Featured Application
The proposed key management scheme provides a solution to the communication security problems of UAV swarms in denied environments, which achieves secure establishment and update of keys of UAV swarms in denied environments.
Abstract
As resources provided by single unmanned aerial vehicles (UAVs) are limited, we propose a cross-platform UAV swarm key management scheme for task scenarios in denied environments. In denied environments where the communication link is open and the UAV nodes may go invalid, secure communication is often at stake. To solve this problem, we propose a key management scheme which, based on the Chinese remainder theorem (CRT) and the Hash function, constructs a swarm key by combining the local key and the session key to reduce the overhead of individual UAV nodes in the swarm. Meanwhile, the swarm head node constructs broadcast messages according to the key update needs, which reduces the overhead of the member nodes, improves the efficiency of key updating, and fulfills the key establishment and updating of the UAV swarm. Experiments show that our proposed scheme has forward and backward security and can defend against collusion attacks and replay attacks; our method was compared with other methods on the MIRACL cryptographic library in Visual Studio 2019, and it was found that our method has a lower computing and communication overhead, provides a solution to cross-platform key management of UAV swarms in denied environments, and ensures safe communication of UAVs in the swarm.
1. Introduction
With advances in defense systems, unmanned aerial vehicles (UAVs) performing tasks under intensive firepower and strong electromagnetic interference have become a hot research topic. However, singular platforms and UAV nodes, because of limited computing and load capacity, are subject to influences from distance, landform, and the environment when performing tasks, and hence suffer low efficiency and cannot fulfill long-distance remote tasks [1]. In December 2020, DARPA released the test results of its dynamic adaptive network in the Air Force Research Laboratory, and in the test, the uninterrupted connection of datalinks like LNK16, Tactical Targeting Networking Technology (TTNT), Common Data Link (CDL), and Wi-Fi networks was achieved in the simulated competing environment [2]. In 2020, France tested the collaborations between five Rafale aircrafts, one airborne early-warning aircraft, and a UAV; in January 2021, France developed the “Mosquito” UAV, which is scheduled to fly in late 2023, for combat in collaboration with the manned “loyal wingman” crafts [3]. In real-world scenarios, there is a trend towards clustering, automation, and intelligence of UAVs in performing tasks [4]; through ad-hoc networks, UAVs collaborate intelligently in complex environments to complete assigned tasks, which effectively extends the task scenarios and the efficiency of UAVs.
In denied environments, there are two types of communication links for UAV swarms: control links and data links [5], both of which rely on wireless communication channels for message transmission. In addition, because of the limited resources of individual UAV nodes, the UAVs are delivered through the delivery platform to exchange information and regroup into a new task swarm according to the environment and task demand. However, the UAV swarm is susceptible to security threats and attacks [6,7] in the open, wireless, and denied environment in the sky. In particular, during cross-platform regrouping and variations in the network topology, the attackers can easily launch attacks by intercepting, tampering with or forging data. Therefore, it is crucial to encrypt the communication links of UAVs to ensure security and confidentiality of data transmission when the UAV swarm is performing tasks in a denied environment [8]. Therefore, here we propose a cross-platform key management scheme for a UAV swarm in denied environments, with a vision to achieve secure and efficient management of UAV keys in the denied environment and improve the efficiency of the UAV swarm in fulfilling tasks.
2. Preliminaries and Definitions
2.1. Preliminaries
This section introduces two notions that will be used in our scheme: the Chinese remainder theorem (CRT) and the Hash function [9]:
2.1.1. Hash Function
The Hash function [10] is a popular encryption algorithm widely used in security applications and network protocols like message authentication, digital signature, password protection, intrusion detection, virus detection, and construction of pseudorandom functions. The security requirements of the Hash function h(·) are as follows:
- Unidirectionality (preimage resistance): , and is given.
- Weak collision resistance (second preimage resistance): for , it is computationally impossible to find with .
- Strong collision resistance (collision resistance): it is computationally impossible to find some pair (x, y) such that H(x) = H(y).
