Proactive Management of Requirement Changes in the Development of Complex Technical Systems
Abstract
Featured Application
Abstract
1. Introduction
- −
- Methods for holistic assessment of requirement change likelihood (exogenous and endogenous) and change impact (direct and subsequent).
- −
- Approaches to reduce the application effort of risk assessment without relying on datasets, which are unavailable in the context of proactive requirement change management (especially for dependency analysis).
- −
- Support to select proactive measures based on the requirement change risk.
- −
- RQ 1: How can the change risk of requirements be assessed in the early stages of developing complex technical systems?
- −
- RQ 1.1: How can requirement dependencies be identified and differentiated by change propagation behavior?
- −
- RQ 1.2: How can the endogenous and exogenous change likelihood of a requirement be assessed?
- −
- RQ 1.3: How can the collective change impact be assessed?
- −
- RQ 2: How can the selection of proactive measures for requirement changes be supported?
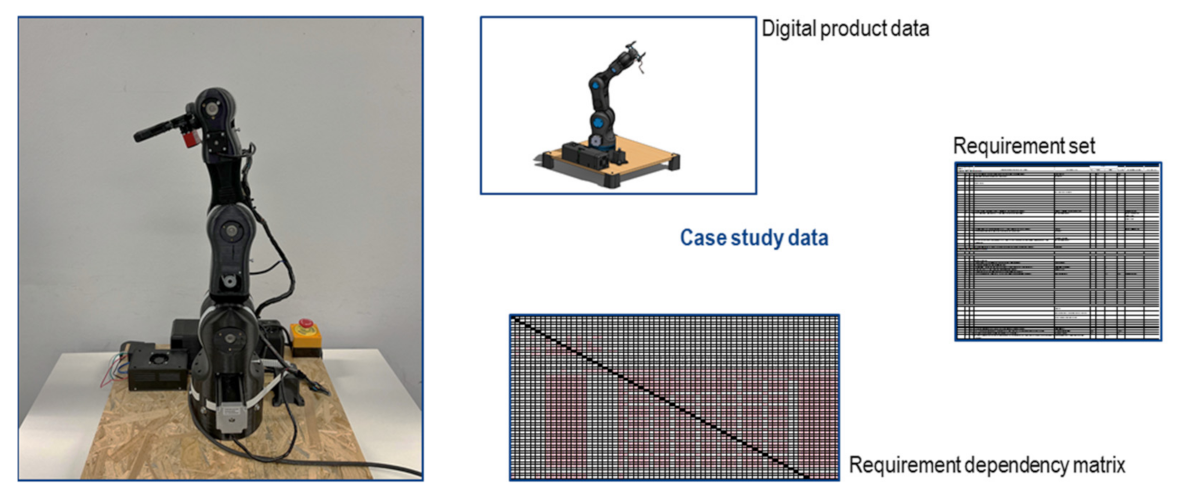
2. Materials and Methods
- Requirement elicitation (3 h, 8 participants: head of department, project leader, team leader, process owner, requirements engineer, developer and subject matter expert).
- Detailing and prioritization of requirements (2 h, 8 participants: see above).
- Definition of use cases and check for completeness of requirements (2 h, 2 participants: requirements engineer and process owner).
3. Method for Proactive Management of Requirement Changes
3.1. Success Criteria for the Method
