
The most challenging aspect of smart health apps is protecting data from numerous assaults while using simple approaches and algorithms. Given the security problems associated with implementing smart health apps as the primary data collecting and transmission source, cyber threats are categorized to create a viable defense strategy. This research [5] contributes to the analysis of security and privacy in the context of smart cities for healthcare applications in two ways. On the one hand, an overview of several IoT applications and their cyber vulnerabilities is provided. On the other hand, a complete assessment of potential solutions to the issue of cyber assaults is given.
In recent years, smart healthcare has gained popularity. Because of the data it collects, a more secure mechanism is required to maintain security and privacy. As a result, these techniques may also guarantee security and privacy in smart health. This review paper aims to assess individuals’ concerns with security issues in their smart homes and to start a debate about how healthcare equipment that comes packaged with future houses is susceptible to cyber attacks that result in data breaches. Blockchain is proposed in this study [108] to increase security and privacy in smart healthcare. The proposed platform uses blockchain technology and considers the client’s control over the healthcare data, implying the ability to share data with a specific association or person on a case-to-case and field basis. Using this platform, the writers discussed emerging blockchain technology and how its components may help healthcare flourish while maintaining total security.
Humans benefit from the fast progress of the MIoT connected with biosensors in various ways, including smart healthcare systems (SHeSs). The combination of MIoT devices and the increasingly networked nature of the healthcare environment enables healthcare providers to provide more efficient and effective emergency and preventative medical services to their patients. SHeS offers several chances for healthcare professionals and institutions to monitor patients’ health remotely. The health statistics acquired by SHeS are kind. However, SHeS exposes patients’ health data to various assaults.
2.5.2. Countermeasures
The most complicated difficulties in smart healthcare systems are ensuring patient health data confidentiality and privacy. This paper [109] explores health data confidentiality, MIoT healthcare security concerns, and the rules and regulations involved in establishing a smart healthcare system. It also describes the many prevalent principles and assaults exposed to corporate digital assets and patients’ health information, as well as the necessary solutions for overcoming the present obstacles, such as a cryptographic function and a communication protocol.
For example, this work [88] provides a complete overview of possible authentication risks and attacks on IoT healthcare devices in the Smart healthcare area. Furthermore, utilizing a hybrid cryptographic technique, the authors of [110] established a secure cloud storage solution for healthcare data. A symmetric algorithm encrypts data, while an asymmetric algorithm encrypts keys. The performance and security of the proposed approach were measured and compared to a well-known current technology. Because it is based on a modular exponentiation process, the RSA method often performs poorly. As a result, the authors used the Montgomery modular multiplication technique to enhance the RSA implementation. Blowfish encryption is used when storing health-related data in the cloud, and keys are handled using the improved RSA technique. This hybrid technique provided advantages such as quick encryption, large prime numbers for essential creation, and efficient key management. The simulation results reveal that the suggested hybrid technique’s encryption and decryption time is faster than other approaches examined for comparison.
Important points to discuss when exchanging information in a smart health system dealing with critical patient data are communicating across institutions and safeguarding patients’ private data. This work [111] proposes a method for saving image-type data using visual cryptography and distributing the data utilizing secretive sharing using practitioners’ passwords. However, if penetrated, the underlying infrastructure might result in private data leaks and the destruction of healthcare records dependent on the control commands supplied by the attacker. The authors of this paper [112] concentrate on several degrees of security associated with the storage and transmission of healthcare information. Furthermore, they test some of the suggested approach’s relevant characteristics using the access control policy testing tool to establish its practicality and examine the state of the art in the subject. However, because the present record management system cannot fully handle privacy and integrity, the health sectors nowadays use blockchain technology to store health data in a more safe, confident and decentralized manner.
This study [113] offers a blockchain architecture for electronic health records to safeguard private data based on the elliptic curve cryptography algorithm. In parallel, this study [114] proposes a realistic solution based on the unique characteristics of blockchain, where the distributed ledger technology is thought to be unbackable. The authors created a blockchain model to safeguard data security and privacy, assure data provenance, and give patients total control over their health information using the smart contract feature, a programmable self-executing protocol operating on a blockchain. This concept delivers a patient-centric procedure by customizing data segmentation and creating permitted lists for physicians to access their data. It assesses the model’s feasibility, stability, security, and robustness. In addition, this article [115] offers a permission Ethereum blockchain that connects hospitals and patients all over the globe. The proposed system employs symmetric and asymmetric key encryption to enable safe storage and selective access to records. It gives patients total control over their health information and allows them to grant or deny access to their records to a hospital. The authors stored records using the interplanetary file system (IPFS), which has the benefit of being dispersed and assuring record immutability. The suggested methodology also keeps illness data without invading any patient’s privacy.
The rising availability of healthcare data necessitates the precise analysis of illness diagnosis, progression, and real-time monitoring to enhance patients’ therapies. Machine learning (ML) models are used in this context to extract significant characteristics and insights from high-dimensional and heterogeneous healthcare data to identify various illnesses and patient behaviours in a SHeS. However, recent studies reveal that ML models employed in different application areas are susceptible to adversarial assaults. This work [116] describes a novel adversarial method for exploiting the ML classifiers used in an SHeS. An attacker with a rudimentary understanding of data distribution, the SHeS model, and an ML algorithm may launch both targeted and untargeted assaults. Their attack employs five different adversarial ML algorithms to carry out various malicious behaviours on an SHeS (e.g., data poisoning, misclassifying outputs, and so on). Using these adversarial capabilities, the authors modify medical device readings resulting from the SHS to change the patient status (disease-affected, normal condition, activities, etc.).
