Reducing Defocused-Information Crosstalk to Multi-View Holography by Using Multichannel Encryption of Random Phase Distribution
Abstract
:1. Introduction
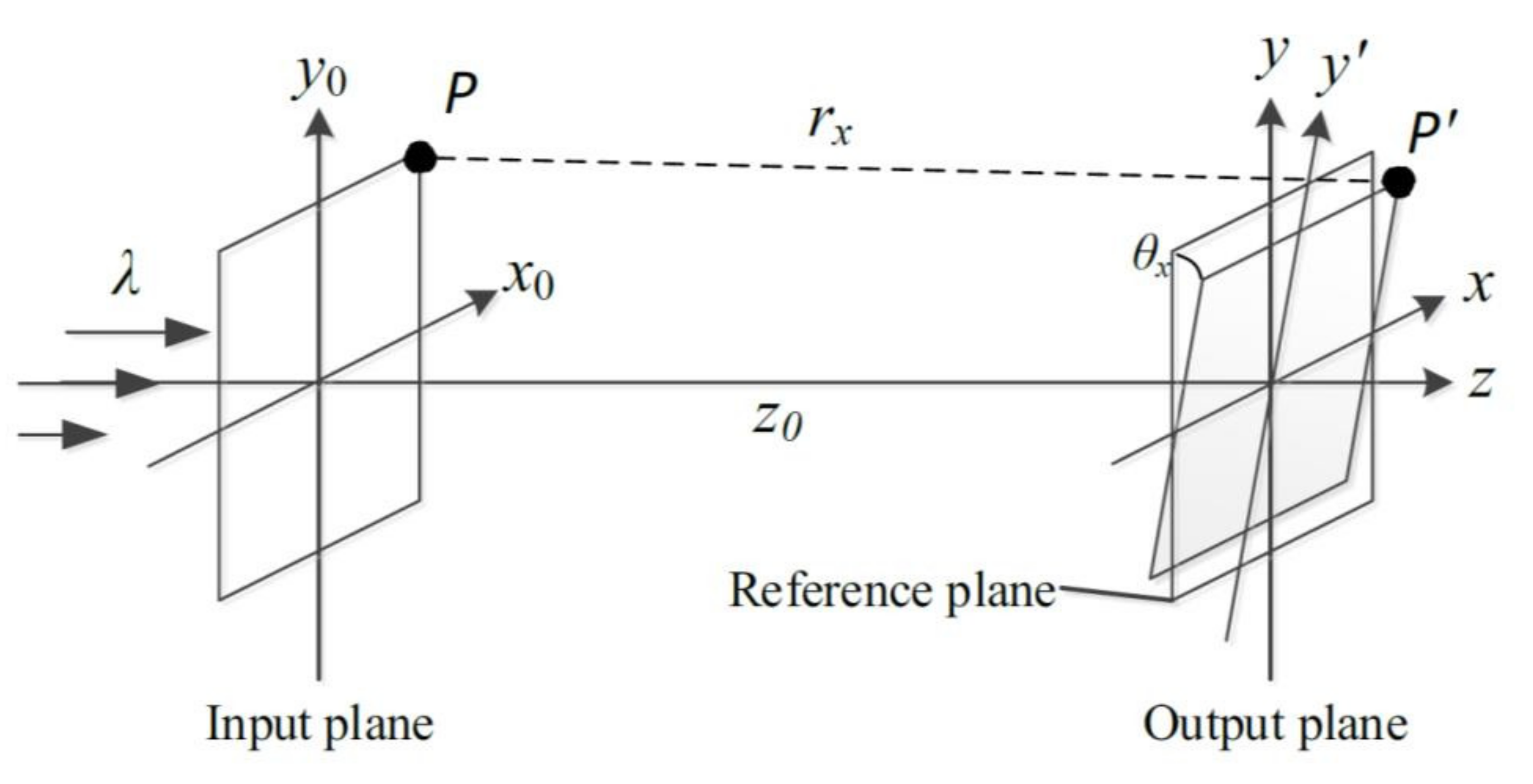
2. Methods
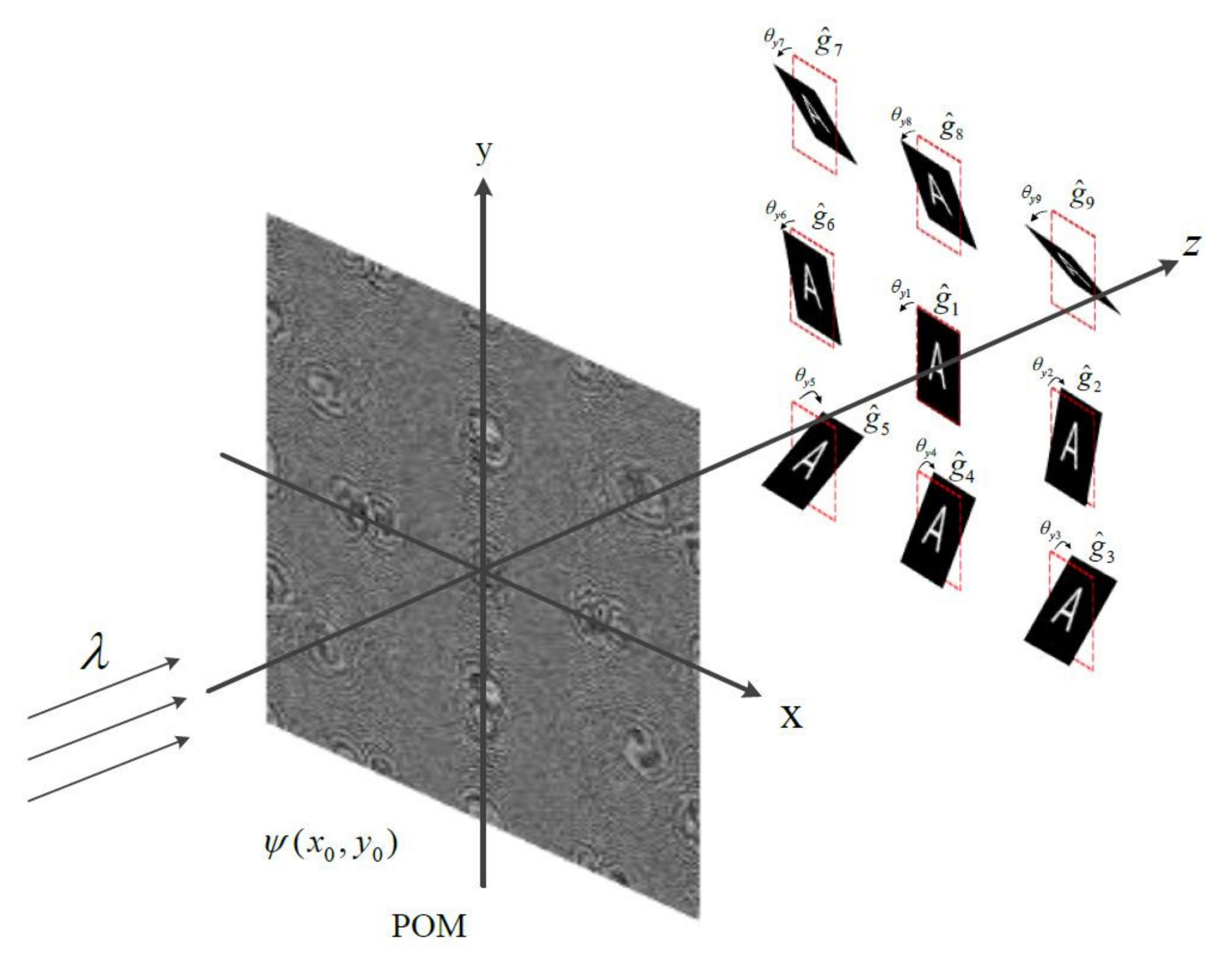
