1. Introduction
A wireless sensor network (WSN) is one of the widely adopted network systems in industry health care and in many intrusion detection areas. It comprises a network of devices defined as nodes. The nodes have the ability to sense the environment from the area under monitoring, gather information, and communicate the collected data by means of wireless links. The final destination node is called the destination node or sink node. The data from the initial node are forwarded through multi-hop routing to the destination node and the collected data are utilized by other networks through the gateway. The structure of the nodes can be moving or stationary, and they must be aware of their identity location. Since a WSN does not require cables or wires, it is flexible and may add new nodes or devices to the network at any time.
The recent developments in WSN extended its application to sophisticated systems. The challenges in WSNs persist even with the modern developments [
1]. A WSN is interconnected with various nodes and forms a network within a range. The expansion of coverage is determined by the type of application as well as the number of nodes and devices. The energy used by these nodes depends on the establishment and the remote areas that require an improved, energy efficient system [
2]. The data collected by the sensor nodes must be transmitted consistently over a long period of time. The modern approaches and recent studies have shown that the data transfer happens through WSN and makes them consume more energy and reduces the network lifespan. The power resource constraint is critical, considered a lifetime factor for WSNs which cannot be replaced if they face certain technical issues in their application. For optimal routing mechanisms, the pattern of clustering and the decision of head selection for clusters are critical. The selection is based on the nodes having maximum energy and minimum traversing distance between the neighboring nodes with medium speed quality, followed by the patterns of clustering for the determination of routing paths. Algorithms in artificial intelligence should be employed for determining the shortest. It is the responsibility of the protocol to administer and update the routing table for effective routing and to minimize the energy consumption. Protocols used for routing mechanisms should focus mainly on the energy needed for the network operation.
Many researchers have developed new techniques to overcome the energy efficiency problem in order to improve the WSN lifespan. However, these techniques are not sufficient to balance everything. Researchers have adopted hybrid approaches to take advantage of different techniques to achieve a balance in WSN. This is because an overperforming WSN results in premature node failures or dead nodes, indicating that nodes die with burden.
If the nodes are used for a long time, they face premature failure [
3]. To overcome this issue, recent studies have attempted to optimize routing to reduce the energy consumed and improve the network lifespan.
The optimization of path in WSNs is important for solving the issue of redundant data forwarded into the network and for reducing energy consumption. Cluster formation helps in the process of minimizing the energy level, where data aggregation is an important criterion that needs to be addressed both at the level of the cluster head and at the base station. The process of data aggregation is performed at each router while forwarding the data packets. The packet transmission follows the working principle of routing protocols that involve many algorithms for the determination of optimal network data transfer and the pathway for communication between the sensor nodes.
Various optimization techniques have been used [
4] by researchers and developers in WSNs, such as Particle Swarm Optimization (PSO) [
5,
6], Grey Wolf Optimization (GWO) [
7], Crow Search Optimization (CSO) [
8,
9], and Dragonfly Optimization (DFO) [
10]. Alternative approaches are also used, such as adopting new network models and topologies [
11,
12] to make the WSN work effectively with available resources [
13,
14]. In the current study, we mainly intended to develop an energy efficient routing mechanism using artificial intelligence to select the optimal path routing in a WSN. Although the existing approaches have attempted to provide routing protocols through cluster formation, most of them fall short in terms of energy consumption and time delay in the transmission, along with security threats in the network. Hence, the use of algorithmic hybridization leads to improvements in the network and improves the overall performance of the routing model used to route data from a sender to a receiver in the network. The aim of the proposed work is to provide an optimal path considering the parameters of computational time, performance, energy consumption, and resource usage. The enhanced system addresses the problem of computational complexities through an artificial intelligence-based model of meta-heuristic and optimization algorithms. For the implementation of this work, we employed an optimization algorithm, GWO, for cluster head selection and a meta-heuristic algorithm, DFO, for path determination. Both algorithms provide efficient transmission of data packets through clustering-based techniques, thereby finding the optimal path for the densely populated network. The proposed hybridization of GWO and DFO focuses on increasing the efficiency in performance in the selection of the optimal path, thereby using minimal energy for transmission. Finally, the outcome of the combined approach can be tested with the QoS metrics for bringing out the advantages of the system. Hence, using the proposed work of artificial intelligence-based optimal path selection in WSNs, the network achieves an extended lifetime through energy consumption and transfers the data reliably with minimum time.
