Joint Hamming Coding for High Capacity Lossless Image Encryption and Embedding Scheme †
Abstract
:1. Introduction
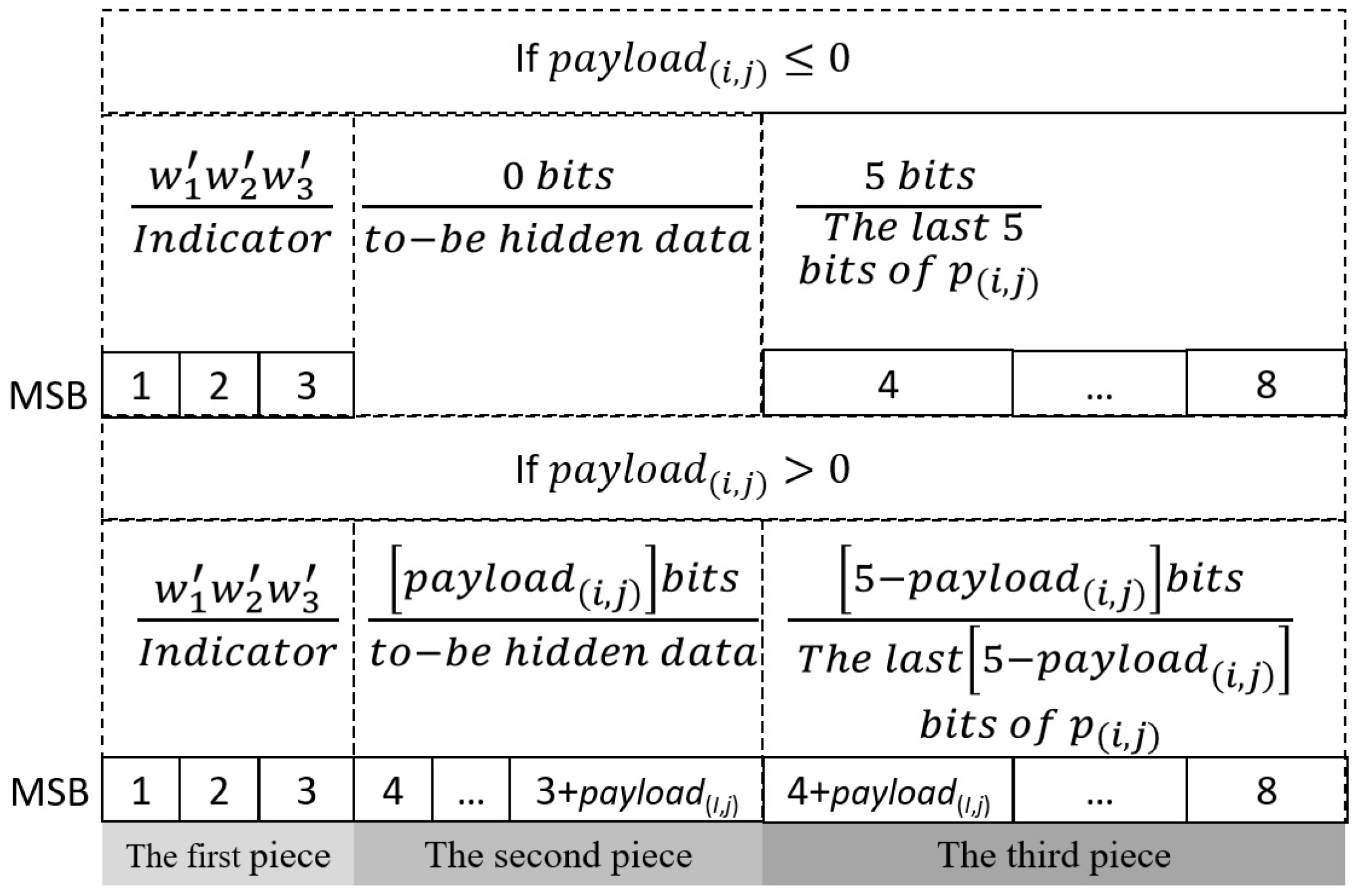
2. Proposed Scheme
2.1. Secret Embedding and Encryption Stage
2.2. Secret Extraction and Decryption Phases
| Algorithm 1 Recovering pseudo code |
|
3. Experimental Results
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Zhu, H.; Zhang, X.; Yu, H.; Zhao, C.; Zhu, Z. An image encryption algorithm based on compound homogeneous hyper-chaotic system. Nonlinear Dyn. 2017, 89, 61–79. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D logistic-modulated-sine-coupling-logistic chaotic map for image encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Zhu, H.; Dai, L.; Liu, Y.; Wu, L. A three-dimensional bit-level image encryption algorithm with Rubik’s cube method. Math. Comput. Simul. 2021, 185, 754–770. [Google Scholar] [CrossRef]
- Coatrieux, G.; Le Guillou, C.; Cauvin, J.M.; Roux, C. Reversible watermarking for knowledge digest embedding and reliability control in medical images. IEEE Trans. Inf. Technol. Biomed. 2008, 13, 158–165. [Google Scholar] [CrossRef]
- Lee, S.; Yoo, C.D.; Kalker, T. Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Trans. Inf. Forensics Secur. 2007, 2, 321–330. [Google Scholar] [CrossRef]
- Celik, M.U.; Sharma, G.; Tekalp, A.M.; Saber, E. Lossless generalized-LSB data embedding. IEEE Trans. Image Process. 2005, 14, 253–266. [Google Scholar] [CrossRef]
- Celik, M.U.; Sharma, G.; Tekalp, A.M. Lossless watermarking for image authentication: A new framework and an implementation. IEEE Trans. Image Process. 2006, 15, 1042–1049. [Google Scholar] [CrossRef]
- Cao, X.; Du, L.; Wei, X.; Meng, D.; Guo, X. High capacity reversible data hiding in encrypted images by patch-level sparse representation. IEEE Trans. Cybern. 2015, 46, 1132–1143. [Google Scholar] [CrossRef]
- Chen, K.; Chang, C.C. High-capacity reversible data hiding in encrypted images based on extended run-length coding and block-based MSB plane rearrangement. J. Vis. Commun. Image Represent. 2019, 58, 334–344. [Google Scholar] [CrossRef]
- Chen, Y.C.; Shiu, C.W.; Horng, G. Encrypted signal-based reversible data hiding with public key cryptosystem. J. Vis. Commun. Image Represent. 2014, 25, 1164–1170. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.S.; Wu, H.Y. An improved reversible data hiding in encrypted images using side match. IEEE Signal Process. Lett. 2012, 19, 199–202. [Google Scholar] [CrossRef]
