A Novel Robust Geolocation-Based Multi-Factor Authentication Method for Securing ATM Payment Transactions
Abstract
:1. Introduction
- Design a novel geolocation-based multi-factor authentication method for improving the security of ATM payment transactions, where it also employs a novel design approach toward further controlling the ownership of transactions.
- Discuss how the proposed approach does not require any major modifications to the existing banking infrastructure, which would be an ideal solution for securing ATM transactions around the world.
- Highlight the implementation results, pros, and cons of the proposed approach, along with how the proposed approach can be further extended.
- To validate our work and differentiate it from recent similar research in terms of security aspects, we provide a brief comparison of our work with the state of the art.
2. Literature Review and Related Work
- Stealing from the database
- Many retailers prefer to keep debit/credit card numbers in online databases to facilitate customer purchases. According to recent reports, attackers have breached merchant websites and stolen databases containing millions of debit/credit card details [1,5], e.g., the compromising of Capital One, a US credit card issuer, which led to the exposure of 106 million customers’ credit card information in 2019 [6], and the compromising of the TJX company chain, which led to the exposure of 94 million customers’ credit card information in 2006 [6].
- Sniffing/packet intercepting
- During online debit/credit card payments, an attacker sniffs data packets to infer confidential payment information. In most circumstances, the attacker does not need to decrypt the presumably encrypted online payment packets (e.g., through Secure Sockets Layer) [1,3,5], but instead deceives the consumer into believing they are visiting a legitimate site while in fact, they are viewing the attacker’s spoofing site.
- Shoulder surfing
- Skimming
- Keypad overlays
- This is a technique that is meant to fit in with the normal ATM keypad and this allows it to go unnoticed. The overlay allows the keypad beneath it to work properly, allowing the person to operate the ATM without any difficulty; when a person punches their PIN onto the fake keypad installed over the existing ATM keypad, an overlay records and captures keystrokes (e.g., customer PIN). Simultaneously, the ATM card slot overlays/records the secret data from the ATM card’s magnetic strip. Using blank cards, the fraudster combines information in their computer to clone the ATM card, and nowadays, this is becoming a significant threat [3].
