Abstract
Electronic-commerce (e-commerce) has become a provider of distinctive services to individuals and companies due to the speed and flexibility of transferring orders and completing commercial deals across far and different places. However, due to the increasing attacks on penetrating transaction information or tampering with e-commerce requests, the interest in protecting this information and hiding it from tamperers has become extremely important. In addition, hacking these deals can cause a huge waste of money and resources. Moreover, large numbers of connected and disconnected networks can cause significant disruption to the built-in security measures. In this paper, we propose to design a protocol to protect transaction information based on ElGamal, advanced encryption standard (AES) and Chinese remainder theorem (CRT) techniques. In addition, our protocol ensures providing scalability with high-performance security measures. We combine these algorithms with a robust methodology that supports the balance of performance and security of the proposed protocol. An analysis of our results proves that our protocol is superior to existing security protocols.
1. Introduction
The online shopping sector, commonly known as e-commerce, has grown dramatically in recent years as a result of technological advancements. More and more customers are choosing to utilize on-line shopping because of the quick advancement in information technology gadgets and Internet connectivity. The evolution of shopping mechanisms is influenced by a variety of social, technological, cultural, and psychological elements, which contribute to e-commerce’s success. The most frequently utilized platform on the Internet is probably e-commerce websites, online auctions and mobile applications. Customers or buyers can order high-tech items, digital music files, books, services, etc., through e-commerce. Additionally, electronic apps provide a wide range of services and prospects, such as chances for developing payment invoices, buying and selling operations, and providing electronic services to customers and institutions via the Internet trade progress [1]. According to [2] in 2021, e-commerce sales increased dramatically at the level of countries; for example, the United Kingdom spent USD 169.02 million and the United States spent USD 843.15 million and USD 2779.31 million; this indicates that e-commerce has become a hugely influential economic factor around the world.
Due to the rise in credit card theft and compromised client accounts, e-commerce security has lately been a major concern. Compromising of customers’ account information and credit card fraud are the two most serious security issues that are known to affect e-commerce [3]. The usage of e-commerce has significantly developed over the past several decades, and as a result, there are now exponentially greater transactions and numbers of payments made on online platforms. E-commerce has sophisticated an explosion of development, leading to security risks that threaten the personal information of users and attempt to detect private, public, and shared keys [4] in encrypting commercial and personal data/information [5]. Bitcoin, Litecoin, Freicoin, and Peercoin are among the currency-encryption approaches utilized in e-commerce applications. Some of these schemes apply cryptography algorithms to provide confidentiality and secrecy features [6]. It is common for e-commerce applications to be attacked (see Figure 1) by the types of common risks such as distributed denial of service (DDoS), phishing, wiretapping, brute force (BF), distributed guessing, financial fraud, sabotage, modification, ransomware, sniffer and zero-day. For instance, by producing a large number of malicious requests, a DDoS will crash the e-commerce applications and make them unusable for customers. Furthermore, e-commerce requests may be collected and modified through wiretapping on the transferred transaction encryption over the Internet. In addition, hackers use phishing attacks to capture the confidential information of customers through the creation of fake websites that are similar to real websites. Moreover, by using all possible combinations of characters, BF will crack passwords. Customers’ private data and payment transactions have become major concerns [7]. Furthermore, financial fraud is committed through the theft of private information from credit cards when e-commerce platforms use this method to purchase services and products. Additionally, it occurs through false requests for credit returns through unauthorized transactions.
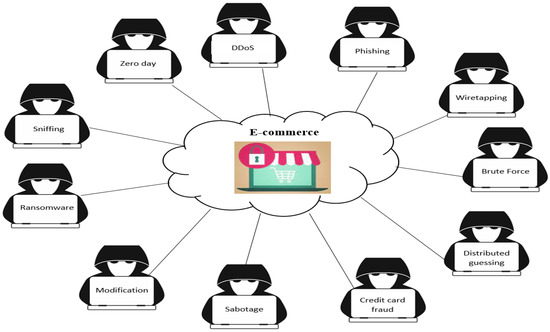
Figure 1.
Various attacks against e-commerce sector.
A report published by [8] indicates that e-commerce attacks are constantly increasing; for example, from 2020 to 2021, there was an increase in credit card fraud attacks from 65% to 68%, BF from 11% to 11.5%, phishing from 56% to 71%, etc. This report also indicated that security-related incidents on Black Friday/Cyber Monday accounted for 17.5% of the total number of e-commerce requests. According to the report [9], 62% of attacks against e-commerce were automated. E-commerce transactions are exposed to various types of threats and attacks due to the rapid development of Internet websites; therefore, the system becomes unsafe. In this study, we focus on the security of commercial transactions using asymmetric and symmetric encryption protocols and algorithms. The system will provide strong security using the public key encryption algorithm (ElGamal) and the symmetric encryption algorithm (AES) to make e-commerce transactions more secure. Our main contributions to this research are:
- Designing a lightweight protocol for customer data authentication in e-commerce applications based on ElGamal for key generation and the AES algorithm for data encryption as well as relying on CRT to improve key generation performance.
- Protecting all stored security parameters associated with business application entities in a systematic and robust manner.
- Testing the e-commerce application protocol in the SYTHER tool for verification and analysis of security results, as well as performance testing of the proposed protocol and proving its superiority over existing protocols.
A quick description of how the paper is organized with the key points: Section 1 is the introduction to e-commerce and security risks. In Section 2, we describe related works of e-commerce security. The background about the used techniques with the proposed protocol is discussed in Section 3. Section 4 demonstrates the methods of the proposed e-commerce protocol. The proposed protocol results and discussion are explained in Section 5. In Section 6, we briefly provide the conclusions of this research, and future directions are presented in Section 7.
2. Related Works of E-Commerce Security
Existing research has addressed issues of using symmetric and asymmetric encryption algorithms in e-commerce applications, but the existing schemes still contain many security and performance flaws. This section will review the recent research related to the topic of our research in an extensive manner.
Hu et al. [10] submitted a proposal to develop digital signal processor (DSP) cipher modules for new embedded devices to execute a safe e-commerce app and to design a functional Rivest, Shamir, and Adleman (RSA) plug-in encryption tool that can store and encrypt confidential data originating from online transactions utilizing common web browsers. Secure online transactions are produced from the client side using the RSA algorithm. However, their scheme still has problems, such as increased cost and increased complexity, and the RSA algorithm suffers from key length and large arithmetic operations, which affect performance. Furthermore, space constraints affect the construction and utilization of Internet applications and databases, while large block sizes make execution more complex. In addition, there is a difference in the speed of encryption implementation and encryption.
Saha et al. [11] proposed a scheme to improve the security of the AES algorithm depending on cryptanalysis. Their algorithm is applied in the commercial field. They used a symmetric random function generator (SRFG) to support randomness. In addition, they used randomness in the process of generating keys in each block cipher. Nevertheless, there are some issues in their scheme, such as ignoring the execution time and the high complexity of their algorithm due to large operations, the round keys are kept separate since they are only needed for decryption and are produced at random.
Logunleko et al. [12] suggested using different methods to protect shared and sensitive data by depending on encrypting keys and implementing zero tolerance for data security in transit. Three encryption approaches—extended base64 (EB64), data encryption standard (DES) and AES algorithms—were used to increase the security and effectiveness of sensitive data. They contrasted their findings for both the encryption and decryption processes after looking at the encryption and decryption times provided at each individual testing step. The problem with their suggestion is using large and complex algebraic operations, a difference in the time of encryption and decryption, and that the amount of communication requests increased, which caused a delay in encryption and decryption.
Yousif et al. [13] introduced a proposal for secure images by integrating chaotic schemes and ElGamal public key cryptography with a scanning technique. Additionally, a permuted image was initially built using zigzag and spiral scanning. Next, the permuted image was encrypted utilizing the ElGamal encryption approach. Finally, in the confusion and diffusion phases, the pixel positions were mixed up using Lorenz and Rössler chaotic sequences. Unfortunately, some problems affect the work of their proposal negatively, which are not calculated for high randomness cost and complex operations, or for a difference in the execution time of the encryption due to the increase in the size of the images and the process of high sensitivity. Their system generated the encryption keys, which affected the sensitivity of the key to the decryption. This key sensitivity can add some complexity.
El Laz et al. [14] presented a proposal to use an effective symmetric cipher scheme in electronic systems. The ElGamal encryption system benefits from homomorphic features while maintaining semantic security, and it may be simply modified to fit a variety of cryptographic groups. This is dependent on the selected group sustaining the decisional Diffie–Hellman (DDH) assumption. Of the 26 libraries, that implement ElGamal’s encryption technique, twenty were found to be semantically unsafe because they violate the DDH assumption. Four distinct message-encoding and -decoding algorithms were found and compared from the five libraries that meet the DDH assumption. However, their proposed problems include applications that generate large numbers without test randomness, and this affects security. Moreover, third-message encryption technology is generally difficult and can only be implemented for a small subset of messages where an account can be solved with a discrete logarithm by BF. In addition, the decryption tool is less important than encryption in the electronic process. Some applications do not use the safe initial setting of the ElGamal scheme, which affects security, and some libraries parse part of the information about the original message, which exposes the system to danger and makes the system unsafe.