Furthermore, according to an adversary’s training and testing phase capabilities, the system undertakes white and black box attacks on an SHeS. They also assess the effectiveness of their work in various SHeS settings and medical equipment. Their rigorous study demonstrates that the suggested adversarial approach may severely reduce the effectiveness of an ML-based SHeS in properly recognizing illnesses and normal patient behaviours, resulting in incorrect treatment.
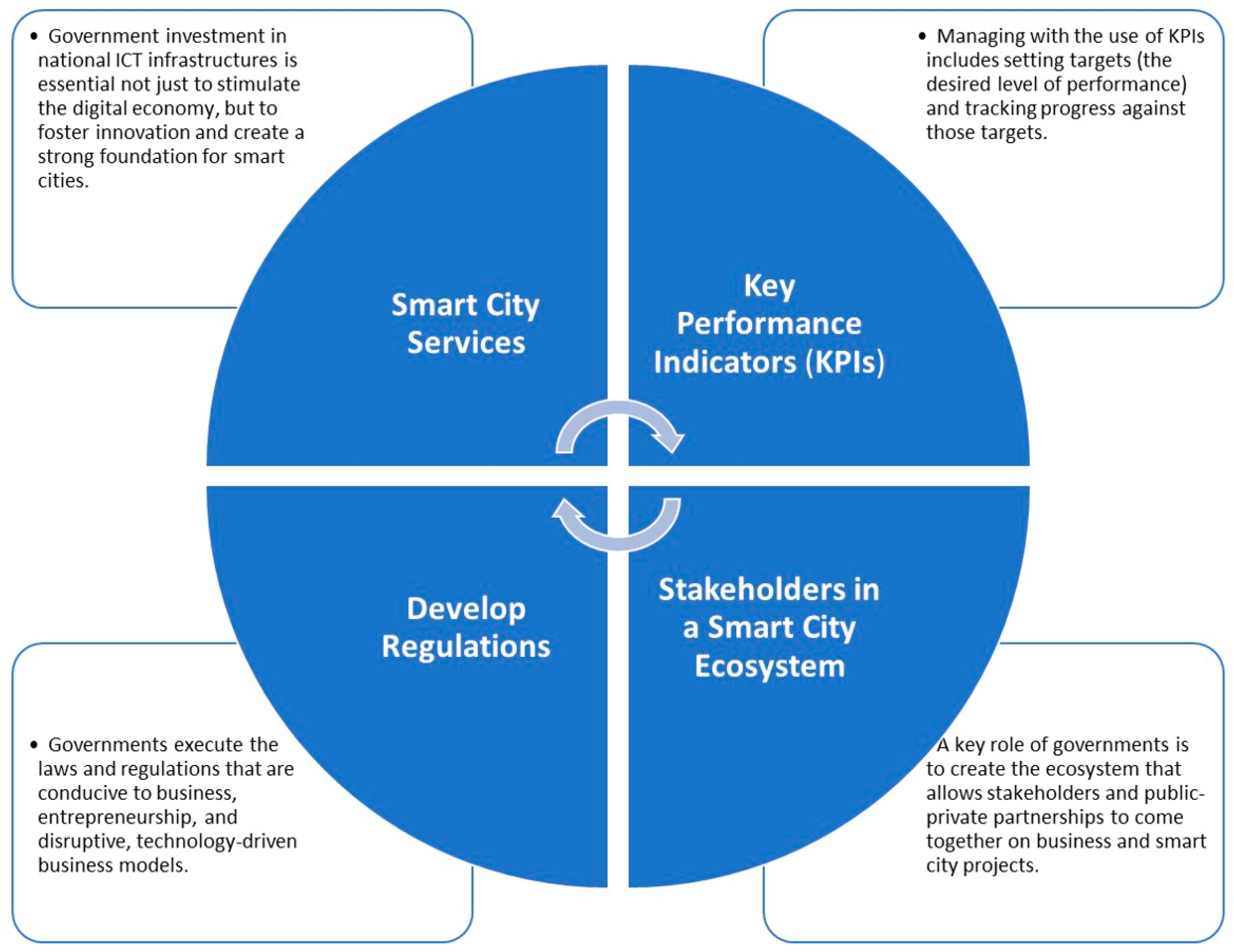
2.6. Smart Economy
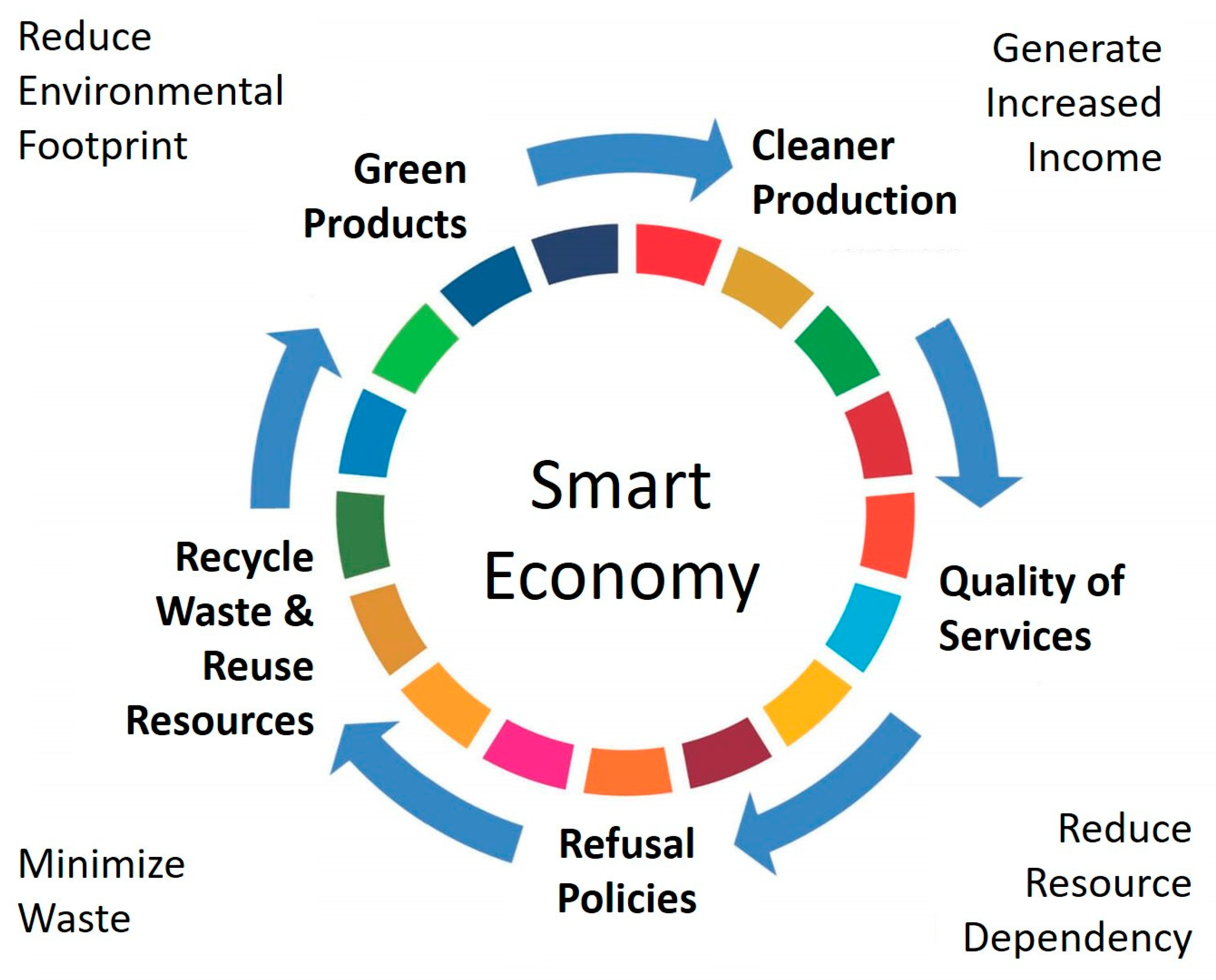
A sustainable and smart city is a fertile platform for innovation and new business models [117]. This vision is supported by sustainable entrepreneurship and the circular economy. These innovative approaches promote local and global financial ecosystem linkages while fostering long-term economic competitiveness. The smart economy concept is a prosperous economic prototype built on technology innovation, resource efficiency, sustainability, and high social welfare. It encourages innovation and new entrepreneurial activities while increasing productivity and competitiveness with the overarching objective of enhancing inhabitants’ quality of life [118].
A depiction of a smart economy in smart cities is presented in Figure 6.
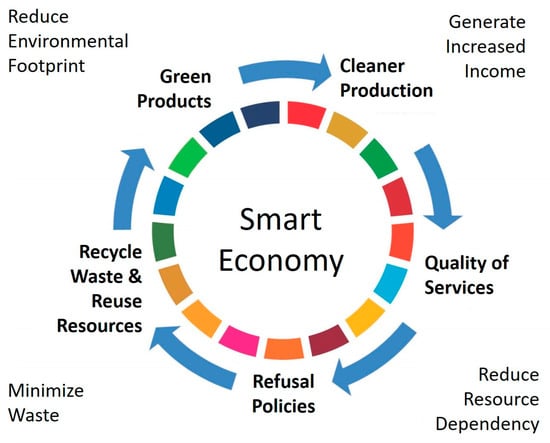
Figure 6.
Smart economy scenario in smart cities.
This technology-driven, interconnected system employs ICT applications for economic progress, urban planning, and public health improvement. It combines enhanced creativity with improved production, efficiency, and competitiveness. Several new flexible kinds of labor and start-ups distinguish it. A smart economy is projected to produce more goods and services using less energy, emitting less pollution, and offering social benefits [119]. For example, in Jakarta, a smart city, the smart economy idea being applied aims to encourage an entrepreneurial and innovative spirit in society to attain high productivity. Jakarta also has several smart economy projects [120,121] that benefit its inhabitants. Among these programs are the following [122,123,124]:
- JakPreneur: Jakarta’s MSME development initiative encourages the creation and collaboration of an entrepreneurial ecosystem. MSME actors will receive training, coaching, marketing, and even instruction on obtaining funding via JakPreneur.
- JakPangan: provides information on the cost of Jakarta’s primary commodities.
- JakNaker Platform: a portal designed to make it simpler for citizens to find jobs.
- JakOne Pay: a non-cash payment option developed in partnership with banks [9].
- JakLingko Card: The JakLingko card may pay for many kinds of transportation (buses, microbuses, railways, etc.).
To attain the degree of smartness that cities manage, smart cities are often tied to development initiatives. Several studies look at intelligent smart city performance utilizing various approaches and assessment criteria. Although there is no way to perform such an assessment, the smart economy is essential in assessing smart cities. The smart economy was a significant feature in determining smart cities in 25 of the 30 studies examined between 2015 and 2020. The authors of this research [117] underline the relevance of the smart economy component in smart city development and demonstrate how it is assessed and evaluated in various evaluation methods. Furthermore, it delves into smart economy-related metrics utilized in multiple evaluation methods. The authors use a theoretical approach combined with quantitative and qualitative data to investigate similarities and relationships among the best-performing cities in the smart economy.
To accomplish urban management services, business survival growth, and inhabitants’ productive lifestyle, a smart city is the application of a new generation of information technology. The smart economy boosts core competitiveness and may give citizens various economic options. Using China as an example, this paper [125] proposes a smart city development path based on the current state of smart city construction: use Internet technology to build big public data, strengthen the structure of digital infrastructure projects, ultimately mine data, lay a good technical foundation for smart city construction, integrate urban development with the Internet, and gradually promote harmonious town development. Moreover, this study [126] proposes a new service-oriented manufacturing business model called a smart linked product–service system (PSS) against the rapid rise of customized service demand, the digitalization of goods and services, and the socializing of service resources. The issue of CPS-oriented smart connected products and associated service resources is explored from the service flow and product serviceability, as well as the smart corresponding product service system design and socialized service crowdsourcing setup. It is divided into three sections: analysis of personalized service demands using service flow design and product minimum service capacity modeling method to meet service requirements; CPS-embedded web services modular design method for smart connected product; and community construction of service resources using federated learning and service order-driven social crowdsourcing configuration. The objective is to create a new generation of service-oriented manufacturing models that are smart, connected, efficient, and adaptable.
Growing a local economy based on sharing data from IoT devices and other open data that can be utilized in apps to better the lives of its residents is one way a city might become smarter. The authors of Ref. [127] investigate how blockchain and other distributed ledger technologies may be used to build a decentralized data marketplace. They explore the potential advantages of such a decentralized architecture, define several features that such a decentralized marketplace should include, and demonstrate how they may be incorporated into a holistic system. They also describe a basic, smart contract implementation of a decentralized registry where data owners may publish items for prospective purchasers to retrieve.
There are several hurdles to overcome to advance this decentralized marketplace. These are some examples:
- Managing system complexity: With so many moving parts and components, the decentralized marketplace system may become fragmented or difficult to scale; how can this be avoided? Maintaining a tight foundation may hinder scalability.
- Economic incentives and centralization: Without sufficient financial incentives for all parties involved, the decentralized marketplace may fail to operate successfully. It may be required to carefully construct the incentives so that additional decision-making power and data do not get concentrated in the hands of specific parties, thereby distorting rankings and recommendations in unjust ways.
- User-friendly interfaces and decentralized applications (apps) that make it simple to publish, browse, search, review, suggest, curate, verify, and data items, vendors, and customers will be required for a successful marketplace. People and organizations should be sufficiently incentivized to build and supply functional and user-friendly apps while keeping them decentralized.