This article is organized as follows.
Section 2 provides the literature review.
Section 3 details the materials and methods of the proposed method.
Section 4 provides a comparative analysis and the results of the proposed method with other studies. Finally,
Section 5 concludes with conclusions and future research prospects.
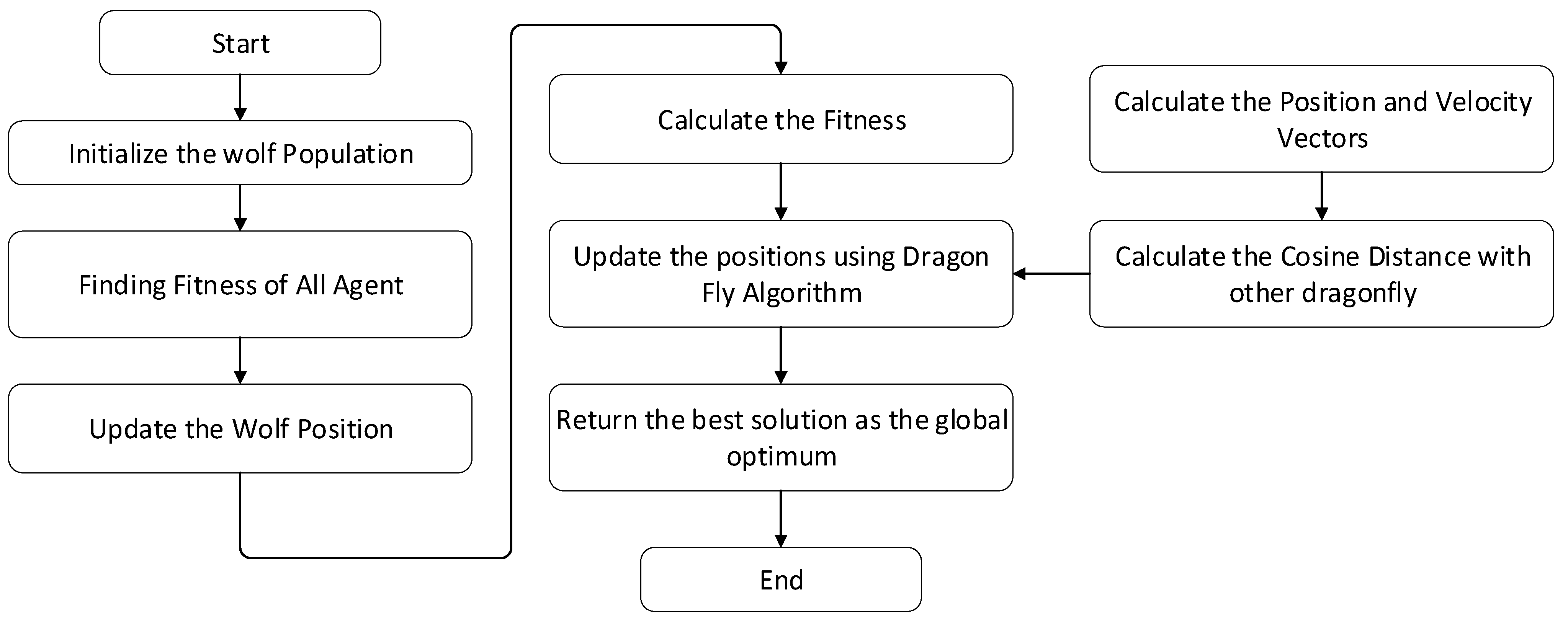
4. Comparative Analysis and Results
In this study, the efficiency and execution of the proposed work are correlated with the methods based on the algorithms of machine learning (ML) and routing protocols. The simulation parameters used for the analysis of wireless sensor networks are depicted in
Table 1.
The results obtained for the proposed methodology and the performance evaluation and comparison with other studies are discussed in this section. The energy consumed for data transfer, the data transfer rate, the computation time, and the criteria of the first dead node end-to-end delay and throughput are compared.
