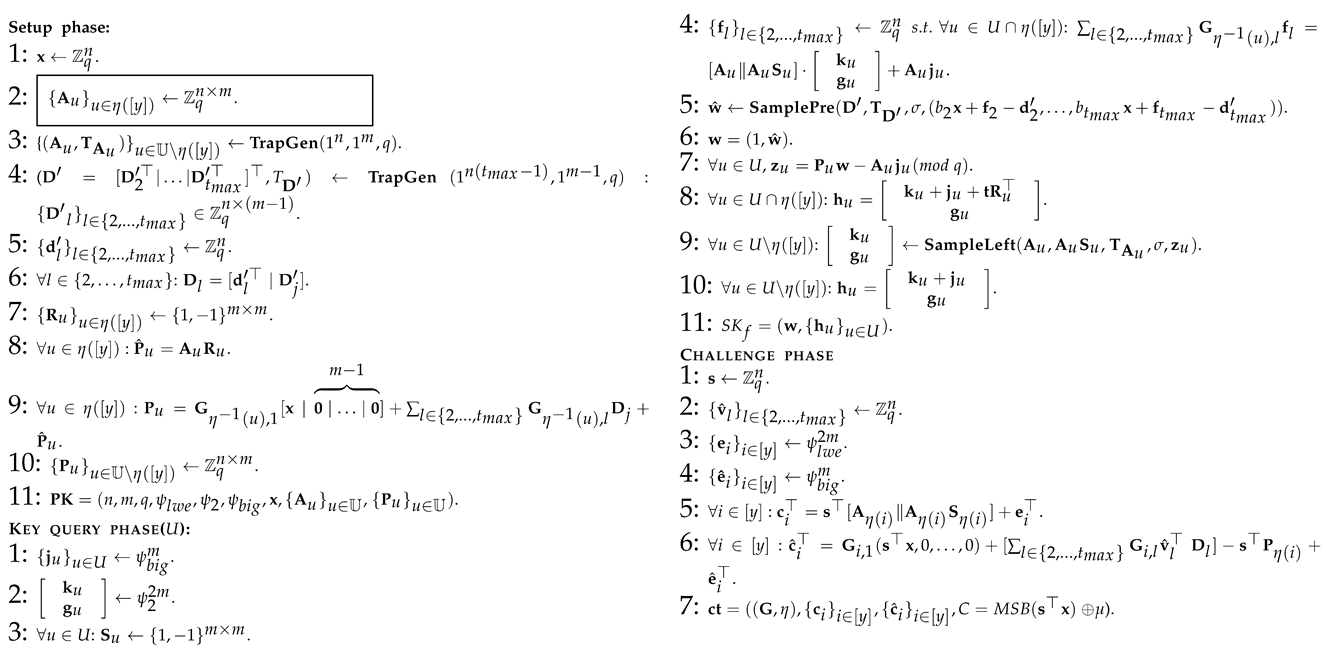
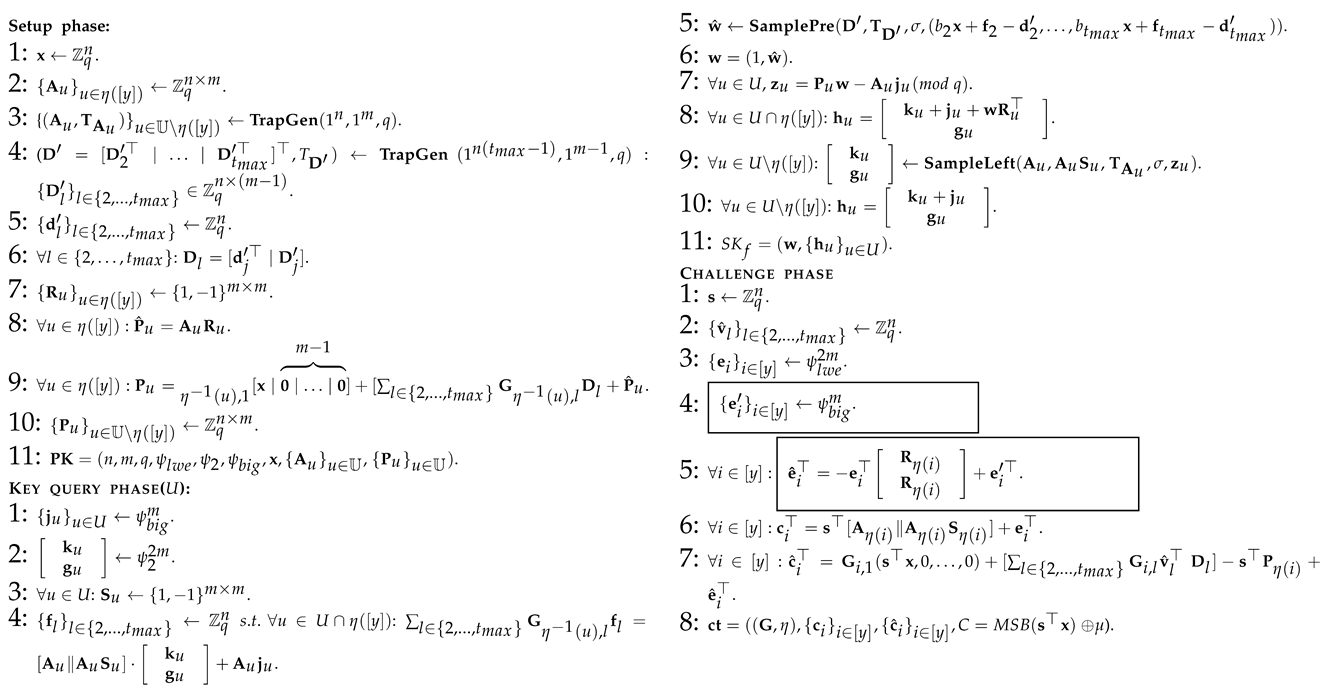
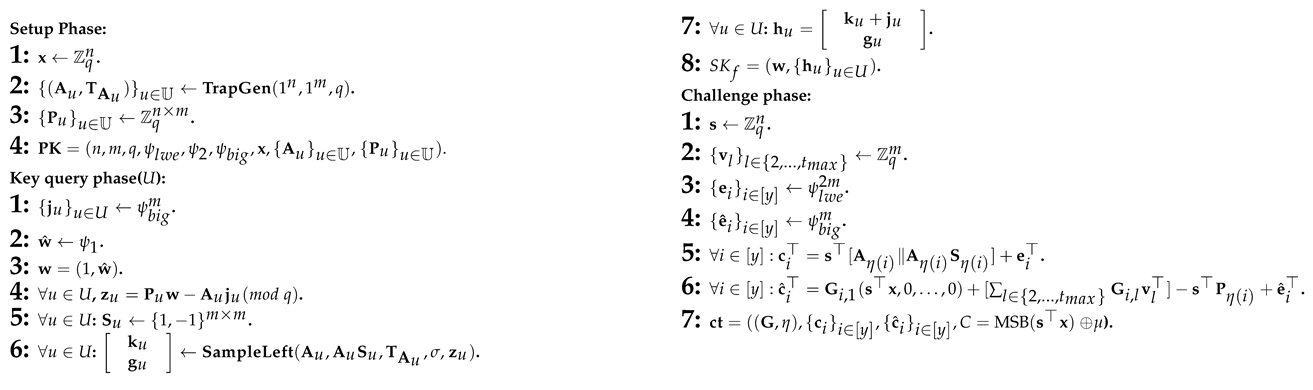Proof. To prove the correctness of Theorem 2, we considered a series of hybrid games, which are slightly different from each other. The first hybrid game matches the real choice security game under the linear independent restriction, and the final hybrid scheme is the one in which the advantage of the opponent is zero. By demonstrating that the advantages of the adversaries have only a completely negligible change between different consecutive hybrid games, we have finally proved the correctness of Theorem 2. Next, we will talk about the specific hybridization and analysis process. In order to facilitate the explanation, we first use 12 algorithm graphs to show, in detail, the process of 12 hybridizations in which all the symbols used are as defined above.