3.2. Change Risk Assessment
3.2.1. Requirement Dependency Analysis
Pre-Training and Context-Specific Fine-Tuning
Data Preprocessing
Classification of Dependencies
Transformation of Results
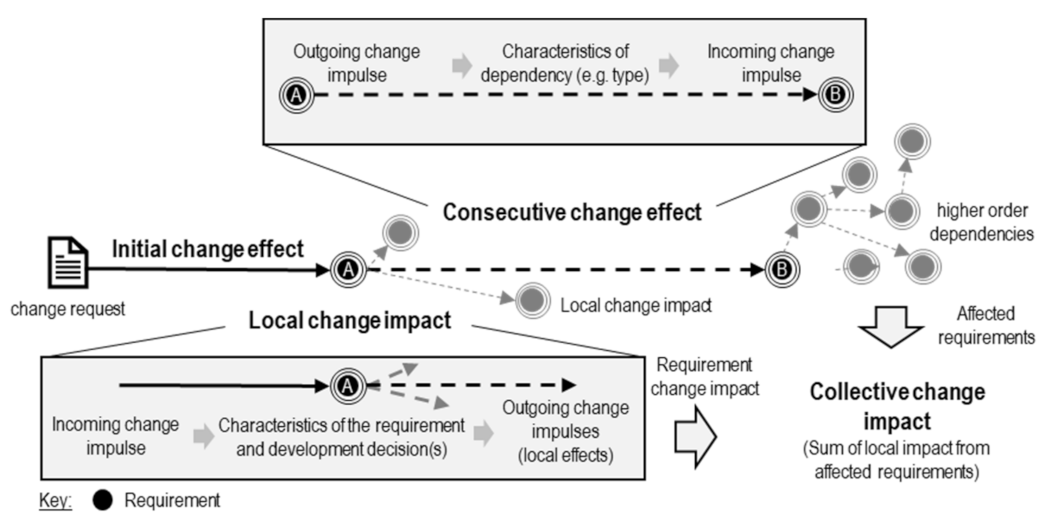
3.2.2. Requirement Change Impact Assessment
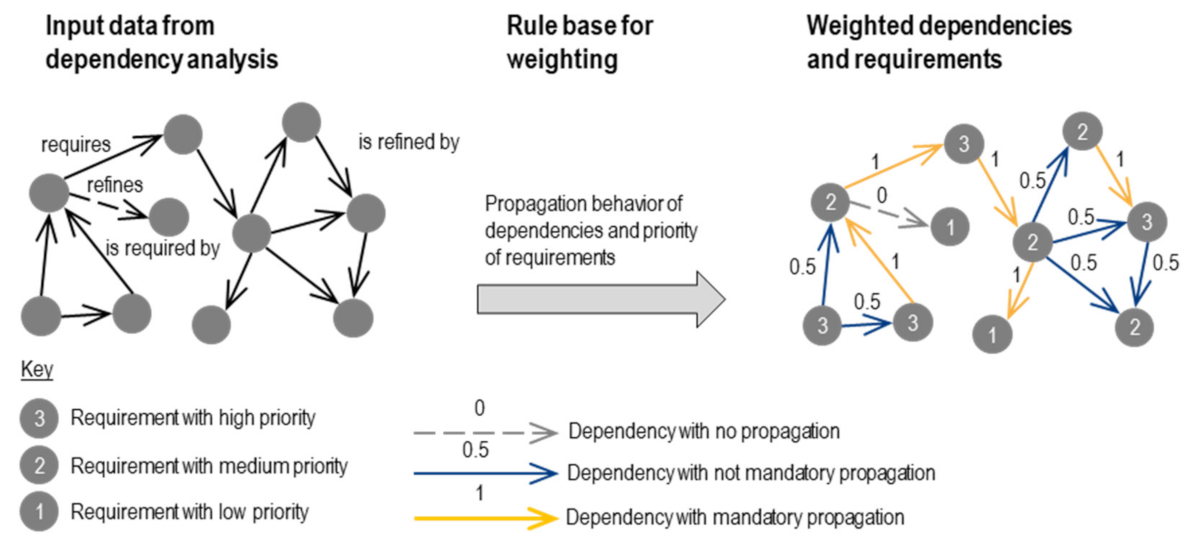
Weighting of Dependencies and Requirements
- Mandatory propagation behavior: requires, is required by and is refined by
- Not mandatory propagation behavior: positive/negative correlation
- No propagation behavior: refines, cost and value
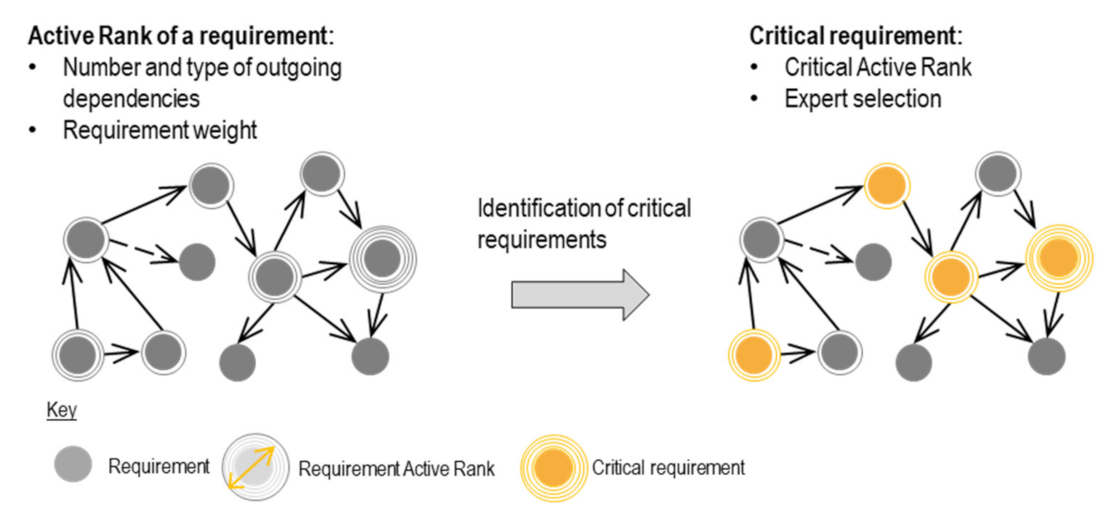
Analysis of Requirement Network
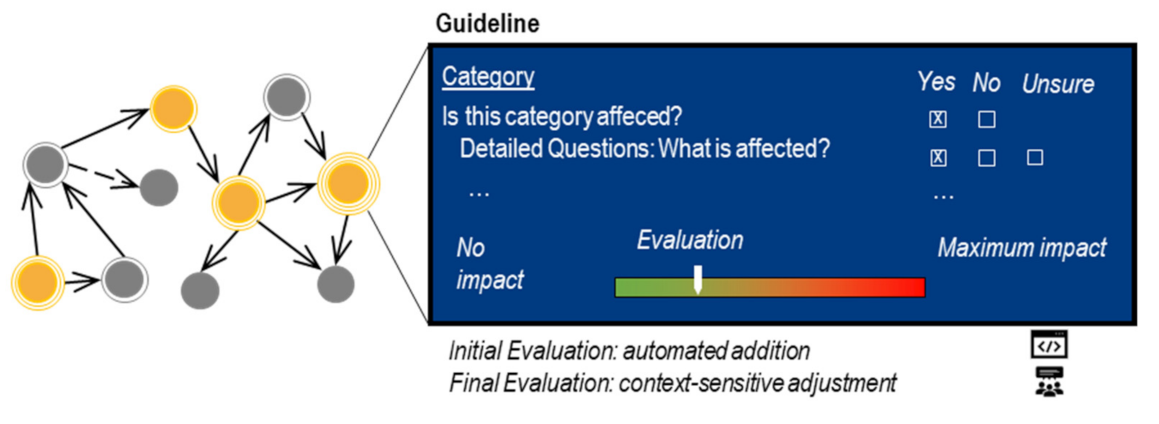
Expert Evaluation of the Collective Change Impact of a Requirement
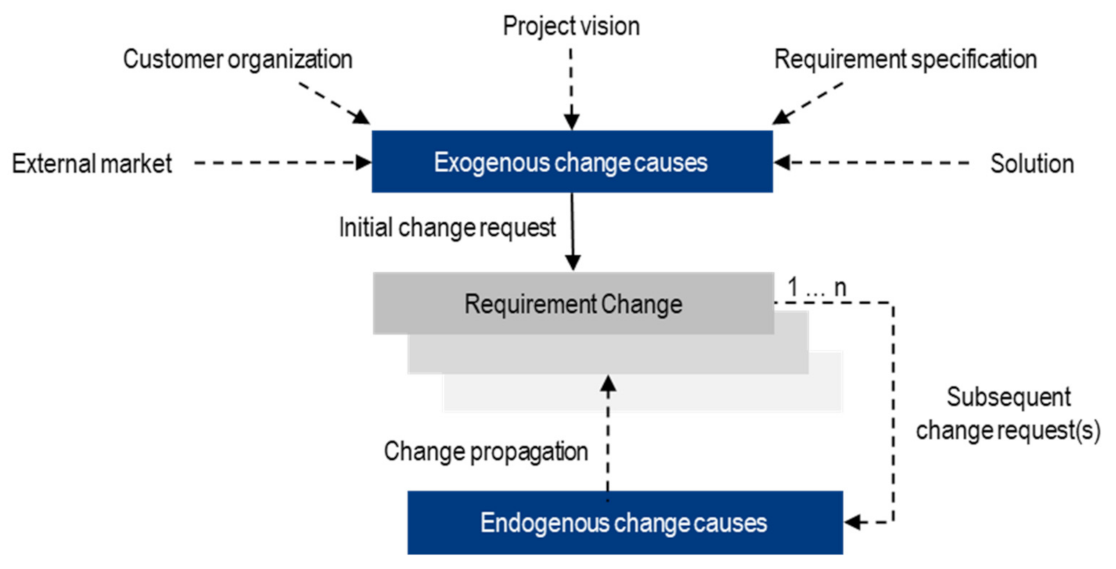
3.2.3. Requirement Change Likelihood
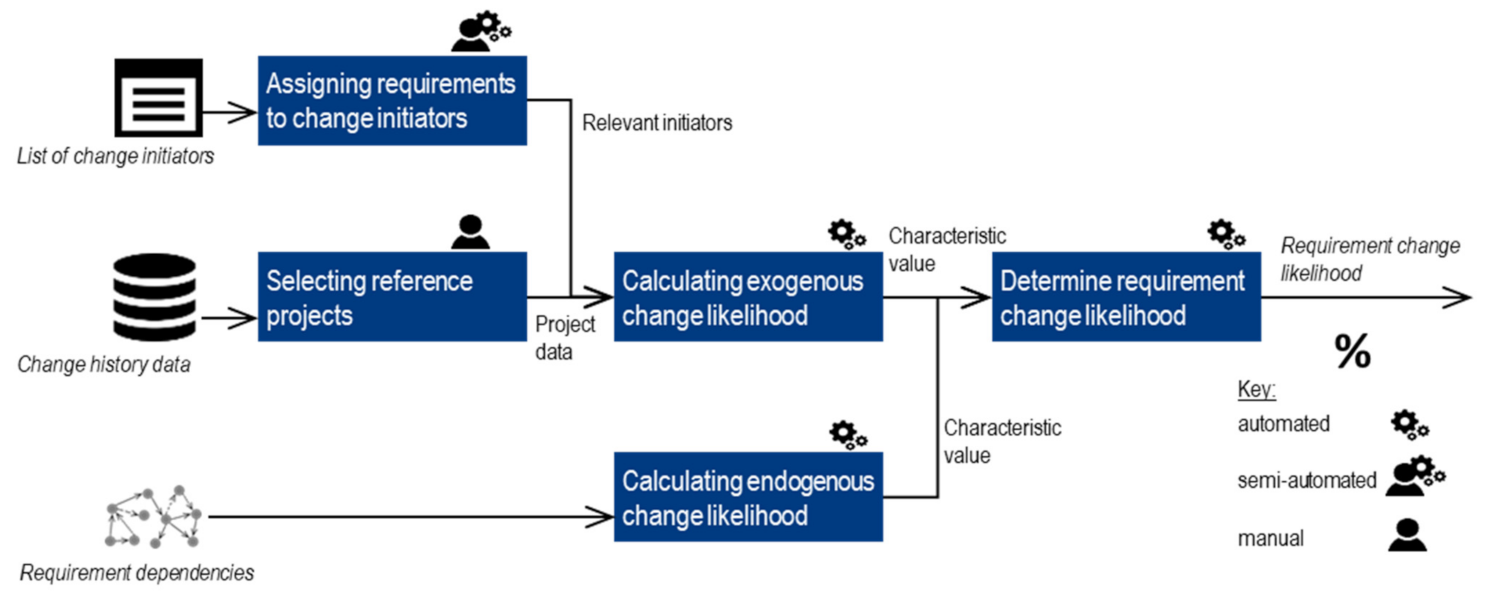
Exogenous Change Likelihood
- Assigning requirements to change initiators
- external market: politics (such as regulations), suppliers (such as market stability) and market including further stakeholders (such as response to competitors),
- customer organization(s): customer (such as strategy) and customer organizational structure (such as reorganization or hardware/software changes),
- project vision: business case (such as cost overrun), technology (such as new opportunity) and knowledge (such as a new stakeholder),
- requirement specification (such as increased understanding): requirements engineer and project leader,
- solution (such as design improvement): software development, hardware development and production.
- 2.
- Selecting reference projects
- 3.