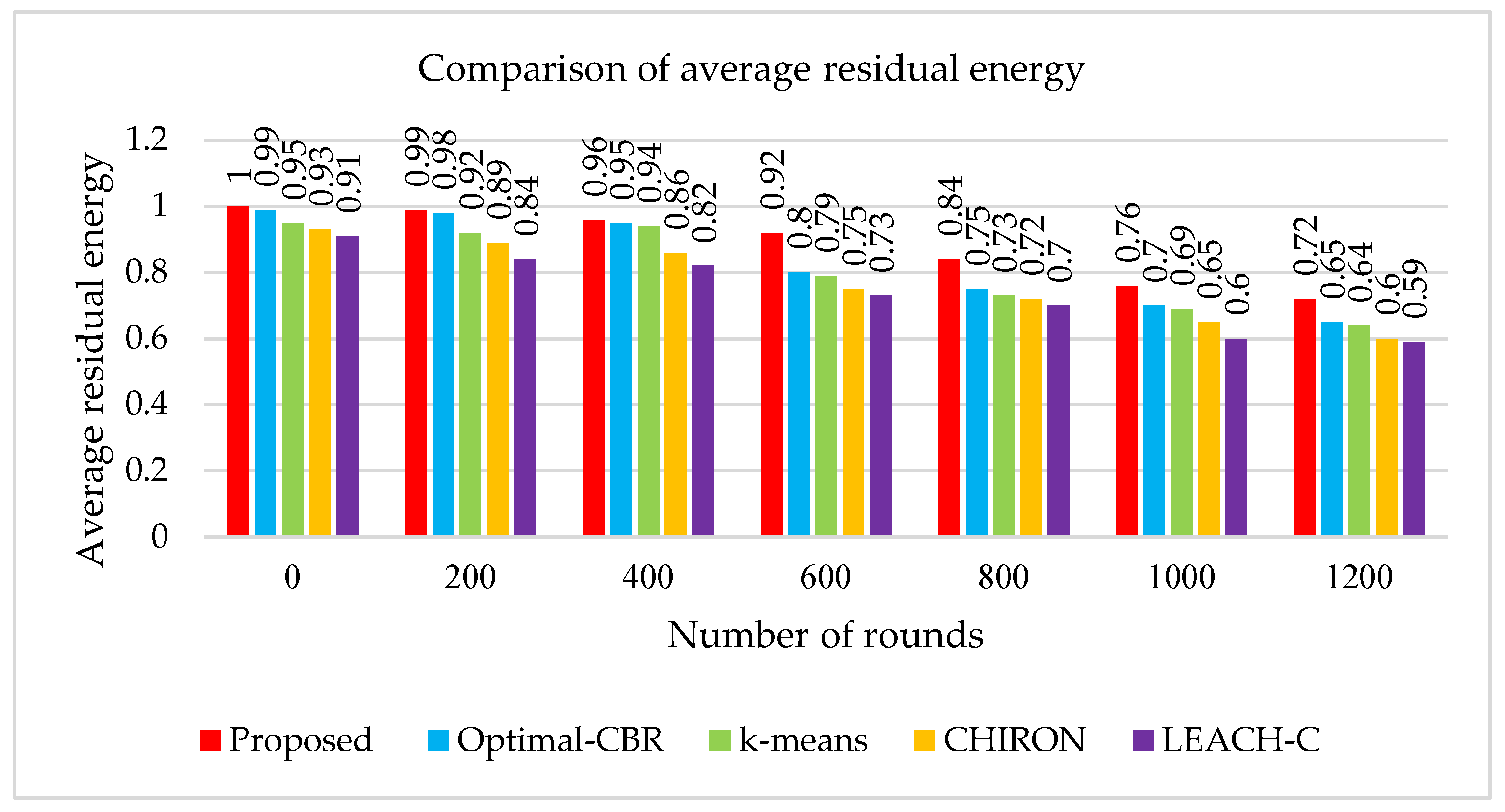
Figure 2 shows the comparative analysis between the proposed method and other studies for the average residual energy spent on the number of rounds. Residual energy is the total amount of energy depleted in each stage of the nodes. The outcomes of the simulation graphs signify that the proposed method has better recorded residual energy than Optimal Cluster-Based Routing (CBR). Compared with k-means, Chain-Based Hierarchical Routing Protocol (CHIRON), and Low-Energy Adaptive Clustering Hierarchy Centralized (LEACH-C) protocols, the proposed method has an increased lifespan. This is mainly due to the quicker optimum solution techniques of the combined GWO-DFO technique.
