Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication
Abstract
:1. Introduction
- Providing a concise survey that clarifies the existence of various cloud MFA authentication techniques using multiple numbers of factors.
- Proposing a multi-factor multi-layer authentication framework for the cloud computing environment.
- Proposing the authentication method selector (AMS) technique for improving the authentication process by selecting the appropriate authentication method based on user behavior.
- Providing interactive response to users’ behaviors based on users’ location and default used web browser information for increasing and enforcing the intrusion detection security steps.
- Obtaining experimental results to demonstrate and validate the performance of the proposed framework.
2. Literature Review
- Reduced risk of data breaches: MFA makes it much more difficult for attackers to gain access to cloud resources, even if they have compromised a user’s password.
- Improved compliance: Many industry regulations require organizations to implement MFA for certain types of data and applications.
- Enhanced user experience: MFA can be implemented in a way that is convenient for users, such as by using push notifications or smartphone apps.
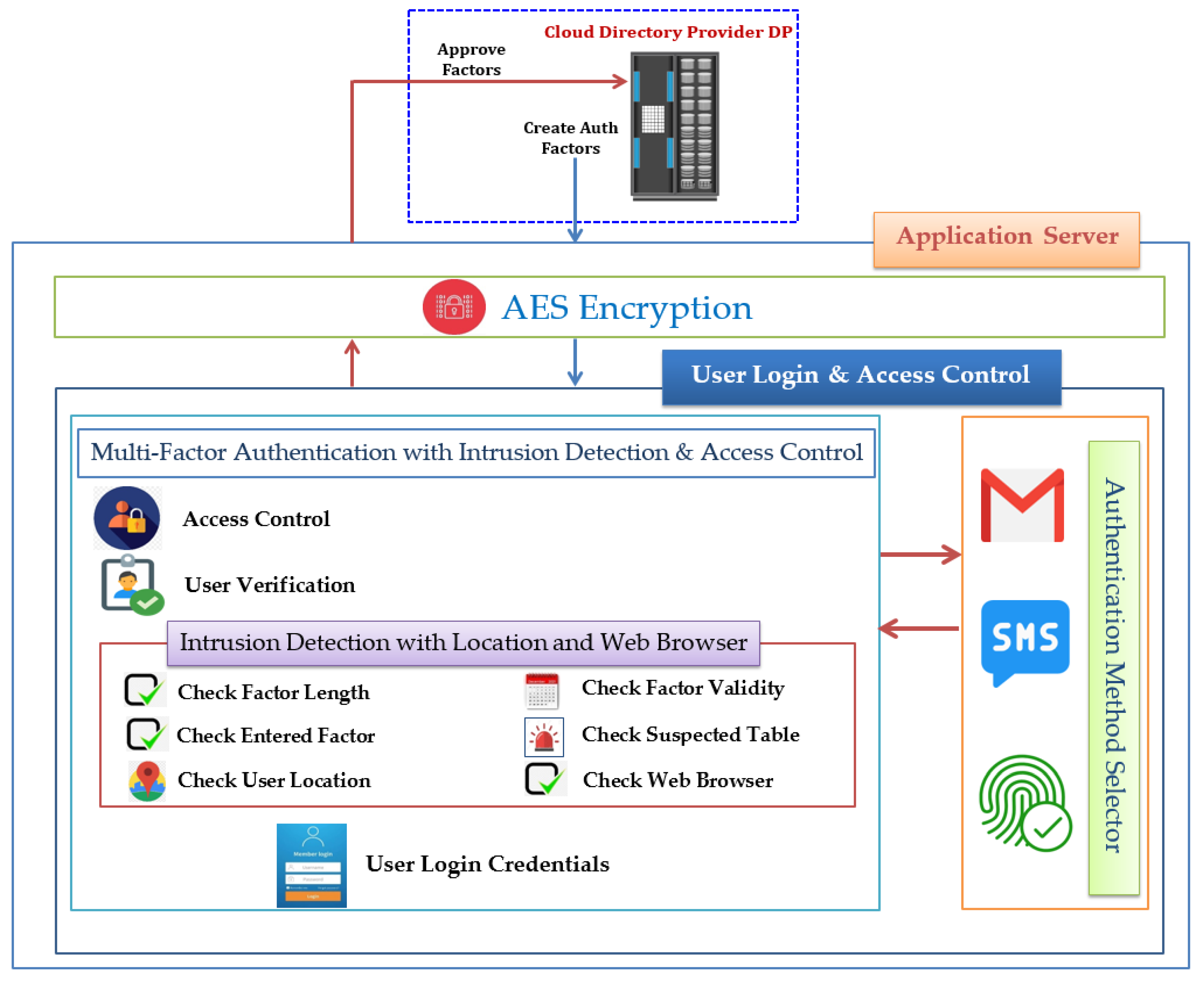
3. Proposed Framework for Cloud Multi-Factor Multi-Layer Authentication
- To enhance the security of cloud platforms and reduce false alarms.
- To make it more difficult for intruders to gain access to the system, even if they have stolen one of the user’s authentication factors.
- To reduce the number of false alarms by using multiple authentication factors.
- To improve the user experience by only requiring users to provide their authentication factors once, when they first log in to the system.
- The length, validity, and value of the authentication factor;
- The suspected table;
- The user’s geolocation;
- The user’s browser name.
3.1. Authentication Method Selector (AMS)
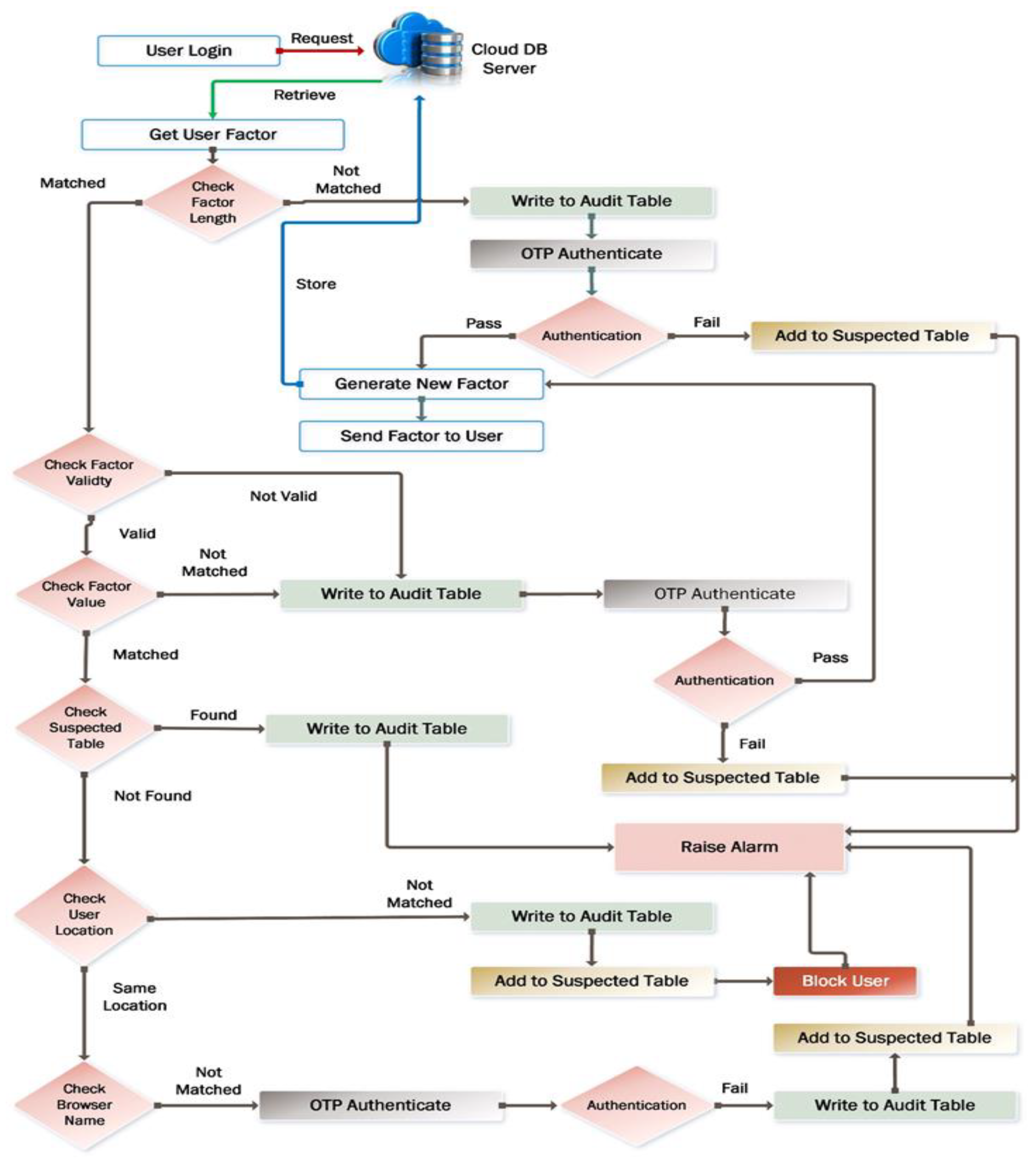
3.2. Cloud MFA Algorithm for Intrusion Detection
- Increased security: multi-factor authentication makes it more difficult for intruders to access the system, even if they have stolen one of the user’s authentication factors.