2.1.2. Chinese Remainder Theorem (CRT)
The Chinese remainder theorem (CRT) is a crucial theorem in the number theory, which performs recovery and construction through congruences, described as follows: let such that , and for any tuple , where , construct a system of congruences ; let , such that has a unique solution, i.e., .
2.2. Definitions
For the sake of clear description and interpretation, the symbols used in the paper are defined, as shown in Table 1.

Table 1.
Definitions of symbols used in this study.
2.3. Division of Task Stages
The denied environment is characterized by long-distance combat, fierce confrontation in the electromagnetic and physical fields, and high risks to manned equipment, making it impossible for most UAVs to fulfill tasks. According to DARPA’s Collaborative Operations in Denied Environment (CODE) program [11], the UAV swarm’s task execution in a denied environment is divided into three stages: the transport and delivery stage, the UAV arrival and regrouping stage, and the collaboration stage. Stage 1 starts as the delivery platform departs from the base and ends as the platform arrives at the safe region and finishes the delivery of the UAV; Stage 2 starts as the new UAV swarm is constructed and ends as the UAV arrives at the target region; Stage 3 starts as the UAV arrives at the target region and ends as the UAV completes the automatic collaboration tasks, as shown in Figure 1.
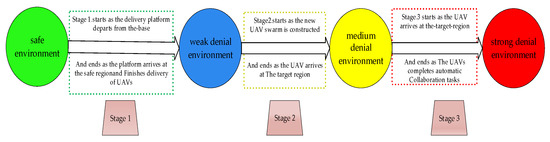
Figure 1.
Division of task stages of UAV swarms in denied environments.
In denied environments, the UAV swarms often face both geographic and physical denial. The major denial conditions and denial intensity in different stages of a task (as shown in Figure 1) are analyzed, and the specifics are shown in Table 2.

Table 2.
Denial intensity at different stages of a task.
3. Cross-Platform Key Management of UAV Swarms in Denied Environments
3.1. Key Parameter Presetting in the Transport and Delivery Stage
The network model in this study consists of the transport and delivery platform and UAV nodes. The delivery platform can be a mother ship, a large-scale transport plane, or a land-based launcher truck with strong capacities for computing, communication, and storage, which presets the key parameters and initializes the system as a top-level key management center (KMC), as shown in Figure 2.
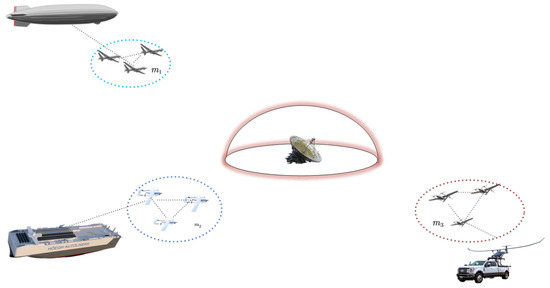
Figure 2.
UAV swarm network in transport and delivery stage.
The UAV swarms are initialized before being launched to the sky. Suppose there are m delivery platforms engaged in a given task; the key management center of the j-th platform is , and the identification label of is . In the delivery stage, presets a private key to the UAVs delivered from the same delivery platform. Security channels between platforms are created through shared keys before execution of a task; selects the node update key seed , the global key , and the set of prime numbers , which are transmitted to the delivery platform engaged in the task through the security channel, where , and for any , is satisfied; then, the configures the key parameters for its UAV swarm. The specific step of the algorithm is as follows (Algorithm 1):
| Algorithm 1 System Initialization |
3.2. Private Key Establishment in the Regrouping and Arrival Stage
In the denied environment, UAVs transported by different platforms vary in their model and load module. Normally, heterogeneous UAVs are reorganized into a full-featured UAV swarm to fulfill specific tasks, as shown in Figure 3.
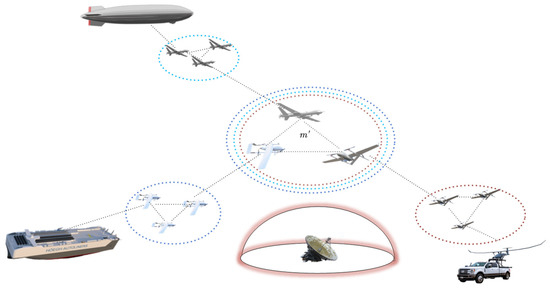
Figure 3.