An improved k-means algorithm is used to choose a cluster head and transform it into a chain route in a network just after the threshold value is larger than the node energy. Another method is a basic clustering algorithm termed clustering by k-means that belongs to an unreasoned approach of clustering. The estimation of the mean value (1, 10) as a centroid is estimated by partitioning the provided node set into k-clusters. The steps involved in the k-means algorithm are as follows:
The selection of k points non-specifically as a centroid in which k is considered to be a number of clusters.
Allocate every node to the nearest median (centroid) by using Euclidean distance to produce clusters.
Calculate the latent centroid for each cluster.
The repetition of the last two steps is performed until no fluctuation occurs in the centroid of each cluster.
By eliminating some sensors in a network, this method extends its useful life while also improving performance metrics.
Another protocol implemented here is a chain-based routing approach called the Chain-Based Hierarchical Routing Protocol (CHIRON) used to reduce several defects related to the data dissemination delay. In the initial stage, the segregation of the network causes various fan-shaped fragments to occur. The base station supplies the control message to each individual node in a group and helps the node determine the group it belongs to. The second step involves far-away nodes available from a base station activated to produce group chains inside a single group. A greedy algorithm is implemented to find the nearest node associated with a node that converts to a new node, which starts the consecutive association levels. The leader/head node is elected in the third level or step and the distant node away from the base station is the head in a community chain. Then, the node with higher residual energy is elected as the chain head of a group. The transmission of data to a group chain head in every group over a chain is implemented in the fourth step. Finally, the obtained data are dispatched to a base station using a leader-to-leader transmission method. This method provides low energy dispersion and clustering overhead can occur.
The other method used is LEACH-C (Low-Energy Adaptive Clustering Hierarchy Centralized), an individual-hop data transmission structure where cluster heads give the combined information to a base station, along with nodes’ endurance level. The head node is the one whose endurance is above the threshold for the ongoing round, and the data are circulated throughout the entire arrangement. The matching of circulated identity to the core identity is interpreted for a lifetime of rounds. This protocol is mainly useful for short distances. The dissipation of endurance usage among available hubs is provided by LEACH-C, but this method is not easily upgraded or updated.
Therefore, all procedures executing WSNs are compared with the proposed work to evaluate the average of the residual energy determined by the score of rounds. The average of the residual energy levels determined by the score rounds is calculated by various methods and classified in
Table 2.
The various methods for routing protocols and machine learning algorithms are analyzed and the outcomes are tabulated. From
Table 1, the average residual energy by the number of rounds by Optimal-CBR is 0.99 per 0 rounds, 0.98 per 200 rounds, 0.95 per 400 rounds, 0.8 per 600 round, 0.75 per 800 rounds, 0.7 per 1000 rounds, and 0.65 per 1200 rounds. K-means produced 0.95 per 1, 0.92 per 200, 0.94 per 400, 0.79 per 600, 0.73 per 800, 0.69 per 1000, and 0.64 per 1200. The CHIRON method yields 0.93 per 0, 0.89 per 200, 0.86 per 400, 0.75 per 600, 0.72 per 800, 0.65 per 1000, and 0.6 per 1200. LEACH-C gives 0.91 per 0, 0.84 per 200, 0.82 per 400, 0.73 per 600, 0.7 per 800, 0.6 per 1000, and 0.59 per 1200. Among these methods, our proposed method has higher average residual energy by the number of rounds than the other methods, and the values of the proposed method are 1 per 0, 0.99 per 200, 0.96 per 400, 0.92 per 600, 0.84 per 800, 0.76 per 1000, and 0.72 per 1200. Therefore, our proposed system scored high compared to the other methods.
