Robustness Optimization of Cloud Manufacturing Process under Various Resource Substitution Strategies
Abstract
1. Introduction
2. Related Works
2.1. Robustness Analysis Study of Manufacturing Systems
2.2. Robustness Enhancement Strategies and Recovery Measures
2.3. Multi-Agent Simulation Study of Cloud Manufacturing System
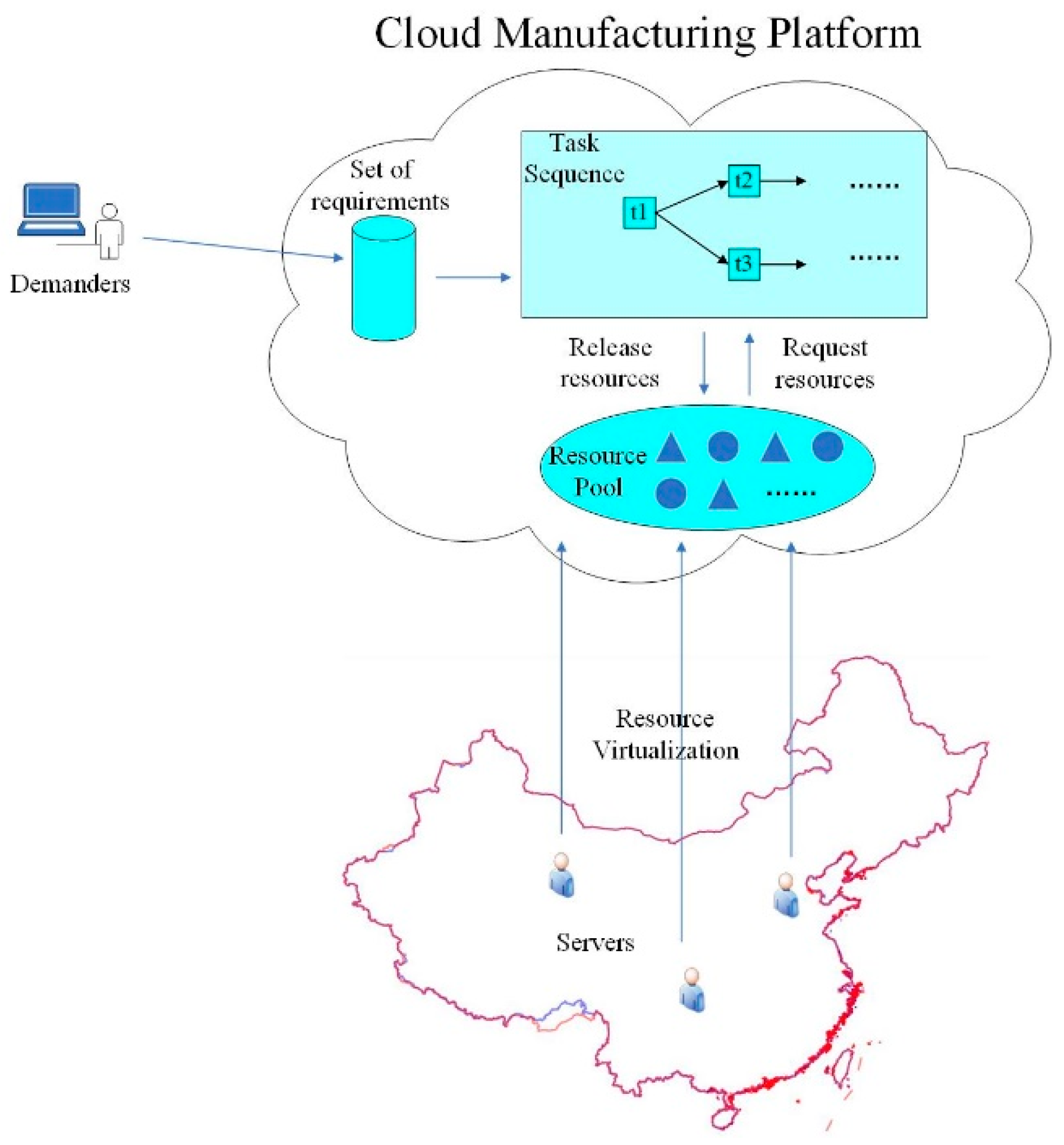
3. Model of the Cloud Manufacturing Process and Robustness Evaluation Indicator Based on Multi-Agent Simulation
3.1. Construction of Multi-Agent Simulation Model
- (1)
- Through information transformation, resource sensing, resource access, unified modeling of cloud services, and other technologies, cloud service providers integrate different kinds of manufacturing equipment and manufacturing capability resources into the cloud platform and deposit them into the cloud resource pool. This allows globally distributed resources to be managed and shared centrally, thereby circumventing the spatial and geographical limitations.
- (2)
- Utilizing terminal devices, cloud demanders submit their requests for services (i.e., orders) to the cloud platform. The cloud demand set uniformly stores orders awaiting processing from various cloud demanders.
