Hybrid Chaotic-Based PRNG for Secure Cryptography Applications
Abstract
:1. Introduction
2. Known 1D Chaotic Maps
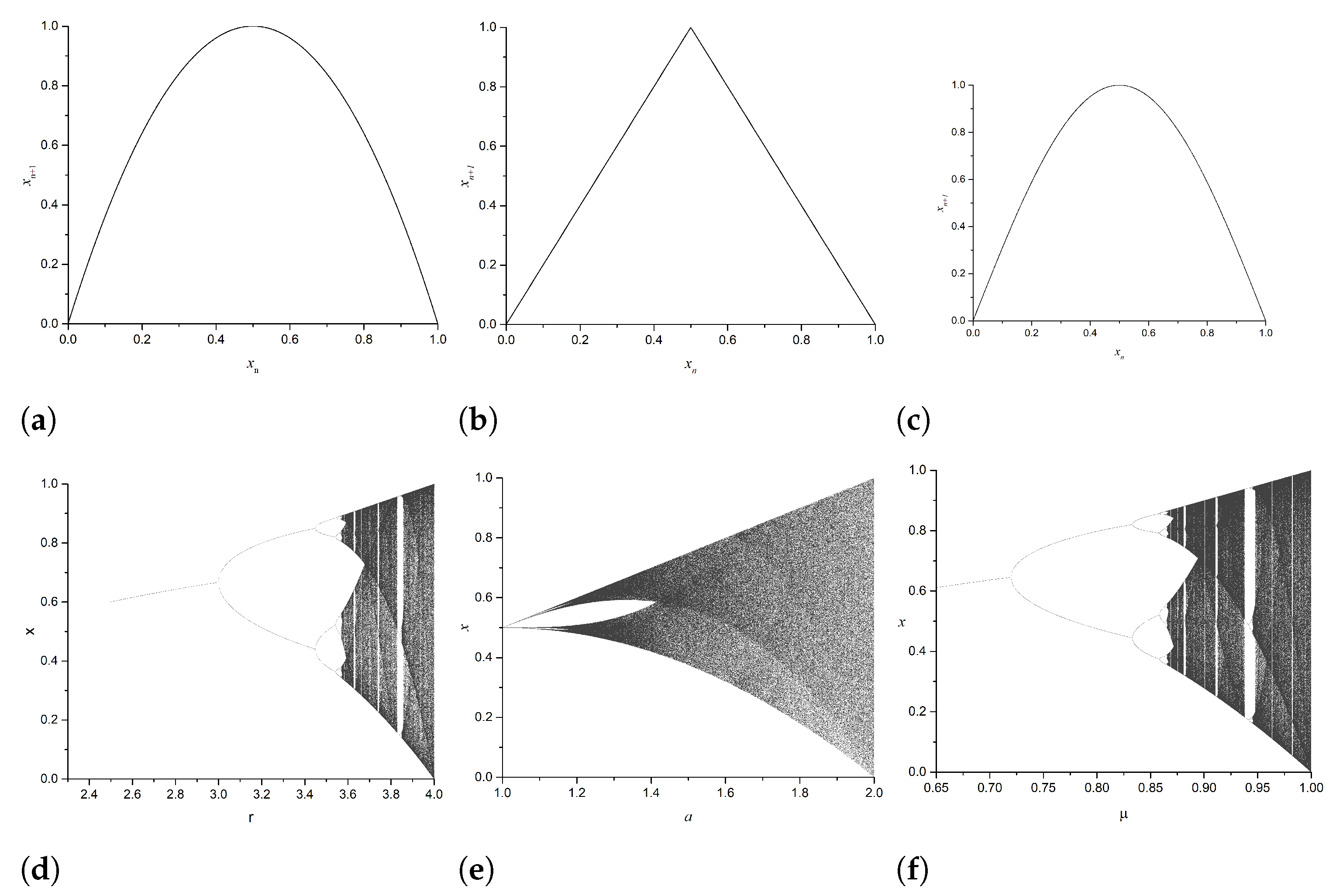
2.1. Logistic Map
2.2. Tent Map
2.3. Sine Map
3. Modified 1D Map
3.1. Sensitivity to Control Parameters and Initial Condition
3.2. Bifurcation Diagram
3.3. Lyapunov Exponent
4. Proposed Encryption Algorithm
4.1. Encryption Steps
- Step 1: Key generation
- Step 2: Permutation stage
- Step 3: Confusion stage
| Algorithm 1 Proposed Image Encryption Algorithm |
|
4.2. Decryption Steps
5. Results and Analysis
5.1. Encryption Quality Analysis
5.1.1. Key Space Analysis
5.1.2. Key Sensitivity Analysis
5.1.3. MSE and PSNR
5.1.4. Histogram Analysis
5.1.5. Correlation Analysis and Chi-Square Test
5.1.6. Information Entropy
5.2. Resistance to Differential Attack
- Number of Pixels Change Rate (NPCR)
- Unified Average Changing Intensity (UACI)
5.3. Encryption Speed Analysis
6. Discussion and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wang, C.; Tianqing, Z.; Xiong, P.; Ren, W.; Choo, K.K.R. A privacy preservation method for multiple-source unstructured data in online social networks. Comput. Secur. 2022, 113, 102574. [Google Scholar] [CrossRef]
- Sun, Q.; Tewari, A.; Xu, W.; Fritz, M.; Theobalt, C.; Schiele, B. In Proceedings of the European conference on Computer Vision (ECCV). Munich, Germany, 8–14 September 2018; pp. 553–569. [Google Scholar]
- Cunha, M.; Mendes, R.; Vilela, J.P. A survey of privacy-preserving mechanisms for heterogeneous data types. Comput. Sci. Rev. 2021, 41, 100403. [Google Scholar] [CrossRef]
- Zhao, Y.; Chen, J. A survey on differential privacy for unstructured data content. ACM Comput. Surv. CSUR 2022, 54, 1–28. [Google Scholar] [CrossRef]
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An overview of encryption algorithms in color images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Gagliardelli, L.; Zecchini, L.; Ferretti, L.; Beneventano, D.; Simonini, G.; Bergamaschi, S.; Orsini, M.; Magnotta, L.; Mescoli, E.; Livaldi, A.; et al. A big data platform exploiting auditable tokenization to promote good practices inside local energy communities. Future Gener. Comput. Syst. 2023, 141, 595–610. [Google Scholar] [CrossRef]
- Fontaine, C.; Galand, F. A survey of homomorphic encryption for nonspecialists. Eurasip J. Inf. Secur. 2007, 2007, 13801. [Google Scholar] [CrossRef]