Ali et al. [15] presented a suggestion about the design of a relational database that covered the creation of a multi-tier secure architecture for integrating the dam management framework with its tasks. They employed the AES technique and generated keys to encrypt and decode the dam data via the password-based key derivation function 2 (PBKDF2), random numbers generator (RNG) sequences generator and the slave key for salting security. However, their suggestion suffered from some problems, including low randomness, complex arithmetic operations efficiency, differences in execution time, encryption and decryption, and long keys being slow due to large dynamic operations.
Mohd and Ashawesh [16] submitted a proposal to optimize operations in encryption algorithms in order to protect digital data and to provide data security using AES cryptography. To decrease the time required for encryption and decryption while still boosting the security of digital data, they reduced the number of rounds in AES to 14. However, their proposal used large arithmetic operations that make encryption operations slow. The encryption transfer rate depends on the size of the files, as well as the speed of the encryption and decryption processes. Employing a key size of 256 makes the encryption process slower and more complex than AES-80 and AES-128. However, AES-256 is safer for applications that deal with sensitive information such as e-commerce applications.
Kumar et al. [17] adopted a recommendation regarding high-speed, low-power hardware designs for effective field programmable gate arrays (FPGA). They implemented AES cryptography to support information security. They used AES encryption and decryption in their method. Combinational logical circuits were used in their architecture to achieve SubBytes and InvSubBytes transformation. Look-up tables (LUTs) were removed from their design, eliminating any unnecessary delays, and a sub-pipelining structure was added to increase the performance of the AES algorithm. To lower the overall hardware requirements, the modified positive polarity Reed Muller (MPPRM) approach was added in this case, and comparisons with various implementations were performed utilizing AES-MPPRM. However, there were several drawbacks to their proposal. The process of generating a key led to consuming more time when expanding the key [18], and the cryptanalysis process checked the algorithm security by testing some threats such as a side channel threat, where their method was weak to some attacks such as DDoS and fraud.
Riadi et al. [19] presented a proposal to use encryption algorithms to secure text document files. They used the ElGamal algorithm. Additionally, they made use of the Fermat prime generator technique, which seeks prime random numbers, from which they derived the randomized prime numbers that made up the public and private keys. Nonetheless, there are some problems with their proposal that may hinder its implementation in real applications. Among these, the ElGamal algorithm suffers from the difficulty of computing the logarithm and large and random arithmetic operations in encryption operations. The algorithm is too complex to encrypt big text files.
Parenreng et al. [20] proposed the use of double encryption by utilizing the ElGamal encryption and the AES encryption approaches to distribute the symmetric key and to secure message data or confidential information. They claimed that their method provides sufficient security and performance when users’ requests are transmitted over the network. Notwithstanding, their method did not provide appropriate performance because the method uses double encryption, the security analysis of the system was not performed in a deep or clear way, and the type of messages was not specified as to whether they were transmitted or stored, such that they were incomprehensible.
Dinata et al. [21] proposed a solution to preserve the integrity of the file and to provide the receiver assurance that the data are unaltered by outside parties. The receiver will be aware that the file is no longer validated if it has been modified, helping them to avoid utilizing the incorrect information. The message digest 5 (MD5) algorithm is used as a hash function method to construct a message digest, and the ElGamal algorithm is used as a public key cryptography to form the digital signature of the message digest in order to guarantee the data validity. However, their proposal is not secure. For example, the MD5 function has the same message digest length for each processed file, which is 32 or 128 bits of message digest. Therefore, if the attacker tries to modify the file, it takes a lot of time to find a pair of data. In the ElGamal algorithm, the public key is on a pair, only one of the private keys, and thus, the compiler cannot encrypt it utilizing any private key. It takes a private key with a pair matching the public key so that it is modified to an unknown. The performance is not balanced with security procedures.
An analysis of the relationship between privacy, security, confidence in the determination to reuse e-commerce apps, and perceived value was proposed by Anshori et al. [22]. Employing the purposive sample method, they applied this strategy to a set of customers who had at least once transacted using the Tokopedia application. The data-collection approach uses Google Forms to distribute surveys online, and the SmartPLS 3.3 program is used to analyze the data using the partial least square (PLS) approach. A total of 242 respondents participated in the survey. Nevertheless, their scheme encountered many problems including that the technique of collecting data was not more in-depth, utilizing random interview techniques with many of the participants. The application of e-commerce suffers from a set of variables such as price and method of promoting goods. This affects the security of e-commerce due to the development of technology exposing types of attacks that lead to the penetration of sensitive user information.
3. Background of E-Commerce and Used Techniques
In order to comprehensively discuss the topic of the research, this section is divided into providing information about the e-commerce methods and security techniques currently used to protect transactions in e-commerce applications.
3.1. E-Commerce Methods
In this section, we will briefly describe e-commerce methods.
- Internet e-commerce:E-commerce services provide access to a number of customers and facilitate buying and selling through the Internet. Customers, people, or businesses can use e-commerce services to access accounts, carry out business transactions, or obtain information about financial goods and services through a public or private network such as the Internet. The use of e-commerce provides convenience for the customer, less time, low cost, ease of use, rapid delivery and payment of bills via the Internet. One of the most important risks of e-commerce services is the security of transactions and the preservation of customer information [23].
- E-commerce payment mannerPayment systems include e-commerce by means of credit cards or checks. The payment of e-commerce invoices is an important advantage of the use of e-commerce. Most customers utilize credit cards or checks when buying goods via e-commerce; Figure 2 shows payment manners in e-commerce applications. Mutual authentication is necessary for a secure electronic payment manner so that parties to the transaction may verify each other’s identities, confidentiality, authentication of transactions, and non-repudiation of customer and company user data. With the increasing proliferation of online shopping centers, the enhancement in payment manners has been studied, as credit cards are widely accepted on e-commerce platforms [24].
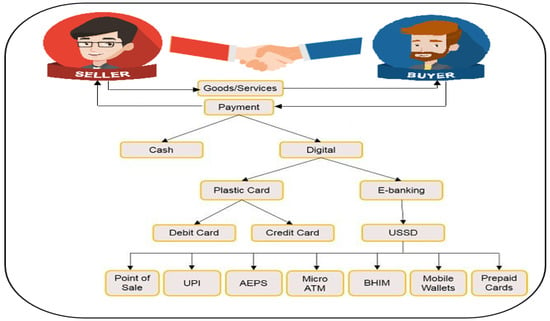 Figure 2. Payment methods in e-commerce.
Figure 2. Payment methods in e-commerce. - E-commerce merchantThe merchant is responsible for the time of delivery of goods, customer choices, customer questions, promoting the quality of goods, and his/her own method of persuading the customer, thus facilitating the process of selecting e-commerce products and selling goods [25].
- E-commerce customerThe attraction of a customer to a vendor indicates that the customer will conduct more transactions with that provider. Providing excellent customer service is a significant approach to generate repeat transactions since clients are likely to continue business with these suppliers again. Nonetheless, any e-commerce app should use the six factors that affect service quality, which will serve as a broad guide to service quality. These factors are tangibility (facilities, equipment, display), reliability (on time), responsiveness (e-commerce provider helps customers if problems occur), assurance (the ability of e-commerce providers to convince customers), empathy (service providers are able to make customers feel personally cared) and security of requests (customer information in e-commerce requests such as selling, purchasing and invoices must be secure; this issue is the most important in making the customer adopt an e-commerce application without another application or vendor) [26].
- Payment gatewayAn e-commerce payment gateway authorizes payments through an intermediary system. In the middle of the payment process, a payment gateway acts as the intermediary between the merchant, customer, e-commerce app and the bank (or card issuer); see Figure 3. Due to the rising popularity of online shopping malls, improvements to credit card payment gateways on e-commerce platforms have been the subject of substantial research in recent years. Secure e-commerce activities are enabled by the public key infrastructure (PKI) authentication system, which establishes a secure connection after the server certificate is validated [27].
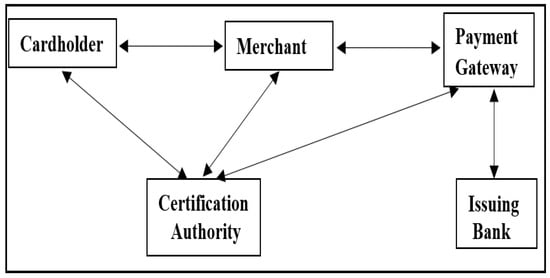 Figure 3. Payment gateway in e-commerce.