2.6.1. Cyber Threats or Attacks
The smart economy’s most pressing difficulty is privacy and security concerns. The smart economy idea, in particular, presents difficulties in analyzing vulnerabilities and revising strategies. Security concerns are real and must be addressed to guarantee the sustained achievement of smart city goals. Since security is a costly operation requiring a large budget, processing in the public sector takes longer. As a result, security and privacy are essential subjects, particularly in smart economy transactions, which are becoming more vital for believing the smart city notion of enhancing living standards. As a result, secure economic services are required to provide quick assistance for transporting data, mainly via smart city networks. Therefore, it is necessary to have secured financial services to extend fast support for moving data, especially over smart city networks. The current research [3] aims to briefly present the core concepts of security and privacy issues concerning smart cities and reveal contemporary cyber-attacks targeting smart cities based on modern literature. Further, this research has elaborated and identified numerous security weaknesses and privacy challenges about various cyber security issues, challenges, and recommendations to provide future directions.
This article [121] provides a resilient architecture that defends smart city communications using autonomic computing, and moving target defense (MTD) approaches to address the most persistent difficulty in the smart economy area. The basic concept behind attaining robustness is to make it exceedingly difficult for attackers to find out the current active execution environments utilized to operate smart city services by randomizing the utilization of these resources at runtime. The authors analyzed and verified their technique by running a variety of assaults on a smart infrastructure testbed and demonstrating that the delivered services could withstand these attacks with minimum overhead.
2.6.2. Countermeasures
Under the same assumption, this research [128] focuses on the relevance of mobility and the strength of elliptic curve cryptography in heterogeneous wireless sensor networks to secure smart city applications. The results of the various simulations revealed that the proposed dynamic approach to secure smart city applications algorithm improves application security by lowering the energy consumption, the number of calculations required, and the storage space necessary for the elliptic curve cryptography keys. In particular, in the proposed approach, a powerful mobile cluster head performs operations that demand more computation and use more battery sensors regularly, such as the development, maintenance, and distribution of elliptic curve cryptography keys and periodic rekeying. Because the powerful mobile cluster head has no energy limits and is considered impenetrable, it is a periodic distributor of cryptographic keys to all the data sensors in different applications.
However, the internet-based economy creates several threats, such as unlawful data copying and digital copyright infringement, posing the problem of preserving the security and copyright of important data housed in databases. This study [122] presents a unique approach, Lossless Database Watermarking in the Homomorphic Encryption domain (HOPE-L), to solve this difficulty. The method combines database encryption (homomorphic encryption, order-preserving encryption) and information concealing (lossless data-based watermarking) technologies. To be more explicit, the information concealing technique uses the homomorphic encryption algorithm’s features to incorporate hidden data. Throughout the data-embedding process, no distortion is introduced. As a result, the proposed approach combines the watermark within the encrypted data without losing any information. The watermark may validate the copyright, and the receivers can retrieve the original database without losing any data. Theorem and analysis show that HOPE-L can attain additional embedding space without distortion. Extensive testing demonstrates that the operating method is time-efficient, the embedded watermark is resilient, and HOPE-L outperforms previous techniques and can withstand typical database assaults.
In contrast, the creative contribution of blockchain to smart economy activities may enhance corporate operations and provide a real-time view of all financial data. On-demand products, for example, of a signed contract in the shortest period feasible, may considerably assist financial operations. This process’s approval time is too lengthy, creating an opportunity to use blockchain as a solution. As a consequence of merging the smart economy with cutting-edge technology, company operations in smart cities may be strengthened by safely using smart contracts in day-to-day activities. This project [123] focuses on the document of understanding (DOU) contract, which serves as the foundation for the relationship between a consumer service and the supplier of that service. The authors leveraged local resources and used design thinking and agile principles to construct a local blockchain ledger for this assignment. As a result, they produced a proof-of-concept blockchain demo that has the whole precise history of the agreement, with immutable transactions and transparency, while providing protection and privacy to the participant’s information. They registered the time required to obtain the DOU contract signed off by everyone engaged in the process with this demo, significantly improving it. It may also be reproduced in other areas that handle sensitive data and financial reporting.
It must be noted that advanced persistent threat (APT) attacks [129] are one of the significant security challenges confronting smart economy sectors in smart cities. APT is a stealthy threat actor that acquires unauthorized network access and stays undiscovered for a lengthy period. The targets of these meticulously selected and studied attacks are often financial institutions or governmental networks. According to this viewpoint, high-level security requirements must be enforced as smart economy frameworks and infrastructures grow more technology-dependent. Furthermore, the candidates must work hard in the front, keeping an eye out for suspicious activity and aberrant conduct. To guarantee compliance with security rules and regulations, measures are essential to secure the weakest link in the smart economy IT infrastructure—endpoints and end-user devices.
2.7. Smart People
The smart people’s [130,131] domain aspires to change how people engage with the public and commercial sectors as individuals or enterprises via information or service supply. Increasing social and digital inclusion/equality via educational offerings is necessary for delivering more efficient communication and services based on new technologies (as depicted in Figure 7).
Figure 7.
Citizen-centric services applications.
Additionally, smart people are about smart types of education that promote job options, labor market possibilities, vocational training, and lifelong learning for people of all ages and ethnicities [132,133]. Talent development is also crucial from an economic development standpoint since it is becoming an increasingly relevant location element. Smart solutions for smart people promote the creation of a welcoming and inclusive atmosphere to boost prosperity and creativity within a city or community. Implementing intelligent solutions facilitates or fosters participation, open-mindedness, and innovation. In general, a city is smart because it leverages technology to improve the lives of its residents [1].
Only humans can use technology, improve economic and political efficiency, and contribute to social, cultural, and urban advancement. However, poor morale and intellect, a lack of qualified human resources, and multi-ethnic conflicts are vital difficulties that often contribute to societal issues. This study [134] aimed to discover and investigate the aspects of clever people in a smart city. The research used a mixed-method approach. Questionnaires, document reviews, and observations were used to gather data. The findings revealed that the variables of agreeableness, conscientiousness, emotional stability, extraversion, and experience with openness all had high mean scores. Aside from that, the component of friendliness had the highest average mean score of 3.78 out of the four factors: conscientiousness, extraversion, emotional stability, and experience with openness. This research indicates that local governments must adopt strategies and policies to construct and promote smart cities.
2.7.1. Cyber Threats or Attacks
Currently, schools disperse the teaching of various components of data skills throughout the curriculum. However, as smart city technologies emerge and demonstrate real promise in contributing to a more sustainable future, it is clear that new skills for working with the large urban data sets that drive these innovations must be taught to future generations for them to be active smart city citizens. The authors of this study [135] question how data skills might be taught more cohesively and practically, allowing for applying skills in actual, smart city scenarios. They suggest using urban data games to provide a setting for learning and showing the practical application of skills for dealing with substantial, complicated data sets, such as big data on smart home energy use. In this regard, do the study programs meet the need for smart city education? What are the opportunities for people to become smart in a smart city? This study [136] offers the excellent integration of smart people educational programs in future smart cities based on practice and a professional field-oriented, diversity-inclusive approach, as it is commonly acknowledged that learning by doing may considerably improve students’ understanding of information security in smart cities. Hands-on laboratories may help individuals learn about security fundamentals. This study [137] includes various hands-on laboratories that might assist individuals in performing practical exercises in risk-free settings.
However, low motivation is the first barrier when educating end-users about smart cities. Game-based learning with interactive exercises and engaging multimedia is an effective way to motivate end-users. Providing a wide range of game material to meet educational demands is critical. For example, in this paper [138], the authors propose a phishing attack game to describe stereotypical features of phishing attack techniques to teach people. As anti-phishing games develop as a scalable, motivating, and practical way for anti-phishing education for non-professional end-users, issues occur owing to a game’s content and context becoming irrelevant. When a game delivers unfamiliar or unrelated instances to the user, the learning potential is restricted since the user lacks a reference point. This study [139] presents a customization pipeline for data collecting, creation, and distribution for anti-phishing learning games to give players more meaningful, relevant game material. With the rise of remote work and education, it is vital to adopt new technologies to teach cybersecurity ideas. This work [140] describes the concept, design, and prototype of a mixed reality-based cybersecurity teaching application on phishing to expose schoolchildren to the topic remotely and allow them to practice distinguishing harmful from authentic mail.
2.7.2. Countermeasures
On the other hand, there are methods and systems to learn without much input from humans, e.g., phishing websites can be detected using machine learning by classifying the websites as legitimate or illegitimate [141]. Furthermore, this paper [142] describes a contemporary research group’s attempt to counteract targeted assaults using spear-phishing by using social engineering via user education (to increase the success probability of phishing attacks, attackers often adopt social engineering techniques). The authors specifically establish a link between human psychological features and sensitivity to social engineering. The outcome may be used to determine if a user has been exposed to a social engineering approach, and the result can be used for countermeasures or user training.
On the other side, ICT can potentially increase people’s intelligence. This paper [143] describes a system that employs smart plugs, smart cameras, smart power strips, and a digital assistant such as Amazon Alexa, Google Home, Google Assistant, Apple Siri, or Microsoft Cortana to capture voice commands spoken in a much more natural manner by a person with physical disabilities to control ordinary home electrical appliances to turn them on or off with minimal effort. Moreover, this research [144] intends to assist blind persons using smartphone devices. The program allows users to start any app and call contacts using voice commands. Speech commands may be used to instruct a mobile device. These orders are quickly interpreted by the voice recognition engine, which transforms speech into text for direct actions. This strategy is beneficial when a person feels alone in a low setting since it allows him to make a voice call to a known individual. Aside from that, the system offers an app interface that allows the user to obtain the most recent information from numerous web servers.
