Efficient Dissemination of Safety Messages in Vehicle Ad Hoc Network Environments
Abstract
1. Introduction
2. Related Work
3. The Proposed Safety Message Dissemination Scheme
3.1. Overall Structure
3.2. Cluster Management
3.2.1. Cluster Subscription
| Algorithm 1. Cluster subscription algorithm. | |
| Cluster subscription algorithm | |
| Notation: | |
| 01: | Vi = Vehicle i |
| 02: | IN = Inferior Node |
| 03: | BSM: Basic information message of vehicle |
| 04: | t: Set amount of time to wait for a vehicle with a score higher than oneself |
| 05: | f: Cluster search state (0: cluster search ended, 1: cluster search) |
| 06: | CH = Cluster head |
| 07: | Input: BSM, t |
| 08: | Output: Cluster subscription |
| 09: | if Vi == IN: |
| 10: | Broadcast(BSM) |
| 11: | t.start() // timer start |
| 12: | f = 1 // cluster search |
| 13: | While t > 0: |
| 14: | if cluster invitation message received: |
| 15: | send cluster invitation confirmation message to CH |
| 16: | if cluster subscription completion message received: |
| 17: | f = 0 |
| 18: | Vi = CM // cluster subscription completed |
| 19: | return |
| 20: | if f == 1: // timer ends and cluster subscription fails |
| 21: | declare oneself as CH |
| 22: | send cluster invitation message |
| 23: | if Vi == CH: |
| 24: | if CH received cluster invitation confirmation message: |
| 25: | if direction, location, and speed are the same as IN: |
| 26: | send cluster subscription completion message to IN |
| 27: | else: |
| 28: | Ignore |
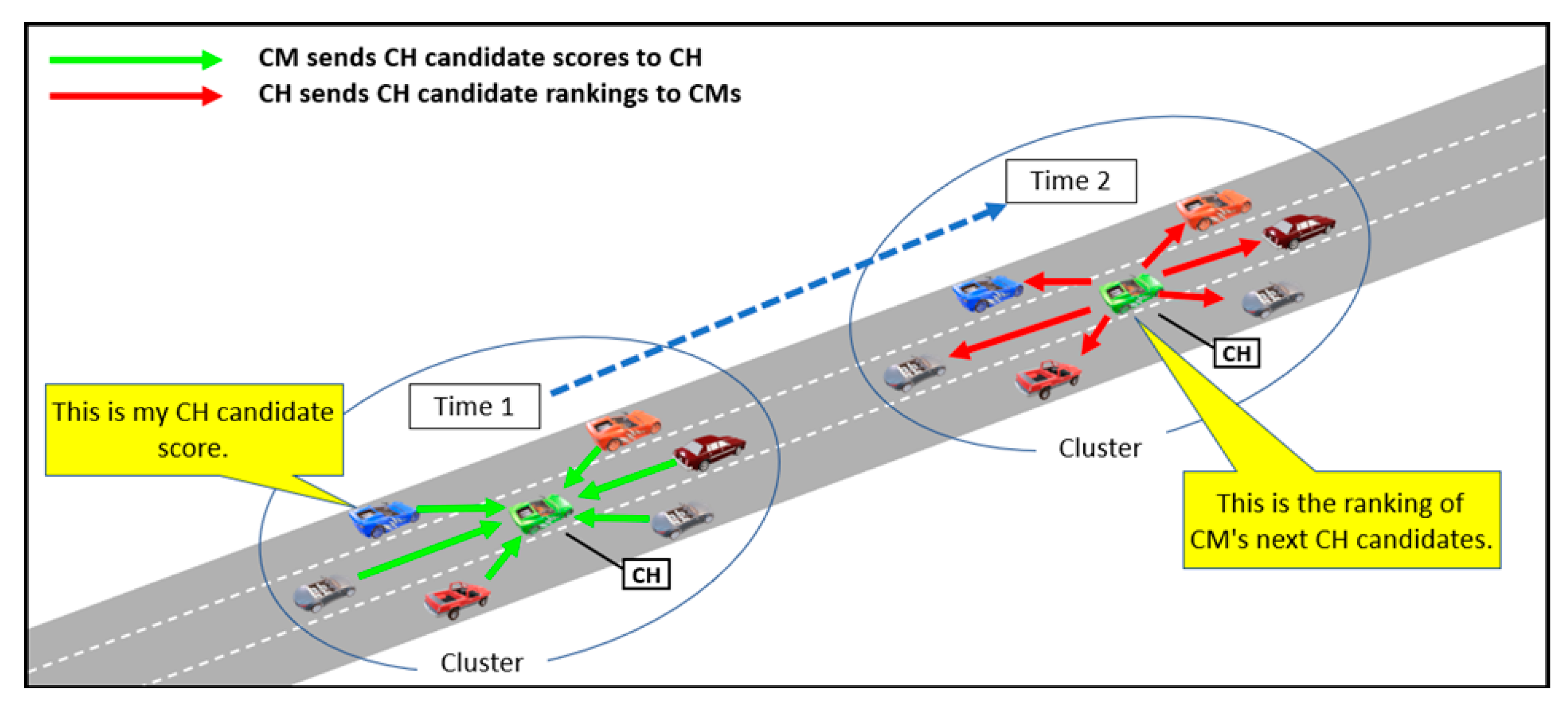
3.2.2. Cluster Head Candidates
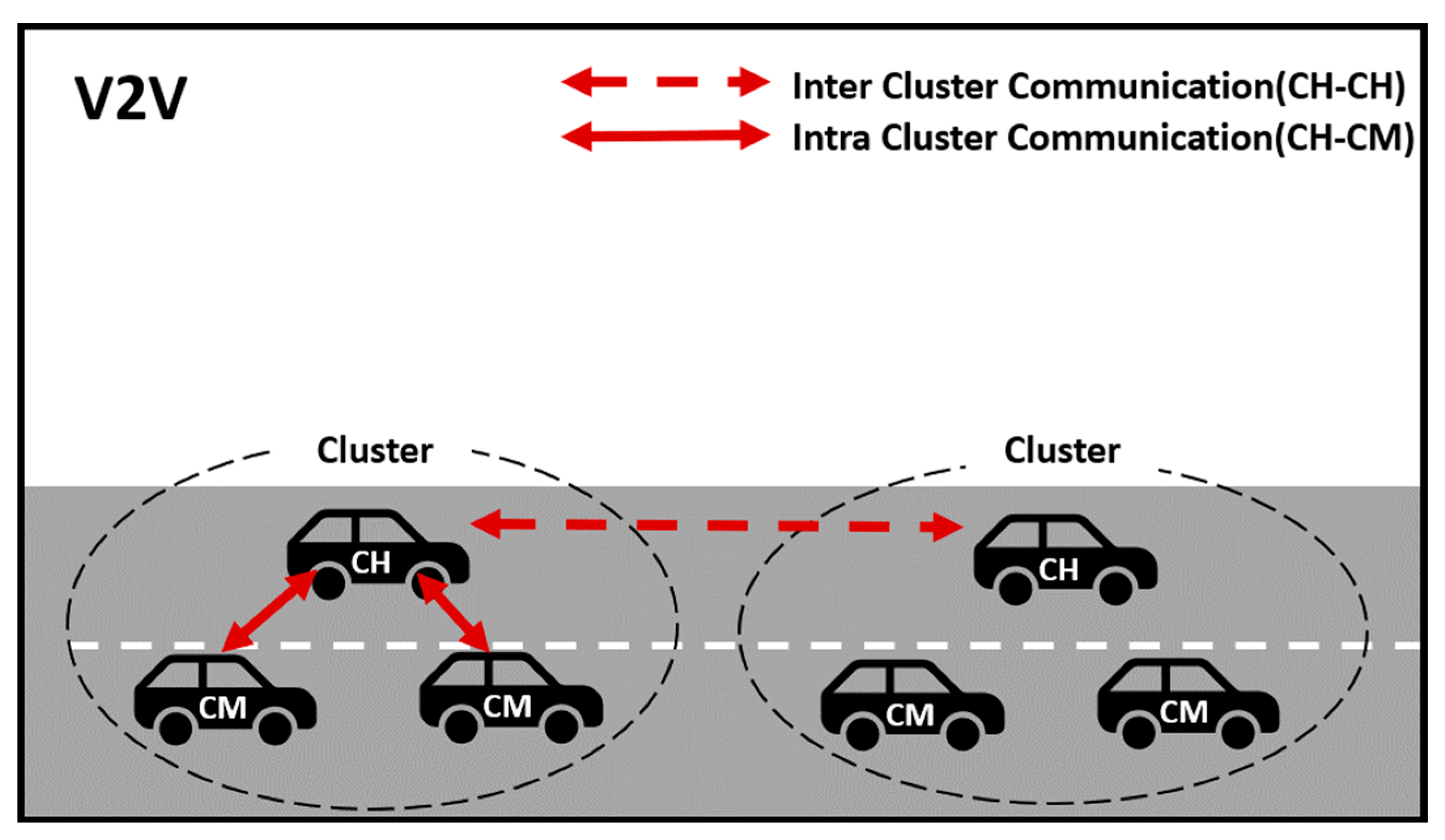
3.3. V2V Communication
3.3.1. Intracluster Communication
| Algorithm 2. Intracluster communication algorithm. | |
| Intracluster communication algorithm | |
| Notation: | |
| 01: | N: Current vehicle |
| 02: | M: Message |
| 03: | EM: Emergency safety message |
| 04: | SM: General safety message |