Figure 3. Payment gateway in e-commerce.
3.2. Overview of Security Techniques
This section will overview the techniques used in the proposed protocol.
- ElGamal AlgorithmThis is a major asymmetric encryption approach that was invented by Taher El Jamal in 1985. This algorithm depends on Diffie–Hellman key exchange. The algorithm can be an alternative manner for RSA public key encryption [28]. The primary distinction between RSA and ElGamal is that RSA relies on how difficult it is to analyze huge prime numbers, whereas ElGamal’s security depends on how challenging it is to compute the discrete logarithm of large prime numbers. Table 1 shows the comparison between ElGamal and RSA in some characteristics, and ElGamal is characterized by key length, scalability, power consumption, application etc. [29]. Because it depends on the specifics in order to find all potential solutions, the discrete logarithm problem is regarded as one of mathematics’s most challenging. This encryption is almost elusive or very time-consuming [13]. Figure 4 shows the use of ElGamal keys with encryption and decryption. Three procedures—key generation, encryption, and decryption—can be used with the ElGamal algorithm. The following is a brief illustration of each procedure:
 Table 1. Asymmetric cryptography algorithms.
Table 1. Asymmetric cryptography algorithms.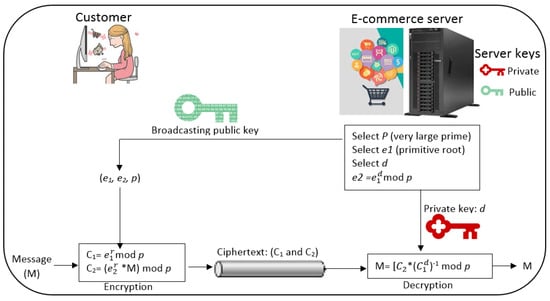 Figure 4. ElGamal keys with encryption and decryption.ElGamal key generation procedure:
Figure 4. ElGamal keys with encryption and decryption.ElGamal key generation procedure:- -
- Generating a large random prime number ();
- -
- Choosing a random number in the period [1,] as a generator number ();
- -
- Choosing an integer () larger than one and less than () as the private number;
- -
- Calculating a public key part value (), where ;
- -
- The private key is , and the public key () is , and .
ElGamal encryption procedure:- -
- Representing the transaction request (plaintext) as an integer , where 0 , and the public key (, , ) is used to achieve encryption;
- -
- Choosing an integer random number such that 1 ;
- -
- Computing the first encryption value , ;
- -
- Computing the second encryption value , ;
- -
- Encryption (E) is .
ElGamal decryption procedure:- -
- Receiver receives the encryption ;
- -
- Using the private key () for decryption procedure;
- -
- Then, r is computed as follows: ;
- -
- E is decrypted by .
The ElGamal algorithm works to increase security, and it is difficult to break [30]. Although the ElGamal cipher algorithm is a popular public-key cryptography algorithm whose security is based on a difficult discrete logarithm problem, the traditional ElGamal encryption algorithm still has some shortcomings including the long ciphertext and the time-consuming calculation, and the higher the complexity, the slower the encryption speed [31]. - Advanced Encryption StandardBlock cipher technology, known as the “advanced encryption algorithm” (or “AES”), operates on 128 bit plaintext and uses the same key for both encryption and decryption. The 128 bit blocks are performed by the AES algorithm, which performs 10, 12, and 14 rounds of operations on each block. It uses an 80, 128, 192 and 256 bit cipher (see Figure 5 [32]). It is made up of a 4-byte array that identifies the state, and in each cipher round, conversions are made as SubBytes (), ShiftRows (), MixColumns and AddRoundK ().
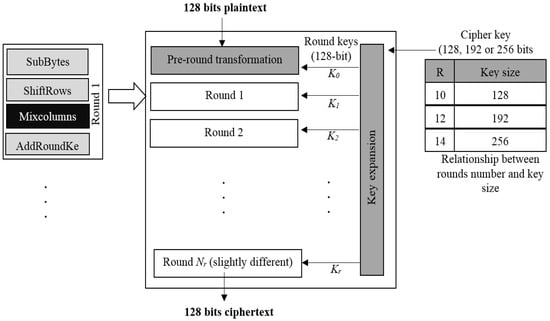 Figure 5. AES algorithm structure.There are four primary functional blocks in AES:
Figure 5. AES algorithm structure.There are four primary functional blocks in AES:- Byte substitution: The byte of each data block is substituted to another block utilizing an S-box.
- Rows shift: Each row receives a cyclic shift to the right relying on where it is in the state matrix.
- Columns mix: In this matrix multiplication process, each column of the state matrix is multiplied by the fixed matrix.
- Round key addition: The new state matrix and the round key matrix are combined using an XOR technique [33].
Distinguishing AES reduces the number of rounds of encryption, reduces data encryption, reduces power consumption and improves the level of security. Table 2 provides a comparison between existing block ciphers with the AES algorithm. Table 2. Comparison between block cipher algorithms.One of the most used symmetric key encryption algorithms is AES, which encrypts and decrypts sensitive data using the same key. Due to its lower cost and simpler execution in both software and hardware, AES is considered the most secure cryptographic method. The encryption and decryption phases of the non-Feistel cipher AES use the same rounds of operations. It has been demonstrated that AES executions on hardware are both quicker and more secure than those on other cryptographic executions [17]. The use of the AES algorithm as a basis decreases the number of encryption rounds and works to increase the complexity and resistance to attacks of various paradigms, leading to more security of data and a safer algorithm [34].
Table 2. Comparison between block cipher algorithms.One of the most used symmetric key encryption algorithms is AES, which encrypts and decrypts sensitive data using the same key. Due to its lower cost and simpler execution in both software and hardware, AES is considered the most secure cryptographic method. The encryption and decryption phases of the non-Feistel cipher AES use the same rounds of operations. It has been demonstrated that AES executions on hardware are both quicker and more secure than those on other cryptographic executions [17]. The use of the AES algorithm as a basis decreases the number of encryption rounds and works to increase the complexity and resistance to attacks of various paradigms, leading to more security of data and a safer algorithm [34]. - Chinese Remainder Theorem TechniqueA theorem in number theory involving simultaneous linear congruences is called the Chinese remainder theorem (CRT). In general, if there are congruences of a certain form, it states:where S is a solution, … are arbitrary integers () and … are pairwise positive integers (). If it has a solution, then the solution is unique in relation to the product …. The equation will satisfy any other solution () if S is a solution to the problem (…). A system of congruences can be solved using the theorem when the moduli have no common factors except 1.This technology was discovered in the world in the third century common era (CE) by the Chinese mathematician Yisunzi Fu Wesunzisuangjing. One of the most crucial theorems in mathematics, CRT is an algorithm for decreasing standard arithmetic by a significant amount for the same arithmetic for each coefficient aspect. In a landscape where new types of applications are open to the perfect combination of beauty and usability, the perfect combination of beauty and usability continues to emerge in new contexts [35]. The CRT algorithm is used in many areas of contemporary research and high-tech industries, including communication, coding, computer, and cryptography [36]. Most recently, the CRT technique and corresponding forms of representation of numbers and methods for reconstructing integers have been studied by residue code, which is intensively used, especially with regard to its application in high-performance calculating. The main focus is on computationally reducing calculations and complexity of the main integrative features of the residue code [37].
4. Proposed Protocol Methodology for E-Commerce
Due to the numerous and varied Internet technologies, the number and kind of sent data across e-commerce have greatly expanded in recent years, which has in turn led to the enormous expansion of e-commerce risks. Several of the data include sensitive data that could be attacked in several ways, including payment data, because security is the biggest issue currently facing all customers, and it plays a crucial role in e-commerce web services. In this study, we use a strong protocol to maintain the security of electronic commerce transactions.
The overall architecture of the proposed e-commerce network includes customers, sellers, delivery services, authenticated servers, goods and services providers (merchants), payment gateways and banking transactions. Figure 6 shows the architecture of the general e-commerce network. Costumers are users around the world who wish to buy a service or goods, sellers are users who try to sell something electronic or physical through e-commerce applications, delivery services are offices that send orders if they are physical things or send via the Internet if they are software or instructions/tips, authenticated servers are computers with large sources that perform and receive authentication requests to ensure the legitimacy of users of e-commerce applications, merchants are users who offer huge and one-class goods for sale through e-commerce applications, and payment gateways are platforms used to support payment authentication, of which there are many popular platforms such as PayPal, PayWay, BrainTree, CorvusPay, etc. A banking transaction is an entity that guarantees the transmission of payments to payment gateways and thus to sellers and merchants. In this paper, we will focus on authenticating customers, sellers and authenticated servers. Documenting the rest of the entities will be left for future research. Initially, we used an asymmetric encryption algorithm for generating keys, the ElGamal algorithm, and a symmetric encryption algorithm for encryption and decryption, the AES algorithm. The following Figure 7 illustrates the general methodology of the proposed protocol.