- Huang, F.; Huang, J.; Shi, Y.Q. New framework for reversible data hiding in encrypted domain. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2777–2789. [Google Scholar] [CrossRef]
- Liao, X.; Shu, C. Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J. Vis. Commun. Image Represent. 2015, 28, 21–27. [Google Scholar] [CrossRef]
- Ma, K.; Zhang, W.; Zhao, X.; Yu, N.; Li, F. Reversible Data Hiding in Encrypted Images by Reserving Room before Encryption. IEEE Trans. Inf. Forensics Secur. 2013, 8, 553–562. [Google Scholar] [CrossRef]
- Puteaux, P.; Puech, W. An efficient MSB prediction-based method for high-capacity reversible data hiding in encrypted images. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1670–1681. [Google Scholar] [CrossRef] [Green Version]
- Qian, Z.; Zhang, X.; Feng, G. Reversible data hiding in encrypted images based on progressive recovery. IEEE Signal Process. Lett. 2016, 23, 1672–1676. [Google Scholar] [CrossRef]
- Qian, Z.; Zhang, X.; Wang, S. Reversible data hiding in encrypted JPEG bitstream. IEEE Trans. Multimed. 2014, 16, 1486–1491. [Google Scholar] [CrossRef]
- Qian, Z.; Zhang, X. Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans. Circuits Syst. Video Technol. 2015, 26, 636–646. [Google Scholar] [CrossRef]
- Wu, X.; Sun, W. High-capacity reversible data hiding in encrypted images by prediction error. Signal Process. 2014, 104, 387–400. [Google Scholar] [CrossRef]
- Xu, D.; Wang, R. Separable and error-free reversible data hiding in encrypted images. Signal Process. 2016, 123, 9–21. [Google Scholar] [CrossRef]
- Yi, S.; Zhou, Y. Binary-block embedding for reversible data hiding in encrypted images. Signal Process. 2017, 133, 40–51. [Google Scholar] [CrossRef]
- Yi, S.; Zhou, Y. Separable and reversible data hiding in encrypted images using parametric binary tree labeling. IEEE Trans. Multimed. 2019, 21, 51–64. [Google Scholar] [CrossRef]
- Yin, Z.; Abel, A.; Tang, J.; Zhang, X.; Luo, B. Reversible data hiding in encrypted images based on multi-level encryption and block histogram modification. Multimed. Tools Appl. 2017, 76, 3899–3920. [Google Scholar] [CrossRef]
- Yin, Z.; Xiang, Y.; Zhang, X. Reversible data hiding in encrypted images based on multi-MSB prediction and Huffman coding. IEEE Trans. Multimed. 2020, 22, 874–884. [Google Scholar] [CrossRef]
