Visualization System for Transparency Requirement Analytics
Abstract
1. Introduction
2. Literature Review
2.1. Background: Transparency Engineering
- Data transparency: A data transparency question (“what, when, where, or who?”) is one that has an answer that contains data, content, or information. For example, in a hosting service platform, data transparency reveals to the client the server performance and price for each plan.
- Process transparency: A process transparency question (“how?”) is one that has an answer that includes procedures, processes, behaviors, and interactions. For example, how data are encrypted in servers and how servers are immune to cyber attacks in a hosting service platform.
- Policy transparency: A policy transparency question (“why?”) has an answer that includes goals, intentions, and policies. For example, policy transparency in a hosting service platform reveals why encryption is required in servers or why users have limited storage capacity.
2.1.1. TranspLan Prototype
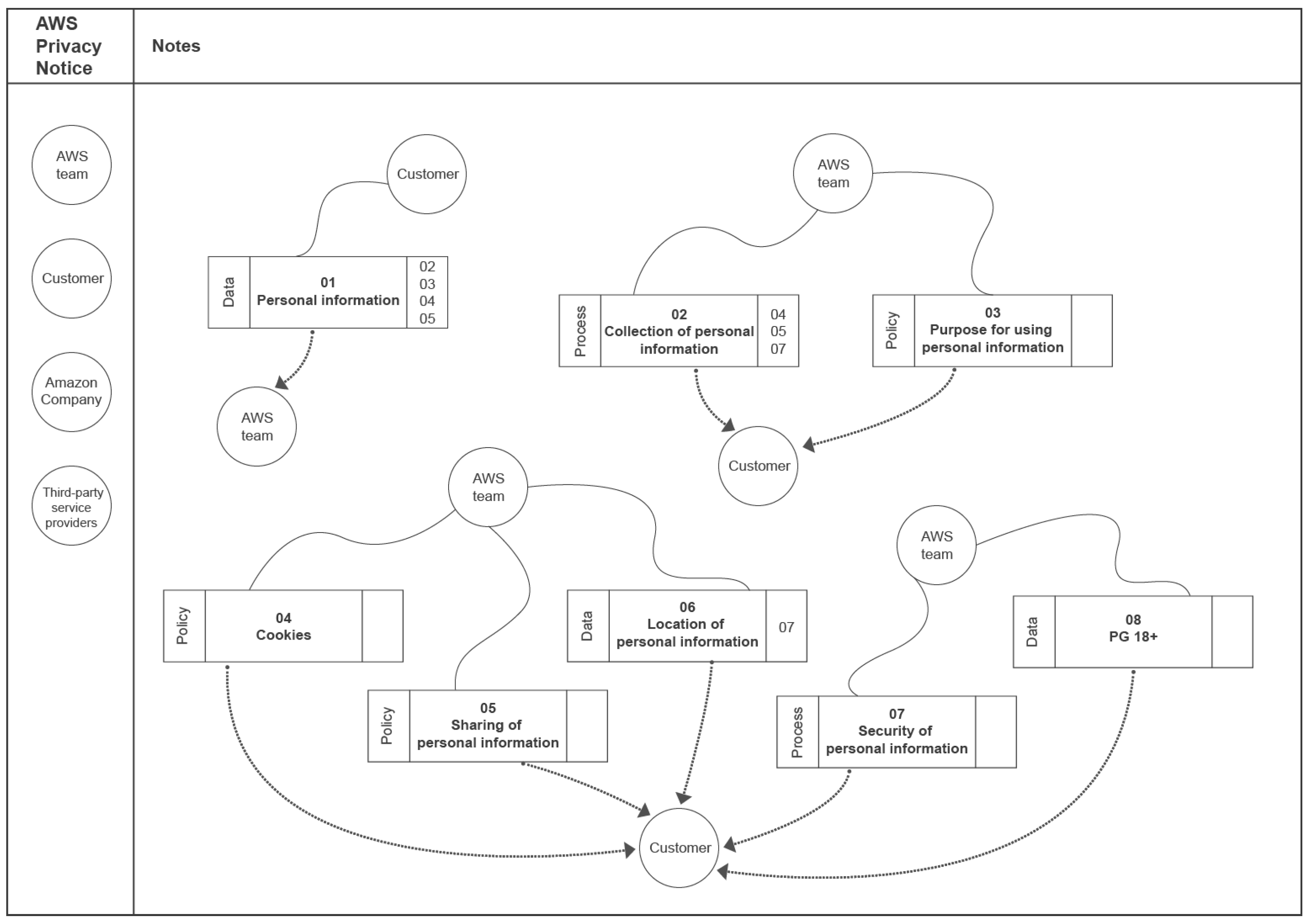
Shield Diagram
SitReq Specifications
- Stakeholder’s name is “customers”;
- IE label is “01”;
- IE name could be “personal information”;
- The relationship with the personal information is “producer”;
- The requirement description explains that customers should provide some personal information to use AWS applications“;
- The transparency requirement type of customer’s personal information could be ”optional“ (i.e., customers can provide or withhold the personal information);
- Transparency meaningfulness type of customer’s personal information is ”data“;
- Stakeholders involved with customer’s personal information could be ”AWS team“.
Infolet Specifications
2.1.2. TranspLan Limitations
- Manual generation: The Shield diagram, Infolet, and SitReq are manually generated by experts, which is time-consuming, difficult, and prone to errors and mismatches.
- Poor visual encoding: The current Shield diagram employs a visual encoding that includes only circles, lines, and rectangles with information redundancy (e.g., a stakeholder can be represented more than once and elements and relations on the diagram can be overwhelmingly overcrowded).
- Interactions: Another limitation is the diagram’s lack of interaction. An interactive graphical representation improves comprehension by allowing users to experiment with initial data and apply filters and visual encoding.
- Difficult for non-experts: Another limitation is that the current Shield diagram is only intended for experts. Non-experts in the transparency requirements domain, on the other hand, may find it difficult to understand the diagram because it employs a high level of visual encoding and technical terms that non-experts are unfamiliar with.
- Inadequate expression of transparency requirements: TranspLan is a prototype in which we cannot easily find relationship information, hierarchy in stakeholders, and the degree of importance of each transparency element, among others.
2.2. Visualization in Transparency Analytics: Related Work
3. Requirements Analysis
- [R1] Transparency keywords: As previously presented in Transparency Actors Wheel and Transparency Depth Pyramid, experts highlighted four keywords: data, process, policy, and stakeholders. These must be defined and presented in a tool for transparency.
- [R2] Information flow management: Using the Transparency Actors Wheel or TranspLan prototype, we should be able to specify ways of communicating information between keywords, such as information provider/receiver/none, and so on.
- [R3] Infolet representation: The proposed tool should enable the creation of a report containing information about keyword data interchange.
- [R4] SitReq representation: The proposed tool should enable the creation of reports containing information about stakeholders who have used the tool.
- [R5] Interactions: The proposed tool should be interactive.