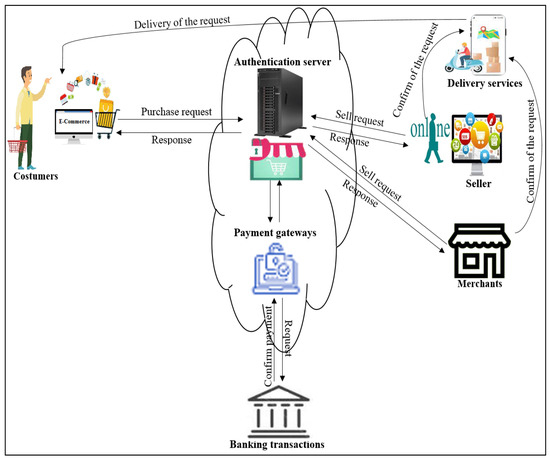
Figure 6.
General network architecture of e-commerce application.
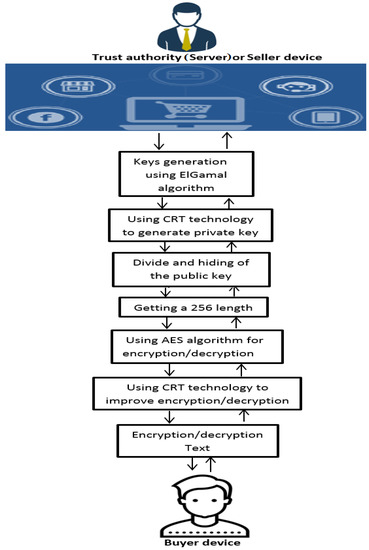
Figure 7.
General diagram for our e-commerce application.
The diagram shows the two types of encryption algorithms we used, symmetric and asymmetric, and we used the CRT technique in the operations of encoding and decoding order information in e-commerce.
4.1. Implicated Symmetric and Asymmetric Cryptography
This section will explain the techniques used in our methodology and how these security measures are used and employed in our protocol. We explain ElGamal, AES and CRT.
4.1.1. Utilizing ElGamal
In our protocol, we need an algorithm that generates large and random keys suitable for encrypting sensitive information in e-commerce applications. There are many asymmetric encryption algorithms, the most prominent of which are ElGamal and RSA. However, we chose ElGamal because it provides faster encryption and decryption processing than RSA, and it consumes less power and provides better scalability than RSA (as shown in Table 1). Our protocol uses the ElGamal algorithm only for generating and calculating public and private keys, and not for encryption and decryption. Encryption and decryption processes are very expensive in asymmetric algorithms such as ElGamal; thus, we use ElGamal only to generate large random keys. ElGamal provides keys with lengths of 1024, 2048, 4096, etc. Our protocol generates a public key of length 1024 and a private key using CRT technology (as shown in the following algorithm).
- Generating a large random prime number (p);
- Choosing a generator number (a);
- Using CRT to generate an random integer (), as the secret number and less than ();
- Computing (d), where ;
- The private key is , and the public key is (), which includes p, a, d.
Then, our protocol divides the public key into four parts, with each part of size 256, and performs the XoR processes for the four parts to obtain a secret and random key ready for use in the AES algorithm. The purpose of using ElGamal is to generate random and different keys for each user of e-commerce applications.
4.1.2. Utilizing the AES Algorithm
The AES algorithm encrypts/decrypts the buy and sell requests upon delivery from the buyer (B), seller (S) or trust authority server (TAS). However, the use of keys as small as 80 and 128 can compromise the customers’ sensitive information. Therefore, our protocol relies on a key length of 256, which is enough to block attacks. In addition, our protocol addresses a scalability problem that is inherent in symmetric algorithms, whereby all users use the same secret key. Our protocol uses a different secret key for each user by using the public keys of the ElGamal algorithm. In addition to the importance of key length, fundamental reasons that AES can be vulnerable to attacks are the randomness level of keys and cryptographic randomness. Therefore, our protocol uses strong AES ciphers that provide appropriate key length (256 bit), key randomness (ElGamal), and cryptographic randomness through the use of a random salt with fewer performance expenses.
4.1.3. Utilizing the CRT Technique
The CRT technique can be used to support randomness issues for encryption algorithms. In addition, it can be used to support performance issues in encryption, decryption and keys generation. This technique is used with the ElGamal algorithm to generate random keys, especially private ones, to increase the randomness, and it is used with the ElGamal algorithm with a faster operating speed, a smaller key, and an increase in the working time capacity with the system. The keys are later used in the process of encryption and decryption for the encryption process, i.e., changing the original text into ciphertext using a public key and for the decryption procedure, which changes the ciphertext into original text/plaintext using a private key. This technique works to represent and process large operands in ciphertext polynomials and to reduce large numbers to small ones. Namely, we use CRT to reduce the private key length and to support its randomness. In our protocol, we relied on CRT to calculate Salt to support the random handling of encryption and decomposition in AES.
4.2. Buying and Selling Requests and Invoices
We implement encryption operations based on the AES algorithm for a set of encryption requests, and there are forms of requests that buy and sell requests and invoices. Figure 8 shows types of request forms. The request information is encrypted, whether it is a request to buy or sell or pay bills, based on the request procedure. Requests forms used in this research are real forms for e-commerce applications, which are forms taken from free databases [38] on the Internet and do not contain personal information or network. In order to complete the encryption process and decryption for the purchase requests to sell and invoice properly, we added some personal information and unreal request data for virtual users. We encrypt a request received from the customer or buyer based on the AES method and then sent it to the TAS. Here, information is encrypted and difficult to hack (if the encryption is strong with high key randomness) by legitimate network parties, and personal information is protected for both the client and the server.
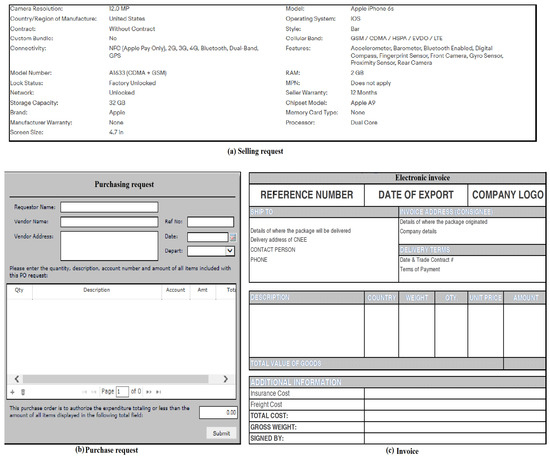
Figure 8.
Selling and buying requests and invoice.
4.3. Proposed Protocol Procedures
In designing the protocol, we rely on the method of encrypting and decrypting request transactions. This is performed using symmetric and asymmetric encryption algorithms. We use the AES algorithm to encrypt the text and request information. We follow the following steps (Figure 9 shows our proposed protocol procedures):
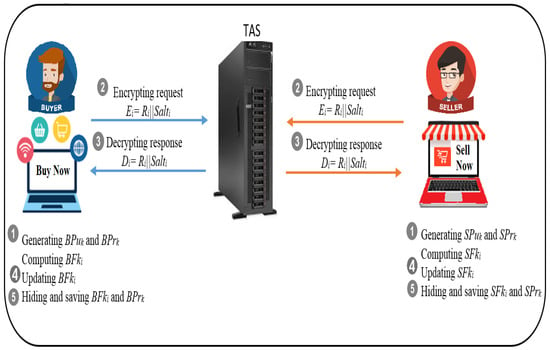
Figure 9.
Proposed methodology procedures.
- We generate random keys that are the private and public keys by default using an ElGamal asymmetric encryption algorithm. Then, we divide the random key whose size is from 1024 to 256 bit to fit the AES algorithm keys.
- We use this public key to encrypt the e-commerce requests among B, S and . Our protocol performs strong encryption using high encryption randomness, which is difficult to crack when sent from B to S.
- The request information will be decrypted using the AES and ElGamal keys. The buyer/seller receives a decrypted text that is difficult to penetrate from an attacker.
- Public and private keys are updated when required or when the number of key mix-ups has expired.
- Hiding information and security parameters on network devices, especially keys, is important in cases of hacking of these devices.