Network model in the arrival stage.
For the process of regrouping and private key establishment, this study puts forth a scheme in which the regrouped UAVs select a swarm head as per specific rules; and for the scenario of a cross-platform UAV swarm performing tasks in a denied environment, the improved LEACH algorithm is employed for the swarm head selection in this study. The new swarm selects the swarm head in the order of priority: the priority level of the UAV nodes from the same platform is determined by their ID, and a smaller ID indicates higher priority. Before the swarm head is identified, the UAV node sends its ID information to other nodes in the same swarm through the global key ; after receiving the ID information, other nodes compute to identify whether it is the node of the highest priority in the swarm according to the steps of swarm head selection. After that, the swarm head is identified to construct the private key establishment factor. The steps for swarm head selection are as follows:
Step 1: every UAV node in the swarm broadcasts their ID information ;
Step 2: each UAV node, after receiving the ID information of other nodes in the swarm, determines whether it is the minimal j () in the swarm through comparison;
Step 3: find the minimal from the in the swarm, which is denoted as .
Step 4: identify the UAV with the highest priority in the swarm according to the rules: .
Figure 4 visualizes the specific steps:
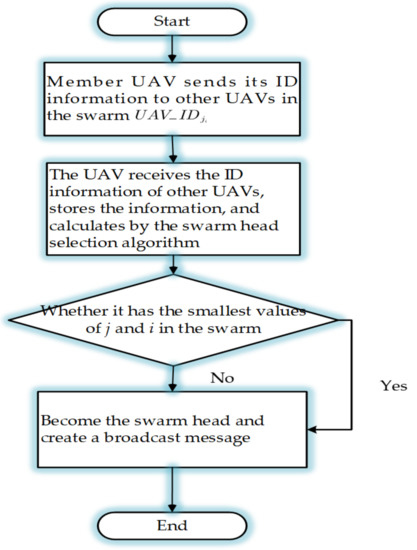
Figure 4.
Steps for swarm head selection.
is the highest-priority UAV node identified through the swarm head selection after UAV reorganization; the node selects the key creation factor and a random number , formulates, and passes on the group key to other UAVs. Other UAV swarms follow the same steps in Figure 4 to identify the swarm head to broadcast messages. The algorithm is specified as follows, with the swarm as an example (Algorithm 2):
| Algorithm 2 Key Distribution |
The legitimate UAV extracts , and from the broadcast message Mt it receives at the task stage t, and then calculates and using . If , the message is validated to be a legitimate message in the reorganized swarm, and the key is constructed for secure communication; if , the message is not validated and will be discarded as an error message. Algorithm 3 shows the specific procedures for key establishment:
| Algorithm 3 Key Establishment |
3.3. Key Update at Collaboration Stage
The cross-platform key management for UAV swarms in the denied environment consists of four stages: system initialization, key distribution, key establishment, and key update. The key parameter presetting, key distribution, and key establishment procedures have already been detailed in Section 3. When introduced to the denied environment with strong electromagnetic radiation and intense firepower, the UAVs are likely to suffer loss of communication signals and damages, resulting in changes in the topology of the UAV swarm network, as shown in Figure 5.
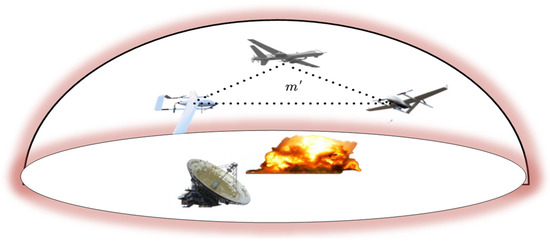
Figure 5.
Network of UAVs in collaboration.
It is necessary to update the key for the UAV swarm to ensure secure communication between the member UAVs. Figure 6 displays the procedures for UAV swarm key update in the denied environment.