2.1. Algorithm Multiplexing
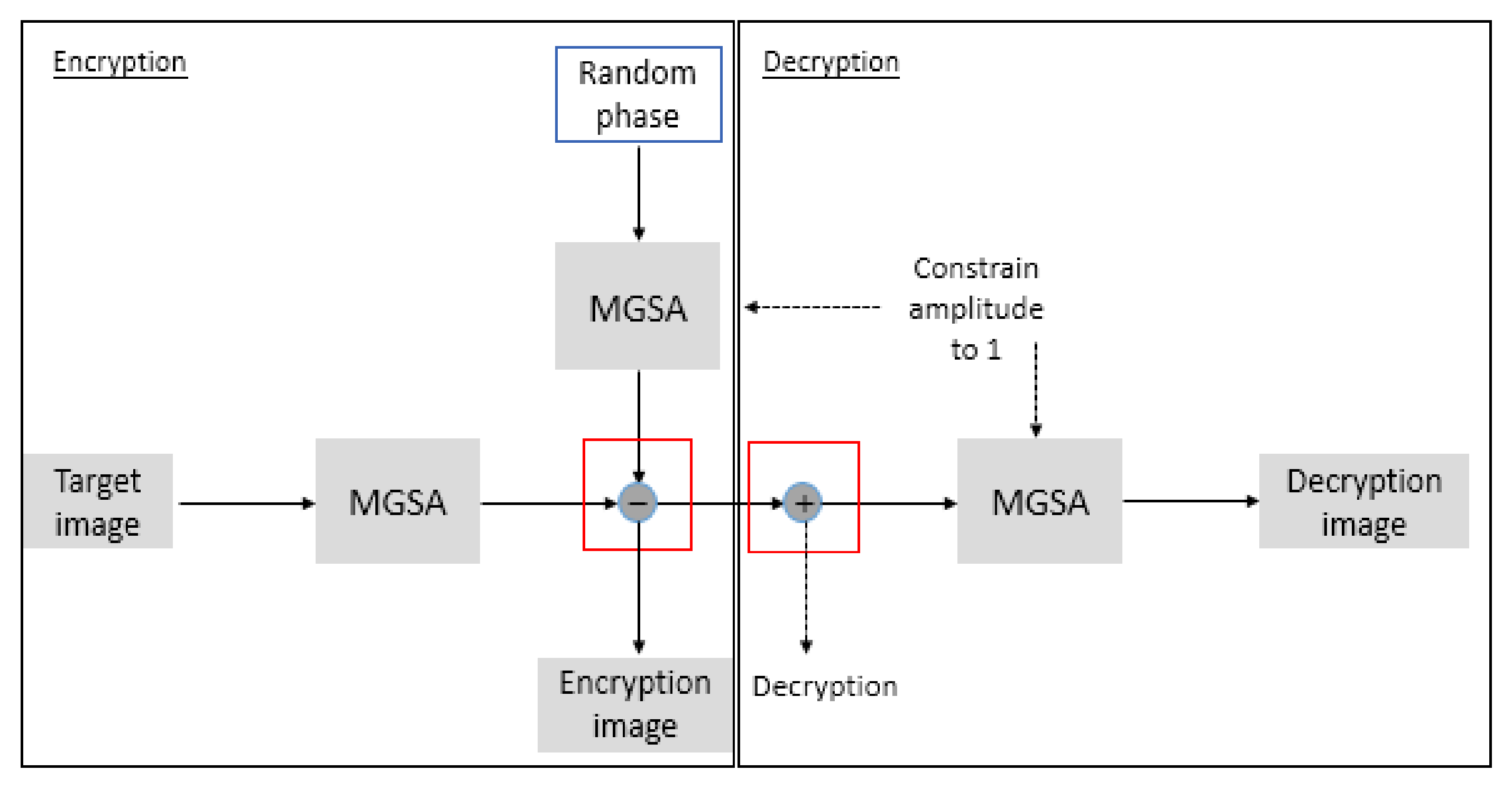
2.2. Phase-Locked Algorithm
- Step 1: Generate a random phase signal and set the initial amplitude = 1. Multiply both to acquire the image amplitude and the phase signal .
- Step 2: Calculate phase-locked key with MGSA to modulate the amplitude to 1 and only retain the phase information.
- Step 3: Subtract phase signal from random phase signal to get the encryption image .