4. TranspVis: The Proposed Visualization Tool for Transparency Analytics
4.1. TranspVis Database
4.2. Visual Structures
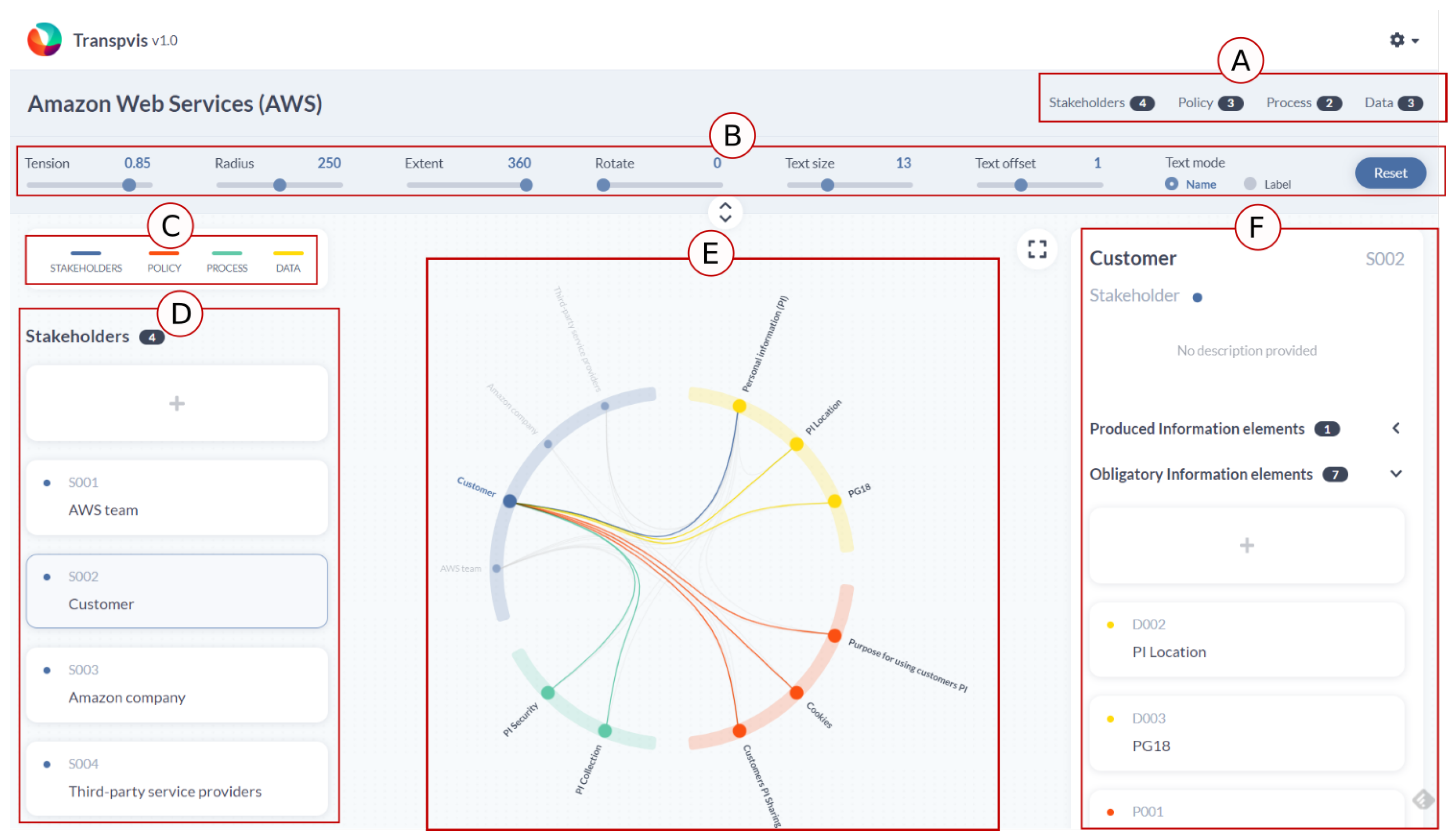
4.2.1. Circle View
4.2.2. Infolet Form
4.2.3. SitReq Form
4.3. Interactions
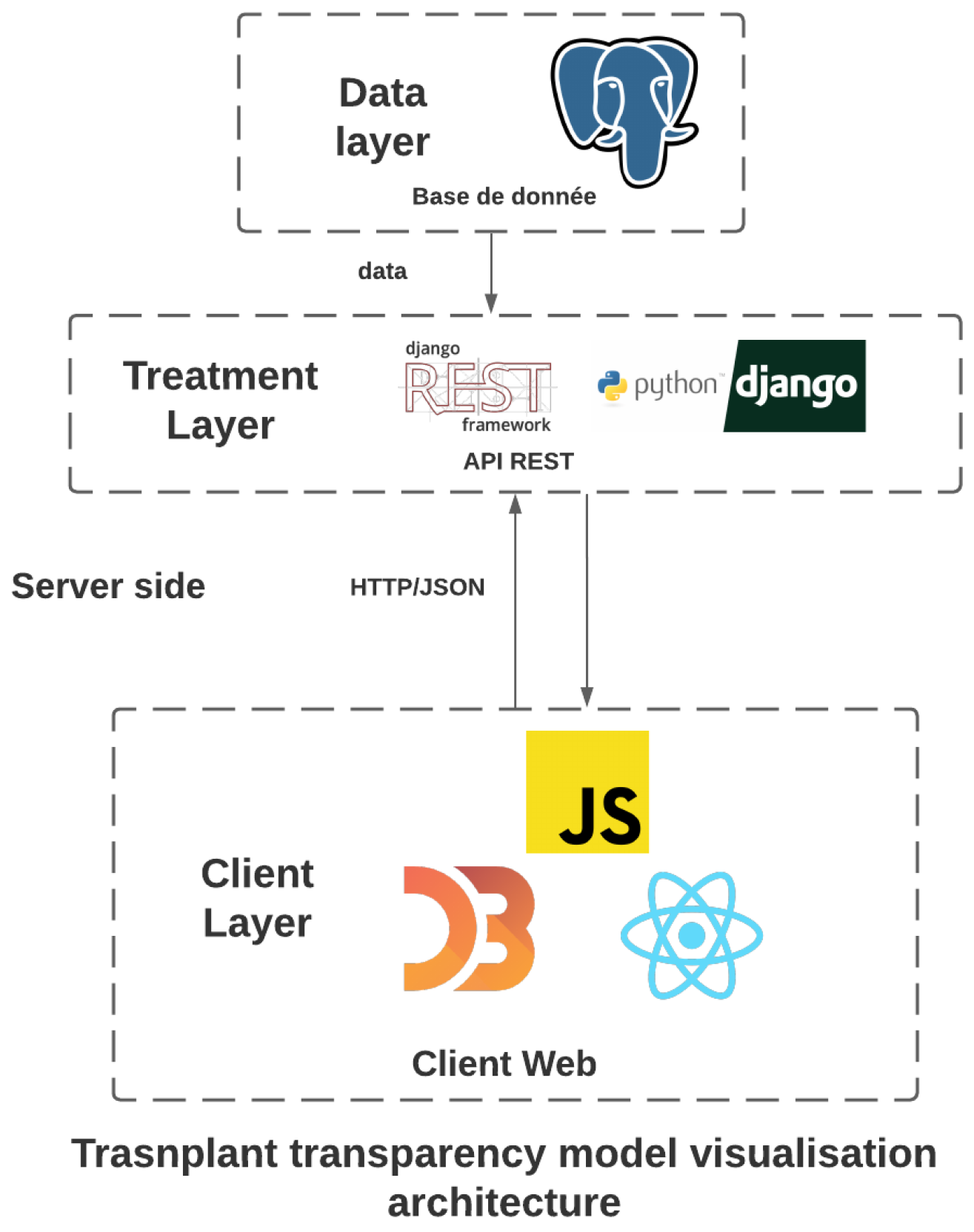
4.4. Technical Considerations
5. Evaluation
5.1. Experiment Data
- Understand the transparency framework: This is performed by identifying its various components: categories, keywords, their relationships, types of relationships, etc.