- (3)
- In accordance with the service route of the to-be-processed order, the cloud platform integrates and adapts various cloud tasks to create structured and reliable cloud task sequences.
- (4)
- In order to perform cloud manufacturing services, the platform imports each order into the appropriate cloud task sequence when the cloud demand set is not vacant. Based on the task type, the appropriate resources are requested from the resource pool while processing cloud tasks. After being requested, resources in an inactive state transition to a busy state. The resource is released and returned to an idle state once the assignment has been finished.
3.1.1. Modeling of Cloud Resource Agent
3.1.2. Modeling of Cloud Task Agent
- (1)
- By means of the enter component, the order is imported into the cloud task’s internal procedure. The order is immediately assigned by the cloud platform if the current task is the first in the task sequence; if not, the preceding task assigns the order after it has been finished (e.g., task 2 orders are assigned by task 1 after task 1 is finished).
- (2)
- The queue component temporarily stores the current order while the following determinations are made: (a) if the current task is first in the task sequence or there is only one task in the previous task sequence, the hold and hold1 components are opened concurrently, and the current order is entered into queue2 for further processing; or (b) if there are multiple tasks in the previous task sequence, the current order must wait until the orders of all previous tasks have been processed before entering queue2 for further processing.
- (3)
- The queue1 component combines the information of multiple branch orders, whereas the hold2 component ensures that only a single order is entered for subsequent processing at any given time. Hold2 reopens and proceeds to serve the next order when the current order is fulfilled and exits through exit.
- (4)
- When the order enters queue3, the task agent selects the optimal service provider and sends “resource request” information to it. When the optimal service provider accepts the request, it chooses to adopt or not adopt the resource replacement strategy according to whether the target resource is faulty. If the resource substitution strategy is adopted, it is necessary to further select which resource substitution strategy to adopt. The busy attribute of the corresponding optimal resource is changed to “true”, the hold3 component opens and the order flows through the delay component to simulate the cloud manufacturing service. After a certain delay time, the service is completed.
- (5)
- The order is placed in queue4 and the “release resource” message is sent to the best server. When the best server acknowledges the message, the busy attribute of the best resource changes from “true” to “false”, and the hold4 component opens. Order traverses the delay1 component, and the release of the resource is accomplished following a predetermined delay period.
- (6)
