Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace
Abstract
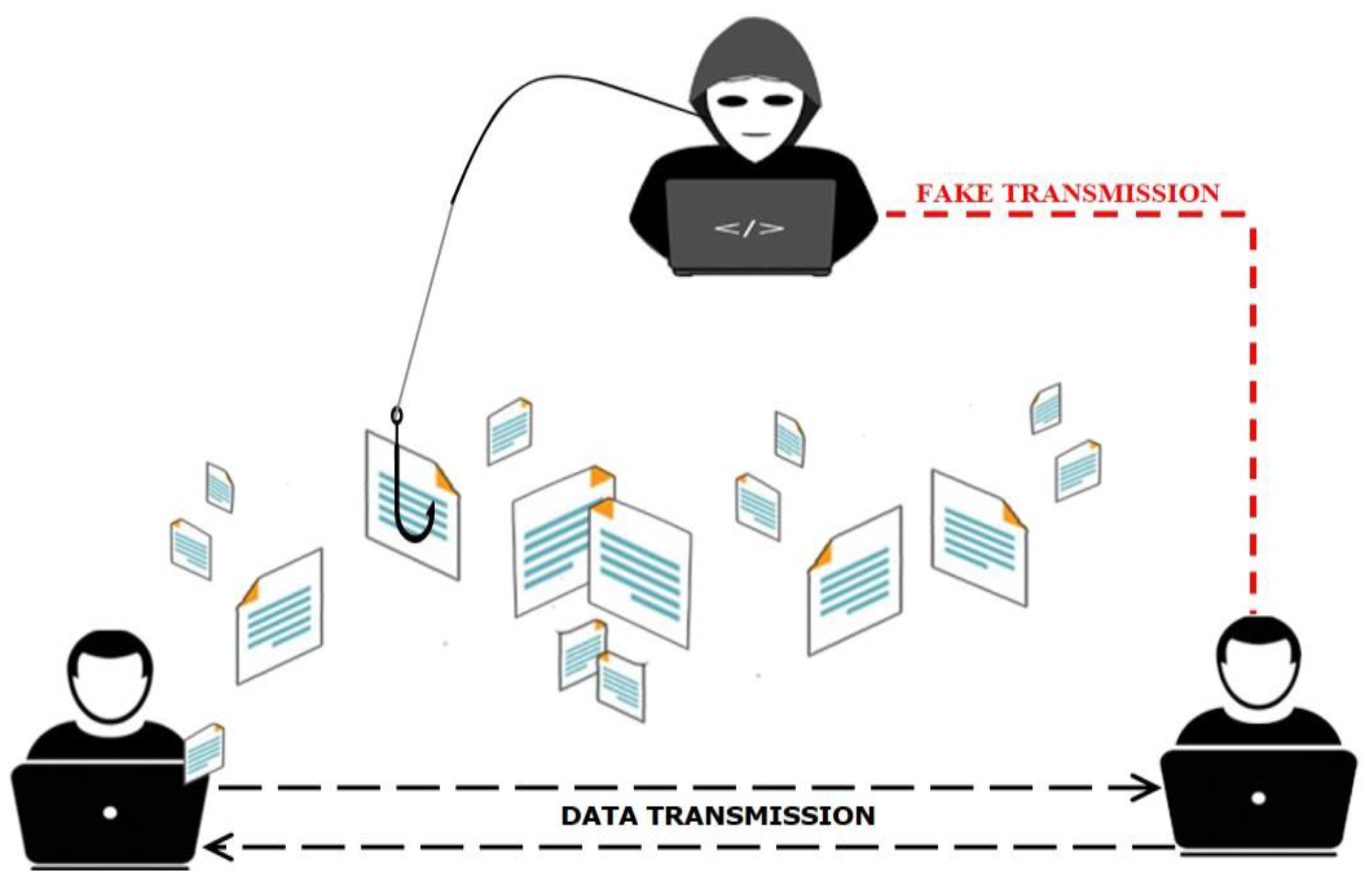
:1. Introduction
1.1. Cryptography
1.2. Vigenère Cipher
1.3. Contribution
2. Literature Review
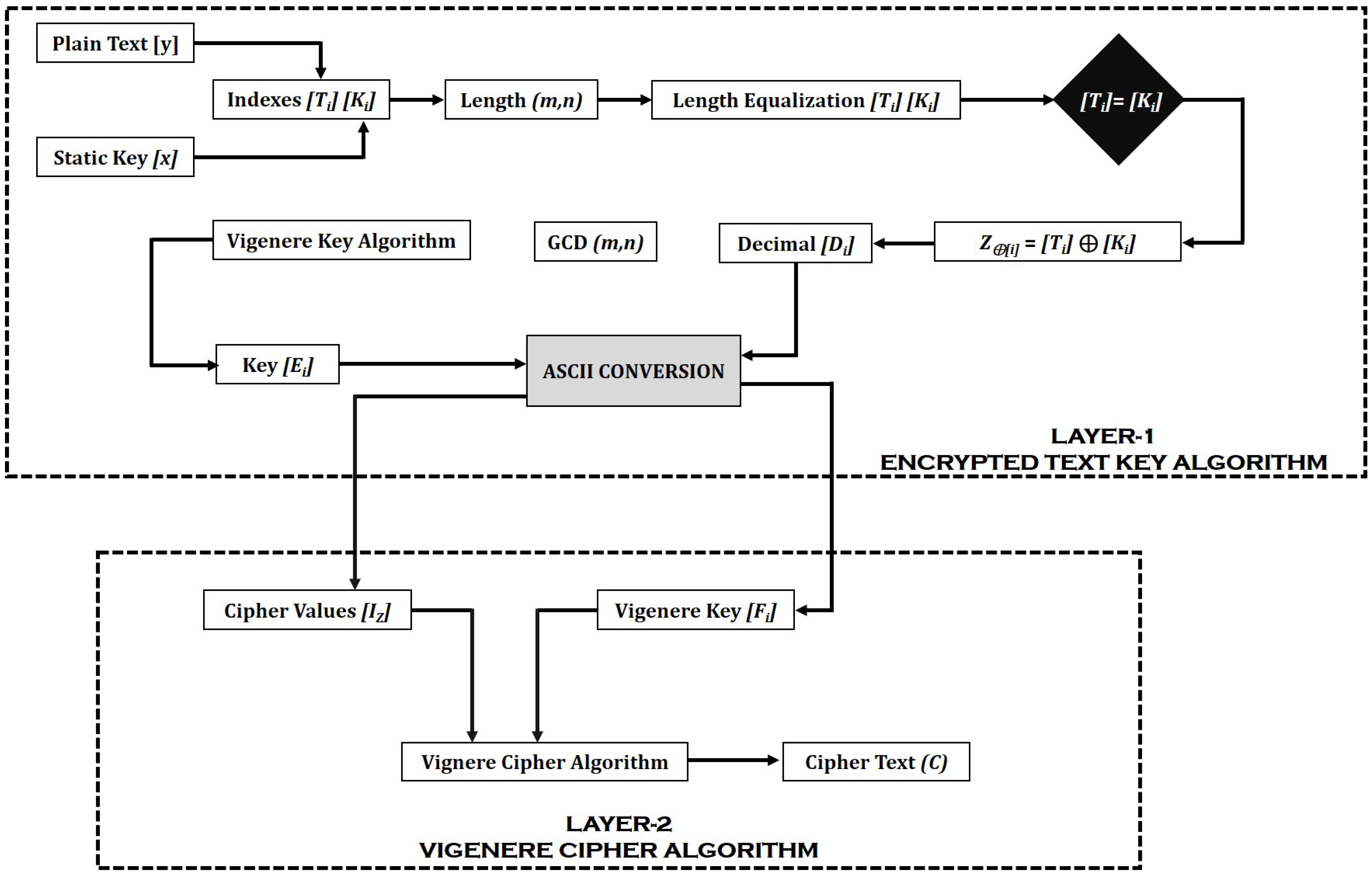
3. Proposed Algorithm
3.1. Work Overflow
3.2. Data Encryption Process
Key Management Process
