High-Performance Actionable Knowledge Miner for Boosting Business Revenue
Abstract
1. Introduction
1.1. Net Promoter Score
1.2. Customer Relationship Management and Decision Support
1.3. Recommender Systems
1.3.1. Recommender System for B2B
1.3.2. NPS-Based Recommender System
1.4. Distributed Data Mining
2. Methods
2.1. Scalability Issues
Business Requirements
- It should be scalable to add more than the current number of 38 companies.
- Up to date—the system’s models should be updated regularly once new data become available, typically once every six months.
- Update of the models should be time-constrained—should not take more than a day (and around half an hour per company).
- Sources: a user can choose the type of survey—whether service, parts, rentals, etc.—that would be used for the recommender system algorithm.
- Timeframe—a user should be able to choose the timeframe for the recommender algorithm’s input: for example, a yearly timeframe, bi-yearly, etc.
- Data preprocessing measures, including handling NULL value and binning the Promoter Status attribute.
- Limiting the number of semantic neighbors in the hierarchical clustering procedure to limit the size of the datasets.
- Setting constraints on the patterns to be mined, by modifying the action rule mining algorithm.
- Implementing distributed action rule mining.
2.2. Dataset
- Quantitative data (structured data)—numbers/scores for questions (benchmarks) that ask customers to “On a scale of 1 to 10, rate…”.
- Qualitative data (unstructured data)—text comments, where customers express their opinions, feelings, and thoughts in a free form.
2.3. Action Rules
Application of Action Rules to Improve NPS
| Listing 1. An example of an action rule applied to customer survey data. |
| ((Benchmark: Repair Completed When Promised, (3->8)) |
| AND (Benchmark: Dealer Communication, (1->10))) => |
| (Detractor->Promoter) sup=4.0, conf=95.0 |
2.4. Data Preprocessing
2.5. User Interface
2.6. Hierarchical Clustering
2.7. Actionable Knowledge Miner
2.8. Text Mining
2.8.1. Meta-Actions
| Algorithm 1 Initial procedure for action rule triggering. |
|
2.8.2. Triggering
2.9. Recommendation Generation
2.10. Improved Data Preprocessing
- Low: <0,4>;
- Medium: <5,6>;
- High: <7,8>;
- Very high: <9,10>.
2.11. Improved HAMIS Strategy
2.12. Improved Pattern Mining
| Listing 2. An example of “Rule—Type 0” |
| ((Benchmark: Likelihood Repeated Customer, 2->10)) AND |
| (Benchmark: Ease of Contact, 4->5)) => (Detractor->Promoter) |
| sup = 3, conf = 98.0 |
| Listing 3. An example of An example of “Rule—Type 1”. |
| ((Benchmark: Tech Equipped to do Job, 3->higher)) AND |
| (Benchmark: Repair Timely, 3->higher)) |
| => (Detractor->Promoter) sup = 3, conf = 100.0 |
2.12.1. Modifications in the Recommender System
| Algorithm 2 The modified triggering procedure to process Rule—Type 1. |
|
2.13. A Distributed Algorithm for the Mining of Action Rules
| Algorithm 3 Algorithm for distributed action rules mining: ARE (A, ,). |
Input: A is data of type (), DF is a decision from, and DT is a decision to
|
3. Results
3.1. Experimental Setup
- Mining times.
- The number of action rules extracted.
- The number of distinct customers covered by the rules.
- Reading in the company’s action rule output file and processing it in the recommendation algorithm. We kept track of the triggering process and recorded the set of recommendations that produced the best NPS effect.
- We defined the base performance as that referring to the algorithm without any above-described modifications.
- We performed the initial testing on a dataset from one year, and then the primary testing on the dataset from the following year.
3.2. Test Cases
- Size:
- –
- Small datasets (200–300 rows);
- –
- Medium datasets (1100 rows);
- –
- Large (6000 rows);
- –
- The largest (10,000 rows).
- Modification 1 (binning benchmark values into categories)
- –
- Original benchmark values (numerical);
- –
- Categorized ranges of benchmark values.
- Type of the rule’s right-hand-side definition:
- –
- Detractor→ Promoter;
- –
- Passive→ Promoter.
- Modification 3 (rule type)
- –
- Base rule type: downwards changes allowed;
- –
- Rule—Type 0—allowing only changes upwards;
- –
- Rule—Type 1—atomic actions can suggest changes to any higher value in benchmark scores.