- Define the information source: Next, we identify a source of information that we should focus on in order to obtain the most valuable information for an in-depth study on transparency. This step concludes with the identification of a trustworthy source of information that satisfies our requirements, namely the privacy policies of these two companies, which meet all of our transparency requirements.
- Understanding the privacy policies: In this step, we investigate the privacy policies of (WhatsApp (https://www.whatsapp.com/legal/updates/privacy-policy/ [accessed on 1 December 2021]) and AWS (https://aws.amazon.com/privacy/ [accessed on 1 December 2021])) using their official privacy policy pages.
- Transparency framework applications: We extract necessary data and information after understanding the companies’ privacy policies by following a set of steps validated by an expert [5]. The following are the steps to take:
- Identifying stakeholders;
- Identifying information element;
- Generating SitReq specifications;
- Generating Infolet specifications.
5.2. Case Study
5.2.1. TranspLan Language
Amazon Web Services Privacy Policy
Identifying Stakeholders
- Customers;
- AWS team (the AWS service provider);
- Amazon company;
- Third-party service providers.
Identifying Information Elements
- Personal information (PI);
- PI collection;
- PI purpose;
- Cookies;
- PI sharing;
- PI location;
- PI security;
- PI children.
Shield Diagram/Infolet/SitReq
WhatsApp Privacy and Security
Identifying Stakeholders
- Customers;
- WhatsApp team.
Identifying Information Elements
- The personal messages (customers provide messages as data) (Data IE);
- WhatsApp end-to-end message encryption system (what kind of security is provided in sending messages with WhatsApp) (Data IE);
- The procedure of encrypting messages, (how WhatsApp encrypts messages with a lock, and only the recipient of the messages can unlock and read them using a special key, all of this being an automatic process) (Process IE);
- The purpose of using end-to-end encryption (why WhatsApp uses end-to-end encryption, which is to ensure the security and the integrity of their customers’ communication model) (Policy IE);
- The payment information provided by the customer (Data IE);
- The payment information (card and bank numbers) security (how customers’ payment information are stored, which is shown to be stored as encrypted and in a highly secured network) (Process IE);
- The location of end-to-end encrypted messages (what is the location of the customers’ messages, which is stated to be end-to-end encrypted messages being stored on customers’ device and not on WhatsApp servers after they are delivered) (Data IE).
Shield Diagram
5.2.2. TranspVis Solution
Evaluating Common Criteria
