Beneficiary Contracts on a Lightweight Blockchain Architecture Using Smart Contracts: A Smart Healthcare System for Medical Records
Abstract
1. Introduction
1.1. Smart Contracts
1.2. Blockchain in the Health Sector
- We provide a dynamic, distributed access control system for effective, reliable, and authoritative data sharing for users in a healthcare system. The registration contract covers the entire medical system scenario by using smart contracts for user authentication. It comprises three entities: patients, hospitals, and some current regulatory frameworks.
- The consensus protocols allow transactions to be made by utilizing blockchain without an outside party. To avoid congestion and reduce overhead in the blockchain network, we modify the original consensus protocol of the blockchain, namely, proof of work (PoW). We choose to formalize an alternative to using a lightweight PoW algorithm. This algorithm consumes low energy when used in the medical history. The design goal is summarized as compact, fast, and optimized for lightweight applications.
2. Related Works
- This prototype system enables patients to actively communicate their data without relying simply on the data supplied by the healthcare facility where patient-defined permissions are located.
- The location of all the data required to access files is kept outside the blockchain.
- Patient-provided private information that is directly attached to the blockchain.
3. Materials and Methods
- 1.
- Privilege-based access: Information is distributed in a hierarchy according to user privileges. Data users with more privileges have access to more sensitive information than users with lesser privileges.
- 2.
- Data privacy: All parties are entirely safeguarded according to the type of user and the data for which they have privileges. Data users have the right to access the levels their data is located in and any levels below them concerning their own data.
3.1. Proposed Scheme
3.2. Identity Authentication
- 1.
- User-beneficiary node: The primary function of the user is to check the data and request access. They can add authorized information and authorize other people to check their medical information.
- 2.
- User-physician node: The primary function of the physician user is to add, delete, modify, and check data, allowing physicians to add medical records to patients.
- 3.
- User administrator node: Manages accounts, passwords, and permissions of users participating in the network, password recovery, and links public and private keys.
3.3. Architecture of the System
3.3.1. Levels of Privacy of Medical Records
- The citizen registry is only visible to governmental institutions, according to regulations.
- Medical records are only visible to administrative staff.
- Medical records are only visible to administrative and health personnel.
- Medical records are only visible to administrative staff, healthcare personnel, and patients or family members.
3.3.2. System Components
- 1.
- Patients/rightsholders: Patients who received treatment or required it out of necessity from a medical institution.
- 2.
- Health personnel: Access to the previous medical records of a visiting patient is necessary for the medical staff to provide better care. Each employee has a set of qualities (A) that can be used to divide them into categories of comparable traits and order them in a hierarchy.
- 3.
- Administrator.
- 4.
- A governmental body, public or private institution.
- 5.
- Family members (entitled).
3.3.3. Functions of Each Entity
- Access instance, government, public or private institution: Health service providers and managers within the Mexican data protection laws covering all medical record data.
- Patient: The patient visited the hospital for a medical check-up. He is a data user.
- Physician: The physician is responsible for generating the patients’ medical records and extracting keywords for integration into the file. In this scheme, the physician is assumed to be honest and not transacting for illegal gain.
- Data user: The data user will use the information, for example, internal departments of the institution or patients’ families who can obtain the relevant records as long as their attributes comply with the corresponding access policy.
- Blockchain mechanism: The blockchain mechanism is the backbone of the architecture and performs operations based on smart contracts.
3.3.4. System Modeling
- is the hash function, which is a deterministic function that transforms data of arbitrary size into fixed sizes.
- is the last accepted block in the blockchain.
- t is the transaction time; obtains the current time of the transaction.
- Merkle root of the transactions of the block to be mined.
- nonce is a scalar, meaning “number used only once”, which solves the proof-of-work.
- number expressing the degree of difficulty of the algorithm.
3.3.5. Smart Contracts
3.3.6. Requirements for Smart Contracts
- Requirement 1: Registration capabilities in compliance with current regulations.
- Requirement 2: Patients must have access to their registers.