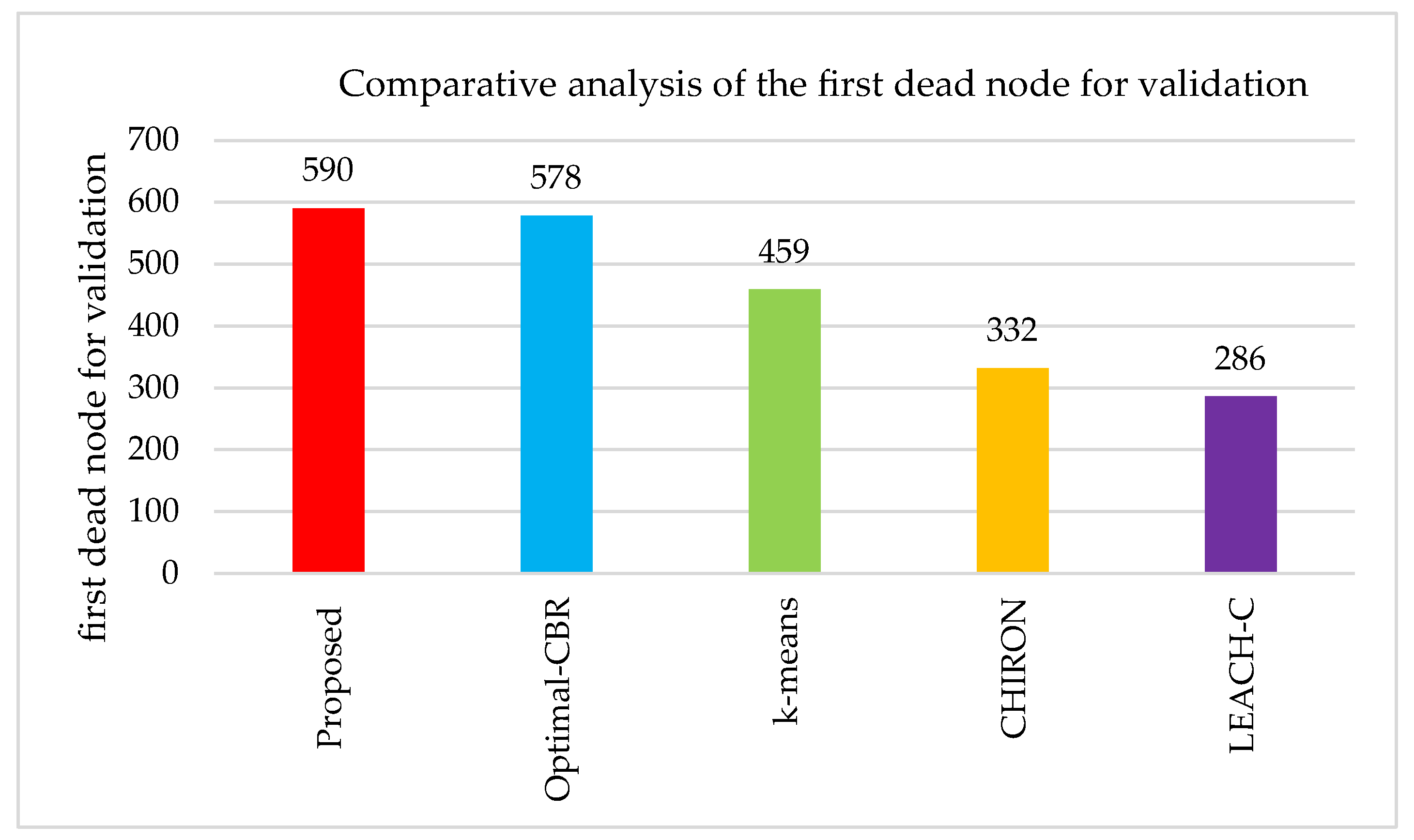
The node with a transmission latency higher than the threshold value in the WSN is called a dead node. The presence of a dead node indicates the reliability of the WSN. The comparative analysis of the first dead node for validation is shown in
Figure 3. The measured value is greater for the proposed model than for the other values. This is due to the threshold configured in the models. It also depends on the user-defined data presented in the node. The first dead node was found after 500 rounds, showing that the proposed model has nodes with better reliability.
The efficiency of data transmission is determined by examining the alive nodes since the looping proceeds because of the network lifetime. In Optimal-CBR, the first node dead by the rounds of communication is higher due to the threshold of user-defined data available in every node, which in turn decreases the energy used by the cluster head. Hence, several methods for routing protocols are employed to compare with the proposed method for the first dead node for validation by the rounds of communication, and the values are categorized in
Table 3.
In
Table 3, the first dead node for validation by the rounds of LEACH-C, Optimal-CBR, CHIRON, and k-means are 286, 578, 332, and 459, respectively. However, the proposed method leads with 590. The end-to-end latency analysis used for performance analysis is shown in
Figure 4. It is seen that less delay is obtained with the proposed algorithm compared to other algorithms.
The occurrence of a delay in the proposed method is compared to Optimal Cluster-Based Routing (CBR), k-means, Chain-Based Hierarchical Routing Protocol (CHIRON), and Low-Energy Adaptive Clustering Hierarchy Centralized (LEACH-C) in
Table 4.