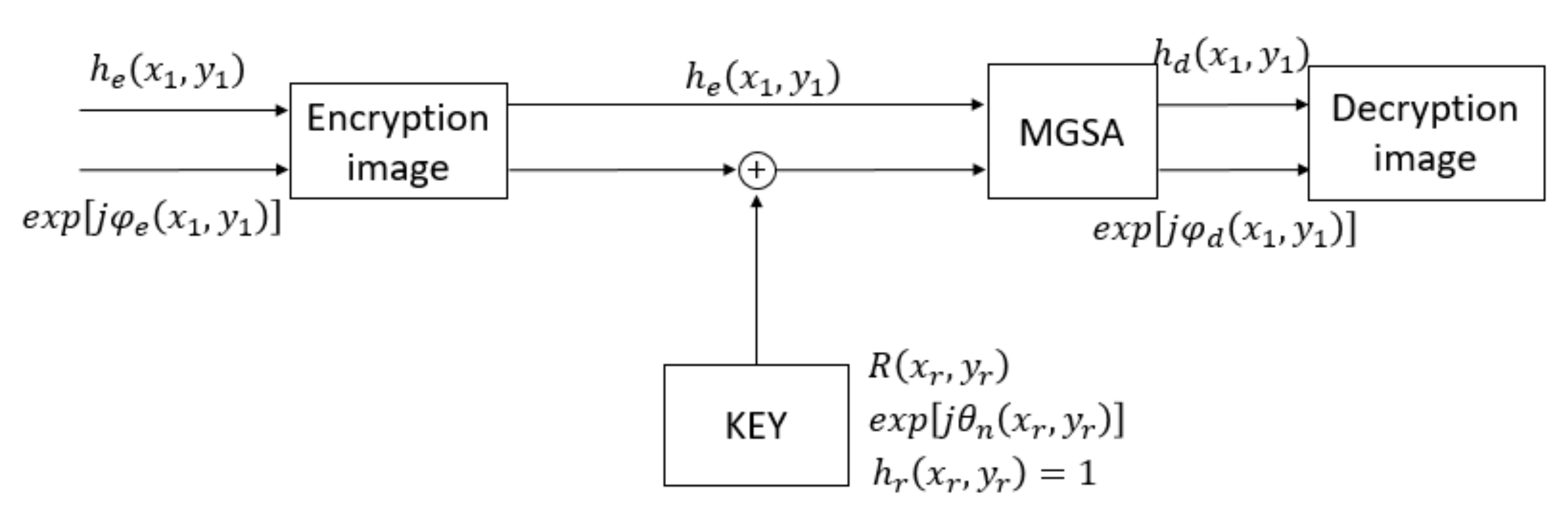
- Step 1: Add the encryption image phase signal and the random phase signal .
- Step 2: Multiply the encryption image amplitude and the decryption phase signal for the MGSA calculation and modulate the amplitude to 1.
- Step 3: Obtain the decryption image .
2.3. Assessment Approaches of Image Reconstruction Quality
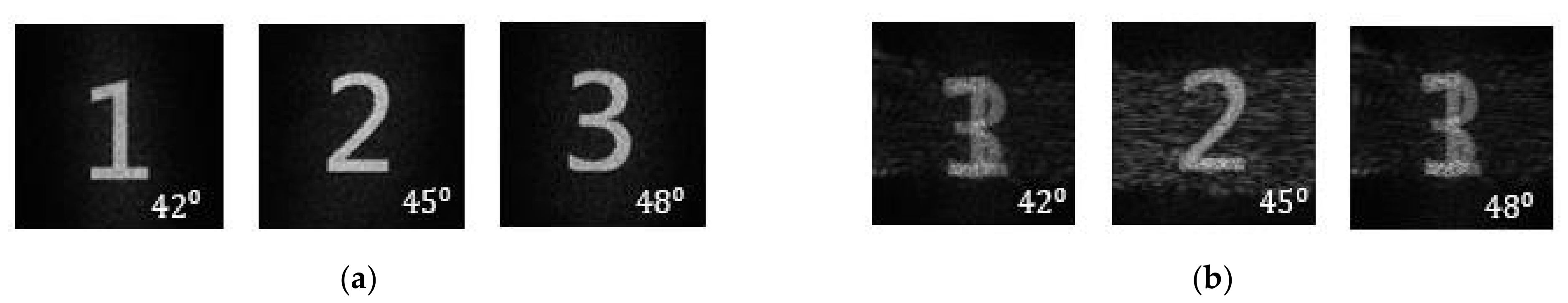
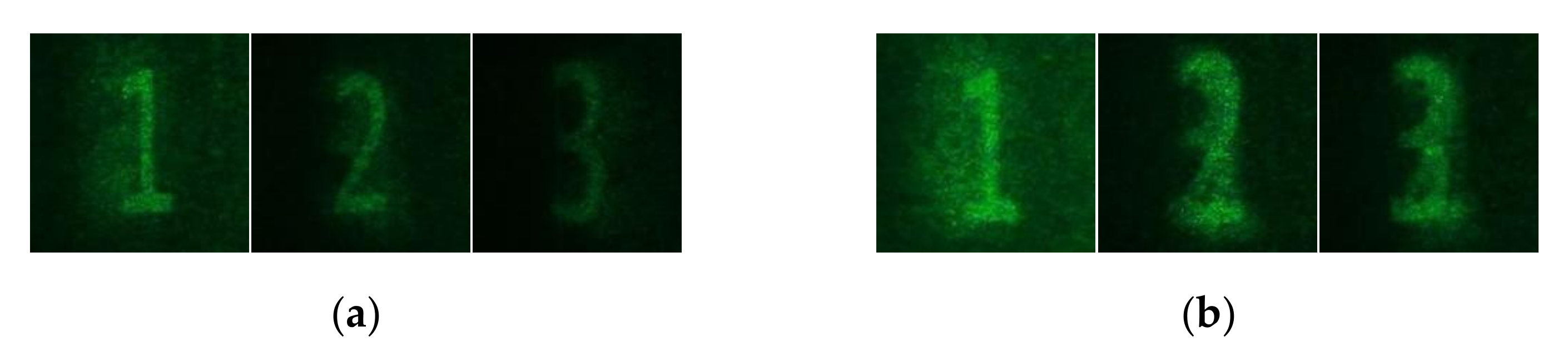
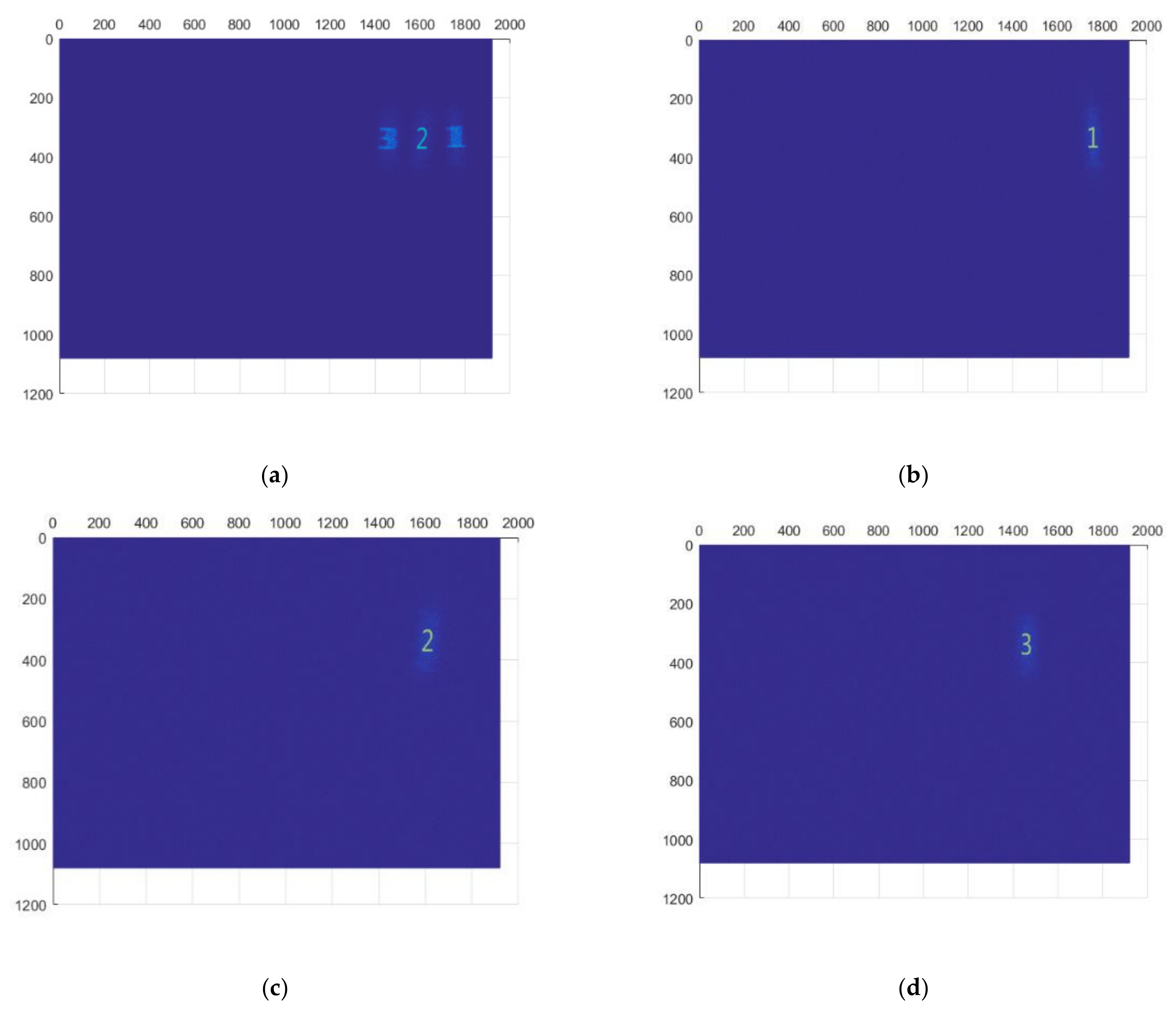
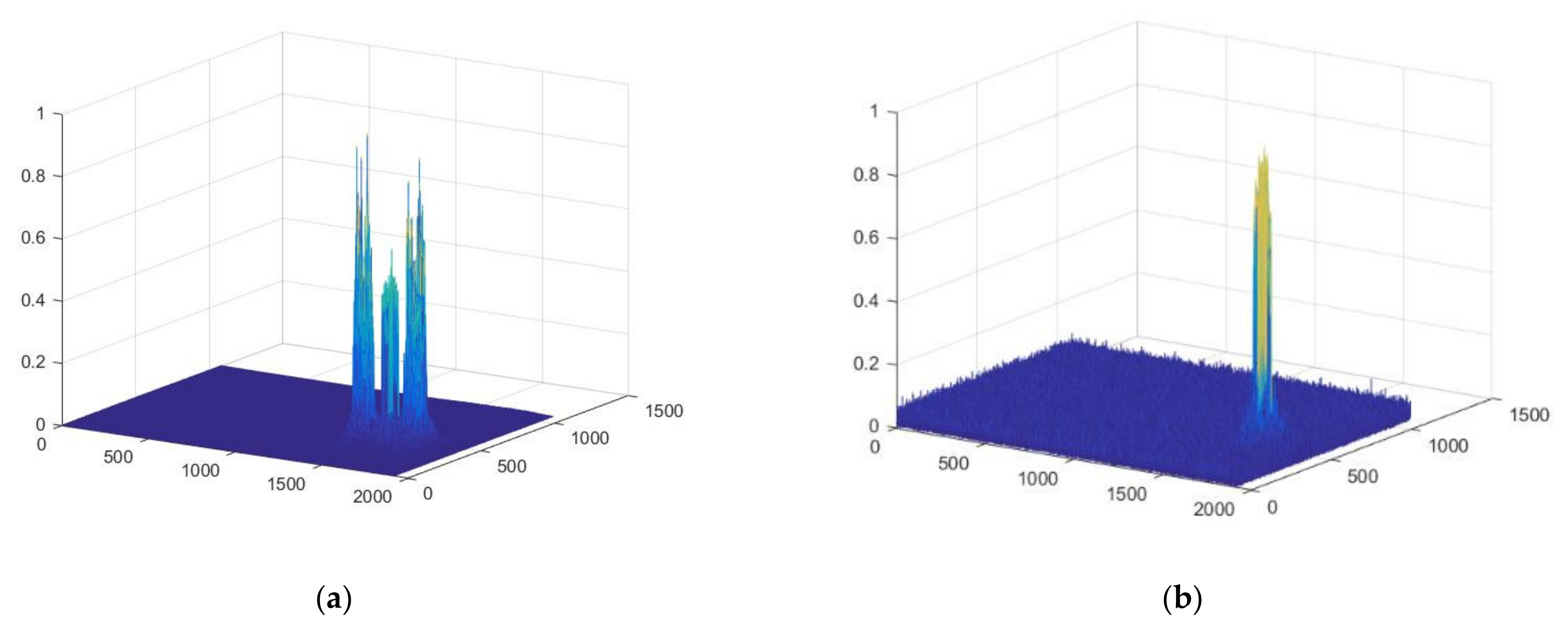
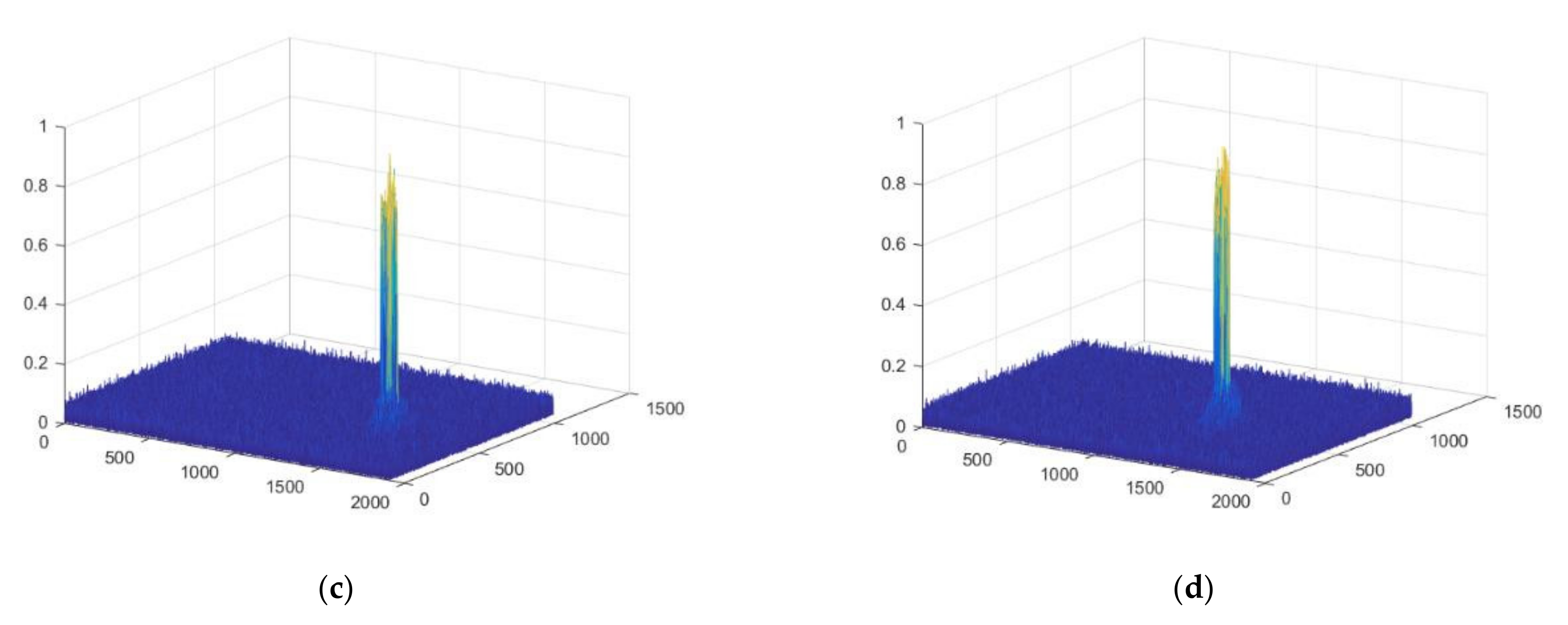
3. Experiments and Results
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kim, S.-C.; Kim, E.-S. Fast computation of hologram patterns of a 3D object using run-length encoding and novel look-up table methods. Appl. Opt. 2009, 48, 1030–1041. [Google Scholar] [CrossRef] [PubMed]
- Wakunami, K.; Hsieh, P.-Y.; Oi, R.; Senoh, T.; Sasaki, H.; Ichihashi, Y.; Okui, M.; Huang, Y.-P.; Yamamoto, K. Projection-type see-through holographic three-dimensional display. Nat. Commun. 2016, 7, 12954. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sugie, T.; Akamatsu, T.; Nishitsuji, T.; Hirayama, R.; Masuda, N.; Nakayama, H.; Ichihashi, Y.; Shiraki, A.; Oikawa, M.; Takada, N.; et al. High-performance parallel computing for next-generation holographic imaging. Nat. Electron. 2018, 1, 254–259. [Google Scholar] [CrossRef]