- Taleby Ahvanooey, M.; Li, Q.; Hou, J.; Rajput, A.R.; Chen, Y. Modern text hiding, text steganalysis, and applications: A comparative analysis. Entropy 2019, 21, 355. [Google Scholar] [CrossRef] [Green Version]
- Thakkar, B.; Thankachan, B. A Survey for Comparative Analysis of various Cryptographic Algorithms used to Secure Data on Cloud. Int. J. Eng. Res. Technol 2020, 9, 753–756. [Google Scholar]
- Cao, C.; Tang, Y.; Huang, D.; Gan, W.; Zhang, C. IIBE: An improved identity-based encryption algorithm for WSN security. Secur. Commun. Netw. 2021, 2021, 8527068. [Google Scholar] [CrossRef]
- Yazdeen, A.A.; Zeebaree, S.R.; Sadeeq, M.M.; Kak, S.F.; Ahmed, O.M.; Zebari, R.R. FPGA implementations for data encryption and decryption via concurrent and parallel computation: A review. Qubahan Acad. J. 2021, 1, 8–16. [Google Scholar] [CrossRef]
- You, X.; Wang, C.X.; Huang, J.; Gao, X.; Zhang, Z.; Wang, M.; Huang, Y.; Zhang, C.; Jiang, Y.; Wang, J.; et al. Towards 6G wireless communication networks: Vision, enabling technologies, and new paradigm shifts. Sci. China Inf. Sci. 2021, 64, 110301. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Ramadoss, J.; Abd-El-Atty, B.; Khalifa, H.S.; Nazarimehr, F. A Novel Chaos-Based Cryptography Algorithm and Its Performance Analysis. Mathematics 2022, 10, 2434. [Google Scholar] [CrossRef]
- Bahbouh, N.; Basahel, A.; Sendra, S.; Sen, A.; Ahmed, A. Tokens Shuffling Approach for Privacy, Security, and Reliability in IoHT under a Pandemic. Appl. Sci. 2023, 13, 114. [Google Scholar] [CrossRef]
- Pourasad, Y.; Ranjbarzadeh, R.; Mardani, A. A new algorithm for digital image encryption based on chaos theory. Entropy 2021, 23, 341. [Google Scholar] [CrossRef]
- Zhang, W.; Fu, C.; Zheng, Y.; Zhang, F.; Zhao, Y.; Sham, C.W. HSNet: A hybrid semantic network for polyp segmentation. Comput. Biol. Med. 2022, 150, 106173. [Google Scholar] [CrossRef]
- Kumar, S.; Srivastava, P.K.; Srivastava, G.K.; Singhal, P.; Singh, D.; Goyal, D. Chaos based image encryption security in cloud computing. J. Discret. Math. Sci. Cryptogr. 2022, 25, 1041–1051. [Google Scholar] [CrossRef]
- Pour, N.R.; Yaghoobi, M. A new method in encryption of gray scale images using chaos game representation. Multimed. Tools Appl. 2022, 81, 29653–29672. [Google Scholar] [CrossRef]
- Salleh, M.; Ibrahim, S.; Isnin, I.F. In Proceedings of the 2003 International Symposium on Circuits and Systems, ISCAS’03. Bangkok, Thailand, 25–28 May 2003; Volume 2, p. II. [Google Scholar]
