Abstract
Generally, biometric authentication is conducted either by mobile terminals in local-processing mode or by public servers in centralized-processing mode. In the former mode, each user has full control of his/her biometric data, but the authentication service is restricted to local mobile apps. In the latter mode, the authentication service can be opened up to network applications, but the owners have no control of their private data. It has become a difficult problem for biometric applications to provide open and trusted authentication services under user control. Existing approaches address these concerns in ad-hoc ways. In this work, we propose BioShare, a framework that provides trusted biometric authentication services to network applications while giving users full control of their biometric data. Our framework is designed around three key principles: each user has full control of his/her biometric data; biometric data is stored and processed in trusted environments to prevent privacy leaks; and the open biometric-authentication service is efficiently provided to network applications. We describe our current design and sample implementation, and illustrate how it provides an open face-recognition service with standard interfaces, combines terminal trusted environments with server enclaves, and enables each user to control his/her biometric data efficiently. Finally, we analyze the security of the framework and measure the performance of the implementation.
1. Introduction
With the prevalence of smartphones and e-commerce, biometric identification technologies are widely used by service providers and are favorably accepted by most consumers. Fingerprint identification and face recognition have become standard features on most Android and iOS devices, and payment platforms based on facial recognition are increasingly popular in countries such as China. Meanwhile, privacy protection has become a serious topic and is attracting comprehensive attention from scholars and governments. The European Union released the General Data Protection Regulation (GDPR) [1,2,3] in 2018, the United States issued the California Consumer Privacy Act (CCPA) [4,5] in 2018, and China published the Personal Information Protection Law (PIPL) [6] in 2021. Google, Facebook, British Airways, and many other companies were fined for data leakage, unauthorized usage, and other data issues. We are currently faced with the dilemma between data usage and privacy protection, and we need a technical solution to achieve both goals within the same framework.
Currently, there are two types of solutions available: local processing solutions and centralized-processing solutions. The former method is to process and store personal biometric data in local trusted environments integrated in personal mobile terminals, and the representative implementations include Apple Touch ID/Face ID and Windows Hello. Through local trusted computation, each user has full control of his/her biometric data without the risk of privacy leakage, but authentication services are restricted only to local mobile apps. As such, the services are secure but not open. The latter method uses a centralized system to collect and process biometric data in centralized-processing mode on public servers, and typical application scenarios include many payment platforms based on facial recognition, as described in Section 2.3. With the help of powerful servers, service providers can provide open biometric authentication services to various network applications efficiently. However, when raw biometric data or extracted feature data are stored by service providers in their database servers, users are put at risk of privacy leakages due to improper maintenance or malicious attacks. While user biometric data are fully controlled by service providers without strict regulation and independent audit, users have no control of their private data and are faced with the abuse of personal data. As a conclusion, the first method is secure but not open, while the second method is open but not secure. We need a framework that provides both secure and open biometric services.
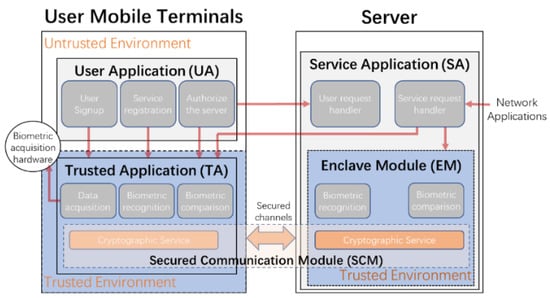
In this paper, we propose BioShare, a framework that provides both secure and open biometric services.To achieve this goal, we store and process biomatric data in secure environments (terminal TEEs and server enclaves) to ensure security, and we coordinate the terminals and the servers to provide open services for network applications. Our framework is designed around three key principles:
a. Each user has full control of his/her biometric data. Biometric services are provided in either forwarding mode or authorized mode. In the forwarding mode, personal biometric data are stored in the user’s terminals. In the authorized mode, biometric data are temporarily stored in the server enclave under user authorization, and users can cancel the authorization at any time. Both modes ensure users have full control of their private data.
b. Open bioauthentication services are efficiently provided to network applications. We design standard interfaces for biometric services, develop service request handler modules running on the server side, and provide open services to network applications.
c. Biometric data are stored and processed in trusted environments to prevent privacy leaks. On the terminal side, we use Trusted Executive Environments to protect biometric data. On the server side, we use enclave technologies to ensure data security. We build secure channels between the terminal side and the server side using cryptographic technologies to ensure data security during transmission.
The BioShare framework is designed to provide open and secure biometric services with secure data storage both on terminal TEEs and server enclaves, and through standard interfaces between terminal–server interactions. We implemented BioShare with facial recognition as an example, and measured the performance of the implementation. Based on the test results, the end-to-end response time is 91 ms to 1011 ms, which meets business requirements in most human interactive scenarios, and the security strength is higher than 128 bits, which fulfils the recommended standard for business systems.
The rest of the paper is organized as follows: We enumerate related works in Section 2, describe key parts of our current design in Section 3, illustrate key challenges with a sample implementation in Section 4, and then measure and analyze the performance in Section 5. Finally, we discuss several open issues in Section 6 and conclude in Section 7.
2. Related Works
2.1. Biometric Identification on Personal Mobile Devices
Currently most biometric services on mobile terminals are implemented as local processing solutions, which is to say that they are secure but restricted to local mobile apps. Since fingerprint identification was introduced into iPhone 5s smartphones by Apple in 2013, biometric recognition technologies have undergone exponential development in the smartphone market. Apple provides biometric services Touch ID [7] and Face ID [8] on iOS platforms, and Microsoft offers Windows Hello [9] on personal Windows devices. Many proven biometric technologies are widely integrated into mobile devices: fingerprint [10,11], face [12,13,14], iris [15,16,17], vein [18,19], etc., and many other biometric modalities are under study: gait [20], keystroke [21], handwriting [22], etc. At the same time, auxiliary methods are used to prevent spoofing and attacks, such as liveness detection [23,24,25], 3D recognition [26,27], micro-expression recognition [28,29], and movement detection such as head-shaking or blinking [30,31]. In general, biometric services are conducted in terminal trusted environments and are provided for device unlocking, online payment, and bank account verification, etc. However, these services are limited to local apps and are not available for remote network applications.
2.2. Trusted Executive Environment
In local processing solutions, biometric data are processed and stored in local secured environments to ensure data privacy and service security. Currently, operating systems for both terminals and servers have become huge and complex because they must support multiple devices and rich applications. As a result, they have become more and more vulnerable, because system software vulnerabilities depend on code size and complexity [32]. Therefore, current CPUs offer a special execution environment isolated from the OS, such as ARM TrustZone [33,34,35], and Intel SGX [36,37] and RISC-V Keystone [38]).
On the terminal market, based on hardware capabilities, terminal manufacturers design and implement native TEE OS software, such as Qualcomm QSEE [39], Google Trusty TEE [40], and Huawei iTrustee, etc. GlobalPlatform defines GPTEE specifications [41,42] to resolve compatibility issues between different TEE OSes, and UnionPay releases TEEI infrastructure [43] to support the coexistence and intercommunication of multiple TEEs in the same CPU. On the server market, CPU manufacturers release original Software Development Kits (SDKs) for different CPU models, such as Intel SGX SDK [44] and RISC-V Keystone SDK [45], and some other companies provide unified open-source solutions to resolve the compatibility issues of different SDKs, such as Microsoft Open Enclave SDK [46], Google Asylo [47], and Huawei secGear [48], etc.
Currently TEE technology is used on either the terminal side or the server side to provide trusted computation environments for local applications; however, no solution is available to combine the terminal TEEs and server enclaves to form an integrated trusted environment.
