Assistive Multimodal Robotic System (AMRSys): Security and Privacy Issues, Challenges, and Possible Solutions
Abstract
:1. Introduction
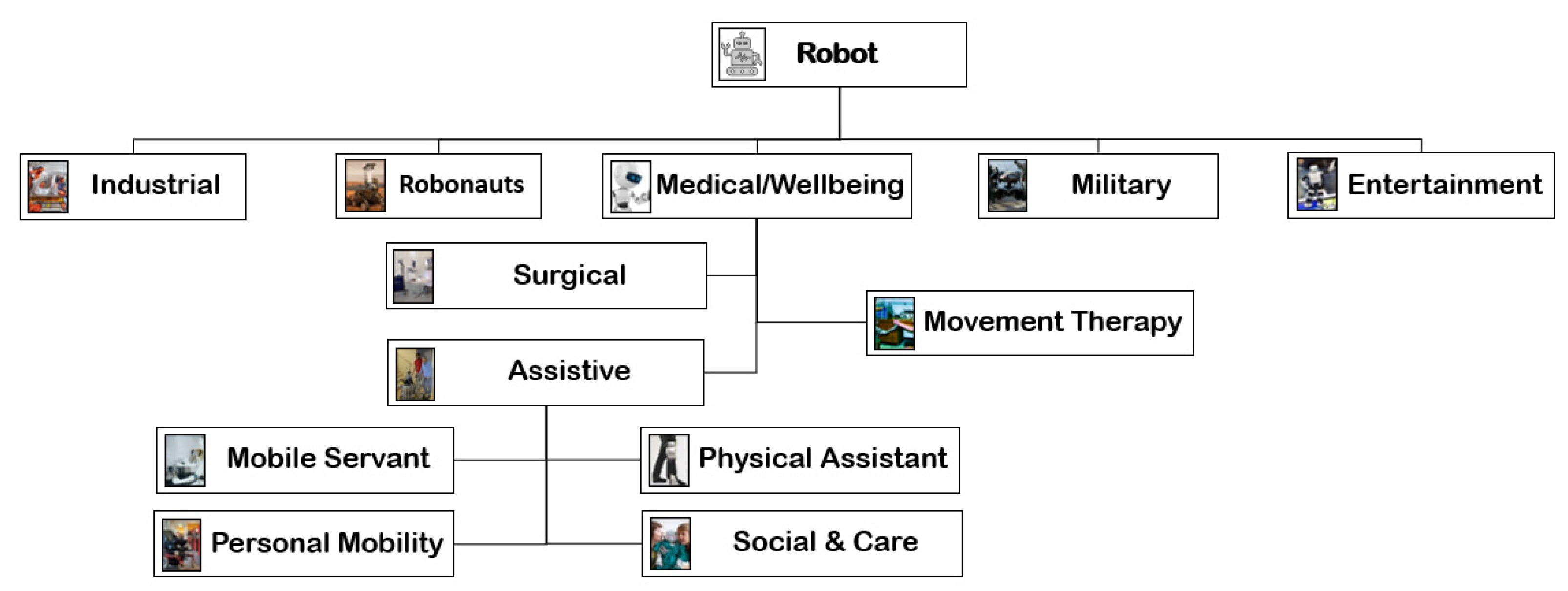
2. Types of Robots
3. Background Study of Assistive Multimodal Robots
4. Need for Transparency of the Robotic System
- (a)
- The data collected from the user, ambient environment of the user, health, and raw or processed wellbeing data, etc., are all collected and securely stored within the robotic system. All data are timestamped, and an ID is assigned. Only authorised users with the correct credentials can access the data and the level of access would depend upon the access priority and access rights provided by the user, or as required by the care provider or the maintenance team or supervisor.
- (b)
- A private BC system could be built among the robot, user’s PC/PCs, and cloud storage. However, the BC would not store any raw data or encrypted data; rather it would store only the ‘Merkle tree’, a hash of the transaction, timestamp, and unique ID of each transaction. This way, there would be no concerns about the data leakage or visibility in the BC network. It will, thus, preserve the user’s privacy in the BC system; even if hackers get into the BC system of the cloud or the PC of the user, no data would be visible. However, the stored encrypted data in the robot would be synced with the BC system that runs in the robot, the user’s PC, and the cloud, so that every activity of the robot is transparently captured in the BC system.
- (c)
- In order to maintain consistency and preserve the integrity of the BC system, a proof of stake (PoS) consensus algorithm approach could be adopted rather than the proof of work (PoW). This is because PoS blocks are assigned to validating nodes rather than miners, solving the hash math problems to validate and update the block, as described in [61]. Such an approach is more appropriate for the proposed BC framework, due to the participation of the limited but known nodes.
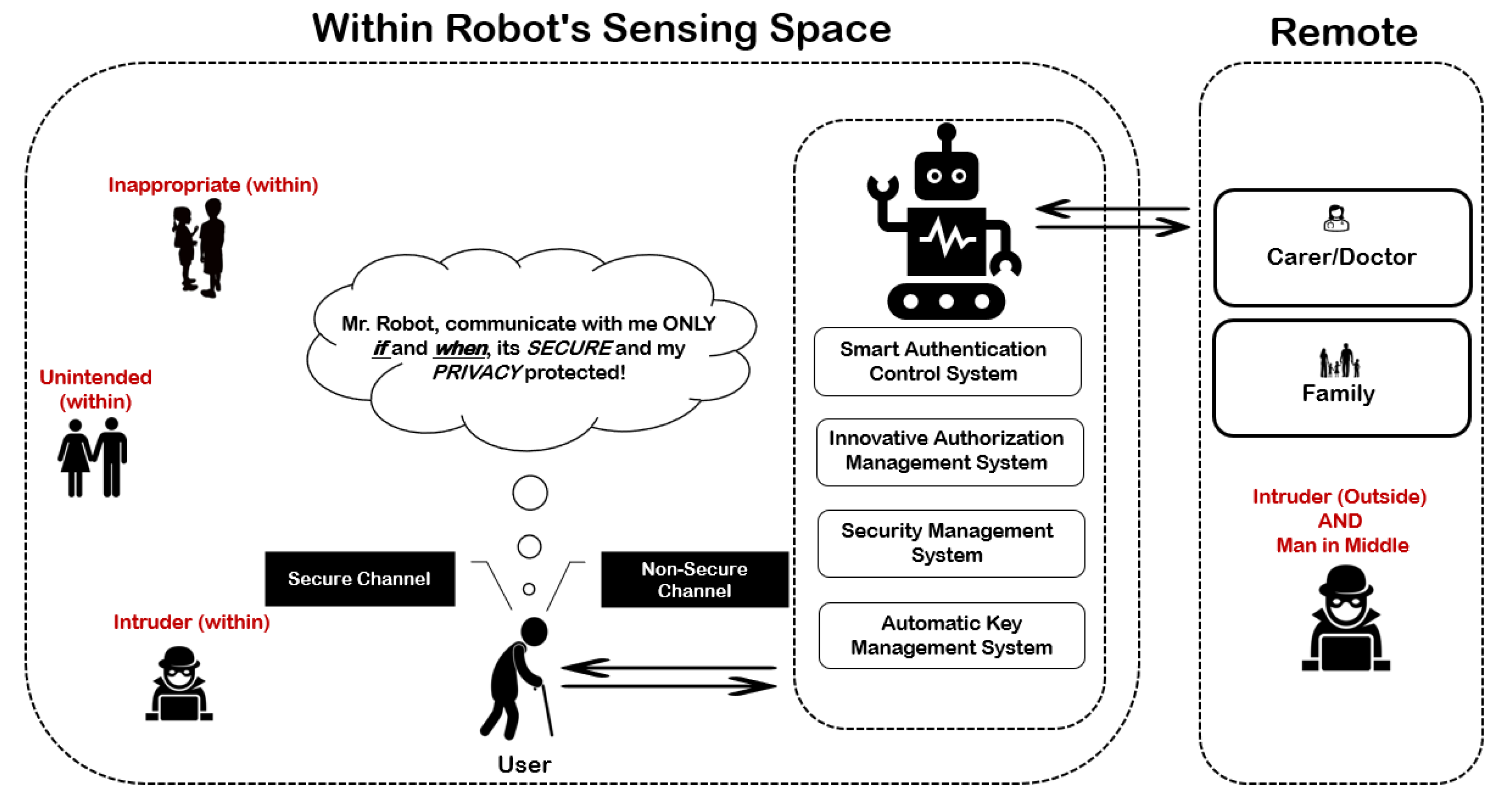
5. Security and Privacy Threat Modelling
5.1. Threat Modelling of Single User Single AMRSys
5.2. Threat Modelling of Single User Single AMRSys with IoT
5.3. Threat Modelling of Multiuser Single AMRSys with IoT
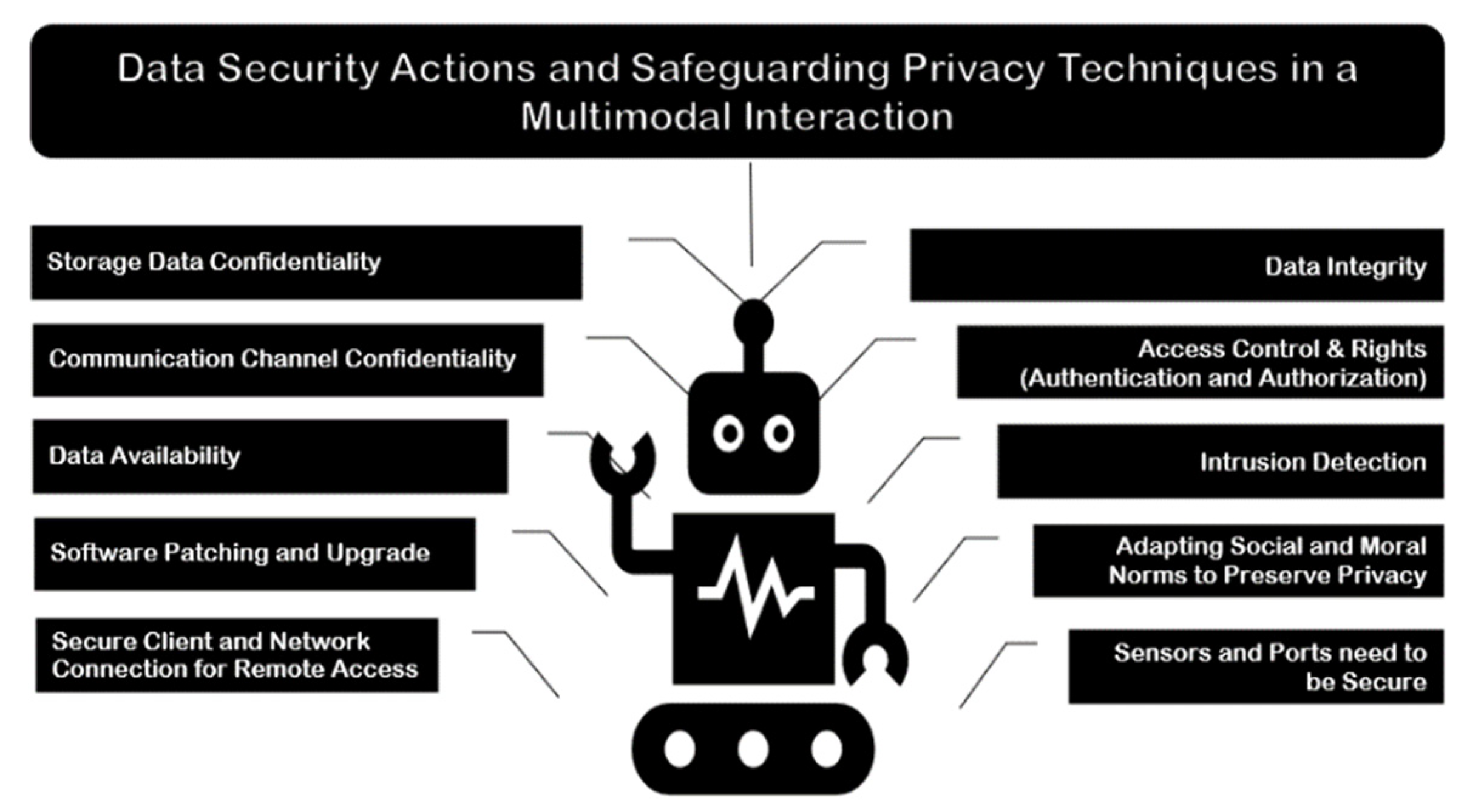