| Algorithm 1: Encryption |
| Input: Plaintext, Static Key |
| Output: Ciphertext |
| 1. Plaintext = [y], static key = [x] |
| 2. Find the indexes [Kx] of key [x] |
| [xi] = |
| 3. nth indexes [Ki] of static key [xi] |
| [Ki] = |
| 4. Find the length (m) of static key [Ki]. |
| m = [Ki] + 1 |
| 5. Find the indexes [Ti] of text [y] |
| [yi] = |
| 6. nth-Index [Ti] of text [y] |
| [Ti] = |
| 7. Find the length (n) of text [Ti] |
| n = [Ti] + 1 |
| 8. Length equalization |
| IF [Ki] ≠ [Ti], THEN repeat [Ki] -> [Ti] times |
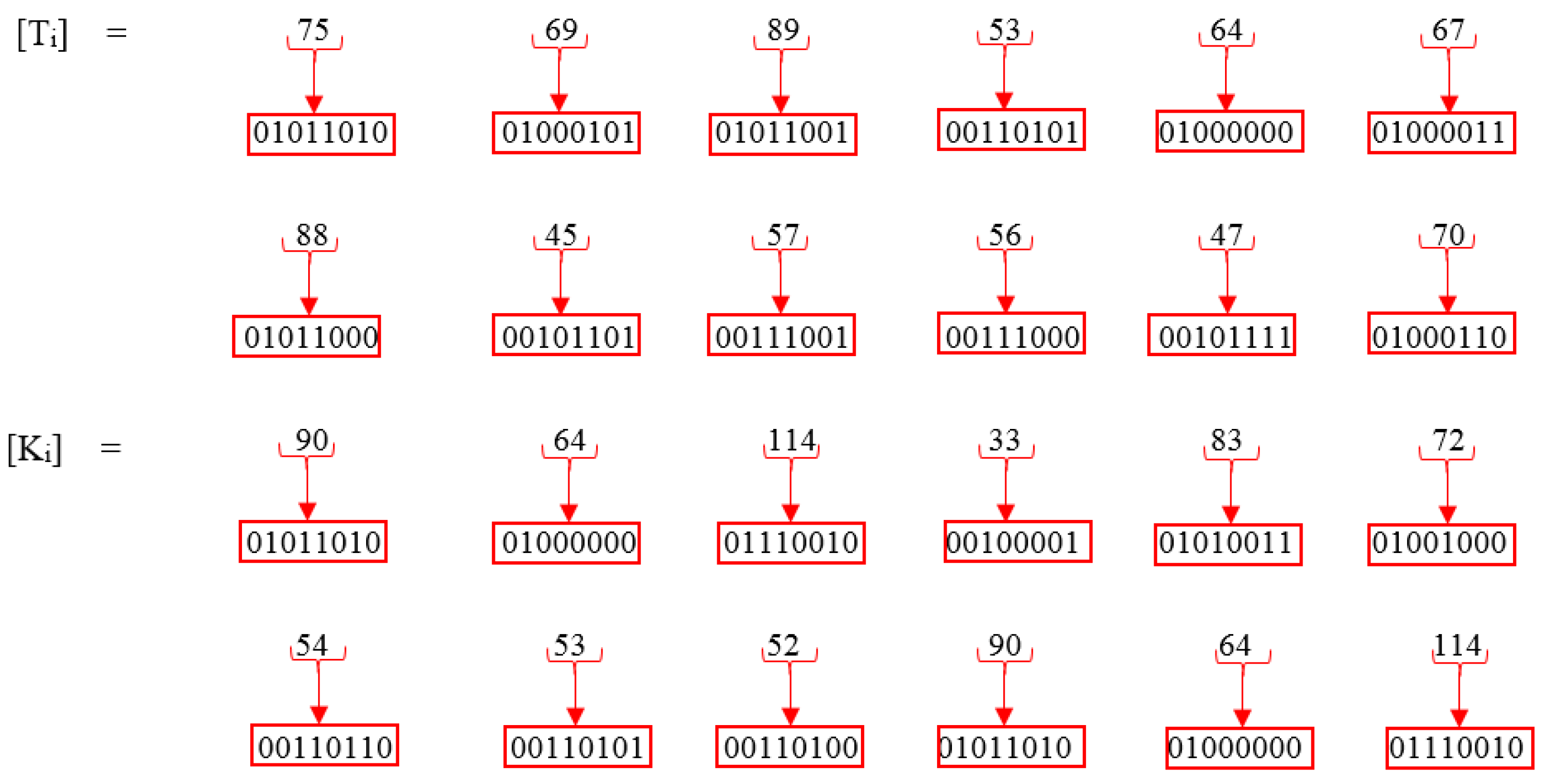
| 9. Convert [Ki] and [Ti] index values into binary form. |
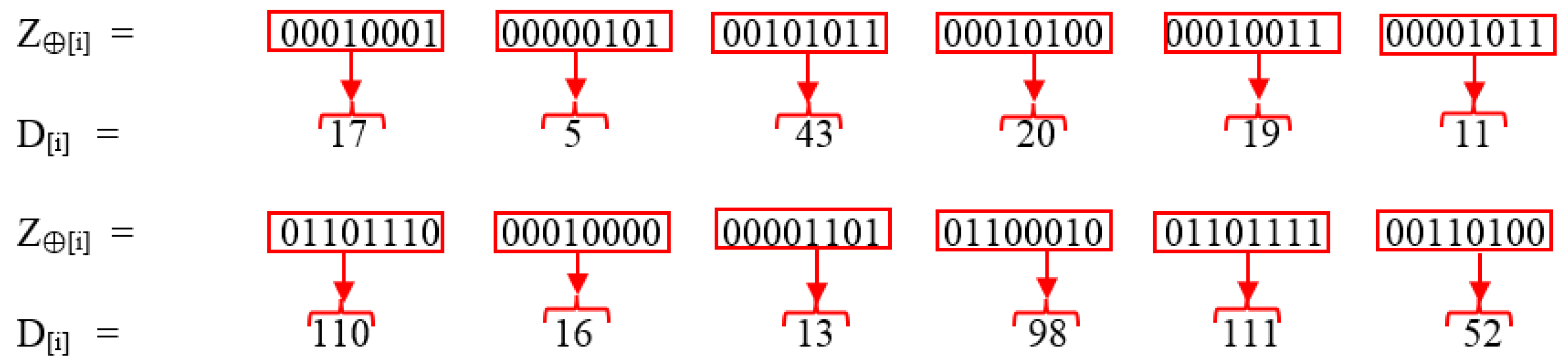
| 10. XOR [Ti] with [Ki]. |
