Abstract
Background: Information and communication technology development provides services to various fields. In particular, the development of mobile technology has made ubiquitous services possible. However, as technology advances, security is being emphasized more and more. The existing method of user authentication by entering an ID and password is likely to leak sensitive information if the server is attacked or keylogged. Therefore, multi-level authentication is needed to prevent server attacks or keylogging. Methods: Biometric authentication technology has been utilized by smartphones, but it is challenging to apply in the case of a lost device because the central server does not manage biometric data. Encrypting transactions through blockchain technology makes data management more secure because blockchain technology is distributed, and there is no primary target for hackers. Results: The method proposed in this study can become a basis for an authentication method that guarantees both security and integrity due to the synergetic use of biometric and blockchain technologies. Conclusions: The information stored in the service provider does not include sensitive information such as the user’s biometric data but is only a means of verifying the user’s information in the blockchain transaction with guaranteed anonymity. Therefore, users can receive services with confidence and safety.
1. Introduction
The development of information and communication technology provides services to various fields. In particular, the development of mobile technology has made ubiquitous services possible. However, as technology advances, security is being emphasized more and more. The existing method of entering an ID and password is highly likely to leak all information if the server is attacked. Therefore, various methods for secure authentication have been studied. In Korea, user authentication in financial institutions has been performed by using public certificates. Still, this has been inconvenient to many users due to required Active X installation and usage difficulties. Accordingly, since November 2020, the Republic of Korea has abolished the accredited certificate system and introduced a multi-level authentication method that utilizes various authentication stages. For example, these authentication stages may include two or more types of simple passwords, Kakao certificates, OTP numbers, and biometrics [1].
Blockchain, which has recently been attracting attention from many researchers, guarantees integrity based on a decentralized and distributed trust structure and enables the implementation of an authentication system that cannot be forged or tampered with. By combining blockchain technology with Internet-based technologies that require perfect security, a system can be developed that applies both data integrity and strong security. Blockchain technology encrypts transactions to protect data, includes various information in blocks, connects them to chains, and continuously generates blocks at short intervals, making it difficult for hackers to prepare time and system resources for attacks [2,3,4].
The use of biometric technology for user authentication is also increasing. In iPhone and Android smartphones, biometric technologies such as fingerprint recognition and face recognition are used along with simple passwords in order to strengthen the mobile device’s security. Additionally, biometrics has begun to be used as a new authentication method for online transactions in the financial field. In particular, facial recognition security systems are easy to use and not easy to forge, so these can help prevent security accidents related to finance [1].
Therefore, this study proposes a multi-level authentication system using blockchain-based technologies such as DID (decentralized identity) technology and biometric recognition technology.
The following are requirements in the process of designing a secure and effective multi-factor authentication system.
- Account information required for user authentication must be free from forgery or alteration by hackers;
- In terms of security, user authentication must be secure;
- The user authentication process should be performed in a simple or easy way;
- During the authentication process, if a legitimate user cannot be identified, even if the user is a legitimate user, that user should not be incorrectly authenticated (miscertified). After entering the ID and password when starting the service, if authentication is performed using facial recognition technology, this information is stored in the blockchain. Since the user’s facial recognition information is accumulated in the blockchain, the integrity of the data can be guaranteed for purposes of identity authentication.
The composition of this study examines the concept of DID with related research in Section 2 and examines various platforms that have been developed based on DID and DID Auth standards, as well as neural network algorithms that can be applied to them. In Section 3, the system structure proposed in this study is designed and explained, and Section 4 describes the development of authentication systems. Finally, Section 5 provides the conclusion of the study and describes future research tasks.
2. Related Works
2.1. Blockchain Architecture
In order to utilize blockchain technology, it is necessary to understand the logical components of blocks. Typically, the size of a block is about 215 b~1 MB, and each block is composed of a block header and a block body, as shown in Figure 1. The block header consists of six components: the version number of the software, the central previous block hash, the root hash of the Merkle tree, the timestamp of the block, the difficulty target, and the nonce. The block body consists of transactions T1, T2, T3… etc. [5,6,7].