- Requirement 3: Dependents must be able to request access to patients’ records.
- Requirement 4: Records must be able to be uploaded based on access for healthcare providers.
- Requirement 5: Records must be accessible to providers and patients for download based on the access.
- Requirement 6: Each record that is uploaded must be encrypted.
3.4. Implementation
Smart Contract Design
| Algorithm 1: Hospital node incorporation |
| Input: Hospital ID, city, name Output: Hospital node 1 if msg.sender == Health Sector ADMIN then//Health Sector Gov. Admin. 2 if a hospital address node exists in hospital mapping then 3 Abort function and output Error 4 else 5 create a hospital node with input data 6 add the public key to hospital mapping 7 else 8 Abort function and output Error |
| Algorithm 2: Medical node incorporation |
| Input: Public key, specialty Output: Medical node 1 if msg.sender == hospital ADMIN then 2 if a medical node address exists in medical mapping then 3 Abort function and output Error 4 else 5 create a medical node with input data 6 add the public key to medical mapping 7 else 8 Abort function and output Error |
| Algorithm 3: Patient node incorporation |
| Input: Public key, gender Output: Patient node 1 if msg.sender == hospital ADMIN then 2 if the patient node address exists in patient mapping then 3 Abort function and output Error 4 else 5 create a patient node with input data 6 add the public key to patient mapping 7 else 8 Abort function and output Error |
| Algorithm 4: Assign physician to patient node |
| Input: Public key medical Output: Physician assigned to a patient 1 if msg.sender == hospital ADMIN then 2 if a Public key exists in patient attention list mapping then 3 Abort function and output Error 4 else 5 add the public key to the patient attention list mapping 6 else 7 Abort function and output Error |
| Algorithm 5: Integrate medical records to file |
| Input: Public key patient Output: Integrating register 1 if msg.sender == doctor then 2 if Public key does not exist in patient attention list mapping then 3 Abort function and output Error 4 else 5 6 7 8 else 9 Abort function and output Error |
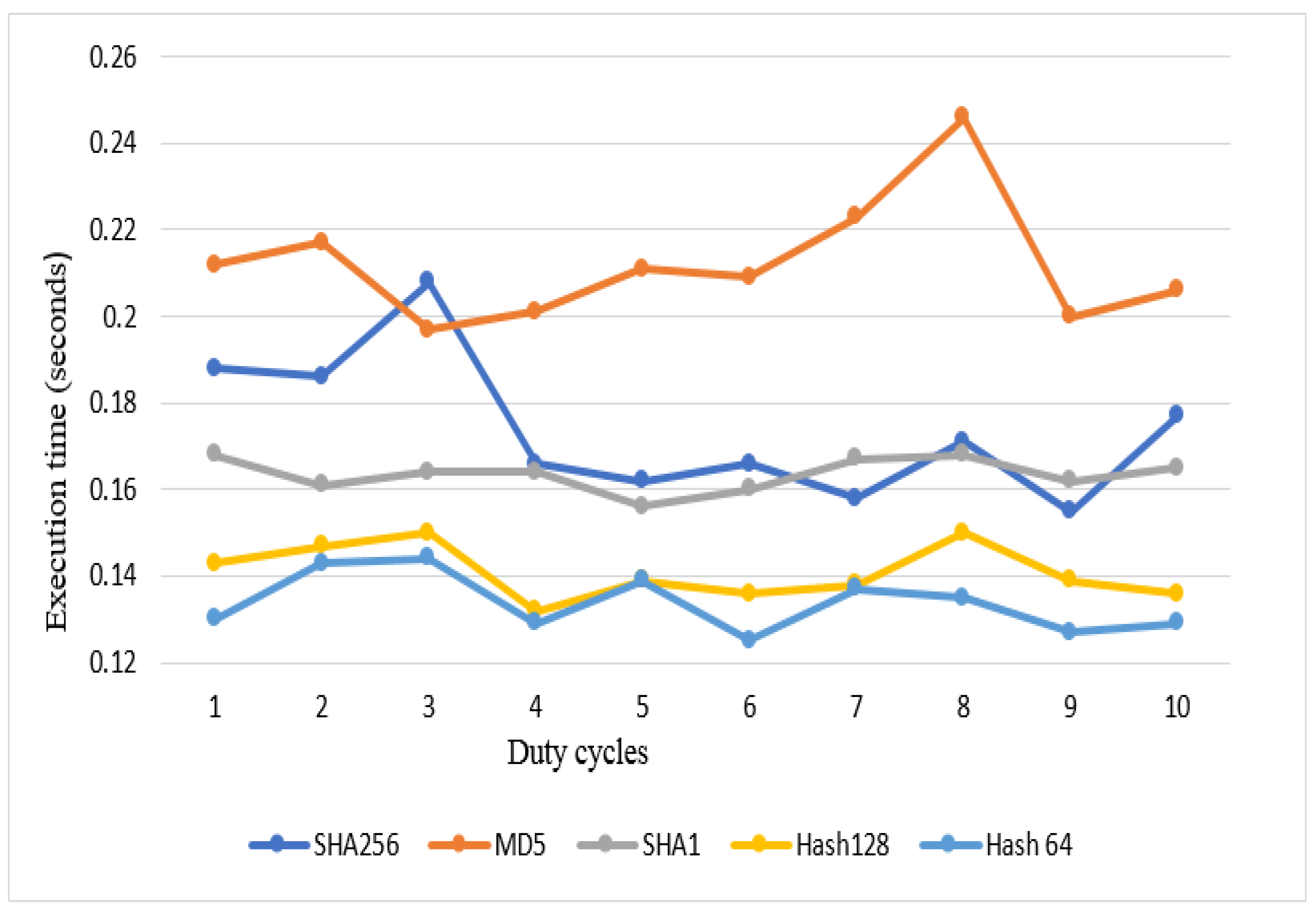