Secondly, we analyze the indistinguishability of any two adjacent hybridization processes in detail. For convenience, we introduce a probability function for all adversaries , and any whose input is and output is the probability of the opponent correctly guesses the challenge bit in each hybrid program. According to the definition of Algorithm 1, it is known that for all . Furthermore, since the generated challenge ciphertext in Algorithm 12 does not disclose any information about the selection of challenge bits, it is known that for all .
Therefore, through the following series of analysis, we can conclude that for all
, there is obviously
: This is the original selective weak security model of the CP-ABE scheme we constructed.
: This is similar to Algorithm 1, except for the three parts marked with a wireframe in Algorithm 2, and these changes are only semantic (As in Algorithm 1, , Algorithm 2 replaces the original vector with , where and . The semantic changes involved later are also similar to the methods here), so there is obviously for all adversaries .
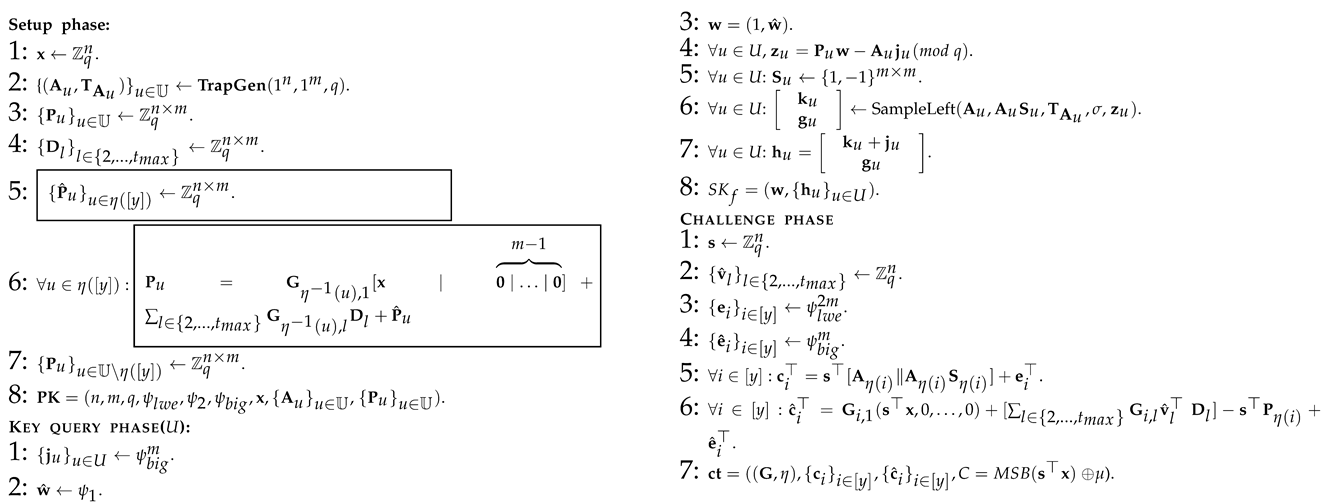
: This is similar to Algorithm 2, except for the two parts marked with a wireframe in Algorithm 3, and these changes are only semantic, so there is obviously for all adversary .
: This is similar to Algorithm 3, except for those parts marked with a wireframe in Algorithm 4. The indistinguishability of Algorithm 3 and Algorithm 4 stems from the leftover hash lemma (as shown in Lemma 1) and the basic fact that the sum of two random matrices is still a random matrix. So, there is obviously for all adversaries .