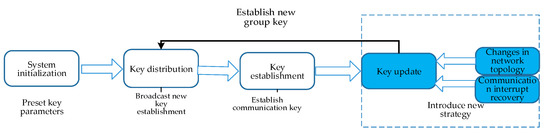
Figure 6.
Key management in denied environment.
3.3.1. Broadcast Update
The original swarm head UAV identifies during patrolling changes in the number of UAVs in the swarm and broadcasts to generate a random number . The legitimate UAV nodes extract from the broadcast message to construct a new swarm key. The procedures are shown in Algorithms 2 and 3.
3.3.2. Mutual-healing Update
If a UAV in the swarm fails to receive the broadcast message because of strong electromagnetic interferences in the denied environment at the t task stage, it can request a neighboring UAV (UAV-Neighbor) to help recover the swarm key. This process is called mutual-healing, as shown in Figure 7. The algorithm process is shown in Algorithm 4. The randomly selected by the swarm head against forgery attacks is combined with the local hash chain and CRT to complete the mutual-healing update. Figure 7 shows the mutual-healing update process, with the m′ swarm as an example:
| Algorithm 4 Key Mutual-Healing | |
| 1: | Initialization: (t: task stage) |
| 2: | Procedure Key mutual-healing |
| 3: | : ;//broadcast request to |
| 4: | : Compute ; |
| 5: | If Compare Then // identity authentication |
| 6: | :; // authenticated, unicast response to |
| 7: | Else If “Illegal message, delete”;// authentication failed, delete the illegitimate message |
| 8: | : Select ;// select response that arrives first |
| 9: | Invoking Key Recovery; //call Algorithm 3 |
| 10: | : ;// send key confirmation message |
| 11: | : Compute ; |
| 12: | If Compare Then |
| 13: | Return “mutual healing key succeeded.”; // confirm success in mutual healing |
| 14: | Else If Return “mutual healing key failure.”; // return mutual-healing failure |
| 15 | End Procedure |
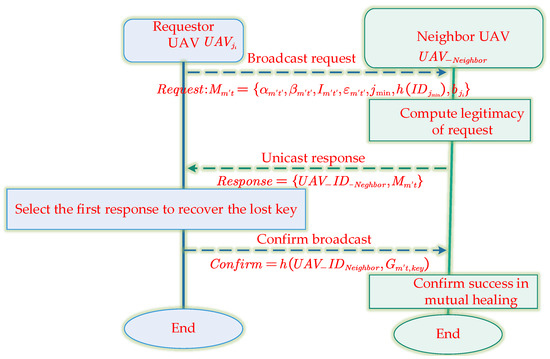
Figure 7.
An example of the mutual-healing update process.
4. Scheme Analysis
For the sake of convenient analysis and proof, the symbols for proving are defined, as shown in Table 3.

Table 3.
Definitions of symbols for proof.
4.1. Correctness Analysis
Lemma 1.
The ACPKMS scheme satisfies the basic attributes of key distribution. At the task stage t, the specific proof process is as follows:
- (1)
- ;
- (2)
- (3)
- ;
- (4)
- ;Q.E.D., is satisfied.
- (5)
- If , , and ,Q.E.D. The ACPKMS scheme has the basic attributes and satisfies the condition: . Given all stated above, the ACPKMS scheme satisfies the task requirements and has good capacity for key establishment.
Lemma 2.
The ACPKMS scheme has the mutual-healing mechanism. If () and fails to receive the broadcast message at the t stage , the communication is recovered at the t + i stage, and the key can be recovered through mutual healing. The proving process is as follows:
- (1)
- : ;
- (2)
- ;
- (3)
- : ;
- (4)
- .Q.E.D., the EHGKM scheme has the mutual-healing mechanism.
4.2. Security Analysis
Lemma 3.
The ACPKMS scheme has forward security (FWS). If joins UAVGN at the t stage, i.e., . The specific proving process is as follows:
- (1)
- ;
- (2)
- If and ;
- (3)
- .Q.E.D., the ACPKMS scheme has forward security, the cannot obtain the key before it joins the swarm.
Lemma 4.