- Modification 4 (original vs. distributed implementation)
- –
- Nonparallel (original) implementation (implemented in Java);
- –
- Parallel action rule mining reimplemented using the Spark technology.
3.3. Experiments
3.3.1. Small Datasets
Passive to Promoter
3.3.2. Medium Datasets
Detractor to Promoter
Passive to Promoter
3.3.3. Distributed Algorithm for Mining Rules
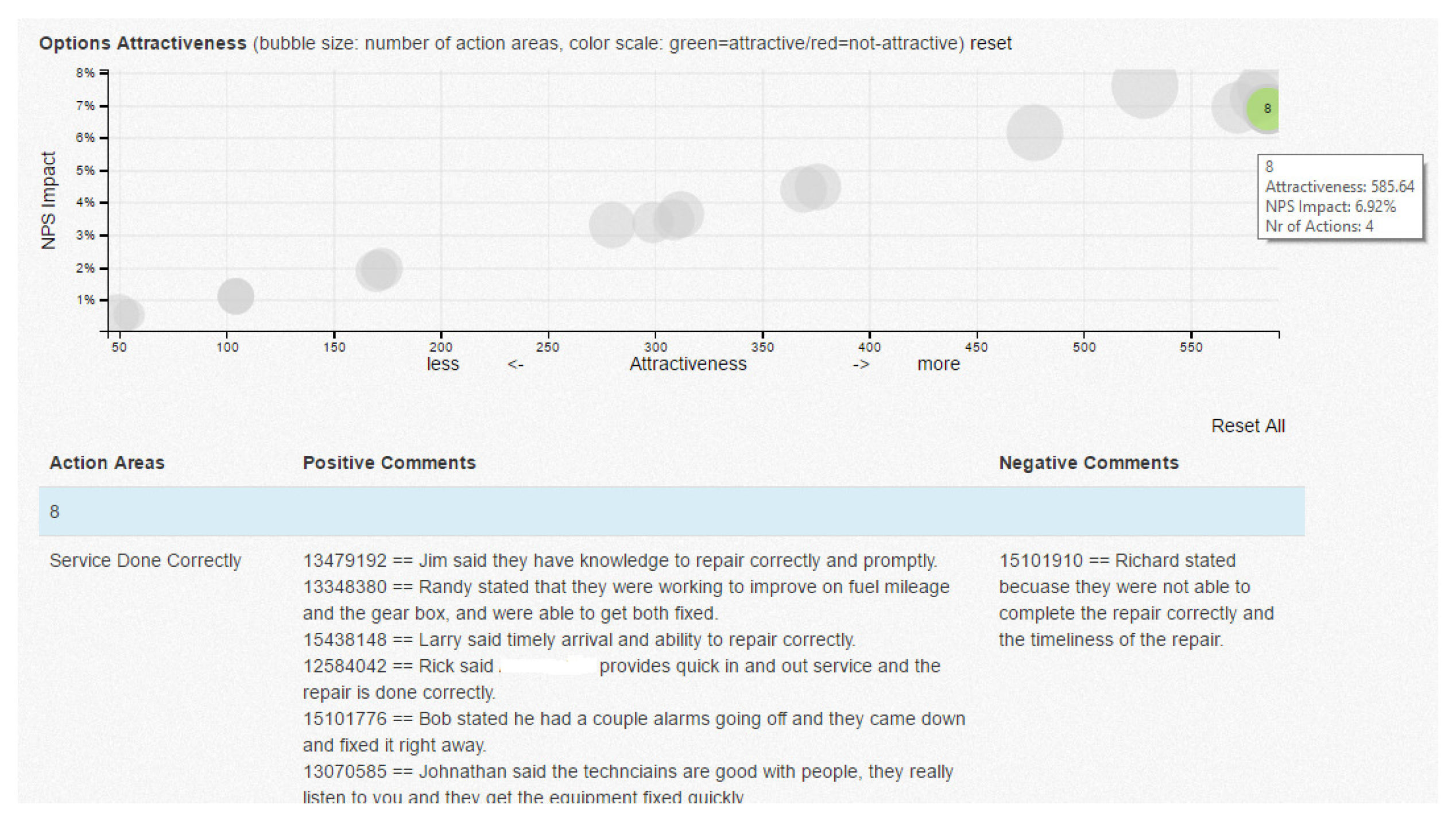
3.3.4. Recommendation Algorithm Testing
Evaluation Metrics
- a
- Action rules extracted—the total number of action rules extracted with the Miner (including redundant ones).