To allow smart connections among various devices, smart city technologies have merged artificial intelligence into smart gadgets. AI-powered smart home gadgets may interact with one another and collect new data to aid in learning human routines. The information gathered is utilized to forecast user behavior and establish situational awareness, i.e., to comprehend user preferences and modify settings appropriately. These values often clash when recognizing some ideals critical for ethical discussion in AI, such as fairness, transparency, and accountability. More openness, for example, may result in less privacy. Introducing higher principles to balance values raises two issues:
- Principles might contradict one another, deflecting the issue into a purely speculative sphere.
- If a higher-level principle is presented and contradicts another, a higher-higher-level regulation is required to enter an endless regress.
Although AI ethics is part of the so-called field of applied ethics, it appears to be about applying principles and values and finding the right balance concerning specific ethical theories, such as Kantian or utilitarianism. Traditional approaches in applied ethics do not provide sufficient conceptual means to deal with practical problems. As a result, the difficulties of installing intelligent systems cannot be fully addressed since the same issue arises: how may values be balanced concerning ethical theories? If higher-level principles are not feasible for resolving value conflicts, the conditions under which they may be applied should be considered. Consequently, it is advocated that precise criteria for implementing the principles be made clear, resulting in at least a clarification for public discussion regarding some technical developments in AI. Furthermore, it is argued that to address these conflicts, the implementation must be reviewed to see whether it allows for future human involvement rather than rendering actions impossible [145].
3. Recommendations
In the face of rising urbanization, city planners are turning to technology to alleviate many challenges in contemporary cities. Smart cities result from deeper technological integration into new or existing urban environments. Building a smart city aims to improve people’s quality of life by leveraging technology to improve service efficiency and meet residents’ needs. A smart city is a vision for urban development that aims to secure and integrate multiple information and communication technology solutions to manage a city’s assets. The smart city is concerned with how the city’s “organism” functions as an integrated whole and survives in harsh environments. A city’s energy, water, transportation, public health and safety, and other aspects as critical infrastructure run smoothly while providing a clean, economic, and safe environment to live and work in [123].
In practice, these transformational impacts will result from the combination of three components of technology: low-cost logic controllers, millions of sensors attached to devices scattered around a city, and a network that links all of these nodes and allows real-time communication. Smart cities rely on networks to ensure the supply and delivery of functions. Such network connections will allow for more effective and efficient delivery of urban services. Additionally, these networks aim to present conservation opportunities, improve efficiencies, and, most importantly, enable coordination among city officials, infrastructure operators, public safety officials, and the general public [146].
Balancing the promise of smart cities against the potential for cyber risks—and properly managing the related risks—will be key to fulfilling the smart city potential. To begin, cities should involve all stakeholders and entities in the greater ecosystem. The following are the next recommended actions that cities should consider:
- Syncing smart city and cyber strategy. Cities should develop a detailed cybersecurity strategy consistent with their overall smart city strategy and can mitigate issues coming from the continuous convergence, interoperability, and interconnection of city technologies. Additionally, they should consider undertaking a thorough impact assessment of their data, procedures, and cyber assets to identify, assess, and reduce the risks associated with technical processes, policies, and solutions. Cities may build a comprehensive cybersecurity strategy with an integrated perspective of the risks and awareness of the interdependencies of important assets.
- Formalizing cyber and data governance. Cities must codify their approach to data governance, assets, infrastructure, and other technological components. Each important part of the smart city ecosystem should have its responsibilities and tasks, which should be defined in a comprehensive governance model. Multiple entities must collaborate to apply an ecosystem approach to cyber challenges, with a robust governance model serving as the foundation. Cities can collaborate with other cities, state agencies, academics, and enterprises to exchange threat information, capabilities, and contracts to bolster cyber defenses. Furthermore, data management, which includes rigorous data sharing and privacy policies, data analytics skills, and monetization models that allow the sourcing and use of “city data,” is an important part of this governance. Policies, regulations, and technology must be constantly coordinated to strike the proper balance of protection, privacy, transparency, and utility. The city’s comprehensive cyber strategy requires the maturation of the government, rules, and processes.
- Build strategic partnerships to grow cyber capabilities [147]. Because the cyber skills gap is not going away anytime soon, cities must be inventive and proactive in filling it in their communities. Smart cities necessitate the development of new skills and competencies across all ecosystem tiers. Strategic collaborations and contracts with service providers can help cities supplement their existing skills. His strategy may necessitate the local administration exploring unorthodox methods of attracting cyber expertise, such as crowdsourcing, rewards, and challenges to address cyber-related concerns.
Cybersecurity is far too critical to be an afterthought. City leaders must recognize that protecting cities from cyber risk is not a one-time event in which cyber strategy evolves as cyber threats grow; rather, it is critical to recovering after a cyberattack occurs. Furthermore, cities cannot or should not fight this struggle alone but rather with an ecosystem of local governments, academia, the business sector, and entrepreneurs. Technology is one component of a cybersecurity solution, but it also requires a comprehensive governance architecture for data and assets. Cities need an integrated strategy for cyber-risk management, with security concepts baked into every stage of the process.
4. Conclusions
The smart cities paradigm emerges as a reaction to the objective of constructing the city of the future, where inhabitants’ and industry well-being and rights are secured, and urban planning is evaluated from an environmental and sustainable standpoint. The development of smart networks must invariably involve the provision of integrated cyber and privacy ICT solutions [65,148]. These solutions must ensure the interoperability of the various elements that make up the city’s structure and lessen the likelihood that multiple technologies will become obsolete. The variety of the infrastructures and the dynamism of their operational environment necessitates a continual reduction in complexity, quicker processing of expansion works, and the inclusion of equivalent new ones [3,12]. These requirements must be met. In addition, unified management proposes clear and definite ways of providing end-to-end smart services based on robust security standards [149] and ensuring the privacy of the information being exchanged to offer quality services [150,151]. Smart cities are becoming more interconnected, so this helps.
In this particular piece of work, to assess the developing dangers, some specific events of threats, attacks, and their respective countermeasures were selected. These are the kinds of occurrences that have been suggested from time to time in the scientific literature. The work seeks to be an indicative model that may be considered during the design and execution of infrastructure improvements connected to smart networks.
Future enhancements will include incorporating operational standards used in industrial network applications, subject to ongoing modification and reordering, and newly recognized standards for smart city networks. Additionally, the recording of the general recommendations by the standardizing bodies per field of operation of the smart networks, as well as the corresponding gaps that were possibly identified and further concern development and evaluation procedures, is a significant development that bears mentioning. This is another important advancement.
Author Contributions
Conceptualization, V.D., S.D. and K.D.; methodology, V.D., S.D. and K.D.; software, V.D., S.D. and K.D.; validation, V.D., S.D. and K.D.; formal analysis, V.D., S.D. and K.D.; investigation, V.D., S.D. and K.D.; resources, V.D., S.D. and K.D.; data curation, V.D., S.D. and K.D.; writing—original draft preparation, V.D. and S.D.; writing—review and editing, V.D., S.D. and K.D.; visualization, V.D., S.D. and K.D.; supervision, K.D.; project administration, K.D.; funding acquisition, V.D., S.D. and K.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Sánchez-Corcuera, R.; Nuñez-Marcos, A.; Sesma-Solance, J.; Bilbao-Jayo, A.; Mulero, R.; Zulaika, U.; Azkune, G.; Almeida, A. Smart cities survey: Technologies, application domains and challenges for the cities of the future. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719853984. [Google Scholar] [CrossRef]