- The order passes through the exit component to conclude all of its service procedures for this task. It then imports the post-order task sequence of this task: (a) if there is only one post-order task, it is imported instantly into the enter component of the post-order task; (b) if there are numerous post-order tasks, the information of the current order is copied and brought into the enter component of the corresponding post-order tasks; and (c) if there is no post-order task, this indicates that the task is already the last task in the task sequence. As a result, the order is included in the group of completed orders, and data such as the service cycle, service cost, and route record are tallied and output.
3.1.3. Modeling of Cloud Server Agent
3.1.4. Modeling of Other Agent
3.2. Multi-Agent Simulation-Based Robustness Evaluation Indicator
- (1)
- Service time
- (2)
- Service cost
- (3)
- Service reliability
- (4)
- Order completion rate
4. Model of the Cloud Manufacturing Network and Robustness Evaluation Indicator Based on Complex Network
4.1. Development of a Complex Network Model for Cloud Manufacturing
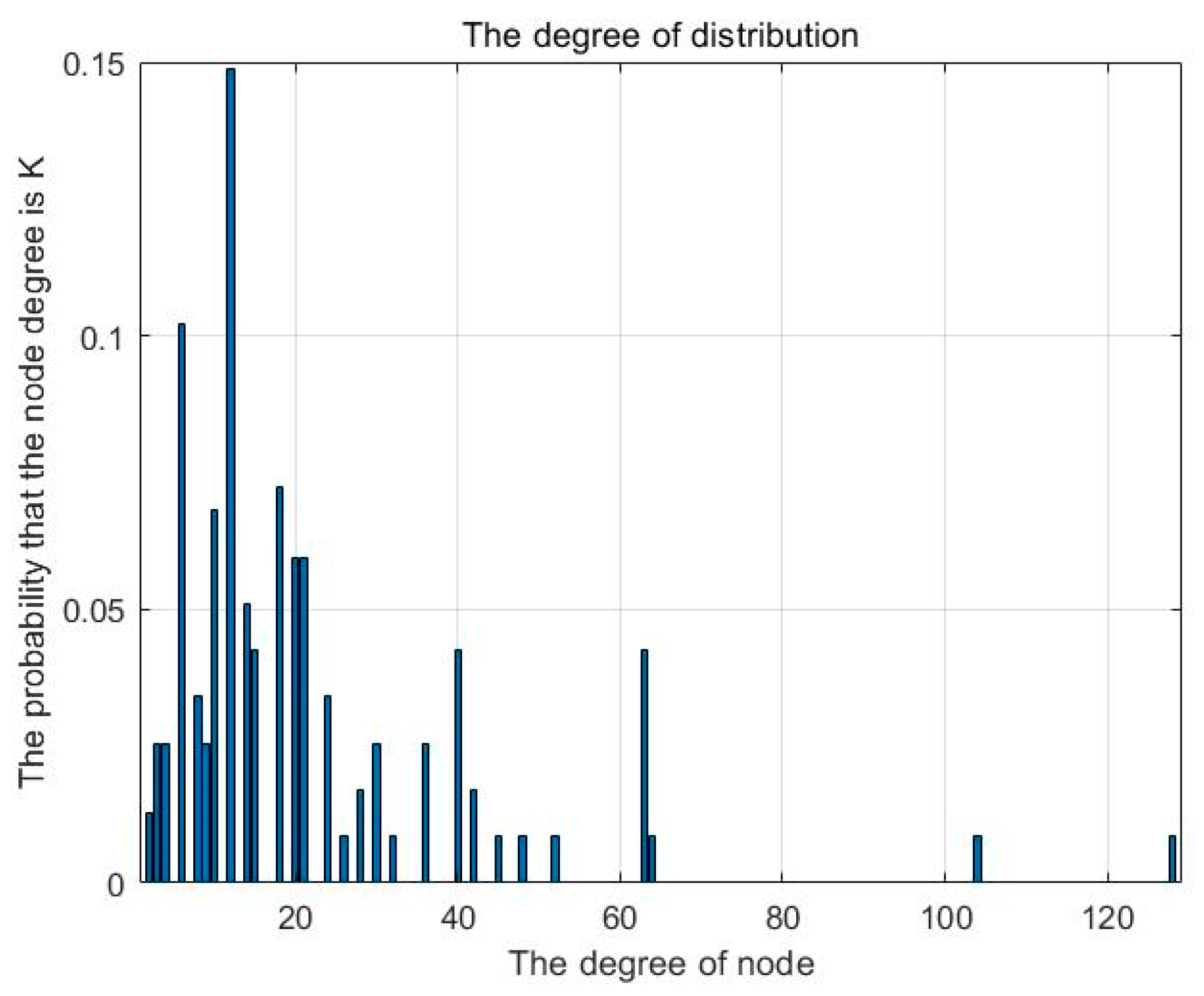
4.2. Evaluation Indicator for Network Robustness Based on Static Topology
5. Robust Failure Mode Definition and Formulation of Multiple Resource Replacement Strategies
5.1. Definition of Failure Modes for Robustness Analysis
5.2. Formulation of Multiple Resource Substitution Strategies
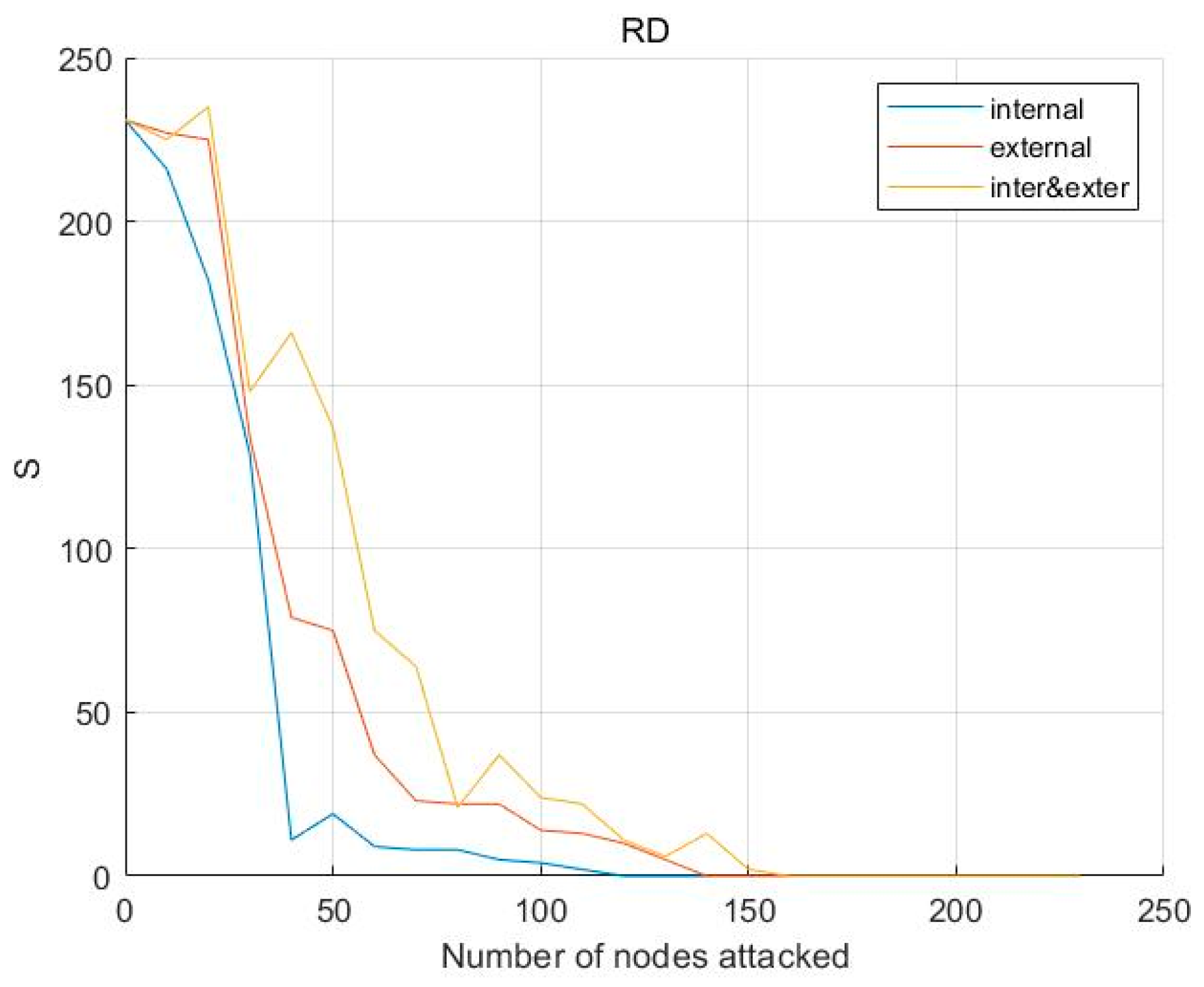
- (1)
- Internal replacement strategy: The cloud service provider Si will internally provide replacement resources Rj for Ri (noted as Ri-Si and Rj-Si, respectively). If Ri-Si fails, Rj-Si will replace it to complete the processing of cloud manufacturing tasks. Although the tasks will be completed, the cloud task time will be increased due to the different resource types, and additional working hours will be incurred.
- (2)
- External replacement strategy: The cloud service provider Sj, Sk…etc. will provide the same type of resources Ri as Ri-Si (recorded as Ri-Sj, Ri-Sk…etc.). When the resource Ri fails, the strategy will comprehensively select the best cloud service provider based on multiple factors, such as resource quotation and the distance between service providers. It will then request alternative resources from them to replace the failed Ri-Si to complete the cloud manufacturing task. Since the resource types are the same, this does not add additional task time; however, the transfer of resources and information among different service providers will generate additional logistics transportation costs and time.
- (3)
- Internal–external integration replacement strategy: This strategy is the combination of the previous two strategies. When a cloud resource fails, this strategy first looks for a replacement resource within the service provider; if no replacement resource is found or its replacement resource also fails, it continues to seek the same type of resource from other service providers. The logical flow of these three strategies is shown in Figure 4.
6. Case Study
6.1. Model Parameters Description
6.2. Structural Robustness Analysis
6.2.1. Structural Robustness Comparison of Three Substitution Strategies under Initial Node Degree Loss (ID) Failure Mode
6.2.2. Structural Robustness Comparison of Three Substitution Strategies under Initial Node Betweenness Loss (IB) Failure Mode
6.2.3. Structural Robustness Comparison of Three Substitution Strategies under Recomputed Node Degree Loss (RD) Failure Mode
6.2.4. Structural Robustness Comparison of Three Substitution Strategies under Recomputed Node Betweenness Loss (RB) Failure Mode
6.3. Process Robustness Analysis