- b
- Action rules read into RS—action rules that were actually used for the knowledge base of the system (after removing redundant ones and transformation).
- c
- Redundancy ratio (a/b)—action rules extracted versus actually used in the system.
- d
- Atomic actions—the total number of distinct atomic actions from all action rules.
- e
- Atomic actions triggered—atomic actions that have associated meta-actions.
- f
- Triggered action rules—action rules for which all the atomics have been triggered.
- g
- Ratio of the rules triggered to the rules read into the system (f/b).
- h
- Meta-actions extracted—the total number of distinct meta-actions extracted from the customers’ comments.
- i
- Effective meta-nodes—meta-nodes created by combining different meta-actions to obtain the highest effect on NPS.
- j
- Max NPS impact—the maximal impact on the Net Promoter Score from the optimal meta-node (that is, the NPS impact of the optimal meta-node).
4. Discussion
4.1. Small Datasets
4.2. Medium Datasets
4.3. Distributed Algorithm
4.4. Impact on Recommendations
5. Conclusions
5.1. Limitations
- Modifying the procedure to generate a greater variety of recommendations with Rule—Type 1. One solution to investigate includes applying a “relaxed” triggering strategy.
- More comprehensive testing—this work did not thoroughly test times for large and very large datasets of companies because the mining runs for days/weeks and is not machine-fault-tolerant.
- Further modifications in the algorithm for distributed action rule mining.
- Testing alternative mining tools such as LispMiner, which is known to efficiently extract rules due to the efficient algorithm based on the so-called GUHAprocedure [38].
5.2. Contribution and Future Work
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- The Daniel Group. Using Customer Feedback to Improve Customer Experience. Available online: http://info.thedanielgroup.com/using-customer-feedback-improve-experience (accessed on 20 November 2022).
- Hausman, A.; Noori, B.; Hossein, S.M. A decision-support system for business-to-business marketing. J. Bus. Ind. Mark. 2005, 20, 226–236. [Google Scholar]
- Hosseini, S. A decision support system based on machined learned Bayesian network for predicting successful direct sales marketing. J. Manag. Anal. 2021, 8, 295–315. [Google Scholar] [CrossRef]
- Bobadilla, J.; Ortega, F.; Hernando, A.; Gutierrez, A. Recommender systems survey. Knowl. Based Syst. 2013, 46, 109–132. [Google Scholar]
- Guo, L.; Liang, J.; Zhu, Y.; Luo, Y.; Sun, L.; Zheng, X. Collaborative filtering recommendation based on trust and emotion. J. Intell. Inf. Syst. 2019, 53, 113–135. [Google Scholar] [CrossRef]
- Mesas, R.M.; Bellogin, A. Exploiting recommendation confidence in decision-aware recommender systems. J. Intell. Inf. Syst. 2020, 54, 45–78. [Google Scholar] [CrossRef]
- Ricci, F.; Rokach, L.; Shapira, B. Recommender Systems Handbook, 2nd ed.; Springer: Boston, MA, USA, 2015. [Google Scholar]
- Shokeen, J.; Rana, C. Social recommender systems: Techniques, domains, metrics, datasets and future scope. J. Intell. Inf. Syst. 2020, 54, 633–667. [Google Scholar] [CrossRef]
- Dara, S.; Chowdary, C.R.; Kumar, C. An survey on group recommender systems. J. Intell. Inf. Syst. 2020, 54, 271–295. [Google Scholar] [CrossRef]
- Li, L.; Chen, L.; Dong, R. CAESAR: Context-aware explanation based on supervised attention for service recommendations. J. Intell. Inf. Syst. 2021, 57, 147–170. [Google Scholar] [CrossRef]