- Zhou, P.; Li, Y.; Liu, S.; Su, Y. Dynamic compensatory Gerchberg–Saxton algorithm for multiple-plane reconstruction in holographic displays. Opt. Express 2019, 27, 8958–8967. [Google Scholar] [CrossRef] [PubMed]
- Makey, G.; Yavuz, Ö.; Kesim, D.K.; Turnalı, A.; Elahi, P.; Ilday, S.; Ilday, F.Ö. Breaking crosstalk limits to dynamic holography using orthogonality of high-dimensional random vectors. Nat. Photonics 2019, 13, 251. [Google Scholar] [CrossRef] [PubMed]
- Refregier, P.; Javidi, B. Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 1995, 20, 767–769. [Google Scholar] [CrossRef] [PubMed]
- Unnikrishnan, G.; Joseph, J.; Singh, K. Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 2000, 25, 887–889. [Google Scholar] [CrossRef] [PubMed]
- Situ, G.; Zhang, J. Double random-phase encoding in the Fresnel domain. Opt. Lett. 2004, 29, 1584–1586. [Google Scholar] [CrossRef] [PubMed]
- Chen, L.; Zhao, D. Optical image encryption based on fractional wavelet transform. Opt. Commun. 2005, 254, 361–367. [Google Scholar] [CrossRef]