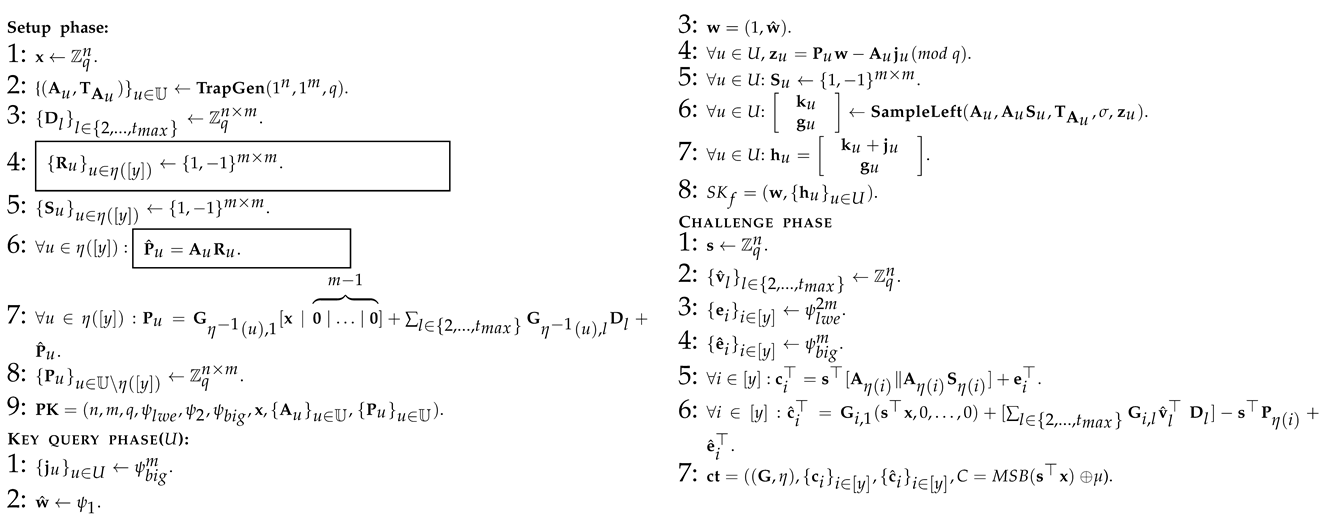
: This is similar to Algorithm 4, except for those parts marked with a wireframe in Algorithm 5. It chooses another indistinguishable way to generate , which stems from the trapdoor lattice sampler. So, there is obviously for all adversaries .
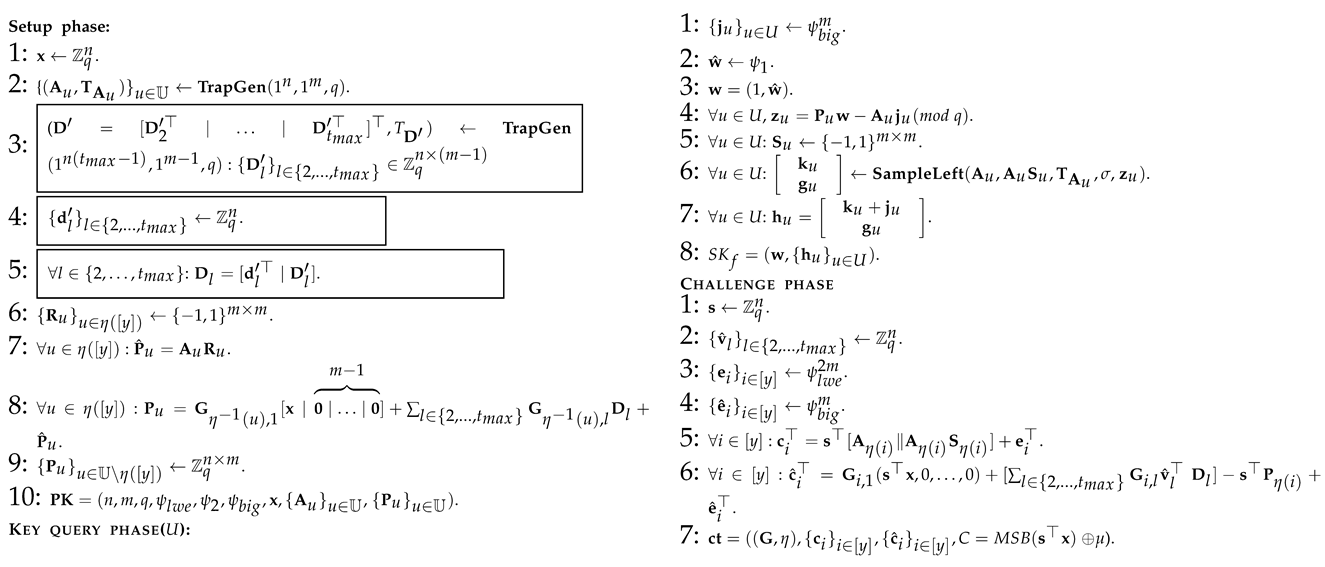
: This is similar to Algorithm 5, except for several parts marked with wireframes in Algorithm 6, which can be summarized as the way in which is generated when answering the private key query of the adversary for all . This indistinguishably stems from the smudging lemma (Lemma 2), so we can deduce that for all adversaries where is a negligible function to measure the indistinguishability of two distributions under smudging and represents the number of private key queries made. For example, for all of the and , when , there is SD (where ).
: It is basically similar to Algorithm 6, just except the generation method of the vector
is different when answering the adversary
. Here, in order to achieve the same purpose, we use the idea of Hybrid 6 in [
20]. Namely, let
be a vector such that
and
for all
. Note that by the game restriction, the set of rows of
G with indices in
must be unauthorized with respect to the access policy
, and, hence, the existence of such a vector
is guaranteed. We can find that the indistinguishability of Algorithm 6 and Algorithm 7 comes from the excellent characteristics of the trapdoor sampling of lattice. So, there is obviously
for all adversaries
.
: This is similar to Algorithm 7, except for several parts marked with wireframes in Algorithm 8. Similar to the methods and goals of Hybrid 7 in [
24], here, due to the restrictions of the game, for each secret key query of
corresponding to some attribute set
, the rows of
with indices in
are linearly independent. These changes can also be seen as a simple semantic, so they are indistinguishable; therefore, there is obviously
for all adversaries
.