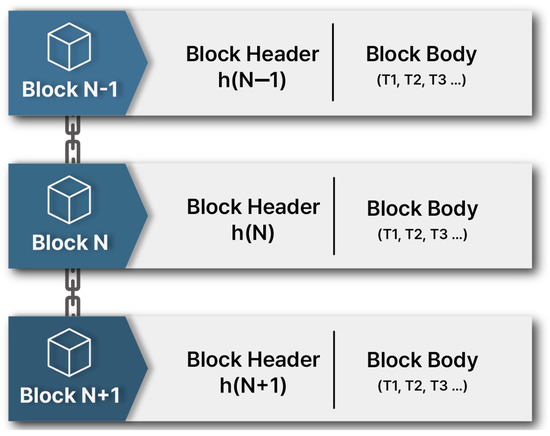
Figure 1.
Structure of a blockchain.
Block body transactions are grouped in pairs in the form of T1 + T2 and T3 + T4 and continue to be hashed to yield a single hash value, which is entered into the Merkle hash tree in the block header and then recombined with the values of the other elements of the block header in order to produce another compressed single hash value through the hashing algorithm.
Each time a block is created by adding a value to the nonce in the block header, a new hash value is obtained. If that hash value meets the condition that is derived from the hashing algorithm, the proof process is successful. The creation of the new block is continued, and it is connected to the previous block.
2.2. Decentralized Identifier & Self-Sovereign ID
DID is a means of identity verification based on distributed ledger technology. It is a digitized identity verification method that is independent of the control of a central system and allows individuals to maintain control over their own information. Users can verify their identity by including their personal information in the digital wallet which is linked to the distributed ledger and by inputting their private key whenever necessary. Participants in the DID service are composed of users (Holder), issuers (Issuer), and verifiers. Users can directly manage their personal information through the electronic wallet application installed on a mobile device. The issuing agency issues the requested data after verifying a user when the user requests the issuance of an ID and certificate. A verifier is a company or institution that provides services. After the ID and certificate submitted by a user are verified, the service is provided to the user [8].
Self-sovereign ID has been designed as a new approach to identity verification in which a user maintains ownership of their information and personal information is not managed by a specific server but is provided according to requests. Blockchain decentralization is the basis for self-sovereign identity, and platforms such as Sovrin [9] and uPort [10] are being developed to address this issue.
Blockchain technology is a technology that allows all participants in the network to share, verify, and record transaction information. Additionally, since the transaction ledger, in which transaction information is recorded, is distributed and stored among all participants in the network, manipulation of the ledger is not possible unless all participants are hacked. The types of shared transaction information include general data types and smart contracts programmed to perform specific functions. Smart contracts are programs that can be designed so that blockchain network participants can run the same code at the same time, verify the results, and record or modify the results only when they are all the same. All participants in the blockchain network can therefore trust the information recorded through a smart contract without needing to use a trusted third public certification authority. If fingerprint information can be shared between clients using these blockchain characteristics, passwords can also be safely recovered with user fingerprints without having to go through an institution to recover passwords when passwords are lost. This eliminates the hassle of the user having to visit an institution to reissue and reset their certificate [11].
2.3. Biometric Technology
Biometric technology is being studied in various fields, such as mobile devices and smart homes. It is a technology that automatically measures an individual’s unique biometric information, which has a different shape for each individual and can be used to identify the individual. The existing recognition method has a problem in that the user has to remember a password or possess a pass, such as a card, which reduces convenience and lowers security due to the risk of duplication and loss. In order to solve these problems, systems using voice recognition technology and fingerprint recognition technology are also being studied. Figure 2 shows the physical and behavioral characteristics of biometric technology. Biometric information can be largely divided into physical characteristics and behavioral characteristics. Physical characteristics include fingerprint recognition, retina or iris recognition, and facial recognition. Behavioral characteristics include motion recognition, pattern recognition, and voice recognition [12,13].