| 05: | RM: Request message for general safety message |
| 06: | Input: N, M |
| 07: | Output: message dissemination and transmission |
| 08: | M receipt // message receipt |
| 09: | if M == EM and EM == new EM: |
| 10: | if N == CH: |
| 11: | disseminate emergency safety message to one’s own CMs |
| 12: | call intercluster communication algorithm // disseminate EM to nearby CHs |
| 13: | elsif N == CM: |
| 14: | disseminate EM to one’s own CH |
| 15: | elsif N == IN: |
| 16: | broadcast emergency safety message |
| 17: | |
| 18: | if M == SM and SM == new SM: |
| 19: | if needed by oneself: |
| 20: | store |
| 21: | if N == CH: |
| 22: | update messages held in cluster |
| 23: | elsif N == CM: |
| 24: | send CH an updated list of held messages |
| 25: | else: |
| 26: | ignore |
| 27: | |
| 28: | if M == RM: |
| 29: | if N == CH: |
| 30: | if oneself has a safety message of RM: |
| 31: | send SM (RM == SM) to the CM that sent the RM |
| 32: | elsif a CM in the cluster has safety message of RM: |
| 33: | SM transmission request to CM with safety message of RM |
| 34: | else: // when there is no safety message of RM in the cluster |
| 35: | call intercluster communication algorithm |
| 36: | |
| 37: | elsif N == CM and CM receives SM transmission request from CH: |
| 38: | send SM (RM == SM) to CM or CH that made the request |
| 39: | |
| 40: | else: |
| 41: | ignore |
3.3.2. Intercluster Communication
| Algorithm 3. Intercluster communication algorithm. | |
| Intercluster communication algorithm | |
| Notation: | |
| 01: | CRD: Cluster request message table |
| 02: | CRD_total: Total messages of CRD |
| 03: | CRD_i: Cluster request message i |
| 04: | EM: Emergency safety message |
| 05: | lifetime = Survival time that must be guaranteed for EM |
| 06: | RM: Request message for general safety message |
| 07: | N: Current vehicle |
| 08: | Input: RM, EM |
| 09: | Output: CRD message request |