- Calculating exogenous change likelihood
Endogenous Change Likelihood
Requirement Change Likelihood
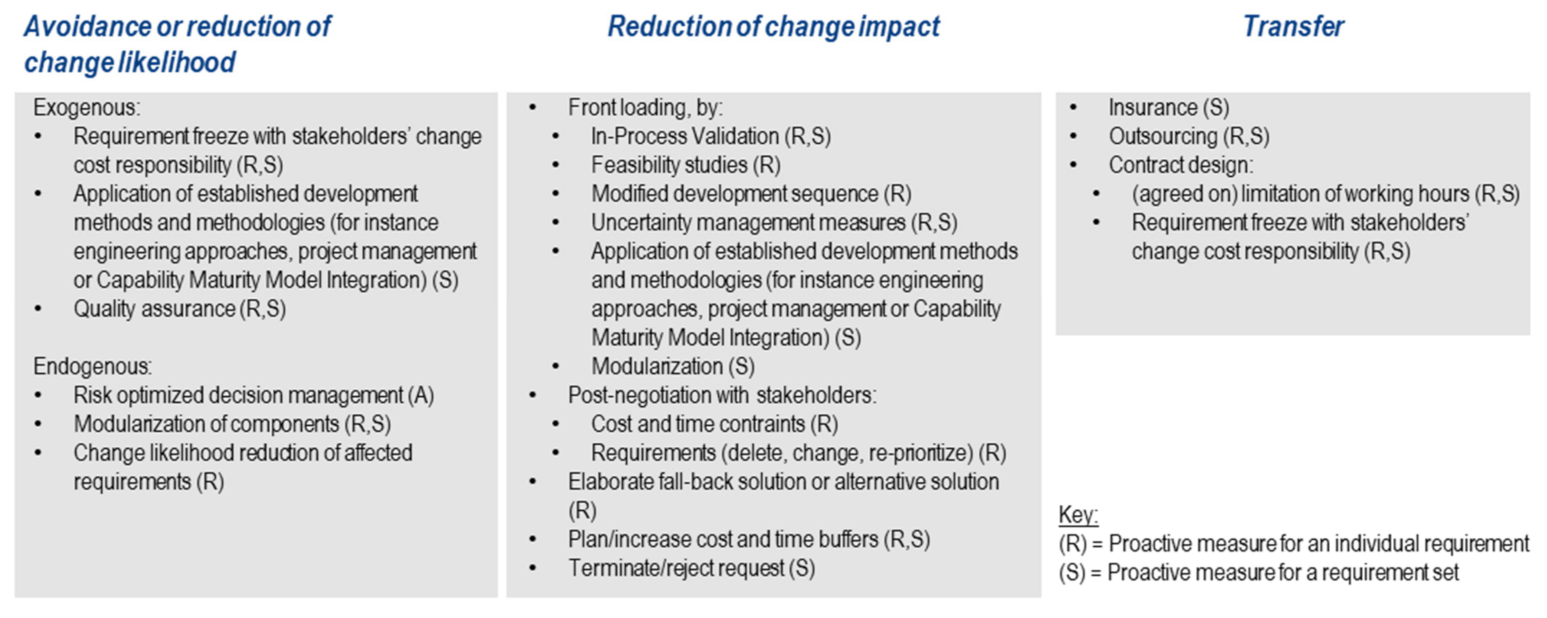
3.3. Selection of Proactive Measures
3.3.1. Prioritizing Requirements
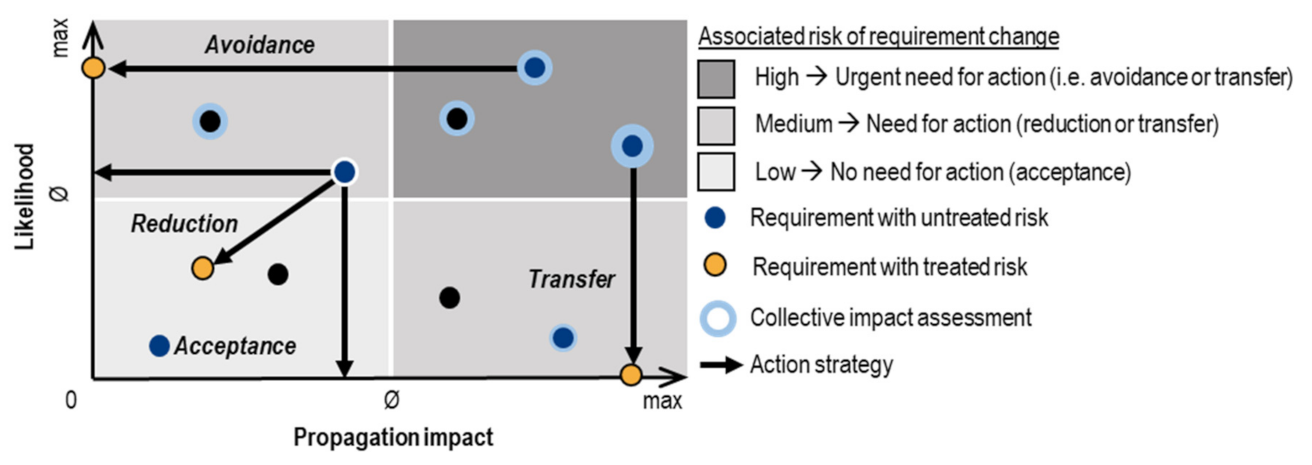
3.3.2. Definition of an Action Strategy
3.3.3. Selection of Proactive Measure
3.4. Software Prototype
4. Evaluation
4.1. Support Evaluation
4.1.1. Success Criteria SC-4: Analysis of Change Propagation
Internal Functional Testing
Validation Workshops with Industry Users [W8, 10 and 11]
4.1.2. Success Criteria SC-5: Analysis of Exogenous and Endogenous Change Likelihood
Internal Function Test
Validation Workshop with Industry Users [W9]
4.1.3. Success Criteria SC-6: Analysis of Collective Change Impact
Internal Functional Testing
Validation Workshop with Industry Users [W8 and 10]
4.1.4. Success Criteria SC-7: Selection of Requirement Specific Proactive Measures
Internal Functional Testing
Validation Workshop with Industry Users [W4, 5 and 11]
4.2. Application Evaluation
4.2.1. Input Success Criteria
Success Criterion SC-1: Processability of Interdisciplinary Requirements
Success Criterion SC-2: Processability of High Number of Requirements
Success Criterion SC-3: Processability of Regular Form of Documentation
4.2.2. Application Success Criteria
Success Criterion SC-8: Easy to Use
Success Criterion SC-9: Availability of Required Software
Success Criterion SC-10 Early Availability of Required Information
Success Criterion SC-11 Generic Applicability
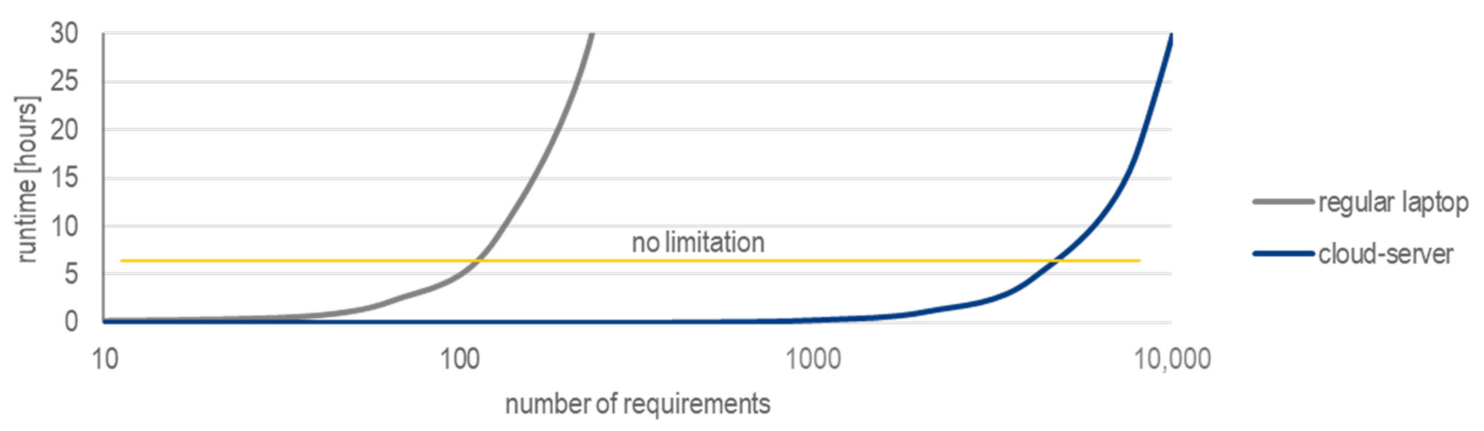
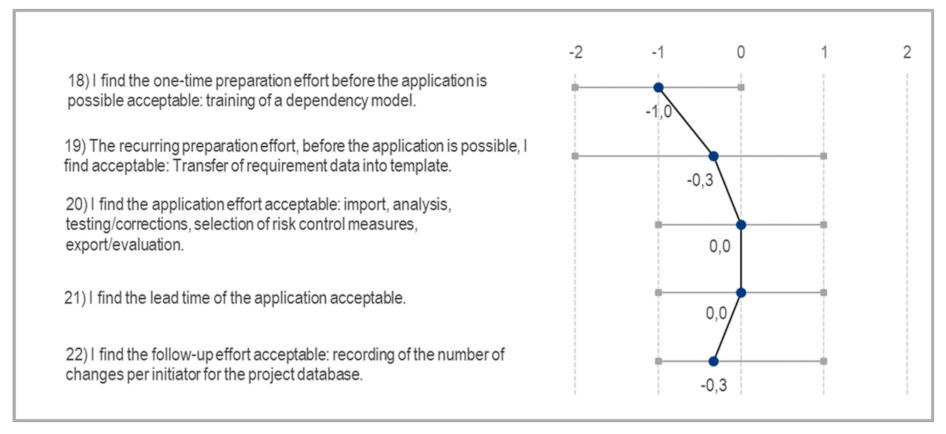
Success Criterion SC-12 Acceptable Application Effort
4.2.3. Output Success Criteria
Success Criterion SC-13 Reusable Database
- Likelihood analysis: Number of changes triggered by an initiator in past projects.