6.3.1. Process Robustness Comparison of Three Substitution Strategies under ID Failure Mode
6.3.2. Process Robustness Comparison of Three Substitution Strategies under IB Failure Mode
6.3.3. Process Robustness Comparison of Three Substitution Strategies under RD Failure Mode
6.3.4. Process Robustness Comparison of Three Substitution Strategies under RB Failure Mode
6.4. Management Suggestion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, B.; Chai, X.; Hou, B.; Li, T.; Zhang, Y.; Yu, H.; Han, J.; Di, Y.; Huang, J.; Song, C.; et al. Networked Modeling & Simulation Platform Based on Concept of Cloud Computing—Cloud Simulation Platform. J. Syst. Simul. 2009, 21, 5292–5299. [Google Scholar]
- Li, B.; Zhang, L.; Wang, S.; Tao, F.; Cao, J.; Jiang, X.; Song, X.; Chai, X. Cloud manufacturing: A new service-oriented networked manufacturing model. Comput. Integr. Manuf. Syst. 2010, 16, 1–7. [Google Scholar]
- Zhao, C.; Zhang, L.; Liu, Y.; Zhang, Z.; Yang, G.; Li, B.H. Agent-based simulation platform for cloud manufacturing. Int. J. Model. Simul. Sci. Comput. 2017, 8, 1742001. [Google Scholar] [CrossRef]
- Jacob, I.; Lu, Y.; Xun, X. Cloud Manufacturing–An Overview of Developments In Critical Areas, Prototypes, and Future Perspectives. IFAC-Pap. 2022, 55, 643–648. [Google Scholar] [CrossRef]
- Narayan Rane, T. System and Risk Analysis of Cloud-Manufacturing System. Int. J. Comput. Sci. Eng. Surv. 2022, 13, 13–27. [Google Scholar] [CrossRef]
- Zeng, Z.; Wu, Q.; Yan, Y. Analysis of Influencing Factors on Cloud Service Composition Flexibility: Based on Perspective of Cloud Manufacturing Service Platform. Sci. Technol. Manag. Res. 2019, 39, 234–239. [Google Scholar]
- Zhang, Y.; Zhang, L.; Liu, Y.; Luo, X. Proof of service power: A blockchain consensus for cloud manufacturing. J. Manuf. Syst. 2021, 59, 1–11. [Google Scholar] [CrossRef]
- Zhu, X.; Shi, J.; Huang, S.; Zhang, B. Consensus-oriented cloud manufacturing based on blockchain technology: An exploratory study. Pervasive Mob. Comput. 2020, 62, 101113. [Google Scholar] [CrossRef]
- Laili, Y.; Lin, S.; Tang, D. Multi-phase integrated scheduling of hybrid tasks in cloud manufacturing environment. Robot Comput.-Int. Manuf. 2020, 61, 101850. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, S.; Kang, L.; Wang, S. An effective dynamic service composition reconfiguration approach when service exceptions occur in real-life cloud manufacturing. Robot Comput. Int. Manuf. 2021, 71, 102143. [Google Scholar] [CrossRef]
- Liang, H.; Wen, X.; Liu, Y.; Zhang, H.; Zhang, L.; Wang, L. Logistics-involved QoS-aware service composition in cloud manufacturing with deep reinforcement learning. Robot Comput. Int. Manuf. 2021, 67, 101991. [Google Scholar] [CrossRef]
- Tao, F.; Zhang, L.; Guo, H.; Luo, Y.; Ren, L. Typical characteristics of cloud manufacturing and several key issues of cloud service composition. Comput. Integr. Manuf. Syst. 2011, 17, 477–486. [Google Scholar]
- Gao, Z.; Zhu, Q.B.; Song, T.X. In Analysis and research on dynamic models of complex manufacturing network cascading failures. In Proceedings of the 2014 Sixth International Conference on Intelligent Human-Machine Systems AND Cybernetics (IHMSC), Hangzhou, China, 26–27 August 2014; Volume 1, pp. 388–391. [Google Scholar]