| 10: | def To_Other_Cluster(CRD): |
| 11: | if len(CRD) != 0: |
| 12: | send all messages of the CRD to other nearby clusters |
| 13: | if the CM that requested CRD_i departed from the cluster or received CRD_i: |
| 14: | CRD_total—CRD_i |
| 15: | if CRD_i within CRD is received from another nearby cluster: |
| 16: | CRD_total—CRD_i |
| 17: | send CRD_i to the CM that made the request |
| 18: | |
| 19: | while N == CH and if not departed from cluster: |
| 20: | if holds EM and the EM’s lifetime != 0: |
| 21: | disseminate emergency safety message // disseminate emergency safety message to nearby CHs |
| 22: | if there is no safety message of RM in the cluster: |
| 23: | insert RM in CRD |
| 24: | To_Other_Cluster(CRD) |
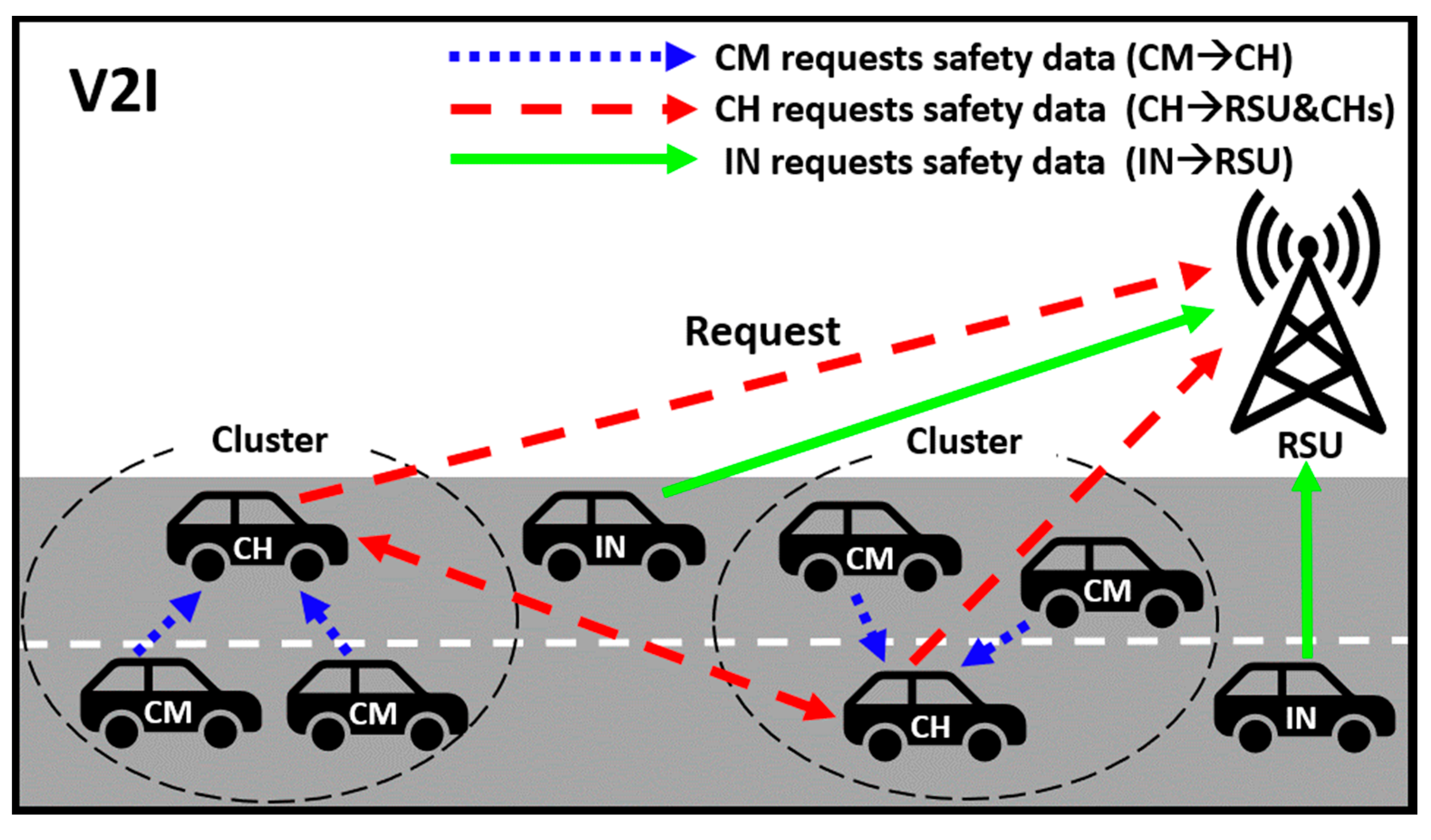
3.4. V2I Communication
3.4.1. Cluster-Based V2I Communication
| Algorithm 4. Cluster-based V2I communication algorithm. | |
| Cluster-based V2I communication algorithm | |
| Notation: | |
| 01: | CRD: Cluster request message table |
| 02: | CRD_i: Cluster request message i |
| 03: | EM: Emergency safety message |
| 04: | RM: Request message for required general safety message |
| 05: | N: Current vehicle |
| 06: | Input: RM, EM |
| 07: | Output: CRD message request |
| 08: | def In_RSU(CRD): |
| 09: | send CRD to RSU and nearby CHs |
| 10: | if CRD_i within CRD is received from RSU: |
| 11: | CRD_total—CRD_i |
| 12: | |
| 13: | while if within the RSU’s communication range: |
| 14: | if N != CM: |
| 15: | if holding the EM: |
| 16: | send emergency safety message to the RSU |
| 17: | if there is a required general safety message: |
| 18: | if N == IN: |
| 19: | send RM to RSU |
| 20: | if N == CM: |
| 21: | send RM to CH |
| 22: | if N == CH: |
| 23: | if there is no message of RM in the cluster: |
| 24: | call intracluster communication algorithm |
| 25: | else: // if there is no requested message in the cluster |
| 26: | insert RM in CRD |