- Dependency analysis: Correctness of dependencies between requirements.
- Proactive action selection: Suitability of the proposed proactive measures.
Success Criterion SC-14 Sufficient Accuracy
4.3. Success Evaluation
5. Discussion and Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Delimitation Matrices
| Key: core topic  partly covered  rudimentarily touched  not covered ▬ | Research Approaches | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [27] | [6] | [71] | [9] | [8] | [23] | [89] | [34] | [90] | [33] | [5] | Own Approach | ||
| Delimitation criteria | Requirement change risk assessment in the development of complex technical systems | ||||||||||||
| Initial change effects |  | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ |  | ▬ | ▬ | ▬ |  | |
| Consecutive change effects | ▬ |  | ▬ |  |  |  |  |  |  | ▬ | ▬ |  | |
| Local change impact |  |  | ▬ | ▬ | ▬ | ▬ | ▬ |  | ▬ | ▬ | ▬ |  | |
| Collective change impact | ▬ | ▬ | ▬ |  |  |  |  |  |  | ▬ | ▬ |  | |
| Exogenous change likelihood |  |  | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ |  | |
| Endogenous change likelihood | ▬ |  | ▬ |  | ▬ |  |  | ▬ | ▬ |  |  |  | |
| Selection of proactive risk measures for requirement changes |  |  |  | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ | ▬ |  | |
Appendix B. Workshops with Industry Experts
| ID | Basic Information |
|---|---|
| W1 | Type and description: Workshop/Initial requirements elicitation (taking into account the results of the preliminary study) Participants: head of department, project leader, team leader, process owner, requirements engineer, developer and subject matter expert (total: 8 participants) Duration and time: 180 min/02.2020 |
| W2 | Type and description: Workshop/Specification and prioritization of requirements; definition of use cases Participants: see W1 Duration and time: 120 min/04.2020 |
| CE1 | Type and description: Regular exchange (approx. monthly)/in particular discussion of interim results with regard to suitability and practicality and characterization of the framework conditions to be taken into account Participants: usually head of department, requirements engineer, process manager and one to three alternating users (total: 2–6 participants) Duration and time: 30–60 min/01.2020 till 12.2021 |
| W3 | Type and description: Workshop/finalizing Use-Cases Participants: requirements engineer and subject matter expert (total: 2 participants) Duration and time: 120 min/04.2020 |
| W4 | Type and description: Workshop/Discussion of the practicability of the risk portfolio Participants: requirements engineer and subject matter expert (total: 2 participants) Duration and time: 120 min/09.2020 |
| W5 | Type and description: Workshop/Discussion and enrichment of the list with proactive measures Participants: requirements engineer and subject matter expert (total: 2 participants) Duration and time: 120 min/11.2020 |
| W6 | Type and description: Workshop/Recording of actual processes and definition of target processes when applying the methodology (change and risk management), recording of software landscape and definition of required interfaces Participants: head of department, requirements engineer, process owner, subject matter expert and user (total: 5 participants) Duration and time: 1120 min/12.2020 |
| W7 | Type and description: Discussion/Validation planning (requirements, available data, framework conditions, etc.) Participants: head of department (drive train sensor development), head of department (cockpit systems), requirements engineer, process owner, subject matter expert and user (total: 6 participants) Duration and time: 120 min/01.2021 |
| W8 | Type and description: Workshop/Validation of the change impact assessment method and prototypical implementation Participants: requirements engineer, subject matter expert and user (total: 3 participants) Duration and time: 120 min/03.2021 |
| W9 | Type and description: Workshop/Validation of the change likelihood assessment method and prototypical implementation Participants: head of department, requirements engineer, process owner, subject matter expert and user (total: 5 participants) Duration and time: 120 min/04.2021 |
| W10 | Type and description: Workshop/Validation of the method for analyzing requirement dependencies and prototypical implementation Participants: requirements engineer and subject matter expert (total: 2 participants) Duration and time: 120 min/05.2021 |
| W11 | Type and description: Workshop/Validation of the risk management method and prototypical implementation as well as the intended learning mechanisms Participants: head of department, requirements engineer and subject matter expert (total: 3 participants) Duration and time: 120 min/06.2021 |
Appendix C. Guideline for Collective Impact Assessment
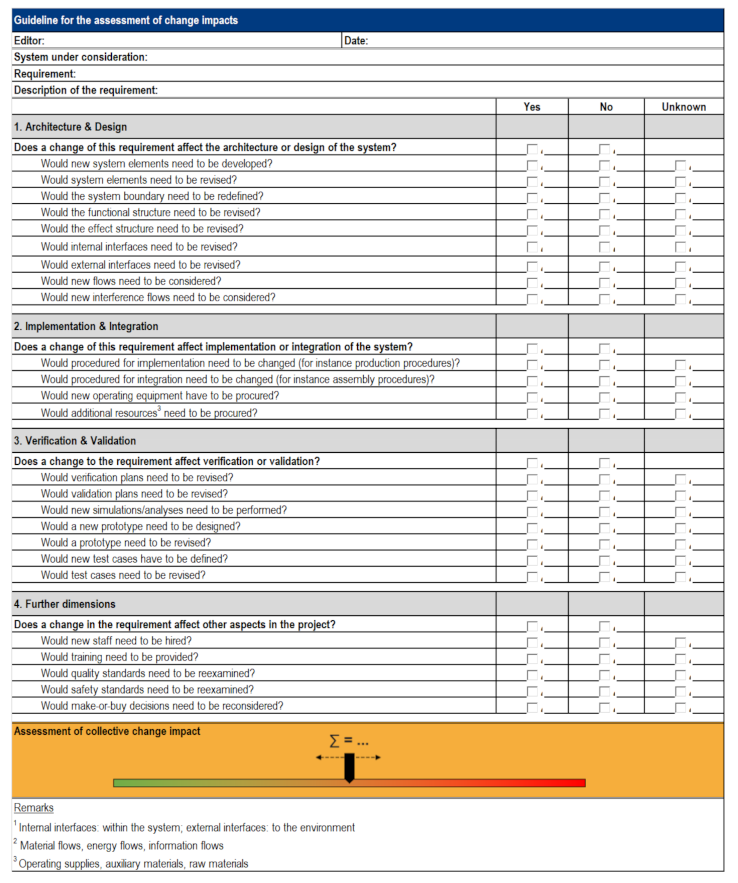
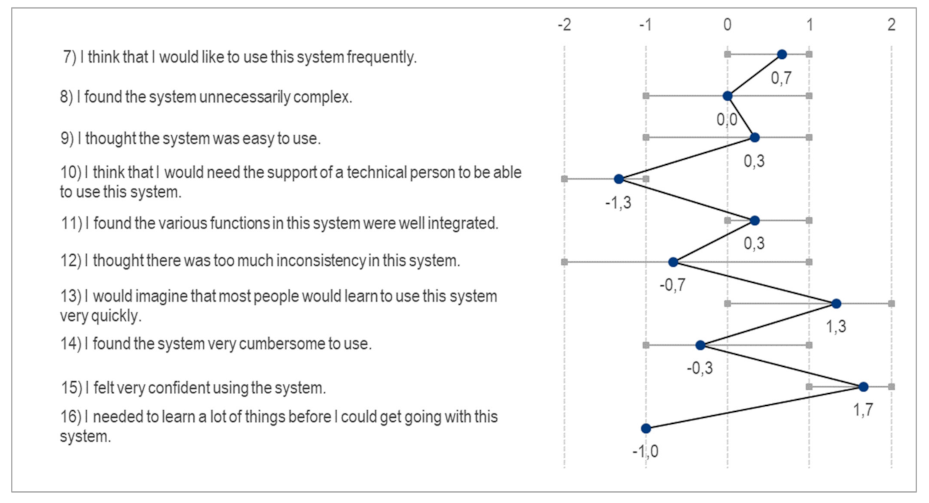
Appendix D. Questionnaire Results
- Strongly disagree (−2)
- Disagree (−1)
- Neither agree nor disagree / neutral (0)
- Agree (1)
- Strongly agree (2)

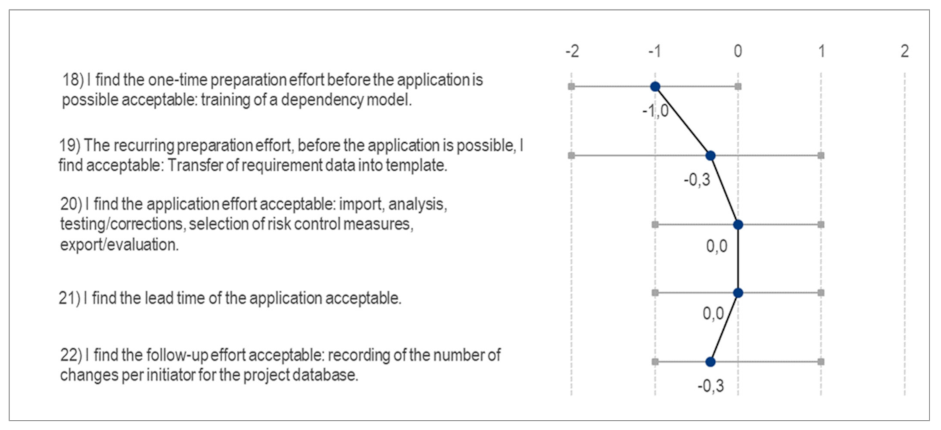
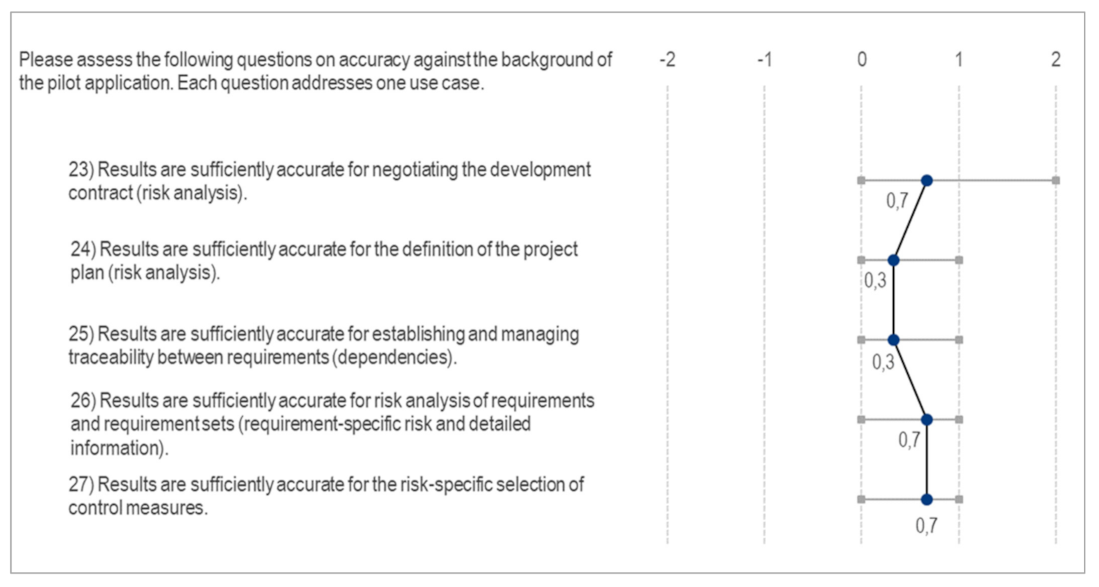
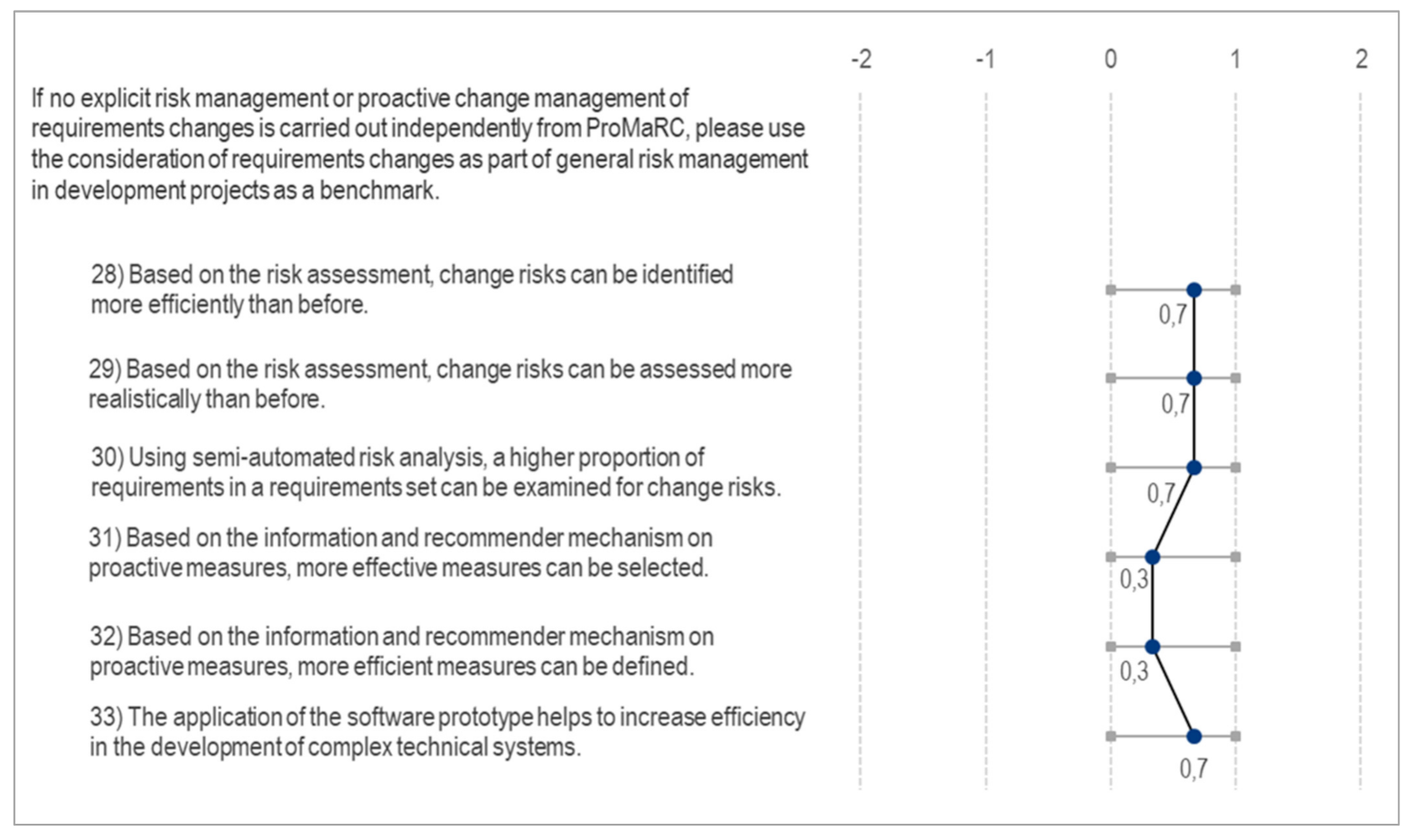
Appendix E. Impact Model for Success Evaluation

Appendix F. Questionnaire for Project Characteristics