6. Security Parameters for Safeguarding and Protecting User’s Data in AMRSys
7. Security and Privacy Challenges and Limitations in AMRSys
7.1. Data Confidentiality of a Channel between the User and Robot
7.1.1. First, Via a Mobile App or Tablet App
7.1.2. Second, Using a GUI Attached to the Robot
7.1.3. Last, One-to-One Open Communication
7.2. Data Integrity and Availability
7.3. Unintended Data Disclosure Issue
7.4. Inappropriate Data Disclosure Issue
7.5. Intruders
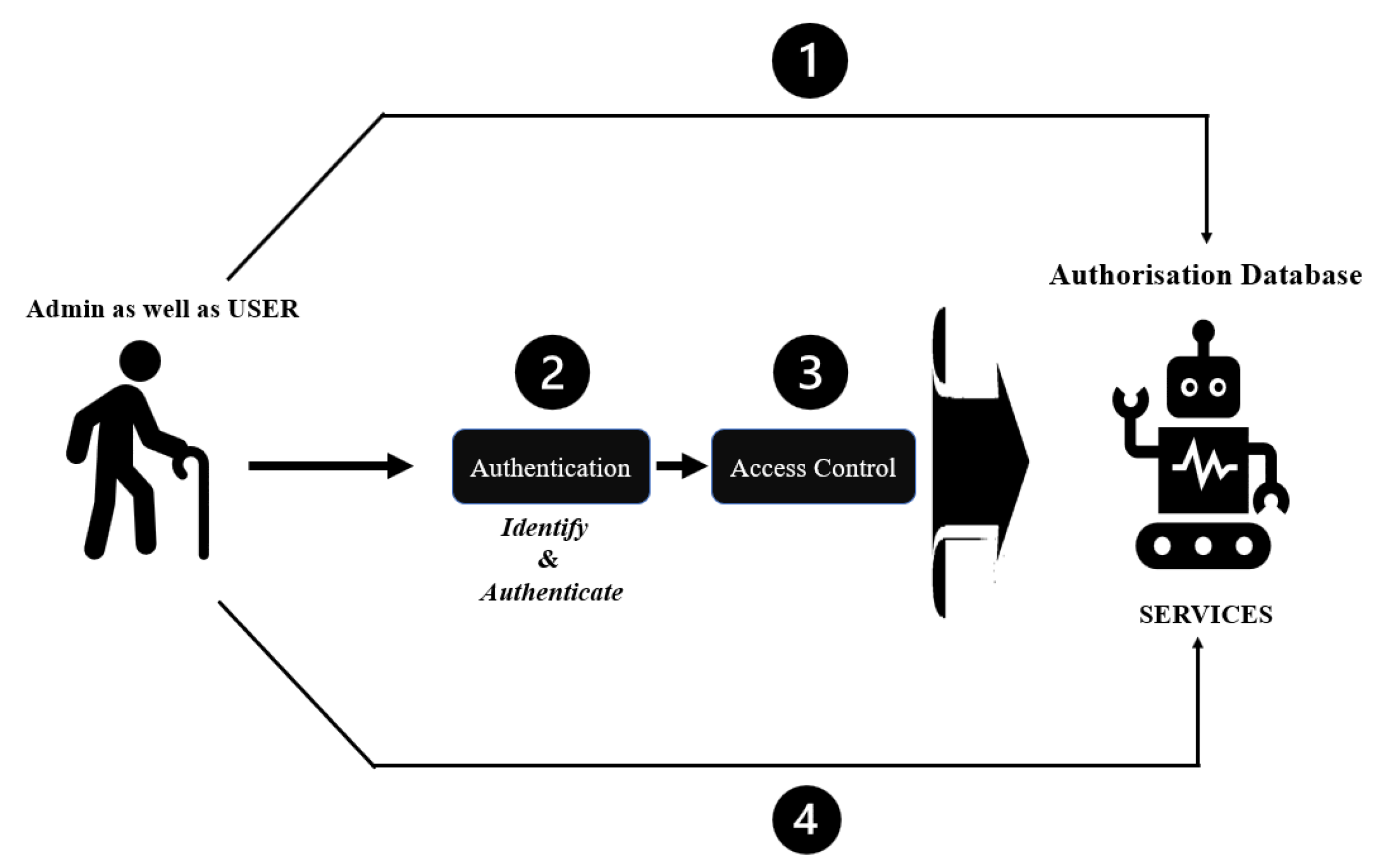
7.6. Access Control
7.6.1. Identification
7.6.2. Authentication
- Password-Based Authentication: This form of authentication is one of the most common and most popular forms of authentication. However, this technique invites multiple forms of attack e.g., phishing attacks, man-in-middle attacks, brute force attacks, dictionary attacks, credential stuffing attacks, keylogger attacks, etc.
- Multi-Factor Based Authentication: This technique is more secure than password-based authentication. This is because in this approach multiple independent methods or combinations of different platforms and techniques are used; e.g., a combination of password and authentication session keys, generated using an authenticator application or through a SMS mobile phone.
- Certificate-Based Authentication: This authentication technique uses digital certificates with keys (public and private) to authenticate the user or the system that has this certificate. These certificates are presented as a proof of authenticity of the user to the server, and the server confirms the genuineness of the certificate and the certificate-issuing authority through the association of the keys with its certificate.
- Token-Based Authentication: This technique allows users to enter their credentials to the server, and the server provides a unique encrypted random string (token) that the system recognizes. In the future, without using the credentials, this token generated with the credential of the user by the server is used for authenticating. However, whoever has this token can compromise the system. This method is safer than directly using a password; however, this method is also prone to different kinds of password-based attacks, as highlighted earlier under password-based authentication.