- Reduced false alarms: By using multiple authentication factors, the framework can help to reduce the number of false alarms. This is because it is less likely that an intruder will be able to provide all of the required authentication factors.
- Improved user experience: Multi-factor authentication can also improve the user experience. This is because users only need to provide their authentication factors once, when they first log in to the system. After that, they can access the system without having to provide their authentication factors again.
- Improved security posture: by using a combination of different security approaches, you can create a more layered security posture that is more difficult for attackers to penetrate.
- Reduced risk of data breaches: A combination of security approaches can help to reduce the risk of data breaches by making it more difficult for attackers to gain access to your systems and data.
- Improved compliance: Many industry regulations require organizations to implement a combination of security approaches. By using a combination of approaches, you can help to ensure that your organization is compliant with all applicable regulations.
| Algorithm 1: User Behavior Authentication | |
| 1 | Initialize |
| 2 | Initialize |
| 3 | Initialize |
| 4 | Request from Cloud DB Server |
| 5 | GET |
| 6 | IF THEN |
| 7 | |
| 8 | Layer |
| 9 | THEN |
| 10 | |
| 11 | into Cloud DB Server |
| 12 | |
| 13 | ELSE |
| 14 | |
| 15 | Raise Alarm |
| 16 | END IF |
| 17 | ELSE |
| 18 | validity |
| 19 | THEN |
| 20 | |
| 21 | Layer |
| 22 | THEN |
| 23 | |
| 24 | into Cloud DB Server |
| 25 | |
| 26 | ELSE |
| 27 | |
| 28 | Raise Alarm |
| 29 | END IF |
| 30 | |
| 31 | for Auth Parameters |
| 32 | END IF |
| 33 | THEN |
| 34 | |
| 35 | Layer |
| 36 | THEN |
| 37 | |
| 38 | into Cloud DB Server |
| 39 | |
| 40 | ELSE |
| 41 | |
| 42 | Raise Alarm |
| 43 | END IF |
| 44 | |
| 45 | |
| 46 | END IF |
| 47 | THEN |
| 48 | |
| 49 | Raise Alarm |
| 50 | ELSE |
| 51 | |
| 52 | END IF |
| 53 | THEN |
| 54 | |
| 55 | |
| 56 | Raise Alarm |
| 57 | ELSE |
| 58 | |
| 59 | END IF |
| 60 | THEN |
| 61 | |
| 62 | |
| 63 | Raise Alarm |
| 64 | ELSE |
| 65 | |
| 66 | END IF |
| 67 | END IF |
4. Threat Model
- Data loss: The framework stores user credentials and authentication parameters in an encrypted format, but there is always a risk that these data could be compromised. If an attacker were to gain access to these data, they could use them to impersonate users and gain unauthorized access to cloud resources.
- Account hijacking: The framework uses a variety of methods to detect suspicious user activity. Once an attacker has hijacked an account, they could use it to access sensitive data or to make unauthorized changes to cloud resources.
- Data leakage: The framework uses a variety of methods to protect user data, but there is always a risk that data could be leaked. For example, an attacker could exploit a vulnerability in the framework to steal data, or could gain access to data by compromising a cloud service provider.
- Brute force attack: in this attack, the attacker tries different possible keys until he obtains an intelligible secret key.
- Monitoring for suspicious activity: when suspicious activity is detected, it is important to verify the activity and perform a suitable action to prevent the suspicious user from attacking the cloud services.
- Using strong authentication: the provided MFA authentication is based on defense-in-depth multi-layers, which authenticate, verify, secure, and maintain the privacy of cloud users who are connected to the cloud platform services.
- Encrypting data: we use strong encryption to protect user credentials and authentication parameters.
- We implement robust security controls to detect and prevent unauthorized access to user data.
- We train users with recommended security practices, such as using secure passwords and staying away from fraudulent websites.
5. Security Analysis for the Proposed MFA Model
5.1. Identify Assets and Vulnerabilities
- -
- Cloud applications;
- -
- Cloud data;
- -
- Provided cloud services;
- -
- Cloud main resources.
- -
- Unauthorized access;
- -
- Data breaches;
- -
- Brute force attacks.
5.2. Assess Threats
- -
- Weak passwords: Passwords are common forms of authentication, but they are also one of the weakest. Attackers can use different techniques, such as brute-force attacks and password cracking tools, to guess or steal passwords.
- -
- Phishing attacks, which aim to deceive users into disclosing private data like passwords and credit card details. Attackers frequently send emails that look like they are coming from reputable businesses or organizations.
- -
- Malware attacks: Malware is harmful software that can be secretly placed on a user’s device. Malware can be used to steal passwords, intercept communications, and launch other attacks.
5.3. Analyze Risks
- -
- Complexity: the proposed cloud framework should be easy to implement and manage.
- -
- Security risks: the framework should introduce and identify major security risks and identify a proposed intrusion detection method for preventing these risks.
- -
- Privacy risks: the framework must preserve the privacy and sensitivity of users in factors such as location and web browser information.
- -
- Time: the execution time for detecting any malicious attacks depends on the complexity of authentication methods, number of authentication factors, number of manipulating users on the cloud, and the performance of the hardware/software used to implement the framework.
5.4. Develop MFA
- -
- Complexity: Although the proposed framework contains multi-factor with multi-layer authentication parameters, the framework and its proposed algorithm provide efficient integration of three main layers with an additional embedded layer for encrypting and decrypting user parameters and authorizations. The first layer is responsible for selecting authentication methods for users based on different priority parameters. The second layer is responsible for detecting user behavior on the cloud system or platform using different multi-factor authentication parameters. The third layer proposes an algorithm for manipulating the behavior of users based on the defined cloud multi-factor authentication methods. The three layers are connected to an additional layer for encrypting user credentials and authentication parameters to prevent any probable disclosure of user information and cloud computing-sensitive data.