| ID | Question | Option |
|---|---|---|
| 1 | What is the degree of innovation of the system to be developed? | 1: low, 2: medium, 3: high |
| 2 | What is the likelihood of change requests from the customer? | 1: low, 2: medium, 3: high |
| 3 | What is the certainty of political conditions that influence the development project? | 1: low, 2: medium, 3: high |
| 4 | What is the complexity of the project? | 1: low, 2: medium, 3: high |
| 5 | What is the supplier’s delivery reliability? | 1: low, 2: medium, 3: high |
| 6 | How well are we positioned compared to our competitors? | 1: worse, 2: equal, 3: better |
| 7 | Are structural changes to be expected at the customer? | 1: yes, 2: no |
| 8 | Are internal structural changes to be expected? | 1: yes, 2: no |
| 9 | Are changes of project staff with technical “know how” expected? | 1: yes, 2: no |
| 10 | Do we apply structured requirements management methods in the project? | 1: yes, 2: no |
| 11 | Is there an exchange across disciplines? | 1: yes, 2: no |
| 12 | Are customer requirements clearly defined? | 1: yes, 2: no |
References
- The Standish Group. Chaos Manifesto 2018; Standish Group: West Yarmouth, MA, USA, 2017. [Google Scholar]
- Morkos, B.; Shankar, P.; Summers, J.D. Predicting requirement change propagation, using higher order design structure matrices: An industry case study. J. Eng. Des. 2012, 23, 905–926. [Google Scholar] [CrossRef]
- Fernandes, J.; Henriques, E.; Silva, A.; Moss, M.A. Requirements change in complex technical systems: An empirical study of root causes. Res. Eng. Des. 2015, 26, 37–55. [Google Scholar] [CrossRef]
- Almefelt, L.; Berglund, F.; Nilsson, P.; Malmqvist, J. Requirements management in practice: Findings from an empirical study in the automotive industry. Res. Eng. Des. 2006, 17, 113–134. [Google Scholar] [CrossRef]
- Hein, H.; Voris, N.; Morkos, B. Predicting requirement change propagation through investigation of physical and functional domains. Res. Eng. Des. 2018, 29, 309–328. [Google Scholar] [CrossRef]
- Neumann, M. Ein Modellbasierter Ansatz zur Risikoorientierten Entwicklung Innovativer Produkte. Ph.D. Thesis, Ruhr-University Bochum, Bochum, Germany, 2016. [Google Scholar]
- Giffin, M.; de Weck, O.; Bounova, G.; Keller, R.; Eckert, C.; Clarkson, P.J. Change Propagation Analysis in Complex Technical Systems. J. Mech. Des. 2009, 131, 81001. [Google Scholar] [CrossRef]
- Koh, Y.; Caldwell, M.; Clarkson, J. A method to assess the effects of engineering change propagation. Res. Eng. Des. 2012, 23, 329–351. [Google Scholar] [CrossRef]
- Clarkson, P.J.; Simons, C.; Eckert, C. Predicting Change Propagation in Complex Design. J. Mech. Des. 2004, 126, 788–797. [Google Scholar] [CrossRef]
- Morkos, B. Computational Representation and Reasoning Support for Requirements Change Management in Complex System Design. Ph.D. Thesis, Clemson University, Clemson, SC, USA, 2012. [Google Scholar]
- Kurrle, A. Durchgängige Dokumentation von Verteilten Zielsystemen in der Produktentwicklung durch Verwendung semantischer Metainformationen am Beispiel Connected Car. Ph.D. Thesis, Karlsruher Institut for Technology, Karlsruhe, Germany, 2018. [Google Scholar]
- Song, Y.-W.; Herzog, M.; Bender, B. Understanding the Initial Requirements Definition in Early Design Phases. Proc. Int. Conf. Eng. Des. 2019, 1, 3751–3760. [Google Scholar] [CrossRef]
- Jayatilleke, S.; Lai, R. A systematic review of requirements change management. Inf. Softw. Technol. 2018, 93, 163–185. [Google Scholar] [CrossRef]
- Graessler, I.; Oleff, C.; Scholle, P. Method for Systematic Assessment of Requirement Change Risk in Industrial Practice. Appl. Sci. 2020, 10, 8697. [Google Scholar] [CrossRef]
- The Standish Group. The CHAOS Report; Standish Group: West Yarmouth, MA, USA, 1995. [Google Scholar]
- The Standish Group. Chaos Manifesto 2011; Standish Group: West Yarmouth, MA, USA, 2011. [Google Scholar]
- Lindvall, M. An Empirical Study of Requirements-Driven Impact Analysis in Object-Oriented Software Evolution. Ph.D. Thesis, Linköping University, Linköping, Sweden, 1997. [Google Scholar]
- Rodrigues da Silva, A. Quality of requirements specifications. In Proceedings of the 29th Annual ACM Symposium on Applied Computing, Gyeongju, Korea, 24–28 March 2014; Cho, Y., Ed.; ACM: New York, NY, USA, 2014; pp. 1021–1022, ISBN 9781450324694. [Google Scholar]
- Merriam-Webster.com. Dictionary. Proactive. Available online: https://www.merriam-webster.com/dictionary/proactive (accessed on 26 November 2021).
- Lindemann, U. Integriertes Änderungsmanagement, 1st ed.; Springer: Berlin/Heidelberg, Germany, 1998; ISBN 978-3540634904. [Google Scholar]
- Ebert, C. Systematisches Requirements Engineering: Anforderungen Ermitteln, Dokumentieren, Analysieren und Verwalten, 6th ed.; Springer: Berlin/Heidelberg, Germany, 2019; ISBN 9783960884545. [Google Scholar]
- Ghosh, S.; Ramaswamy, S.; Jetley, R.P. Towards Requirements Change Decision Support. In Proceedings of the 20th Asia-Pacific Software Engineering Conference (APSEC), Bangkok, Thailand, 2–5 December 2013; Muenchaisri, P., Rothermel, G., Eds.; IEEE: Piscataway, NJ, USA, 2013; pp. 148–155. [Google Scholar]
- Wickel, M.C. Änderungen Besser Managen. Ph.D. Thesis, Technical University Munich, Munich, Germany, 2017. [Google Scholar]