- [C1] Visual encoding: We focus on visual structures and how TranspVis helps specialists analyze their datasets. For instance, experts search for keyword repetition, circle size/centralization (when adding multiple new keywords/relationships), readability (text appearance), and the detection of incoming and outgoing relationships.
- [C2] Interactions: The synchronization of TranspVis could facilitate the analysis of Infolet and SitReq data by professionals.
- [C3] Insights extraction: We examine whether TranspVis reflects any valuable insights from the dataset represented.
AWS TranspVis Encoding
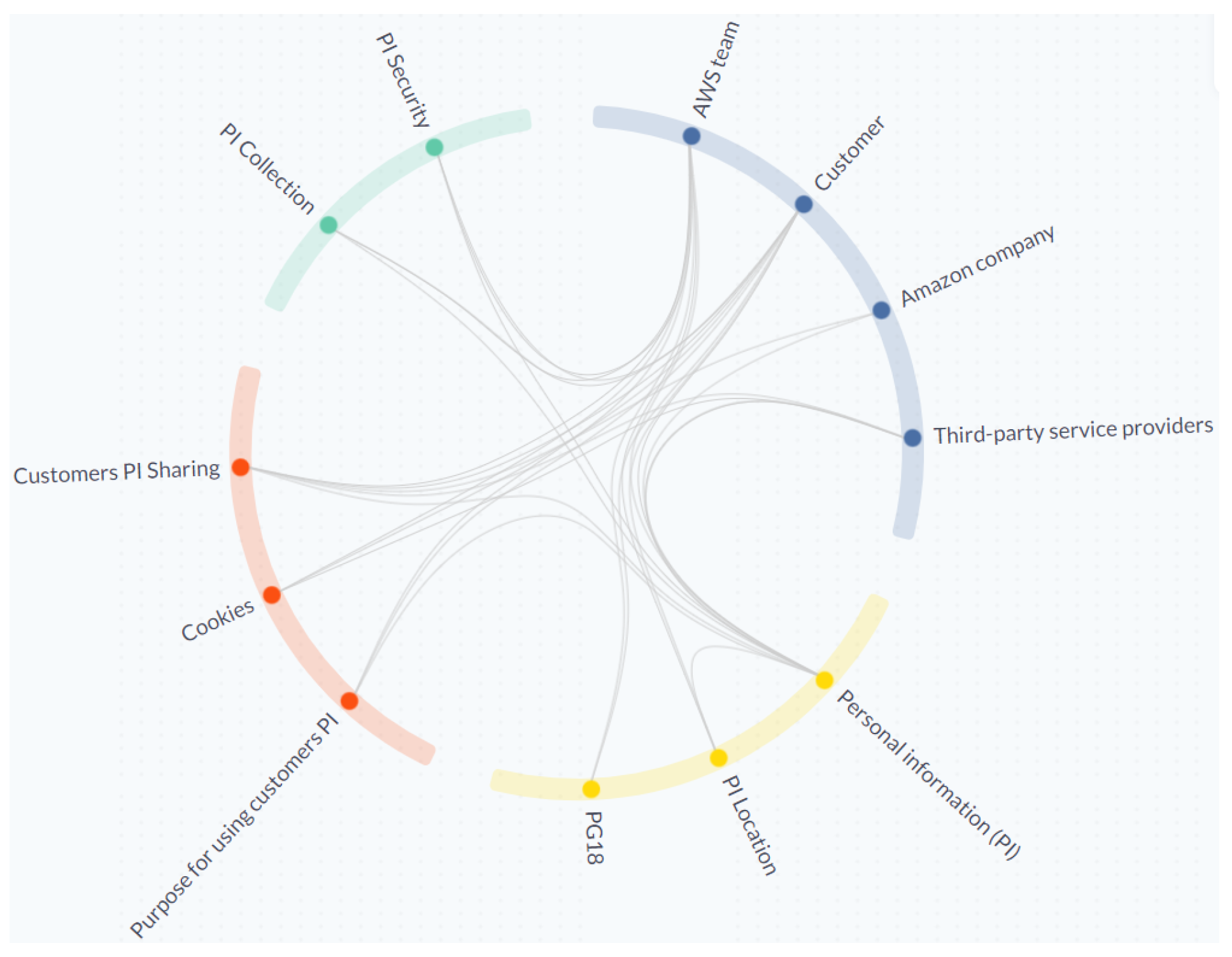
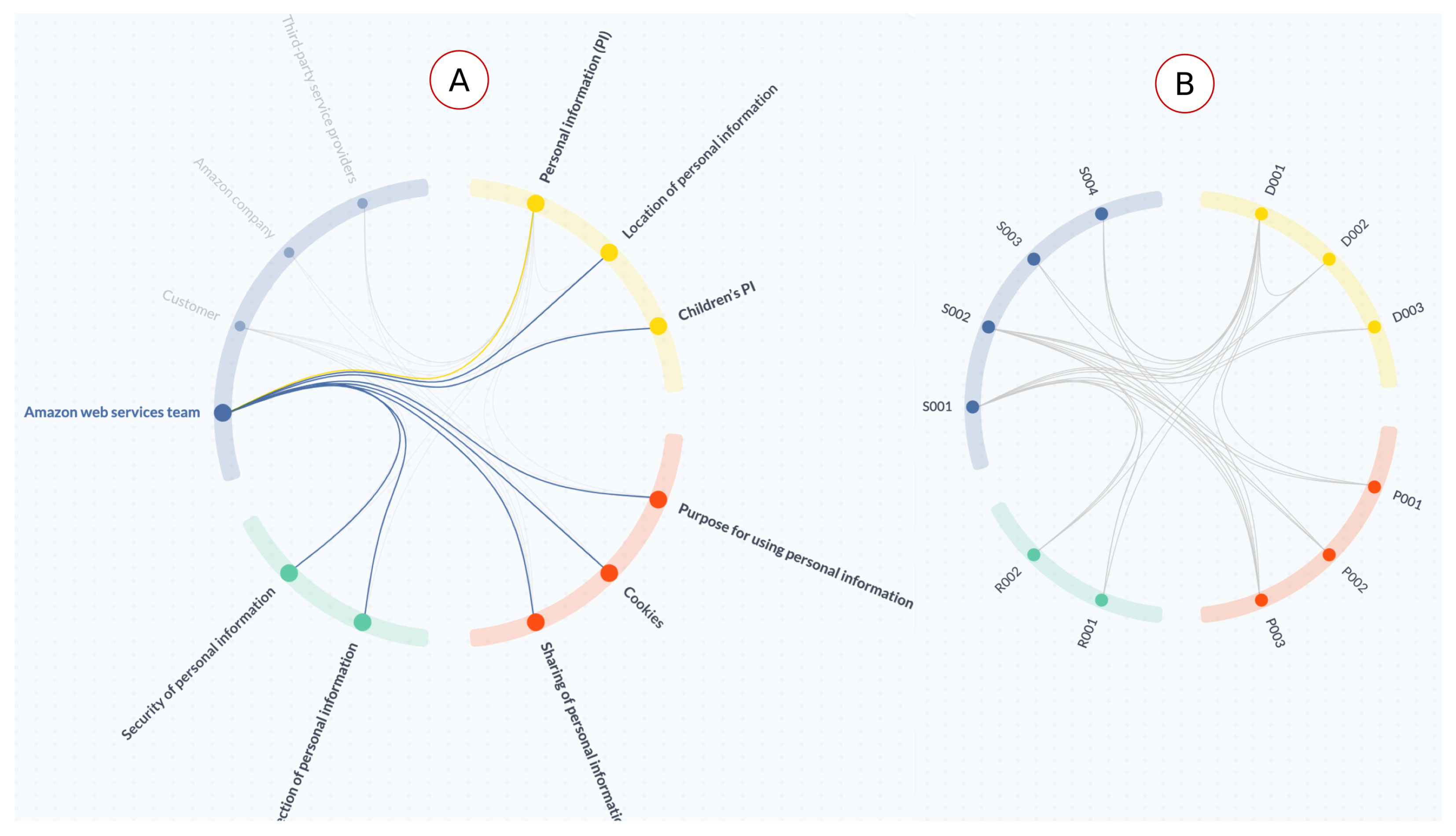
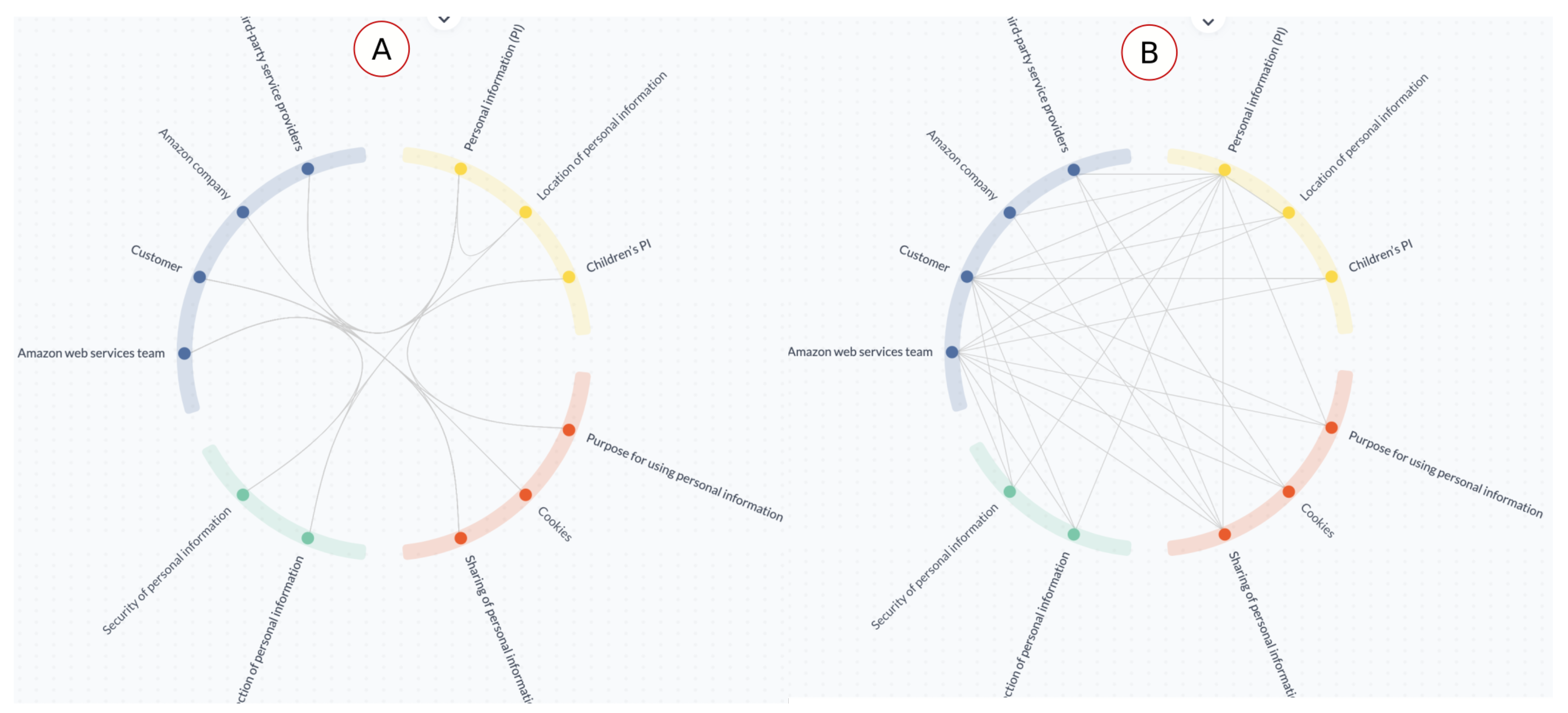
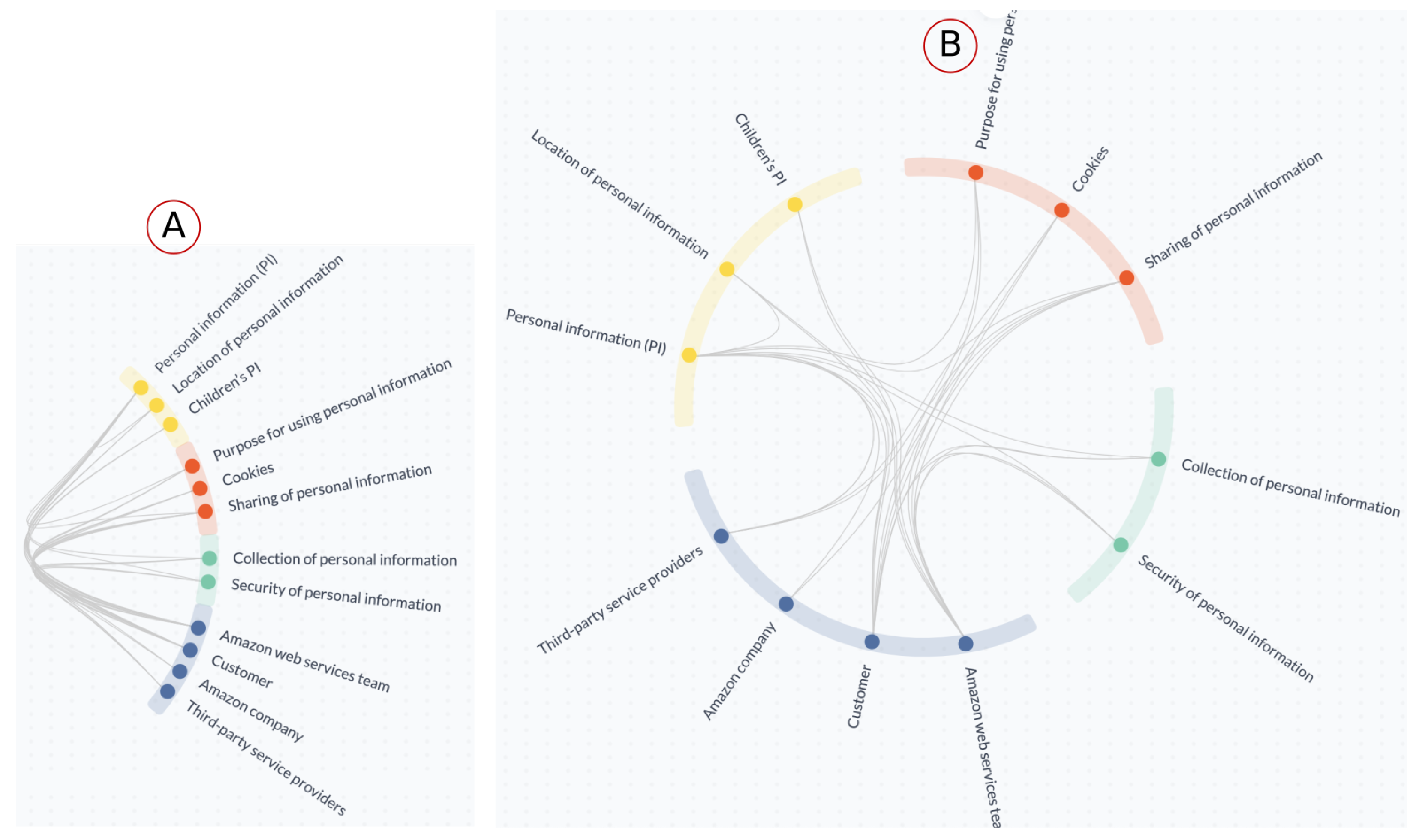
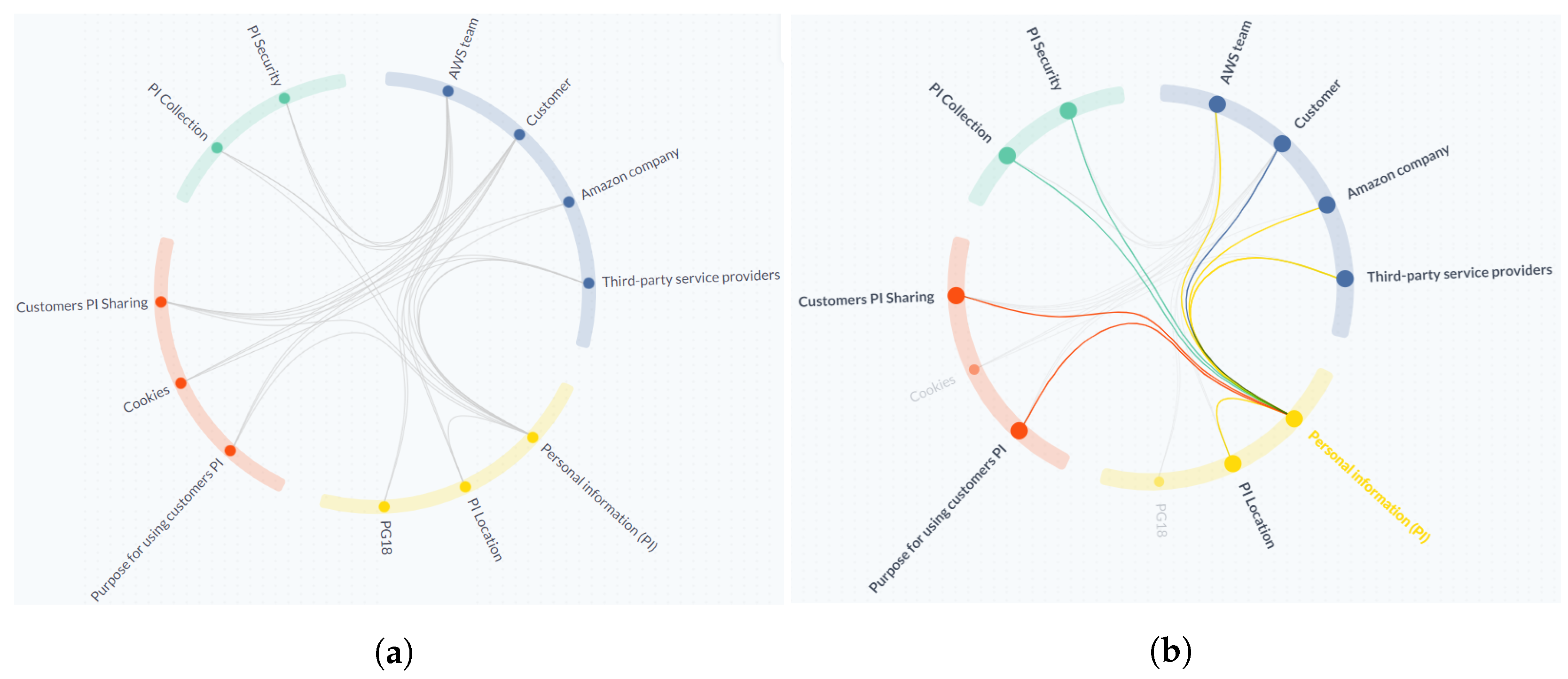
- [C1] Visual encoding: The Customer stakeholder was repeated twice in the AWS Shield diagram, but in TranspVis, selecting the Customer stakeholder will show both incoming and outgoing relations without the need for repetition. Furthermore, the Shield diagram is larger than the circle in TranspVis. TranspVis centralizes all keywords into a circle and controls the increased number of keywords/relationships in such a way that readability is not affected. Colors can also be used to quickly identify keywords and relationships. TranspVis text is readable, especially with the ability to rotate the circle to focus on specific labels.Figure 10a shows, for example, categories colored by unique colors and keywords within each category. We can easily see the four categories and the relationships between them.