- -
- Security risks: The proposed framework introduces new security risks, such as vulnerabilities in the authentication method selector (AMS) technique or the intrusion detection component. Additionally, the framework collects sensitive user data, such as location and web browser information, which could be misused if compromised.
- -
- Privacy risks: The proposed framework collects sensitive user data, such as location and web browser information. These data could be misused if compromised. Additionally, the framework uses these data to manipulate user behavior, which could be seen as an invasion of privacy. To mitigate these privacy risks, the framework can be designed to collect only the information that is necessary for its operation, and this information should be protected using appropriate security measures. Additionally, users should be given the option to opt out of having their data used to manipulate their behavior.
- -
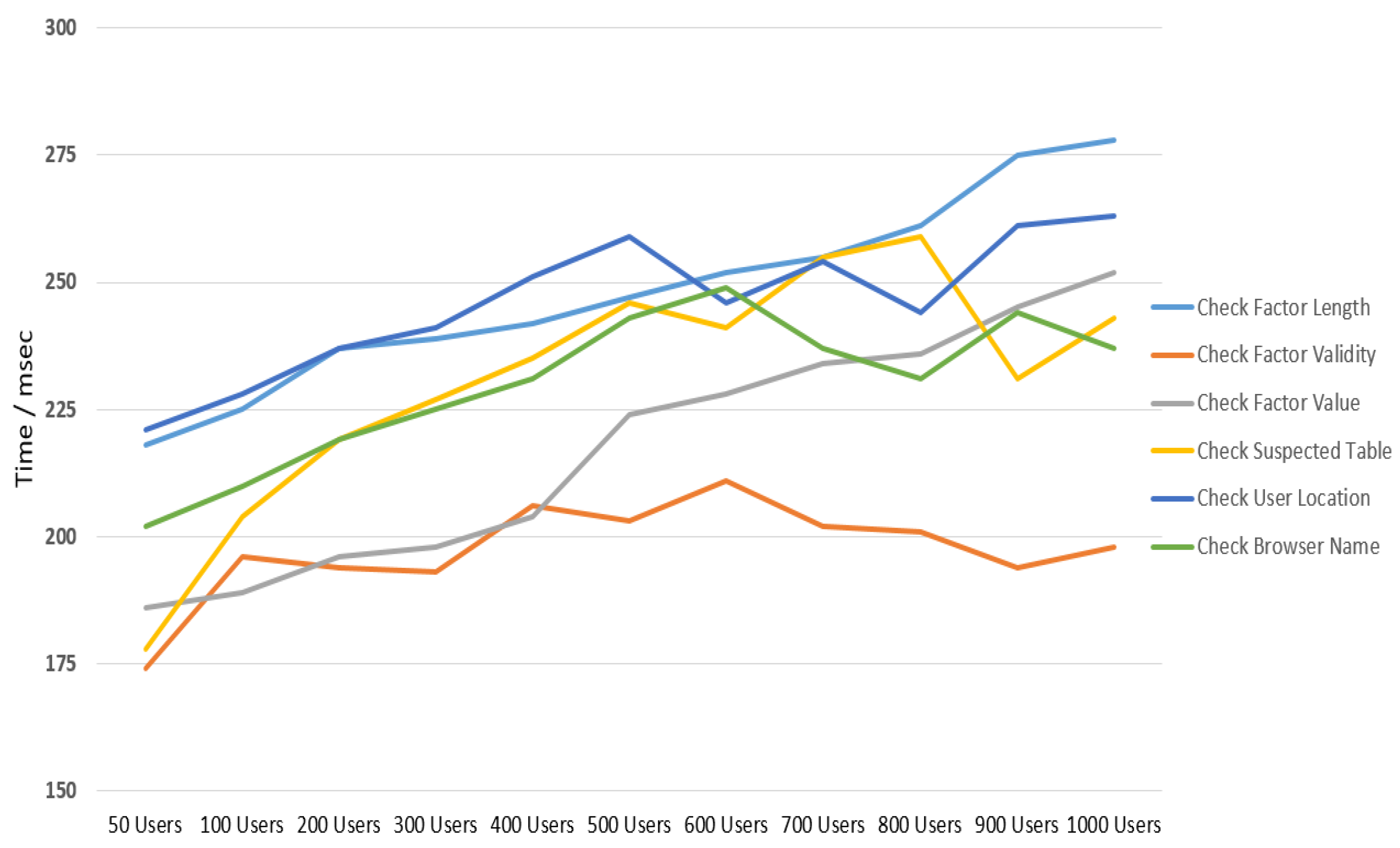
- Execution time: although the proposed framework contains different authentication factors, the overall time complexity is considered relatively low with the increasing number of cloud users.
- -
- One-time passwords (OTPs): OTPs are generated by a separate device, such as a smartphone app or a hardware token.
- -
- Location-based authentication: Location-based authentication methods use the user’s location to authenticate them. For example, a user can enter a code that is sent to their smartphone when they are trying to log in to a cloud application from a new location.
- -
- The strength of the authentication factors used: The authentication factors used should be strong and resistant to attack. For example, passwords should be complex and unique, and OTPs should be generated using a secure algorithm.
- -
- The implementation of the MFA method: The MFA method should be implemented correctly and securely. For example, OTPs should be transmitted and stored securely.
- -
- The management of MFA users and devices: MFA users and devices should be managed securely. For example, users should be required to change their passwords regularly, and devices should be improved with the latest security patches.
- -
- Improved security: the MFA framework makes it more difficult for attackers to gain unauthorized access to cloud systems and applications.
- -
- Reduced risk of data breaches: the MFA framework can help to reduce the risk of data breaches by making it more difficult for attackers to steal user credentials.
- -
- Increased compliance: many organizations are subject to industry-specific regulations that require them to implement MFA.
- -
- Improved user confidence: customers are more likely to trust organizations that can demonstrate that they are taking steps to protect their data.