2.3. Payment Platforms Based on Facial Recognition
As a typical implementation of centralized-processing solutions, most facial recognition payment systems are open to network applications, but they process user biometric data in unsecure environments on public servers. Since the first facial recognition payment system was launched by Uniqul in Finland in 2013 [49], the paying-with-your-face service is becoming more and more popular in China. Alipay launched smile-to-pay products named Dragonfly [50], Tencent issued face-payment devices named Frog [51], and UnionPay cooperated with 60+ banks to provide facial payment solutions to merchants [52]. All of these cases have one thing in common: Users must upload private biometric data to service providers, and service providers store and process user biometric data in centralized mode on background servers. However, when biometric data are stored by service providers in their database servers, users are put at risk of privacy leakages due to improper maintenance or malicious attacks. When biometric data are processed by service providers without strict regulation and independent audit, users will lose control of their biometric data and face the abuse of personal data.
4. Sample Implementation
BioShare is currently implemented with facial recognition as an example, and deployed on Android mobile terminals with TEE communicating with a server with enclaves. The following sections describe several implementation details and challenges specific to our current implementation.
4.1. General Information
In our implementation, we chose mainstream CPU architectures with dominant TEE platforms, specifically ARM Cortex-A architecture with ARM TrustZone on the terminal side, and Intel Xeon E3 CPU with Intel SGX support on the server side. Table 3 lists the configurations of the hardware and software on each side.

Table 3.
The Configurations of Mobile Terminals and the Server.
4.2. User Application (UA)
The BioShare User Application is implemented as an Android app that is deployed on mobile terminals. The key challenge in the implementation of UA is to maintain a reliable connection between the terminals and the server in a changing environment.
TCP Connections: The user application either creates a short TCP/IP connection to the server for each call, or keeps a long connection with the server for a certain period. The former requires lower resource costs, while the latter shows better performance.
Notification Mechanism: Because Android or iOS kills the application running in the background automatically at irregular intervals, the User Application may be unreachable to the server from time to time. We need a notification mechanism through which the service application can notify the terminal to relaunch the user application at any time. Apple Push Notification Service [53], Google Firebase Cloud Messaging [54], and other third-party products provide reliable notification services for iOS and Android devices.
4.3. Service Application (SA)
The BioShare Service Application is implemented as two system service processes running in the background. One service process is responsible for handling the command requests from user applications on the terminal side, while the other is responsible for handling the service requests from network applications. The two processes coordinate with each other by sharing the same user-registration database.
We have developed two different experiments in which network applications call the biometric service in either forwarding mode or authorized mode. Experimenters can currently register terminal biometric capabilities to the server in the User Application on the terminal side, then the biometric service on the server will run in forwarding mode and all service requests from network applications will be forwarded to the user’s terminals registered. Furthermore, experimenters can also authorize the server in the User Application; accordingly, the biometric service on the server will run in authorized mode and all service requests from network applications will be handled locally by the Enclave Module on the server.
4.4. Trusted Application (TA)
The BioShare Trusted Application is implemented as a trusted module deployed in the Trusted Executive Environment on the terminal side. The key challenge is the choice of the appropriate biometric algorithms and implementations for facial recognition and comparison, due to the limitations of TEE capabilities. We attempt to choose open-source implementations with complete functionality, good performance, low computing and memory overheads, embedded-environment support, and appropriate licensing agreements.
Facial Recognition and Comparison: Currently, many open-source projects for facial recognition are available from GitHub, and Table 4 lists some popular projects. In our implementation, we chose SeetaFace2 because it is built with C++, is independent of third-party libraries, and is compatible with X86, iOS, and Android systems. We used pretrained models from the SeetaFace2 project. According to the SeetaFace2 document, Cascaded-CNN is used as a face-detection algorithm, achieving 92% in the FDDB public dataset. FEC-CNN is used as a face landmaker algorithm, achieving a 0.069 average positioning error on the 300-W Challenge public dataset. ResNet50 is used for facial feature extraction/comparison with 25 million parameters, and the model has been pretrained with 33 million photos with an accuracy rate of more than 98% in the general 1:N scenario on a 1000-person dataset when the error acceptance rate is 1%. Figure 2 shows the flow chart of the processes.

Table 4.
Typical Opensource Projects for Facial Recognition.

Figure 2.
The flow chart of face recognition.
Liveness Detection: We chose the open-source project FeatherNets for liveness detection in the implementation, because several models provided by the project achieve the goal of low computing cost (about 80 M FLOPs), small model size (0.35 M parameters), and complete functionality (applicable to infrared images and depth images, etc.). Table 5 shows the test results of the models within the FeatherNets project.

Table 5.
Test Results of Liveness Detection Models.
4.5. Enclave Module (EM)
The BioShare Enclave Module is implemented as trusted code that runs in the Intel SGX enclave on the server side. On other TEEs such as ARM TrustZone and RISC-V keystone, we have to develop new code due to incompatibilities between them. In order to achieve the goal “develop once and deploy anywhere”, we use Microsoft Open Enclave SDK [46] to resolve compatibility issues between different TEEs, and other opensource projects including Google Asylo [47] and Huawei secGear [48] etc., provide similar functionality.
We have developed invocation interfaces to authenticate both facial image data and facial feature data, and experimenters can specify either raw data or feature data in service requests from network applications. We use the open-source code SeetaFace2 to conduct facial recognition and comparison. If the input is facial feature data, the service request will be processed with high performance due to the low computing overhead of the feature comparison algorithm, but this is achieved with low compatibility because the input feature data must be extracted with the same algorithm as that of the Enclave Module. If the input is facial image data, the service request will be processed with higher computing costs but with better compatibility. The experimental results are described in Section 5.2.
4.6. Secured Communication Module (SCM)
The BioShare Secured Communication Module is implemented as trusted functions running in trusted environments on both the terminal and server sides to provide cryptographic services. In our implementation, we choose Advanced Encryption Standard (AES) as the symmetric encryption algorithm and specify 128 or 192 bytes as the key length to ensure a sufficient encryption intensity. We select RSA or ECC as the asymmetric encryption algorithm, specify 3072 or 7680 bytes as the key length for RSA, and 256 or 384 bytes as the key length for ECC; and we specify the SHA-256 algorithm in the hash value calculation.
During the entire lifecycle of each transaction, all biometric data are transmitted in encrypted format in untrusted environments, and decrypted and processed only in trusted environments; and the result is returned with a digital signature to ensure non-repudiation.
5. Evaluation and Analysis
We now evaluate and analyze BioShare in terms of terminal-side performance, server-side performance, communication performance, and holistic security.
5.1. Overview
BioShare processes service requests from network applications in either forwarding mode or authorized mode, and we measure the time overhead of processing a service request in both modes.
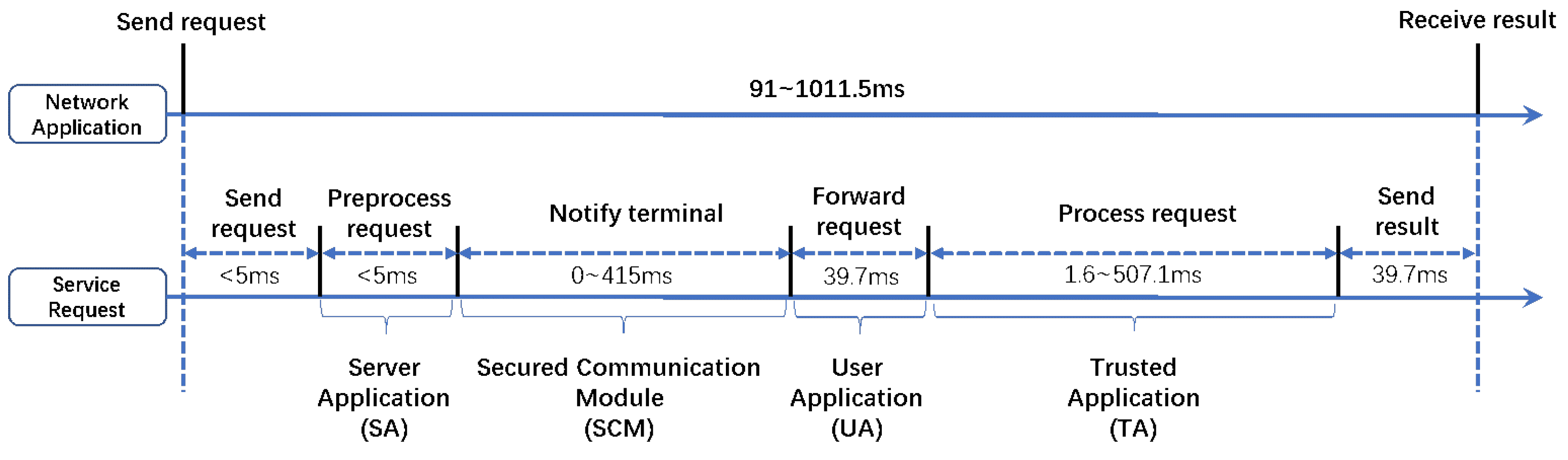
In forwarding mode, the server forwards the service request to the user terminal, as shown in Figure 3. The total overhead of processing a service request varies from 91 ms to 1011.5 ms, and the major parts are the request-processing cost and the server-client communication cost, which are evaluated in Section 5.2 and Section 5.4.