- Knowledge factor (something you know)
- Possession factor (something you have)
- Inherence factor (something you are)
- Protection against password attacks
- Compliance requirements
- User-friendly
- EMV
- EMV is a widely adopted global standard for chip-based payment cards. EMV cards contain embedded microchips that generate dynamic authentication codes for each transaction [3,4,8]. When the card is inserted into an EMV-enabled ATM or POS terminal, the chip communicates with the terminal to verify the card’s authenticity and the cardholder’s identity. This method makes it difficult for fraudsters to clone or counterfeit cards [26,27,28,29].
- PIN
- Biometric authentication
- Some modern ATMs and POS systems are equipped with biometric authentication methods, such as fingerprint scanners or facial recognition. Biometric data provides a highly secure way to verify the cardholder’s identity [21,22,23,30,31,32]. However, the major drawback of biometric approaches is that they require large systems with very high power and processing capability with high implementation and deployment costs.
- OTP
- The use of OTPs as a second layer of authentication has been extensively studied. OTPs sent via SMS, email, or generated through authenticator apps add an extra security layer, protecting against unauthorized access even if the primary authentication credentials (e.g., PIN) are compromised [3,4,5]. However, concerns have been raised regarding the reliance on mobile networks and email security.
- Voice recognition
- Voice recognition technology has also been investigated for ATM authentication. Early studies indicate that voice-based systems can be vulnerable to voice-mimicking attacks, which raises concerns about their reliability as a standalone authentication method. However, when used in conjunction with other factors, such as location-based authentication, voice recognition can be a valuable component of a multi-layered security approach [9,21,22,23,24,33,34,35].
3. Proposed Solution
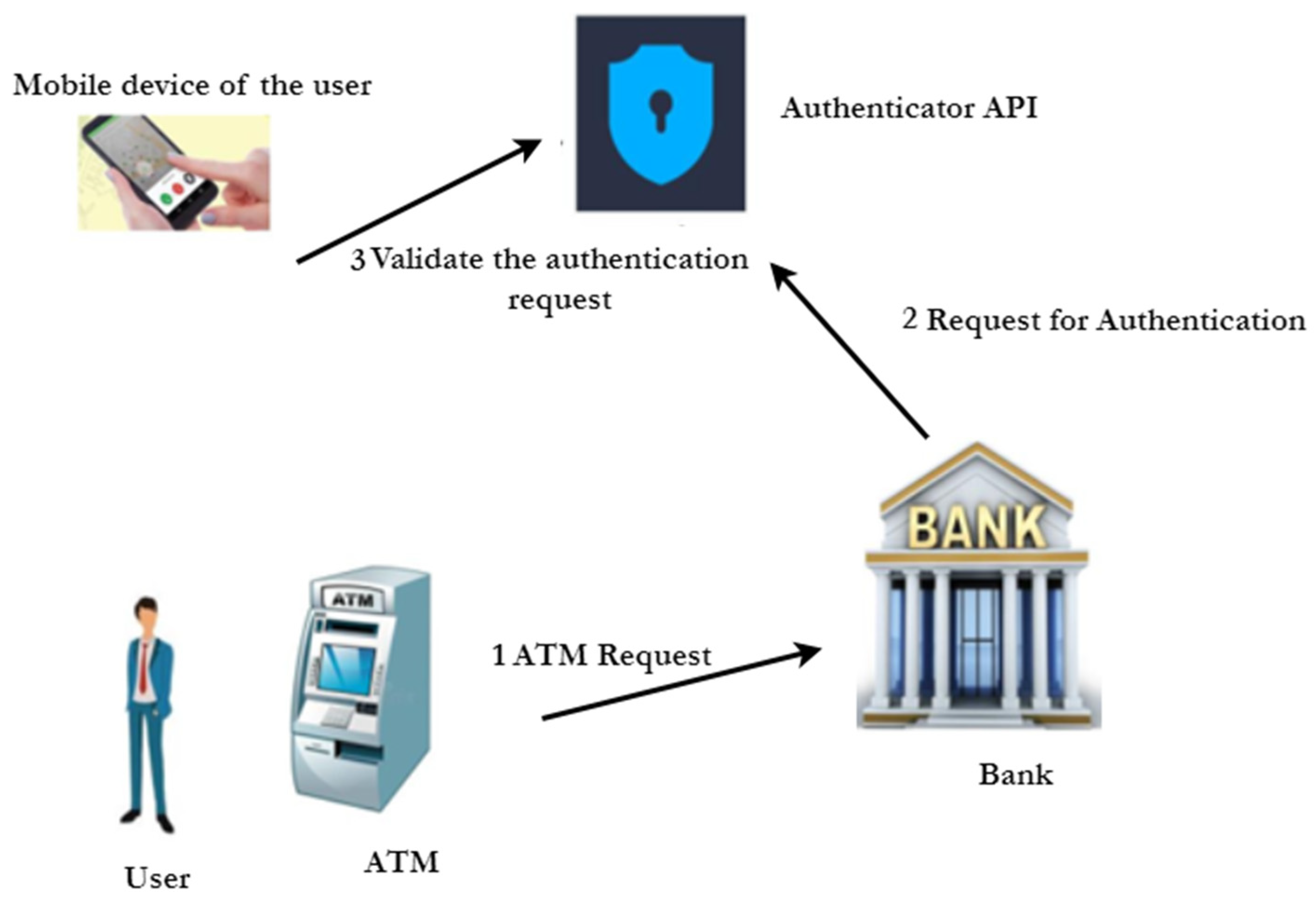
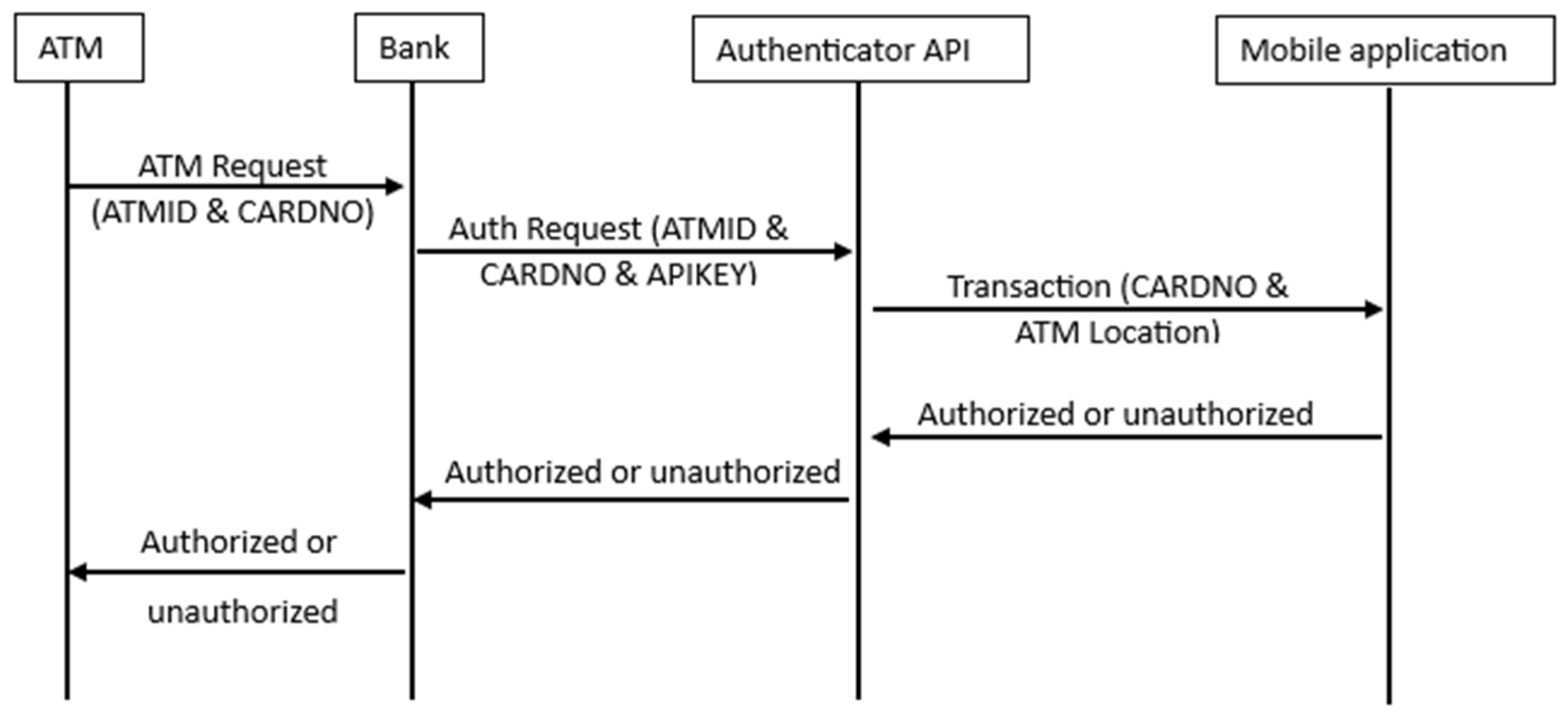
- Step 1: The user makes a transaction request (ATMID, CARDNO) at the ATM.
- Step 2: The bank receives the transaction request and fetches BankID and APIKEY.
- Step 3: The bank sends an authentication request (Input ATMID, CARDNO, APIKEY) to an authenticator API.
- Step 4: The authentication API fetches data from user’s authenticator mobile app.
- Step 5: IF Authenticated? Then
- IF Request amount < withdrawal limit Then
- Go to Step 6.
- Else
- Go to step 7.
- Else
- Go to Step 7.
- Step 6: Approve the transaction.
- Step 7: Deny the transaction.