- Biometric Based Authentication: This form of authentication uses the biometric data of an individual to uniquely identify the user. This form of authentication has gained popularity because the biometric data is associated and stays with the individual and generally does not change (facial, fingerprint, voice, retina, gait, heart signal). Moreover, it does not involve memory recall or require technical skills from the user, so it can be used by any user to identify the individual to the system. However, one of its biggest drawbacks is that it can also be easily extracted, unlike a password, token, or certificate that can be memorized or stored (locally or remotely). Moreover, biometric data, such as fingerprint, voice, and facial data, can be extracted and replicated easily in this machine learning- and AI-powered 21st century.
7.6.3. Authorisation
7.7. Network Security and Proxy System
7.8. Storage Security
7.9. Scalability and System Constraints
7.10. User Constraint
8. Cyber Attack Assessment on AMRSys
9. Discussion
- (a)
- The robot may end up providing a service without being aware of the inappropriateness of the situation and presence of other people. Therefore, this requires continuous monitoring and decision making to learn and know when the environment is safe to provide a service.
- (b)
- Since it is authenticated once, and there is no mechanism to check the authenticity of the user continuously, other users may end up requesting a service.
9.1. CASE STUDY: Security Vulnerability of Alexa (Especial Focus on Authentication)
- -
- The system may wake up if the wake-up word is used during a conversation, without having the intention to wake up Alexa.
- -
- If the sound of a word is similar to the wake-up word, it may still detect it as a wake-up signal.
- -
- The system may not be recording, but it is listening; otherwise, how would the system detect a wake-up word or phrase? There is a provision to manage and control the voice recording; however, how many times and how often, would someone check if a recording was made accidentally or on purpose. Unless this is checked and managed regularly, sensitive information and data might be recorded by the system.
- -
- Once the system is live, the system has no idea of who can access or query. It does not monitor what is appropriate to age, situations, and scenarios. It will provide the service to anyone.