- Fricke, E. Der Änderungsprozess als Grundlage einer nutzerzentrierten Systementwicklung. Ph.D. Thesis, Technical University Munich, Munich, Germany, 1998. [Google Scholar]
- Jarratt, T.A.W.; Eckert, C.M.; Caldwell, N.H.M.; Clarkson, P.J. Engineering change: An overview and perspective on the literature. Res. Eng. Des. 2011, 22, 103–124. [Google Scholar] [CrossRef]
- VDA QMC Working Group 13/Automotive SIG. Automotive SPICE Process Assessment / Reference Model. 2017. Available online: http://www.automotivespice.com/ (accessed on 19 December 2021).
- Smith, P.G.; Merritt, G.M. Proactive Risk Management: Controlling Uncertainty in Product Development; Productivity Press: New York, NY, USA, 2002; ISBN 1563272652. [Google Scholar]
- Lührig, T. Risikomanagement in der Produktentwicklung der Deutschen Automobilindustrie: Von der Konzeptentwicklung bis zum Produktionsanlauf, 1st ed.; Shaker: Aachen, Germany, 2006; ISBN 3832248277. [Google Scholar]
- Grundmann, T. Ein Anwendungsorientiertes System für das Management von Produkt- und Prozessrisiken. Ph.D. Thesis, Technical University, Aachen, Germany, 2008. [Google Scholar]
- Hamraz, B.; Caldwell, N.H.M.; Clarkson, P.J. A Holistic Categorization Framework for Literature on Engineering Change Management. Syst. Engin. 2013, 16, 473–505. [Google Scholar] [CrossRef]
- Jayatilleke, S.; Lai, R.; Reed, K. A method of requirements change analysis. Requir. Eng. 2018, 23, 493–508. [Google Scholar] [CrossRef]
- Conrow, E.H. Effective Risk Management: Some Keys to Success; Aiaa: Reston, VA, USA, 2003; ISBN 1-563749-581-2. [Google Scholar]
- Kocar, V.; Akgunduz, A. ADVICE: A virtual environment for Engineering Change Management. Comput. Ind. 2010, 61, 15–28. [Google Scholar] [CrossRef]
- Gärtner, T.; Rohleder, N.; Schlick, C.M. Simulation of Product Change Effects on the Duration of Development Processes based on the DSM. In Proceedings of the 10th International DSM Conference, Stockholm, Sweden, 11–12 November 2008; pp. 199–208. [Google Scholar]
- Guodong, Y.; Yu, Y.; Xuefeng, Z.; Chi, L. Network-Based Analysis of Requirement Change in Customized Complex Product Development. Int. J. Inf. Technol. Decis. Mak. 2017, 16, 1125–1149. [Google Scholar] [CrossRef]
- Zheng, Y.; Yang, Y.; Zhang, N. A model for assessment of the impact of configuration changes in complex products. J. Intell. Manuf. 2020, 31, 501–527. [Google Scholar] [CrossRef]
- Pasqual, M.C.; de Weck, O.L. Multilayer network model for analysis and management of change propagation. Res. Eng. Des. 2012, 23, 305–328. [Google Scholar] [CrossRef]
- Engelhardt, R.A. Uncertainty Mode and Effects Analysis—Heuristische Methodik zur Analyse und Beurteilung von Unsicherheiten in Technischen Systemen des Maschinenbaus. Ph.D. Thesis, Techniche Universitat Darmstadt, Darmstadt, Germany, 2013. [Google Scholar]
- Fricke, E.; Gebhard, B.; Negele, H.; Igenbergs, E. Coping with changes: Causes, findings, and strategies. Syst. Engin. 2000, 3, 169–179. [Google Scholar] [CrossRef]
- Bender, B.; Gericke, K. Pahl/Beitz Konstruktionslehre: Methoden und Anwendung Erfolgreicher, 9th ed.; Springer Vieweg: Wiesbaden, Germany, 2019; ISBN 978-3-662-57302-0. [Google Scholar]
- Ulrich, H. Die Betriebswirtschaftslehre als anwendungsorientierte Sozialwissenschaft. In Die Führung des Betriebes: Curt Sandig zu Seinem 80. Geburtstag Gewidmet; Geist, M., Köhler, R., Eds.; Poeschel: Stuttgart, Germany, 1981; pp. 1–27. ISBN 3791003089. [Google Scholar]
- Hevner, A.; Chatterjee, S. Design Research in Information Systems: Theory and Practice; Springer Science+Business Media LLC: Boston, MA, USA, 2010; ISBN 9781441956521. [Google Scholar]
- Johannesson, P.; Perjons, E. An Introduction to Design Science; Springer International Publishing AG: New York, NY, USA, 2014; ISBN 978-3-319-10631-1. [Google Scholar]
- Eckert, C.M.; Clarkson, P.J.; Stacey, M.K. The spiral of applied research: A methodological view on integrated design research. In Proceedings of the 14th International Conference on Engineering Design, Stockholm, Sweden, 19–21 August 2003; Folkeson, A., Gralen, K., Norell, M., Sellgren, U., Eds.; Design Society: Glasgow, UK, 2003; pp. 245–255, ISBN 1-904670-00-8. [Google Scholar]
- Peffers, K.; Tuunanen, T.; Rothenberger, M.A.; Chatterjee, S. A Design Science Research Methodology for Information Systems Research. J. Manag. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Blessing, L.T.M.; Chakrabarti, A. DRM, a Design Research Methodology, 1st ed.; Springer London: London, UK, 2009; ISBN 978-1-84882-587-1. [Google Scholar]
- Gräßler, I.; Dattner, M.; Bothen, M. Main Feature List as core success criteria of organizing Requirements Elicitation. In Proceedings of the R & D Management Conference 2018, Milan, Italy, 30 June–4 July 2018; pp. 1–16. [Google Scholar]
- Felfernig, A.; Stettinger, M.; Falkner, A.; Atas, M.; Franch, X.; Palomares, C. OpenReq: Recommender Systems in Requirements Engineering. In Proceedings of the Workshop Papers of I-Know 2017: Co-Located with International Conference on Knowledge Technologies and Data-Driven Business, Graz, Austria, 11–12 October 2017; Available online: http://ase.ist.tugraz.at/ASE/wp-content/uploads/2014/01/openreq-4.pdf (accessed on 6 December 2021).