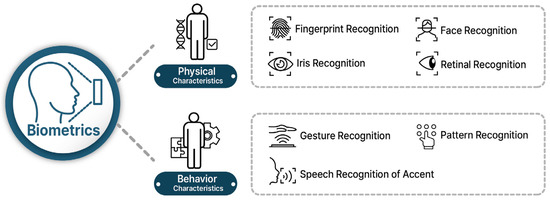
Figure 2.
Features of Biometrics.
The biometric system converts the unique physical or behavioral characteristics of a person into a digital format and then compares the results with each person’s biometric information that has been extracted in advance. The technology has a high discriminating power to determine whether or not the two compared characteristics are, in fact, characteristics of the same individual. A practical and important point in designing a biometric system is to determine how an individual is recognized, and the biometric system can be used as an authentication system or a recognition system [14,15,16].
Facial recognition is a system that recognizes a person’s face using a camera at a short distance and is the most excellent system in terms of user convenience that enables non-contact authentication. It is a technology that can establish a database of existing users’ facial photos and compare them with the images captured by the camera in order to identify who they are. Facial recognition technology can replace existing identification cards such as passports and driver’s licenses and is often used for airport immigration screening. In addition, it can be easily used to manage telecommuting or school attendance in the current era caused by the COVID-19 pandemic. However, the recognition rate of facial recognition technology may decrease and the rejection rate may increase when a face shape is changed or too similar to another, such as in the case of twins or plastic surgery [14,15,16].
3. DID-Based Authentication
3.1. DID Gateway
DID is not fixed to one particular blockchain or system but can be distributed and stored in several types of blockchain networks [17]. When a client accesses the DID gateway and requests a DID, the DID blockchain is read. After that, DID attributes deliver the DID document to the client through the DID gateway. The client can register, modify, deactivate, inquire, and verify the DID document through these operations.
The DID gateway unifies and standardizes common data related to authentication between various blockchains and converts it into a standardized format for storage in a new chain, thereby enabling interworking with different chains.
Figure 3 shows the client accessing the DID blockchain through the DID gateway.
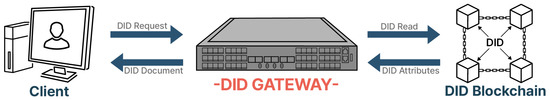
Figure 3.
DID authentication network.
3.2. DID Authentication Network
When the blocks seen in Figure 1 are gathered and connected, the blocks are continuously connected in a chain as in Figure 2. The user requests the DID from the DID gateway, which reads the DID in the blockchain and brings in the DID attribute. The DID gateway then performs DID authentication by creating a DID document based on the DID attribute information received from the DID blockchain and providing it to the clients who are the users.
Figure 4 illustrates that when the blockchain is configured in this way, and the user requests DID-auth from the DID system through the DID gateway via auth #N materials, the DID system sends a response to DID-auth #N materials.
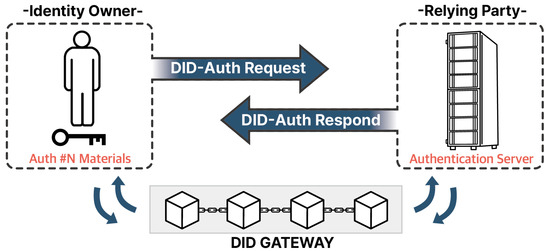
Figure 4.
Details of the DID authentication network.
3.3. DID Certification Process
Figure 5 shows how the blocks shown in Figure 1 and Figure 2 are connected to the user. A DID mobile card or DID distributed network sits between the user and the DID blockchain. When the user enters and stores information while accessing the DID mobile card, the DID mobile card system installs the DID mobile card based on the information provided. Then, when a request is made to retrieve a DID, the user provides his or her DID.
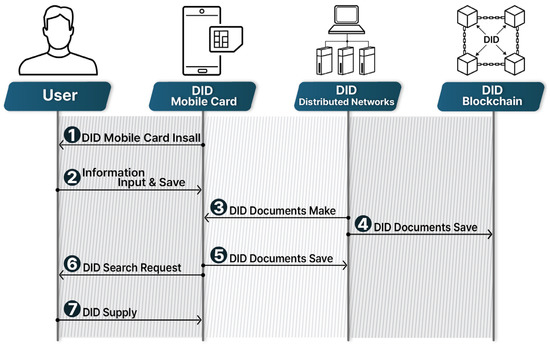
Figure 5.