- Boriga, R.E.; Dăscălescu, A.C.; Diaconu, A.V. A new fast image encryption scheme based on 2D chaotic maps. IAENG Int. J. Comput. Sci. 2014, 41, 249–258. [Google Scholar]
- Akhshani, A.; Behnia, S.; Akhavan, A.; Hassan, H.A.; Hassan, Z. A novel scheme for image encryption based on 2D piecewise chaotic maps. Opt. Commun. 2010, 283, 3259–3266. [Google Scholar] [CrossRef]
- Zhu, L.; Jiang, D.; Ni, J.; Wang, X.; Rong, X.; Ahmad, M.; Chen, Y. A stable meaningful image encryption scheme using the newly-designed 2D discrete fractional-order chaotic map and Bayesian compressive sensing. Signal Process. 2022, 195, 108489. [Google Scholar] [CrossRef]
- Elmanfaloty, R.A.; Abou-Bakr, E. Random property enhancement of a 1D chaotic PRNG with finite precision implementation. Chaos, Solitons Fractals 2019, 118, 134–144. [Google Scholar] [CrossRef]
- AbdElHaleem, S.H.; Abd-El-Hafiz, S.K.; Radwan, A.G. A generalized framework for elliptic curves based PRNG and its utilization in image encryption. Sci. Rep. 2022, 12, 13278. [Google Scholar] [CrossRef] [PubMed]
- Elmanfaloty, R.A.; Abou-Bakr, E. An image encryption scheme using a 1D chaotic double section skew tent map. Complexity 2020, 2020, 7647421. [Google Scholar] [CrossRef]
- Elmanfaloty, R.A.; Alnajim, A.M.; Abou-Bakr, E. A finite precision implementation of an image encryption scheme based on DNA encoding and binarized chaotic cores. IEEE Access 2021, 9, 136905–136916. [Google Scholar] [CrossRef]
- Khairullah, M.K.; Alkahtani, A.A.; Bin Baharuddin, M.Z.; Al-Jubari, A.M. Designing 1D chaotic maps for fast chaotic image encryption. Electronics 2021, 10, 2116. [Google Scholar] [CrossRef]
- Moysis, L.; Tutueva, A.; Volos, C.; Butusov, D.; Munoz-Pacheco, J.M.; Nistazakis, H. A two-parameter modified logistic map and its application to random bit generation. Symmetry 2020, 12, 829. [Google Scholar] [CrossRef]
- Moysis, L.; Volos, C.; Jafari, S.; Munoz-Pacheco, J.M.; Kengne, J.; Rajagopal, K.; Stouboulos, I. Modification of the logistic map using fuzzy numbers with application to pseudorandom number generation and image encryption. Entropy 2020, 22, 474. [Google Scholar] [CrossRef] [Green Version]
- Sprott, J.C. Chaos and Time-Series Analysis; Oxford University Press: New York, NY, USA, 2003; Volume 69. [Google Scholar]
- The USC-SIPI Image Database, University of Southern California. Available online: https://sipi.usc.edu/database/database.php (accessed on 16 April 2023).