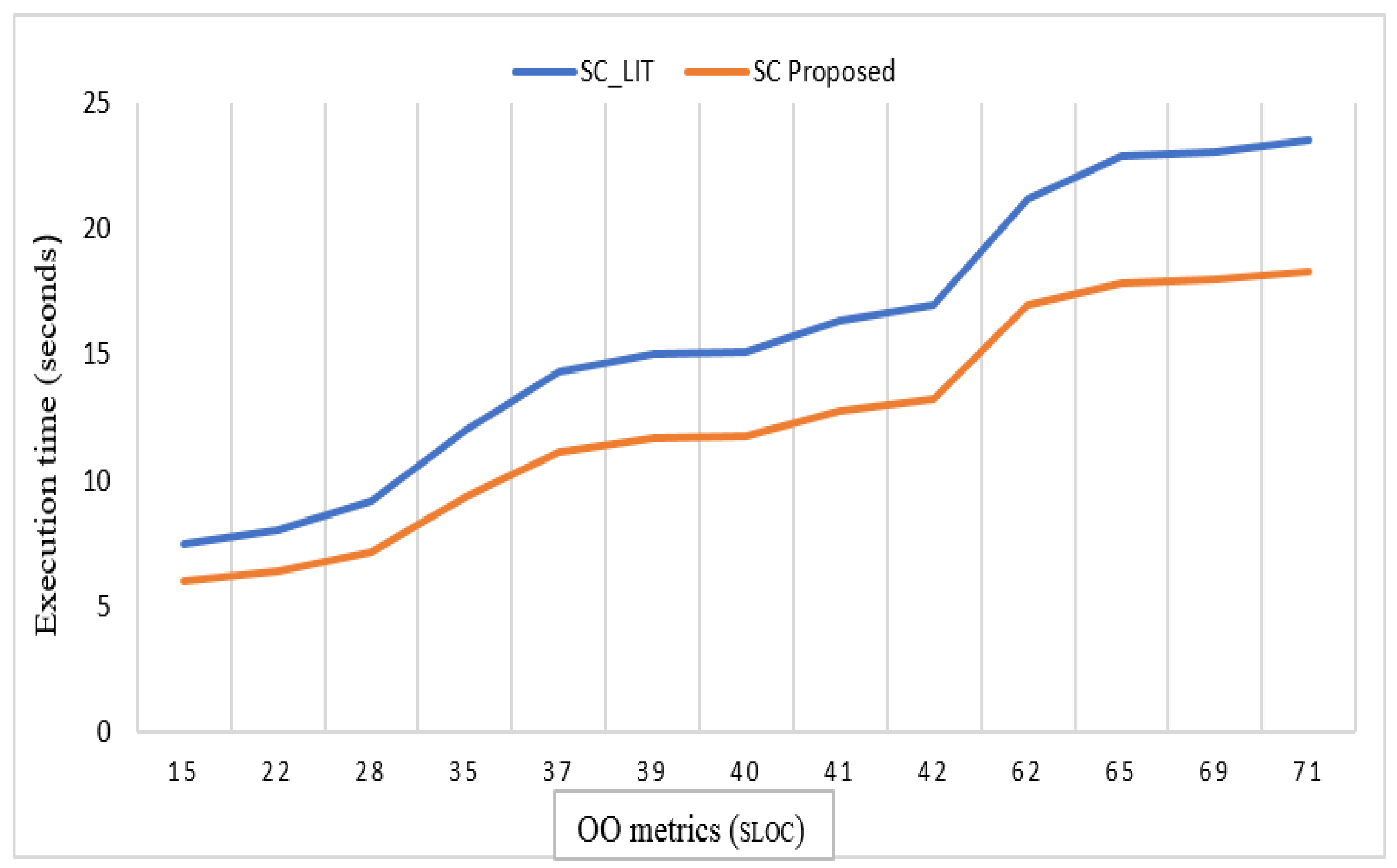
4. Results
- SLOC: source lines of code;
- LLOC: logical lines of code;
- CLOC: comment-only lines of code;
- NF: number of functions;
- McCC: McCabe’s cyclomatic complexity of the functions.
5. Discussion and Conclusions
- 1.
- Privacy of information: Given the nature of the type of data—personal, diagnostic, and treatment—the actors will have the protection of the right to privacy regarding the records as well as the operations carried out on them and on the entities that execute them.
- 2.
- Immutability: Given that each block contains a previous block hash, any change in a medical record will result in different data in the block identification. In this way, a modification is identified, which avoids the alteration of the data.
- 3.
- Identity of the actors: Access to data must be performed only by authorized entities, and the system must be able to manage the different operations according to the type of user or node.
- 4.
- Data traceability: Data access must always be recorded. Writing, reading, and modifying data should be accessible to authorized actors on the blockchain without restrictions.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Georgiev, S.; Priftis, S.; Grigorov, E. Blockchain in the Logistics of Health Technologies. In Proceedings of the Information Systems and Grid Technologies, Online, 28–29 May 2021; pp. 189–202. [Google Scholar]
- Haddad, A.; Habaebi, M.H.; Suliman, F.E.M.; Elsheikh, E.A.; Islam, M.R.; Zabidi, S.A. Generic Patient-Centered Blockchain-Based EHR Management System. Appl. Sci. 2023, 13, 1761. [Google Scholar] [CrossRef]
- Kelly, B.; Quinn, C.; Lawlor, A.; Killeen, R.; Burrell, J. Cybersecurity in Healthcare. In Trends of Artificial Intelligence and Big Data for E-Health; Springer: Berlin/Heidelberg, Germany, 2023; pp. 213–231. [Google Scholar]
- Thakur, A. Market Determinants Impacting Distributed Ledger Technology, and AI-Based Architectures in the Healthcare Industry. Int. J. Bus. Anal. Intell. 2022, 10, 10. [Google Scholar]
- Lehto, M. Cyber-attacks against critical infrastructure. In Cyber Security: Critical Infrastructure Protection; Springer: Berlin/Heidelberg, Germany, 2022; pp. 3–42. [Google Scholar]