- -
- Anyone can wake up the system, simply by knowing the authenticating word, it means that anyone who can speak, can activate the system. Since the sound of a word is used to activate the process, the authentication mechanism is very insecure, mainly because it is easy and anyone within an audible vicinity can hear the code. If a voice recognition system is included, to detect and authorise the users, then knowing the sound of the passcode will not activate the service, unless the user is authorised and validated through a voice recognition authentication process.
- -
- The system has a mechanism to recall and reread the past recoded data from the system, so anyone can listen to past recorded queries if they know the wake-up word. This is very inappropriate, as it easily leaks private and sensitive information. Medical records and problems, legal issues, and private choices including financial status and records could be leaked.
9.2. CASE STUDY: Potential Security Solution for Authentication—Sophia the Robot
- -
- Eye contact and face visibility is poor.
- -
- The user is not speaking or responding, or cannot talk or cannot respond and turn his/her back away; it would not be able to detect the user.
- -
- If the user is blocked by a screen or object, or if the user is in another room, then even if the distance of separation is less, it would not be possible to detect and conduct continuous authentication through face and voice recognition.
10. Conclusions and Future Direction
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Golinelli, D.; Boetto, E.; Carullo, G.; Nuzzolese, A.G.; Landini, M.P.; Fantini, M.P. Adoption of digital technologies in health care during the COVID-19 pandemic: Systematic review of early scientific literature. J. Med. Internet Res. 2020, 22, e22280. [Google Scholar] [CrossRef] [PubMed]
- Anthony Jnr, B. Implications of telehealth and digital care solutions during COVID-19 pandemic: A qualitative literature review. Inf. Health Soc. Care. 2021, 46, 68–83. [Google Scholar] [CrossRef] [PubMed]
- Camp, N.; Lewis, M.; Hunter, K.; Johnston, J.; Zecca, M.; Di Nuovo, A.; Magistro, D. Technology used to recognize activities of daily living in community-dwelling older adults. Int. J. Environ. Res. Public Health 2021, 18, 163. [Google Scholar] [CrossRef] [PubMed]
- Getson, C.; Nejat, G. Socially Assistive Robots Helping Older Adults through the Pandemic and Life after COVID-19. Robotics 2021, 10, 106. [Google Scholar] [CrossRef]
- Pu, L.; Moyle, W.; Jones, C.; Todorovic, M. The Effectiveness of Social Robots for Older Adults: A Systematic Review and Meta-Analysis of Randomized Controlled Studies. Gerontologist 2019, 59, e37–e51. [Google Scholar] [CrossRef]
- Allaban, A.A.; Wang, M.; Padır, T. A Systematic Review of Robotics Research in Support of In-Home Care for Older Adults. Information 2020, 11, 75. [Google Scholar] [CrossRef] [Green Version]
- Bedaf, S.; Gelderblom, G.J.; De Witte, L. Overview and categorization of robots supporting independent living of elderly people: What activities do they support and how far have they developed. Assist. Technol. 2015, 27, 88–100. [Google Scholar] [CrossRef]
- Beuscher, L.M.; Fan, J.; Sarkar, N.; Dietrich, M.S.; Newhouse, P.A.; Miller, K.F.; Mion, L.C. Socially assistive robots: Measuring older adults’ perceptions. J. Gerontol. Nurs. 2017, 43, 35–43. [Google Scholar] [CrossRef]
- Conti, D.; Di Nuovo, S.; Di Nuovo, A. A brief review of robotics technologies to support social interventions for older users. Hum. Cent. Intell. Syst. Smart Innov. Syst. Technol. 2020, 189, 221–232. [Google Scholar]
- Cavallo, F.; Esposito, R.; Limosani, R.; Manzi, A.; Bevilacqua, R.; Felici, E.; Di Nuovo, A.; Cangelosi, A.; Lattanzio, F.; Dario, P. Robotic services acceptance in smart environments with older adults: User satisfaction and acceptability study. J. Med. Internet Res. 2018, 20, e264. [Google Scholar] [CrossRef]
- Čaić, M.; Mahr, D.; Oderkerken-Schröder, G. Value of social robots in services: Social cognition perspective. J. Serv. Mark. 2019, 33, 463–478. [Google Scholar] [CrossRef]
- Frennert, S.; Östlund, B. Seven matters of concern of social robots and older people. Int. J. Soc. Robot. 2014, 6, 299–310. [Google Scholar] [CrossRef]
- Sharkey, A.; Sharkey, N. We need to talk about deception in social robotics! Ethics Inf. Technol. 2021, 23, 309–316. [Google Scholar] [CrossRef]
- Char, D.S.; Shah, N.H.; Magnus, D. Implementing machine learning in health care—addressing ethical challenges. N. Engl. J. Med. 2018, 378, 981. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- May, R.; Denecke, K. Security, privacy, and healthcare-related conversational agents: A scoping review. Inform. Health Soc. Care. 2021, 1–17. [Google Scholar] [CrossRef] [PubMed]
- Lutz, C.; Schöttler, M.; Hoffmann, C.P. The privacy implications of social robots: Scoping review and expert interviews. Mob. Media Commun. 2019, 7, 412–434. [Google Scholar] [CrossRef]
- Meingast, M.; Roosta, T.; Sastry, S. August. Security and privacy issues with health care information technology. In 2006 International Conference of the IEEE Engineering in Medicine and Biology Society; IEEE: New York, NY, USA, 2006; pp. 5453–5458. [Google Scholar]
- United Nations; Department of Economic and Social Affairs; Population Division. World Population Prospects; Office of the Director, Population Division, United Nations, 2 United Nations Plaza, Room DC2-1950: New York, NY, USA, 2019. [Google Scholar]
- Lee, J.D.; See, K.A. Trust in Automation: Designing for Appropriate Reliance. Human Factors 2004, 46, 50–80. [Google Scholar] [CrossRef] [PubMed]
- Ben-Ari, M.; Mondada, F. Robots and their applications. In Elements of Robotics; Springer: Cham, Switzerland, 2018; pp. 1–20. [Google Scholar]
- Friis, D. Industrial robots–definition and classification. World Robot. 2016, 25–34. [Google Scholar]
- Hersh, M. Evaluation framework for ICT-based learning technologies for disabled people. Comput. Educ. 2014, 78, 30–47. [Google Scholar] [CrossRef]