- Win, L.L.; Tonyali, S. Security and privacy challenges, solutions, and open issues in smart metering: A review. In Proceedings of the 2021 6th International Conference on Computer Science and Engineering (UBMK), Ankara, Turkey, 15–17 September 2021; pp. 800–805. [Google Scholar] [CrossRef]
- Hamid, B.; Jhanjhi, N.; Humayun, M.; Khan, A.; Alsayat, A. Cyber security issues and challenges for smart cities: A survey. In Proceedings of the 2019 13th International Conference on Mathematics, Actuarial Science, Computer Science and Statistics, Karachi, Pakistan, 14–15 December 2019. [Google Scholar] [CrossRef]
- Sedinić, I.; Lovrić, Z. Influence of established information security governance and infrastructure on future security certifications. In Proceedings of the 2013 36th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 20–24 May 2013; pp. 1111–1115. [Google Scholar]
- Alromaihi, S.; Elmedany, W.; Balakrishna, C. Cyber security challenges of deploying IoT in smart cities for healthcare applications. In Proceedings of the 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, 6–8 August 2018; pp. 140–145. [Google Scholar] [CrossRef]
- Bekkanti, A.; Aishwarya, R.; Suganya, Y.; Valarmathi, P.; Ganesan, S.; Basha, C.Z. Novel approach of internet of things (IoT) based smart ambulance system for patient’s health monitoring. In Proceedings of the 2021 2nd International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 7–9 October 2021; pp. 29–34. [Google Scholar] [CrossRef]
- Ganguly, P.; Nasipuri, M.; Dutta, S. Challenges of the existing security measures deployed in the smart grid framework. In Proceedings of the 2019 IEEE 7th International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 12–14 August 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Giffinger, R.; Gudrun, H. Smart cities ranking: An effective instrument for the positioning of the cities? ACE Archit. City Environ. 2010, 4, 7–26. [Google Scholar] [CrossRef]
- Kartika, H.; Fatimah, Y.A.; Supangkat, S.H. Secure cashless payment governance in indonesia: A systematic literature review. In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semarang, Indonesia, 10–11 August 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Lopes, N.V. Tutorial: Smart governance for Smart cities. In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semerang, Indonesia, 10–11 October 2018; pp. 1–2. [Google Scholar] [CrossRef]
- Lopes, N.V. Smart governance: A key factor for smart cities implementation. In Proceedings of the 2017 IEEE International Conference on Smart Grid and Smart Cities (ICSGSC), Singapore, 23–26 July 2017; pp. 277–282. [Google Scholar] [CrossRef]
- Bai, Y.; Hu, Q.; Seo, S.-H.; Kang, K.; Lee, J.J. Public Participation Consortium Blockchain for Smart City Governance. IEEE Internet Things J. 2021, 9, 2094–2108. [Google Scholar] [CrossRef]
- Alotaibi, S.S. Registration Center Based User Authentication Scheme for Smart E-Governance Applications in Smart Cities. IEEE Access 2018, 7, 5819–5833. [Google Scholar] [CrossRef]
- Roy, A. Smart delivery of multifaceted services through connected governance. In Proceedings of the 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 27–29 March 2019; pp. 476–482. [Google Scholar] [CrossRef]
- Ruiz-Zafra, A.; Pigueiras, J.; Millan-Alcaide, A.; Larios, V.M.; Maciel, R. A digital object-based infrastructure for smart governance of heterogeneous internet of things systems. In Proceedings of the 2020 IEEE International Smart Cities Conference (ISC2), Piscataway, NJ, USA, 28 September–1 October 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Cho, Y.; Oh, J.; Kwon, D.; Son, S.; Yu, S.; Park, Y.; Park, Y. A Secure Three-Factor Authentication Protocol for E-Governance System Based on Multiserver Environments. IEEE Access 2022, 10, 74351–74365. [Google Scholar] [CrossRef]
- Guo, Y.; Tang, Z.; Li, P.; Peng, H. The research on the connotation characteristics and policy analysis of smart urban agglomeration under holistic governance. In Proceedings of the 2021 International Conference on Big Data and Intelligent Decision Making (BDIDM), Guilin, China, 23–25 July 2021; pp. 96–99. [Google Scholar] [CrossRef]
- Javed, A.; Kubler, S.; Malhi, A.; Nurminen, A.; Robert, J.; Framling, K. bIoTope: Building an IoT Open Innovation Ecosystem for Smart Cities. IEEE Access 2020, 8, 224318–224342. [Google Scholar] [CrossRef]
- Cirillo, F.; Gomez, D.; Diez, L.; Maestro, I.E.; Gilbert, T.B.J.; Akhavan, R. Smart City IoT Services Creation Through Large-Scale Collaboration. IEEE Internet Things J. 2020, 7, 5267–5275. [Google Scholar] [CrossRef]
- Bartolucci, S.; Fiorentino, S. Blockchain and smart contracts as new governance tools for the sharing economy. In Proceedings of the 2021 IEEE 18th International Conference on Software Architecture Companion (ICSA-C), Stattgart, Germany, 22–26 March 2021; pp. 118–119. [Google Scholar] [CrossRef]
- Razaghi, M.; Finger, M. Smart Governance for Smart Cities. Proc. IEEE 2018, 106, 680–689. [Google Scholar] [CrossRef]
- Gowthami, J.; Shanthi, N.; Krishnamoorthy, N. Secure three-factor remote user authentication for e-governance of smart cities. In Proceedings of the 2018 International Conference on Current Trends towards Converging Technologies (ICCTCT), Coimbatore, India, 1–3 March 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Sifah, E.B.; Xia, H.; Cobblah, C.N.A.; Xia, Q.; Gao, J.; Du, X. BEMPAS: A Decentralized Employee Performance Assessment System Based on Blockchain for Smart City Governance. IEEE Access 2020, 8, 99528–99539. [Google Scholar] [CrossRef]
- Tang, Z. Analysis of information security problems and countermeasures in big data management of colleges and universities under smart campus environment. In Proceedings of the 2021 2nd International Conference on Information Science and Education (ICISE-IE), Chongqing, China, 22–26 November 2021; pp. 912–915. [Google Scholar] [CrossRef]
- EL Majdoubi, D.; EL Bakkali, H.; Sadki, S. Towards smart blockchain-based system for privacy and security in a smart city environment. In Proceedings of the 2020 5th International Conference on Cloud Computing and Artificial Intelligence: Technologies and Applications (CloudTech), Marrakesh, Morocco, 24–26 November 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Guo, G.; Zhu, Y.; Yu, R.; Chu, W.C.-C.; Ma, D. A Privacy-Preserving Framework With Self-Governance and Permission Delegation in Online Social Networks. IEEE Access 2020, 8, 157116–157129. [Google Scholar] [CrossRef]
- Alamleh, H.; AlQahtani, A.A.S. Analysis of the design requirements for remote Internet-based E-voting systems. In Proceedings of the 2021 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 10–13 March 2021; pp. 386–390. [Google Scholar] [CrossRef]
- Khlaponin, Y.; Vyshniakov, V.; Prygara, M.; Poltorak, V. The new concept of guaranteeing confidence in the E-voting system. In Proceedings of the 2020 IEEE International Conference on Problems of Infocommunications. Science and Technology (PIC S&T), Kharkhiv, Ukraine, 6–9 October 2020; pp. 747–752. [Google Scholar] [CrossRef]
- Mahrez, Z.; Sabir, E.; Badidi, E.; Saad, W.; Sadik, M. Smart Urban Mobility: When Mobility Systems Meet Smart Data. IEEE Trans. Intell. Transp. Syst. 2021, 23, 6222–6239. [Google Scholar] [CrossRef]
- Al-Rahamneh, A.; Astrain, J.J.; Villadangos, J.; Klaina, H.; Guembe, I.P.; Lopez-Iturri, P.; Falcone, F. Bi2Bi Communication: Toward Encouragement of Sustainable Smart Mobility. IEEE Access 2022, 10, 9380–9394. [Google Scholar] [CrossRef]
- Butler, L.; Yigitcanlar, T.; Paz, A. Smart Urban Mobility Innovations: A Comprehensive Review and Evaluation. IEEE Access 2020, 8, 196034–196049. [Google Scholar] [CrossRef]
- Derawi, M.; Dalveren, Y.; Cheikh, F.A. Internet-of-things-based smart transportation systems for safer roads. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Vishal, D.; Afaque, H.S.; Bhardawaj, H.; Ramesh, T.K. IoT-driven road safety system. In Proceedings of the 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), Mysuru, India, 15–16 December 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Taha, A.-E.M. An IoT Architecture for Assessing Road Safety in Smart Cities. Wirel. Commun. Mob. Comput. 2018, 2018, 1–11. [Google Scholar] [CrossRef]
- Brincat, A.A.; Pacifici, F.; Martinaglia, S.; Mazzola, F. The Internet of things for intelligent transportation systems in real smart cities scenarios. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 128–132. [Google Scholar] [CrossRef]
- Yongjun, Z.; Xueli, Z.; Shuxian, Z.; Shenghui, G. Intelligent transportation system based on Internet of Things. In Proceedings of the World Automation Congress, Puerto Vallarta, Mexico, 24–28 June 2012; pp. 1–3. [Google Scholar]
- Bojan, T.M.; Kumar, U.R.; Bojan, V.M. An internet of things based intelligent transportation system. In Proceedings of the 2014 IEEE International Conference on Vehicular Electronics and Safety, Hyderabad, India, 16–17 December 2014; pp. 174–179. [Google Scholar] [CrossRef]
- Sherly, J.; Somasundareswari, D. Internet of things based smart transportation systems. Int. Res. J. Eng. Technol. 2015, 2, 1207–1210. [Google Scholar]
- Herrera-Quintero, L.F.; Banse, K.; Vega-Alfonso, J.C.; Jalil-Nasser, W.D.; Bedoya, O.E.H. IoT approach applied in the context of ITS: Monitoring highways through instant messaging. In Proceedings of the 14th International Conference on ITS Telecommunications (ITST), Copenhagen, Denmark, 2–4 December 2015; pp. 27–31. [Google Scholar] [CrossRef]