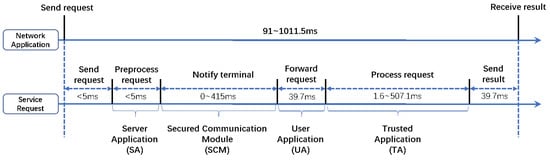
Figure 3.
Overhead Imposed by BioShare in Processing a Service Request with Forwarding Mode.
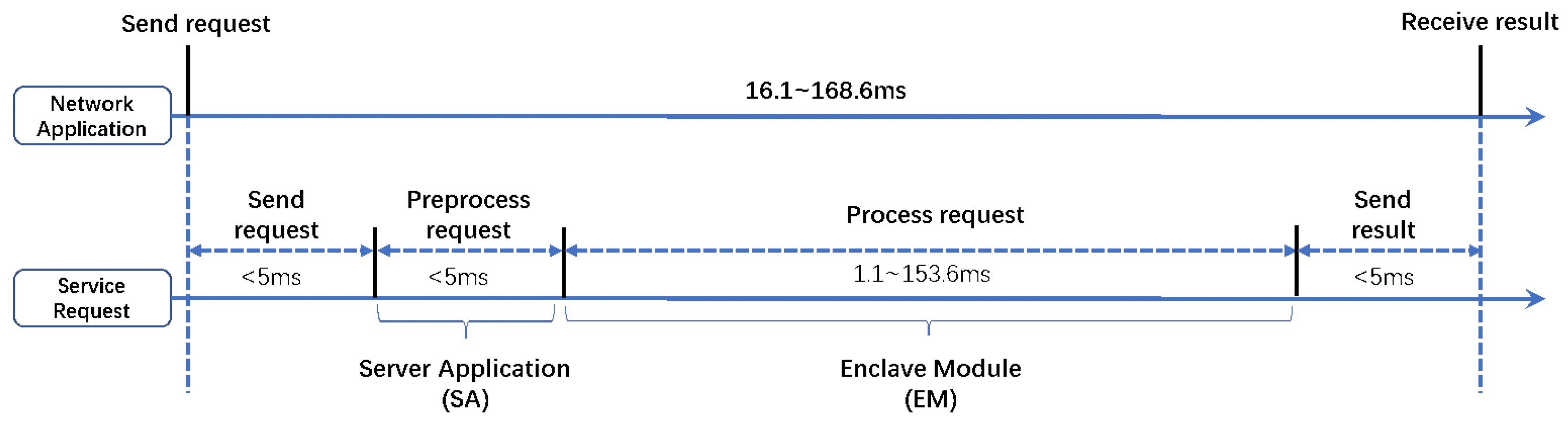
In authorized mode, the server processes service requests in the server enclave under user authorization, as shown in Figure 4. The total overhead of processing a service request varies from 16.1 ms to 168.6 ms, and the major part is the request-processing cost, which is evaluated in Section 5.3.
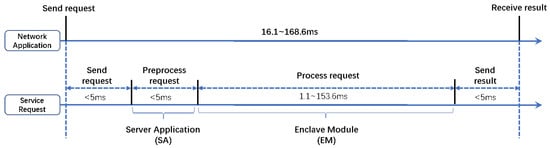
Figure 4.
Overhead Imposed by BioShare in Processing a Service Request with Authorized Mode.
5.2. Performance Evaluation of Terminal TEE
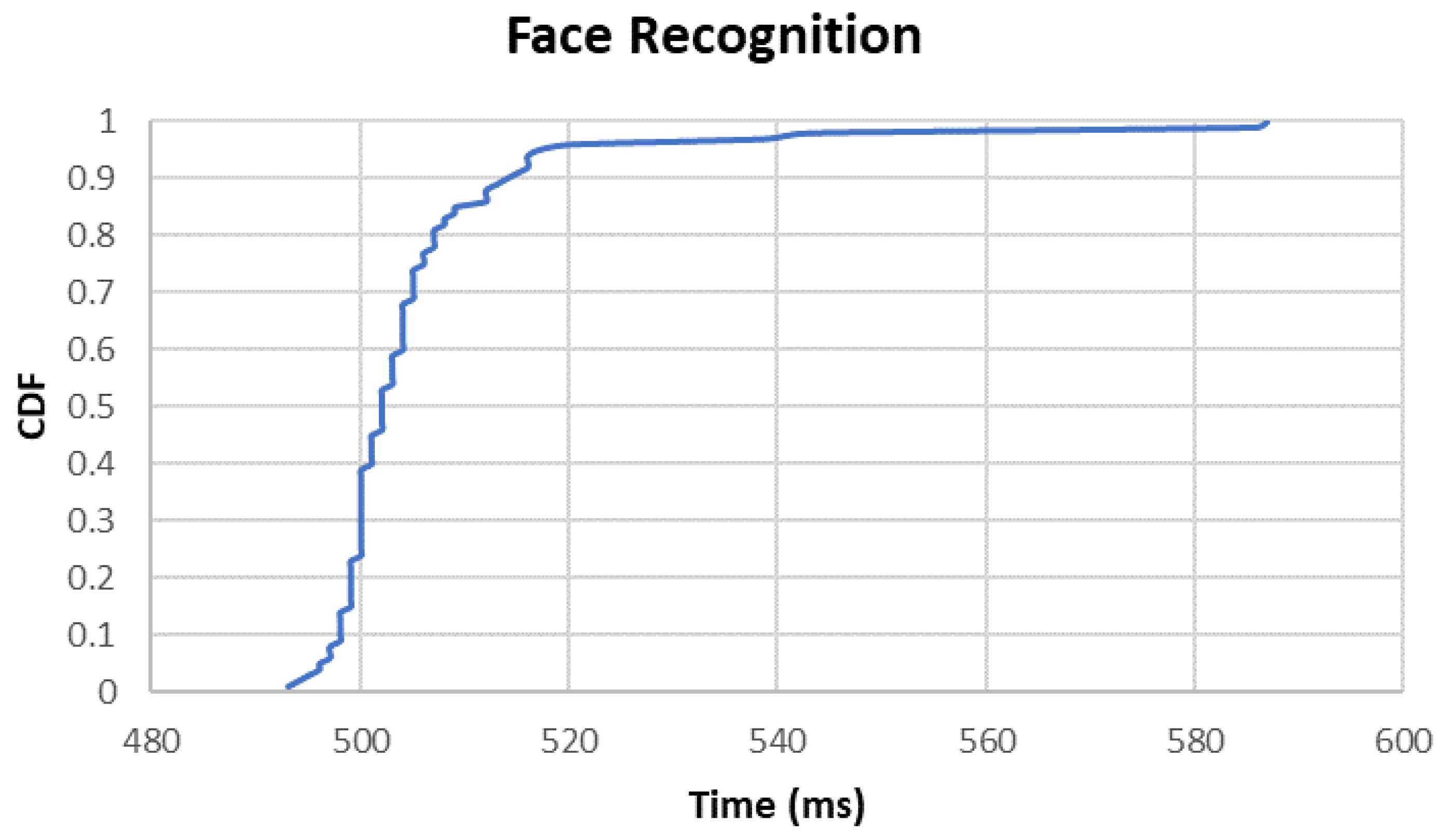
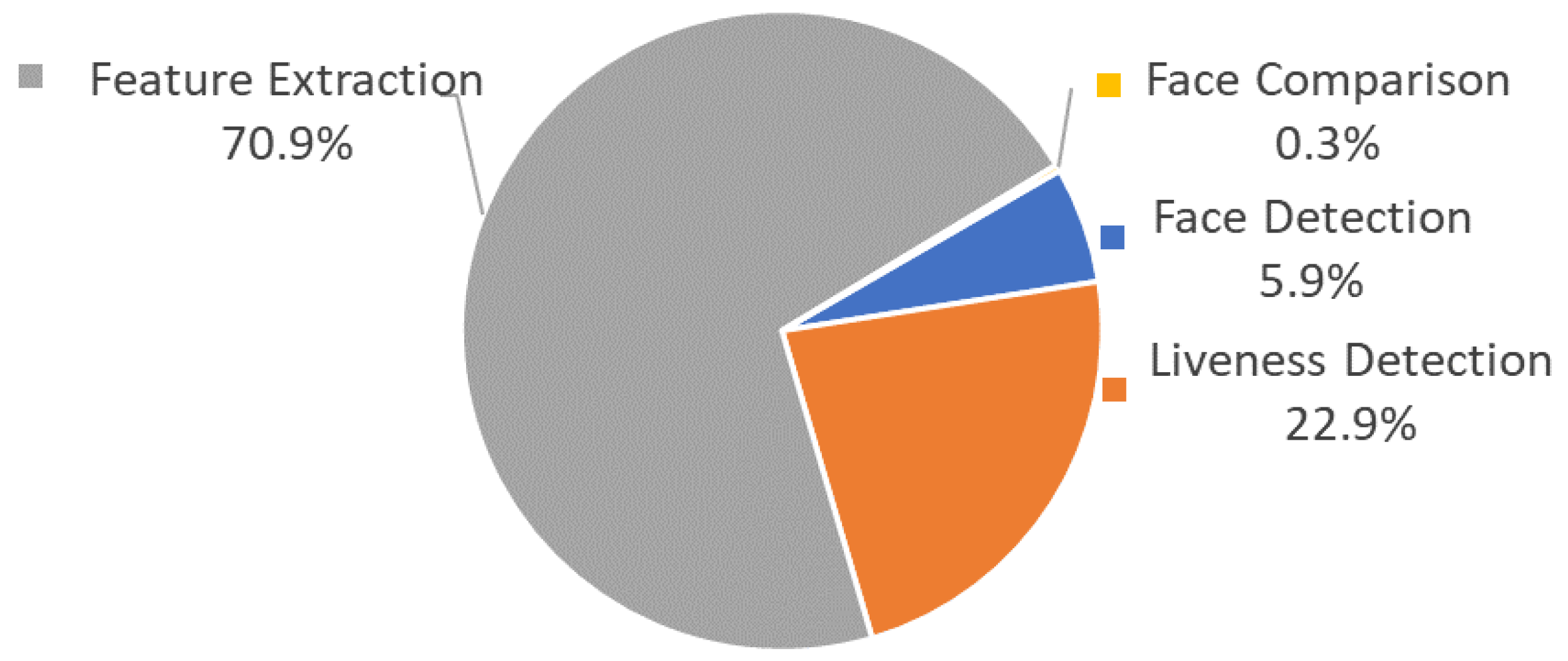
We measure the performance of the terminal TEE in conducting facial authentication upon different data inputs. The overhead of face recognition is 507.1 ms upon facial raw image input, while the overhead of face comparison reduces to 1.6 ms upon facial feature data input, as shown in Table 6. Figure 5 shows the cumulative distribution of time consumption