- Su, Y.; Chai, G.; Liu, P. Topological Structure and Vulnerability of Cloud Manufacturing Network. In Proceedings of the International Conference on Artificial Intelligence and Communication Technology (AICT 2020), Chongqing, China, 7–9 October 2020; p. 5. [Google Scholar]
- Cauvin, A.C.A.; Ferrarini, A.F.A.; Tranvouez, E.T.E. Disruption management in distributed enterprises: A multi-agent modelling and simulation of cooperative recovery behaviours. Int. J. Prod. Econ. 2009, 122, 429–439. [Google Scholar] [CrossRef]
- Li, P.; Cheng, Y.; Tao, F. Failures detection and cascading analysis of manufacturing services collaboration toward industrial internet platforms. J. Manuf. Syst. 2020, 57, 169–181. [Google Scholar] [CrossRef]
- Lachenmaier, J.F.; Lasi, H.; Kemper, H. Simulation of Production Processes Involving Cyber-physical Systems. Procedia CIRP 2017, 62, 577–582. [Google Scholar] [CrossRef]
- Galaske, N.; Anderl, R. Disruption Management for Resilient Processes in Cyber-physical Production Systems. Procedia CIRP 2016, 50, 442–447. [Google Scholar] [CrossRef]
- Hou, Y. Study on Robust Scheduling of Flexible Job Shop based on Process Relationship Network under Machine Failure. Master’s Thesis, Xinjiang University, Urumqi, China, 2020. [Google Scholar]
- Zhang, Z. Research on Robustness of Manufacturing Product Warranty Network. Master’s Thesis, Hangzhou Dianzi University, Hangzhou, China, 2012. [Google Scholar]
- Beygelzimer, A.; Grinstein, G.; Linsker, R.; Rish, I. Improving network robustness by edge modification. Phys. A Stat. Mech. Its Appl. 2005, 357, 593–612. [Google Scholar] [CrossRef]
- Ma, C. Research on Robustness Evaluation of Urban Gas Pipeline Network based on Cascade Failure. Master’s Thesis, North China University of Technology, Beijing, China, 2022. [Google Scholar]
- Ji, X.; Wang, B.; Liu, D.; Chen, G.; Tang, F.; Wei, D.; Tu, L. Improving interdependent networks robustness by adding connectivity links. Phys. A Stat. Mech. Its Appl. 2016, 444, 9–19. [Google Scholar] [CrossRef]
- Li, X. Study on the Robustness of Complex Production Process under Disturbing Environment. Master’s Thesis, Xinjiang University, Urumqi, China, 2018. [Google Scholar]
- Wang, S. Robust Analysis of Production Supply Chain Network. Master’s Thesis, Hangzhou Dianzi University, Hangzhou, China, 2021. [Google Scholar]
- Wang, X.; Cao, J.; Li, R.; Zhao, T. A preferential attachment strategy for connectivity link addition strategy in improving the robustness of interdependent networks. Phys. A Stat. Mech. Its Appl. 2017, 483, 412–422. [Google Scholar] [CrossRef]
- Chen, C.; Zhao, Y.; Qin, H.; Meng, X.; Gao, J. Robustness of interdependent scale-free networks based on link addition strategies. Phys. A Stat. Mech. Its Appl. 2022, 604, 127851. [Google Scholar] [CrossRef]
- Kazawa, Y.; Tsugawa, S. Effectiveness of link-addition strategies for improving the robustness of both multiplex and interdependent networks. Phys. A Stat. Mech. Its Appl. 2020, 545, 123586. [Google Scholar] [CrossRef]
- Bachmann, I.; Valdés, V.; Bustos-Jiménez, J.; Bustos, B. Effect of adding physical links on the robustness of the Internet modeled as a physical–logical interdependent network using simple strategies. Int. J. Crit. Infr. Prot. 2022, 36, 100483. [Google Scholar] [CrossRef]
- Cao, X.; Hong, C.; Du, W.; Zhang, J. Improving the network robustness against cascading failures by adding links. Chaos Solitons Fractals 2013, 57, 35–40. [Google Scholar] [CrossRef]