3.1. Design the Simulation Environment
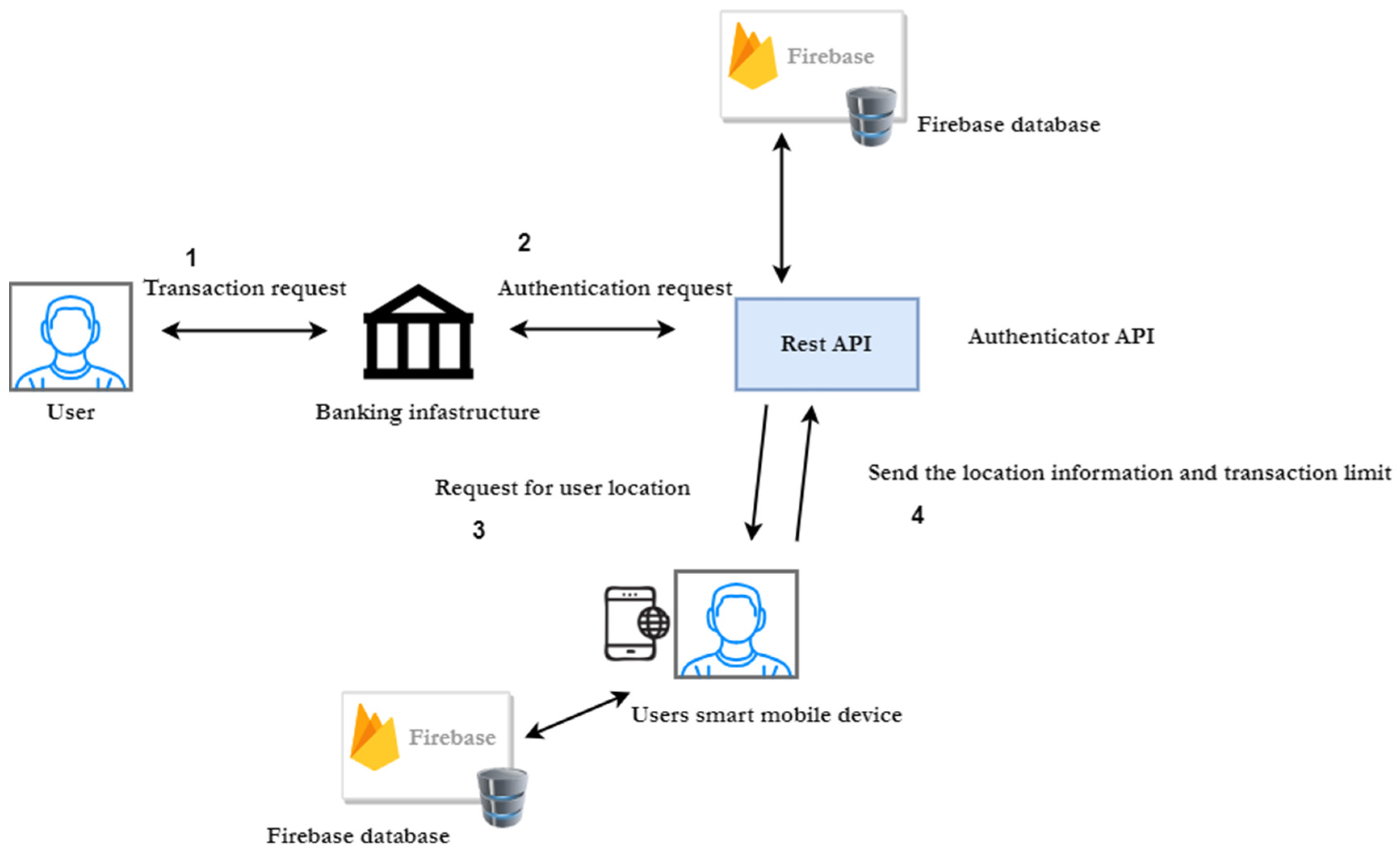
3.2. Implementation of Geolocation-Based Authentication and Rest API
- Step 1: The API receives an authentication request from the bank with the ATM location.
- Step 4: The authentication API fetches data from the user’s authenticator mobile app regarding the user’s current location.
- Step 5: IF ATM location and users’ current location match? Then
- IF Request amount < withdrawal limit Then
- Go to Step 6.
- Else
- Go to step 7.
- Else
- Go to Step 7.
- Step 6: Approve the transaction.
- Step 7: Deny the transaction.
- Step 8: Send the status (approval or denial) of the transaction to the bank.
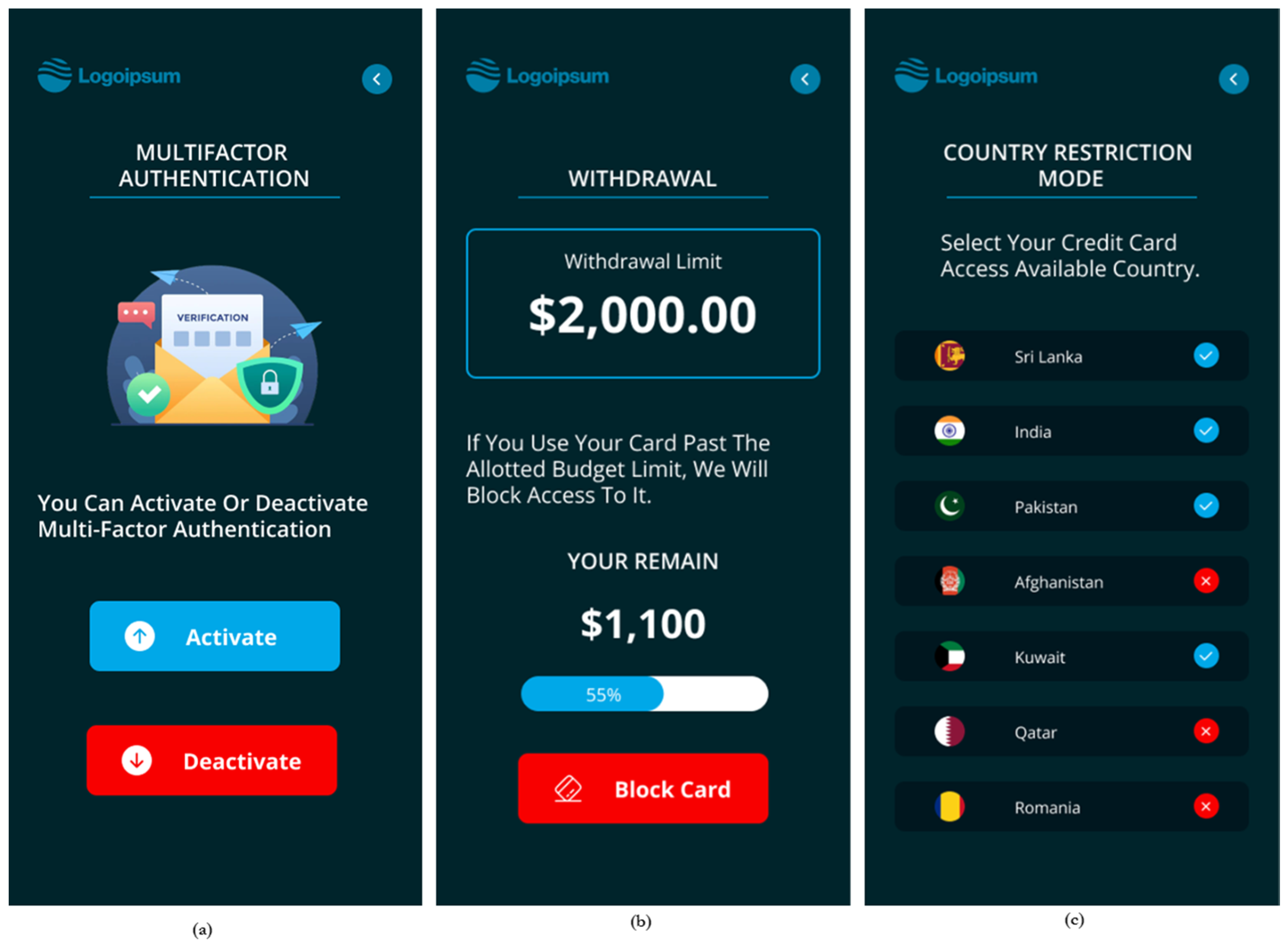
3.3. Mobile Application Implementation
3.4. Implementation of the Control Panel
4. Implementation
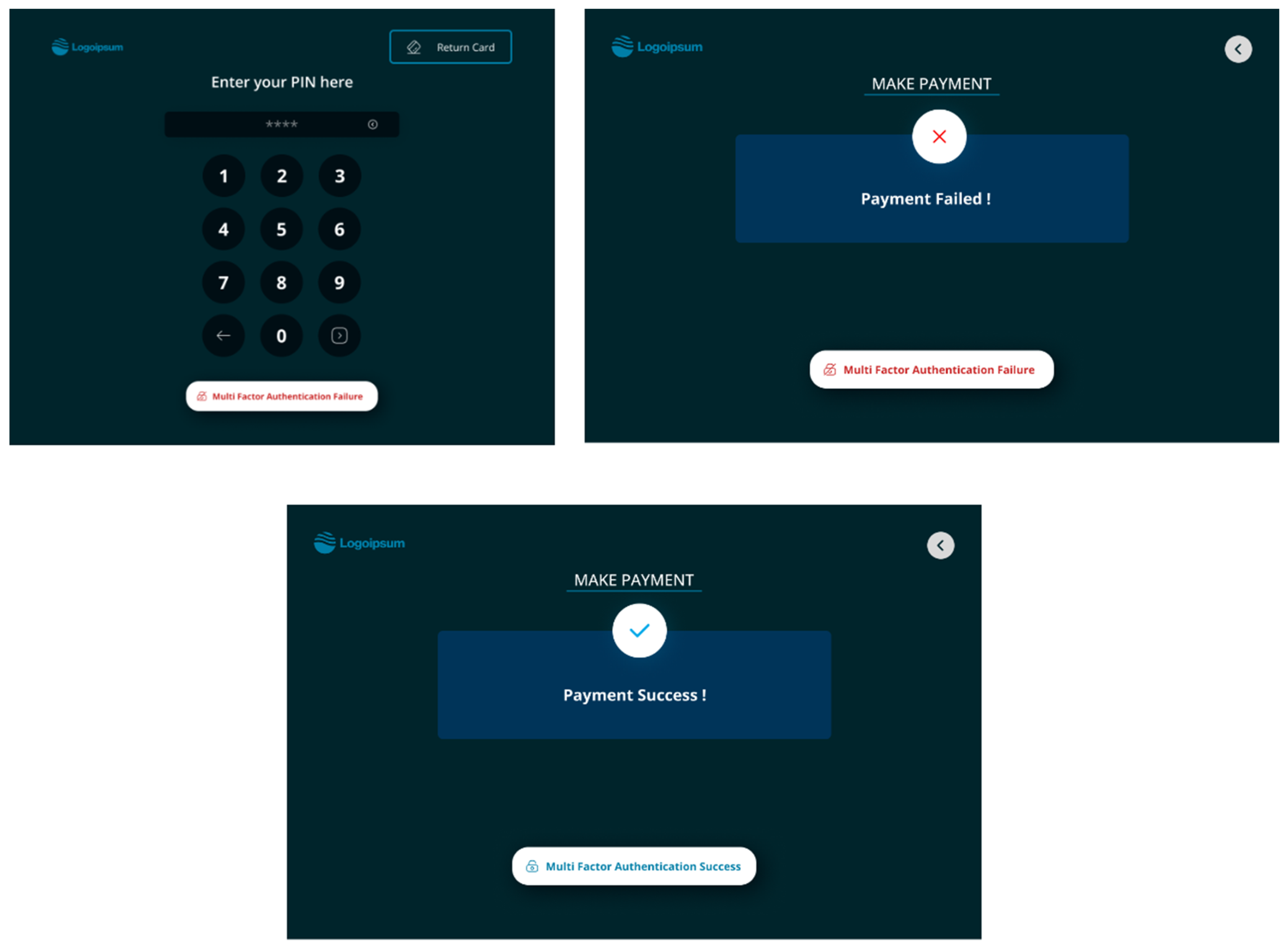
4.1. ATM Inquiry
4.2. Mobile Authentication and Control
4.3. Status of the ATM Inquiry
5. Results and Discussion
Analysis of Security Testing
- Ensures data confidentiality and integrity
- As per the prototype development, we employed the Google Firebase database to store confidential user information and transaction information, which are protected by Firebase’s security standards. The data stored on Firebase were encrypted with the AES-256 algorithm, and each encryption key was also encrypted with a regularly rotated set of master keys, providing better security over stored data. On the other hand, all the communication links were secured using the HTTPS protocol, making sure that the data sent between the user and the server could not be tampered with during transmission, guaranteeing confidentiality and data integrity.