in face recognition, and we can see that the performance of the terminal TEE is quite stable. We perform further research on each step of face recognition and find that feature extraction and liveness detection are the most time-consuming steps, accounting for 70.9% and 22.9%, respectively, as shown in Figure 6.

Table 6.
Overhead of TA in Processing Facial Recognition.
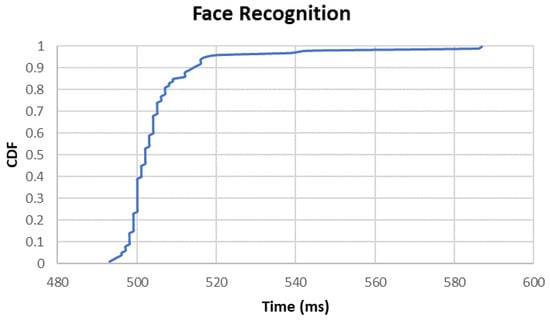
Figure 5.
CDF of Time Consumption of Face Recognition.
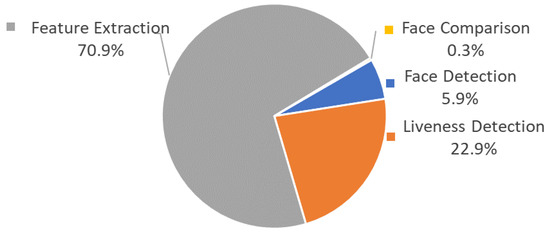
Figure 6.
Overhead Proportion of Each Step in Facial Recognition.
We measure the prediction accuracy rate of facial recognition with an actual business dataset of 329 pre-captured photos with a resolution of 640 × 480 from 110 employees. In the test, we compare each photo in the dataset with other photos, and the test results are shown in Table 7. The accuracy rate is 99.937%, the false acceptance rate (FAR) is 0.054%, and the false rejection rate (FRR) is 1.524%, which meets business requirements in most scenarios.

Table 7.
Test Results of Facial Recognition and Comparison.