| 27: | if len(CRD) != 0: |
| 28: | In_RSU(CRD) |
| 29: | if the vehicle that requested CRD_i has departed: |
| 30: | CRD_total—CRD_i |
| 31: | |
| 32: | if outside the RSU’s communication range: |
| 33: | call intracluster communication algorithm |
3.4.2. RSU Scheduling
| Algorithm 5. RSU scheduling algorithm (with broadcast). | |
| RSU scheduling algorithm (with broadcast) | |
| Notation: | |
| 01: | lifetime = Survival time that must be guaranteed for EM |
| 02: | BCT = Broadcast candidate table |
| 03: | BCTscore(D(a)) = BCT priority score for a message |
| 04: | Input: cluster information and requests, sorted_BCTscore_list |
| 05: | Output: broadcast |
| 06: | def FT_update(cluster information and requests, BCT): // update formula table |
| 07: | calculate holding rate |
| 08: | calculate request rate |
| 09: | return HR(D(a)), RR(D(a)) |
| 10: | |
| 11: | def BCT_update(HR(D(a)), RR(D(a))): //update BCT |
| 12: | BCTscore(D(a)) = HR(D(a) + RR(D(a)) //priority score |
| 13: | BCTscore_list = BCT[BCTscore(D(a)), .... BCTscore(D(c))] |
| 14: | sorted_BCTscore_list = BCTscore_list.sort(reverse = True) // sort priority scores in descending order |
| 15: | return sorted_BCTscore_list |
| 16: | |
| 17: | def RSU_Broadcast(cluster information and requests, sorted_BCTscore_list): |
| 18: | if a new message is received: |
| 19: | BCT management // insert new messages, delete low-importance messages |
| 20: | FT_update(cluster information and requests) |
| 21: | BCT_update(HR(D(a)), RR(D(a))) |
| 22: | if there is a safety message to request to vehicle: |
| 23: | add safety message request |
| 24: | // send priority messages corresponding to the packet size RSU can send at once |
| 25: | for i in len(max(RSUpacketsize)): |
| 26: | broadcast(sorted_BCTscore_list[i]) |
| 27: | |
| 28: | while if a vehicle is within communication range: |
| 29: | receive cluster information and requests |