- Mogensen, P.C.; Glückstad, J. Phase-only optical encryption. Opt. Lett. 2000, 25, 566–568. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.-Y.; Li, W.-C.; Chang, H.-T.; Chuang, C.-H.; Chang, T.-J. 3-D modified Gerchberg–Saxton algorithm developed for panoramic computer-generated phase-only holographic display. J. Opt. Soc. Am. B 2017, 34, B42–B48. [Google Scholar] [CrossRef]
- Hwang, H.-E.; Chang, H.T.; Lie, W.-N. Multiple-image encryption and multiplexing using a modified Gerchberg-Saxton algorithm and phase modulation in Fresnel-transform domain. Opt. Lett. 2009, 34, 3917–3919. [Google Scholar] [CrossRef] [PubMed]
- Hwang, H.-E.; Chang, H.T.; Lie, W.-N. Fast double-phase retrieval in Fresnel domain using modified Gerchberg-Saxton algorithm for lensless optical security systems. Opt. Express 2009, 17, 13700–13710. [Google Scholar] [CrossRef] [PubMed]
- Leseberg, D.; Frère, C. Computer-generated holograms of 3-D objects composed of tilted planar segments. Appl. Opt. 1988, 27, 3020–3024. [Google Scholar] [CrossRef] [PubMed]
- Frére, C.; Leseberg, D.; Bryngdahl, O. Computer-generated holograms of three-dimensional objects composed of line segments. J. Opt. Soc. Am. A 1986, 3, 726–730. [Google Scholar] [CrossRef]