- Gräßler, I.; Preuß, D.; Oleff, C. Automatisierte Identifikation und Charakterisierung von Anforderungsabhängigkeiten—Literaturstudie zum Vergleich von Lösungsansätzen. In Design fox X-Beiträge Zum 30. DfX-Symposium; Krause, D., Paetzold, K., Wartzack, S., Eds.; TuTech Verlag: Hamburg, Germany, 2020; pp. 199–208. [Google Scholar]
- González-Carvajal, S.; Garrido-Merchán, E.C. Comparing BERT against Traditional Machine Learning Text Classification, 2020. Available online: https://arxiv.org/pdf/2005.13012 (accessed on 6 December 2021).
- Alpaydin, E. Maschinelles Lernen, 2nd ed.; De Gruyter: Berlin, Germany, 2019; ISBN 9783110617894. [Google Scholar]
- Devlin, J.; Chang, M.-W.; Lee, K.; Toutanova, K. BERT: Pre-Training of Deep Bidirectional Transformers for Language Understanding, 2019. Available online: https://arxiv.org/pdf/1810.04805v2 (accessed on 19 December 2021).
- huggingface. bert-base-cased. Available online: https://huggingface.co/bert-base-cased (accessed on 6 December 2021).
- huggingface. BERT Tokenizer. Available online: https://huggingface.co/transformers/main_classes/tokenizer.html (accessed on 6 December 2021).
- Gräßler, I.; Oleff, C.; Preuß, D. Holistic change propagation and impact analysis in requirements management. In Proceedings of the R&D Management Conference 2021, Strathclyde, UK, 6–8 July 2018. [Google Scholar]
- Dahlstedt, Å.G.; Persson, A. Requirements Interdependencies—Moulding the State of Research into a Research Agenda. In Proceedings of the Ninth International Workshop on Requirements Engineering: Foundation for Software Quality (REFSQ 2003), Klagenfurt, Austria, 16–17 June 2003; Salinesi, C., Regnell, B., Kamsties, E., Eds.; Universitätsbibliothek Essen: Essen, Germany, 2003; pp. 71–80. [Google Scholar]
- Gräßler, I.; Hentze, J. Structuring and Describing Requirements in a Flexible Mesh for Development of Smart Interdisciplinary Systems. In Proceedings of the Smart Structures and Materials 7th ECCOMAS Thematic Conference on Smart Structures and Materials, Ponta Delgada, Portugal, 3–6 June 2015; Araujo, A., Mota Soares, C.A., Eds.; Springer International Publishing: Basel, Switzerland, 2017; pp. 1622–1631. [Google Scholar]
- Pohl, K. Process-Centered Requirements Engineering; Research Studies Press: Taunton, UK, 1996; ISBN 9780863801938. [Google Scholar]
- Zhang, H.; Li, J.; Zhu, L.; Jeffery, R.; Liu, Y.; Wang, Q.; Li, M. Investigating dependencies in software requirements for change propagation analysis. Inf. Softw. Technol. 2014, 56, 40–53. [Google Scholar] [CrossRef]
- Goknil, A.; Kurtev, I.; van den Berg, K.; Spijkerman, W. Change impact analysis for requirements: A metamodeling approach. Inf. Softw. Technol. 2014, 56, 950–972. [Google Scholar] [CrossRef][Green Version]
- Pohl, K.; Rupp, C. Basiswissen Requirements Engineering: Aus- und Weiterbildung nach IREB-Standard zum Certified Professional for Requirements Engineering Foundation Level, 5th ed.; dpunkt: Heidelberg, Germany, 2021; ISBN 978-3-86490-814-9. [Google Scholar]
- Xing, W.; Ghorbani, A. Weighted PageRank algorithm. In Proceedings of the Second Annual Conference on Communication Networks and Services Research, Fredericton, NB, Canada, 21 May 2004; IEEE Computer Society, Ed.; IEEE: Piscataway, NJ, USA, 2004; pp. 305–314. [Google Scholar]
- Gräßler, I.; Thiele, H.; Oleff, C.; Scholle, P.; Schulze, V. Method for Analysing Requirement Change Propagation Based on a Modified Pagerank Algorithm. In Proceedings of the Design Society: International Conference on Engineering Design, ICED, Delft, The Netherlands, 5–8 August 2019; Design Society, Ed.; Cambridge University Press: Cambridge, UK, 2019; pp. 3681–3690. [Google Scholar]
- Brin, S.; Page, L. The anatomy of a large-scale hypertextual Web search engine. Comput. Netw. ISDN Syst. 1998, 30, 107–117. [Google Scholar] [CrossRef]
- Walden, D.D.; Roedler, G.J.; Forsberg, K.; Hamelin, R.D.; Shortell, T.M. Systems Engineering Handbook: A Guide for System Life Cycle Processes and Activities, 4th ed.; Wiley: Hoboken, NJ, USA, 2015; ISBN 9781118999400. [Google Scholar]
- McGee, S.; Greer, D. Software requirements change taxonomy: Evaluation by case study. In Proceedings of the 19th IEEE International Requirements Engineering Conference (RE), Trento, Italy, 29 August–2 September 2011; IEEE: Piscataway, NJ, 2011; pp. 25–34. [Google Scholar]
- McGee, S.; Greer, D. A Software Requirements Change Source Taxonomy. In Proceedings of the Fourth International Conference on Software Engineering Advances, Porto, Portugal, 20–25 September 2009; Boness, K., Fernandes, J.M., Hall, J., Machado, R.J., Oberhauser, R., Eds.; IEEE: Piscataway, NJ, USA, 2009; pp. 51–58, ISBN 978-1-4244-4779-4. [Google Scholar]
- Kleine Büning, H. Aussagenlogik: Deduktion und Algorithmen; Springer Vieweg: Wiesbaden, Germany, 1994; ISBN 9783322848093. [Google Scholar]
- Gräßler, I.; Pottebaum, J.; Oleff, C.; Preuß, D. Handling of explicit uncertainty in requirements change management. In Proceedings of the Design Society: International Conference in Engineering Design, Gothenburg, Sweden, 16–20 August 2021; Cambridge University Press: Cambridge, UK, 2021; pp. 1687–1696. [Google Scholar]
- Diederichs, M. Risikomanagement und Risikocontrolling, 3rd ed.; Verlag Franz Vahlen: München, Germany, 2012; ISBN 9783800642229. [Google Scholar]
- Gericke, K.; Blessing, L. Enhancing Project Robustness: A Risk Management Perspective. Ph.D. Thesis, Technische Universität Berlin, Berlin, Germany, 2011. [Google Scholar]
- Dahmen, J.W. Prozeßorientiertes Risikomanagement zur Handhabung von Produktrisiken; Shaker: Aachen, Germany, 2002; ISBN 3832208356. [Google Scholar]
- Riverbank Computing. PyQt. Available online: https://riverbankcomputing.com/software/pyqt/intro (accessed on 7 December 2021).