| 30: | RSU_Broadcast(cluster information and requests, BCT) |
4. Performance Evaluation
4.1. Performance Evaluation Environment
4.2. Performance Evaluation Results
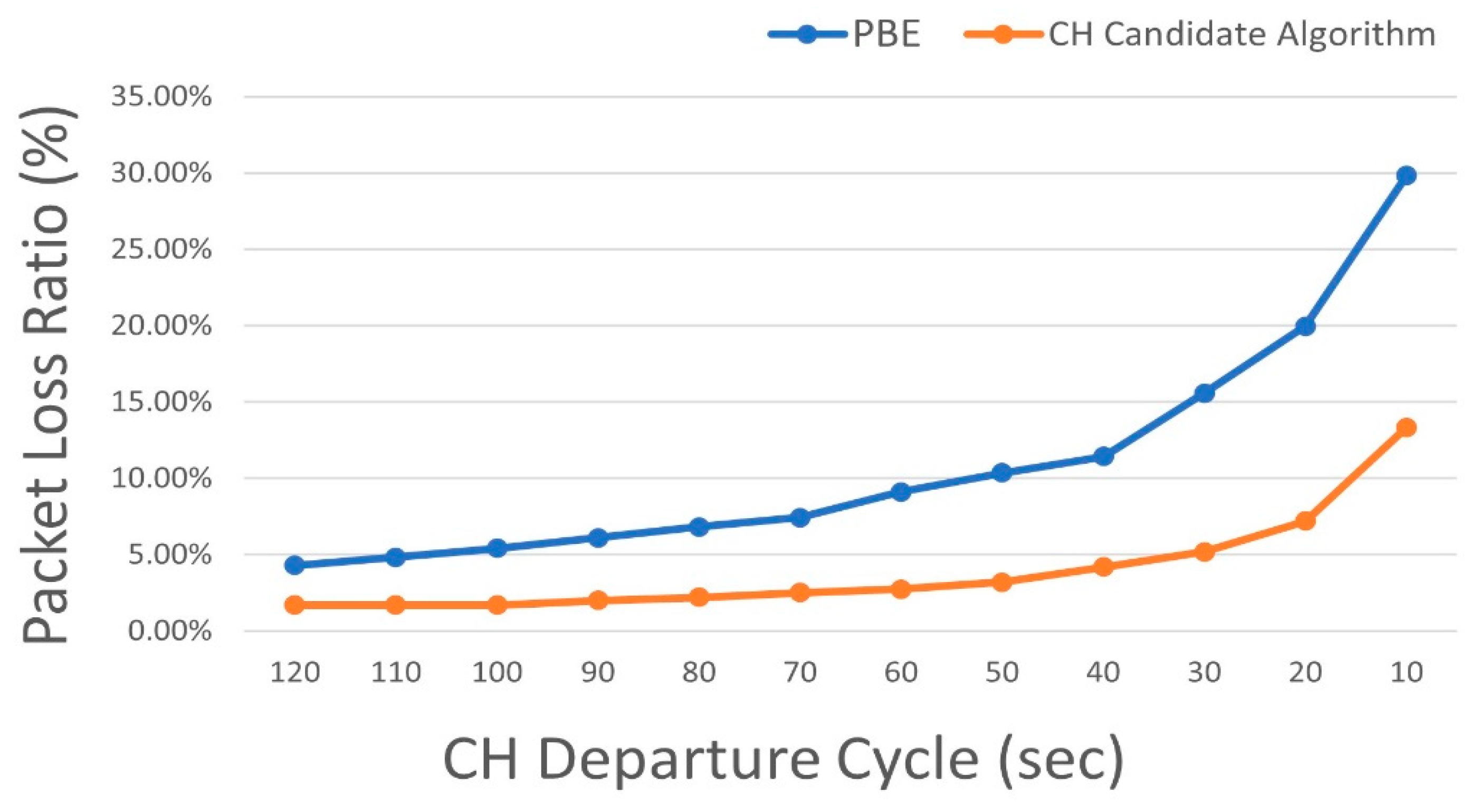
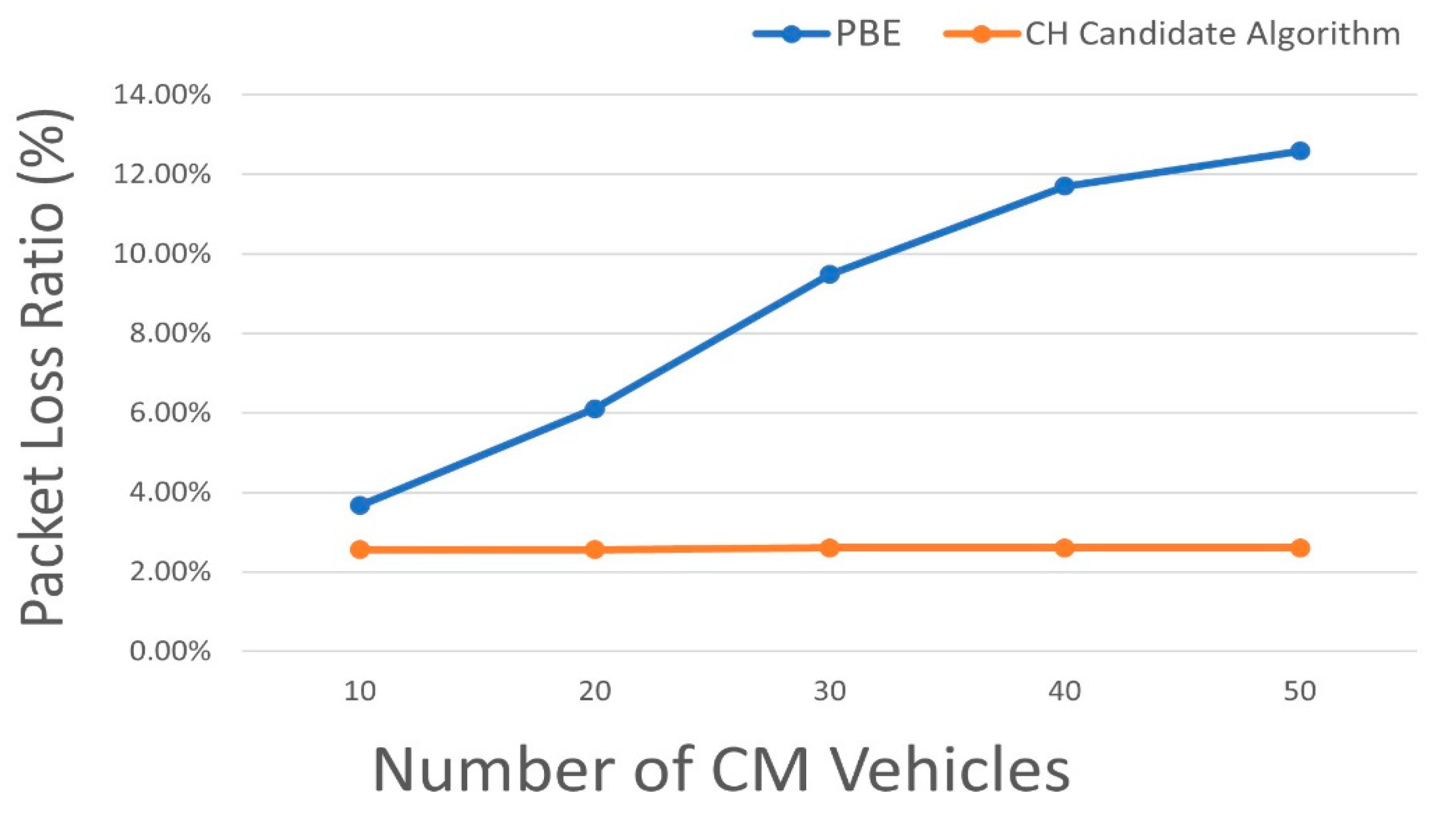
4.2.1. Comparison of Safety Message Packet Loss
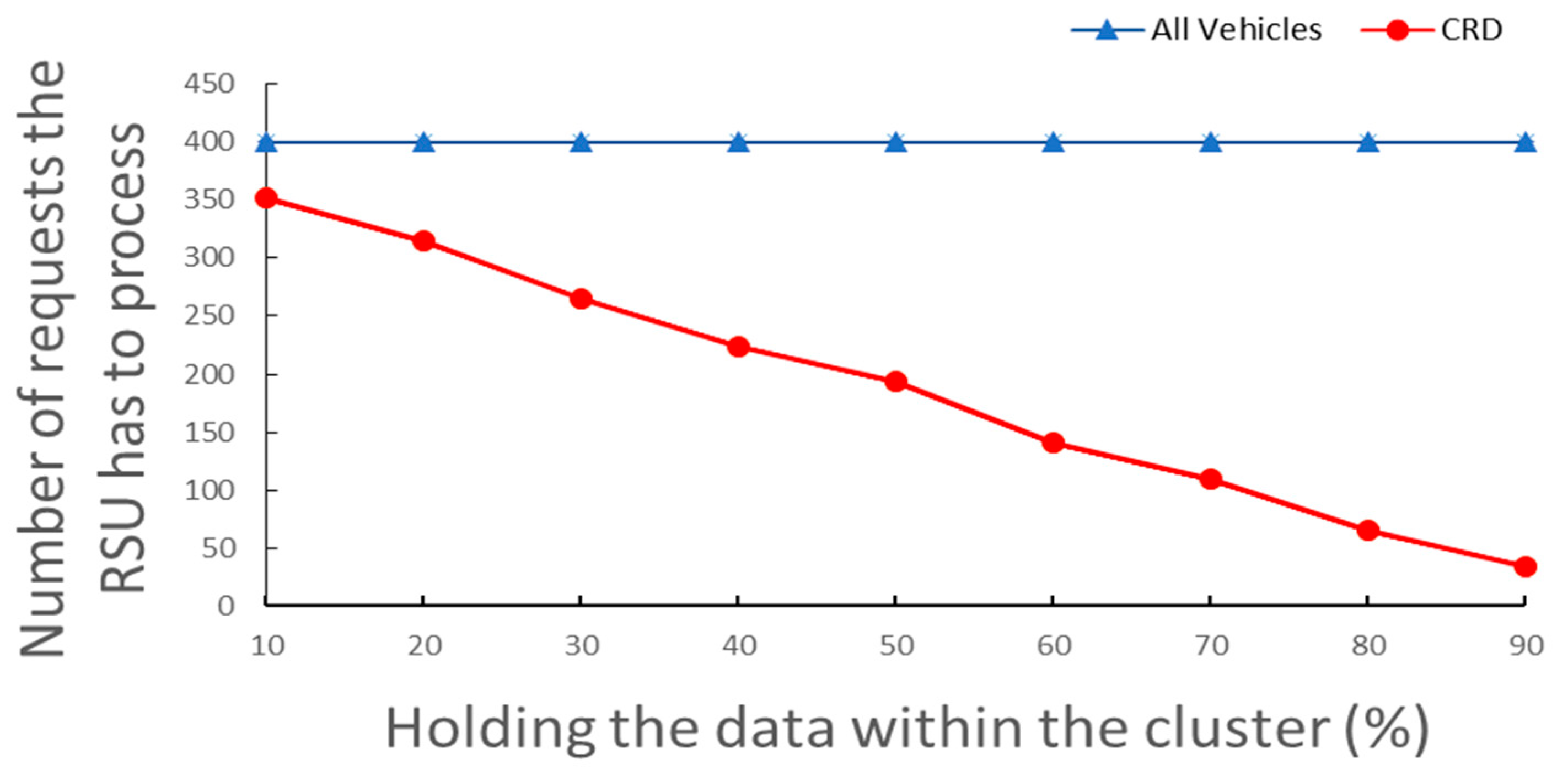
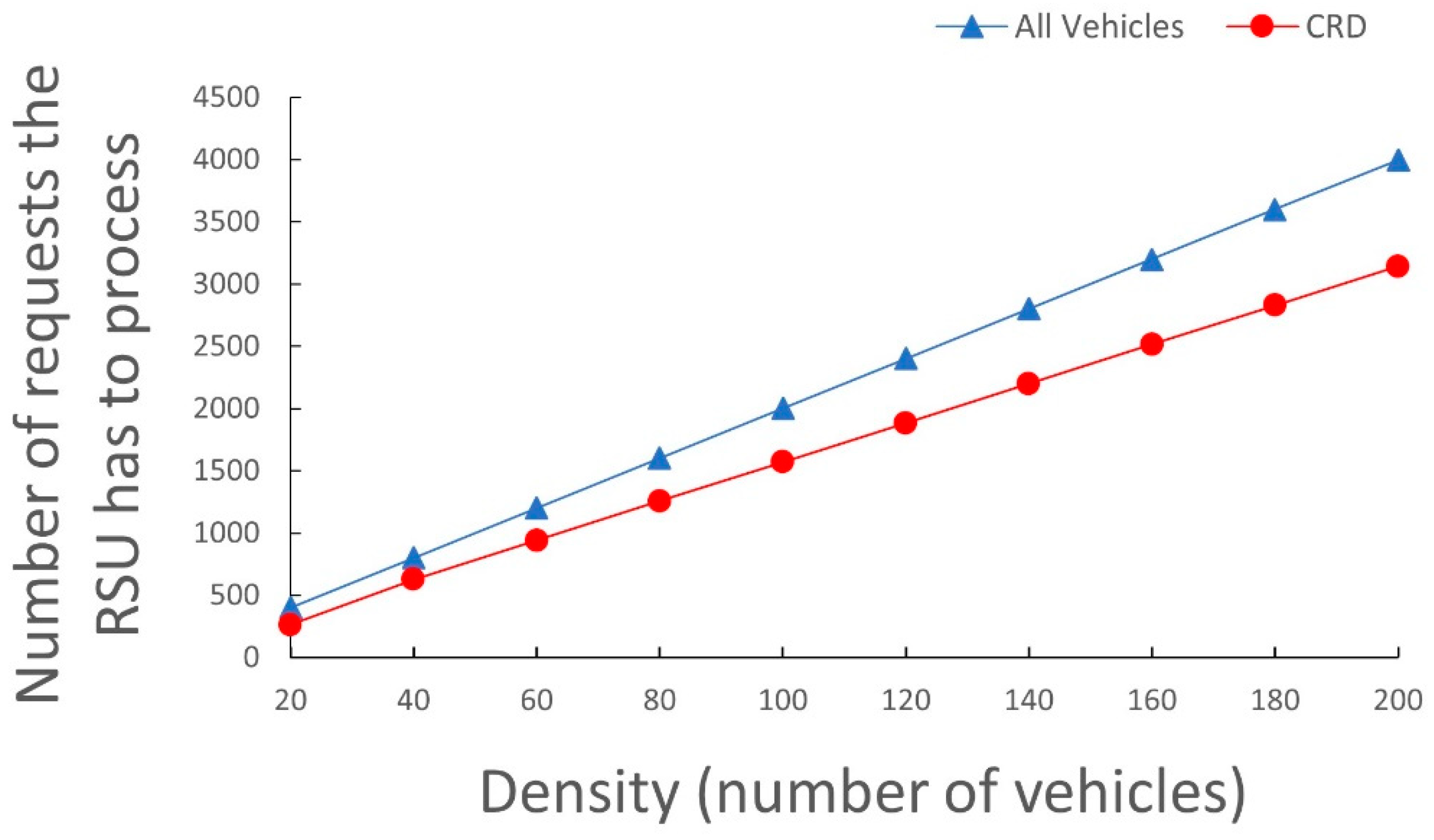
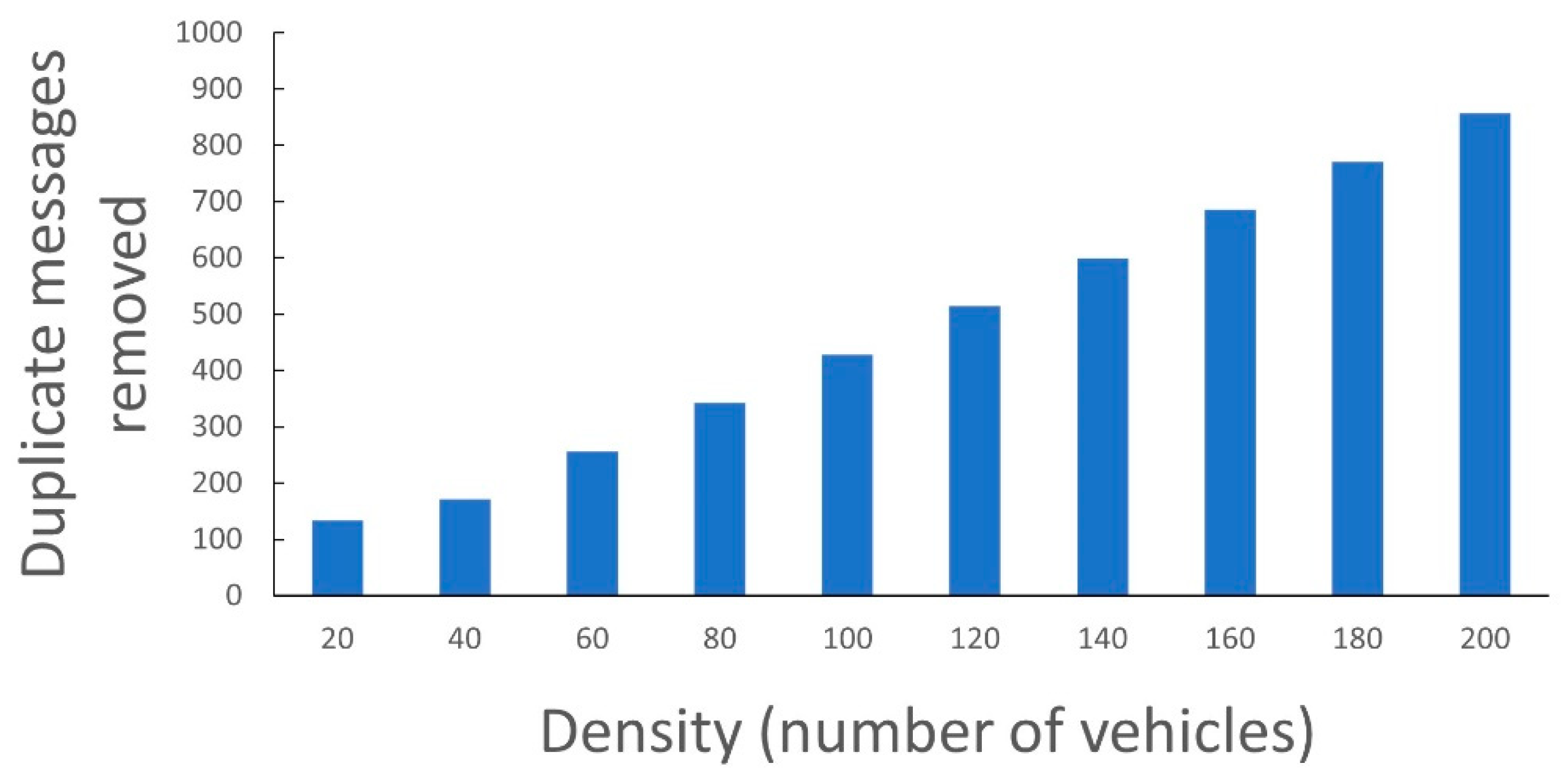
4.2.2. Comparison of the Number of RSU Processing Requests
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nitti, M.; Girau, R.; Floris, A.; Atzori, L. On adding the social dimension to the internet of vehicles: Friendship and middleware. In Proceedings of the 2014 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Chisinau, Moldova, 27–30 May 2014. [Google Scholar]
- Alam, K.M.; Saini, M.; El Saddik, A. Toward social internet of vehicles: Concept, architecture, and applications. IEEE Access 2015, 3, 343–357. [Google Scholar] [CrossRef]
- Maglaras, L.A.; Al-Bayatti, A.H.; He, Y.; Wagner, I.; Janicke, H. Social internet of vehicles for smart cities. J. Sens. Actuator Netw. 2016, 5, 3. [Google Scholar] [CrossRef]
- Contreras-Castillo, J.; Zeadally, S.; Guerrero-Ibañez, J.A. Internet of vehicles: Architecture, protocols, and security. IEEE Internet Things J. 2017, 5, 3701–3709. [Google Scholar] [CrossRef]
- Butt, T.A.; Iqbal, R.; Shah, S.C.; Umar, T. Social Internet of Vehicles: Architecture and enabling technologies. Comput. Electr. Eng. 2018, 69, 68–84. [Google Scholar] [CrossRef]
- Din, S.; Paul, A.; Rehman, A. 5G-enabled Hierarchical architecture for software-defined intelligent transportation system. Comput. Netw. 2019, 150, 81–89. [Google Scholar] [CrossRef]
- Raza, N.; Jabbar, S.; Han, J.; Han, K. Social vehicle-to-everything (V2X) communication model for intelligent transportation systems based on 5G scenario. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems, Amman, Jordan, 26–27 June 2018. [Google Scholar]