Table 4 shows that the end-to-end delay by the number of rounds by Optimal-CBR is 0.5 per 200 rounds, 1.9 per 400 rounds, 2.9 per 600 rounds, 3.9 per 800 rounds, and 5.2 per 1000 rounds. The method k-means produced 0.8 per 200, 1.7 per 400, 2.6 per 600, 3.5 per 800, and 4.7 per 1000. The CHIRON method yields 1 per 200, 2.8 per 400, 3.8 per 600, 4.5 per 800, and 6 per 1000. LEACH-C gives 0.7 per 200, 2.3 per 400, 3.2 per 600, 4.1 per 800, and 5.5 per 1000. Among all these methods, the proposed method has lower end-to-end delay by the number of rounds than the other methods, and the values in the proposed method are 1 per 0.3 per 200, 1.4 per 400, 2.3 per 600, 3.1 per 800, and 4.4 per 1000. Therefore, our proposed system scored low in the end-to-end delay by the number of rounds compared to k-means, LEACH-C, CHIRON, and Optimal-CBR.
The simulation graphs in
Figure 5 show that the proposed method has better recorded throughput than Optimal Cluster-Based Routing (CBR). Compared with the k-means, Chain-Based Hierarchical Routing Protocol (CHIRON), and Low-Energy Adaptive Clustering Hierarchy Centralized (LEACH-C) protocols, the proposed method has an increased lifespan. This is mainly due to the quicker optimum solution techniques of the combined GWO-DFO technique.
The calculation of the throughput value of the proposed simulator is given in Equation (19). Here
Dsuccessful delivered is refers to the successful delivered packet in each communication,
DAverage Size is refers to the average packet size, and
DSent Time is refers to the total time taken for the sent packets. The list of throughput values measured is given in
Table 5.
Table 5 illustrates that throughput by the number of rounds by Optimal-CBR is 0.9 per 500 rounds, 1.8 per 1000 rounds, 2.4 per 1500 rounds, 2.5 per 2000 round, and 2.4 per 25,000 rounds. K-means produced 0.7 per 500, 1.5 per 1000, 2.1 per 1500, 2.1 per 2000, and 2.1 per 2500. The CHIRON method yields 0.3 per 500, 0.9 per 1000, 1 per 1500, 1.1 per 2000, and 1.1 per 2500. LEACH-C gives 0.5 per 500, 1 per 1000, 1.5 per 1500, 1.7 per 2000, and 1.7 per 2500. The proposed method has higher throughput by the number of rounds than the other methods. The values in the proposed method are 1 per 500, 1.9 per 1000, 2.5 per 1500, 2.8 per 2000, and 2.9 per 25,000. Therefore, from the above interpretation, our proposed system scored high in the throughput by the number of rounds compared to k-means, LEACH-C, CHI-RON, and Optimal-CBR.
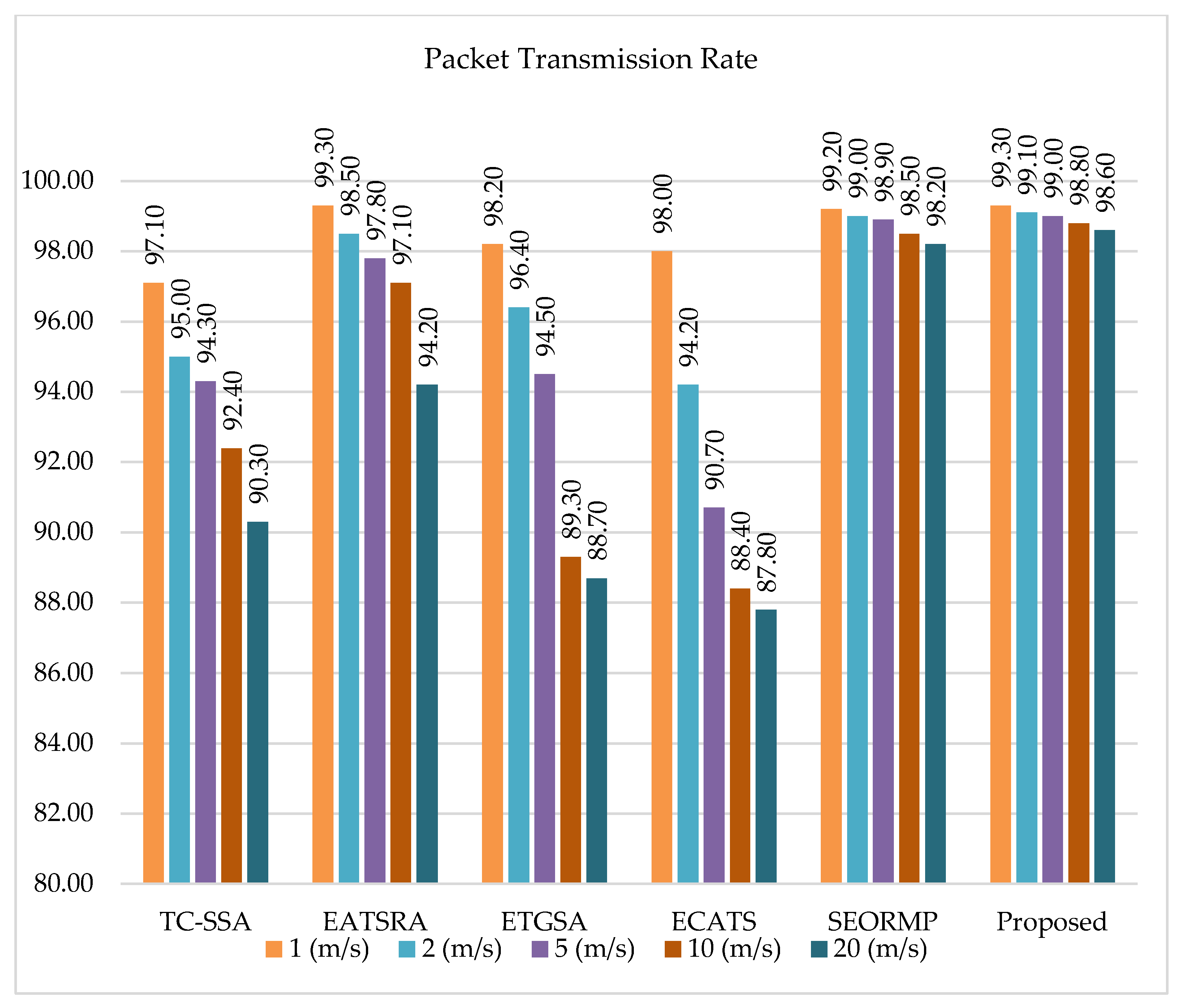
The packet transmission rate comparison is shown in
Figure 6. TC-SSA [