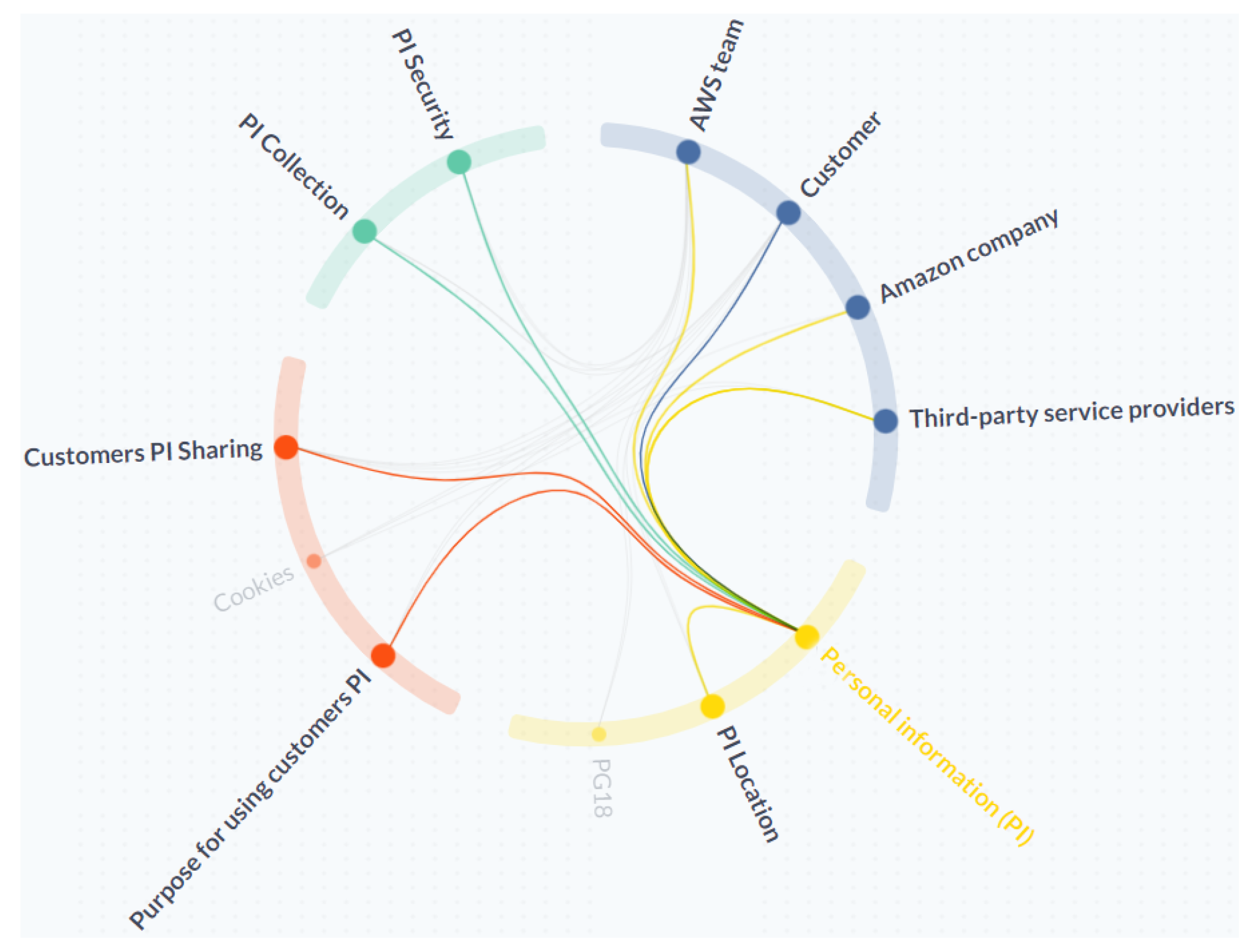
- [C2] Interactions: Removing/adding new keywords in TranspVis is possible with only one click, but in the Shield diagram, to remove the AWS Team stakeholder, you should remove them twice. Furthermore, mouse-over/click actions can assist experts in analyzing incoming and outgoing relationships.For example, Figure 10b shows the mouse-over action in “Personal Information (PI)” keyword. Experts can easily identify PI outgoing relationships as “AWS team,” “Amazon company”, “Third-party service provider”, and “PI location”. “Customer”, “PI security”, “PI collection”, “Customers PI sharing”, and “Purpose for using customers PI” are the incoming relations.
- [C3] Insights extraction: In TranspVis for AWS (as shown in Figure 10b), experts discover that “AWS team”, “Amazon company”, and “Third-party service provider” data are using “Personal Information (PI)” data, which may not be preferred by AWS users. These details were difficult for the expert to detect in the Shield diagram.
WhatsApp TranspVis encoding
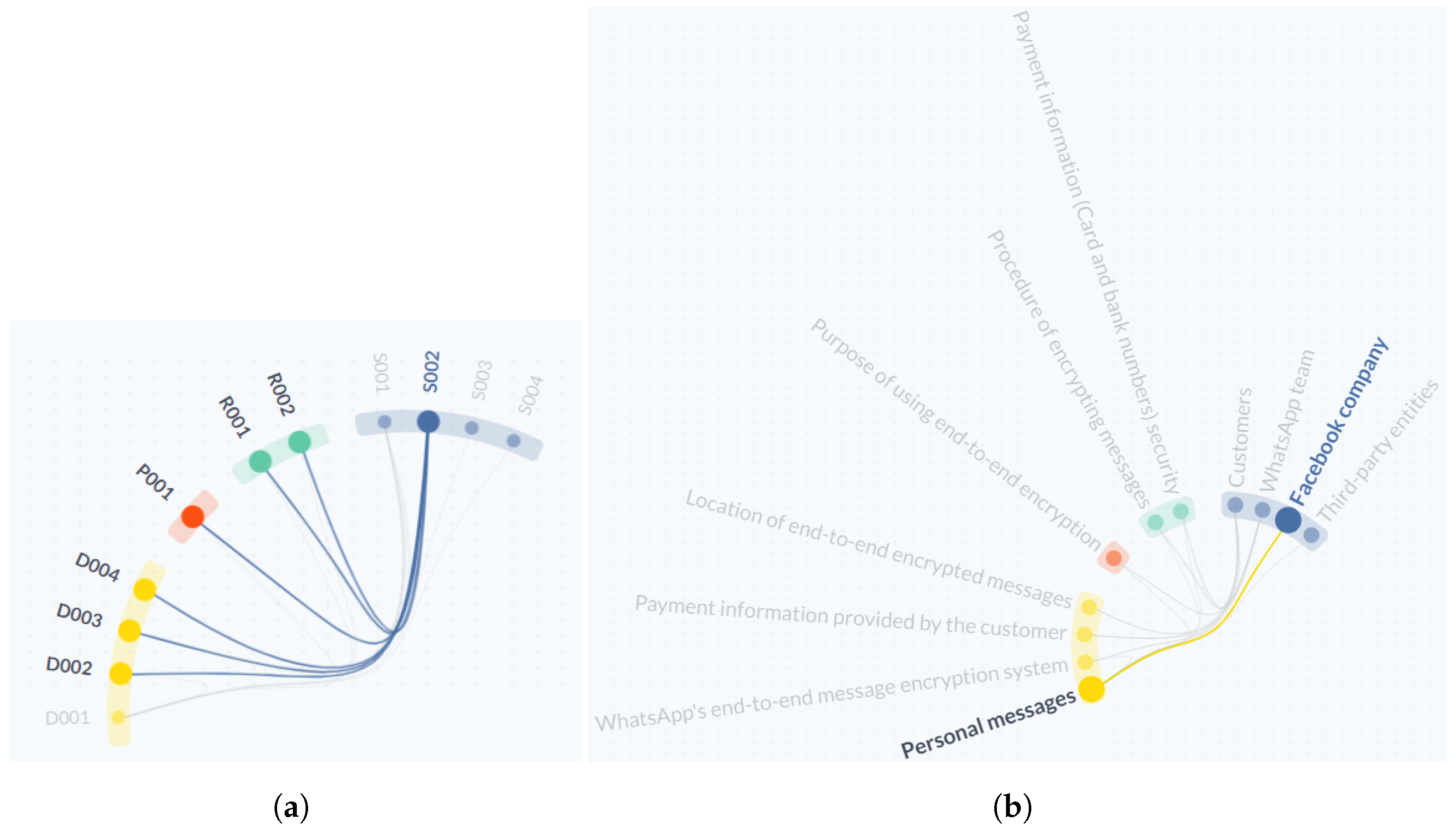
- [C1] Visual encoding: In the Shield diagram, the WhatsApp team stakeholder is repeated twice, and the customer stakeholder is repeated three times. All incoming and outgoing relationships in the TranspVis circles are linked to the unique appearance of these two stakeholders in the main circle. Other visual structure notes are the same as AWS visual encoding (see Figure 11).