6. Implementation and Results for Authentication Algorithm
6.1. Execution Time for Multi-Factor Authentication Layer
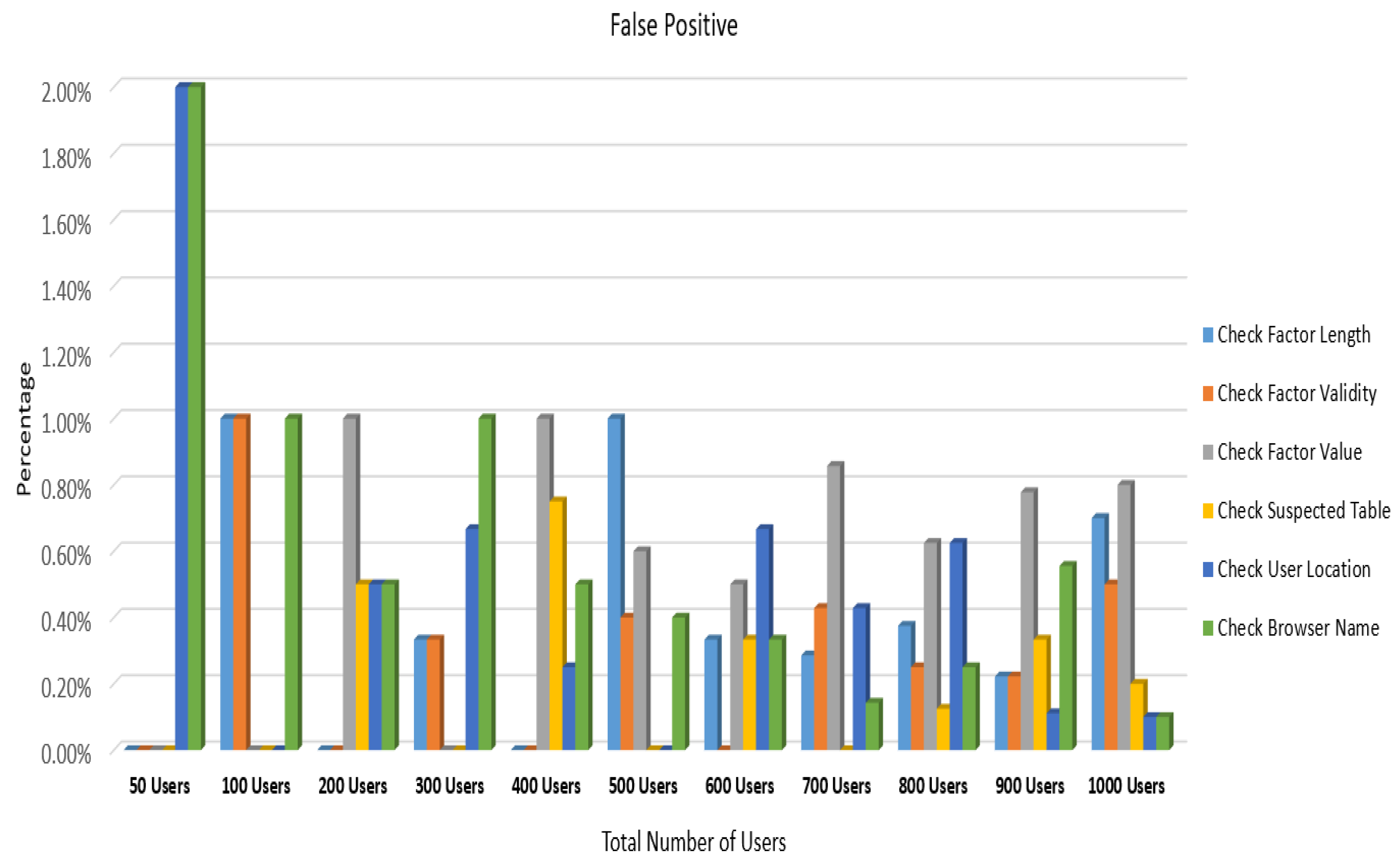
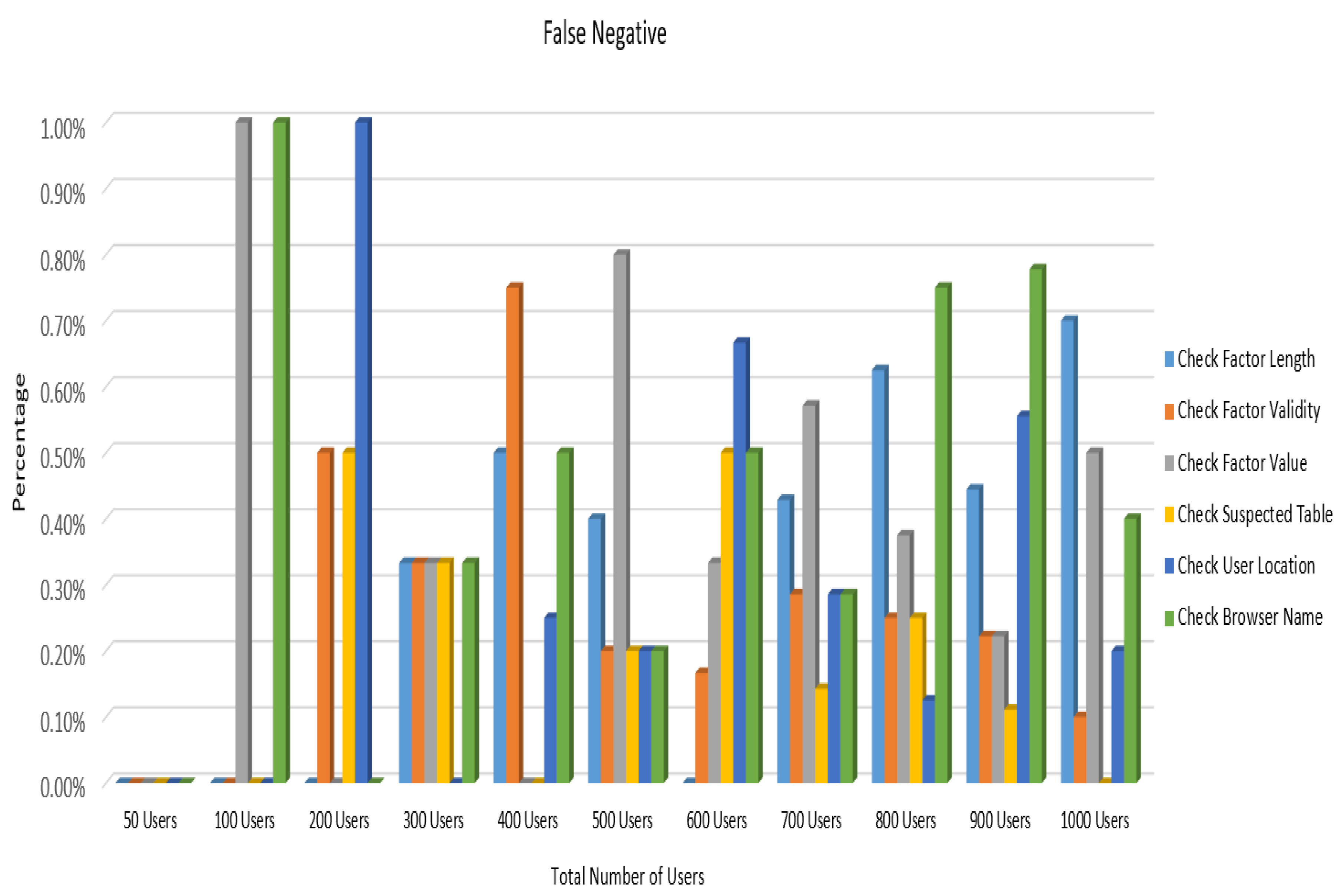
6.2. Detection Performance
- -
- Usability testing: Usability testing can be conducted to observe users as they interact with the MFA system. This can help to identify any areas where the system is confusing or difficult to use.
- -
- Scalability: The system should be able to scale to meet the needs of a growing organization.
- -
- Flexibility: The system should be flexible enough to accommodate different security requirements.