26], EATSRA [
27], ETGSA [
28], ECATS [
29], and SEORMP [
16] are used for the comparison. It can be observed that the transmission rate reduces with the mobility. The earlier research models are lower than the proposed model and SEORMP model. The amount of data transfer that occurs shows the ability of the model to provide stability for a longer lifetime. For the proposed model, the transmission rate was higher at the initial stage, where the mobility was 1 m/s, and it was measured to be around 99.30, which is similar to the model EATSRA [
27].
During the packet transmission, the status of nodes is mobile and there is a decrease in the energy level. According to many researchers, every node will maintain a routing table to recognize the transmitted node or nearby node. The maintenance of the routing table to create an effective protocol is the greatest challenge in WSN. Therefore, this comparative analysis is carried out to find an optimal routing protocol.
The optimization of the routing protocol is carried out with the aid of the gravitational search technique, considering indirect and direct trust in nodes and concern over energy saving. This routing approach is termed ETGSA (Energy-Aware Trust-Based Gravitational Search Approach). It is proved that the ETGSA algorithm maximizes the reliability to resist certain attacks in a network and decreases the computing overhead, and NS-2 is used for the simulation process [
28].
With the help of the DT algorithm and the spatio-temporal constraint, wireless sensor networks can identify malicious users and choose safe paths. This algorithm develops security and a suitable delivery ratio, and to choose efficient decisions, certain kinds of constraints called spatio-temporal constraints are introduced in this model [
27].
After the experimental analysis, the overall production of all systems is presented graphically in
Figure 6. The ratio of transmission rate in a packet along with motility speed is calculated, and this criterion is analyzed with many systems and the proposed approach. Among existing approaches, the mobility of a node in the path construction is available in the Secured Energy Optimal Routing with Mobility Prediction (SEORMP) approach. By analyzing the total trust of a node and its instant trust, SEORMP builds an efficient and secure route. The energy consumption in a node is modified after the packet transmission maximizes throughput and reduces the time delay in the packet transmission. However, the proposed method, in terms of packet transmission rate, performs better than the SEORMP technique.