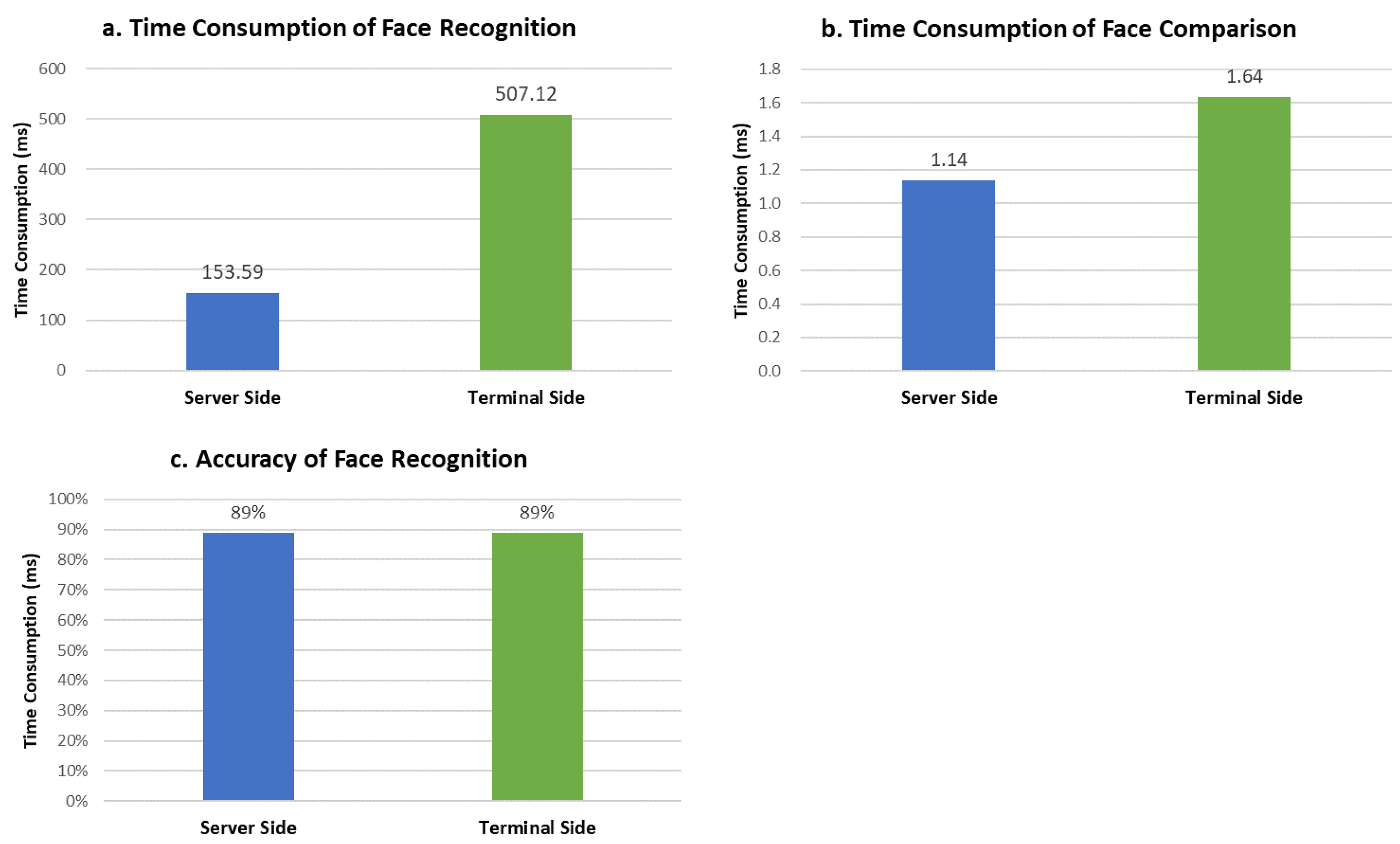
We measure the performance difference between the terminal TEE and the server enclave during facial authentication. To ensure the comparability of experimental results, we specify that the same algorithmic code runs in a single thread on a single CPU core in both environments. The evaluation results show that the face-recognition cost of the terminal TEE is more than three times that of the server enclave, the face-comparison overhead on both sides is as low as 1–2 ms, and the face-recognition accuracy is equal on both sides. Please refer to Figure 7 for more details.
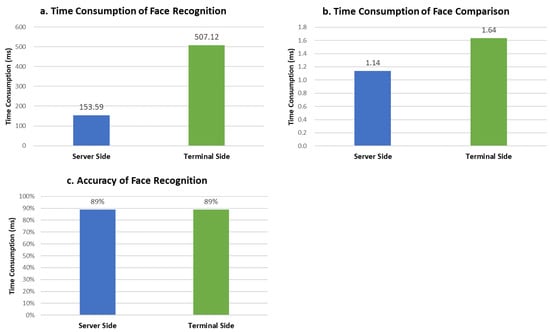
Figure 7.
Performance Difference between Terminal TEE and Server Enclave.
5.3. Performance Evaluation of Server Enclave
The key challenge with server-side facial authentication is the performance of the server enclave, which differs across CPU platforms. Our demo implementation works fine on the Pentium Silver CPU enclave with four physical cores and 128 MB RAM at most for low or moderate load scenarios, but more powerful enclave environments with more CPU cores and higher RAM support are required in high load scenarios. Table 8 lists some key indicators of enclaves on specific Intel CPU platforms.

Table 8.
Key Indicators of Enclaves on Different CPU Platforms.
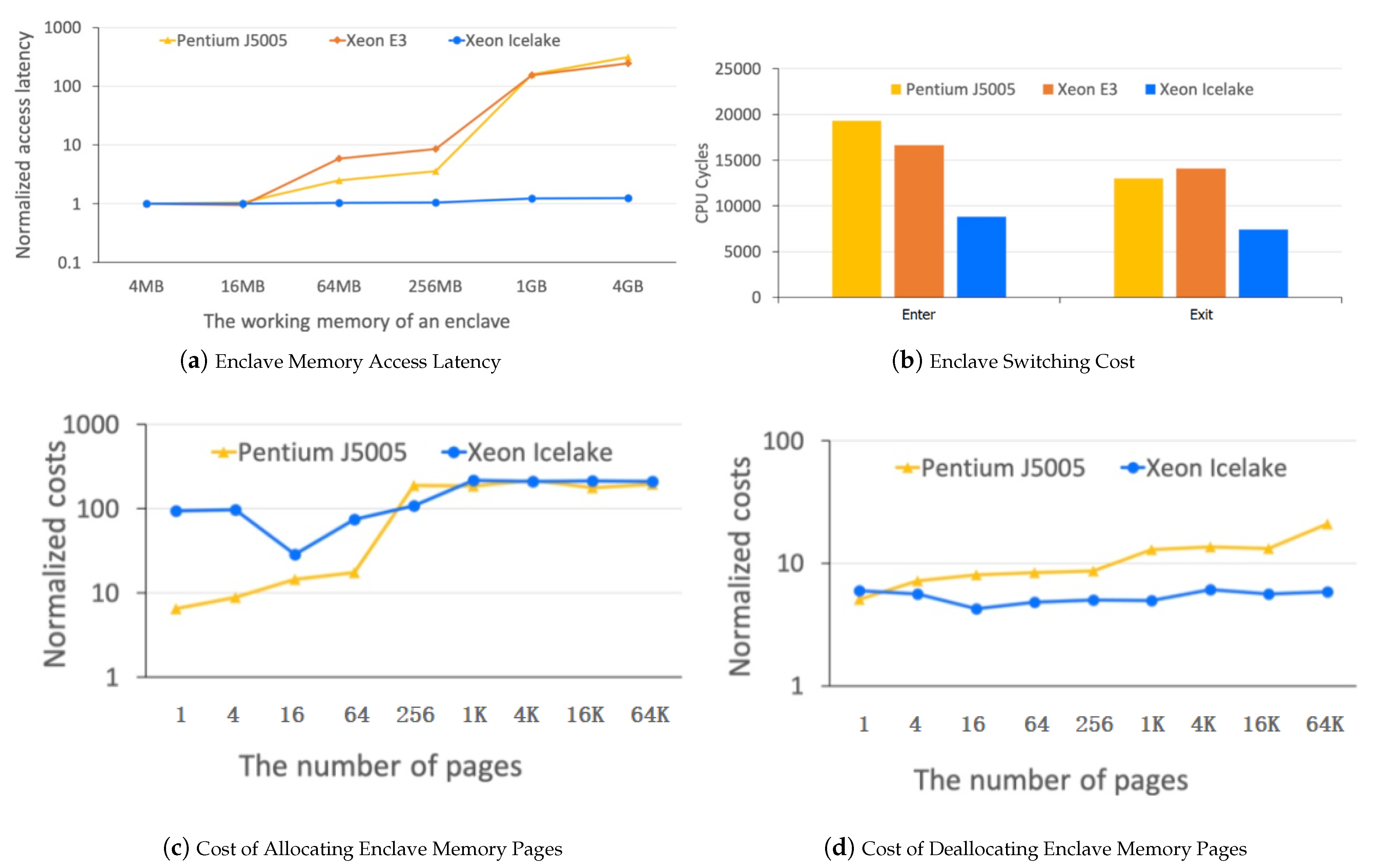
Generally, the performance overhead of server enclaves consists of three major parts: enclave memory access latency, enclave switching cost, and enclave dynamic-memory-management cost. Figure 8 lists the evaluation results of the three parts in professional tests [55]. Specifically, on the Intel Xeon Icelake platform, the overhead caused by enclave memory access latency is almost negligible, the enclave switching cost is less than 10,000 CPU lifecycles, and the enclave dynamic-memory-management cost is quite high. The performance analysis is instructive for further optimization of the current implementation.