UML-based flowchart with entities.
Between the DID mobile card and the DID distributed network, the DID mobile card system stores the DID document, and the DID distributed network creates the DID document through the DID blockchain. The above operation is shown in Figure 3.
Step 1. The user installs the DID mobile card through the smartphone.
Step 2. The user enters their information and saves it.
Step 3. The DID distributed network creates a DID document.
Step 4. The DID document is saved in a block in the DID blockchain.
Step 5. The DID document is saved through the DID distributed network.
Step 6. The DID search result is sent to the user.
Step 7. The DID is supplied to the DID mobile card.
3.4. DID Network Configuration
The structure of the system proposed in this study is presented as shown in Figure 6. The DID distributed network requests DID registration from the DID mobile card, and the DID mobile card authenticates the DID documents after authentication. If authentication for the DID mobile card proceeds in the mobile card distributed network, the DID mobile card sends a notification that authentication has been made. After each DID distributed network request and mobile card distribution network authentication request to the DID mobile card, the DID mobile card system proceeds with the authentication process through Face ID, and the VP (verifiable presentation) system requests and receives a response.
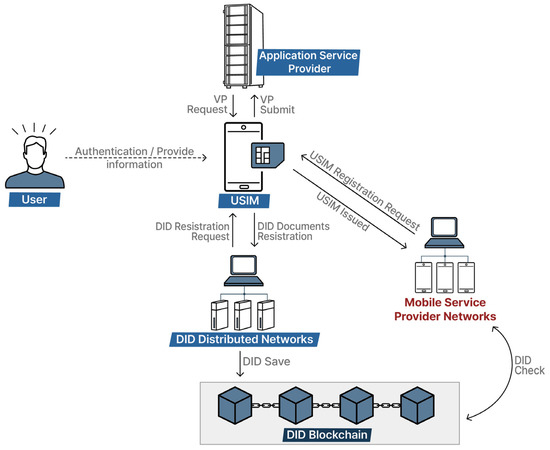
Figure 6.
The architecture of the proposed technique.
The VP consists of presentation metadata, verifiable credentials, and proofs, and the VP does not require users to directly submit VC (verifiable credentials) to prove their identity but includes their VC in the VP and then processes and submits it again. VC is used as a means for including identity attributes such as identification, career certificates, driver’s licenses, and other certificates, and a single VP may include multiple VCs. If a VC is continuously loaded and stored, it can become vulnerable to leakage when a hacking attempt is made on it later.
After that, the DID mobile card system responds to the DID distributed networks and the mobile card distribution network with authentication.
In the system proposed in this study, the authentication information is transmitted to the network and then the validation is performed. Blocks in the current blockchain can be saved after checking block validity, chain validity, and genesis block validity as shown in the source code below (Algorithm 1).
| Algorithm 1 Blockchain Based Authentication Code |
| const isValidNewBlock = (newBlock: Block, previousBlock: Block): boolean => { |
| if (!isValidBlockStructure(newBlock)) { |
| console.log(‘invalid structure’); |
| return false;} |
| if (previousBlock.index + 1 !== newBlock.index) { |
| console.log(‘invalid index’); |
| return false;} |
| else if (previousBlock.hash !== newBlock.previousHash) { |
| console.log(‘invalid previoushash’); |
| return false; } |
| else if (calculateHashForBlock(newBlock) !== newBlock.hash) { |
| console.log(typeof (newBlock.hash) + ‘ ‘ + typeof calculateHashForBlock(newBlock)); |
| console.log(‘invalid hash: ‘ + calculateHashForBlock(newBlock) + ‘ ‘ + newBlock.hash); |
| return false;} |
| return true;}; |
| const isValidChain = (blockchainToValidate: Block[]): boolean => { |
| const isValidGenesis = (block: Block): boolean => { |
| return JSON.stringify(block) === JSON.stringify(genesisBlock); }; |
| if (!isValidGenesis(blockchainToValidate[0])) { |
| return false; } |
| for (let i = 1; i < blockchainToValidate.length; i++) { |
| if (!isValidNewBlock(blockchainToValidate[i], blockchainToValidate[i - 1])) { |
| return false; }} |
| return true;}; |
4. Multiple Authentication Methods Using DID in the Blockchain
Section 4 implemented the applied service using the DID blockchain based on the system designed in Section 3.