- Zhang, X. Reversible data hiding in encrypted image. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Zhang, X. Separable Reversible Data Hiding in Encrypted Image. IEEE Trans. Inf. Forensics Secur. 2012, 7, 826–832. [Google Scholar] [CrossRef]
- Zhang, W.; Ma, K.; Yu, N. Reversibility improved data hiding in encrypted images. Signal Process. 2014, 94, 118–127. [Google Scholar] [CrossRef]
- Zhang, X.; Qian, Z.; Feng, G.; Ren, Y. Efficient reversible data hiding in encrypted images. J. Vis. Commun. Image Represent. 2014, 25, 322–328. [Google Scholar] [CrossRef]
- Zhang, X.; Long, J.; Wang, Z.; Cheng, H. Lossless and reversible data hiding in encrypted images with public-key cryptography. IEEE Trans. Circuits Syst. Video Technol. 2015, 26, 1622–1631. [Google Scholar] [CrossRef]
- Zhang, W.; Wang, H.; Hou, D.; Yu, N. Reversible data hiding in encrypted images by reversible image transformation. IEEE Trans. Multimed. 2016, 18, 1469–1479. [Google Scholar] [CrossRef]
- Zheng, S.; Li, D.; Hu, D.; Ye, D.; Wang, L.; Wang, J. Lossless data hiding algorithm for encrypted images with high capacity. Multimed. Tools Appl. 2016, 75, 13765–13778. [Google Scholar] [CrossRef]
- Zhou, J.; Sun, W.; Dong, L.; Liu, X.; Au, O.C.; Tang, Y.Y. Secure reversible image data hiding over encrypted domain via key modulation. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 441–452. [Google Scholar] [CrossRef]
- Zhang, X.; Feng, G.; Ren, Y.; Qian, Z. Scalable coding of encrypted images. IEEE Trans. Image Process. 2012, 21, 3108–3114. [Google Scholar] [CrossRef]
- Dragoi, I.C.; Coltuc, D. On the security of reversible data hiding in encrypted images by MSB prediction. IEEE Trans. Inf. Forensics Secur. 2021, 16, 187–189. [Google Scholar] [CrossRef]
- Chen, Y.H.; Lin, P.Y. Integrated Hamming Coding Operation to Reversible Data Hiding Scheme for Encrypted Images. In Proceedings of the 22nd IEEE/ACIS International Fall Virtual Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD2021-Fall), Taichung, Taiwan, 24–26 November 2021. [Google Scholar]
- Greenwald, S.W. Matrix Multiplication with Asynchronous Logic Automata. Ph.D. Thesis, Massachusetts Institute of Technology, Cambridge, MA, USA, 2010. [Google Scholar]
- Puteaux, P.; Puech, W. EPE-based huge-capacity reversible data hiding in encrypted images. In Proceedings of the 2018 IEEE International Workshop on Information Forensics and Security (WIFS), Hong Kong, China, 11–13 December 2018; pp. 1–7. [Google Scholar]