- Felfernig, A.; Polat-Erdeniz, S.; Uran, C. An overview of recommender systems in the internet of things. J. Intell. Inf. Syst. 2019, 52, 285–309. [Google Scholar] [CrossRef]
- Stratigi, M.; Pitoura, E.; Nummenmaa, J. Sequential group recommendations based on satisfaction and disagreement scores. J. Intell. Inf. Syst. 2022, 58, 227–254. [Google Scholar] [CrossRef]
- Tarnowska, K.A.; Ras, Z.W.; Jastreboff, P.J. Decision Support System for Diagnosis and Treatment of Hearing Disorders—The Case of Tinnitus; Studies in Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Duan, L.; Street, W.N.; Xu, E. Healthcare information systems: Data mining methods in the creation of a clinical recommender system. Enterp. Inf. Syst. 2011, 5, 169–181. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, H. Study on recommender systems for business-to-business electronic commerce. Commun. IIMA 2005, 5, 46–48. [Google Scholar]
- Tarnowska, K.; Ras, Z.W.; Daniel, L. Recommender System for Improving Customer Loyalty; Studies in Big Data; Springer: Berlin/Heidelberg, Germany, 2020; Volume 55. [Google Scholar]
- Ras, Z.W.; Wieczorkowska, A. Action Rules: How to Increase Profit of a Company. In Proceedings of the PKDD’00, Lyon, France, 13–16 September 2000; LNAI, No. 1910. Springer: Berlin/Heidelberg, Germany, 2000; pp. 587–592. [Google Scholar]
- Dardzinska, A.; Ras, Z.W. Extracting Rules from Incomplete Decision Systems: System ERID. In Foundations and Novel Approaches in Data Mining; Lin, T.Y., Ohsuga, S., Liau, C.J., Hu, X., Eds.; Advances in Soft Computing; Springer: Berlin/Heidelberg, Germany, 2006; Volume 9, pp. 143–154. [Google Scholar]
- Ras, Z.W.; Tsay, L.S. Discovering Extended Action-Rules (System DEAR). In Proceedings of the Intelligent Information Processing and Web Mining, Zakopane, Poland, 2–5 June 2003; Advances in Soft Computing. Springer: Berlin/Heidelberg, Germany, 2003; Volume 22. [Google Scholar]
- Ras, Z.W.; Dardzinska, A. Action Rules Discovery, a New Simplified Strategy. In Proceedings of the ISMIS 2006, Foundations of Intelligent Systems, Bari, Italy, 27–29 September 2006; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2006; Volume 4203. [Google Scholar]
- Ras, Z.W.; Wyrzykowska, E.; Wasyluk, H. ARAS: Action Rules Discovery Based on Agglomerative Strategy. In Proceedings of the MCD 2007, Mining Complex Data, Warsaw, Poland, 17–21 September 2007; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2007; Volume 4944. [Google Scholar]
- Ras, Z.W.; Dardzinska, A.; Tsay, L.-S.; Wasyluk, H. Association Action Rules. In Proceedings of the MCD 2008, IEEE/ICDM Workshop on Mining Complex Data, Pisa, Italy, 15–19 December 2008; pp. 283–290. [Google Scholar]
- Im, S.; Ras, Z.W. Action rule extraction from a decision table: ARED. In Foundations of Intelligent Systems, Proceedings of the ISMIS’08, Toronto, ON, Canada, 20–23 May 2008; An, A., Matwin, S., Ras, Z.W., Slezak, D., Eds.; LNCS; Springer: Berlin/Heidelberg, Germany, 2008; Volume 4994, pp. 160–168. [Google Scholar]
- Dean, J.; Ghemawat, S. MapReduce: Simplified Data processing on large clusters. In Proceedings of the 6th Conference on Symposium on Operating Systems Design and Implementation, Berkeley, CA, USA, 3 October 2004; USENIX Association: Berkeley, CA, USA, 2004; Volume 6. [Google Scholar]
- Zaharia, M.; Chowdhury, M.; Das, T.; Dave, A.; Ma, J.; McCauley, M.; Franklin, M.J.; Shenkar, S.; Stoica, I. Resilient distributed datasets: A fault-tolerant abstraction for in-memory cluster computing. In Proceedings of the the 9th USENIX Conference on Networked Systems Design and Implementation, San Jose, CA, USA, 25–27 April 2012; USENIX Association: Berkeley, CA, USA, 2012. [Google Scholar]