- -
- Affordability: The system should be affordable for the organization.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Tabrizchi, H.; Kuchaki Rafsanjani, M. A survey on security challenges in cloud computing: Issues, threats, and solutions. J. Supercomp. 2020, 76, 9493–9532. [Google Scholar] [CrossRef]
- Yeng, P.K.; Wulthusen, S.D.; Yang, B. Comparative analysis of threat modeling methods for cloud computing towards healthcare security practice. Int. J. Adv. Comp. Sci. Appl. (IJACSA) 2020, 11, 772–784. [Google Scholar] [CrossRef]
- Panda, D.R.; Behera, S.K.; Jena, D. A Survey on Cloud Computing Security Issues, Attacks and Countermeasures. Advances in Machine Learning and Computational Intelligence; Patnaik, X.-S., Yang, I.K., Sethi, S., Eds.; Springer: Singapore, 2021; pp. 513–524. [Google Scholar] [CrossRef]
- Sumitra, B.; Pethuru, C.; Misbahuddin, M. A survey of cloud authentication attacks and solution approaches. Int. J. Innov. Res. Comp. Commun. Eng. (IJIRCCE) 2014, 2, 6245–6253. [Google Scholar]
- Ghasemisharif, M.; Kanich, C.; Polakis, J. Towards automated auditing for account and session management flaws in single sign-on deployments. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–26 May 2022; pp. 1774–1790. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Duan, Y.; Tao, X. Secure and lightweight user authentication scheme for cloud-assisted internet of things. IEEE Trans. Inf. Forensics Secur. 2023, 18, 2961–2976. [Google Scholar] [CrossRef]
- Li, Z.; Wang, D.; Morais, E. Quantum-safe round-optimal password authentication for mobile devices. IEEE Trans. Dependable Secur. Comp. 2020, 19, 1885–1899. [Google Scholar] [CrossRef]
- Balaram, V.S. Cloud computing authentication techniques: A survey. Int. J. Sci. Eng. Technol. Res. IJSETR 2017, 6, 458–464. [Google Scholar]
- Sudha, S.; Manikandasaran, S. A survey on different authentication schemes in cloud computing environment. Int. J. Manag. IT Eng. 2019, 9, 359–375. [Google Scholar]
- Li, Y.; Luo, J.; Deng, S.; Zhou, G. SearchAuth: Neural architecture search based continuous authentication using auto augmentation search. ACM Trans. Sensor Networks 2023, 19, 1–23. [Google Scholar] [CrossRef]
- Ometov, A.; Bezzateev, S.; Mäkitalo, N.; Andreev, S.; Mikkonen, T.; Koucheryavy, Y. Multi-factor authentication: A survey. Cryptography 2018, 2, 1. [Google Scholar] [CrossRef]
- ALSaleem, B.O.; Alshoshan, A.I. Multi-factor authentication to systems login. In Proceedings of the National Computing Colleges Conference (NCCC), Taif, Saudi Arabia, 27–28 March 2021; pp. 1–4. [Google Scholar] [CrossRef]
- AlQahtani, A.A.S.; El-Awadi, Z.; Min, M. A survey on user authentication factors. In Proceedings of the IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021; pp. 323–328. [Google Scholar] [CrossRef]
- Dasgupta, D.; Roy, A.; Nag, A. Multi-Factor Authentication. Advances in User Authentication; Dasgupta, D., Roy, A., Nag, A., Eds.; Infosys Science Foundation; Springer International Publishing: Cham, Switzerland, 2017; pp. 185–233. [Google Scholar]
- Singh, C.; Kaur, R. Relevance of Multifactor Authentication for Secure Cloud Access. Big Data, Cloud Computing and IoT: Tools and Applications, 1st ed.; Sita Rani, P.B., Aman, K., Khang, A., Kumar Sivaraman, A., Eds.; Chapman and Hall/CRC: London, UK, 2023; Chapter 10. [Google Scholar]
- Andrés, S. Zero factor authentication: A four-year study of simple password-less website security via one-time emailed tokens. J. Inf. Secur. Appl. 2015, 1–11. [Google Scholar]
- Gunson, N.; Marshall, D.; Morton, H.; Jack, M. User perceptions of security and usability of single-factor and two-factor authentication in automated telephone banking. Comput. Secur. 2011, 30, 208–220. [Google Scholar] [CrossRef]
- Bruun, A.; Jensen, K.; Kristensen, D. Usability of Single- and Multi-Factor Authentication Methods on Tabletops: A Vomparative Study. Human-Centered Software Engineering; Sauer, S., Bogdan, C., Forbrig, P., Bernhaupt, R., Winckler, M., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8742, pp. 299–306. [Google Scholar] [CrossRef]
- Said, W.; Mostafa, S.; Hassan, M.M.; Mostafa, A.M. A multi-factor authentication-based framework for identity management in cloud applications. Comput. Mater. Contin. 2022, 71, 3193–3209. [Google Scholar] [CrossRef]
- Mupila, F.K.; Gupta, H. A multi-factor approach for cloud security. Innovations in Computer Science and Engineering. In Lecture Notes in Networks and Systems; Saini, H.S., Sayal, R., Govardhan, A., Buyya, R., Eds.; Springer: Singapore, 2013; Volume 171, pp. 437–445. [Google Scholar] [CrossRef]
- Neware, R.; Shrawankar, U.; Mangulkar, P.; Khune, S. Review on multi-factor authentication (mfa) sources and operation challenges. Int. J. Smart Secur. Technol. IJSST 2020, 7, 62–67. [Google Scholar] [CrossRef]
- Boonkrong, S. Multi-Factor Authentication. Authentication and Access Control: Practical Cryptography Methods and Tools; Boonkrong, S., Ed.; Apress: Berkeley, CA, USA, 2021; Chapter 6; pp. 133–162. [Google Scholar]
- Tirfe, D.; Anand, V.K. A Survey on Trends of Two-Factor Authentication. Contemporary Issues in Communication, Cloud and Big Data Analytics; Sarma, H.K.D., Balas, V.E., Bhuyan, B., Dutta, N., Eds.; Lecture Notes in Networks and Systems; Springer: Singapore, 2022; Volume 281, pp. 285–296. [Google Scholar] [CrossRef]
- Wang, P.; Baskerville, R. The Case for Two-Factor Authentication- Evidence from a Systematic Literature Review. In Proceedings of the Pacific Asia Conference on Information Systems (PACIS 2019) Proceedings, X’ian, China, 8–12 July 2019. [Google Scholar]
- Archana, B.S.; Chandrashekar, A.; Bangi, A.G.; Sanjana, B.M.; Akram, S. Survey on usable and secure two-factor authentication. In Proceedings of the IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19–20 May 2017; pp. 842–846. [Google Scholar] [CrossRef]
- Lee, H.; Kang, D.; Lee, Y.; Won, D. Secure three-factor anonymous user authentication scheme for cloud computing environment. Wirel. Commun. Mob. Comput. 2021, 2021, 1–20. [Google Scholar] [CrossRef]
- Jain, S.; Gautam, R.; Sharma, S.; Tomar, R.; Choudhury, T. Four-Factor Authentication with Emerging Cybersecurity for Mobile Transactions. Innovations in Cyber Physical Systems; Singh, J., Kumar, S., Choudhury, U., Eds.; Lecture Notes in Electrical Engineering; Springer: Singapore, 2021; Volume 788, pp. 391–399. [Google Scholar] [CrossRef]
- Brainard, J.; Juels, A.; Rivest, R.L.; Szydlo, M.; Yung, M. Fourth-factor authentication: Somebody you know. In Proceedings of the 13th ACM conference on Computer and communications security, Alexandria, VA, USA, 30 October–3 November 2006. [Google Scholar] [CrossRef]