- Provides robust authentication
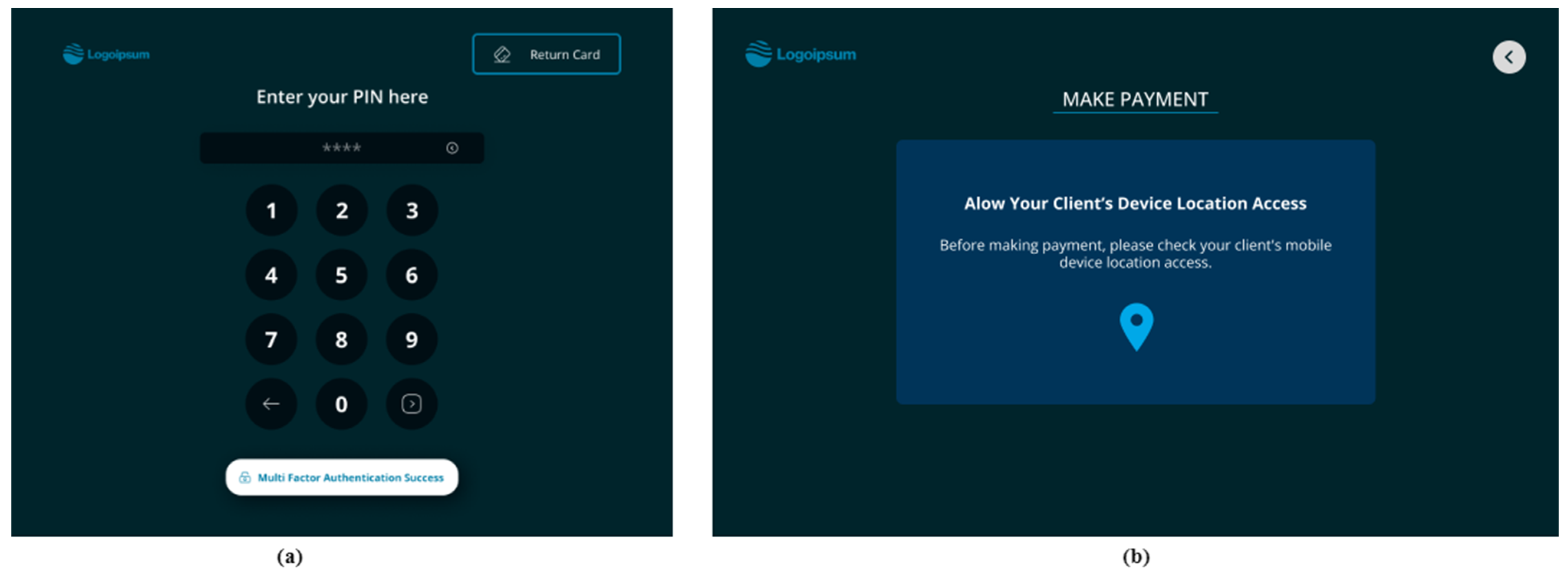
- The proposed multi-factor authentication in the study used a PIN, the user’s smart mobile device, and the location of the device as the authentication factors. As all modern smartphones are equipped with GPS location services, the proposed method allowed users to authenticate in a convenient and more secure way, as once the user activated the multi-factor authentication from the mobile app, the transactions were authenticated, matching the user’s GPS location with the ATM location.
- Ensure user privacy.
- All the database records and the data that communicate over the entire ecosystem were encrypted, thus protecting the user and the data privacy.
- Protection against theft or loss
- In the case of theft or loss of the card, the authenticator app enabled users to block the card at any time, allowing them to protect their bank accounts.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Acronym | Description |
| ATM | Automated Teller Machine |
| PIN | Personal Identification Number |
| OTP | One-Time Password |
| EMV | Europay, Mastercard and Visa |
| MFA | Multi-Factor Authentication |
| 2FA | Two-Factor Authentication |
| PCI DSS | Payment Card Industry Data Security |
| GDPR | General Data Protection Regulation |
| POS | Point of Sale |
| RFID | Radio Frequency Identification |
| NFC | Near Field Communication |
| API | Application Programming Interface |
| GPS | Global Positioning System |
| IDE | Integrated Development Environment |
| AES | Advanced Encryption Standard |
| HTTPS | Hypertext Transfer Protocol Secure |
References
- Pranith, C.V.; Sujith, V.L.; Kiran, K.S.; Goutham, P.; Kiran, K.V.D. A Multifactor Security Protocol for Wireless Payment-Secure Web Authentication Using Mobile Devices. In Cybernetics, Cognition and Machine Learning Applications; Gunjan, V.K., Suganthan, P.N., Haase, J., Kumar, A., Eds.; Springer Nature: Singapore, 2023; pp. 29–38. [Google Scholar] [CrossRef]
- Bissada, A.; Olmsted, A. Mobile multi-factor authentication. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 210–211. [Google Scholar] [CrossRef]
- Sankhwar, S.; Pandey, D. A Safeguard against ATM Fraud. In Proceedings of the 2016 IEEE 6th International Conference on Advanced Computing (IACC), Bhimavaram, India, 27–28 February 2016; pp. 701–705. [Google Scholar] [CrossRef]
- Gold, S. The evolution of payment card fraud. Comput. Fraud. Secur. 2014, 2014, 12–17. [Google Scholar] [CrossRef]
- Yang, S.; Meng, J. Research on Multi-factor Bidirectional Dynamic Identification Based on SMS. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 12–14 October 2018; pp. 1578–1582. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, X. A security-enhanced one-time payment scheme for credit card. In Proceedings of the 14th International Workshop Research Issues on Data Engineering: Web Services for e-Commerce and e-Government Applications, 2004. Proceedings, Boston, MA, USA, 28–29 March 2004; pp. 40–47. [Google Scholar] [CrossRef]
- Kish, L.B.; Entesari, K.; Granqvist, C.-G.; Kwan, C. Unconditionally Secure Credit/Debit Card Chip Scheme and Physical Unclonable Function. Fluct. Noise Lett. 2017, 16, 1750002. [Google Scholar] [CrossRef]
- Jerry Gao, J.C. A Wireless Payment System. In Proceedings of the Second International Conference on Embedded Software and Systems (ICESS’05), Xi’an, China, 16–18 December 2005; pp. 367–374. [Google Scholar] [CrossRef]
- Greene, C.; Stavins, J. Did the Target Data Breach Change Consumer Assessments of Payment Card Security? Social Science Researh Network: Rochester, NY, USA, 2016; Available online: https://papers.ssrn.com/abstract=2818262 (accessed on 5 July 2023).