- Gong, L.; Yan, J.; Chen, Y.; An, J.; He, L.; Zheng, L.; Zou, Z. An IoT-based intelligent irrigation system with data fusion and a self-powered wide-area network. J. Ind. Inf. Integr. 2022, 29, 100367. [Google Scholar] [CrossRef]
- Ras, Z.W.; Wieczorkowska, A. Advances in Music Information Retrieval; Studies in Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Ras, Z.W.; Wieczorkowska, A.; Tsumoto, S. Recommender Systems for Medicine and Music; Studies in Computational Intelligence; Springer: Berlin/Heidelberg, Germany, 2021; Volume 946. [Google Scholar]
- Ras, Z.W.; Tarnowska, K.; Kuang, J.; Daniel, L.; Fowler, D. User Friendly NPS-based Recommender System for driving Business Revenue. In Proceedings of the 2017 International Joint Conference on Rough Sets (IJCRS’17), Olsztyn, Poland, 3–7 July 2017; LNCS. Springer: Berlin/Heidelberg, Germany, 2017; Volume 10313, pp. 34–48. [Google Scholar]
- Kuang, J.; Ras, Z.W.; Daniel, A. Hierarchical agglomerative method for improving NPS. In PReMI 2015; Kryszkiewicz, M., Bandyopadhyay, S., Rybinski, H., Pal, S.K., Eds.; LNCS; Springer: Cham, Switzerland, 2015; Volume 9124, pp. 54–64. [Google Scholar]
- Tarnowska, K.A.; Ras, Z.W. Sentiment Analysis of Customer Data. Web Intell. J. 2019, 17, 343–363. [Google Scholar] [CrossRef]
- Wang, K.; Jiang, Y.; Tuzhilin, A. Mining actionable patterns by role models. In Proceedings of the 22nd International Conference on Data Engineering (ICDE’06), Atlanta, GA, USA, 3–7 April 2006; Liu, L., Reuter, A., Whang, K.-Y., Zhang, J., Eds.; IEEE Computer Society: New York, NY, USA, 2006; p. 16. [Google Scholar]
- Larose, D.T.; Larose, C.D. Data Mining and Predictive Analytics, 2nd ed.; Wiley Publishing: Hoboken, NJ, USA, 2015. [Google Scholar]
- Bagavathi, A.; Mummoju, P.; Tarnowska, K.; Tzacheva, A.A.; Ras, Z.W. SARGS method for distributed actionable pattern mining using spark. In Proceedings of the 4th International Workshop on Pattern Mining and Applications of Big Data (BigPMA 2017) at IEEE International Conference of Big Data (IEEE Big Data’17), Boston, MA, USA, 11–14 December 2017; pp. 4272–4281. [Google Scholar]
- Tzacheva, A.A.; Bagavathi, A.; Ganesan, P.D. MR-Random Forest Algorithm for Distributed Action Rules Discovery. Int. J. Data Min. Knowl. Manag. Process. IJDKP 2016, 6, 15–30. [Google Scholar] [CrossRef]
- Rathee, S.; Kaul, M.; Kashyap, A. R-Apriori: An efficient apriori based algorithm on spark. In Proceedings of the 8th Workshop on Ph.D. Workshop in Information and Knowledge Management, Melbourne, Australia, 19 October 2015; pp. 27–34. [Google Scholar]
- Hahsler, M.; Karpienko, R. Visualizing association rules in hierarchical groups. J. Bus. Econ. 2017, 87, 317–335. [Google Scholar] [CrossRef]
- Simunek, M. Academic KDD Project LISp-Miner; Springer: Berlin/Heidelberg, Germany, 2003; pp. 263–272. [Google Scholar]







| a | b | |
|---|---|---|
| Rule/Dataset Type | Processing Time | % Customers Covered |
|---|---|---|
| Base rule | 10 s | 71.4% |
| Rule—Type 0 | 5 s | 71.4% |
| Rule—Type 1 | 2.3 s | 71.4% |
| Binned—base | 17 s | 71.4% |
| Binned—Type 0 | 4.3 s | 71.4% |
| Binned—Type 1 | 3 s | 71.4% |
| Rule/Dataset Type | Processing Time | % Customers Covered |
|---|---|---|
| Base rule | 77 s | 80.6% |
| Rule—Type 0 | 19.6 s | 74.2% |
| Rule—Type 1 | 15.7 s | 74.2% |
| Binned—base | 47.6 s | 77.4% |
| Binned—Type 0 | 8.8 s | 58.1% |
| Binned—Type 1 | 10.5 s | 58.1% |
| Rule/Dataset Type | Processing Time | % Customers Covered |
|---|---|---|