- Puyang, Y.; Yin, Z.; Qian, Z. Reversible data hiding in encrypted images with two-MSB prediction. In Proceedings of the 2018 IEEE International Workshop on Information Forensics and Security (WIFS), Hong Kong, China, 11–13 December 2018; pp. 1–7. [Google Scholar]


| Label | Smooth Image | Complex Image | ||||
|---|---|---|---|---|---|---|
| Capacity | Code Length | Payload | Capacity | Code Length | Payload | |
| 0 | 0 | 3 | −3 | 1 | 3 | −2 |
| 1 | 3 | 3 | 0 | 2 | 3 | −1 |
| 2 | 4 | 3 | 1 | 3 | 3 | 0 |
| 3 | 5 | 3 | 2 | 4 | 3 | 1 |
| 4 | 6 | 3 | 3 | 5 | 3 | 2 |
| 5 | 7 | 3 | 4 | 6 | 3 | 3 |
| 6 | 8 | 3 | 5 | 7 | 3 | 4 |
| 7 | 8 | 3 | 5 | 7 | 3 | 4 |
| Label | Lena ( = − 1, = 1) | ( = 0, = 0) | Jetplane ( = 0, = − 1) | |||
|---|---|---|---|---|---|---|
| Distribution | Payload | Distribution | Payload | Distribution | Payload | |
| −1 | 1023 | − | 1023 | − | 1023 | − |
| 0 | 8200 7493 | −24,600 −22,479 | 34,591 | −69,182 | 4457 9990 | −13,371 −29,970 |
| 1 | 18,984 | 0 | 22,574 | −22,574 | 8427 | 0 |
| 2 | 28,742 | 28,742 | 40,173 | 0 | 16,430 | 16,430 |
| 3 | 47,653 | 95,306 | 44,464 | 44,464 | 26,250 | 52,500 |
| 4 | 53,002 | 159,006 | 41,394 | 82,788 | 33,346 | 100,038 |
| 5 | 42,304 | 169,216 | 32,230 | 96,690 | 36,543 | 146,172 |
| 6 | 25,060 | 125,300 | 20,949 | 83,796 | 36,952 | 184,760 |
| 7 | 29,683 | 148,415 | 12,033 12,713 | 48,132 50,852 | 88,726 | 443,630 |
| Total | - | 677,883 | - | 313,943 | - | 899,166 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, Y.-H.; Lin, P.-Y.; Wu, H.-P.; Chen, S.-H. Joint Hamming Coding for High Capacity Lossless Image Encryption and Embedding Scheme . Appl. Sci. 2022, 12, 1966. https://doi.org/10.3390/app12041966
Chen Y-H, Lin P-Y, Wu H-P, Chen S-H. Joint Hamming Coding for High Capacity Lossless Image Encryption and Embedding Scheme . Applied Sciences. 2022; 12(4):1966. https://doi.org/10.3390/app12041966
Chicago/Turabian StyleChen, Yi-Hui, Pei-Yu Lin, Hsin-Pei Wu, and Shih-Hsin Chen. 2022. "Joint Hamming Coding for High Capacity Lossless Image Encryption and Embedding Scheme " Applied Sciences 12, no. 4: 1966. https://doi.org/10.3390/app12041966
APA StyleChen, Y.-H., Lin, P.-Y., Wu, H.-P., & Chen, S.-H. (2022). Joint Hamming Coding for High Capacity Lossless Image Encryption and Embedding Scheme . Applied Sciences, 12(4), 1966. https://doi.org/10.3390/app12041966