- Kachouie, R.; Sedighadeli, S.; Khosla, R.; Chu, M.-T. Socially Assistive Robots in Elderly Care: A Mixed-Method Systematic Literature Review. Int. J. Hum.-Comput. Interact. 2014, 30, 369–393. [Google Scholar] [CrossRef]
- Khosla, R.; Chu, M.-T.; Khaksar, S.M.S.; Nguyen, K.; Nishida, T. Engagement and experience of older people with socially assistive robots in home care. Assist. Technol. 2019, 33, 57–71. [Google Scholar] [CrossRef]
- Oviatt, S. User-centered Modeling and evaluation of multimodal interfaces. Proc. IEEE. 2003, 91, 1457–1468. [Google Scholar] [CrossRef]
- Di Nuovo, A.; Broz, F.; Wang, N.; Belpaeme, T.; Cangelosi, A.; Jones, R.; Esposito, R.; Cavallo, F.; Dario, P. The multi-modal interface of Robot-Era multi-robot services tailored for the elderly. Intell. Serv. Robot. 2018, 11, 109–126. [Google Scholar] [CrossRef] [Green Version]
- Di Nuovo, A.; Varrasi, S.; Lucas, A.; Conti, D.; McNamara, J.; Soranzo, A. Assessment of Cognitive skills via Human-robot Interaction and Cloud Computing. J. Bionic Eng. 2019, 16, 526–539. [Google Scholar] [CrossRef]
- Chen, S.; Epps, J. Multimodal Coordination Measures to Understand Users and Tasks. ACM Trans. Comput. Interact. 2020, 27, 1–26. [Google Scholar] [CrossRef]
- Andries, M.; Simonin, O.; Charpillet, F. Localization of Humans, Objects, and Robots Interacting on Load-Sensing Floors. IEEE Sensors J. 2015, 16, 1026–1037. [Google Scholar] [CrossRef] [Green Version]
- Li, Q.; Liu, Y.; Meng, S.; Zhang, H.; Shen, H.; Long, H. A dynamic taint tracking optimized fuzz testing method based on multi-modal sensor data fusion. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 1–21. [Google Scholar] [CrossRef]
- Qu, Y.; Zhang, G.; Zou, Z.; Liu, Z.; Mao, J. Active Multimodal Sensor System for Target Recognition and Tracking. Sensors 2017, 17, 1518. [Google Scholar] [CrossRef] [Green Version]
- Bellotto, N.; Hu, H. A Bank of Unscented Kalman Filters for Multimodal Human Perception with Mobile Service Robots. Int. J. Soc. Robot. 2010, 2, 121–136. [Google Scholar] [CrossRef] [Green Version]
- Al-Qaderi, M.K.; Rad, A.B. A Multi-Modal Person Recognition System for Social Robots. Appl. Sci. 2018, 8, 387. [Google Scholar] [CrossRef] [Green Version]
- Krupke, D.; Steinicke, F.; Lubos, P.; Jonetzko, Y.; Gorner, M.; Zhang, J. Comparison of Multimodal Heading and Pointing Gestures for Co-Located Mixed Reality Human-Robot Interaction. In Proceedings of the 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Madrid, Spain, 1–5 October 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Tan, Y.; Sun, Z.; Duan, F.; Solé-Casals, J.; Caiafa, C.F. A multimodal emotion recognition method based on facial expressions and electroencephalography. Biomedical Signal Processing and Control. Biomed. Signal Processing Control. 2021, 70, 103029. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, B.; Zhang, C.; Xiao, Y.; Wang, M.Y. An EEG/EMG/EOG-based multimodal human-machine interface to real-time control of a soft robot hand. Front. Neurorobotics 2019, 13, 7. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gao, Q.; Liu, J.; Ju, Z. Hand gesture recognition using multimodal data fusion and multiscale parallel convolutional neural network for human–robot interaction. Expert Syst. 2021, 38, e12490. [Google Scholar] [CrossRef]
- Pasqui, V.; Saint-Bauzel, L.; Zong, C.; Clady, X.; Decq, P.; Piette, F.; Michel-Pellegrino, V.; El Helou, A.; Carré, M.; Durand, A.; et al. Projet MIRAS: Robot d’assistance à la déambulation avec interaction multimodale. IRBM 2012, 33, 165–172. [Google Scholar] [CrossRef]
- Mohammad, H.T. Multimodal Multisensor Attention Modeling. Ph.D. Thesis, NottingHam Trent University, Nottingham, UK. 2020. Available online: http://irep.ntu.ac.uk/id/eprint/41691 (accessed on 11 October 2021).
- Urquhart, L.; Reedman-Flint, D.; Leesakul, N. Responsible domestic robotics: Exploring ethical implications of robots in the home. J. Information, Commun. Ethic-Soc. 2019, 17. [Google Scholar] [CrossRef]
- Escalera, S.; Gonzalez, J.; Baro, X.; Shotton, J. Guest Editors’ Introduction to the Special Issue on Multimodal Human Pose Recovery and Behavior Analysis. IEEE Trans. Pattern Anal. Mach. Intell. 2016, 38, 1489–1491. [Google Scholar] [CrossRef]
- Umar, S.; Mosisa, E.K. A Survey on Evolution of Cognitive Robotics with Internet of Things. Int. J. Sci. Res. Sci. Eng. Technol. 2021, 8, 337–344. [Google Scholar] [CrossRef]
- Simoens, P.; Dragone, M.; Saffiotti, A. The Internet of Robotic Things. Int. J. Adv. Robot. Syst. 2018, 15, 172988141875942. [Google Scholar] [CrossRef]
- Harman, H.; Chintamani, K.; Simoens, P. Robot Assistance in Dynamic Smart Environments—A Hierarchical Continual Planning in the Now Framework. Sensors 2019, 19, 4856. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kamilaris, A.; Botteghi, N. The penetration of Internet of Things in robotics: Towards a web of robotic things. J. Ambient Intell. Smart Environ. 2020, 12, 491–512. [Google Scholar] [CrossRef]
- Cesar, C.; Lucas, A. Hacking Robots Before Skynet. IOActive Website 2017, 1–17. [Google Scholar]
- Kim, T.; Kang, B.; Rho, M.; Sezer, S.; Im, E.G. A Multimodal Deep Learning Method for Android Malware Detection Using Various Features. IEEE Trans. Inf. Forensics Secur. 2018, 14, 773–788. [Google Scholar] [CrossRef] [Green Version]
- Wachter, S.; Mittelstadt, B.; Floridi, L. Transparent, explainable, and accountable AI for robotics. Sci. Robot. 2017, 2, eaan6080. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Pilkington, M. Blockchain Technology: Principles and Applications. In Research Handbook on Digital Transformations; Xavier, F., Zhegu, O.M., Eds.; Edward Elgar Publishing: London, UK, 2015; pp. 1–39. [Google Scholar]
- Peck, M.E. Blockchains: How they work and why they’ll change the world. IEEE Spectr. 2017, 54, 26–35. [Google Scholar] [CrossRef]
- Shakir, M.; Aijaz, A. IoT, Robotics and Blockchain: Towards the Rise of a Human Independent Ecosystem. 2018. Available online: https://www.comsoc.org/publications/ctn/iot-robotics-and-blockchain-towards-rise-human-independent-ecosystem (accessed on 11 October 2021).