- Zualkernan, I.A.; Aloul, F.; Al Qasimi, S.; AlShamsi, A.; Al Marashda, M.; Ahli, A. Digimesh-based social internet of vehicles (siov) for driver safety. In Proceedings of the 2018 International Symposium in Sensing and Instrumentation in IoT Era (ISSI), Shanghai, China, 6–7 September 2018. [Google Scholar]
- Khan, I.; Härri, J. Can IEEE 802. 11 p and Wi-Fi coexist in the 5.9 GHz ITS band? In Proceedings of the 2017 IEEE 18th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Macau, China, 12–15 June 2017. [Google Scholar]
- Gräfling, S.; Mähönen, P.; Riihijärvi, J. Performance evaluation of IEEE 1609 WAVE and IEEE 802。 11 p for vehicular communications. In Proceedings of the 2010 Second International Conference on Ubiquitous and Future Networks (ICUFN), Jeju Island, Republic of Korea, 16–18 June 2010. [Google Scholar]
- Klingler, F.; Dressler, F.; Sommer, C. IEEE 802. 11 p unicast considered harmful. In Proceedings of the 2015 IEEE Vehicular Networking Conference (VNC), Kyoto, Japan, 16–18 December 2015. [Google Scholar]
- Benrhaiem, W.; Hafid, A.; Sahu, P.K. Reliable emergency message dissemination scheme for urban vehicular networks. IEEE Trans. Intell. Transp. Syst. 2019, 21, 1154–1166. [Google Scholar] [CrossRef]
- Ali, M.; Malik, A.W.; Rahman, A.U.; Iqbal, S.; Hamayun, M.M. Position-based emergency message dissemination for Internet of vehicles. Int. J. Distrib. Sens. Netw. 2019, 15. [Google Scholar] [CrossRef]
- Ko, B.; Liu, K.; Son, S.H.; Park, K.J. RSU-assisted adaptive scheduling for vehicle-to-vehicle data sharing in bidirectional road scenarios. IEEE Trans. Intell. Transp. Syst. 2020, 22, 977–989. [Google Scholar] [CrossRef]
- Ali, G.M.N.; Chong, P.H.J.; Samantha, S.K.; Chan, E. Efficient data dissemination in cooperative multi-RSU vehicular ad hoc networks (VANETs). J. Syst. Softw. 2016, 117, 508–527. [Google Scholar]