- Zhu, L.; Li, P.; Yang, X.; Shen, G.; Zhao, Y. EE-RJMTFN: A novel manufacturing risk evaluation method for alternative resource selection in cloud manufacturing. Concurr. Eng. 2019, 27, 3–13. [Google Scholar] [CrossRef]
- Barbosa, J.; Leitão, P.; Adam, E.; Trentesaux, D. Dynamic self-organization in holonic multi-agent manufacturing systems: The ADACOR evolution. Comput. Ind. 2015, 66, 99–111. [Google Scholar] [CrossRef]
- Dobrescu, R.; Merezeanu, D.; Mocanu, S. Process simulation platform for virtual manufacturing systems evaluation. Comput. Ind. 2019, 104, 131–140. [Google Scholar] [CrossRef]
- Chen, T.; Chiu, M. Development of a cloud-based factory simulation system for enabling ubiquitous factory simulation. Robot Comput. Int. Manuf. 2017, 45, 133–143. [Google Scholar] [CrossRef]
- Zhang, L.; Zhou, L.; Ren, L.; Laili, Y. Modeling and simulation in intelligent manufacturing. Comput. Ind. 2019, 112, 103123. [Google Scholar] [CrossRef]
- Zhao, C.; Luo, X.; Zhang, L. Modeling of service agents for simulation in cloud manufacturing. Robot Comput. Int. Manuf. 2020, 64, 101910. [Google Scholar] [CrossRef]
- Zhao, C.; Wang, L.; Zhang, X. Service agent networks in cloud manufacturing: Modeling and evaluation based on set-pair analysis. Robot Comput. Int. Manuf. 2020, 65, 101970. [Google Scholar] [CrossRef]
- Eisa, M.; Younas, M.; Basu, K.; Awan, I. Modelling and Simulation of QoS-Aware Service Selection in Cloud Computing. Simul. Model Pract. Theory 2020, 103, 102108. [Google Scholar] [CrossRef]
- Zhou, L.; Zhang, L.; Ren, L. Modelling and simulation of logistics service selection in cloud manufacturing. Procedia CIRP 2018, 72, 916–921. [Google Scholar] [CrossRef]
- Vespoli, S.; Grassi, A.; Guizzi, G.; Santillo, L.C. Evaluating the advantages of a novel decentralised scheduling approach in the Industry 4.0 and Cloud Manufacturing era. IFAC Pap. 2019, 52, 2170–2176. [Google Scholar] [CrossRef]
- Li, B.; Zhang, L.; Ren, L.; Chai, X.; Tao, F.; Luo, Y.; Wang, Y.; Yin, C.; Huang, G.; Zhao, X. Further discussion on cloud manufacturing. Comput. Integr. Manuf. Syst. 2011, 17, 449–457. [Google Scholar]
- Zheng, X.; Zhang, X. Robustness of Cloud Manufacturing System Based on Complex Network and Multi-Agent Simulation. Entropy 2023, 25, 45. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Wang, S.; Gao, S.; Guo, X.; Yang, B. Adaptive multi-objective service composition reconfiguration approach considering dynamic practical constraints in cloud manufacturing. Knowl. Based Syst. 2021, 234, 107607. [Google Scholar] [CrossRef]
- Yang, B.; Wang, S.; Cheng, Q.; Jin, T. Scheduling of field service resources in cloud manufacturing based on multi-population competitive-cooperative GWO. Comput. Ind. Eng. 2021, 154, 107104. [Google Scholar] [CrossRef]
- Huang, B.; Li, C.; Tao, F. A chaos control optimal algorithm for QoS-based service composition selection in cloud manufacturing system. Enterp. Inf. Syst. 2014, 8, 445–463. [Google Scholar] [CrossRef]
- Zhou, H. Research on Dynamic Robustness of Knowledge Collaboration Network of Open Source Product Community. Ph.D. Thesis, University of Science and Technology Beijing, Beijing, China, 2018. [Google Scholar]
- Lei, S. Robustness of Open-Source Community Knowledge Collaboration Network based on Multiple Failure Modes. Ph.D. Thesis, University of Science and Technology Beijing, Beijing, China, 2022. [Google Scholar]