The ACPKMS scheme has backward security (BWS). If exits UAVGN at the session stage t, i.e., . The specific proving process is as follows:
- (1)
- ;
- (2)
- If and ;
- (3)
- ;Q.E.D., the ACPKMS scheme has backward security, and the UAV cannot obtain the key after it leaves the swarm.
Lemma 5.
The ACPKMS scheme can resist replay attacks (RRA). During the distribution and update of keys, the task label random number is introduced. When receives the key update message , it checks the freshness of . The has already been used in previous sessions, then is discarded to prevent the attacker (AT) from replaying the broadcast message in previous sessions. Suppose that the t session broadcast message replayed by the attacker is , the proving process is as follows:
- (1)
- ;
- (2)
- Replay Attack;Therefore, receives the replayed message and cannot pass the message legitimacy test.
Lemma 6.
The ACPKMS scheme can resist impersonation attacks (RIA).
Impersonation node attacks: suppose the attacker forges to join UAVGN and needs to obtain to establish communication, i.e., . The proving process is , which does not hold and conflicts with , as the forged needs to obtain the private key of to join UAVGN.
Table 4 shows the performance of different UAV key management schemes. As the table shows, our scheme has forward and backward security, and can resist replay attacks and impersonation attacks. Compared with other schemes, ours uses the hash function for verification, which ensures legitimacy of the requests and responses, and avoids malicious attacks. “malicious attacks” Our approach establishes keys by constructing broadcast messages, has good security and efficiency, and hence is applicable to cross-platform UAV swarm key management.

Table 4.
Performance of different UAV swarm key management schemes.
4.3. Efficiency Analysis
Because of the limited communication and computing capacity of UAVs, it is necessary to minimize the computing time and information exchange to reduce the computing and communication overhead [16]. In this study, the efficiency of our scheme is analyzed from the computing overhead, communication overhead, and storage overhead, with focus on the first two aspects. Table 5 shows the definitions of the signs of operations.

Table 5.
Definitions of signs of operation.
According to the simulation tests and the efficiency analysis in Section 4.3, the performance of our scheme using the cryptographic library MIRACL is tested in an environment of the following settings: Intel (R) Core (TM), 2 i5-7500CPU, 3.40GHz processor, Windows 10. The results are shown in Table 6.

Table 6.
Computing time on the 256-bit experiment data.
4.3.1. Computing Overhead
In this section, the computing overhead of the swarm head and in the ACPKMS scheme is analyzed. During key establishment, the swarm head node CHN performs the hash operation two times, with the time consumed marked as ; the broadcast receiving node performs the hash operation three times, taking . Though theoretically, our scheme has a computing overhead higher than the scheme proposed in [17], part of the key is updated locally, which reduces the overhead and prevents the from directly engaging in the construction of congruences; the attacker must know all the parameters of , i.e., before it can crack , which enhances the key security and cuts the computing overhead during key establishment. Figure 8 shows the computing overhead of the nodes during the key establishment process.
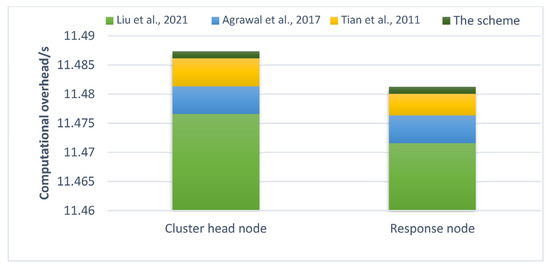
Figure 8.
Computing overhead of nodes for key establishment in different schemes [16,17,18].
In our scheme, the key update process is divided into the local key update and the session key update to reduce the computing workload. For convenient comparison, the data processed in this paper are set to be half that in [17,18], and the key establishment broadcast message is only one session stage, that is, to solve with a given . Normally, 12 UAVs create a formation. The Visual Studio 2019 is employed to call the MIRACL cryptographic library to measure the computing overhead of different schemes, and the mean value of multiple tests is used for measurement and comparison. Figure 9 shows the key establishment process. In our proposed scheme, the swarm head UAV and the receiver UAV take an average of 1.068 µs in the key establishment process, which is lower than other schemes, so our scheme is applicable to the fast-moving UAVGN with limited resources.