- [C2] Interactions: “WhatsApp team” (S002) stakeholder is a source for six IEs, but the Shield diagram does not reflect this information easily. For TranspVis, in Figure 12a, it shows this information from a circle view by just selecting the “WhatsApp team” keyword.
- [C3] Insights extraction: Expert can easily detect serious outgoing and incoming relations and keywords using TranspVis. For example, in Figure 12b, the expert can easily notice that “Facebook company” is a stakeholder in WhatsApp company and that it uses WhatsApp company “Personal messages”.
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Stakeholder’s Information Transparency REQuirements Specification (SitReq) | ||||||
|---|---|---|---|---|---|---|
| Stakeholder’s Name: Customer | ||||||
| IE Label | IE Name | Relationship | Requirement Description | Transparency Requirement Type | Transparency Meaningfulness Type | Stakeholders Involved |
| 01 | Personal information | Producer | Customer should provide some personal information in order to use the AWS services | Optional | Data | AWS team |
| 02 | PI collection | Receiver | AWS team provides some processes about how they collect personal data of users | Coercive | Process | AWS team |
| 03 | PI using purpose | Receiver | AWS team provides policies and why they are using users personal information | Coercive | Policy | AWS team |
| 04 | Cookies | Receiver | AWS team provides policies about using users cookies, and how it works | Coercive | Policy | AWS team |
| 05 | PI sharing | Receiver | AWS team provides policies about why and how they are sharing users personal information | Coercive | Policy | AWS team, Amazon Company, Third-party service providers |
| 06 | Location of PI | Receiver | AWS team must provide data about the location of users personal information | Coercive | Data | AWS team |
| 07 | PI security | Receiver | AWS team must provide policies about how they are securing personal information | Coercive | Policy | AWS team |
| 08 | PI children | Receiver | AWS team provides data about children use of the aws services | Coercive | Data | AWS team |
| INFOrmation eLEment Transparency Specification (Infolet) | ||
|---|---|---|
| Information Element (IE) Label 01 | Information Element (IE) Name Personal information | Information Element (IE) Type Process |
| Information Element Description This information element contains the customer’s personal information. This includes name, email address, physical address, and payment records, such as credit card and bank account numbers, as well as other related contact information. | ||
| List of Other Information Elements Using This Information Element (2) PI collection (3) Purpose for using PI (5) PI sharing | ||
| Information Element Creator/Authority Customer | ||
| Information Element Provider Customer | ||
| List of Stakeholders Receiving Information Element and Information Element Provision Type N/A | ||
| List of Stakeholders Requesting Information Element and Information Element Request Type N/A | ||
| List of Stakeholders with Restricted Access to Information Element and Restriction Type N/A | ||
| Information Element Notes N/A | ||
| INFOrmation eLEment Transparency Specification (Infolet) | ||
|---|---|---|
| Information Element (IE) Label 02 | Information Element (IE) Name PI collection | Information Element (IE) Type Process |
| Information Element Description This information element contains how the AWS team collects information about customers, using the information provided by them, automatic information, or information from public sources. | ||
| List of Other Information Elements Using This Information Element (4) The purpose for using PI (5) PI sharing | ||
| Information Element Creator/Authority AWS team | ||
| Information Element Provider AWS team | ||
| List of Stakeholders Receiving Information Element and Information Element Provision Type N/A | ||
| List of Stakeholders Requesting Information Element and Information Element Request Type N/A | ||
| List of Stakeholders with Restricted Access to Information Element and Restriction Type N/A | ||
| Information Element Notes N/A | ||
| INFOrmation eLEment Transparency Specification (Infolet) | ||
|---|---|---|
| Information Element (IE) Label 05 | Information Element (IE) Name PI sharing | Information Element (IE) Type Policy |
| Information Element Description This information element contains how personal information sharing works, AWS uses other third-party service providers, but they make sure that personal information is secure and share only related data. | ||
| List of Other Information Elements Using This Information Element N/A | ||
| Information Element Creator/Authority AWS team | ||
| Information Element Provider AWS team | ||
| List of Stakeholders Receiving Information Element and Information Element Provision Type Customer | ||
| List of Stakeholders Requesting Information Element and Information Element Request Type N/A | ||
| List of Stakeholders with Restricted Access to Information Element and Restriction Type N/A | ||
| Information Element Notes N/A | ||
| INFOrmation eLEment Transparency Specification (Infolet) | ||
|---|---|---|
| Information Element (IE) Label 08 | Information Element (IE) Name PI children | Information Element (IE) Type Data |
| Information Element Description This information element says that AWS offerings are not meant for children. If a customer is under 18, only with the intervention of a parent or guardian can they use AWS Offers. | ||
| List of Other Information Elements Using This Information Element N/A | ||
| Information Element Creator/Authority AWS team | ||
| Information Element Provider AWS team | ||
| List of Stakeholders Receiving Information Element and Information Element Provision Type Customer | ||
| List of Stakeholders Requesting Information Element and Information Element Request Type N/A | ||
| List of Stakeholders with Restricted Access to Information Element and Restriction Type N/A | ||
| Information Element Notes N/A | ||

References
- Hosseini, M.; Shahri, A.; Phalp, K.; Ali, R. A modelling language for transparency requirements in business information systems. In Proceedings of the International Conference on Advanced Information Systems Engineering, Ljubljana, Slovenia, 13–17 June 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 239–254. [Google Scholar]