- Choi, K.; Kim, H.; Lee, B. Synthetic phase holograms for auto-stereoscopic image displays using a modified IFTA. Opt. Express 2004, 12, 2454–2462. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, J.-P.; Hsieh, W.-Y.; Poon, T.-C.; Tsang, P. Complex Fresnel hologram display using a single SLM. Appl. Opt. 2011, 50, H128–H135. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Koek, W.D.; Bhattacharya, N.; Braat, J.J.M.; Ooms, T.A.; Westerweel, J. Influence of virtual images on the sig-nal-to-noise ratio in digital in-line particle holography. Opt. Express 2005, 13, 2578–2589. [Google Scholar] [CrossRef] [PubMed] [Green Version]






| Picture | RDE | RMSE | SNR | |
|---|---|---|---|---|
| MGSA algorithm | 1 | 69.22% | 0.0262 | 3.52 dB |
| 2 | 76.62% | 0.0246 | 5.16 dB | |
| 3 | 62.17% | 0.0286 | 3.72 dB | |
| Phase encryption algorithm | 1 | 82.56% | 0.0180 | 6.75 dB |
| 2 | 92.99% | 0.0122 | 11.23 dB | |
| 3 | 91.66% | 0.0132 | 10.41 dB |
| View | RDE | RMSE | SNR | |
|---|---|---|---|---|
| MGSA algorithm | 39.71% | 0.0315 | 2.157 dB | |
| 41.72% | 0.0689 | 1.4513 dB | ||
| 40.23% | 0.0284 | 1.1362 dB | ||
| Phase encryption algorithm | 94.0% | 0.013 | 11.957 dB | |