- Savithramma, R.M.; Ashwini, B.P.; Sumathi, R. Smart Mobility Implementation in Smart Cities: A Comprehensive Review on State-of-art Technologies. In Proceedings of the 2022 4th International Conference on Smart Systems and Inventive Technology (ICSSIT), Tirunelveli, India, 20–22 January 2022; pp. 10–17. [Google Scholar] [CrossRef]
- Semanjski, I.; Mandzuka, S.; Gautama, S. Smart Mobility. In Proceedings of the 2018 International Symposium ELMAR, Zadar, Croatia, 16–19 September 2018. [Google Scholar] [CrossRef]
- Kumar, B.; AbuAlhaija, M.; Alqasmi, L.; Dhakhri, M. Smart cities: A new age of digital insecurity. In Proceedings of the 2020 9th International Conference System Modeling and Advancement in Research Trends (SMART), Moradabad, India, 4–5 December 2020; pp. 267–272. [Google Scholar] [CrossRef]
- Righini, S.; Calderoni, L.; Maio, D. A Privacy-Aware Zero Interaction Smart Mobility System. IEEE Access 2022, 10, 11924–11937. [Google Scholar] [CrossRef]
- Axelsson, J.; Nylander, S. An analysis of systems-of-systems opportunities and challenges related to mobility in smart cities. In Proceedings of the 2018 13th Annual Conference on System of Systems Engineering (SoSE), Paris, France, 19–22 June 2018; pp. 132–137. [Google Scholar] [CrossRef]
- Szymanski, T.H. The “Cyber Security via Determinism” Paradigm for a Quantum Safe Zero Trust Deterministic Internet of Things (IoT). IEEE Access 2022, 10, 45893–45930. [Google Scholar] [CrossRef]
- Pundir, A.; Singh, S.; Kumar, M.; Bafila, A.; Saxena, G.J. Cyber-Physical Systems Enabled Transport Networks in Smart Cities: Challenges and Enabling Technologies of the New Mobility Era. IEEE Access 2022, 10, 16350–16364. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Shi, Z.; Shen, X.S. A Lightweight Conditional Privacy-Preservation Protocol for Vehicular Traffic-Monitoring Systems. IEEE Intell. Syst. 2013, 28, 62–65. [Google Scholar] [CrossRef]
- Samara, G.; Alsalihy, W.A.A. A new security mechanism for vehicular communication networks. In Proceedings of the 2012 International Conference on Cyber Security, Cyber Warfare and Digital Forensic, Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 18–22. [Google Scholar] [CrossRef]
- Skorput, P.; Vojvodic, H.; Mandzuka, S. Cyber security in cooperative intelligent transportation systems. In Proceedings of the 2017 International Symposium ELMAR, Zadar, Croatia, 18–20 September 2017; pp. 35–38. [Google Scholar] [CrossRef]
- Badra, M.; Ben Hamida, E. A novel cryptography based privacy preserving solution for urban mobility and traffic control. In Proceedings of the 2015 7th International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 27–29 July 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Vaidya, B.; Mouftah, H.T. Security for Shared Electric and Automated Mobility Services in Smart Cities. IEEE Secur. Priv. 2020, 19, 24–33. [Google Scholar] [CrossRef]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H.; Guizani, M. A secure, lightweight, and privacy-preserving authentication scheme for V2G connections in smart grid. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019; pp. 541–546. [Google Scholar] [CrossRef]
- Sabaliauskaite, G.; Liew, L.S.; Zhou, F.; Cui, J. Designing safe and secure mixed traffic systems. In Proceedings of the 2019 IEEE 19th International Symposium on High Assurance Systems Engineering (HASE), Hangzhou, China, 3–5 January 2019; pp. 222–227. [Google Scholar] [CrossRef]
- Arabi, N.S.; Halabi, T.; Zulkernine, M. Reinforcement learning-driven attack on road traffic signal controllers. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 218–225. [Google Scholar] [CrossRef]
- Dong, C.; Wang, H.; Ni, D.; Liu, Y.; Chen, Q. Impact Evaluation of Cyber-Attacks on Traffic Flow of Connected and Automated Vehicles. IEEE Access 2020, 8, 86824–86835. [Google Scholar] [CrossRef]
- Ongel, A.; Cornet, H.; Kong, P.; Khoo, R.; Liu, T.; Kloeppel, M. Public transport service quality improvement using universal design standards and advanced vehicle technologies. In Proceedings of the 2018 International Conference on Intelligent Autonomous Systems (ICoIAS), Singapore, 1–3 March 2018; pp. 211–216. [Google Scholar] [CrossRef]
- Li, H.; Fu, Y. Research on the triggering factors of PPP in urban mass transit. In Proceedings of the 2017 4th International Conference on Industrial Economics System and Industrial Security Engineering (IEIS), Kyoto, Japan, 24–27 July 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Wazid, M.; Bera, B.; Das, A.K.; Mohanty, S.P.; Jo, M. Fortifying Smart Transportation Security Through Public Blockchain. IEEE Internet Things J. 2022, 9, 16532–16545. [Google Scholar] [CrossRef]
- Data Analysis and Information Security of an Internet of Things (IoT) Intelligent Transit System—IEEE Conference Publication. Available online: https://ieeexplore.ieee.org/document/8374744 (accessed on 6 February 2020).
- Kim, S.; Won, Y.; Park, I.-H.; Eun, Y.; Park, K.-J. Cyber-Physical Vulnerability Analysis of Communication-Based Train Control. IEEE Internet Things J. 2019, 6, 6353–6362. [Google Scholar] [CrossRef]
- Guo, H.; Wong, J.W. Cyber-physical authentication for metro systems. In Proceedings of the 23rd Asia-Pacific Conference on Communications (APCC), Perth, WA, Australia, 11–13 December 2017. [Google Scholar] [CrossRef]
- Aktouche, S.R.; Sallak, M.; Bouabdallah, A.; Schon, W. Towards reconciling safety and security risk analysis processes in railway remote driving. In Proceedings of the 2021 5th International Conference on System Reliability and Safety (ICSRS), Palermo, Italy, 24–26 November 2021; pp. 148–154. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L. Detecting invasive species with a bio-inspired semi-supervised neurocomputing approach: The case of Lagocephalus sceleratus. Neural Comput. Appl. 2016, 28, 1225–1234. [Google Scholar] [CrossRef]
- Ullo, S.L.; Sinha, G.R. Advances in Smart Environment Monitoring Systems Using IoT and Sensors. Sensors 2020, 20, 3113. [Google Scholar] [CrossRef]
- Anezakis, V.-D.; Iliadis, L.; Demertzis, K.; Mallinis, G. Hybrid soft computing analytics of cardiorespiratory morbidity and mortality risk due to air pollution. In Proceedings of the International Conference on Information Systems for Crisis Response and Management in Mediterranean Countries, Xanthi, Greece, 18–20 October 2017; pp. 87–105. [Google Scholar] [CrossRef]
- Anezakis, V.-D.; Demertzis, K.; Iliadis, L.; Spartalis, S. A hybrid soft computing approach producing robust forest fire risk indices. In Proceedings of the IFIP International Conference on Artificial Intelligence Applications and Innovations, Thessaloniki, Greece, 16–18 September 2016; pp. 191–203. [Google Scholar] [CrossRef]
- Elhabyan, R.; Shi, W.; St-Hilaire, M. Coverage protocols for wireless sensor networks: Review and future directions. J. Commun. Networks 2019, 21, 45–60. [Google Scholar] [CrossRef]
- Patel, S.T.; Mistry, N.H. A review: Sybil attack detection techniques in WSN. In Proceedings of the 2017 4th International Conference on Electronics and Communication Systems (ICECS), Coimbatore, India, 24–25 February 2017; pp. 184–188. [Google Scholar] [CrossRef]
- Sudheendran, S.; Bouachir, O.; Moussa, S.; Dahmane, A.O. Review—Challenges of mobility aware MAC protocols in WSN. In Proceedings of the 2018 Advances in Science and Engineering Technology International Conferences (ASET), Abu Dhabi, United Arab Emirates, 16 February–5 April 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, C.-H.; Teng, P.-C. The study for campus monitoring system of attacks analysis. In Proceedings of the 2010 International Symposium on Computer, Communication, Control and Automation (3CA), Tainan, Taiwan, 5–7 May 2010; Volume 1, pp. 407–410. [Google Scholar] [CrossRef]
- Teng, Z.; Pang, B.; Du, C.; Li, Z. Malicious Node Identification Strategy With Environmental Parameters. IEEE Access 2020, 8, 149522–149530. [Google Scholar] [CrossRef]
- Bajwa, S.S.; Khan, M.K. Grouped Black hole Attacks Security Model (GBHASM) for wireless Ad-hoc networks. In Proceedings of the 2010 The 2nd International Conference on Computer and Automation Engineering (ICCAE), Singapore, 26–28 February 2010; Volume 1, pp. 756–760. [Google Scholar] [CrossRef]
- Murino, G.; Armando, A.; Tacchella, A. Resilience of Cyber-Physical Systems: An Experimental Appraisal of Quantitative Measures. In Proceedings of the 2019 11th International Conference on Cyber Conflict (CyCon), Tallinn, Estonia, 28–31 May 2019. [Google Scholar] [CrossRef]
- Hasan, M.K.; Khan, M.A.; Issa, G.F.; Atta, A.; Akram, A.S.; Hassan, M. Smart waste management and classification system for smart cities using deep learning. In Proceedings of the 2022 International Conference on Business Analytics for Technology and Security (ICBATS), Dubai, United Arab Emirates, 16–17 February 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Addeen, H.H.; Xiao, Y.; Li, J.; Guizani, M. A Survey of Cyber-Physical Attacks and Detection Methods in Smart Water Distribution Systems. IEEE Access 2021, 9, 99905–99921. [Google Scholar] [CrossRef]
- Binnar, P.; Dalvi, A.; Bhirud, S.; Kazi, F. Cyber forensic case study of waste water treatment plant. In Proceedings of the 2021 IEEE Bombay Section Signature Conference (IBSSC), Gwalior, India, 18–20 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. Distributed Attack Detection in a Water Treatment Plant: Method and Case Study. IEEE Trans. Dependable Secur. Comput. 2018, 18, 86–99. [Google Scholar] [CrossRef]