- Sharmila, K.; Janaki, V. Necessity of fourth factor authentication with multiple variations as enhanced user authentication technique. In Proceedings of the Third International Conference on Computational Intelligence and Informatics, Singapore, 28–29 December 2018; Raju, K.S., Govardhan, A., Rani, B.P., Sridevi, R., Murty, M.R., Eds.; Advances in Intelligent Systems and Computing. Springer: Singapore, 2020; Volume 1090, pp. 491–500. [Google Scholar] [CrossRef]
- Edwards, J.; Aparicio-Navarro, F.J.; Maglaras, L.; Douligeris, C. FFDA: A novel four-factor distributed authentication mechanism. In Proceedings of the IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 27–29 July 2022; pp. 376–381. [Google Scholar] [CrossRef]
- Hemamalini, S.; Manuel, M. A fuzzy implementation of biometrics with five factor authentication system for secured banking. Int. J. Smart Sens. Adhoc Netw. 2012, 1, 238–242. [Google Scholar] [CrossRef]
- Mukhin, V.E. Multifactor authentication as a protection mechanism in computer networks. Cybern. Syst. Anal. 1999, 35, 832–835. [Google Scholar] [CrossRef]
- Ahmad, M.O. A Blockchain-based multi-factor authentication mechanism for securing smart cities. Sensors 2023, 23, 2757. [Google Scholar] [CrossRef]
- Sethuraman, S.C.; Mitra, A.; Ghosh, A.; Galada, G.; Subramanian, A. MetaSecure: A passwordless authentication for the metaverse. arXiv 2023, arXiv:2301.01770. [Google Scholar]
- Albuquerque, S.L.; Miosso, C.J.; da Rocha, A.F.; Gondim, P.R. Multi-factor authentication protocol based on electrocardiography signals for a mobile cloud computing environment. In Mobile Computing Solutions for Healthcare Systems; Bentham Science: Sharjah, United Arab Emirates, 2023; Chapter 5; pp. 62–88. [Google Scholar]
- Zaenchkovski, A.; Lazarev, A.; Masyutin, S. Multi-factor authentication in innovative business systems of industrial clusters. In Advances in Automation IV; Springer International Publishing: Berlin/Heidelberg, Germany, 2023; pp. 271–281. [Google Scholar]
- Saqib, R.M.; Khan, A.S.; Javed, Y.; Ahmad, S.; Nisar, K.; Abbasi, I.A.; Haque, M.R.; Julaihi, A.A. Analysis and Intellectual structure of the multi-factor authentication in information security. Intell. Autom. Soft Comput. 2022, 32, 1633–1647. [Google Scholar] [CrossRef]
- Singh, C.; Singh, T.D. A 3-level multifactor authentication scheme for cloud computing. Int. J. Comput. Eng. Technol. IJCET 2019, 10, 184–195. [Google Scholar] [CrossRef]
- Patel, S.C.; Jaiswal, S.; Singh, R.S.; Chauhan, J. Access control framework using multi-factor authentication in cloud computing. Int. J. Green Comput. IJGC 2018, 9, 1–15. [Google Scholar] [CrossRef]
- Kaleem, M.; Arshad, M.J. A customizable client authentication framework (ccaf) based on multi-factor for cloud computing application. Int. J. Comput. Sci. Telecommun. IJCST 2017, 8, 18–25. [Google Scholar]
- Banyal, R.K.; Jain, P.; Jain, V.K. Multi-factor authentication framework for cloud computing. In Proceedings of the Fifth International Conference on Computational Intelligence, Modelling and Simulation (CSSIM), Seoul, Korea, 24–25 September 2013; pp. 105–110. [Google Scholar] [CrossRef]
- Patil, D.H.; Asbe, V.S.; Chavan, M.S.; Birajdar, P.L.; Joshi, G.A. A survey on private cloud storage security using multifactor authentication. J. Archit. Technol. 2019, XI, 7–11. [Google Scholar]
- Nikam, R.; Potey, M. Cloud storage security using multi-factor authentication. In Proceedings of the 2016 International Conference on Recent Advances and Innovations in Engineering (ICRAIE), Jaipur, India, 23–25 December 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Priya, K.D.; Sumalatha, L. Trusted hybrid multifactor authentication for cloud users. i-Manager’s J. Cloud Comp. 2020, 7, 12–20. [Google Scholar] [CrossRef]
- Monaswarnalakshmi, S.R.; Sai Aravindhan, C.P. Multifactor authentication in iot devices for ensuring secure cloud storage in smart banking. Int. Res. J. Eng. Technol. IRJET 2018, 5, 1307–1311. [Google Scholar]
- Hussain, M.I.; He, J.; Zhu, N.; Sabah, F.; Zardari, Z.A.; Hussain, S.; Razque, F. AAAA: SSO and MFA implementation in multi-cloud to mitigate rising threats and concerns related to user metadata. Appl. Sci. 2021, 11, 3012. [Google Scholar] [CrossRef]
- Karabulut, Z.E.; Kasapbaşı, M.C. Cloud computing integrated multi-factor authentication framework application in logistics information systems. J. Int. Trade Logist. Law JITAL 2018, 3, 50–57. [Google Scholar]
- Erdem, E.; Sandıkkaya, M.T. OTPaaS—One time password as a service. IEEE Trans. Infor. Forensics Secur. 2019, 14, 743–756. [Google Scholar] [CrossRef]
- Dhanasekaran, S.; Murugan, B.S.; Vasudevan, V. A reliable agent system for cloud service discovery using mfa technique. Int. J. Recent Technol. Eng. IJRTE 2019, 8, 682–685. [Google Scholar] [CrossRef]
- Meena, S.; Gayathri, V. Securing personal health records using advanced multi-factor authentication in cloud computing. Int. J. Recent Technol. Eng. IJRTE 2020, 8, 5133–5140. [Google Scholar] [CrossRef]
- Midha, S.; Verma, S.; Kavita; Mittal, M.; Jhanjhi, N.; Masud, M.; AlZain, M.A. A secure multi-factor authentication protocol for healthcare services using cloud-based sdn. Comput. Mater. Contin. 2023, 74, 3711–3726. [Google Scholar]
- Prabakaran, D.; Ramachandran, S. Multi-factor authentication for secured financial transactions in cloud environment. Comput. Mater. Contin. 2022, 70, 1781–1798. [Google Scholar] [CrossRef]
- Gordin, I.; Graur, A.; Potorac, A. Two-factor authentication framework for private cloud. In Proceedings of the 23rd International Conference on System Theory, Control and Computing (ICSTCC), Sinaia, Romania, 9–11 October 2019; pp. 255–259. [Google Scholar] [CrossRef]
- Kambou, S.; Bouabdallah, A. A strong authentication method for web/mobile services. In Proceedings of the 2019 6th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2019 5th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Paris, France, 21–23 June 2019; pp. 124–129. [Google Scholar] [CrossRef]
- Taher, K.A.; Nahar, T.; Hossain, S.A. Enhanced Cryptocurrency Security by Time-Based Token Multi-Factor Authentication Algorithm. In Proceedings of the 2019 International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 10–12 January 2019; pp. 308–312. [Google Scholar] [CrossRef]
- Kennedy, W.; Olmsted, A. Three factor authentication. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 212–213. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z. A secure multi factor user authentication framework for electronic payment system. In Proceedings of the 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z.; Hasan, M.K. Enhancing multi-factor user authentication for electronic payments. Inventive Computation and Information Technologie; Smys, S., Balas, V.E., Kamel, K.A., Lafata, P., Eds.; Lecture Notes in Networks and Systems; Springer: Singapore, 2021; Volume 173. [Google Scholar] [CrossRef]