| Changed Parameter | MSE | PSNR (dB) |
|---|---|---|
| 7.767 | ||
| 7.748 |
| Original Image | Encrypted Image | ||||||||
|---|---|---|---|---|---|---|---|---|---|
| File Name | Size | V-Correlation | H-Correlation | D-Correlation | V-Correlation | H-Correlation | D-Correlation | ||
| bird.png | 2625 × 2250 | 0.9876 | 0.9736 | 0.9706 | 37,036 × | −6.46 × | 0.0188 | −0.0061 | 271.7370 |
| lion.png | 2362 × 3047 | 0.971 | 0.9764 | 0.957 | 42,846 × | 0.0189 | −0.0164 | 0.0198 | 249.2168 |
| pyramids.png | 4755 × 3090 | 0.9894 | 0.9908 | 0.9841 | 62,090 × | −0.0033 | −0.038 | 0.0143 | 230.8222 |
| sphinx.png | 1704 × 2272 | 0.9793 | 0.9839 | 0.9733 | 55,280 × | 0.0253 | 0.0126 | 0.0058 | 235.8652 |
| Global Entropy | Local Shannon Entropy | |||||
|---|---|---|---|---|---|---|
| File Name | Size | |||||
| Original Image | Encrypted Image | |||||
| bird | 7.559383165 | 7.999966812 | 7.902673265 | 7.902100541 | 7.902336555 | |
| lion | 4.868976964 | 7.999975018 | 7.902084826 | 7.902600108 | 7.902215068 | |
| pyramids | 6.840163701 | 7.999988669 | 7.902317244 | 7.90294224 | 7.902561135 | |
| sphinx | 6.951101185 | 7.999956064 | 7.902838446 | 7.901851957 | 7.902802677 | |
| NPCR Test Result | UACI Test Result | |||||||
|---|---|---|---|---|---|---|---|---|
| File Name | Score% | Status | Ref. [26] | Ref. [25] | Score % | Status | Ref. [26] | Ref. [25] |
| Dimention 256 × 256 | ||||||||
| 5.1.09 | 99.6094 | pass | 99.588 | 99.5941 | 33.4659 | pass | 33.5688 | 33.4722 |
| 5.1.10 | 99.5773 | pass | 99.6689 | 99.5728 | 33.4735 | pass | 33.5222 | 33.6179 |
| 5.1.11 | 99.585 | pass | 99.5743 | 99.5743 | 33.5218 | pass | 33.4894 | 33.5225 |
| 5.1.12 | 99.5789 | pass | 99.6277 | 99.5758 | 33.3434 | pass | 33.4975 | 33.3374 |
| 5.1.13 | 99.617 | pass | 99.5712 | 99.6459 | 33.5078 | pass | 33.5465 | 33.5497 |
| 5.1.14 | 99.5895 | pass | 99.5697 | 99.6170 | 33.2638 | pass | 33.5711 | 33.5752 |
| Dimention 512 × 512 | ||||||||
| 5.2.08 | 99.5956 | pass | 99.5998 | 99.5918 | 33.429 | pass | 33.5446 | 33.4202 |
| 5.2.09 | 99.5895 | pass | 99.6086 | 99.6040 | 33.4564 | pass | 33.4976 | 33.3967 |
| 5.2.10 | 99.6014 | pass | 99.6048 | 99.5987 | 33.411 | pass | 33.3785 | 33.5028 |
| 7.1.01 | 99.6052 | pass | 99.5934 | 99.6014 | 33.4872 | pass | 33.4887 | 33.4886 |
| 7.1.02 | 99.6193 | pass | 99.6094 | 99.6056 | 33.5014 | pass | 33.5073 | 33.4162 |
| 7.1.03 | 99.612 | pass | 99.6025 | 99.5975 | 33.4781 | pass | 33.4612 | 33.5348 |
| 7.1.04 | 99.6136 | pass | 99.6189 | 99.6006 | 33.4653 | pass | 33.5243 | 33.4449 |
| 7.1.05 | 99.6357 | pass | 99.6094 | 99.6109 | 33.3931 | pass | 33.4804 | 33.4587 |