- Zhao, Q. Supply Chain Modeling and Robustness Analysis in the Perspective of Complex Network-a Case Study of Smartphone Supply Chain. Master’s Thesis, Beijing University of Posts and Telecommunications, Beijing, China, 2021. [Google Scholar]











| Failure Mode Description | Failure Mode Calculation Process | |
|---|---|---|
| Resource failure based on initial topology | Initial node degree loss (ID) | Sort the resource nodes in the initial network (Network-0) by degree, from largest to smallest. Remove one node at a time, and repeat n times until all nodes in the network are removed. |
| Initial node betweenness loss (IB) | Sort the resource nodes in the initial network (Network-0) by betweenness, from largest to smallest. Remove one node at a time, and repeat n times until all nodes in the network are removed. | |
| Resource failure based on recomputed topology | Recomputed node degree loss (RD) | Sort the resource nodes in the initial network (Network-0) by degree, from largest to smallest. Remove the first node and generate a new network (Network-1). Recalculate and sort the resource nodes in the new network (Network-1) by degree, from largest to smallest. Remove the first node and generate a new network (Network-2) … and so on, until all nodes in the network are removed. |
| Recomputed node betweenness loss (RB) | Sort the resource nodes in the initial network (Network-0) by betweenness, from largest to smallest. Remove the first node and generate a new network (Network-1). Recalculate and sort the resource nodes in the new network (Network-1) by betweenness, from largest to smallest. Remove the first node and generate a new network (Network-2) … and so on, until all nodes in the network are removed. |
| Order Type | Cloud Service Route | Order Type | Cloud Service Route |
|---|---|---|---|
| Order 11 |  | Order 12 |  |
| Order 13 |  | Order 14 |  |
| Order 15 |  | Order 16 |  |
| Order 21 |  | Order 22 |  |
| Order 23 |  | Order 24 |  |
| Order 25 |  | Order 26 |  |
| Order 31 |  | Order 32 |  |
| Order 33 |  | Order 34 |  |
| Order 41 |  | Order 42 |  |
| Order 43 |  | Order 44 |  |
| Order 51 |  | Order 52 |  |
| Order 53 |  | Order 54 |  |
| Task | Resource | Task | Resource | Task | Resource | Task | Resource |
|---|---|---|---|---|---|---|---|
| t1 | (r1) | t2 | (r3) | t3 | (r2) | t4 | (r4) |
| t5 | (r11, r30) | t6 | (r5) | t7 | (r12, r29) | t8 | (r6) |
| t9 | (r12, r29) | t10 | (r31) | t11 | (r11, r30) | t12 | (r67) |
| t13 | (r32) | t14 | (r1) | t15 | (r7) | t16 | (r1) |
| t17 | (r2) | t18 | (r8) | t19 | (r2) | t20 | (r5) |
| t21 | (r5) | t22 | (r41) | t23 | (r6) | t24 | (r6) |
| t25 | (r71) | t26 | (r42) | t27 | (r33) | t28 | (r9) |
| t29 | (r9) | t30 | (r34) | t31 | (r10) | t32 | (r10) |
| t33 | (r9) | t34 | (r7) | t35 | (r9) | t36 | (r7) |
| t37 | (r10) | t38 | (r8) | t39 | (r10) | t40 | (r8) |
| t41 | (r13, r14) | t42 | (r61) | t43 | (r21, r23) | t44 | (r51, r52) |
| t45 | (r15, r16) | t46 | (r62) | t47 | (r22, r24) | t48 | (r53, r54) |
| t49 | (r21, r23) | t50 | (r47, r48) | t51 | (r47, r48) | t52 | (r33) |
| t53 | (r35, r37) | t54 | (r63) | t55 | (r43, r45) | t56 | (r22, r24) |
| t57 | (r49, r50) | t58 | (r49, r50) | t59 | (r34) | t60 | (r36, r38) |
| t61 | (r64) | t62 | (r44, r46) | t63 | (r35, r37) | t64 | (r41) |
| t65 | (r41) | t66 | (r39) | t67 | (r25, r27) | t68 | (r65) |