- Oke, B.A.; Olaniyi, O.M.; Aboaba, A.A.; Arulogun, O.T. Multifactor authentication technique for a secure electronic voting system. Electron. Gov. Int. J. EG 2021, 17, 312–338. [Google Scholar] [CrossRef]
- Oke, B.A.; Olaniyi, O.M.; Aboaba, A.A.; Arulogun, O.T. Developing multifactor authentication technique for secure electronic voting system. In Proceedings of the 2017 International Conference on Computing Networking and Informatics (ICCNI), Lagos, Nigeria, 29–31 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Olaniyi, O.M.; Dogo, E.M.; Nuhu, B.K.; Treiblmaier, H.; Abdulsalam, Y.S.; Folawiyo, Z. A Secure Electronic Voting System Using Multifactor Authentication and Blockchain Technologies. Blockchain Applications in the Smart Era; Misra, S., Kumar Tyagi, A., Eds.; Springer International Publishing: Cham, Switzerland, 2022; pp. 41–63. [Google Scholar]
- Olaniyi, O.M.; Arulogun, O.T.; Omidiora, E.O.; Oludotun, A. Design of secure electronic voting system using multifactor authentication and cryptographic hash functions. Int. J. Comp. Inf. Technol. 2013, 2, 1122–1130. [Google Scholar]
- Abayomi-Zannu, T.P.; Odun-Ayo, I.A.; Barka, T.F. A proposed mobile voting framework utilizing blockchain technology and multi-factor authentication. J. Phys. Conf. Ser. JPCS 2019, 1378, 032104. [Google Scholar] [CrossRef]
- Rusdan, M.; Manurung, D.T. Designing of user authentication based on multi-factor authentication on wireless networks. J. Adv. Res. Dynam. Control Syst. JARDCS 2020, 12, 201–209. [Google Scholar] [CrossRef]
- Kinai, A.; Otieno, F.; Bore, N.; Weldemariam, K. Multi-factor authentication for users of non-internet based applications of blockchain-based platforms. In Proceedings of the IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; pp. 525–531. [Google Scholar] [CrossRef]
- Lee, K. A study on user access control method using multi-factor authentication for EDMS. Int. J. Secur. Its Appl. IJSIA 2013, 7, 327–334. [Google Scholar] [CrossRef]
- Santhi, S.G.; Kameswara Rao, M. Multifactor user authentication mechanism using internet of things. In Proceedings of the Second International Conference on Computer Networks and Communication Technologies, 15–16 June 2019; Smys, S., Senjyu, T., Lafata, P., Eds.; Lecture Notes on Data Engineering and Communications Technologies; Springer International Publishing: Cham, Switzerland, 2020; Volume 44, pp. 496–502. [Google Scholar] [CrossRef]
- Rao, M.K.; Santhi, S.G.; Hussain, M.A. Multi factor user authentication mechanism using internet of things. In Proceedings of the Third International Conference on Advanced Informatics for Computing Research, Shimla, India; 2019. [Google Scholar]
- Chen, Z.; Cheng, Z.; Luo, W.; Ao, J.; Liu, Y.; Sheng, K.; Chen, L. FSMFA: Efficient firmware-secure multi-factor authentication protocol for IoT devices. Internet Things 2023, 21, 100685. [Google Scholar] [CrossRef]
- Liu, J.; Zou, X.; Han, J.; Lin, F.; Ren, K. BioDraw: Reliable multi-factor user authentication with one single finger swipe. In Proceedings of the IEEE/ACM 28th International Symposium on Quality of Service (IWQoS), Hang Zhou, China, 15–17 June 2020; pp. 1–10. [Google Scholar] [CrossRef]
- Lu, D.; Huang, D.; Deng, Y.; Alshamrani, A. Multifactor user authentication with in-air-handwriting and hand geometry. In Proceedings of the International Conference on Biometrics (ICB), 20–23 February 2018; pp. 255–262. [Google Scholar] [CrossRef]
- Abiew, N.A.K.; Jnr, M.D.; Banning, S.O. Design and implementation of cost effective multi-factor authentication framework for ATM systems. Asian J. Res. Comp. Sci. (AJRCoS) 2020, 5, 7–20. [Google Scholar] [CrossRef]
- Bouck-Standen, D.; Kipke, J. Multi-factor authentication for public displays using the semantic ambient media framework. In Proceedings of the ADVCOMP 2019: The Thirteenth International Conference on Advanced Engineering Computing and Applications in Sciences, Porto, Portugal, 22–26 September 2019; Rückemann, C.-P., Münster, W.-U., Eds.; International Academy, Research and Industry Association (IARIA): Athens, Greece, 2019; pp. 30–35. [Google Scholar]
- Şahan, S.; Ekici, A.F.; Bahtiyar, Ş. A multi-factor authentication framework for secure access to blockchain. In Proceedings of the 2019 5th International Conference on Computer and Technology Applications (ICCTA 2019), Istanbul, Turkey, 16–17 April 2019. [Google Scholar]
- Zin, M.Z.M.; Saidi, R.M.; Sappar, F.; Arshad, M.A. Multi-factor authentication to authorizing access to an application: A conceptual framework. J. Adv. Res. Comp. Appl. 2019, 16, 1–9. [Google Scholar]
- Al-Shqeerat, K.H.A. Securing a question-based multi-factor authentication system using LSB steganography technique. In Explore Business, Technology Opportunities and Challenges After the COVID-19 Pandemic; Springer International Publishing: Cham, Switzerland, 2023; pp. 1118–1128. [Google Scholar]
- Chunka, C.; Banerjee, S.; Sachin Kumar, G. A secure communication using multifactor authentication and key agreement techniques in internet of medical things for COVID-19 patients. Concurr. Comp. Pract. Exp. 2023, 35, e7602. [Google Scholar] [CrossRef]
- Asani, E.O.; Longe, O.B.; Balla, A.J.; Ogundokun, R.O.; Adeniyi, E.A. Secure Human-Computer Interaction: A Multi-Factor Authentication CAPTCHA Scheme. Handbook of Research on the Role of Human Factors in IT Project Management; Misra, S., Adewumi, A., Eds.; IGI Global: Hershey, PA, USA, 2020; pp. 149–163. [Google Scholar]
- Lala, O.G.; Aworinde, H.O.; Ekpe, S.I. Towards A secured financial transaction: A multi-factor authentication model. In Proceedings of the 25th iSTEAMS Trans-Atlantic Multidisciplinary Virtual Conference, Laboratoire Jean Kuntzmann, Universite Laboratoire Jean Kuntzmann, Universite Grenoble, Alpes, France; 2020; pp. 139–146. [Google Scholar]
- Alghamdi, A.A. A verification system for multi-factor authentication for e-healthcare architectures. Arab J. Sci. Publ. (AJSP) 2021, 31, 1–44. [Google Scholar]
- Tanveer, M.; Badshah, A.; Khan, A.; Alasmary, H.; Chaudhry, S. CMAF-IIoT: Chaotic map-based authentication framework for industrial internet of things. Internet Things 2023, 23, 100902. [Google Scholar] [CrossRef]
- Alasmary, H.; Tanveer, M. ESCI-AKA: Enabling secure communication in an iot-enabled smart home environment using authenticated key agreement framework. Mathematics 2023, 11, 3450. [Google Scholar] [CrossRef]
- Aleluya, E.R.M.; Vicente, C.T. Faceture ID: Face and hand gesture multi-factor authentication using deep learning. Procedia Comput. Sci. 2018, 135, 147–154. [Google Scholar] [CrossRef]