| Z⊕[i] = ([T0] ⊕ [K0]) ([T1] ⊕ [K1]) ……… ([Tn] ⊕ [Kn]) |
| Z⊕[i] = Ti Ki |
| 11. Convert Z⊕[i] into decimal format [D[i]]. |
| D[i] = |
| 12. Find GCD (δ) of (m) and (n). |
| δ = GCD (m, n) |
| 13. Obtain key (E[i]) by adding “δ” with [D[i]]. |
| E[i] = (D[1] + δ) (D[2] + δ) (D[3] + δ) … (D[n] + δ) |
| E[i] = |
| If E[i] > 25 then E[i]–24 |
| 14. Convert step 13 [E[i]] values to equivalent ASCII characters [F[i]]. |
| F[i] = |
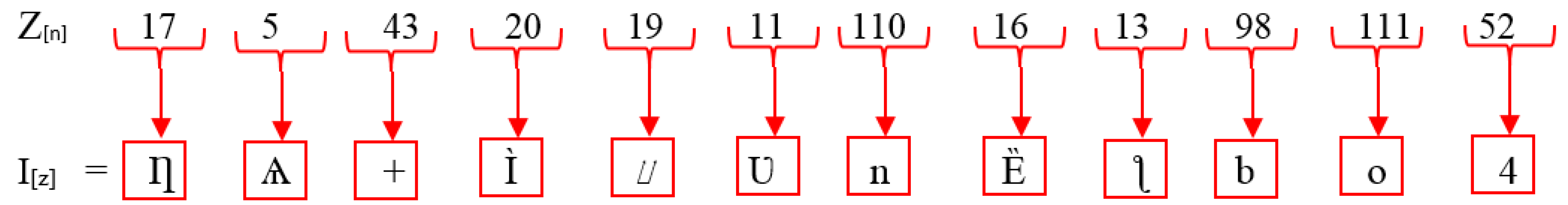
| 15. Convert step 11 [D[i]] values to equivalent ASCII characters (I[z]). |
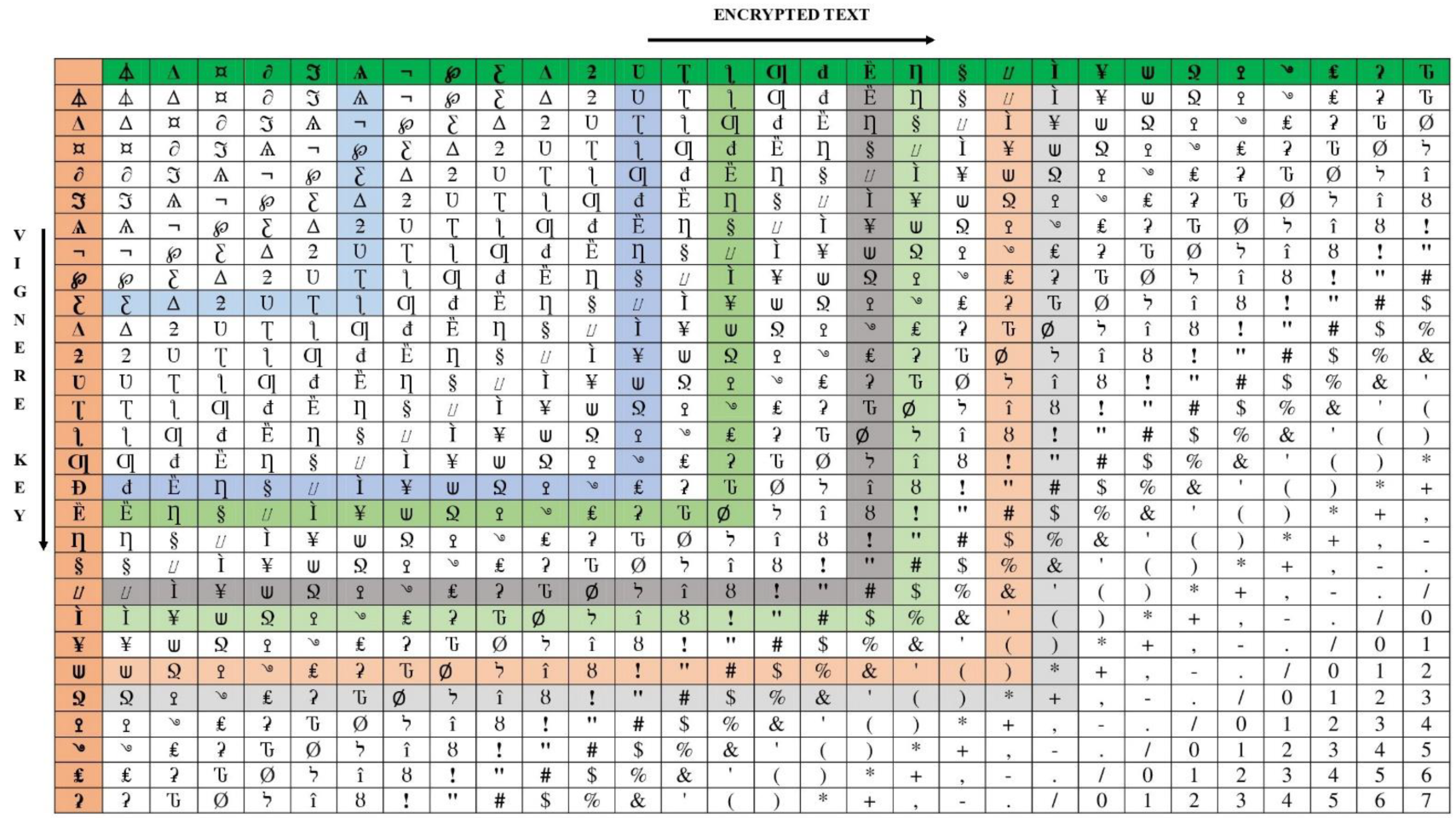
| 16. Apply the Vigenère cipher algorithm on I[z] and F[i]. |
| 17. Obtain ciphertext (C). |
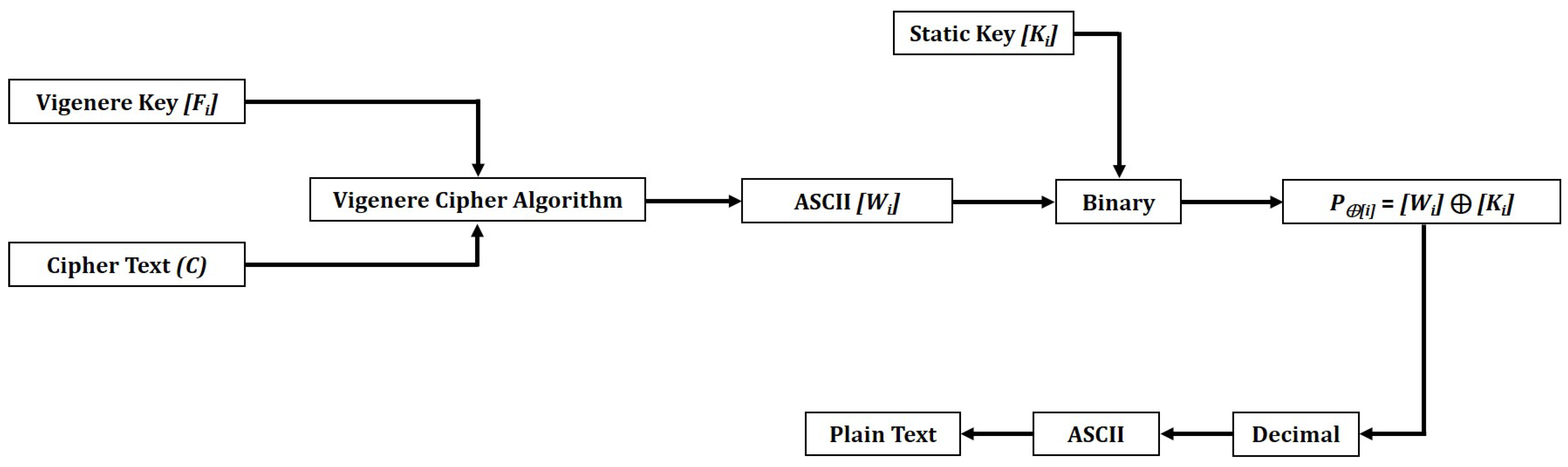