| t69 | (r13, r14) | t70 | (r36, r38) | t71 | (r42) | t72 | (r42) |
| t73 | (r40) | t74 | (r26, r28) | t75 | (r66) | t76 | (r15, r16) |
| t77 | (r47, r48) | t78 | (r51, r52) | t79 | (r57, r58) | t80 | (r47, r48) |
| t81 | (r49, r50) | t82 | (r53, r54) | t83 | (r68) | t84 | (r59, r60) |
| t85 | (r49, r50) | t86 | (r57, r58) | t87 | (r17, r19) | t88 | (r63) |
| t89 | (r55) | t90 | (r59, r60) | t91 | (r18, r20) | t92 | (r69) |
| t93 | (r64) | t94 | (r70) | t95 | (r56) |
| Resource | Alternative Resource | Re-Source | Alternative Resource | Re-Source | Alternative Resource | Re-Source | Alternative Resource |
|---|---|---|---|---|---|---|---|
| r1 | r2 | r2 | r1 | r3 | r4 | r4 | r3 |
| r5 | r6 | r6 | r5 | r7 | r8 | r8 | r7 |
| r9 | r10 | r10 | r9 | r11 | r12 | r12 | r11 |
| r13 | r16 | r14 | r15 | r15 | r14 | r16 | r13 |
| r17 | r20 | r18 | r19 | r19 | r18 | r20 | r17 |
| r21 | r24 | r22 | r23 | r23 | r22 | r24 | r21 |
| r25 | r28 | r26 | r27 | r27 | r26 | r28 | r25 |
| r29 | r30 | r30 | r29 | r31 | r32 | r32 | r31 |
| r33 | r34 | r34 | r33 | r35 | r38 | r36 | r37 |
| r37 | r36 | r38 | r35 | r39 | r40 | r40 | r39 |
| r41 | r42 | r42 | r41 | r43 | r44 | r44 | r43 |
| r45 | r46 | r46 | r45 | r47 | r49 | r48 | r50 |
| r49 | r47 | r50 | r48 | r51 | r53 | r52 | r54 |
| r53 | r51 | r54 | r52 | r55 | r56 | r56 | r55 |
| r57 | r59 | r58 | r60 | r59 | r57 | r60 | r58 |
| r61 | r62 | r62 | r61 | r63 | r64 | r64 | r63 |
| r65 | r66 | r66 | r65 | r67 | r68 | r68 | r67 |
| r69 | r70 | r70 | r69 | r71 | r72 | r72 | r71 |
| ID | City | Location (Latitude, Longitude) | ID | City | Location (Latitude, Longitude) |
|---|---|---|---|---|---|
| S1 | Beijing | (39.91, 116.41) | d5 | Jinan | (36.4, 117) |
| S2 | Shanghai | (31.21, 121.43) | d6 | Lanzhou | (36.03, 103.73) |
| S3 | Chengdu | (30.66, 104.06) | d7 | Wulumuqi | (43.76, 87.68) |
| S4 | Hangzhou | (30.26, 120.2) | d8 | Changsha | (28.21, 113) |
| S5 | Shenzhen | (22.61, 114.06) | d9 | Nanchang | (28.68, 115.9) |
| d10 | Fuzhou | (26.08, 119.3) | |||
| d1 | HaErbin | (45.75, 126.63) | d11 | Nanning | (22.48, 108.19) |
| d2 | ShenYang | (41.8, 123.38) | d12 | Lasa | (29.6, 91) |
| d3 | Baotou | (40.39, 109.49) | d13 | Lianyungang | (34.36, 119.1) |
| d4 | Tianjin | (39.13, 117.2) | d14 | Hefei | (31.52, 117.17) |
| Topological Parameter | Number of Nodes | Average Degree | Density | Average Path Length |
|---|---|---|---|---|
| Cloud resource network | 231 | 21.208 | 0.087 | 4.231 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Zheng, X.; Wang, Y. Robustness Optimization of Cloud Manufacturing Process under Various Resource Substitution Strategies. Appl. Sci. 2023, 13, 7418. https://doi.org/10.3390/app13137418
Zhang X, Zheng X, Wang Y. Robustness Optimization of Cloud Manufacturing Process under Various Resource Substitution Strategies. Applied Sciences. 2023; 13(13):7418. https://doi.org/10.3390/app13137418
Chicago/Turabian StyleZhang, Xiaodong, Xin Zheng, and Yiqi Wang. 2023. "Robustness Optimization of Cloud Manufacturing Process under Various Resource Substitution Strategies" Applied Sciences 13, no. 13: 7418. https://doi.org/10.3390/app13137418
APA StyleZhang, X., Zheng, X., & Wang, Y. (2023). Robustness Optimization of Cloud Manufacturing Process under Various Resource Substitution Strategies. Applied Sciences, 13(13), 7418. https://doi.org/10.3390/app13137418