- Carrillo-Torres, D.; Pérez-Díaz, J.A.; Cantoral-Ceballos, J.A.; Vargas-Rosales, C. A novel multi-factor authentication algorithm based on image recognition and user established relations. Appl. Sci. 2023, 13, 1374. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P.; Wang, C. Efficient multi-factor user authentication protocol with forward secrecy for real-time data access in WSNs. ACM Trans. Cyber-Physical Syst. 2020, 1, 1–25. [Google Scholar] [CrossRef]
- Alsirhani, A.; Ezz, M.; Mostafa, A.M. advanced authentication mechanisms for identity and access management in cloud computing. Comp. Syst. Sci. Eng. 2022, 43, 967–984. [Google Scholar] [CrossRef]
- Roy, S.; Das, A.K.; Chatterjee, S.; Kumar, N.; Chattopadhyay, S.; Rodrigues, J. Provably secure fine-grained data access control over multiple cloud servers in mobile cloud computing based healthcare applications. IEEE Trans. Ind. Inf. 2019, 1, 457–468. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K. Unified biometric privacy preserving three-factor authentication and key agreement for cloud-assisted autonomous vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Qui, S.; Wang, D.; Xu, G.; Kumari, S. Practical and provably secure three-factor authentication protocol based on extended chaotic maps for mobile lightweight devices. IEEE Trans. Dependable Secur. Comp. 2022, 20, 1338–1351. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, D. Understanding failures in security proofs of multi-factor authentication for mobile devices. IEEE Trans. Infor. Forensics Secur. 2022, 18, 597–612. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, D.; Cheng, C.; He, D. Quantum2FA: Efficient quantum-resistant two-factor authentication scheme for mobile devices. IEEE Trans. Dependable Secur. Comp. 2021, 20, 193–208. [Google Scholar] [CrossRef]
- Kaur, S.; Kaur, G.; Shabaz, M. A Secure two-factor authentication framework in cloud computing. Secur. Commun. Netw. 2022, 2022, 7540891. [Google Scholar] [CrossRef]
- Otta, S.; Panda, S.; Gupta, M.; Hota, C. A Systematic survey of multi-factor authentication for cloud infrastructure. Future Internet MDPI 2023, 15, 146. [Google Scholar] [CrossRef]
- Lee, J.; Kim, M.; Yu, S.; Park, K.; Park, Y. A secure multi-factor remote user authentication scheme for cloud-IOT applications. In Proceedings of the International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019. [Google Scholar] [CrossRef]
- Babu, R.; Badirova, A.; Moghaddam, F.; Wieder, P.; Yahyapour, R. Authentication and access control in cloud-based systems. In Proceedings of the Fourteenth International Conference on Ubiquitous and Future Networks (ICUFN), Paris, France, 4–7 July 2023. [Google Scholar] [CrossRef]
- Gordin, I.; Graur, A.; Vlad, S. Adomnitei, Moving forward passwordless authentication: Challenges and implementations for the private cloud. In Proceedings of the 20th RoEduNet Conference: Networking in Education and Research (RoEduNet), Iasi, Romania, 4–6 November 2021. [Google Scholar] [CrossRef]
| Ref. | Authentication Technique | Security Factors | Factor Classification | Environment |
|---|---|---|---|---|
| [38] | MFA + SHA 1 + AES- 128-CBC | Encrypted Password, OTP based on OOB, Email Account, Mobile Number, Count of mouse clicks | SYK + SYH | Cloud Computing |
| [39] | MFA | PIN/Password, Biometrics, SMS OTP | SYH + SYA | Cloud Computing |
| [40] | MFA | Username-Password, Email Account, Mobile Number, PIN, OTP | SYK + SYH | Cloud Computing |
| [41] | MFA | Secret-splitting key, OTP, IMEI number | SYH | Cloud Computing |
| [42] | MFA + CP-ABE | Username—Password, QR Code-based OTP | SYK + SYH | Private Cloud Storage |
| [43] | MFA + CP-ABE | Username—Password, QR Code-based OTP | SYK + SYH | Private Cloud Storage |
| [44] | MFA + VGG face model | Username—Password, Security Questions, Mobile OTP, Face image | SYK + SYH + SYA | Cloud Storage |
| [45] | MFA | Username—Password, OTP, Fingerprints | SYK + SYH + SYA | Cloud Storage in Smart Banking |
| [46] | MFA + SSO | SMS OTP, Call on Phone, App approval | SYH | User’s Metadata in a Multi-Cloud |
| [47] | MFA | Face Verification, NFC Card Authentication, Geofence Location, Temporal Data Verification | SYH + SYA | Cloud-based Logistics IS |
| [48] | 2FA + PSK | Username—Password, OTP | SYK + SYH | Cloud-based OTP Services |
| [49] | MFA | Username—Password, Secret key to AES technique, Biometrics | SYK + SYH + SYA | Multiple Agents Cloud-based Search Engine |
| [50] | MFA + RSA + Hash Func | Contextual, Sign encryption, Iris Biometric | SYH + SYA | Cloud Health Care |
| [51] | MFA + Hash Func | Username and Password, Biometrics, Timestamp, Random number nonce | SYK + SYH + SYA | Cloud-based SDN Health Care |
| [52] | MFA + ECC | Username and Low Entropy, Password, Fingerprints, Voice print, IMSI identity | SYK + SYH + SYA | Cloud-based Financial Transactions |
| [53] | 2FA | Username and Password, TOTP | SYK + SYH | Private Cloud |
| [54] | 2FA | OTP, IoT Token | SYH | Cloud-based Web Services |
| Authentication Method | Priority |
|---|---|
 | 3 |
 | 2 |
 | 1 |
| Method Selector | Authentication Method | Next Auth Method | Priority Reason | ||
|---|---|---|---|---|---|
| User Name |  |  |  | ||
| 5 | 4 | 4 |  | Higher Priority | |
| Percentage | 38.46% | 30.77% | 30.77% | ||
| 5 | 5 | 4 |  | Lower Usage | |
| Percentage | 35.71% | 35.71% | 28.58% | ||
| 5 | 5 | 5 |  | Higher Priority | |
| Percentage | 33.33% | 33.33% | 33.33% | ||
| Ref. | Usability Testing | Scalability | Flexibility | Affordability |
|---|---|---|---|---|
| [92] | Moderate | Effective | Effective | Effective |
| [93] | Effective | Effective | Effective | Moderate |
| [94] | Moderate | Effective | Moderate | Moderate |
| [95] | Moderate | Effective | Effective | Moderate |
| [96] | Minimal | Moderate | Effective | Minimal |
| Proposed MFA | Effective | Effective | Effective | Effective |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mostafa, A.M.; Ezz, M.; Elbashir, M.K.; Alruily, M.; Hamouda, E.; Alsarhani, M.; Said, W. Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication. Appl. Sci. 2023, 13, 10871. https://doi.org/10.3390/app131910871
Mostafa AM, Ezz M, Elbashir MK, Alruily M, Hamouda E, Alsarhani M, Said W. Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication. Applied Sciences. 2023; 13(19):10871. https://doi.org/10.3390/app131910871
Chicago/Turabian StyleMostafa, Ayman Mohamed, Mohamed Ezz, Murtada K. Elbashir, Meshrif Alruily, Eslam Hamouda, Mohamed Alsarhani, and Wael Said. 2023. "Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication" Applied Sciences 13, no. 19: 10871. https://doi.org/10.3390/app131910871
APA StyleMostafa, A. M., Ezz, M., Elbashir, M. K., Alruily, M., Hamouda, E., Alsarhani, M., & Said, W. (2023). Strengthening Cloud Security: An Innovative Multi-Factor Multi-Layer Authentication Framework for Cloud User Authentication. Applied Sciences, 13(19), 10871. https://doi.org/10.3390/app131910871