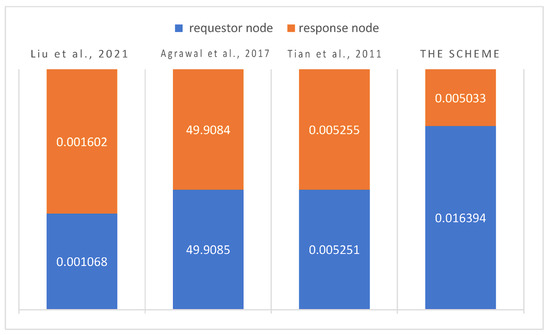
Figure 9.
Computing overhead during key establishment [16,17,18].
4.3.2. Communication Overhead
As UAVGN is a wireless network, the communication overhead is an important indicator in key management. During the key establishment process in the ACPKMS scheme, the requestor node needs to send messages including and , which incurs communication overhead; the response node needs to send , incurring communication overhead. Table 7 displays the communication overhead of various schemes. According to the performance of several mainstream UAVs analyzed in [19], “RQ-23 Tigershark”, “MQ-9 Reaper”, and “MQ-1 Predator” can fly above 24 h. In this study, we set the UAV flying time as 24 h, and the task cycle is 2 h, that is, . For the convenience of comparison, the transmitted data are set to be 256-bit. Table 7 shows the communication overheads during the key establishment process in different schemes.

Table 7.
Communication and storage overheads of nodes during key construction of different schemes.
4.3.3. Storage Overhead
In the ACPKMS scheme, the usually needs to store :. For the sake of more convenient comparison, the size of the transmitted data is set at 256 bit; that is, the seven parameters have the same size, so the storage overhead is . Though the ACPKMS scheme has a higher storage overhead and is slightly higher than schemes in [20], the computing and communication overheads are reduced, which has sound security and is more applicable to the dynamic UAVGN featured by instability and unreliability [21].
5. Conclusions
A simple but efficient swarm key management scheme based on the hash chain and the Chinese Remainder Theorem (CRT), termed ACPKMS, is proposed here as a solution to secure communication of UAV swarms across platforms. The proposed scheme, by combining the node update key and the session update key, achieves the local static update and the session dynamic update, which enhances the key update efficiency and reduces the communication overhead. Meanwhile, the simple swarm head selection method in the scheme further enhances the flexibility of cross-platform key establishment of UAV swarms. The scheme is compared with other schemes through experiments, and it is found that the EHGKM has good security and high efficiency: the requestor node takes 1.18 µs in the key establishment stage to acquire the key establishment broadcast message and 3.36 µs to recover the key; the ACPKMS scheme can meet the requirements for the UAV swarm key management. In future works, we will study the key management solutions for multiple UAV swarms and design a key management scheme for multiple UAV swarms, thereby providing more efficient and secure key management solutions to the intelligent and integrated development of UAV swarms.
Author Contributions
Conceptualization, L.Y. and Z.F.; methodology, L.Y. and C.Z.; software and validation, L.Y., Z.F. and C.Z.; formal analysis, H.J., C.Z. and Z.F.; writing—original draft preparation, L.Y. and Z.F.; writing—review and editing, H.J. and L.Y.; funding acquisition, Z.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, grant number 61902427.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data are available from the corresponding author Binglong Li upon reasonable request.