- ATM/PoS Malware ‘Recovers’ from COVID-19, with the Number of Attacks Continuing to Grow in 2022|Kaspersky. Available online: https://www.kaspersky.com/about/press-releases/2022_atmpos-malware-recovers-from-covid-19-with-the-number-of-attacks-continuing-to-grow-in-2022 (accessed on 24 July 2023).
- Nambiar, S.; Lu, C.-T.; Liang, L.R. Analysis of payment transaction security in mobile commerce. In Proceedings of the 2004 IEEE International Conference on Information Reuse and Integration, IRI 2004., Las Vegas, NV, USA, 8–10 November 2004; pp. 475–480. [Google Scholar] [CrossRef]
- Asokan, N.; Janson, P.A.; Steiner, M.; Waidner, M. The state of the art in electronic payment systems. Computer 1997, 30, 28–35. [Google Scholar] [CrossRef]
- Téllez Isaac, J.; Sherali, Z. Secure Mobile Payment Systems. IT Prof. 2014, 16, 36–43. [Google Scholar] [CrossRef]
- Herzberg, A. Payments and banking with mobile personal devices. Commun. ACM 2003, 46, 53–58. [Google Scholar] [CrossRef]
- Chabbi, S.; Araar, C. RFID and NFC authentication protocol for securing a payment transaction. In Proceedings of the 2022 4th International Conference on Pattern Analysis and Intelligent Systems (PAIS), Oum El Bouaghi, Algeria, 12–13 October 2022; pp. 1–8. [Google Scholar] [CrossRef]
- Yeh, K.-H. A Secure Transaction Scheme with Certificateless Cryptographic Primitives for IoT-Based Mobile Payments. IEEE Syst. J. 2018, 12, 2027–2038. [Google Scholar] [CrossRef]
- Yeh, K.-H.; Su, C.; Hou, J.-L.; Chiu, W.; Chen, C.-W. A Robust Mobile Payment Scheme With Smart Contract-Based Transaction Repository. IEEE Access 2018, 6, 59394–59404. [Google Scholar] [CrossRef]
- Sharma, A.; Kansal, V.; Tomar, R.P.S. Location Based Services in M-Commerce: Customer Trust and Transaction Security Issues. Int. J. Comput. Sci. Secur. 2015, 9, 11–21. [Google Scholar]
- Konidala, D.M.; Yeun, C.Y.; Kim, K. Enhanced protocol for location-based services in ubiquitous society. In Proceedings of the IEEE Global Telecommunications Conference, GLOBECOM ’04, Dallas, TX, USA, 29 November–3 December 2004; pp. 2164–2168. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Bhattia, S.; Ali Alojail, M.; Nisar, K.; Cao, Y.; Chaudhry, S.A.; Sun, Z. Towards Secure IoT-Based Payments by Extension of Payment Card Industry Data Security Standard (PCI DSS). Wirel. Commun. Mob. Comput. 2022, 2022, 9942270. [Google Scholar] [CrossRef]
- Geolocation Drives Future of Payments; GeoComply: Vancouver, BC, Canada, 2020. Available online: https://www.geocomply.com/blog/geolocation-drives-future-of-payments/ (accessed on 6 July 2023).
- Schuman, E. Geolocation: Great for Authentication, but Far from Perfect. 2016. Available online: https://blog.sift.com/geolocation-nice-tool-authentication-far-perfect/ (accessed on 6 July 2023).
- Ashfield, J.; Shroyer, D.; Brown, D. Location Based Authentication of Mobile Device Transactions. U.S. Patent US8295898B2, 23 October 2012. Available online: https://patents.google.com/patent/US8295898B2/en (accessed on 6 July 2023).
- Securing FinTech Apps With GPS Data. Velmie. 2020. Available online: https://www.velmie.com/post/securing-fintech-apps-with-gps-data (accessed on 6 July 2023).