4.1. Credential Storage
In order to utilize the DID blockchain service proposed in this study, the authentication structure will be reviewed. Authentication is the process of verifying whether the DID information presented by the user actually belongs to the user. In this study, in order to use the multi-factor authentication structure, facial recognition technology was added and used as biometric recognition. As a representative authentication method among the multi-level structures in this study, the method of signing in with an ID and password and the method of receiving authentication through the facial authentication procedure were mixed and used together. Through these operations, the user ID, password, and face vector data required for face authentication can be stored in the blockchain.
The representation of the authentication information storage system is shown in Figure 7.
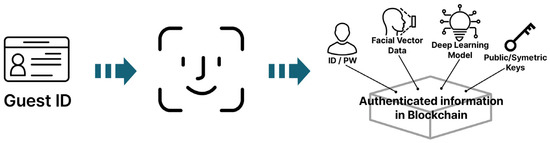
Figure 7.
Authentication information storage.
As shown in Figure 7, in the authentication information storage system, the user inputs their ID and password and performs authentication using face ID. The authentication information stored in the blockchain includes the user ID, password, face vector data, deep learning model, public key and symmetric key.
4.2. Authentication Steps
The user proceeds with the authentication process through the DID distribution network. Figure 8 descripts step by step authentication process.
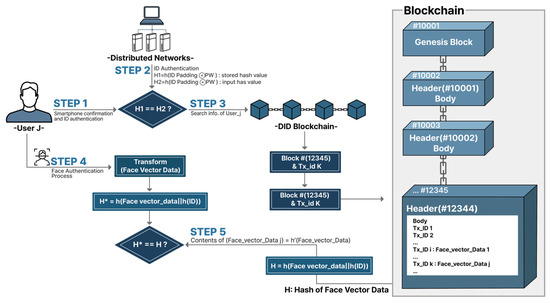
Figure 8.
Step-by-step process.
Step 1. In the first procedure, after attempting authentication with an ID and password, the block ID in the DID blockchain is compared with the information entered by the user. After the user enters the ID and the password is processed, the previously stored face vector data is fetched from the DID blockchain. The authenticated data is accumulated as a hash value, then entered into the authentication information storage system.
Step 2. The second step is to authenticate the user’s face. The previously stored block ID and face ID are set through face vector data. After that, the face vector data stored in the existing DID blockchain and the face vector data currently being authenticated are matched. After facial authentication is performed in this way, the service of the corresponding content can be provided. In addition, among the information stored in the block by the user, sensitive information such as facial recognition is not stored as it is, but is distributively stored in the block. In addition, the user information used within the block is only used as a means of checking user information in the transaction within the block.
Step 3. In the third step, the user goes through the process of authenticating with face ID after the ID and password are processed. If the face ID is authenticated following the processing of the user ID and password, the probability that it is not actually the correct person is inevitably reduced significantly.
Step 4. In step four, the details authenticated by face ID in the previously saved block are found.
Step 5. In step five, the currently authenticated face ID is compared with the previously saved face ID value. A person’s face may be slightly different depending on weight change, makeup status, health status, and so on, so a slight allowable threshold is permitted.
Step 6. In step six, after authentication based on the comparison result is conducted in Step 5, the content provided by the application becomes available for use.
4.3. Multi-Factor Authentication Technique
The most important of the techniques proposed in this study is multi-factor authentication. Multi-factor authentication is a method that allows users to authenticate by creating multiple steps using attributes they already know.
In one-step verification, a user is randomly presented with one of the various methods to authenticate, such as an ID/password combination, pattern drawing, or a pin number. The owner of a smartphone must know their authentication information for all three methods because it is unknown which method will be presented. In fact, this is the same as the method of authenticating a user with all three.