- Casey, S. How millennial are you? PM World J. 2015, 4, 239–254. [Google Scholar]
- Castells, M. End of Millennium, The Information Age: Economy, Society and Culture; John Wiley & Sons, Ltd.: New York, NY, USA, 1998; Volume 3. [Google Scholar]
- Kim, M.; Ly, K.; Soman, D. A Behavioural Lens on Consumer Privacy; Rotman School of Management: Toronto, ON, Canada, 2015; pp. 1–40. [Google Scholar]
- Hosseini, M.; Shahri, A.; Phalp, K.; Ali, R. Engineering transparency requirements: A modelling and analysis framework. Inf. Syst. 2018, 74, 3–22. [Google Scholar] [CrossRef]
- Fekete, J.; van Wijk, J.J.; Stasko, J.T.; North, C. The Value of Information Visualization. In Information Visualization—Human-Centered Issues and Perspectives; Springer: Berlin/Heidelberg, Germany, 2008; pp. 1–18. [Google Scholar]
- Fung, A. Infotopia: Unleashing the democratic power of transparency. Politics Soc. 2013, 41, 183–212. [Google Scholar] [CrossRef]
- Albu, O.B.; Flyverbom, M. Organizational transparency: Conceptualizations, conditions, and consequences. Bus. Soc. 2019, 58, 268–297. [Google Scholar] [CrossRef]
- Hosseini, M.; Shahri, A.; Phalp, K.T.; Ali, R. Transparency as a requirement. In Proceedings of the Joint Proceedings of REFSQ-2015 Workshops, Research Method Track, and Poster Track colocated with the 21st International Conference on Requirements Engineering: Foundation for Software Quality (REFSQ), Essen, Germany, 23–26 March 2015. [Google Scholar]
- Hosseini, M.; Shahri, A.; Phalp, K.; Ali, R. Towards engineering transparency as a requirement in socio-technical systems. In Proceedings of the 2015 IEEE 23rd International Requirements Engineering Conference (RE), Ottawa, ON, Canada, 24–28 August 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 268–273. [Google Scholar]
- Bannister, F.; Connolly, R. The trouble with transparency: A critical review of openness in e-government. Policy Internet 2011, 3, 1–30. [Google Scholar] [CrossRef]
- Keim, D.; Andrienko, G.; Fekete, J.D.; Görg, C.; Kohlhammer, J.; Melançon, G. Visual analytics: Definition, process, and challenges. In Information Visualization; Springer: Berlin/Heidelberg, Germany, 2008; pp. 154–175. [Google Scholar]
- Lavigne, V.; Gouin, D. Visual analytics for cyber security and intelligence. J. Def. Model. Simul. 2014, 11, 175–199. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, J.; Zhang, B. Visual analysis of cybersecurity situational awareness. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 685–688. [Google Scholar]
- Wang, X.; Chen, W.; Chou, J.; Bryan, C.; Guan, H.; Chen, W.; Pan, R.; Ma, K. GraphProtector: A Visual Interface for Employing and Assessing Multiple Privacy Preserving Graph Algorithms. IEEE Trans. Vis. Comput. Graph. 2019, 25, 193–203. [Google Scholar] [CrossRef] [PubMed]
- DeHart, J.; Stell, M.; Grant, C. Social Media and the Scourge of Visual Privacy. Information 2020, 11, 57. [Google Scholar] [CrossRef]
- Chou, J.K.; Wang, Y.; Ma, K.L. Privacy preserving visualization: A study on event sequence data. In Proceedings of the Computer Graphics Forum; Wiley Online Library: Hoboken, NJ, USA, 2019; Volume 38, pp. 340–355. [Google Scholar]
- Ghazinour, K.; Majedi, M.; Barker, K. A model for privacy policy visualization. In Proceedings of the 2009 33rd Annual IEEE International Computer Software and Applications Conference, Seattle, WA, USA, 20–24 July 2009; IEEE: Piscataway, NJ, USA, 2009; Volume 2, pp. 335–340. [Google Scholar]
- Ghazinour, K.; Albalawi, T. A usability study on the privacy policy visualization model. In Proceedings of the 2016 IEEE 14th International Conference on Dependable, Autonomic and Secure Computing, 14th International Conference on Pervasive Intelligence and Computing, 2nd International Conference on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), Auckland, New Zealand, 8–12 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 578–585. [Google Scholar]
- Jutla, D.N.; Bodorik, P.; Ali, S. Engineering privacy for big data apps with the unified modeling language. In Proceedings of the 2013 IEEE International Congress on Big Data, Silicon Valley, CA, USA, 6–9 October 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 38–45. [Google Scholar]
- Cook, K.A.; Thomas, J.J. Illuminating the Path: The Research and Development Agenda for Visual Analytics; IEEE Computer Society Press: Piscataway, NJ, USA, 2005. [Google Scholar]
- Sedlmair, M.; Meyer, M.; Munzner, T. Design study methodology: Reflections from the trenches and the stacks. IEEE Trans. Vis. Comput. Graph. 2012, 18, 2431–2440. [Google Scholar] [CrossRef] [PubMed]
- Silva, S.; Santos, B.S.; Madeira, J. Using color in visualization: A survey. Comput. Graph. 2011, 35, 320–333. [Google Scholar] [CrossRef]
- Gramazio, C.C.; Laidlaw, D.H.; Schloss, K.B. Colorgorical: Creating discriminable and preferable color palettes for information visualization. IEEE Trans. Vis. Comput. Graph. 2016, 23, 521–530. [Google Scholar] [CrossRef] [PubMed]
- Popleteev, A.; Louveton, N.; McCall, R. Colorizer: Smart glasses aid for the colorblind. In Proceedings of the 2015 Workshop on Wearable Systems and Applications, Florence, Italy, 18 May 2015; pp. 7–8. [Google Scholar]
- Zhou, H.; Xu, P.; Yuan, X.; Qu, H. Edge bundling in information visualization. Tsinghua Sci. Technol. 2013, 18, 145–156. [Google Scholar] [CrossRef]
- Munzner, T. A nested model for visualization design and validation. IEEE Trans. Vis. Comput. Graph. 2009, 15, 921–928. [Google Scholar] [CrossRef] [PubMed]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fadloun, S.; Meshoul, S.; Hosseini, M.; Amokrane, A.; Bennaceur, H. Visualization System for Transparency Requirement Analytics. Appl. Sci. 2022, 12, 12423. https://doi.org/10.3390/app122312423
Fadloun S, Meshoul S, Hosseini M, Amokrane A, Bennaceur H. Visualization System for Transparency Requirement Analytics. Applied Sciences. 2022; 12(23):12423. https://doi.org/10.3390/app122312423
Chicago/Turabian StyleFadloun, Samiha, Souham Meshoul, Mahmood Hosseini, Abdennour Amokrane, and Hichem Bennaceur. 2022. "Visualization System for Transparency Requirement Analytics" Applied Sciences 12, no. 23: 12423. https://doi.org/10.3390/app122312423
APA StyleFadloun, S., Meshoul, S., Hosseini, M., Amokrane, A., & Bennaceur, H. (2022). Visualization System for Transparency Requirement Analytics. Applied Sciences, 12(23), 12423. https://doi.org/10.3390/app122312423