- Chenaru, O.; Popescu, D.; Enache, D.; Ichim, L.; Stoican, F. Improving operational security for web-based distributed control systems in wastewater management. In Proceedings of the 2017 25th Mediterranean Conference on Control and Automation (MED), Valletta, Malta, 3–6 July 2017; pp. 1089–1093. [Google Scholar] [CrossRef]
- Zhe, W.; Wei, C.; Chunlin, L. DoS attack detection model of smart grid based on machine learning method. In Proceedings of the 2020 IEEE International Conference on Power, Intelligent Computing and Systems (ICPICS), Shenyang, China, 28–30 July 2020; pp. 735–738. [Google Scholar] [CrossRef]
- Kumar, S.; Kumar, H.; Gunnam, G.R. Security integrity of data collection from smart electric meter under a cyber attack. In Proceedings of the 2019 2nd International Conference on Data Intelligence and Security (ICDIS), South Padre Island, TX, USA, 28–30 June 2019; pp. 9–13. [Google Scholar] [CrossRef]
- Lu, X.; Jing, J.; Wu, Y. False data injection attack location detection based on classification method in smart grid. In Proceedings of the 2020 2nd International Conference on Artificial Intelligence and Advanced Manufacture (AIAM), Manchester, UK, 15–18 October 2020; pp. 133–136. [Google Scholar] [CrossRef]
- E Silva, F.A.C.; Villibor, J.P.; Almeida, T.A.D.S.; Bonatto, B.D.; Ribeiro, P.F. Smart cities criteria: A discussion about relevant and contextualized indicators for sustainable smart living. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies Conference—Latin America (ISGT Latin America), Lima, Peru, 15–17 September 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Kor, A.-L.; Yanovsky, M.; Pattinson, C.; Kharchenko, V. SMART-ITEM: IoT-enabled smart living. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 739–749. [Google Scholar] [CrossRef]
- Das, S.K. Cyber-physical-social convergence in smart living: Challenges and opportunities. In Proceedings of the 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops), Sydney, NSW, Australia, 14–18 March 2016; p. 1. [Google Scholar] [CrossRef]
- Hussain, A.J.; Marcinonyte, D.M.; Iqbal, F.I.; Tawfik, H.; Baker, T.; Al-Jumeily, D. Smart home systems security. In Proceedings of the 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Exeter, UK, 28–30 June 2018; pp. 1422–1428. [Google Scholar] [CrossRef]
- Karimi, K.; Krit, S. Smart home-smartphone systems: Threats, security requirements and open research challenges. In Proceedings of the 2019 International Conference of Computer Science and Renewable Energies (ICCSRE), Agadir, Morocco, 22–24 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- James, F. A risk management framework and a generalized attack automata for IoT based smart home environment. In Proceedings of the 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019. [Google Scholar] [CrossRef]
- Gamundani, A.M. An impact review on internet of things attacks. In Proceedings of the 2015 International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 17–20 May 2015; pp. 114–118. [Google Scholar] [CrossRef]
- Ibrahim, M.; Nabulsi, I. Security analysis of smart home systems applying attack graph. In Proceedings of the 2021 5th World Conference on Smart Trends in Systems Security and Sustainability (WorldS4), London, UK, 29–30 July 2021; pp. 230–234. [Google Scholar] [CrossRef]
- She, W.; Gu, Z.-H.; Lyu, X.-K.; Liu, Q.; Tian, Z.; Liu, W. Homomorphic Consortium Blockchain for Smart Home System Sensitive Data Privacy Preserving. IEEE Access 2019, 7, 62058–62070. [Google Scholar] [CrossRef]
- Li, T.; Han, D.; Li, J.; Li, A.; Zhang, Y.; Zhang, R.; Zhang, Y. Your home is insecure: Practical attacks on wireless home alarm systems. In Proceedings of the IEEE INFOCOM 2021—IEEE Conference on Computer Communications, Vancouver, BC, Canada, 10–13 May 2021; pp. 1–10. [Google Scholar] [CrossRef]
- He, W.; Zhao, V.; Morkved, O.; Siddiqui, S.; Fernandes, E.; Hester, J.; Ur, B. SoK: Context sensing for access control in the adversarial home IoT. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroS&P), Vienna, Austria, 6–10 September 2021; pp. 37–53. [Google Scholar] [CrossRef]
- Singh, A.; Sikdar, B. Adversarial attack for deep learning based IoT appliance classification techniques. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 657–662. [Google Scholar] [CrossRef]
- Demertzis, K.; Tziritas, N.; Kikiras, P.; Sanchez, S.L.; Iliadis, L. The Next Generation Cognitive Security Operations Center: Adaptive Analytic Lambda Architecture for Efficient Defense against Adversarial Attacks. Big Data Cogn. Comput. 2019, 3, 6. [Google Scholar] [CrossRef]
- Muhammed, T.; Mehmood, R.; Albeshri, A.; Katib, I. UbeHealth: A Personalized Ubiquitous Cloud and Edge-Enabled Networked Healthcare System for Smart Cities. IEEE Access 2018, 6, 32258–32285. [Google Scholar] [CrossRef]
- Islam, M.; Razzaque, A.; Hassan, M.M.; Ismail, W.N.; Song, B. Mobile Cloud-Based Big Healthcare Data Processing in Smart Cities. IEEE Access 2017, 5, 11887–11899. [Google Scholar] [CrossRef]
- Amin, S.U.; Hossain, M.S.; Muhammad, G.; Alhussein, M.; Rahman, A. Cognitive Smart Healthcare for Pathology Detection and Monitoring. IEEE Access 2019, 7, 10745–10753. [Google Scholar] [CrossRef]
- Kumar, A.; Krishnamurthi, R.; Nayyar, A.; Sharma, K.; Grover, V.; Hossain, E. A Novel Smart Healthcare Design, Simulation, and Implementation Using Healthcare 4.0 Processes. IEEE Access 2020, 8, 118433–118471. [Google Scholar] [CrossRef]
- Khan, U.T.; Zia, M.F. Smart city technologies, key components, and its aspects. In Proceedings of the 2021 International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 9–10 November 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 100. Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 1 Introduction to smart healthcare and telemedicine systems. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 1–12. Available online: https://ieeexplore.ieee.org/document/9782809 (accessed on 10 July 2022).
- Hussain, F.; Hammad, M. Smart healthcare facilities via IOT in the healthcare industry. In Proceedings of the 3rd Smart Cities Symposium (SCS 2020), Online, 21–23 September 2021; pp. 386–391. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 3 Role of Artificial Intelligence, IoT and Blockchain in Smart Healthcare. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 25–36. Available online: https://ieeexplore.ieee.org/document/9782803 (accessed on 10 July 2022).
- Karunarathne, S.M.; Saxena, N.; Khan, M.K. Security and Privacy in IoT Smart Healthcare. IEEE Internet Comput. 2021, 25, 37–48. [Google Scholar] [CrossRef]
- Sharma, H.K.; Kumar, A.; Pant, S.; Ram, M. 7 Security and Privacy challenge in Smart Healthcare and Telemedicine systems. In Artificial Intelligence, Blockchain and IoT for Smart Healthcare; River Publishers: Gistrup, Denmark, 2022; pp. 67–76. Available online: https://ieeexplore.ieee.org/document/9782812 (accessed on 10 July 2022).
- Qiu, J.; Liang, X.; Shetty, S.; Bowden, D. Towards secure and smart healthcare in smart cities using blockchain. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Cook, D.J.; Duncan, G.; Sprint, G.; Fritz, R.L. Using Smart City Technology to Make Healthcare Smarter. Proc. IEEE 2018, 106, 708–722. [Google Scholar] [CrossRef] [PubMed]
- Butt, S.A.; Diaz-Martinez, J.L.; Jamal, T.; Ali, A.; De-La-Hoz-Franco, E.; Shoaib, M. IoT smart health security threats. In Proceedings of the 2019 19th International Conference on Computational Science and Its Applications (ICCSA), St. Petersburg, Russia, 1–4 July 2019; pp. 26–31. [Google Scholar] [CrossRef]
- Safavi, S.; Meer, A.M.; Melanie, E.K.J.; Shukur, Z. Cyber Vulnerabilities on smart healthcare, review and solutions. In Proceedings of the 2018 Cyber Resilience Conference (CRC), Putrajaya, Malaysia, 13–15 November 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Nidhya, R.; Kumar, M.; Maheswar, R.; Pavithra, D. Security and privacy issues in smart healthcare system using internet of things. In IoT-Enabled Smart Healthcare Systems, Services and Applications; Wiley: Hoboken, NJ, USA, 2022; pp. 63–85. [Google Scholar] [CrossRef]
- Chinnasamy, P.; Deepalakshmi, P. Design of Secure Storage for Health-care Cloud using hybrid cryptography. In Proceedings of the 2018 Second International Conference on Inventive Communication and Computational Technologies (ICICCT), Coimbatore, India, 20–21 April 2018; pp. 1717–1720. [Google Scholar] [CrossRef]
- Yang, D.; Doh, I.; Chae, K. Secure medical image-sharing mechanism based on visual cryptography in EHR system. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018. [Google Scholar] [CrossRef]
- Quamara, M.; Gupta, B.B.; Yamaguchi, S. An end-to-end security framework for smart healthcare information sharing against botnet-based cyber-attacks. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–12 January 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Poonguzhali, N.; Gayathri, S.; Deebika, A.; Suriapriya, R. A framework for electronic health record using blockchain technology. In Proceedings of the 2020 International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 3–4 July 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Zhuang, Y.; Sheets, L.R.; Chen, Y.-W.; Shae, Z.-Y.; Tsai, J.J.P.; Shyu, C.-R. A Patient-Centric Health Information Exchange Framework Using Blockchain Technology. IEEE J. Biomed. Health Inform. 2020, 24, 2169–2176. [Google Scholar] [CrossRef] [PubMed]