Keys Generation Procedure
The first procedure in our protocol is the key generation procedure. Algorithm 1 refers to the operations performed for the key generation procedure. Key generation instructions for the ElGamal algorithm are described earlier in Section 3.2. In this section, we will describe directives added to support public and private key security. Initially, the parameters and were used to generate the keys in ElGamal. We use ElGamal to generate public keys with a size of 1024 bit. In addition, we make use of ElGamal-CRT to generate the private key (). To support randomness in public keys, we split the public key () into subkeys (). These are , , and with a length of 256 bit, which fits the AES algorithm. Our protocol performs the operations and . Then, our protocol obtains the final key () of length 256 bit through (where can be the value of , , and ). To protect the keys and on network devices, they are hidden using the operations result () = (where represents the interim value) and final key ephemeral () = . At this point, and are safely stored on devices using e-commerce applications. On the next connection, our protocol moves to the fourth step in Algorithm 1 without generating keys. Our protocol relies on scrambling to use new public keys; for example, our protocol computes and and then performs the same operations in Algorithm 1 until 16 connections are completed. If the network device has made 16 connections in e-commerce applications, then in the next connection, it should start from step 1 in Algorithm 1. Bypassing key generation for 16 connections reduces computational costs, especially in .
| Algorithm 1 Keys generation procedure |
Input: , values and Output: and keys with 256 bit length
|
Encryption Procedure
To perform the encryption process in our protocol, , , and (buying, selling or invoice request) are used. However, before the encryption process can be performed, the keys and that are hidden on the network devices must be extracted. As described in Algorithm 2, Steps 1 and 2 represent the extractions of and for use in AES-256 ciphers. Next, our protocol uses a CRT technique with the key to obtain a random with minimal computational overhead. Then, our protocol uses and to perform the encryption operations, whereas the encryption operation is executed through the operation . Our protocol uses the operation to obtain a hidden ephemeral salt (). Finally, the cipher is sent to the target device. In the same way, and are hidden by to prevent attackers from hacking the device and from gaining security parameters.
| Algorithm 2 Encryption procedure |
Input: , keys with 256 bit, and Output: and
|
Decryption Procedure
The encryption procedure is followed by a process called decryption. After the target device receives the encrypted request, it decrypts it with the public and private keys as well as security parameters such as . For example, sellers need to decrypt buyers’ requests to identify the type of request, the quantity ordered, the destination of the request, and the information that represents the invoice payment. In the same way as Algorithm 2, Algorithm 3 extracts the keys and stored on network devices during steps 1 and 2. Next, the receiver receives requests such as , then subtracts from the encryption request, and then extracts from to perform the decryption process. Then, our protocol uses and to perform the decoding of by . After the receiving device receives the explicit text of the requests, it is stored in the datasets for archiving. In the same manner as Algorithms 2 and 3, it stores keys anonymously.
| Algorithm 3 Decryption procedure |
Input: keys with 256 bit, and Output:
|
Keys Updating Procedure
For a protocol to be robustly designed for security, it should include a key update procedure (see Algorithm 4). Initially, our protocol applies steps 1 to 6 in Algorithm 1 which performs key generation operations and and then obtains by ElGamal-CRT and by mixing . To hide , the last salt () is used within the process . The sender (buyer) sends to the receiver (seller). Finally, public and private keys are protected on network devices in the same way as Algorithms 1–3.
| Algorithm 4 Keys updating procedure |
Input: , values and Output: and keys with 256 bit length
|
5. Security and Performance of Proposed E-Commerce Applications
This section will discuss security analysis by testing the ability of our protocol to block e-commerce attacks; after that, the Scyther tool is used to test the security of our protocol in practice.
5.1. Attacks Analysis on Our Protocol
The security analysis of a range of e-commerce attacks is summarized as follows (Table 3 provides a comparison of cryptographic protocols in terms of blocking attacks within the scope of this research):

Table 3.
Comparison of threat resistance between cryptography protocols.
- DDoSAn attacker tries to stop all the services provided by the servers and makes them unavailable to the customers/buyers/sellers, and the goal is to prevent user requests from being fulfilled by servers in e-commerce applications, whether buying or selling or e-commerce payment operations. DDoS attacks are more perilous than DoS attacks, and the reason is that DDoS uses several different systems to attack from multiple locations, which makes the impact of stopping the network bigger and faster. In addition, it is difficult to track. Moreover, e-commerce applications deal with sensitive information, and any delay or blocking of user requests can cause economic disasters. Preventing these attacks completely is very difficult. However, limiting its impact and mitigating its severity are crucial. Our protocol uses a small token inside that proves the legitimacy of the connected device. This process is inexpensive to perform (). Thus, our protocol is able to mitigate the risk of DDoS attacks.
- PhishingAn attacker tries to penetrate the personal information (usernames, passwords and credit card) of the buyers or sellers or to penetrate the information of requests or the information of a company or institution that is sensitive and important in e-commerce applications. Phishing attacks rely on mined links or malicious malware to steal confidential information. Our protocol does not allow e-commerce applications to transmit or send links between users (buyers and sellers). Even if a user downloads malware without knowing it or accidentally clicks on a link in other programs, the malware or the attacker will not receive clear and useful information about that user. In addition, is not stored on users’ machines. Therefore, our protocol repels phishing attacks.
- WiretappingAn unauthorized intruder or attacker tries to access the company’s or user’s data by eavesdropping on purchase and sale requests between the buyer/seller and the servers by revealing and analyzing the transmitted request. This attack is resisted using a request information encryption ( process) based on the AES 256 algorithm. These requests can be decrypted with only their private and public key. Process breaking the encryption is impossible because the buying/selling request data are hidden.
- Brute forceIn this attack, the attacker tries to access confidential information such as , and in e-commerce applications. This attack relies on trial and error to gain access to the or login credentials. Our protocol does not transmit any confidential information in the encryption and decryption procedures. For example, does not contain any explicit secret parameters (see Algorithms 2 and 3). No matter how hard the attacker tries to hack/crack , and , it is not possible because it is not transmitted through the unsecured channel. Additionally, is not stored on network devices. Moreover, is selected according to strict security criteria (such as uppercase and lowercase letters, symbols, etc.). As a result, our protocol is able to completely prevent brute force attacks.
- Distributed guessing for electronic paymentThe guesser’s probability of succeeding on a randomly chosen key depends on the probability of guessing . The guesser attempts to capture the packet passing from the sender to the receiver in order to decrypt it using a single guess or distributed multiple guesses. An attacker can use distributed guesses to reveal secret parameters if they are sent explicitly, use as an encryption key, or use weak security measures. In addition, the guesser uses a large number of guesses to make this attack more effective. The attacker cannot decrypt the electronic payment details (see Figure 8c) because we rely on a sufficiently long, random 256 bit key to fend off this type of attack. Our protocol does not send secrets over the insecure channel. In addition, when the guesser captures the packet, it cannot parse it to derive the keys and . Therefore, our protocol deservedly resists this attack.
- Credit card fraudA fraudster tries to access a customer’s account and compromises a credit card account in order to obtain secret parameters (such as the credit card number, the card security code, or knowing the expiration of the attack value) for the user/company. An attacker uses document falsification and fraudulent information using credit card fraud attacks. Even if the fraudster receives some credit card details or uses some fake details, he/she does not have secret parameters such as and without which he/she cannot complete the e-commerce transactions. Thus, our protocol is able to prevent this type of attack.
- SabotageA saboteur intends to destroy, subvert or obstruct by penetrating certain websites, stopping the system of a company/institution, stopping the sale/purchase requests or online payment operations, or sending sensitive information from the client or server to another party. Infecting an e-commerce app with a malicious program is an example of online buying and selling environment sabotage. A more extreme instance is causing e-commerce in a nation to go down. To counter this attack, our protocols use that change each time the buyer and seller’s devices connect to the e-commerce network.
- Data modificationAn attacker attempts to penetrate the exchanged e-commerce information then modifies or deletes the information of the e-commerce requests (purchasing, selling and invoices), and changes some of its contents or prevents access to the information receiver. In order to prevent this attack, we maintain the confidentiality of the information by implementing an encryption algorithm (AES-256). In our protocol, any change in e-commerce requests will be detected by the receiver app because our protocol uses specific forms for e-commerce requests. If the attacker makes a change to the encrypted requests, upon decryption, the change will be exposed and not match the forms used.
- RansomwareAn attacker compromises a website or application by injecting or analyzing to try to obtain secrets such as a credit card number, encryption keys and , and they use this information to demand a ransom from the targeted victims. Then, attackers can demand the ransom online payment or even set up a ransom program. If the victim does not pay or execute the ransom, the attacker either destroys the data, publishes the data, or encrypts the data in a way that the victim cannot access. In our protocol, if an attacker can access , and (which is impossible) on the current connection, the attacker will not benefit from these parameters because they will not be used on the next connection. That is, the attacker cannot demand ransom for the secret parameters even if he/she receives them. We use a protocol that combines encryption algorithms such as ElGamal-1024 and AES-256, which are difficult to penetrate due to their high security.