- Haque, A.B.; Muniat, A.; Ullah, P.R.; Mushsharat, S. An automated approach towards smart healthcare with blockchain and smart contracts. In Proceedings of the 2021 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 19–20 February 2021; pp. 250–255. [Google Scholar]
- Abutaleb, R.A.; Alqahtany, S.S.; Syed, T.A. Integrity and Privacy-Aware, Patient-Centric Health Record Access Control Framework Using a Blockchain. Appl. Sci. 2023, 13, 1028. [Google Scholar] [CrossRef]
- Amir Latif, R.M.; Hussain, K.; Jhanjhi, N.Z.; Nayyar, A.; Rizwan, O. A remix IDE: Smart contract-based framework for the healthcare sector by using Blockchain technology. Multimed. Tools Appl. 2020, 1–24. [Google Scholar] [CrossRef]
- Zaghloul, E.; Li, T.; Ren, J. Security and privacy of electronic health records: Decentralized and hierarchical data sharing using smart contracts. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 375–379. [Google Scholar]
- Szabo, N. Formalizing and Securing Relationships on Public Networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Morabito, V. Business Innovation through Blockchain; Springer: Berlin/Heidelberg, Germany, 2017; Volume 2021, pp. 1–188. [Google Scholar]
- Swan, M. Blockchain thinking: The brain as a decentralized autonomous corporation [commentary]. IEEE Technol. Soc. Mag. 2015, 34, 41–52. [Google Scholar] [CrossRef]
- Kormiltsyn, A.; Udokwu, C.; Karu, K.; Thangalimodzi, K.; Norta, A. Improving healthcare processes with smart contracts. In Proceedings of the International Conference on Business Information Systems, Seville, Spain, 26–28 June 2019; pp. 500–513. [Google Scholar]
- Hathaliya, J.J.; Tanwar, S. An exhaustive survey on security and privacy issues in Healthcare 4.0. Comput. Commun. 2020, 153, 311–335. [Google Scholar] [CrossRef]
- Gordon, W.J.; Catalini, C. Blockchain technology for healthcare: Facilitating the transition to patient-driven interoperability. Comput. Struct. Biotechnol. J. 2018, 16, 224–230. [Google Scholar] [CrossRef]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on E-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–17 September 2016; pp. 1–3. [Google Scholar]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar]