- Reen, G.S.; Mohandas, M.; Venkatesan, S. Decentralized patient centric e-health record management system using blockchain and IPFS. In Proceedings of the 2019 IEEE Conference on Information and Communication Technology, Allahabad, India, 6–8 December 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Newaz, A.I.; Haque, N.I.; Sikder, A.K.; Rahman, M.A.; Uluagac, A.S. Adversarial attacks to machine learning-based smart healthcare systems. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwa, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Youssef, A.; Hajek, P. The role of smart economy in developing smart cities. In Proceedings of the 2021 International Symposium on Computer Science and Intelligent Controls (ISCSIC), Rome, Italy, 12–14 November 2021; pp. 276–279. [Google Scholar] [CrossRef]
- Purnomo, A.; Sano, A.V.D.; Nindito, H.; Madyatmadja, E.D.; Sianipar, C.P.M. Mapping of smart economy research themes: A nine-year review. In Proceedings of the 2021 International Conference on ICT for Smart Society (ICISS), Bandung, Indonesia, 2–4 August 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Riasat, S.; Shah, M.A. Securing smart cities: An analysis on using blockchain for digital economies. In Proceedings of the Competitive Advantage in the Digital Economy (CADE 2021), Online, 2–3 June 2021; pp. 143–148. [Google Scholar] [CrossRef]
- Bongestu, D.R.; Yappiter; Warnars, H.L.H.S. Jakarta smart city mobile application for problem reporting. In Proceedings of the 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS), Coimbatore, India, 25–27 March 2021; pp. 735–740. [Google Scholar] [CrossRef]
- Madyatmadja, E.D.; Abdurachman, E.; Gaol, F.L.; Pudjianto, B.W.; Hapsara, M. Potential impact of social media to support government services in jakarta smart city. In Proceedings of the 2018 International Conference on Information Management and Technology (ICIMTech), Jakarta, Indonesia, 3–5 September 2018; pp. 534–538. [Google Scholar] [CrossRef]
- Parlina, A.; Murfi, H.; Ramli, K. Smart city research in Indonesia: A bibliometric analysis. In Proceedings of the 2019 16th International Conference on Quality in Research (QIR): International Symposium on Electrical and Computer Engineering, Padang, Indonesia, 22–24 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Anindra, F.; Supangkat, S.H.; Kosala, R.R. Smart governance as smart city critical success factor (case in 15 cities in Indonesia). In Proceedings of the 2018 International Conference on ICT for Smart Society (ICISS), Semarang, Indonesia, 10–11 October 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Surbakti, E.; Tobing, F.; Prisalia, R.; Septa, R. AHP hierarchy structure for indicators of smart city implementation in Indonesia. In Proceedings of the 2021 2nd International Conference On Smart Cities, Automation & Intelligent Computing Systems (ICON-SONICS), Tangerang, Indonesia, 12–13 October 2021; pp. 25–30. [Google Scholar] [CrossRef]
- Wei, C.; Dong, Z. Promote Internet economic development and smart city construction with data sharing. In Proceedings of the 2021 2nd International Conference on Big Data Economy and Information Management (BDEIM), Sanya, China, 3–5 December 2021; pp. 483–486. [Google Scholar] [CrossRef]
- Guo, W.; Jiang, P. Framework for designing a smart connected product service system. In Proceedings of the 2021 IEEE 1st International Conference on Digital Twins and Parallel Intelligence (DTPI), Beijing, China, 15 July–15 August 2021; pp. 448–451. [Google Scholar] [CrossRef]
- Ramachandran, G.S.; Radhakrishnan, R.; Krishnamachari, B. Towards a decentralized data marketplace for smart cities. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Said, S.M.; Abderrahim, M.; Mohamed, O.; Mohamed, T. Dynamic approach to secure smart city applications (DCESA). In Proceedings of the 2018 Renewable Energies, Power Systems & Green Inclusive Economy (REPS-GIE), Casablanca, Morocco, 23–24 April 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Zainudin, Z.S.; Molok, N.N.A. Advanced persistent threats awareness and readiness: A case study in malaysian financial institutions. In Proceedings of the 2018 Cyber Resilience Conference (CRC), Putrajaya, Malaysia, 13–15 November 2018; pp. 1–3. [Google Scholar] [CrossRef]
- Ando, B. A Smart Multisensor Approach to Assist Blind People in Specific Urban Navigation Tasks. IEEE Trans. Neural Syst. Rehabilitation Eng. 2008, 16, 592–594. [Google Scholar] [CrossRef]
- Wang, L.; Xu, L.; Zheng, Z.; Liu, S.; Li, X.; Cao, L.; Li, J.; Sun, C. Smart Contract-Based Agricultural Food Supply Chain Traceability. IEEE Access 2021, 9, 9296–9307. [Google Scholar] [CrossRef]
- Krejcar, O.; Maresova, P.; Selamat, A.; Melero, F.J.; Barakovic, S.; Husic, J.B.; Herrera-Viedma, E.; Frischer, R.; Kuča, K. Smart Furniture as a Component of a Smart City—Definition Based on Key Technologies Specification. IEEE Access 2019, 7, 94822–94839. [Google Scholar] [CrossRef]
- Kirimtat, A.; Krejcar, O.; Kertesz, A.; Tasgetiren, M.F. Future Trends and Current State of Smart City Concepts: A Survey. IEEE Access 2020, 8, 86448–86467. [Google Scholar] [CrossRef]
- Chye, C.M.; Fahmy-Abdullah, M.; Sufahani, S.F.; Bin Ali, M.K. A study of smart people toward smart cities development. In Proceedings of the Third International Conference on Trends in Computational and Cognitive Engineering; Springer: Singapore, 2022; pp. 257–271. [Google Scholar] [CrossRef]
- Wolff, A.; Kortuem, G.; Cavero, J. Towards smart city education. In Proceedings of the 2015 Sustainable Internet and ICT for Sustainability (SustainIT), Madrid, Spain, 14–15 April 2015; pp. 1–3. [Google Scholar] [CrossRef]
- Bululukova, D.; Tabakovic, M.; Wahl, H. Smart cities education as mobility, energy & ICT hub. In Proceedings of the 2016 5th International Conference on Smart Cities and Green ICT Systems (SMARTGREENS), Rome, Italy, 23–25 April 2016; pp. 1–8. [Google Scholar]
- Kwon, M.J.; Kwak, G.; Jun, S.; Kim, H.-J.; Lee, H.Y. Enriching security education hands-on labs with practical exercises. In Proceedings of the 2017 International Conference on Software Security and Assurance (ICSSA), Altoona, PA, USA, 24–25 July 2017; pp. 100–103. [Google Scholar] [CrossRef]
- Tseng, S.-S.; Chen, K.-Y.; Lee, T.-J.; Weng, J.-F. Automatic content generation for anti-phishing education game. In Proceedings of the 2011 International Conference on Electrical and Control Engineering, Yichang, China, 16–18 September 2011; pp. 6390–6394. [Google Scholar] [CrossRef]
- Ropke, R.; Schroeder, U.; Drury, V.; Meyer, U. Towards personalized game-based learning in anti-phishing education. In Proceedings of the 2020 IEEE 20th International Conference on Advanced Learning Technologies (ICALT), Tartu, Estonia, 6–9 July 2020; pp. 65–66. [Google Scholar] [CrossRef]
- Chiou, Y.-M.; Shen, C.-C.; Mouza, C.; Rutherford, T. Augmented reality-based cybersecurity education on phishing. In Proceedings of the 2021 IEEE International Conference on Artificial Intelligence and Virtual Reality (AIVR), Taichung, Taiwan, 15–17 November 2021; pp. 228–231. [Google Scholar] [CrossRef]
- Yahya, F.; Mahibol, R.I.W.; Ying, C.K.; Bin Anai, M.; Frankie, S.A.; Nin Wei, E.L.; Utomo, R.G. Detection of phising websites using machine learning approaches. In Proceedings of the 2021 International Conference on Data Science and Its Applications (ICoDSA), Bandung, Indonesia, 6–7 October 2021; pp. 40–47. [Google Scholar] [CrossRef]
- Takata, T.; Ogura, K. Confront Phishing Attacks—From a Perspective of Security Education. In Proceedings of the 2019 IEEE 10th International Conference on Awareness Science and Technology (iCAST), Morioka, Japan, 23–25 October 2019. [Google Scholar] [CrossRef]
- Mtshali, P.; Khubisa, F. A smart home appliance control system for physically disabled people. In Proceedings of the 2019 Conference on Information Communications Technology and Society (ICTAS), Durban, South Africa, 6–8 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Kasthuri, R.; Nivetha, B.; Shabana, S.; Veluchamy, M.; Sivakumar, S. Smart device for visually impaired people. In Proceedings of the 2017 Third International Conference on Science Technology Engineering & Management (ICONSTEM), Chennai, India, 23–24 March 2017; pp. 54–59. [Google Scholar] [CrossRef]
- Richter, F. Ethics of AI as practical ethics. In Proceedings of the 2021 IEEE International Symposium on Technology and Society (ISTAS), Waterloo, ON, Canada, 28–31 October 2021; p. 1. [Google Scholar] [CrossRef]
- Gamundani, A.M.; Phillips, A.; Muyingi, H.N. An overview of potential authentication threats and attacks on Internet of Things(IoT): A Focus on Smart Home Applications. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 50–57. [Google Scholar] [CrossRef]
- Demertzis, K.; Kikiras, P.; Tziritas, N.; Sanchez, S.L.; Iliadis, L. The Next Generation Cognitive Security Operations Center: Network Flow Forensics Using Cybersecurity Intelligence. Big Data Cogn. Comput. 2018, 2, 35. [Google Scholar] [CrossRef]
- Demertzis, K.; Iliadis, L.; Pimenidis, E.; Tziritas, N.; Koziri, M.; Kikiras, P. Blockchained adaptive federated auto metalearning BigData and DevOps CyberSecurity Architecture in Industry 4.0. In Proceedings of the International Neural Networks Society; Springer: Berlin/Heidelberg, Germany, 2021; pp. 345–363. [Google Scholar] [CrossRef]
- R, M.; K, G.; Rao, V.V. Proactive measures to mitigate cyber security challenges in IoT based smart healthcare networks. In Proceedings of the 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Alshalali, T.; Mbale, K.; Josyula, D. Security and privacy of electronic health records sharing using hyperledger fabric. In Proceedings of the 2018 International Conference on Computational Science and Computational Intelligence (CSCI), Las Ve-gas, NV, USA, 13–15 December 2018. [Google Scholar]
- Bringer, J.; Chabanne, H.; Patey, A. Privacy-Preserving Biometric Identification Using Secure Multiparty Computation: An Overview and Recent Trends. IEEE Signal Process. Mag. 2013, 30, 42–52. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).