Many available studies, while suggesting an optimal path, do not take the mobility speed into account. On the basis of security concerns, a path is created given the path and energy level in a node. If mobility is considered, then automatically, time concern is dispersed. The comparative analysis of several systems along with the proposed system in terms of the transmission rate of the packet depending on the speed of mobility is categorized in
Table 6.
Table 6 shows that the packet transmission rate of the proposed system is higher than other methods such as Energy-Aware Trust-Based Gravitational Search Approach (ETGSA), Taylor-Based Cat Salp Swarm Optimization Algorithm (TC-SSA), Enhanced Fuzzy C-Means and Adaptive TDMA Scheduling (ECATS), and Energy-Aware Trust-Based Secure Routing Algorithm (EATSRA). When the mobility speed is 1, the packet transmission rates of ETGSA, SEROMP, TC-SSA, the proposed system, ECATS, and EATSRA are 98.2, 99.2, 97.1, 99.3, 98, and 99.3, respectively. When the motility speed changed to 2, the corresponding packet transmission rates of ETGSA, SEORMP, TC-SSA, the proposed system, ECATS, and EATSRA were 96.4, 99, 95, 99.1, 94.2, and 98.5, respectively. If the mobility speed increases to 5, the transmission rates of packets in ETGSA, SEORMP, TC-SSA, the proposed system, ECATS, and EATSRA are 94.5, 98.9, 94.3, 99, 90.7, and 97.8, respectively. The packet transmission rates of ETGSA, SEORMP, TC-SSA, the proposed system, ECATS, and EATSRA when the mobility speed is 10 are 89.3, 98.5, 92.4.98.8, 88.4, and 97.1, respectively. If the mobility speed increases to 20, then the packet transmission rates of ETGSA, SEORMP, TC-SSA, the proposed system, ECATS, and EATSRA are 88.7, 98.2, 90.3, 98.6, 87.8, and 94.2, respectively.
Table 6 explains that the proposed system achieves a higher packet transmission rate based on the mobility speed compared to the other methods.
A graphical representation of the comparative analysis of the proposed method with other techniques such as RPL, EESRA, E-ALWO, MDSMAP, and GWO based on the computational time is illustrated in
Figure 7. With the proposed technique, less computation time for data transfer is achieved compared to GWO [
30], EESRA [
31], MDS-MAP [
32], RPL and E-ALWO [
17]. This shows that the proposed method is energy efficient, as the more the computational power used, the more the model consumes energy for the process. Here, GWO implemented alone suffered from slow convergence and failed to find the local optimum effectively, having to search repeatedly and thus increasing the time to find the optimum solution.
The most efficient algorithms are those with low computational time and minimum steps. The computational time is defined as the time taken by an algorithm to compute a given task. the algorithm with minimum steps accomplishes the task with minimal computation time.
The same issue can be solved by many algorithms with different computation times, but the steps implemented by different routing protocols differ, which leads to high computation time in some cases. The algorithm with the minimum number of steps to resolve an issue has the lowest computational time. The computational times of the proposed technique and various techniques such as RPL, MSD-MAP, EESRA, E-ALWO, and GWO are calculated and categorized in
Table 7.
Table 7 states that the computational time required for the proposed system is the lowest, 6 s, while the computational time taken by Grey Wolf Optimizer is 11 s. The computational time needed by the Routing Protocol for Low-Power and Lossy Networks is 7 s and the computational time of the Multidimensional-Scaling Map is 8 s. The computational time needed by an Efficient Energy Scaling Routing Algorithm is 9.5 s, and finally, the computational time required for the Exponentially Ant Lion Whale Optimization algorithm is 6.5 s. Therefore, our proposed system is efficient in terms of computational time since it provides the lowest computational time of the methods. The algorithm E-ALWO consumes less computational time than other existing methods such as GWO, MDS-MAP, RPL, and EESRA, but our proposed method beats the E-ALWO algorithm and secures the first position in the least computational time consumed by an algorithm.
By analyzing and comparing our proposed method with several other methods, it is confirmed that our proposed method is efficient in many ways and is suitable for resolving the energy concerns in wireless sensor networks (WSNs).