- Peterson, K.; Deeduvanu, R.; Kanjamala, P.; Boles, K. A blockchain-based approach to health information exchange networks. In Proceedings of the NIST Workshop Blockchain Healthcare, Gaithersburg, MD, USA, 26–27 September 2016; pp. 1–10. [Google Scholar]
- Rotbi, M.F.; Motahhir, S.; Ghzizal, A.E. Blockchain technology for a safe and transparent covid-19 vaccination. arXiv 2021, arXiv:2104.05428. [Google Scholar] [CrossRef]
- Pham, H.L.; Tran, T.H.; Nakashima, Y. A secure remote healthcare system for hospital using blockchain smart contract. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M.; Wang, F. Secure and trustable electronic medical records sharing using blockchain. In Proceedings of the AMIA Annual Symposium Proceedings, Washington, DC, USA, 6–8 November 2017; p. 650. [Google Scholar]
- Khatoon, A.J. A blockchain-based smart contract system for healthcare management. Electronics 2020, 9, 94. [Google Scholar] [CrossRef]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-less medical data sharing among cloud service providers via blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Ahram, T.; Sargolzaei, A.; Sargolzaei, S.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the 2017 IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar]
- Saravanan, M.; Shubha, R.; Marks, A.M.; Iyer, V. SMEAD: A secured mobile enabled assisting device for diabetics monitoring. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Odisha, India, 17–20 December 2017; pp. 1–6. [Google Scholar]
- Benchoufi, M.; Ravaud, P. Blockchain technology for improving clinical research quality. Trials 2017, 18, 335. [Google Scholar] [CrossRef] [PubMed]
- Nugent, T.; Upton, D.; Cimpoesu, M. Improving data transparency in clinical trials using blockchain smart contracts. F1000Research 2016, 5, 2541. [Google Scholar] [CrossRef]
- McFarlane, C.; Beer, M.; Brown, J.; Prendergast, N. Patientory: A Healthcare Peer-to-Peer Emr Storage Network v1; Entrust Inc.: Addison, TX, USA, 2017; Volume 3, p. 19. [Google Scholar]
- Coperneec. “How to represent a blockchain through a mathematical model?”. Available online: https://canopee-group.com/wp-content/uploads/2020/05/ (accessed on 26 April 2023).