- Haden, C.; Amirabdollahian, F. A Call for Stronger Privacy Protections to Promote the Development of Ethical Domestic Robots. 2021, pp. 31–32. Available online: https://doi.org/10.31256/Gy2Wm9H (accessed on 11 October 2021).
- Bourimi, M.; Tesoriero, R.; Villanueva, P.G.; Karatas, F.; Schwarte, P. Privacy and Security in Multi-modal User Interface Modeling for Social Media. In Proceedings of the 2011 IEEE Third International Conference on Privacy, Security, Risk and Trust and 2011 IEEE Third International Conference on Social Computing, Boston, MA, USA, 9–11 October 2011; pp. 1364–1371. [Google Scholar] [CrossRef]
- Wei, F.; Zeadally, S.; Vijayakumar, P.; Kumar, N.; He, D. An Intelligent Terminal Based Privacy-Preserving Multi-Modal Implicit Authentication Protocol for Internet of Connected Vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 3939–3951. [Google Scholar] [CrossRef]
- Aditya, U.S.; Singh, R.; Singh, P.K.; Kalla, A. A Survey on Blockchain in Robotics: Issues, Opportunities, Challenges and Future Directions. J. Netw. Comput. Appl. 2021, 196, 103245. [Google Scholar] [CrossRef]
- Henson, V.; Henderson, R. Guidelines for using compare-by-hash. Comput. Sci. 2005, 1–14. [Google Scholar]
- De Leon, D.C.; Stalick, A.Q.; Jillepalli, A.A.; Haney, M.A.; Sheldon, F.T. Blockchain: Properties and misconceptions. Asia Pac. J. Innov. Entrep. 2017, 11, 286–300. [Google Scholar] [CrossRef]
- Yaacoub, J.P.A.; Noura, H.N.; Salman, O.; Chehab, A. Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. Int. J. Inf. Secur. 2021, 21, 115–158. [Google Scholar] [CrossRef] [PubMed]
- Mohanta, B.K.; Jena, D.; Panda, S.S.; Sobhanayak, S. Blockchain technology: A survey on applications and security privacy challenges. Internet Things 2019, 8, 100107. [Google Scholar] [CrossRef]
- Wüst, K.; Gervais, A. Do you need a blockchain? In 2018 Crypto Valley Conference on Blockchain Technology (CVCBT); IEEE: Piscataway Township, NJ, USA, 2018; pp. 45–54. [Google Scholar]
- Leonardos, S.; Reijsbergen, D.; Piliouras, G. Presto: A systematic framework for blockchain consensus protocols. IEEE Trans. Eng. Manag. 2020, 67, 1028–1044. [Google Scholar] [CrossRef]
- CESG. Information Security Arm of GCHQ. Common Cyber Attacks: Reducing the Impact. Online report by: GCHQ and Cert-UK. 2015. Available online: https://www.ncsc.gov.uk/guidance/white-papers/common-cyber-attacks-reducing-impact (accessed on 11 October 2021).
- Velásquez, I.; Caro, A.; Rodríguez, A. Authentication schemes and methods: A systematic literature review. Inf. Softw. Technol. 2018, 94, 30–37. [Google Scholar] [CrossRef]
- Amin, R.; Gaber, T.; ElTaweel, G.; Hassanien, A.E. Biometric and traditional mobile authentication techniques: Overviews and open issues. In Bio-Inspiring Cyber Security and Cloud Services: Trends and Innovations; Springer: Berlin/Heidelberg, Germany, 2014; pp. 423–446. [Google Scholar]
- Enamamu, T.; Otebolaku, A.; Marchang, J.; Dany, J. Continuous m-Health data authentication using wavelet decomposition for feature extraction. Sensors 2020, 20, 5690. [Google Scholar] [CrossRef] [PubMed]
- IBM. Available online: https://www.ibm.com/uk-en/security/data-breach (accessed on 10 October 2021).
- IBM. Reported on 2017 and Updated in 2020 by Anna Gerber and Satwik Kansal. Available online: https://developer.ibm.com/articles/iot-top-10-iot-security-challenges/ (accessed on 11 October 2021).
- Marchang, J.; Ibbotson, G.; Wheway, P. Will blockchain technology become a reality in sensor networks? In 2019 Wireless Days (WD); IEEE: Manchester, UK, 2019; pp. 1–4. [Google Scholar]
- Warren, S.D.; Louis, D. Brandeis. The right to privacy. In Harvard Law Review 4:5; 1890; pp. 193–220. [Google Scholar]
- Ferdinand, D.S. Privacy and Social Freedom; Cambridge University Press: Cambridge, UK, 1992. [Google Scholar]
- UN, Article 12. Available online: www.un.org (accessed on 20 November 2021).
- GDPR. Available online: https://gdpr.eu/data-privacy/ (accessed on 21 December 2021).
- Ingham, M.; Marchang, J.; Bhowmik, D. IoT security vulnerabilities and predictive signal jamming attack analysis in LoRaWAN. IET Inf. Secur. 2020, 14, 368–379. [Google Scholar] [CrossRef] [Green Version]
- BBC. Reported on 13 August 2020. Available online: https://www.bbc.co.uk/news/technology-53770778 (accessed on 1 December 2021).
- Lentzsch, C.; Shah, S.J.; Andow, B.; Degeling, M.; Das, A.; Enck, W. Hey Alexa, is this Skill Safe? Taking a Closer Look at the Alexa Skill Ecosystem. In Proceedings of the 28th Annual Network and Distributed System Security Symposium (NDSS 2021). The Internet Society, San Diego, CA, USA, 21–25 February 2021. [Google Scholar]
- Independent. Reported 23 October 2021. Available online: https://www.independent.co.uk/life-style/gadgets-and-tech/alexa-amazon-echo-voice-recordings-b1943527.html (accessed on 1 December 2021).
- Amazon. Available online: https://developer.amazon.com/en-GB/alexa (accessed on 17 November 2021).
- Hanson, R. Spphia. Available online: https://www.hansonrobotics.com/sophia/ (accessed on 21 December 2021).