| 91.4% | 0.0258 | 10.266 dB | ||
| 92.46% | 0.023 | 10.884 dB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chuang, C.-H.; Chen, C.-Y.; Chang, H.-T.; Lin, H.-Y.; Kuo, C.-F. Reducing Defocused-Information Crosstalk to Multi-View Holography by Using Multichannel Encryption of Random Phase Distribution. Appl. Sci. 2022, 12, 1413. https://doi.org/10.3390/app12031413
Chuang C-H, Chen C-Y, Chang H-T, Lin H-Y, Kuo C-F. Reducing Defocused-Information Crosstalk to Multi-View Holography by Using Multichannel Encryption of Random Phase Distribution. Applied Sciences. 2022; 12(3):1413. https://doi.org/10.3390/app12031413
Chicago/Turabian StyleChuang, Chih-Hao, Chien-Yu Chen, Hsuan-Ting Chang, Hoang-Yan Lin, and Chuan-Feng Kuo. 2022. "Reducing Defocused-Information Crosstalk to Multi-View Holography by Using Multichannel Encryption of Random Phase Distribution" Applied Sciences 12, no. 3: 1413. https://doi.org/10.3390/app12031413
APA StyleChuang, C.-H., Chen, C.-Y., Chang, H.-T., Lin, H.-Y., & Kuo, C.-F. (2022). Reducing Defocused-Information Crosstalk to Multi-View Holography by Using Multichannel Encryption of Random Phase Distribution. Applied Sciences, 12(3), 1413. https://doi.org/10.3390/app12031413