| 7.1.06 | 99.6033 | pass | 99.6105 | 99.6113 | 33.4627 | pass | 33.4292 | 33.4813 |
| 7.1.07 | 99.6086 | pass | 99.6078 | 99.5968 | 33.3644 | pass | 33.4592 | 33.4569 |
| 7.1.08 | 99.6147 | pass | 99.6052 | 99.6117 | 33.4791 | pass | 33.4667 | 33.4746 |
| 7.1.09 | 99.6204 | pass | 99.604 | 99.6151 | 33.5324 | pass | 33.4781 | 33.4900 |
| boat.512 | 99.6067 | pass | 99.6365 | 99.6009 | 33.4882 | pass | 33.4683 | 33.3759 |
| gray21.512 | 99.5876 | pass | 99.6178 | 99.5937 | 33.4121 | pass | 33.545 | 33.4828 |
| File Name | Score% | Status | Ref. [26] | Ref. [25] | Score % | Status | Ref. [26] | Ref. [25] |
| ruler.512 | 99.6239 | pass | 99.6231 | 99.6021 | 33.4651 | pass | 33.4407 | 33.4163 |
| Dimention 1024 × 1024 | ||||||||
| 5.3.01 | 99.6078 | pass | 99.6063 | 99.6078 | 33.4627 | pass | 33.4725 | 33.4706 |
| 5.3.02 | 99.6084 | pass | 99.602 | 99.6009 | 33.483 | pass | 33.4983 | 33.4801 |
| 7.2.01 | 99.5984 | pass | 99.6073 | 99.6010 | 33.4672 | pass | 33.4723 | 33.4664 |
| Dimention 1704 × 1704 | ||||||||
| sphinx | 99.6099 | pass | - | - | 33.4517 | pass | - | - |
| Dimention 2362 × 2362 | ||||||||
| lion | 99.6079 | pass | - | - | 33.4658 | pass | - | - |
| Dimention 2625 × 2625 | ||||||||
| bird | 99.6108 | pass | - | - | 33.4701 | pass | - | - |
| Dimention 4755 × 4755 | ||||||||
| pyramids | 99.6081 | pass | - | - | 33.4597 | pass | - | - |
| File Name | Dimension | Encryption Speed (s) |
|---|---|---|
| 5.1.09.tiff | 256 × 256 | 0.4648439 |
| 7.1.01.tiff | 512 × 512 | 1.6287242 |
| 5.3.01.tiff | 1024 × 1024 | 6.9461746 |
| sphinx.tiff | 1704 × 2272 | 22.4399294 |
| bird.tiff | 2625 × 2250 | 38.3284587 |
| lion.tiff | 2362 × 3047 | 46.8042111 |
| pyramids.tiff | 4755 × 3090 | 103.5472705 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alnajim, A.M.; Abou-Bakr, E.; Alruwisan, S.S.; Khan, S.; Elmanfaloty, R.A. Hybrid Chaotic-Based PRNG for Secure Cryptography Applications. Appl. Sci. 2023, 13, 7768. https://doi.org/10.3390/app13137768
Alnajim AM, Abou-Bakr E, Alruwisan SS, Khan S, Elmanfaloty RA. Hybrid Chaotic-Based PRNG for Secure Cryptography Applications. Applied Sciences. 2023; 13(13):7768. https://doi.org/10.3390/app13137768
Chicago/Turabian StyleAlnajim, Abdullah M., Ehab Abou-Bakr, Sarah S. Alruwisan, Sheroz Khan, and Rania A. Elmanfaloty. 2023. "Hybrid Chaotic-Based PRNG for Secure Cryptography Applications" Applied Sciences 13, no. 13: 7768. https://doi.org/10.3390/app13137768
APA StyleAlnajim, A. M., Abou-Bakr, E., Alruwisan, S. S., Khan, S., & Elmanfaloty, R. A. (2023). Hybrid Chaotic-Based PRNG for Secure Cryptography Applications. Applied Sciences, 13(13), 7768. https://doi.org/10.3390/app13137768