- SniffingAn unauthorized sniffer monitors, intercepts and captures all sensitive request data for the targeted network that passes through the sending and receiving processes of a certain request. The goal of this attack is to expose login credentials and financial information or to hijack a target’s device by sending a packet or group of packets to the victim’s device to gain access to sensitive information. In our protocol, any packet that does not use legitimate parameters such as for the receiver device will be rejected outright. Thus, our protocol does not handle requests that use hijacking packets. Our protocol applies encryption and decryption procedures to all network devices (buying, selling and server), namely, our protocol resists these attacks.
- Zero dayThe attacker tries to exploit security vulnerabilities in e-commerce software or applications to use them to carry out malicious attacks on network devices and applications. In commerce institutions, an attacker tries to obtain sensitive transaction information or execute fraudulent threats. After the attacker carries out this attack, he/she tries to exploit the documents, files and information to apply his/her attack on the entire network. When detection of this attack is delayed, this can give the attacker time to apply their attack on a larger scale. If we assume that the attacker penetrates one of the network devices (buyer, seller or server device) and obtains requests for buying, selling or invoices, then he will not benefit from these files because they are all encrypted on the network devices. In addition, all security parameters are hidden (such as ) on network devices. Therefore, our protocol supports robust protection of e-commerce applications and controls zero day attacks.
5.2. Security Analysis Using Scyther
One automated tool for verifying security protocol is called Scyther. It has a number of intriguing characteristics, including the ability to characterize protocols and produce a finite representation of all conceivable protocol behaviors. It can also verify protocols with an infinite number of sessions and nonces. This tool is the result of research by Cremers Cas in 2006. During that time, Cremers Cas published his research related to a methodology for formal analysis and verification of encryption. It is a tool designed to analyze formal security protocols and their security requirements and was designed assuming full or unbreakable encryption. Furthermore, Scyther is used to verify security claims and to find potential attacks against authentication protocols, for instance, sales, purchases or payment operations in e-commerce. This tool analyzes the secrecy (confidentiality) and authentication property in the cryptographic protocol. Using the Scyther tool can ensure that objectivity of the formal verification of the protocol is performed by means of security analysis and proof.
Scyther description with the proposed e-commerce protocol: This tool uses security protocol description language (SPDL) and a set of roles depending on the protocol designed. Each role represents an e-commerce network entity. We wrote a set of commands to configure our network entities, which are buyer (B), seller (S) and trust authority server (). These commands simulate the procedures of our methodology. Furthermore, in order to communicate between network entities, Scyther provides us with send() and recv() directives. To verify our protocol, this tool enables us to implement a set of claims and to test events to achieve security and authentication properties and to protect data and e-commerce requests. The scyther tool can be utilized to search problems that emerge from the manner the protocol is constructed. The following claims (Alive, Niagree, Nisynch, Secret and Weakagree) are checked for the elements in the exchanged requests. The process of achieving the intended communication with some events is described as “Alive”. “Niagree” stands for non-injective agreement and ensures that a protocol assures a sender B non-injective agreement with a receiver or S on a set of request elements. “Nisynch” stands for non-injective synchronization, which ensures that the intended sender sends all requests received by the receiver in a synchronized manner. “Secret” is used to protect secrecy parameters. “Weakagree” stands for weak agreement and ensures that a protocol guarantees to a sender B weak agreement with another entity or S. If B completes a run of the protocol, apparently with receiver S, then S has previously been running the protocol, apparently with B.
Scyther test results: Here, we describe a test of the proposed e-commerce protocol by the Scyther tool. Figure 10 shows the results of testing our protocol based on the “Alive”, “Niagree”, “Nisynch”, “Secret” and “Weakagree” claim events. The tests show that the public (, and ) and private keys (, and ) and buyer/seller requests (/) are secret. The figure shows that requests are securely exchanged between network entities (B, S and ) without any threats or attacks that compromise network entities, security parameters or e-commerce request data transmitted over the network. This analysis proves that the proposed e-commerce protocol resists the scope of attacks in this research.
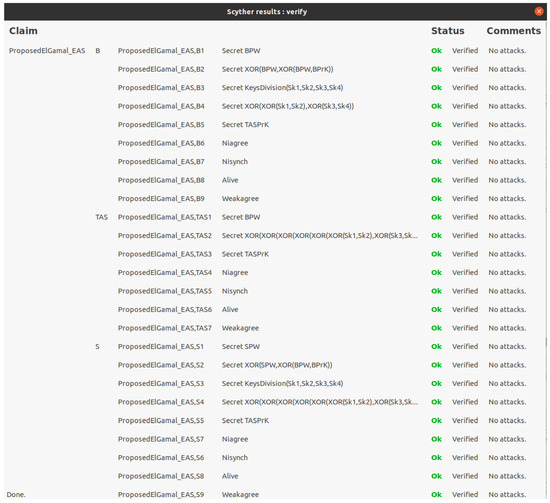
Figure 10.
Scyther security tool test of proposed e-commerce protocol.
5.3. Performance of Proposed E-Commerce Applications
To test the eligibility of the proposed protocol, this section illustrates the performance results of the algorithms and techniques used in our protocol. Our codes were implemented on a laptop with Intel ® Core ™ i5-2540M CPU @ 2.60 GHz, RAM 4 GB, operating system Ubuntu 18.04.6 LTS and OS type 64 bit. In addition, we used Java language to deal with the ElGamal, AES and CRT algorithms. Our protocol relied on ElGamal public and private keys of 1024 bit length, the AES algorithm of 256 bit keys to encrypt e-commerce requests and the CRT approach to generate fast 256 bit private keys.
At first, we implemented the encryption and decryption procedures without e-commerce requests to find the execution/running time one hundred times, as shown in Figure 11. The previous figure shows that the encryption operations in the AES-256 algorithm require more execution time than the decryption operations. Our proposed protocol uses real e-commerce files (see Figure 8) with various sizes such as an invoice file with 1.6 KB, purchasing file with 3.9 KB and selling file with 2.9 KB. Next, we performed AES-256 encryption operations on e-commerce requests (invoice, purchasing and selling) to find the execution time, as shown in Figure 12. From the aforementioned figure, purchasing request encryption requires the most execution time, and the reason for this is that the size of the purchasing files is larger (3.9 KB) than the invoice and selling files. In addition, Figure 13 shows the implementation of AES-256 decryption operations for invoice, purchasing and selling requests, where we note that invoice files require less execution time than the rest of the files because the invoice file size is 1.6 KB, which is the smallest among the rest of the files. Figure 12 and Figure 13 show that the encryption procedures require more execution time than the decryption procedures. Furthermore, Figure 14 shows the execution time of the public and private keys of the ElGamal-1024 algorithm as well as the use of a CRT to generate the private keys. As we can see from the previous figure, the private keys need less execution time than the public keys of the ElGamal algorithm, and the CRT approach generates the private keys faster than the private keys of the ElGamal algorithm. In addition, Table 4 provides an execution time comparison of the private keys for both traditional ElGamal and ElGamal-CRT. We can see from the previous figure that ElGamal-CRT achieves less execution time than traditional ElGamal. Table 5 shows a comparison of memory consumption between public key algorithms such as traditional ElGamal, RSA and ElGamal-CRT. The table shows that the ElGamal-CRT algorithm uses less memory than RSA and traditional ElGamal. Finally, the total running time for encryption with XOR operation and keys division is 0.369143 ms, and the total running time for decryption is 0.274815 ms.
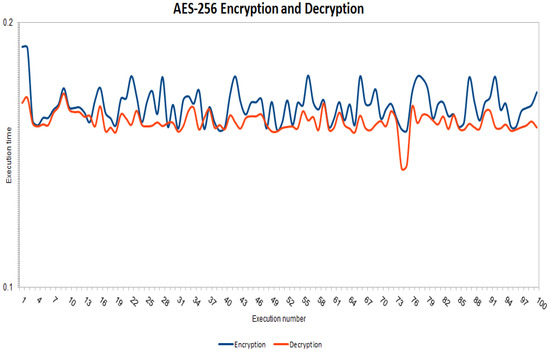
Figure 11.
Running time for AES-256 encryption and decryption.
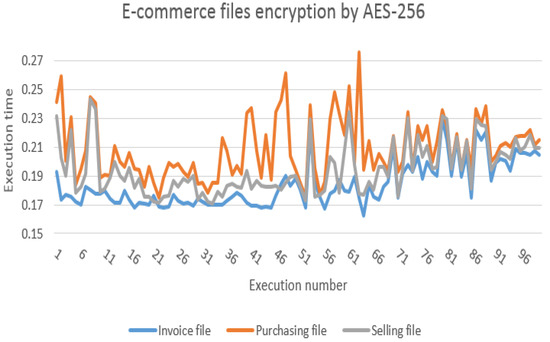
Figure 12.
Running time for AES-256 file encryption (invoice, purchasing and selling).