- Lande, S.; Zunino, R. SoK: Unraveling Bitcoin smart contracts. In Principles of Security and Trust LNCS; Springer: Berlin/Heidelberg, Germany, 2018; Volume 10804, p. 217. [Google Scholar] [CrossRef]
- Shahnaz, A.; Qamar, U.; Khalid, A. Using blockchain for electronic health records. IEEE Access 2019, 7, 147782–147795. [Google Scholar] [CrossRef]
- Mercenne, L.; Brousmiche, K.-L.; Hamida, E.B. Blockchain studio: A role-based business workflows management system. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 1215–1220. [Google Scholar]
- Bhavin, M.; Tanwar, S.; Sharma, N.; Tyagi, S.; Kumar, N. Blockchain and quantum blind signature-based hybrid scheme for healthcare 5.0 applications. J. Inf. Secur. Appl. 2021, 56, 102673. [Google Scholar] [CrossRef]
- Alexaki, S.; Alexandris, G.; Katos, V.; Petroulakis, N.E. Blockchain-based electronic patient records for regulated circular healthcare jurisdictions. In Proceedings of the 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona, Spain, 17–19 September 2018; pp. 1–6. [Google Scholar]
- Liu, P.T.S. Medical record system using blockchain, big data and tokenization. In Proceedings of the Information and Communications Security: 18th International Conference, ICICS 2016, Singapore, 29 November–2 December 2016; pp. 254–261. [Google Scholar]
- Tith, D.; Lee, J.S.; Suzuki, H.; Wijesundara, W.M.A.B.; Taira, N.; Obi, T.; Ohyama, N. Patient consent management by a purpose-based consent model for electronic health record based on blockchain technology. Healthc. Inform. Res. 2020, 26, 265–273. [Google Scholar] [CrossRef]
- Sharma, R.; Kumar, A. Electronic Health Records Using Blockchain. Available online: www.ir.juit.ac.in (accessed on 15 November 2022).
- Alharby, M.; van Moorsel, A. Blocksim: An extensible simulation tool for blockchain systems. Front. Blockchain 2020, 3, 28. [Google Scholar] [CrossRef]
- Banks, J. Discrete Event System Simulation, 4th ed.; Pearson Education India: Delhi, India, 2005. [Google Scholar]
- Wang, Q.; Qin, S. A Hyperledger Fabric-Based System Framework for Healthcare Data Management. Appl. Sci. 2021, 11, 11693. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart contract-based access control for the internet of things. IEEE Internet Things J. 2018, 6, 1594–1605. [Google Scholar] [CrossRef]
- Jiang, Y.; Wang, C.; Wang, Y.; Gao, L. A cross-chain solution to integrating multiple blockchains for IoT data management. Sensors 2019, 19, 2042. [Google Scholar] [CrossRef]
- Ma, M.; Shi, G.; Li, F. Privacy-oriented blockchain-based distributed key management architecture for hierarchical access control in the IoT scenario. IEEE Access 2019, 7, 34045–34059. [Google Scholar] [CrossRef]
- Liu, C.H.; Lin, Q.; Wen, S. Blockchain-enabled data collection and sharing for industrial IoT with deep reinforcement learning. IEEE Trans. Ind. Inform. 2018, 15, 3516–3526. [Google Scholar] [CrossRef]
- Omar, I.A.; Jayaraman, R.; Debe, M.S.; Salah, K.; Yaqoob, I.; Omar, M. Automating procurement contracts in the healthcare supply chain using blockchain smart contracts. IEEE Access 2021, 9, 37397–37409. [Google Scholar] [CrossRef]
- Yadav, A.K.; Bajpai, R.K. KYC optimization using blockchain smart contract technology. Int. J. Innov. Res. Appl. Sci. Eng. 2020, 4, 669–674. [Google Scholar] [CrossRef]
- Zhang, G.; Li, T.; Li, Y.; Hui, P.; Jin, D. Blockchain-based data sharing system for ai-powered network operations. J. Commun. Inf. Netw. 2018, 3, 1–8. [Google Scholar] [CrossRef]
- Valeriano Ortiz, O. Development of a Web System for Records Management in ICB’s Nutrition Clinic in Compliance with Federal Regulation NOM-024-SSA3-2010. Available online: http://hdl.handle.net/20.500.11961/2911 (accessed on 5 November 2022).