| Base rule | 11 min | 80.6% |
| Rule—Type 0 | 0.9 min | 74.2% |
| Rule—Type 1 | 24 s | 74.2% |
| Binned—base | 7.1 min | 77.4% |
| Binned—Type 0 | 24 s | 58.1% |
| Binned—Type 1 | 18 s | 58.1% |
| Rule/Dataset Type | Processing Time | % Customers Covered |
|---|---|---|
| Base rule | 169.8 min | 86.9% |
| Rule—Type 0 | 32 min | 85.2% |
| Rule—Type 1 | 4.2 min | 82% |
| Binned—base | 131.1 min | 88.5% |
| Binned—Type 0 | 14.5 min | 88.5% |
| Binned—Type 1 | 4.9 min | 73.8% |
| Rule/Dataset Type | Processing Time | % Customers Covered |
|---|---|---|
| Base rule | 28 h | 85% |
| Rule—Type 0 | 2 h | 79.4% |
| Rule—Type 1 | 24.3 min | 76.7% |
| Binned—base | 18 h | 87.2% |
| Binned—Type 0 | 19.2 min | 61.1% |
| Binned—Type 1 | 11.4 min | 61.1% |
| Dataset’s Size | Distributed | Nondistributed |
|---|---|---|
| #17–547 rows | 0.9 min | 8.6 min |
| #16–2078 rows | 1.4 min | 3.7 h |
| #20–2590 rows | 3.0 min | 17 h |
| #30–3335 rows | 3.0 min | 10 h |
| Dataset’s Size | Distributed | Nondistributed |
|---|---|---|
| #17–547 rows | 77.3% | 77.3% |
| #16–2078 rows | 73.8% | 76.9% |
| #20–2590 rows | 79.5% | 81.8% |
| #30–3335 rows | 79.8% | 79.8% |
| Metric | Type 0 | Type 1 | Bin—Type 1 |
|---|---|---|---|
| A: Action rules extracted | 329 | 141 | 179 |
| B: Action rules read into RS | 102 | 46 | 46 |
| C: Ratio B/A | 31% | 32.6% | 25.7% |
| D: Atomic actions | 12 | 8 | 8 |
| E: Atomic actions triggered | 12 | 8 | 8 |
| F: Triggered action rules | 102 | 46 | 46 |
| G: Ratio: F/B | 100% | 100% | 100% |
| H: Meta-actions extracted | 7 | 7 | 7 |
| I: Effective meta-nodes | 4 | 1 | 0 |
| J: Max NPS impact | 3.21% | 2.89% | 0% |
| Metric | Type 0 | Type 1 | Bin-Type 1 |
|---|---|---|---|
| A: Action rules extracted | 24,515 | 5153 | 14,233 |
| B: Action rules read into RS | 5686 | 1230 | 3066 |
| C: Ratio B/A | 23.2% | 23.9% | 21.5% |
| D: Atomic actions | 137 | 54 | 44 |
| E: Atomic actions triggered | 135 | 54 | 44 |
| F: Triggered action rules | 5555 | 1230 | 3066 |
| G: Ratio: F/B | 97.7% | 100% | 100% |
| H: Meta-actions extracted | 9 | 9 | 9 |
| I: Effective meta-nodes | 18 | 5 | 6 |
| J: Max NPS impact | 8.58% | 7.37% | 1.9% |
| Metric | Type 0 | Type 1 | Bin-Type 1 |
|---|---|---|---|
| A: Action rules extracted | 59,508 | 11,799 | 31,228 |
| B: Action rules read into RS | 13,423 | 2624 | 6121 |
| C: Ratio B/A | 22.56% | 22.24% | 19.6% |
| D: Atomic actions | 286 | 89 | 55 |
| E: Atomic actions triggered | 160 | 69 | 40 |
| F: Triggered action rules | 4879 | 892 | 1585 |
| G: Ratio: F/B | 36.4% | 34% | 25.9% |
| H: Meta-actions extracted | 11 | 11 | 11 |
| I: Effective meta-nodes | 49 | 6 | 4 |
| J: Max NPS impact | 3.7% | 3.45% | 1.65% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tarnowska, K.A.; Bagavathi, A.; Ras, Z.W. High-Performance Actionable Knowledge Miner for Boosting Business Revenue. Appl. Sci. 2022, 12, 12393. https://doi.org/10.3390/app122312393
Tarnowska KA, Bagavathi A, Ras ZW. High-Performance Actionable Knowledge Miner for Boosting Business Revenue. Applied Sciences. 2022; 12(23):12393. https://doi.org/10.3390/app122312393
Chicago/Turabian StyleTarnowska, Katarzyna A., Arunkumar Bagavathi, and Zbigniew W. Ras. 2022. "High-Performance Actionable Knowledge Miner for Boosting Business Revenue" Applied Sciences 12, no. 23: 12393. https://doi.org/10.3390/app122312393
APA StyleTarnowska, K. A., Bagavathi, A., & Ras, Z. W. (2022). High-Performance Actionable Knowledge Miner for Boosting Business Revenue. Applied Sciences, 12(23), 12393. https://doi.org/10.3390/app122312393