Acknowledgments
The authors would like to thank all the editors and reviewers who participated in the review.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| CODE | Collaborative Operations in Denied Environment |
| UAVs | Unmanned Aerial Vehicles |
| KMC | Key Management Center |
| UAVCN | UAV cluster network |
References
- Arafat, M.Y.; Moh, S. A survey on cluster-based routing protocols for unmanned aerial vehicle networks. IEEE Access 2018, 7, 498–516. [Google Scholar] [CrossRef]
- Ge, J.; Liu, L.; Wang, J. Key technologies for distributed intelligent combat of patrol UAVs in denied environments. Tactical Missile Technol. 2018, 5, 62–73. [Google Scholar] [CrossRef]
- Xin, X.; Xie, C. Application and development of artificial intelligence in UAV systems. Aerodyn. Missile J. 2021, 5, 48–51. [Google Scholar] [CrossRef]
- Zhou, Y.; Rao, B.; Wang, W. UAV swarm intelligence: Recent advances and future trends. IEEE Access 2020, 8, 183856–183878. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing from the Sky: A Tutorial on UAV Communications for 5G and beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef]
- Fotohi, R.; Nazemi, E.; Aliee, F.S. An Agent-Based Self-Protective Method to Secure Communication between UAVs in Unmanned Aerial Vehicle Networks. Vehic. Commun. 2020, 26, 100267–100272. [Google Scholar] [CrossRef]
- Rodrigues, M.; Amaro, J.; Osório, F.S.; Branco Kalinka, R.L.J.C. Authentication methods for UAV communication. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019. [Google Scholar]
- Liu, J.; Yuan, L. Key management technology analysis based on UAV cluster communication security. In Proceedings of the International Conference on Network Communication and Information Security, Austin, TX, USA, 26–28 September 2022. [Google Scholar]
- Stallings, W. Cryptography and Network Security: Principles and Practices, 8th ed.; Jing, C.; Ruiying, D.U.; Ming, T., Translators; Publishing House of Electronics Industry: Beijing, China, 2021. [Google Scholar]
- Li, Y.; Niu, W.; Zhang, Y.; Chang, W. Multi-level UAV dynamic swarm network key management protocol. J. Commun. 2011, 32, 39–44. [Google Scholar]
- Li, L.; Wang, T.; Jiang, Q. The US CODE Program promotes development of distributed collaborative combat. Unmanned Syst. Technol. 2018, 1, 59–66. [Google Scholar]
- Zhou, J.; Shi, W.; Yin, H.; Sun, L. Non-interactive dynamic group key management of UAV ad hoc networks. J. Front. Comput. Sci. Technol. 2018, 12, 1126–1135. [Google Scholar]
- Shi, J. Research on Communication Security of UAV Network Based on Key Management. Master’s Thesis, Shandong University, Shandong, China, 2019. [Google Scholar]
- Li, X.; Wang, Y.; Vijayakumar, P.; He, D.; Kumar, N.; Ma, J. Blockchain-based mutual-healing group key distribution scheme in unmanned aerial vehicles ad-hoc network. IEEE Trans. Vehic. Technol. 2019, 68, 11309–11322. [Google Scholar] [CrossRef]
- Frimpong, E.; Rabbaninejad, R.; Michalas, A. Arrows in a quiver: A secure certificateless group key distribution protocol for drones. In Proceedings of the Nordic Conference on Secure IT Systems, NordSec 2021, Virtual Event, 29–30 November 2021; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; pp. 31–48. [Google Scholar]
- Liu, J.; Yuan, L.; Feng, Z.S. Research on UAV swarm key management framework. Cyber Sec. 2021, 33, 348–352. [Google Scholar]
- Agrawal, S.; Das, M.L. Mutual healing enabled group-key distribution protocol in wireless sensor networks. Comput. Commun. 2017, 112, 131–140. [Google Scholar] [CrossRef]
- Tian, B.; Han, S.; Hu, J.; Dillon, T. A mutual-healing key distribution scheme in wireless sensor networks. J. Network Comput. Appl. 2011, 34, 80–88. [Google Scholar] [CrossRef]
- Agrawal, S.; Patel, J.; Das, M.L. Pairing based mutual healing in wireless sensor networks. In Proceedings of the 2016 8th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 5–10 January 2016. [Google Scholar]
- Chaumette, S.; Kim, J.H. Namuduri. UAV Networks and Communications; Liu, Y.W.; Yan, J., Translators; China Machine Press: Beijing, China, 2019; pp. 128–129. [Google Scholar]
- Chien, H. Self-healing group key distribution facilitating source authentication using block codes. Sec. Commun. Networks 2021, 2021, 2942568. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).