- Gupta, R.; Shukla, A.; Tanwar, S. Aayush: A smart contract-based telesurgery system for healthcare 4.0. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Virtual, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Musamih, A.; Salah, K.; Jayaraman, R.; Arshad, J.; Debe, M.; Al-Hammadi, Y.; Ellahham, S. A blockchain-based approach for drug traceability in healthcare supply chain. IEEE Access 2021, 9, 9728–9743. [Google Scholar] [CrossRef]
- Hegedűs, P. Towards analyzing the complexity landscape of solidity based ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May 2018; pp. 35–39. [Google Scholar]
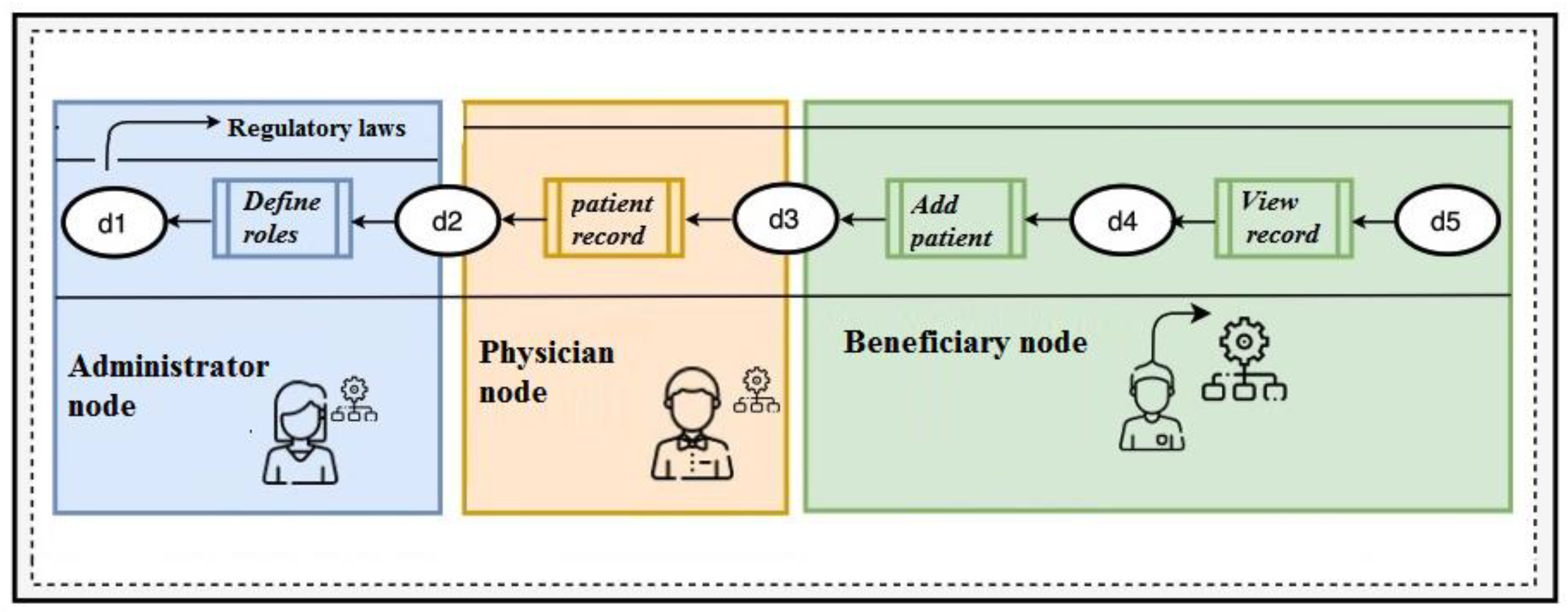
| Author | Function | Dimension | User |
|---|---|---|---|
| [33,34] | Define roles | Define roles | Administrator |
| [17,35] | Add patient record | Add medical records | Physician |
| [34,36] | View patient record | View medical records | Administrator, physician, and patient |
| [37,38] | Update patient record | Update medical records | Physician |
| [34,38] | Delete patient record | Delete medical records | Physician |
| Model | Target | Tools for Development | Platform | Environments of Simulation |
|---|---|---|---|---|
| Access administration system [42] | IoT access control | Remix IDE | Ethereum, raspberry | Javascript |
| System for controlling access [43] | Cross-chain-based access control in the IoT | - | IOTA and Tangle | Ubuntu 16.04 |
| Access administration system [44] | Access control with IoT-related key management | - | Multiple public blockchains | OMNeT++ 5.4.1 |
| Safeguard data exchange [45] | Deep learning is used to share data | Go | Ethereum | Python |
| Secure data exchanges | Data sharing with A.I. | - | Hyperledger fabric | - |
| The proposed model includes access control, record sharing, and management | Access control, data exchange, and management. | Remix IDE, Solidity | Hyperledger, separate modules | Remix IDE, python, JavaScript |