- Twum, F.; Nti, K.; Asante, M. Improving Security Levels in Automatic Teller Machines (ATM) Using Multifactor Authentication. IJSEA 2016, 5, 126–134. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z. Device Identity-Based User Authentication on Electronic Payment System for Secure E-Wallet Apps. Electronics 2021, 11, 4. [Google Scholar] [CrossRef]
- Sanyal, S.; Tiwari, A.; Sanyal, S. A Multifactor Secure Authentication System for Wireless Payment. In Emergent Web Intelligence: Advanced Information Retrieval; Chbeir, R., Badr, Y., Abraham, A., Hassanien, A.-E., Eds.; Springer: London, UK, 2010; pp. 341–369. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z.; Hasan, M.K.; Al-Khaleefa, A.S. A Review on Electronic Payments Security. Symmetry 2020, 12, 1344. [Google Scholar] [CrossRef]
- Sahi, A.M.; Khalid, H.; Abbas, A.F.; Zedan, K.; Khatib, S.F.A.; Al Amosh, H. The Research Trend of Security and Privacy in Digital Payment. Informatics 2022, 9, 32. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z.; Hasan, M.K. An Efficient Secure Electronic Payment System for E-Commerce. Computers 2020, 9, 66. [Google Scholar] [CrossRef]
- Liu, Y.; Huang, W.; Zhuo, M.; Zhou, S.; Li, M. Mobile Payment Protocol with Deniably Authenticated Property. Sensors 2023, 23, 3927. [Google Scholar] [CrossRef]
- Jiang, Y.; Sun, G.; Feng, T. Research on Data Transaction Security Based on Blockchain. Information 2022, 13, 532. [Google Scholar] [CrossRef]
- Hwang, Y.; Park, S.; Shin, N. Sustainable Development of a Mobile Payment Security Environment Using Fintech Solutions. Sustainability 2021, 13, 8375. [Google Scholar] [CrossRef]
- De Luca, A.; Langheinrich, M.; Hussmann, H. Towards understanding ATM security: A field study of real world ATM use. In Proceedings of the Sixth Symposium on Usable Privacy and Security, Redmond, WA, USA, 14–16 July 2010; pp. 1–10. [Google Scholar] [CrossRef]
- Singh, A.; Singh, K.; Khan, M.H.; Chandra, M. A Review: Secure Payment System for Electronic Transaction. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2012, 2, 237–243. [Google Scholar]
- An Empirical Study of Customers’ Perceptions of Security and Trust in E-Payment Systems—ScienceDirect. Available online: https://www.sciencedirect.com/science/article/pii/S1567422309000283 (accessed on 6 August 2023).
- Ceipidor, U.B.; Medaglia, C.M.; Marino, A.; Sposato, S.; Moroni, A. KerNeeS: A protocol for mutual authentication between NFC phones and POS terminals for secure payment transactions. In Proceedings of the 2012 9th International ISC Conference on Information Security and Cryptology, Tabriz, Iran, 13–14 September 2012; pp. 115–120. [Google Scholar] [CrossRef]
- Kovács, L.; David, S. Fraud risk in electronic payment transactions. J. Money Laund. Control 2016, 19, 148–157. [Google Scholar] [CrossRef]
- Chaum, D. Security without identification: Transaction systems to make big brother obsolete. Commun. ACM 1985, 28, 1030–1044. [Google Scholar] [CrossRef]
- Tsiakis, T.; Sthephanides, G. The concept of security and trust in electronic payments. Comput. Secur. 2005, 24, 10–15. [Google Scholar] [CrossRef]
- Bellare, M.; Garay, J.A.; Hauser, M.; Herzberg, A.; Krawczyk, H.; Steiner, M.; Tsudik, G.; Van Herreweghen, E.; Waidner, M. Design, implementation, and deployment of the iKP secure electronic payment system. IEEE J. Sel. Areas Commun. 2000, 18, 611–627. [Google Scholar] [CrossRef]
- Ali, G.; Dida, M.A.; Elikana Sam, A. A Secure and Efficient Multi-Factor Authentication Algorithm for Mobile Money Applications. Future Internet 2021, 13, 12. [Google Scholar] [CrossRef]
- Hassan, M.A.; Shukur, Z. A Secure Multi Factor User Authentication Framework for Electronic Payment System. In Proceedings of the 2021 3rd International Cyber Resilience Conference (CRC), Langkawi Island, Malaysia, 29–31 January 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Geolocation API Overview|Google for Developers. Available online: https://developers.google.com/maps/documentation/geolocation/overview (accessed on 9 September 2023).
- Keerthiwardane, S.S.; Wijethunga, I.A. ATM Detail Protection Using Geo-Fence Technology; Kotelawala Defence University: Rathmalana, Sri Lanka, 2020. [Google Scholar]
- How to Detect GPS Spoofing, Location & Fake GPS Spoofing in Android Apps. Available online: https://www.appdome.com/how-to/mobile-malware-prevention/android-malware-detection/detect-a-fake-gps-attack/ (accessed on 20 September 2023).
- Spens, N.; Lee, D.-K.; Nedelkov, F.; Akos, D. Detecting GNSS Jamming and Spoofing on Android Devices. NAVIGATION J. Inst. Navig. 2022, 69, 3. [Google Scholar] [CrossRef]

| Reference | Authentication Method | Discusses Either ATM or Other Sorts of Payments Transactions | Scope | Limitations |
|---|---|---|---|---|
| Pranith et al., 2023 [1] | Transaction identification code and SMS-based MFA | Other | The authors proposed a novel protocol based on MFA that uses transaction identification codes and SMS to enforce extra security for wireless payments. | The researchers did not consider the security of communication media (mobile networks). |
| Yingjiu Li and Xinwen Zhang, 2004 [6] | OTP-based authentication | Other | The researchers used a hash function in the generation of one-time credit card numbers, and by comparing with similar research, they proved their approach puts less burden on credit card issuers and can be easily deployed in both online and offline scenarios. | Having OTP provides only a basic level of security, and OTPs are vulnerable to SMS code theft and SIM swap attacks. |
| Chabbi and Araar, 2022 [15] | RFID (Radio Frequency Identification) and NFC (Near Field Communication)-based authentication | ATM | The authors introduced a novel method for payment transactions combining RFID and NFC. Overall, they proposed a protocol to secure payment transactions using an Automated Teller Machine (ATM) and a smartphone. | It is very expensive for the banking sector to adopt the NFC-enabled devices, and the NFC data can be rerouted to a device other than the one that is intended. |
| Twum et al., 2016 [25] | PIN and fingerprint-based authentication | ATM | The researchers proposed a multi-factor (PIN and fingerprint)-based authentication security arrangement to enhance the security and safety of the ATM and its users. | Introducing fingerprint-based authentication requires major modification of existing ATM/banking infrastructure. |