After passing one-step verification, two-step verification is tried. In Step 2 of Figure 9, the ARS authentication process is presented by the system, and if verified, the authentication is passed. After passing through two-step verification, three-step verification is tried. Three-step authentication is the final identity verification process and uses biometric information such as fingerprints or faces. In Step 4, the previously processed authentication data stored in the existing blockchain is imported and compared with the newly processed authentication data and then passed on to the service process in Step 5. At this stage, no action is actually taken by the user, and the authentication process takes place in the backend during system latency. If the result of blockchain matching turns out to be false, the first step is resumed, or the service process is terminated.
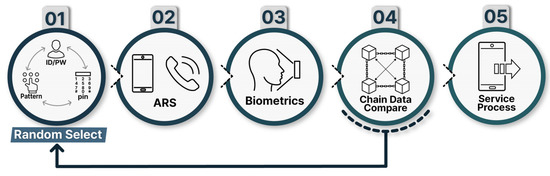
Figure 9.
Multi-factor authentication.
4.4. Analysis and Evaluation of the Proposed Method
In the method proposed in this study, a user’s ID, password, and facial information, which is the minimum necessary information for user authentication, are stored, and authentication is performed by comparing and verifying the hash value of biometric authentication information from the DID blockchain.
Through the system design, the structure of the basic DID blockchain system was defined, and the authentication system could be implemented by utilizing the system structure.
The system proposed in this study is an authentication model that combines ID/PW and biometric information and stores it in a blockchain, which guarantees more stability than the one-step authentication method. In addition, as of November 2020, the accredited certificate system was abolished in Korea, and Internet banking has been implemented through various authentication methods. Therefore, this study makes it possible to enter various certificate markets.
The system proposed in this study can have the following advantages.
The requirements for an effective multi-factor authentication system are as follows.
- Because the account information is recorded on the blockchain using blockchain technology, the integrity of the blockchain is guaranteed, so there is no possibility of hackers tampering with the user’s account information;
- There is a possibility that biometric authentication may not properly authenticate a user. Therefore, security is guaranteed by applying two or more authentication techniques through multi-factor authentication;
- Due to the widespread use of smartphones, the proposed technique is authentication using a smartphone possessed by a user, so authentication proceeds in a simple and easy way.
First, if biometric information such as facial recognition technology is stored in the DID blockchain and distributed, it is difficult to find out what kind of data it actually is without confirmation from the service provider, even if anyone can access it. Therefore, the security and safety of user authentication information can be improved through confidentiality through biometric technology.
Secondly, the service provider cannot misuse biometric information. Even if someone wanted to access the DID blockchain and combine distributed and stored data, data abuse by the system provider can be avoided because there is no authentication information held by the user, and it can be safely stored from attacks by external attackers.
Third, the existing technique requires the user to change their ID and password at regular intervals, but in the proposed technique, there is no need to change the biometric information stored in the blockchain because it is the basis for the authentication. Therefore, user convenience can be improved;
- 4.
- Since the proposed technique performs authentication through multi-factor authentication, legitimate users are not unauthenticated due to the basic user identification that is performed in Step 1, and illegitimate users are not erroneously authenticated due to the biometric authentication performed in Step 2.
4.5. Discussion
Research on authentication using blockchain technology is just beginning, and this research is still in the early stages. The study “Biometric Information and OTP based on Authentication Mechanisms using Blockchain” is a study that records biometric information on a blockchain and authenticates users in that way. This study’s results are compared and analyzed in Table 1 below.

Table 1.
Comparison of related research and this study.
The existing method of user authentication is two-factor authentication using an ID or OTP, but in the proposed method, various authentication methods are performed by applying a random sequence of multi-factor authentication methods. In both techniques, the stored authentication information is recorded on the blockchain, so there is no possibility of tampering or forgery.
In the existing technique, security is a method of two-step authentication based on the blockchain after ID or OTP authentication. The proposed model is applied to various authentication methods at random, and finally, stability is improved by performing authentication based on biometric face ID. The big difference from previous studies is whether DID technology is applied.