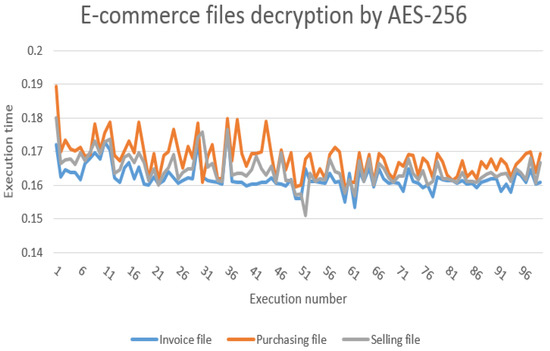
Figure 13.
Running time for AES-256 file decryption (invoice, purchasing and selling).
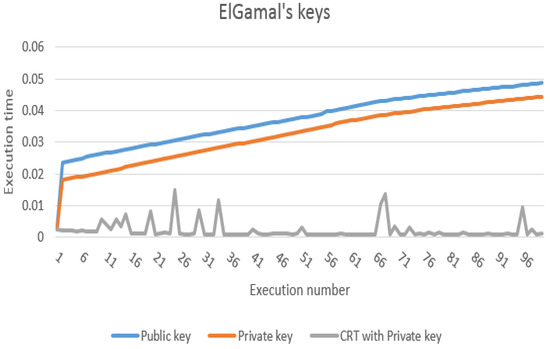
Figure 14.
Running time for ElGamal keys (public, private and CRT with private key).

Table 4.
Key generation comparison of traditional ElGamal and ElGamal-CRT.

Table 5.
Comparison of public key algorithms in terms of memory used.
5.3.1. Theoretical Discussion
E-commerce networks are considered huge networks due to the dependence of buyers and sellers from all over the world on the use of online transactions, which causes major problems in the consumption of hardware/software and network resources such as memory and execution time. Our protocol uses several lightweight methods that make it suitable for e-commerce applications. It relies on relatively small and random keys compared to public key algorithms (see Table 5), which lead to reduced memory usage and consumption, especially in networks that use large organizations and companies. In addition, the AES-256 encryption algorithm is fast when compared to public encryption algorithms such as elliptic curve cryptography (ECC) and RSA. In addition, our protocol relies on the CRT approach to generate small and fast keys, which greatly affects the speed of key generation, encryption and decryption. It changes the public keys every sixteen times depending on the four partitions of size 256. This means that the customer does not need to change the public key every sixteen times, which contributes to performance improvement. It eliminates the expense of generating public keys. Based on the above, the solid methodology used in designing our protocol makes it eligible for application in the e-commerce environment.
For more detail, our protocol is lightweight because, first, it uses hybrid encryption based on ElGamal-AES. It uses AES-256 bit for encryption and decryption. It is common knowledge that symmetric algorithms have high performance compared to asymmetric encryption algorithms because the latter use complex operations and generate very large keys. That is, our protocol encrypts with the AES algorithm and not with asymmetric encryption algorithms, as in some existing research that uses ECC, RSA and ElGamal. Second, symmetric encryption algorithms suffer from a major problem, which is the use of one shared key for all users. Our protocol generates keys using the ElGamal-1024 bit algorithm, taking advantage of CRT technology to speed up the process of generating private keys, and then converting these public keys into a suitable length for the AES algorithm, which is 256 bit using an XOR gate that does not require complex calculations. This means that our protocol uses an asymmetric key exchange in the algorithm and does not use a single key for all users. If one user’s keys are exposed, it will not affect the rest of the users (providing solid security); at the same time, ElGamal’s algorithm generates keys only every 16 times (see Algorithm 1, step 10) based on a permutation of and random addition (providing high performance). This confirms that our protocol balances performance and security.
5.3.2. Results, Comparison and Analysis
In practice, our protocol performs lighter security measures for e-commerce applications than existing protocols. Although the environments, parameters and algorithms used in our protocol are not very identical to existing protocols, we investigated finding some comparable aspects between our protocol and existing protocols. Table 6 provides a comparison of performance parameters (key lengths, encryption algorithm, key generation algorithm, key generation support techniques, and encryption type) between our protocol and existing protocols.

Table 6.
Comparison of performance parameters between our protocol and existing protocols.
Hu et al. [10] relied on RSA to encrypt e-commerce requests. However, we indicated in Table 1 that ElGamal is more efficient than RSA. In addition, our protocol uses ElGamal only for generating public and private keys and not for encryption and decryption procedures. Saha et al. [11] used AES to encrypt the data with the shared key of all users. However, their scheme does not have the flexibility offered in our protocol to generate separate keys for each user. Imran et al. [30] used ElGamal for encryption and decryption in their scheme. This means that encryption of any data request will require a lot of execution time, especially in large networks such as e-commerce. In comparison with our protocol, it only uses ElGamal to generate public and private keys, and the encryption and decryption process is only performed by the AES-256 algorithm, which is fast and efficient. Yousif et al. [13] also used the ElGamal algorithm with a scanning technique to encrypt the data. In terms of performance, their proposal does not concern memory overheads and key sizes since traditional ElGamal uses 1024, 2048 keys, etc. When the number of data encryption requests is large, it will affect the memory size. Fortunately, our protocol generates ElGamal random keys and converts them into small sizes of length 256, which are suitable for encryption in AES and e-commerce environments. Ali et al. [15] utilized several built-in methods such as PBKDF2, RNG and slave key to generate shared keys. However, their protocol is complex and increases implementation running time costs. In addition, the key remains shared between the source and the target, while our protocol uses a CRT-only approach to improve private key generation performance. Although Mohd and Ashawesh [16] indicated that they improved the performance of AES by reducing the number of rounds, the execution time for encryption and decryption is 15 s, which is very large compared to our protocol, as the execution time for encryption is 0.369143 ms, and for decryption, it is 0.274815 ms (taking into account the different environments, such as the different processor speeds).
6. Conclusions
Providing security requirements for electronic commerce transactions, such as buying and selling transactions or payment operations, as well as the customer and server information are sensitive and personal, and this information requires high security. In this study, we designed a protocol that enhances security and that is difficult to penetrate from various attacks as well as that supports high performance. The proposed e-commerce applications have been designed to use asymmetric encryption algorithms such as ElGamal generation random incremental keys and symmetric algorithms such as AES 256 in encryption and decryption operations. After security (attack analysis and Scyther results) and performance (Table 4, Table 5 and Table 6) analyses, we conclude that our protocol provides secure and strong procedures with high performance.
7. Future Works
For future directions, we will improve on server encryption because the server encryption and decryption processes are many times greater than on the buyer’s device. In addition, we plan to use an attack detection method that will help to improve network performance significantly. Furthermore, one of the future contributions that we would like to improve in our protocol is to focus on the merchant’s requests from suppliers and companies, because when the merchant buys a large commodity, it costs him/her a lot of money, as any breach of the merchant’s information in e-commerce will cause a great loss compared to the regular customer, which can even affect the country’s economy. Moreover, we plan to study post-quantum cryptography (PQC) to support the security of our protocol. Finally, to broaden the scope of analysis, we aspire to analyze more attacks such as fault and side-channel attacks on our protocol in addition to the attacks analyzed in this research.
Author Contributions
All authors provided contributions to the work. Conceptualization, G.S.S. and M.A.-Z.; methodology, G.S.S. and M.A.-Z.; software, G.S.S. and M.A.-Z.; validation, G.S.S. and M.A.-Z.; formal analysis, M.A.-Z.; investigation, G.S.S. and M.A.-Z.; writing—original draft preparation, G.S.S. and M.A.-Z.; writing—review and editing, M.A.-Z.; supervision, M.A.-Z.; project administration, M.A.-Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
In this research, the following acronyms are utilized:
| AES | Advanced encryption standard |
| B | Buyer |
| CRT | Chinese remainder theorem |
| E-commerce | Electronic commerce |
| Private key | |
| Public key | |
| RSA | Rivest, Shamir, and Adleman |
| S | Seller |
| Subkeys | |
| TAS | Trust authority server |
References
- Florea, N.; Ionescu, C.; Duică, M.; ăpusneanu, S.; Paschia, L.; Stanescu, S.D.; Coman, M. Trends and perspectives of Romanian e-commerce sector based on mathematical simulation. Electronics 2022, 11, 2295. [Google Scholar] [CrossRef]
- Liu, X.; Ahmad, S.; Anser, M.; Ke, J.; Irshad, M.; Ul-Haq, J.; Abbas, S. Cyber security threats: A never-ending challenge for e-commerce. Front. Psychol. 2022, 13, 4863. [Google Scholar] [CrossRef]
- Cebeci, S.; Nari, K.; Ozdemir, E. Secure e-commerce scheme. IEEE Access 2022, 10, 10359–10370. [Google Scholar] [CrossRef]
- Muhajjar, R.; Flayh, N.; Al-Zubaidie, M. A perfect security key management method for hierarchical wireless sensor networks in medical environments. Electronics 2023, 12, 1011. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. Efficient and secure ECDSA algorithm and its applications: A survey. Int. J. Commun. Netw. Inf. Secur. (IJCNIS) 2019, 11, 7–35. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. RAMHU: A new robust lightweight scheme for mutual users authentication in healthcare applications. Secur. Commun. Netw. 2019, 2019, 3263902. [Google Scholar] [CrossRef]
- Jahnavi, P.; Kumar, B. Survey paper on the various security algorithms used for e-commerce security. EPRA Int. J. Res. Dev. (IJRD) 2021, 6, 39–46. [Google Scholar]
- WEBSCALE. The Global Ecommerce Securityreport 2022. 2022. Available online: https://www.webscale.com/global-ecommerce-security-report-2022/ (accessed on 18 March 2023).