- Bah, S.M.; Ming, F. An improved face recognition algorithm and its application in attendance management system. Array 2020, 5, 100014. [Google Scholar] [CrossRef]





| Region | Number of Persons Aged 65 or Over in 2019 (Millions) | Number of Persons Aged 65 or Over in 2050 (Millions) | Percentage Change between 2019 and 2050 |
|---|---|---|---|
| World | 702.9 | 1548.9 | 120 |
| Sub-Saharan Africa | 31.9 | 101.4 | 218 |
| Northern Africa and Western Asia | 29.4 | 95.8 | 226 |
| Central and Southern Asia | 119.0 | 328.1 | 176 |
| Eastern and South-Eastern Asia | 260.6 | 572.5 | 120 |
| Latin America and the Caribbean | 56.4 | 144.6 | 156 |
| Australia and New Zealand | 4.80 | 8.80 | 84 |
| Oceania, excluding Australia and New Zealand | 0.50 | 1.50 | 190 |
| Europe and Northern America | 200.4 | 296.2 | 48 |
| Requirements | Motivation | Current State | Possible Solution |
|---|---|---|---|
| Transparency | User would know what, why, and when actions are taken by the robot. | No known blockchain solutions exist for a multimodal robotic system, but a detailed survey about blockchain solutions in robotics is highlighted in [55]. There are lots of blockchain solutions in different applications, as provided by different authors in [49,50,51,57,59,60,61]. It could also be applied for a security solution in a multimodal robotic system. | A private blockchain with permission based access control mechanism is a potential solution. So that only authorised users can access the data, but it would be designed in such a way that the consensus technique and storage does not affect the blockchain network performance. The design would consider the block storage mechanism, data trasmission rate, computation power requirement for block update, and validation process and participation of nodes during consensus to improve efficiency and reduce overheads. |
| Security and Privacy Threat Modelling Framework | To understand methods and means of attack and to protect user’s data and privacy. | The authors of [46] explored the vulnerabilities of robots, but no security framework or solution was designed. | The threat model differs depending on the environment, presence of users, local or remote access, and the presence of intruders or unauthorised users. Therefore, secure frameworks would be develeoped in such a way that the robot communicates with the users if and only if the user’s privacy is protected and the enviroment is safe and channel secure. |
| Channel Security | Avoid data leakage | There are no known solutions for an interative or multimodal robotic system because audible conversation between the user and robot cannot be encrypted. Transmission using technology such as a tablet, internet, phone etc. can be secured by using any standard data encryption techniques such as AES and RSA; but note that DES is vulnerable and not secure. DES has been depreciated by the NIST since 2017. | User and assistive robot communication should be secured. However, it would be impoossible to secure all the channels, e.g., the verbal conversation, signals, and signs in presence of other users. Therefore, the robot should know what to do and what to say and when to say it, or when to provide the service (in other words teaching the robot to behave in such scenario may be the best solution to secure data and preserve user’s privacy). If technology is used to communicate with assistive multimodal robots then this can be secured easily using any standard encryption techniques, but the method used should not degrade the robot’s performance and response time. |
| Data Integrity and Avalability | To avoid non-repudiation and tampering. Detect and protect from attacks to increase data availability etc. | Secure standard hashing algorithms should be used like SHA2, SHA3 etc. Because hashing like SHA0, MD4, MD5 are no longer secure, so it should be avoided [56], even SHA1 is no longer secure, since hash collision attack was found by Google (https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html, accessed on 12 January 22) recently. Authors of [58] conduct a systematic review paper on robotic attacks, counter-measures and recommendations but not related to multimodal security system. | No new mechsnisms for data integrity would be developed, but the most effective mechanisms would be explored and incorporated in a blockchain solution. A novel approach of an efficient integrity detecting technique would be developed within a merkle tree of a blockchain system, so that any attempt at tampering is self-healing within a node. This would avoid invoking other nodes or devices for approval or concensus when changes within a block take place after it is created and validated. This approach would revert any changes safely to the original state of the block. Such an approach will improve the effiency of the lockchain system and reduce energy consumption and computation power. |
| Unintended, Inappropriate and Intruder | To protect user’s data and safeguard user’s privacy. | There is no known solution for multimodal assistive robotic system. Even the existing interactive Alexa system doesn’t differentiate the users be it authorised user or unauthorised users as long as the wake up code word is known. If wake up code word is considered as an authentication then probably this is the weakest known authentication technique. The Alexa system doesn’t successfully differentate between the sounds of “Alixa, Alexsha, Alisha”. | The interactive robotic system should have strong access control mechanisms to uniquely identify authentic users, and it should be aware of the presence of others and provide the services to the user only at an appropriate time and place. It should also know what is appropriate, e.g., an interactive system such as Alexa doe not know what is age appropriate; but it is very important to know what information to share with whom and whose presence is key to safeguard the user’s privacy and protect against data leakage. Protecting against intruders will involve monitoring the activity and requests from users. Intrusion detection and prevention mechanisms should be in place to safeguard against intruders. To avoid man-in-middle attacks during remote connection, a safe and secure IP security technique should be applied. |
| Access Control (Identification, authorisation, access rights etc) | So that only authentic users and authorised users have an access and have a mechanism to limit the access rights. | The existing access control and authentication techniques [62,63,64] will not be appropriate in most of cases, because assistive multimodal robotic systems are to be adopted by older, disabled, or physically challenged people. Moreover, without continuous authentication, the data and the privacy will be leaked easily because of the nature of the assistive robotic system’s multimodality. Using heart signals could be a potential solution to ensure a continuous and seamless authentication [65]. | Using traditional password-based, token, or passphrase authentication may be challenging to use for older people and disabled individuals. It would also be hard to adopt if biometric authentications such as a fingerprint is used. Moroever, one time authentication would leave the robotic system open from attacks, as an Alexa waiting for a request once it wakes up. Therefore, a continuous and a seamless authentication mechnism needs to be developed so that the older, disabled, or physically challenged individuals can use the system without any worries about leaving the system open for attacks. In addition, the continuous authentication process should use no, or minimal, user knowledge or remembering capacity, so that its seamless and easy to adopt. Moreover, the input factors for the authentication should be multi-factor, accurate, reliable, and consistent, so that they d not fail when the user’s heath condition changes, e.g., sick or not well. |