Applying DID technology, which is a technique that can authenticate users with a single ID when logging into multiple organizations, has the advantage of increasing user convenience. In addition, by applying DID technology when logging in to multiple organizations, a single ID can be authenticated, which has the advantage of increasing user convenience. In addition, the recent smartphone replacement cycle in Korea is only around 33 months, which is not long. In other words, since the proportion of usage of the latest smartphones in Korea is high, the fingerprint recognition and face recognition required in this study can be utilized effectively, the proportion of use in mobile applications can be increased, and even general users will be able to use various biometrics authentication technologies.
Due to the limited amount of power in smartphones, an analysis of energy consumption utilizing this method is required. Since the proposed method performs authentication in several steps, there may be relatively more energy consumption, but it is not large. There is a trade-off relationship between security and energy consumption. In addition, taking Korea as an example, when applying a solution using a mobile device, authentication methods such as fingerprint recognition and face recognition have been routinely used without any problems. One more use of the mobile application by the user does not drain the battery to the point of being inconvenient in their daily lives. Therefore, it cannot be said that the system proposed in this study consumes too much more of the battery of the mobile device.
Blockchain has mainly two well-known challenges, which are scalability and high cost. Blockchain technology involves several complex algorithms to process a single transaction. First, from the scalability perspective, as more and more people get used to it, the average number of transactions has also increased dramatically. This can severely hurt the processing speed of blockchain transactions, as a higher number of people using the system implies more computers writing and accessing the network, which can create an overall cumbersome system. The other challenge is cost. Blockchain is usually implemented to eliminate the expenses related to third parties and intermediaries involved in transferring values. Though blockchain technology is beneficial, it is still in the nascent stages of innovation, making it tough to integrate into legacy systems. Overall, this makes it an expensive affair, preventing its adoption by the government and private firms. In addition, in this research, we added multi-level authentication to the blockchain system, making scalability and cost worse. However, verification costs of identification for users on the blockchain is still low.
On the other hand, the blockchain mining process takes the most time, not the verification process, which is relatively low and can be considered ignorable. Furthermore, the performance of smartphones improves each year, and it will soon equal the performance of PC systems. Therefore, overhead costs will be ignorable and will not significantly affect the overall multi-level authentication cost on the blockchain system.
5. Conclusions
Numerous Internet services reinforce security through user authentication when accessing their systems. The old method of using an ID and password combination can be found in email authentication, and the public certificate system has many elements about it that are very inconvenient to use. To overcome these vulnerabilities and inconveniences, a login system was designed using facial recognition technology based on the ID and password authentication environment. The information in this authentication process is stored in the blockchain using DID technology, and blocks can be continuously generated. DID is a new paradigm shift in security because, from a hacker’s point of view, they do not know where to attack because they have no primary target.
The method proposed in this study can become a basis for an authentication method that guarantees both security and integrity. The information stored in the service provider does not contain sensitive information such as the user’s biometric information but is only a means of verifying the user’s information in the blockchain transaction with guaranteed anonymity. Furthermore, user information is disclosed within the blockchain, but it is safe because it is transformed by a hash function and is immutable. Therefore, users can authenticate and receive services with confidence.
In particular, since the accredited certificate system in Korea has disappeared and user authentication has been made possible through various authentication methods, it is thought that the technique proposed in this study will become an opportunity for this technology to be widely used in the Korean financial and Internet service market.
As a future research task, an evaluation of the stability and usability of the system proposed in this study will be conducted, and the results will be presented.