| Hassan et al., 2020 [30] | Cryptography-based authentication | Other | In the study, the researchers developed an efficient and secure electronic payment protocol for e-commerce where consumers can immediately connect with the merchants. | The proposed approach is only applicable to online payments. |
| Hassan and Shukur, 2021 [43] | Password, biometric, and OTP-based MFA | Other | The authors provided an MFA-based security framework for securing payment transactions. | The authors do not provide details of the implementation of their proposed method, and they are not specific about which transactions can be implemented. |
| Ali et al., 2021 [44] | PIN, biometric, and OTP-based MFA | Other | The authors proposed a novel approach combining PIN, OTP, and a biometric fingerprint to enforce extra security during mobile payment transactions. | OTPs are vulnerable to SMS code theft and SIM swap attacks, and not all modern smartphones are equipped with fingerprint readers. |
| Keerthiwardane and Wijethunga, 2020 [45] | Geolocation-based authentication | ATM | The authors proposed a novel approach for securing ATM transactions using geolocation-based (geo-fence) authentication as a substitution for PIN-based authentication. | The authors introduce their approach as a substitution for PIN-based authentication, whereas no MFA can be seen, and no implementation is provided for the proposed approach. |
| Our work | Geolocation-based MFA | ATM | We propose a novel geolocation-based MFA for authenticating ATM transactions without making major modifications to the existing banking infrastructure, and the proposed approach offers the facility to control the ownership of transactions in a convenient way (deactivate, reactivate MFA at any time, set the limit for withdrawal amount/block the card if it is stolen or lost, etc.). | The proposed solution is made in such a way as to overcome the limitations of previous work. |
| Test Case | Test Results |
|---|---|
| Verify that the user is prompted to enter a PIN before the account data are shown. | Passed |
| Verify to see whether the user has a certain amount of PIN tries. | Passed |
| Verify that if the total number of incorrect PIN tries is exceeded, the user is not permitted to proceed. | Passed |
| Verify that the PIN is presented in masked form when input. | Passed |
| Verify that the user is authorized to view account information such as available balance. | Passed |
| Verify to ensure that the proper amount of money has been withdrawn as specified by the user for cash withdrawal. | Passed |
| Verify that the user’s session timeout is not exceeded. | Passed |
| Verify that the user is not permitted to exceed the transaction limit. | Passed |
| Verify that the user is not permitted to proceed with the expired ATM card and that the appropriate error message is provided. | Passed |
| Transaction ID | Available Balance (USD) | Withdraw Limit (USD) | Request Amount (USD) | Multi-Factor Authentication ON/OFF | Payment Status | Authentication Time Using the App |
|---|---|---|---|---|---|---|
| 1 | 200 | 2000 | 100 | ON | Success | 4.2 s |
| 2 | 300 | 2000 | 400 | ON | Failed | 4.1 s |
| 3 | 3500 | 2000 | 50 | ON | Success | 3.9 s |
| 4 | 700 | 2000 | 500 | ON | Success | 3.9 s |
| 5 | 800 | 2000 | 600 | ON | Success | 3.9 s |
| 6 | 900 | 2000 | 900 | ON | Failed | 4.0 s |
| 7 | 4000 | 2000 | 2500 | ON | Failed | 4.1 s |
| 8 | 5000 | 2000 | 3000 | ON | Failed | 4.0 s |
| 9 | 1200 | 2000 | 600 | ON | Success | 3.9 s |
| 10 | 500 | 2000 | 400 | OFF | Success | 3.9 s |
| 11 | 1000 | 2000 | 600 | OFF | Failed | 3.7 s |
| 12 | 4500 | 2000 | 700 | OFF | Failed | 4.1 s |
| 13 | 3200 | 2000 | 800 | OFF | Failed | 4.1 s |
| 14 | 1600 | 2000 | 300 | OFF | Failed | 4.0 s |
| 15 | 2500 | 2000 | 3400 | OFF | Failed | 3.8 s |
| 16 | 500 | 2000 | 2100 | OFF | Failed | 3.7 s |
| 17 | 500 | 2000 | 150 | OFF | Failed | 3.7 s |
| 18 | 7500 | 2000 | 250 | OFF | Failed | 3.8 s |
| 19 | 450 | 2000 | 750 | OFF | Failed | 3.7 s |
| 20 | 340 | 2000 | 1500 | OFF | Failed | 3.7 s |
| Security Features | [1] | [6] | [15] | [25] | [30] | [43] | [44] | Our Solution |
|---|---|---|---|---|---|---|---|---|
| Provides data confidentiality | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Provides data integrity | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Ensures data privacy | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Ensures user privacy | ✗ | ✓ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ |
| Provides robust authentication | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Prevention of social engineering attacks | ✗ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ |
| Protection against lost or stolen card | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Prevention of SMS code theft and SIM swap attacks | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ |
| Prevention of PIN-guessing attacks | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Prevention of brute-force attacks | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Prevention of MITM attacks/packet intercepting | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Prevention of Shoulder surfing | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Prevention of Skimming attacks | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Prevention of Keypad overlay attacks | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Prevention of GPS spoofing attacks | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Prevention of GPS jamming | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alabdulatif, A.; Samarasinghe, R.; Thilakarathne, N.N. A Novel Robust Geolocation-Based Multi-Factor Authentication Method for Securing ATM Payment Transactions. Appl. Sci. 2023, 13, 10743. https://doi.org/10.3390/app131910743
Alabdulatif A, Samarasinghe R, Thilakarathne NN. A Novel Robust Geolocation-Based Multi-Factor Authentication Method for Securing ATM Payment Transactions. Applied Sciences. 2023; 13(19):10743. https://doi.org/10.3390/app131910743
Chicago/Turabian StyleAlabdulatif, Abdullah, Rohan Samarasinghe, and Navod Neranjan Thilakarathne. 2023. "A Novel Robust Geolocation-Based Multi-Factor Authentication Method for Securing ATM Payment Transactions" Applied Sciences 13, no. 19: 10743. https://doi.org/10.3390/app131910743
APA StyleAlabdulatif, A., Samarasinghe, R., & Thilakarathne, N. N. (2023). A Novel Robust Geolocation-Based Multi-Factor Authentication Method for Securing ATM Payment Transactions. Applied Sciences, 13(19), 10743. https://doi.org/10.3390/app131910743