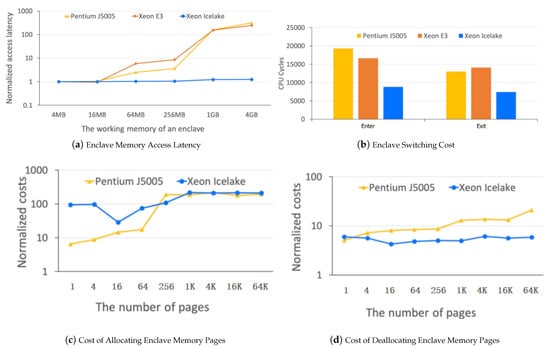
Figure 8.
Performance Overhead of Enclaves on Intel SGX Platforms.
5.4. Performance Analysis of Mobile Communication
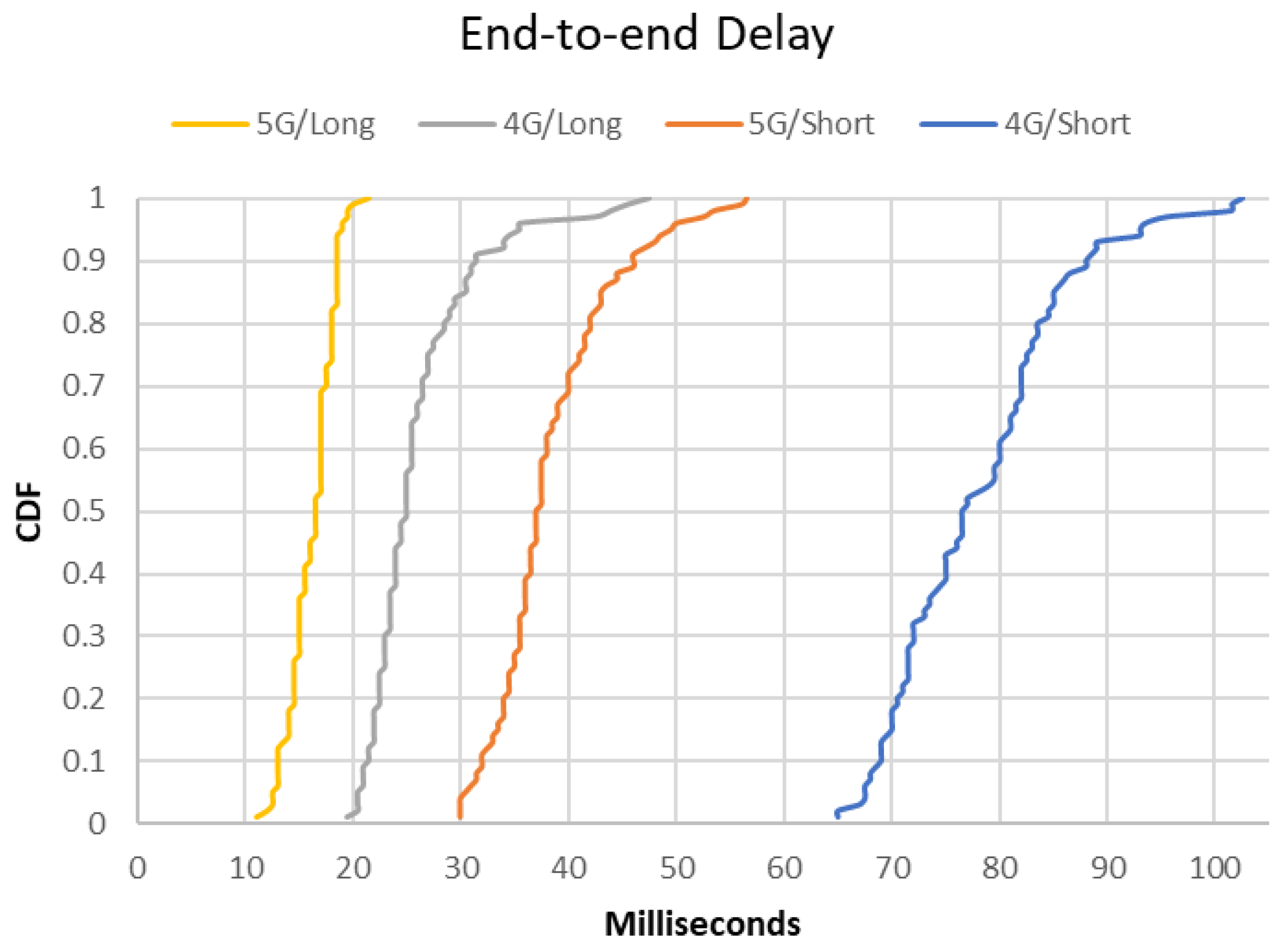
Most user terminals communicate with the server through short or long TCP/IP connections over a 4G/5G network, and we measure the end-to-end delays of different communication methods. Based on the experiment, the average delay is 39.7 ms for one-way trips between the terminal and the server, long TCP/IP connections have lower latency than short connections (average 21.1 ms vs. 58.3 ms), and 5G networks show better performance than 4G (average 27.3 ms vs. 52.1 ms). Figure 9 shows the experimental results in detail.
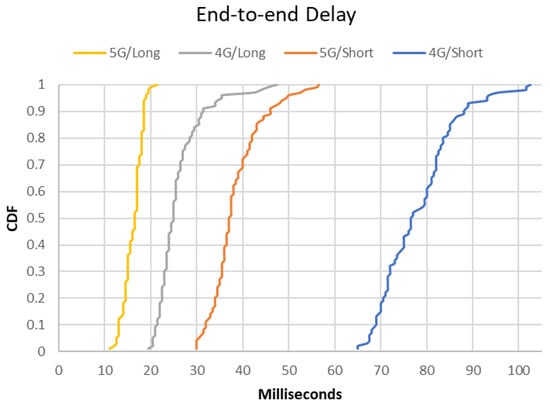
Figure 9.
CDF of End-to-End Communication Delays.
We have performed further research on the performance of the notification mechanism used in BioShare. We kill the user application on the user terminal, relaunch it with the notification services [56], and measure the communication delay from the server to the terminal. Based on the experiment, it takes 415 ms for Aurora Mobile JPush to notify the terminal from the server, which is close to the reported time delay for Apple Push Notification Service and Google Firebase Cloud Messaging, as shown in Table 9.

Table 9.
Normal Delay of Notification Services.
5.5. Security Analysis of BioShare
We evaluate the security level of secure communication channels between the terminal TEE and the server enclave by analyzing the cryptographic algorithms used in BioShare, as shown in Table 10. In the implementation, we specify key lengths of 128/192 for the AES algorithm; thus, the security strength of symmetric encryption is 128/192. We specify key lengths of 3072/7680 for the RSA algorithm and key lengths of 256/384 for the ECC algorithm, and therefore, the security strength of asymmetric encryption is 128/192. We use SHA-256 as the hash algorithm, and the security strength is 256. In conclusion, the security strength of secure communication channels is 128/192, which fulfils and even exceeds the values recommended by the National Institute of Standards and Technology (NIST) [57].

Table 10.
Security Strength of Cryptographic Algorithms of BioShare.
The terminal TEE empowers the Trusted Application with secure hardware, secure OS, secure storage, and secure provisioning, etc. The server enclave empowers the Enclave Module with isolated execution, encrypted RAM, secure storage, sealing and attestation mechanisms, etc. The TEEs on both terminal and server sides provide trusted environments to process and store biometric data at a high security level, and Table 11 lists some security properties of trusted environments.

Table 11.
Security Properties of Terminal TEE and Server Enclave.