| Systems | Reliability | Authorization | Authentication | Validation | Decentralized | Regulations |
|---|---|---|---|---|---|---|
| Access administration system [42] | Yes | No | No | Yes | Yes | No |
| Access administration system [43] | No | No | No | No | Yes | No |
| Access administration system [44] | No | Yes | No | No | Yes | Yes |
| Data sharing system [45] | No | No | Yes | Yes | Yes | Yes |
| Data sharing system [48] | Yes | No | No | No | Yes | No |
| Proposed data sharing and access control system | Yes | Yes | Yes | Yes | Yes | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mendoza Arvizo, A.I.; Avelar Sosa, L.; García Alcaraz, J.L.; Cruz-Mejía, O. Beneficiary Contracts on a Lightweight Blockchain Architecture Using Smart Contracts: A Smart Healthcare System for Medical Records. Appl. Sci. 2023, 13, 6694. https://doi.org/10.3390/app13116694
Mendoza Arvizo AI, Avelar Sosa L, García Alcaraz JL, Cruz-Mejía O. Beneficiary Contracts on a Lightweight Blockchain Architecture Using Smart Contracts: A Smart Healthcare System for Medical Records. Applied Sciences. 2023; 13(11):6694. https://doi.org/10.3390/app13116694
Chicago/Turabian StyleMendoza Arvizo, Arturo I., Liliana Avelar Sosa, Jorge Luis García Alcaraz, and Oliverio Cruz-Mejía. 2023. "Beneficiary Contracts on a Lightweight Blockchain Architecture Using Smart Contracts: A Smart Healthcare System for Medical Records" Applied Sciences 13, no. 11: 6694. https://doi.org/10.3390/app13116694
APA StyleMendoza Arvizo, A. I., Avelar Sosa, L., García Alcaraz, J. L., & Cruz-Mejía, O. (2023). Beneficiary Contracts on a Lightweight Blockchain Architecture Using Smart Contracts: A Smart Healthcare System for Medical Records. Applied Sciences, 13(11), 6694. https://doi.org/10.3390/app13116694