- Hu, B.; Fang, L.; Cheng, X.; Yang, L. In-Vehicle caching (IV-Cache) via dynamic distributed storage relay (D2SR) in vehicular networks. IEEE Trans. Veh. Technol. 2018, 68, 843–855. [Google Scholar] [CrossRef]
- Fang, S.; Khan, Z.; Fan, P. A cooperative RSU caching policy for vehicular content delivery networks in two-way road with a T-junction. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25–28 May 2020. [Google Scholar]
- Vijayakumar, V.; Joseph, K.S. Adaptive load balancing schema for efficient data dissemination in Vehicular Ad-Hoc Network VANET. Alex. Eng. J. 2019, 58, 1157–1166. [Google Scholar] [CrossRef]
- Pyun, D.W.; Lim, J.T.; Bok, K.S.; Yoo, J.S. Data Dissemination Strategies Considering Data Characteristics in Social Internet of Vehicles Environments. In Proceedings of the International Conference of Convergence Contents, Busan, Republic of Korea, 12–14 November 2020. [Google Scholar]
- Pessoa, G.; Guardalben, L.; Luís, M.; Senna, C.; Sargento, S. Evaluation of content dissemination strategies in urban vehicular networks. Information 2020, 11, 163. [Google Scholar] [CrossRef]
- Ning, Z.; Huang, J.; Wang, X.; Rodrigues, J.J.; Guo, L. Mobile edge computing-enabled Internet of vehicles: Toward energy-efficient scheduling. IEEE Netw. 2019, 33, 198–205. [Google Scholar] [CrossRef]
- C-ITS. Available online: https://www.c-its.kr/introduction/service.do (accessed on 1 May 2023).
- Sethi, V.; Pal, S.; Vyas, A. Online energy-efficient scheduling algorithm for renewable energy-powered roadside units in VANETs. In Proceedings of the 2020 IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Delhi, India, 10–13 December 2020. [Google Scholar]
- Tang, C.; Zhu, C.; Wei, X.; Chen, W.; Rodrigues, J.J. RSU-empowered resource pooling for task scheduling in vehicular fog computing. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020. [Google Scholar]