- Pedregosa, F.; Varoquaux, G.; Gramfort, A.; Michel, V.; Thirion, B.; Grisel, O.; Blondel, M.; Prettenhofer, P.; Weiss, R.; Dubourg, V.; et al. Scikit-learn: Machine Learning in {P}ython. J. Mach. Learn. Res. 2011, 2825–2830. [Google Scholar]
- Gräßler, I.; Oleff, C.; Hieb, M.; Preuß, D. Automated requirement dependency analysis for complex technical systems: (in Review). In Proceedings of the 17th International Design Conference, Cavtat, Croatia, 23–26 May 2022; Design Society, Ed.; Cambridge University Press: Cambridge, UK, 2022. [Google Scholar]
- Sommerville, I. Software Engineering, 10th ed.; Pearson Studium: München, Germany, 2018; ISBN 9783863268350. [Google Scholar]
- International Organization for Standardization/International Electrotechnical Commission (ISO/IEC). Software-Engineering—Qualitätskriterien und Bewertung von Softwareprodukten (SQuaRE): Qualitätsmodell und Leitlinien; International Organization for Standardization/International Electrotechnical Commission (ISO/IEC): Washington, DC, USA, 2011. [Google Scholar]
- Brooke, J. SUS-A quick and dirty usability scale. Usability Eval. Ind. 1996, 189, 4–7. [Google Scholar]
- Laugwitz, B.; Held, T.; Schrepp, M. Construction and evaluation of a user experience questionnaire. In Proceedings of the 4th Symposium of the Workgroup Human-Computer Interaction and Usability Engineering of the Austrian Computer Society, USAB, Graz, Austria, 20–21 November 2008; Holzinger, A., Ed.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 63–76. [Google Scholar]
- Bangor, A.; Kortum, P.; Miller, J. Determining what individual SUS scores mean: Adding an adjective rating scale. J. Usability Stud. 2009, 4, 114–123. [Google Scholar]
- presseportal.de. Meistgenutzte Office-Software von Büromitarbeitern in Unternehmen in Deutschland im Jahr 2020. Available online: https://de.statista.com/statistik/daten/studie/77226/umfrage/internetnutzer---verbreitung-von-office-software-in-deutschland/ (accessed on 26 November 2021).
- Guido van Rossum. Python license. Available online: https://docs.python.org/3/license.html (accessed on 30 November 2021).
- Virtual Desktop Infrastructure (VDI); Vanguard Energy ETF (VDE). Entwicklung Mechatronischer und Cyber-Physischer Systeme; Beuth Verlag GmbH: Düsseldorf, Germany, 2021. [Google Scholar]
- Virtual Desktop Infrastructure (VDI). Entwicklung Technischer Produkte und Systeme—Modell der Produktentwicklung; Beuth Verlag GmbH: Düsseldorf, Germany, 2019. [Google Scholar]
- ISO/IEC/IEEE. Systems and Software Engineering-System Life Cycle Processes; ISO/IEC/IEEE: Geneva, Switzerland, 2015. [Google Scholar]
- Pohl, K. Requirements Engineering: Fundamentals, Principles, and Techniques; Springer: Berlin/Heidelberg, Germany, 2010; ISBN 3642125778. [Google Scholar]
- Dunn-Rankin, P. Scaling Methods: Peter Dunn-Rankin; L. Erlbaum: Hillsdale, NJ, USA, 1983; ISBN 0898592038. [Google Scholar]
- Hamraz, B.; Caldwell, N.H.; Wynn, D.C.; Clarkson, P.J. Requirements-based development of an improved engineering change management method. J. Eng. Des. 2013, 24, 765–793. [Google Scholar] [CrossRef]
- Deubel, T.; Conrad, J.; Köhler, C.; Wanke, S.; Weber, C. Change impact and risk analysis (CIRA): Combining the CPM/PDD theory and FMEA-methodology for an improved engineering change management. In Proceedings of the Design Society, 16th International Conference on Engineering Design, Paris, France, 28–31 July 2007; Cambridge University Press: Cambridge, UK, 2007. [Google Scholar]
- Cheng, H.; Chu, X. A network-based assessment approach for change impacts on complex product. J. Intell. Manuf. 2012, 23, 1419–1431. [Google Scholar] [CrossRef]
- Gräßler, I.; Wiechel, D.; Koch, A.-S.; Preuß, D.; Oleff, C. Model-based effect chain analysis for complex systems: (in Review). In Proceedings of the 17th International Design Conference, Cavtat, Croatia, 23–26 May 2022; Design Society, Ed.; Cambridge University Press: Cambridge, UK, 2022. [Google Scholar]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2019, 57, 2117–2135. [Google Scholar] [CrossRef]
- Gräßler, I.; Scholle, P.; Hentze, J.; Oleff, C. Semi-Automatized Assessment of Requirement Interrelations. In Proceedings of the 15th International Design Conference, Dubrovnik, Croatia, 21–24 May 2018; pp. 325–334. [Google Scholar]
- Gräßler, I.; Oleff, C. Risikoorientierte Analyse und Handhabung von Anforderungsänderungen. In Design for X, Proceedings of the Beiträge zum 30. DfX-Symposium, Bamberg, Germany, 18–19 September 2019; Krause, D., Paetzold, K., Wartzack, S., Eds.; TuTech Verlag: Hamburg, Germany, 2019. [Google Scholar]






| Input | Application |
|---|---|
| SC-1: Processability of interdisciplinary requirements | SC-8: Easy to use |
| SC-2: Processability of high number of requirements | SC-9: Availability of required software |
| SC-3: Processability of regular form of documentation | SC-10: Early availability of required information |
| Method | SC-10: Generic applicability |
| SC-4: Analysis of change propagation | SC-11: Acceptable application effort |
| SC-5: Analysis of exogenous and endogenous change likelihood | SC-12: Generic applicability |
| SC-6: Analysis of collective change impact | Output |
| SC-7: Selection of requirement specific proactive measures | SC-13: Reusability of database |
| SC = Success Criteria | SC-14: Sufficient accuracy for intended use cases |
| Criteria | MLR | SVM | RNN | BERT |
|---|---|---|---|---|
| Precision (macro avg.) | 20.47% | 24.00% | 22.07% | 54.10% |
| Recall (macro avg.) | 21.30% | 23.43% | 60.92% | 56.98% |
| F1 (macro avg.) | 6.29% | 23.92% | 12.92% | 55.12% |
| ROC_AUC (w. avg.) | 0.64 | 0.74 | 0.81 | 0.93 |
| Expected Number of Requirement Changes | Change Likelihood |
|---|---|
| Low—less than 0.25 changes are expected for this requirement | |
| Medium—between 0.25 and 0.75 changes are expected for this requirement | |
| High—between 0.75 and 1 changes are expected for this requirement | |
| very high—more than one change is expected for this requirement |
| Dependencies | Number | Precision | Recall | F1 |
|---|---|---|---|---|
| None | 3081 | 99.12% | 99.06% | 99.09% |
| Dependent | 92 | 69.15% | 70.65% | 69.89% |
| Macro avg. | - | 84.14% | 84.86% | 84.49% |
| Weighted avg. | - | 98.25% | 98.24% | 98.24% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gräßler, I.; Oleff, C.; Preuß, D. Proactive Management of Requirement Changes in the Development of Complex Technical Systems. Appl. Sci. 2022, 12, 1874. https://doi.org/10.3390/app12041874
Gräßler I, Oleff C, Preuß D. Proactive Management of Requirement Changes in the Development of Complex Technical Systems. Applied Sciences. 2022; 12(4):1874. https://doi.org/10.3390/app12041874
Chicago/Turabian StyleGräßler, Iris, Christian Oleff, and Daniel Preuß. 2022. "Proactive Management of Requirement Changes in the Development of Complex Technical Systems" Applied Sciences 12, no. 4: 1874. https://doi.org/10.3390/app12041874
APA StyleGräßler, I., Oleff, C., & Preuß, D. (2022). Proactive Management of Requirement Changes in the Development of Complex Technical Systems. Applied Sciences, 12(4), 1874. https://doi.org/10.3390/app12041874