- Imperva. The State of Security within Ecommerce in 2022. 2022. Available online: https://www.imperva.com/resources/reports/The-State-of-Security-Within-eCommerce-in-2022_report.pdf (accessed on 19 March 2023).
- Hu, J.; Hoang, X.; Khalil, I. An embedded DSP hardware encryption module for secure e-commerce transactions. Secur. Commun. Netw. 2011, 4, 902–909. [Google Scholar] [CrossRef]
- Saha, R.; Geetha, G.; Kumar, G.; Kim, T. RK-AES: An improved version of AES using a new key generation process with random keys. Secur. Commun. Netw. 2018, 2018, 9802475. [Google Scholar] [CrossRef]
- Logunleko, K.; Adeniji, O.; Logunleko, A. A comparative study of symmetric cryptography mechanism on DES AES and EB64 for information security. Int. J. Sci. Res. Comput. Sci. Eng. 2020, 8, 45–51. [Google Scholar]
- Yousif, S.; Abboud, A.; Radhi, H. Robust image encryption with scanning technology, the El-Gamal algorithm and chaos theory. IEEE Access 2020, 8, 155184–155209. [Google Scholar] [CrossRef]
- Laz, M.; Grégoire, B.; Rezk, T. Security analysis of ElGamal implementations. In Proceedings of the SECRYPT 2020-17th International Conference on Security and Cryptography, Lieusant, Paris, 8–10 July 2020; pp. 310–321. [Google Scholar]
- Ali, H.; Jawad, T.; Zuhair, H. Data security using random dynamic salting and AES based on master-slave keys for Iraqi dam management system. Indones. J. Electr. Eng. Comput. Sci. 2021, 23, 1018–1029. [Google Scholar] [CrossRef]
- Mohd, N.; Ashawesh, A. Enhanced AES algorithm based on 14 rounds in securing data and minimizing processing time. J. Phys. Conf. Ser. 2021, 1793, 012066. [Google Scholar] [CrossRef]
- Kumar, T.; Reddy, K.; Rinaldi, S.; Parameshachari, B.; Arunachalam, K. A low area high speed FPGA implementation of AES architecture for cryptography application. Electronics 2021, 10, 2023. [Google Scholar] [CrossRef]
- Al-Zubaidie, M. Implication of lightweight and robust hash function to support key exchange in health sensor networks. Symmetry 2023, 15, 152. [Google Scholar] [CrossRef]
- Riadi, A.; Furqan, M.; Kurniawan, R. Document based text data security using the prime generator algorithm fermat’s and the ElGamal algorithm. INFOKUM 2021, 10, 810–817. [Google Scholar]
- Parenreng, J.; Maulida, S.; Wahid, A. The E-mail security system using El-Gamal hybrid algorithm and AES (advanced encryption standard) algorithm. Internet Things Artif. Intell. J. 2022, 2, 1–9. [Google Scholar] [CrossRef]
- Dinata, D.; Mayasari, N.; Hardinata, R. Keeping file authenticity with digital signature technique using a combination of MD5 and ElGamal algorithm. INFOKUM 2022, 10, 350–356. [Google Scholar]
- Anshori, M.; Karya, D.; Gita, M. A study on the reuseIntention of e-commerce platform applications: Security, privacy, perceived value, and trust. J. Manaj. Teor. Dan Ter. J. Theory Appl. Manag. 2022, 15, 13–24. [Google Scholar]
- Chaimaa, B.; Najib, E.; Rachid, H. E-banking overview: Concepts, challenges and solutions. Wirel. Pers. Commun. 2021, 117, 1059–1078. [Google Scholar] [CrossRef]
- Kim, S.-I.; Kim, S.-H. E-commerce payment model using blockchain. J. Ambient. Intell. Humaniz. Comput. 2020, 13, 1673–1685. [Google Scholar] [CrossRef]
- Deng, J.; Lin, J.; Hu, J.; Qian, J. A multi-party secure e-commerce voting scheme based on SDGHV algorithm. J. Phys. Conf. Ser. 2021, 1827, 012195. [Google Scholar] [CrossRef]
- Suharto, S.; Junaedi, I.; Muhdar, H.; Firmansyah, A.; Sarana, S. Consumer loyalty of indonesia e-commerce smes: The role of social media marketing and customer satisfaction. Int. J. Data Netw. Sci. 2022, 6, 383–390. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. PAX: Using pseudonymization and anonymization to protect patients’ identities and data in the healthcare system. Int. J. Environ. Res. Public Health 2019, 16, 1490. [Google Scholar] [CrossRef] [PubMed]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. REISCH: Incorporating lightweight and reliable algorithms into healthcare applications of WSNs. Appl. Sci. 2020, 10, 2007. [Google Scholar] [CrossRef]
- Guruprakash, J.; Koppu, S. EC-ElGamal and genetic algorithm-based enhancement for lightweight scalable blockchain in IoT domain. IEEE Access 2020, 8, 141269–141281. [Google Scholar] [CrossRef]
- Imran, O.; Yousif, S.; Hameed, I.; Abed, W.; Hammid, A. Implementation of El-Gamal algorithm for speech signals encryption and decryption. Procedia Comput. Sci. 2020, 167, 1028–1037. [Google Scholar] [CrossRef]
- Wan, P.; Liao, T.; Yan, J.; Tsai, H. Discrete sliding mode control for chaos synchronization and its application to an improved El-Gamal cryptosystem. Symmetry 2019, 11, 843. [Google Scholar] [CrossRef]
- Zodpe, H.; Sapkal, A. An efficient AES implementation using FPGA with enhanced security features. J. King Saud-Univ.-Eng. Sci. 2020, 32, 115–122. [Google Scholar] [CrossRef]
- Arab, A.; Rostami, M.; Ghavami, B. An image encryption method based on chaos system and AES algorithm. J. Supercomput. 2019, 75, 6663–6682. [Google Scholar] [CrossRef]
- Yang, C.; Chien, Y. FPGA implementation and design of a hybrid chaos-AES color image encryption algorithm. Symmetry 2020, 12, 189. [Google Scholar] [CrossRef]
- Hidayat, A.; Arifudin, R.; Akhlis, I. Implementation of RSA and RSA-CRT algorithms for comparison of encryption and decryption time in android-based instant message applications. J. Adv. Inf. Syst. Technol. 2020, 2, 1–10. [Google Scholar] [CrossRef]
- Selianinau, M. Efficient implementation of Chinese remainder theorem in minimally redundant residue number system. Comput. Sci. 2020, 21. [Google Scholar] [CrossRef]
- Selianinau, M.; Povstenko, Y. An efficient CRT-base power-of-two scaling in minimally redundant residue number system. Entropy 2022, 24, 1824. [Google Scholar] [CrossRef]
- 123FormBuilder. E-Commerce Forms. 2023. Available online: https://www.123formbuilder.com/free-form-templates/gallery-ecommerce/ (accessed on 14 April 2023).
- Fang, W.; Xu, M.; Zhu, C.; Han, W.; Zhang, W.; Rodrigues, J. FETMS: Fast and efficient trust management scheme for information-centric networking in internet of things. IEEE Access 2019, 7, 13476–13485. [Google Scholar] [CrossRef]
- Noor, U.; Anwar, Z.; Altmann, J.; Rashid, Z. Customer-oriented ranking of cyber threat intelligence service providers. Electron. Commer. Res. Appl. 2020, 41, 100976. [Google Scholar] [CrossRef]
- Kumar, V.; Sinha, D. A robust intelligent zero-day cyber-attack detection technique. Complex Intell. Syst. 2021, 7, 2211–2234. [Google Scholar] [CrossRef]
- Mitra, D.; Kulkarni, P.; Pathak, P.; Natrai, N. Importance of coping with cyber security challenges in e commerce business. In Proceedings of the 2022 International Interdisciplinary Humanitarian Conference for Sustainability (IIHC), Bengaluru, India, 18–19 November 2022; pp. 1596–1601. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).