| Network and Storage Security | So that remote access, storage do not leak user data. | During the remote access, available standard IPSec security mechanisms would be adopted, and to protect the robotic system, a proxy system would be in place. In addition, storage security e.g., encryption is available; however, there is no mechanism to protect from tampering, deletion, etc., by attackers or unintentional actions by authentic users, etc. | A private permission based blockchain system would be designed. It would be designed in such a way that the blocks will not hold the data, but only parameters necessary to detect and identify any changes to the actual data, so that the resource hungry blockchain does not degrate the robotic performance. Moreover, the storage framework should not lead to a single point failure either. |
| Scalability, user and system constraints | So that the assistive robotic system can serve multiple users, performance does not degrade, overheads are low, and reponse time is sensitive. | Blockchains are resource hungry in nature, but Cardano (https://whitepaper.io/coin/cardano, accessed on 12 January 22) and Decentraland (https://decentraland.org/, accessed on 12 January 22)-based solutions for NFT may be the way forward, to make the blockchain network light and efficient. | This approach would adopt existing techniques, but methods have to be developed in such a way that the system is easily adoptable and usable. It should also be easy to integrate with the assistive robotic system, so that the overheads do not degrade the response time and performance of the robotic system. Moroever, the data should be stored encrypted, and visibility should be controlled based on the needs and rights of the users and the third party service providers, such as the engineer, nurse, doctors etc. |
| Type | Ease of Adoption | Ease of Implementation | Cost and Advantage (Adv) Disadvantage (Disadv) | Security Level | |||
|---|---|---|---|---|---|---|---|
| Normal Individual (It Is Easy to Adopt) | With Health Issues | ||||||
| Have Physical Condition (It Is Easy to Adopt) | Have Mental Condition (It Is Easy to Adopt) | ||||||
| Password | YES | YES, if user can remember and enter otherwise, NO | NO | YES, but challenging for serious physical and mental health issues. | LOW Adv: Change it anytime Disadv: Need to remember | LOW, if easy common and short passwords are used and if not changed for long time. | |
| Multi-Factor | YES | YES, if user have input source, otherwise NO | NO | YES, if the right system and devices are available for the multi-factor, but challenging for physically and mentally challenged people. | LOW Adv: Use of different medium. Disadv: Need to remember some factor. | HIGH, if the second factor uses authentication app or email. SMS is not secure. | |
| Certificate | YES | YES | YES | YES, since it is digitally stored. | LOW Adv: Can be updated any time. Disadv: User doesn’t remember or possesses it, only in the system. | HIGH, but authenticating user may be challenging | |
| Token | YES | YES, if user has hands, mouth to input, otherwise NO | NO | YES, but impossible or challenging to use for physically and mentally challenged people. | LOW Adv: New token can be created. Disadv: User must remember. | LOW, it involves possessing or remembering the token. | |
| Biometric | Facial | YES | YES | YES | NO, a facial recognition app is required and a camera is necessary. | EXPENSIVE Adv: No need to remember. Disadv: Cannot change. | HIGH, if physically present and 3D live aspect is taken into account, otherwise it is not. |
| Finger- | YES | YES, if the user has fingers, otherwise NO | YES, if the user has fingers, otherwise NO | NO, biometric finger print reader and app is required. | EXPENSIVE Adv: No need to remember. Disadv: Cannot change and left everywhere we touch. | HIGH, if the user is present physically and if used with second factor authentication, otherwise NO. | |
| Voice | YES | YES, if the user is not mute and/or deaf. | NO, if the user is mute and or deaf. | NO, voice recorder and recognition app is required. | EXPENSIVE Adv: No need to remember unless a passcode is used. Disadv: Can be regenerated by someone. | HIGH, if the user is physically present, and a second factor is considered, otherwise AI can easily spoof the voice. | |
| Retina | YES | YES, if the user has eyes and is not blind, otherwise NO | YES, if the user has eyes and is not blind, otherwise NO | NO, scanner and recognition app is required. | EXPENSIVE Adv: No need to remember Disadv: Can be replicated and captured from external source. | HIGH, if the user is physically present and second factor authentication is taken into account, otherwise NO. | |
| Gait | YES | NO | NO | NO, recording and recognition app is required. | EXPENSIVE Adv: No need to remember. Disadv: Can be replicated or captured from external. | HIGH, if accompanied with second factor authentication. | |
| Heart- Signal | YES | YES | YES | NO, recording and recognition app is required. | EXPENSIVE Adv: No need to remember and not visible externally. Disadv: If signal is captured, it can be re-used. | HIGH, since it cannot be captured without physical contact or within close vicinity. | |
| Attack on AMRISys | Functionality of AMRISys | Control on the AMRISys | Its Impact |
|---|---|---|---|
| Confidentiality | Normal Function | No | Data would be made visible and available to a third party. The privacy of the user’s data would be compromised. |
| - Key hijack, | |||
| - Key compromise | |||
| - Certificate attack, | |||
| - Reconnaissance | |||
| Integrity | Normal Function | No | Data alteration, tampering, and modification. |
| - Non-repudiation, | |||
| - Digital signature attack | |||
| Availability | Partly Function | Yes | It can allow the system to operate or make it inactive indirectly. However, the attacks will not completely stop the robot from functioning. It will definitively affect the services. |
| - DoS, | |||
| - DDoS, | |||
| - Jamming, | |||
| - Spamming, | |||
| - Black hole, | |||
| - Worm hole, | |||
| - Sink hole etc. | |||
| Access Control | Functional | Yes | The authentication process and the authorisation and control of the system could be compromised. Unauthorised users will access the services and storage would be visible unless storage is secure. |
| - Dictionary attacks, | |||
| - Brute-force attack, | |||
| - Man-in-middle, | |||
| - Phishing, | |||
| - Keylogger attack, | |||
| - Password Spraying attack | |||
| Storage | Functional | No | Data corruption, alteration, deletion; data visibility and available to a third party. Moreover, unauthorised users will see the data. |
| - Storage account discovery, | |||
| - Data Deletion, | |||
| - Data Alteration or Modification | |||
| Services | Partly Functional | Yes | The services may stop functioning as intended. |
| - Malware, | |||
| - Viruses to induce a malfunction | |||
| Sensory | Partly Functional | Yes | If the sensory devices are replaced or replicated, the robotic system may end up collecting or sensing incorrect or invalid data or leak the data. It may even lead to data falsification. |
| - Replacement, | |||
| - Replication | |||
| - Tampering | |||
| Network | Functional | No | It may cause dysfunction in the network and even capture traffic, but the functionality of the MRISys may be affected. The remote connection and remote delivery of information would be disrupted. |
| - Attack on Proxy server, | |||
| - Man-in-middle attack, | |||
| - Routing attack, | |||
| - Media Access, | |||
| - ARP attack, | |||
| - Buffer overflow attack |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marchang, J.; Di Nuovo, A. Assistive Multimodal Robotic System (AMRSys): Security and Privacy Issues, Challenges, and Possible Solutions. Appl. Sci. 2022, 12, 2174. https://doi.org/10.3390/app12042174
Marchang J, Di Nuovo A. Assistive Multimodal Robotic System (AMRSys): Security and Privacy Issues, Challenges, and Possible Solutions. Applied Sciences. 2022; 12(4):2174. https://doi.org/10.3390/app12042174
Chicago/Turabian StyleMarchang, Jims, and Alessandro Di Nuovo. 2022. "Assistive Multimodal Robotic System (AMRSys): Security and Privacy Issues, Challenges, and Possible Solutions" Applied Sciences 12, no. 4: 2174. https://doi.org/10.3390/app12042174
APA StyleMarchang, J., & Di Nuovo, A. (2022). Assistive Multimodal Robotic System (AMRSys): Security and Privacy Issues, Challenges, and Possible Solutions. Applied Sciences, 12(4), 2174. https://doi.org/10.3390/app12042174