Author Contributions
Conceptualization, S.K., H.-J.M. and S.H.; methodology, S.K. and S.H.; software, S.K. and S.H.; validation, H.-J.M. and S.H.; formal analysis, H.-J.M.; investigation, S.K.; resources, S.K. and S.H.; data curation, S.K. and S.H.; writing–original draft preparation, S.K.; writing–review and editing, H.-J.M. and S.H.; visualization, S.K.; supervision, S.H.; project administration, S.H.; funding acquisition, S.H. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT) (No. 2020R1F1A1048684).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Mun, H.-J. Biometric Information and OTP based on Authentication Mechanism using Blockchain. J. Converg. Inf. Technol. 2018, 8, 85–90. [Google Scholar] [CrossRef]
- Salah, K.; Rehman, M.H.U.; Nizamuddin, N.; Al-Fuqaha, A. Blockchain for AI: Review and Open Research Challenges. IEEE Access 2019, 7, 10127–10149. [Google Scholar] [CrossRef]
- Yang, J.-H. A Study on the Effect of Block Chain Application and Legal Issue in Logistics Industry. J. Converg. Inf. Technol. 2018, 8, 187–199. [Google Scholar] [CrossRef]
- Lee, D.-Y.; Park, J.-W.; Lee, J.-H.; Lee, S.-R.; Park, S.-Y. Blockchain Core Technology and Domestic and Foreign Trends. Commun. Korean Inst. Inf. Sci. Eng. 2017, 35, 22–28. [Google Scholar]
- Woodside, J.M.; Augustine, F.K., Jr.; Giberson, W. Blockchain technology adoption status and strategies. J. Int. Technol. Inf. Manag. 2017, 26, 65–93. [Google Scholar]
- Hu, R.; Yan, W.Q. Design and Implementation of Visual Blockchain With Merkle Tree. In Handbook of Research on Multimedia Cyber Security; IGI Global: Hershey, PA, USA, 2020; pp. 282–295. [Google Scholar] [CrossRef]
- Kim, J. Application of the Blockchain Principle to Composition Technique: Focusing on the Method for Deriving a Tone Row by Applying Blockhash and Hash Function. J. Ewha Music Res. Inst. 2018, 22, 83–110. [Google Scholar] [CrossRef]
- Kim, H.-Y.; Han, K.-H.; Shin, S.-S. A Model for Self-Authentication Based on Decentralized Identifier. J. Converg. Inf. Technol. 2021, 11, 66–74. [Google Scholar] [CrossRef]
- Windley, P.; Reed, D. Sovrin: A Protocol and Token for Self-Sovereign Identify and Decentralized Trust. In A White Paper from the Sovrin Foundation; Sovrin Foundation: Provo, UT, USA, 2018; pp. 1–42. [Google Scholar]
- Lundkvist, C.; Heck, R.; Torstensson, J.; Mitton, Z.; Sena, M. Uport: A platform for self-sovereign identity. Whitepaper 2016; pp. 1–17. Available online: https://blockchainlab.com/pdf/uPort_whitepaper_DRAFT20161020.pdf (accessed on 23 January 2022).
- Kim, H.; Kim, S.; Kim, T.; Yu, H. A Design of Certificate Password Recovery Using Decentralized Identifier. J. Ventur. Innov. 2019, 2, 21–29. [Google Scholar] [CrossRef]
- Zhang, Y.N.; Ma, J.; Park, H.J. Factors Affecting the Usage of Face Recognition Payment Service. J. Korea Contents Assoc. 2019, 19, 490–499. [Google Scholar] [CrossRef]
- Park, H.B. A study on Home IoT Automatic System Based Customized Service. Ph.D. Dissertation, Paichai University, Daejeon, Korea, 2020. [Google Scholar]
- Lee, C.H. A Study on the Creditcard Approval System Using Biometric. Master’s Thesis, Konkuk University, Seoul, Korea, 2008. [Google Scholar]
- Miranda, L.; Miranda, L.N., Jr.; Oseña, L.J.C.T.; Delmo, J.A.B. Helmet for Road Hazard Warning and Wireless Motorcycle Authentication. Int. J. Adv. Sci. Converg. 2019, 1, 33–40. [Google Scholar] [CrossRef]
- Yu, M.J. Simple Payment System Using Biometrics. Master’s Thesis, Soongsil University, Seoul, Korea, 2021. [Google Scholar]
- Song, Y.; Hong, S. Build a Secure Smart City by using Blockchain and Digital Twin. Int. J. Adv. Sci. Converg. 2021, 3, 9–13. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).