- Pal, R.; Prakash, A.; Tripathi, R.; Naik, K. Scheduling algorithm based on preemptive priority and hybrid data structure for cognitive radio technology with vehicular ad hoc network. IET Commun. 2019, 13, 3443–3451. [Google Scholar] [CrossRef]
- Ullah, A.; Yaqoob, S.; Imran, M.; Ning, H. Emergency message dissemination schemes based on congestion avoidance in VANET and vehicular FoG computing. IEEE Access 2018, 7, 1570–1585. [Google Scholar] [CrossRef]
- Bok, K.; Hong, S.; Cha, J.; Lim, J.; Yoo, J. Cooperative RSU Scheduling for Efficient Data Dissemination in VANET Environments. J. Korea Contents Assoc. 2013, 13, 27–36. [Google Scholar] [CrossRef]



| Environment | Value |
|---|---|
| CPU | Intel(R) Core(TM) i5-9600 CPU 3.70 GHz |
| Memory | 32.0 GB |
| OS | Window 10 64-bit |
| Language | Python 3 |
| MAC Model | IEEE 802.11p WAVE |
| Parameter | Value |
|---|---|
| Time to wait for disconnected CH | 1.5 s |
| Message transmission rate | 6 Mbps |
| Channel synchronization period | 100 ms |
| Beacon size | 194 bytes |
| EM packet size | 170 bytes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lim, J.; Pyun, D.; Choi, D.; Bok, K.; Yoo, J. Efficient Dissemination of Safety Messages in Vehicle Ad Hoc Network Environments. Appl. Sci. 2023, 13, 6391. https://doi.org/10.3390/app13116391
Lim J, Pyun D, Choi D, Bok K, Yoo J. Efficient Dissemination of Safety Messages in Vehicle Ad Hoc Network Environments. Applied Sciences. 2023; 13(11):6391. https://doi.org/10.3390/app13116391
Chicago/Turabian StyleLim, Jongtae, Dowoong Pyun, Dojin Choi, Kyoungsoo Bok, and Jaesoo Yoo. 2023. "Efficient Dissemination of Safety Messages in Vehicle Ad Hoc Network Environments" Applied Sciences 13, no. 11: 6391. https://doi.org/10.3390/app13116391
APA StyleLim, J., Pyun, D., Choi, D., Bok, K., & Yoo, J. (2023). Efficient Dissemination of Safety Messages in Vehicle Ad Hoc Network Environments. Applied Sciences, 13(11), 6391. https://doi.org/10.3390/app13116391