: This is similar to Algorithm 8, except for several parts marked with wireframes in Algorithm 9, which can be summarized as the way in which is generated when answering the private key query of the adversary . The indistinguishability of Algorithm 8 and Algorithm 9 is derived from the excellent characteristics of the trapdoor sampling of lattice. So, there is obviously for all adversaries .
: This is similar to Algorithm 9, except for the part marked with wireframes in Algorithm 10. Namely, the way to generate the matrices has been replaced. The indistinguishability of Algorithm 1 and Algorithm 2 is derived from the excellent characteristics of the trapdoor sampling of lattice as described earlier. So, there is obviously for all adversaries .
: This is similar to Algorithm 10, except for the two parts marked with wireframes in Algorithm 11. Namely, the way to generate the vectors in the has been replaced. The indistinguishability of Algorithm 10 and Algorithm 11 is derived from the smudging lemma (Lemma 2). So, there is obviously for all adversaries .
: This is basically the same as Algorithm 11, except for a few framed parts, which are summarized as different ways of generating ciphertext in the challenge phase. In Algorithm 11, resembles a set of LWE samples, and, here, we really want to use LWE to hide s. Assume that for any , , then . Because of the decisional LWE, we have that the selection of in Algorithm 11 and Algorithm 12 is indistinguishable. In addition, Algorithm 12 makes a semantic transformation with so that gets rid of s and has the same distribution as the selection in Algorithm 11. In turn, if we look at , because of , we can make and randomly select . Then, there must be MSB = MSB. Then, according to the decisional LWE, we have that the distribution of MSB is indistinguishable from that of MSB (where ). To sum up, the indistinguishability of Algorithm 11 and Algorithm 12 is derived from the LWE assumption. So, there is obviously for all adversaries . □