6. Discussion and Future Work
This paper makes the case for biometric authentication as a trusted service under users’ full control, and demonstrates how we addressed several challenges in making this service secure, practical, and efficient. Our solution reconciles the demand for open services and the requirement for privacy security, and shows comparative advantages over the currently available solutions. Table 12 lists the details of the comparisons. When compared to terminal local-processing solutions, such as Apple Touch ID and Windows Hello, as shown in Section 2.1, our solution extends open biometric authentication services from local mobile apps to remote network applications with high security levels. When compared to centralized-processing solutions such as facial recognition payment systems, as listed in Section 2.3, BioShare can avoid both unintentional leakages and the intentional abuse of biometric data by keeping private data in an encrypted format within secure storage, and running trusted code in isolated secure environments. Based on our test results, the BioShare implementation meets the performance requirements of most human-interactive businesses and fulfills the security requirements of recommended standards for business systems.

Table 12.
Security Properties of Terminal TEE and Server Enclave.
We now discuss important challenges that are outside the focus of this paper.
TEE Fragmentation: BioShare relies on terminal TEEs and server enclaves to handle service requests; however, the TEE market as a whole is currently fragmented. In both terminal and server markets, different manufacturers offer different TEE solutions that are incompatible with each other, such as QSEE/iTrustee on the terminal side and SGX/TrustZone on the server side, and therefore, we have to develop native code for each manufacturer, and even for each system model. This tremendously increases the development costs and implementation complexity for large-scale applications of BioShare, and we need a universal standard and interface protocol for terminal TEEs as well as server enclaves.
Network Attacks: BioShare opens up terminal capabilities to network applications, meaning that the terminals are faced with various network attacks, such as replay attacks and man-in-the-middle attacks. In addition, the server connects to numerous terminals through TCP/IP connections, and therefore is put at risk of cyber-attacks such as impersonation attacks and distributed denial of service attacks. We need to design defense technology and systems against various network attacks on user terminals, as well as the BioShare server.
Business Model: BioShare relies on users to install the User Application on individual terminals, raising the question of whether there are proper incentives for users to do so. We need a business model for BioShare to ensure that all participants can benefit from service provision. One possible solution is to charge a fee for each service request from network applications, and reward the user with a certain proportion of the income.
7. Conclusions
In this paper, we make the case for a unified framework that provides trusted biometric authentication services to network applications under the user’s full control of personal biometric data. Our demo implementation of BioShare provides: (a) authorized and forward service modes to ensure users’ full control of personal data, (b) standard interfaces to ensure service openness to network applications, (c) trusted computation to prevent privacy leaks on both terminal and server sides, (d) secure channels to ensure data security during transmission, and (e) a unified framework to ensure effective collaboration between user terminals and the server. We showed that our system is efficient, based on standard interfaces, and provides a unified terminal–server collaboration mode to support new biometric services under user control. As part of our future work, we are designing standard TEE solutions to facilitate the development of new biometric service experiments, developing defense technology and systems against various network attacks, and exploring business models to ensure that each user benefits from participation.
Author Contributions
Conceptualization, Q.S. and J.W.; methodology, Q.S.; investigation, Q.S. and W.Y.; formal analysis, Q.S. and W.Y.; resources, Q.S. and J.W.; validation, Q.S. and W.Y.; visualization, Q.S.; writing—original draft preparation, Q.S. and W.Y.; writing—review and editing, Q.S. and J.W. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the Program of Shanghai Academic/Technology Research Leader under Grant 19XD1433700.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The National Engineering Laboratory for Electronic Commerce and Electronic Payment provided the experimental environment for the model validation in this article, and we are thankful for suggestions from academician Chai Hongfeng and manager Chen Chengqian for model improvements.
Conflicts of Interest
The authors declare no conflict of interest.
References
- General Data Protection Regulation. Available online: https://gdpr-info.eu/ (accessed on 24 February 2022).
- Gobeo, A.; Fowler, C.; Buchanan, W.J. GDPR and cyber security for business information systems. In GDPR and Cyber Security for Business Information Systems; River Publishers: Gistrup, Denmark, 2020; pp. i–xix. [Google Scholar] [CrossRef]
- Layton, R.; Elaluf-Calderwood, S. A social economic analysis of the impact of GDPR on security and privacy practices. In Proceedings of the 2019 12th CMI Conference on Cybersecurity and Privacy (CMI), Copenhagen, Denmark, 28–29 November 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Bonta, R. California Consumer Privacy Act (CCPA). Available online: https://oag.ca.gov/privacy/ccpa (accessed on 24 February 2022).
- Stallings, W. Handling of Personal Information and Deidentified, Aggregated, and Pseudonymized Information under the California Consumer Privacy Act. IEEE Secur. Priv. 2020, 18, 61–64. [Google Scholar] [CrossRef]
- Personal Information Protection Law. Available online: http://www.npc.gov.cn/npc/c30834/202010/569490b5b76a49c292e64c416da8c994.shtml (accessed on 24 February 2022).
- About Touch ID Advanced Security Technology. Available online: https://support.apple.com/en-us/HT204587 (accessed on 24 February 2022).
- About Face ID Advanced Technology. Available online: https://support.apple.com/en-us/HT208108 (accessed on 24 February 2022).
- Learn about Windows Hello and Set It Up. Available online: https://support.microsoft.com/en-us/windows/learn-about-windows-hello-and-set-it-up-dae28983-8242-bb2a-d3d1-87c9d265a5f0 (accessed on 24 February 2022).
- Xu, Y.; Lu, G.; Lu, Y.; Zhang, D. High resolution fingerprint recognition using pore and edge descriptors. Pattern Recognit. Lett. 2019, 125, 773–779. [Google Scholar] [CrossRef]
- Jo, Y.H.; Jeon, S.Y.; Im, J.H.; Lee, M.K. Security analysis and improvement of fingerprint authentication for smartphones. Mob. Inf. Syst. 2016, 2016, 8973828. [Google Scholar] [CrossRef]
- Cavazos, J.G.; Phillips, P.J.; Castillo, C.D.; O’Toole, A.J. Accuracy comparison across face recognition algorithms: Where are we on measuring race bias? arXiv 2019, arXiv:1912.07398. [Google Scholar] [CrossRef] [PubMed]
- Rana, A.; Ciardulli, A. Identity verification through face recognition, android smartphones and NFC. In Proceedings of the World Congress on Internet Security (WorldCIS-2013), London, UK, 9–12 December 2013; pp. 162–163. [Google Scholar] [CrossRef]
- Baqeel, H.; Saeed, S. Face detection authentication on smartphones: End users usability assessment experiences. In Proceedings of the 2019 International Conference on Computer and Information Sciences (ICCIS), Aljouf, Saudi Arabia, 3–4 April 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Hongo, K.; Takano, H. Personal authentication with an iris image captured under visible-light condition. In Proceedings of the 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Miyazaki, Japan, 7–10 October 2018; pp. 2266–2270. [Google Scholar] [CrossRef]
- Ali, S.A.; Shah, M.A.; Javed, T.A.; Abdullah, S.M.; Zafar, M. Iris recognition system in smartphones using light version (LV) recognition algorithm. In Proceedings of the 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, UK, 7–8 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Raja, K.B.; Raghavendra, R.; Busch, C. Smartphone based robust iris recognition in visible spectrum using clustered k-means features. In Proceedings of the 2014 IEEE Workshop on Biometric Measurements and Systems for Security and Medical Applications (BIOMS) Proceedings, Rome, Italy, 17 October 2014; pp. 15–21. [Google Scholar] [CrossRef]
- Garcia-Martin, R.; Sanchez-Reillo, R. Vein Biometric Recognition on a Smartphone. IEEE Access 2020, 8, 104801–104813. [Google Scholar] [CrossRef]
- Garcia-Martin, R.; Sanchez-Reillo, R. Deep Learning for Vein Biometric Recognition on a Smartphone. IEEE Access 2021, 9, 98812–98832. [Google Scholar] [CrossRef]
- Zou, Q.; Wang, Y.; Wang, Q.; Zhao, Y.; Li, Q. Deep Learning-Based Gait Recognition Using Smartphones in the Wild. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3197–3212. [Google Scholar] [CrossRef]
- Coakley, M.J.; Monaco, J.V.; Tappert, C.C. Keystroke biometric studies with short numeric input on smartphones. In Proceedings of the 2016 IEEE 8th International Conference on Biometrics Theory, Applications and Systems (BTAS), Niagara Falls, NY, USA, 6–9 September 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Kutzner, T.; Ye, F.; Bönninger, I.; Travieso, C.; Dutta, M.K.; Singh, A. User verification using safe handwritten passwords on smartphones. In Proceedings of the 2015 Eighth International Conference on Contemporary Computing (IC3), Washington, DC, USA, 20–22 August 2015; pp. 48–53. [Google Scholar] [CrossRef]
- Daniel, N.; Anitha, A. A study on recent trends in face spoofing detection techniques. In Proceedings of the 2018 3rd International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 15–16 November 2018; pp. 583–586. [Google Scholar] [CrossRef]
- Chen, H.; Chen, Y.; Tian, X.; Jiang, R. A Cascade Face Spoofing Detector Based on Face Anti-Spoofing R-CNN and Improved Retinex LBP. IEEE Access 2019, 7, 170116–170133. [Google Scholar] [CrossRef]
- Simanjuntak, G.D.; Nur Ramadhani, K.; Arifianto, A. Face spoofing detection using color distortion features and principal component analysis. In Proceedings of the 2019 7th International Conference on Information and Communication Technology (ICoICT), Kuala Lumpur, Malaysia, 24–26 July 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Luo, J.; Hu, F.; Wang, R. 3D face recognition based on deep learning. In Proceedings of the 2019 IEEE International Conference on Mechatronics and Automation (ICMA), Tianjin, China, 4–7 August 2019; pp. 1576–1581. [Google Scholar] [CrossRef]
- Xu, K.; Wang, X.; Hu, Z.; Zhang, Z. 3D face recognition based on twin neural network combining deep map and texture. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 1665–1668. [Google Scholar] [CrossRef]
- Li, Y.; Huang, X.; Zhao, G. Joint Local and Global Information Learning With Single Apex Frame Detection for Micro-Expression Recognition. IEEE Trans. Image Process. 2021, 30, 249–263. [Google Scholar] [CrossRef] [PubMed]
- Yao, L.; Xiao, X.; Cao, R.; Chen, F.; Chen, T. Three stream 3D CNN with SE block for micro-expression recognition. In Proceedings of the 2020 International Conference on Computer Engineering and Application (ICCEA), Guangzhou, China, 27–29 March 2020; pp. 439–443. [Google Scholar] [CrossRef]
- Suzaki, K.; Shimizu, K.; Oguchi, K. Feasible personal identification by eye blinking using wearable device. In Proceedings of the 2019 IEEE 15th International Colloquium on Signal Processing Its Applications (CSPA), Batu Feringghi,, Malaysia, 8–9 March 2019; pp. 266–269. [Google Scholar] [CrossRef]
- Anjos, A.; Chakka, M.M.; Marcel, S. Motion-based counter-measures to photo attacks in face recognition. IET Biom. 2013, 3, 147–158. [Google Scholar] [CrossRef]
- Alhazmi, O.; Malaiya, Y. Quantitative vulnerability assessment of systems software. In Proceedings of the Annual Reliability and Maintainability Symposium, 2005. Proceedings, Alexandria, VA, USA, 24–27 January 2005; pp. 615–620. [Google Scholar] [CrossRef]
- Arm TrustZone Technology. Available online: https://developer.arm.com/ip-products/security-ip/trustzone (accessed on 24 February 2022).
- Cerdeira, D.; Santos, N.; Fonseca, P.; Pinto, S. SoK: Understanding the prevailing security vulnerabilities in TrustZone-assisted TEE systems. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), Francisco, CA, USA, 17–21 May 2020; pp. 1416–1432. [Google Scholar] [CrossRef]
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Costan, V.; Lebedev, I.; Devadas, S. Secure Processors Part I: Background, Taxonomy for Secure Enclaves and Intel SGX Architecture; Now Publishers Inc.: Delft, The Netherlands, 2017. [Google Scholar]
- Costan, V.; Lebedev, I.; Devadas, S. Secure Processors Part II: Intel SGX Security Analysis and MIT Sanctum Architecture; Now Publishers Inc.: Delft, The Netherlands, 2017. [Google Scholar]
- Lee, D.; Kohlbrenner, D.; Shinde, S.; Asanović, K.; Song, D. Keystone: An open framework for architecting trusted execution environments. In Proceedings of the Fifteenth European Conference on Computer Systems (EuroSys’20), Heraklion, Greece, 27–30 April 2020; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Mobile Security Solutions Secure Mobile Technology | Qualcomm. Available online: https://www.qualcomm.com/products/features/mobile-security-solutions (accessed on 24 February 2022).
- Trusty TEE Android Open Source Project. Available online: https://source.android.com/security/trusty (accessed on 24 February 2022).
- GlobalPlatform Specifications Archive—GlobalPlatform. Available online: https://globalplatform.org/specs-library/ (accessed on 24 February 2022).
- Suzaki, K.; Nakajima, K.; Oi, T.; Tsukamoto, A. Library implementation and performance analysis of GlobalPlatform TEE internal API for intel SGX and RISC-V keystone. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 10–13 November 2020; pp. 1200–1208. [Google Scholar] [CrossRef]
- Chai, H.; Lu, Z.; Meng, Q.; Wang, J.; Zhang, X.; Zhang, Z. TEEI—A mobile security infrastructure for TEE integration. In Proceedings of the 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications, Beijing, China, 24–26 September 2014; pp. 914–920. [Google Scholar] [CrossRef]
- Intel® Software Guard Extensions (Intel® SGX). Available online: https://www.intel.com/content/www/us/en/architecture-and-technology/software-guard-extensions.html (accessed on 24 February 2022).
- Keystone. An Open Framework for Architecting TEEs. Available online: https://keystone-enclave.org/ (accessed on 24 February 2022).
- Open Enclave SDK. Available online: https://openenclave.io/sdk/ (accessed on 24 February 2022).
- Asylo: An Open, Flexible Framework for Enclave Applications. Available online: https://asylo.dev/ (accessed on 24 February 2022).
- secGear. Available online: https://gitee.com/src-openeuler/secGear (accessed on 24 February 2022).
- Vrankulj, A. Uniqul Launches Facial Recognition Payment System. Available online: https://www.biometricupdate.com/201307/uniqul-launches-facial-recognition-payment-system (accessed on 24 February 2022).
- About AliPay Facial Payment. Available online: https://opendocs.alipay.com/open/20180402104715814204/intro (accessed on 24 February 2022).
- About WeChat Facial Payment. Available online: https://pay.weixin.qq.com/wiki/doc/wxfacepay/ (accessed on 24 February 2022).
- About UnionPay Facial Payment. Available online: https://cn.unionpay.com/upowhtml/cn/templates/newInfo-nosub/9ed2b7ea4873410186ae96112fccfc7d/20191211194221.html (accessed on 24 February 2022).
- Notifications Overview—Apple Developer. Available online: https://developer.apple.com/notifications/ (accessed on 24 February 2022).
- Firebase Cloud Messaging. Available online: https://firebase.google.com/docs/cloud-messaging/ (accessed on 24 February 2022).
- Ant-Techfin. Performance Test Results of Intel SGX. Available online: https://my.oschina.net/u/4587334/blog/5014463 (accessed on 24 February 2022).
- About JPush. Available online: https://docs.jiguang.cn/jpush/guideline/intro/ (accessed on 24 February 2022).
- Giry, D. Keylength—NIST Report on Cryptographic Key Length and Cryptoperiod (2020). Available online: https://www.keylength.com/en/4/ (accessed on 24 February 2022).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).