3.3. Data Decryption Process
| Algorithm 2: Decryption |
| Input: Ciphertext, Static Key, Vigenère Key |
| Output: Plaintext |
| 1. Apply Vigenère cipher on ciphertext (C) and Vigenère text key [F[i]]. |
| 2. Convert step 1 Vigenère results [V[i]] into their equivalent ASCII [W[i]]. |
| 3. Convert [W[i]] ASCII static key [K[i]] values into 8-bit binary. |
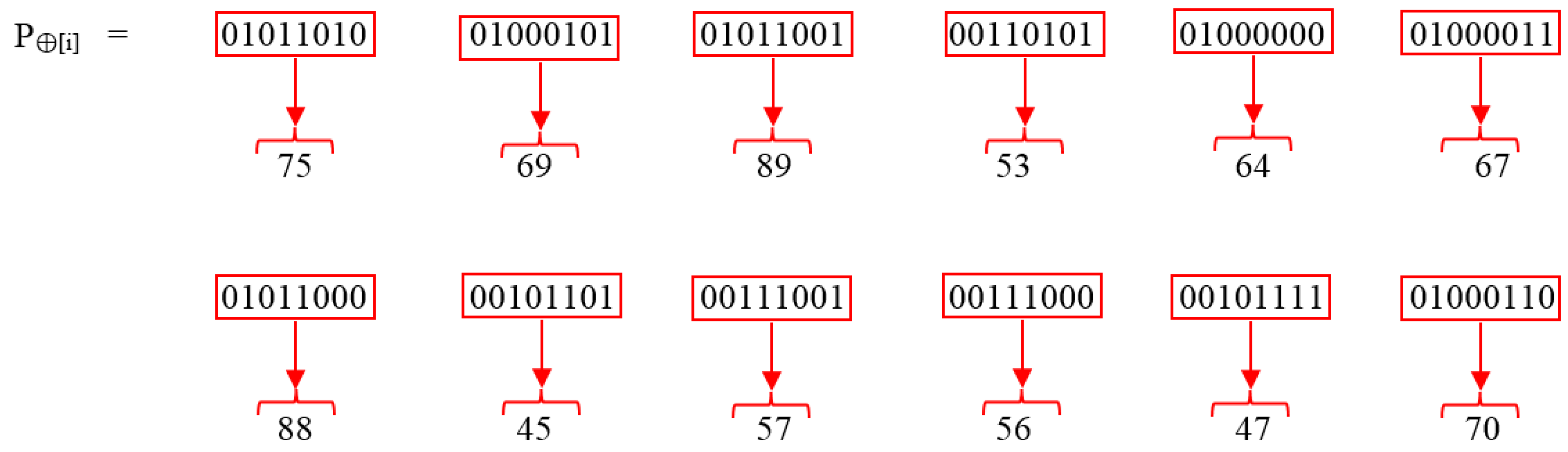
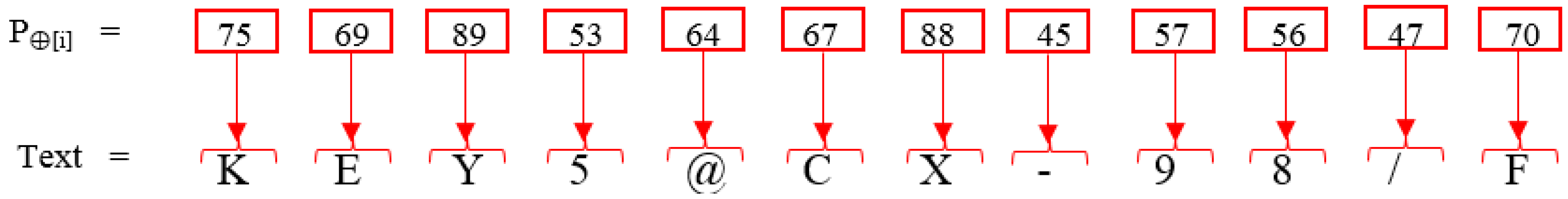
| 4. Apply P⊕[i] = [Wi] ⊕ [Ki] on step 3. |
| 5. Convert the P⊕[i] result into a decimal by making 8-bit pairs. |
| 6. Convert decimal values into equivalent ASCII. |
| 7. Obtain the plaintext. |
4. Experiment
4.1. Encryption Algorithm
δ = 3
4.2. Decryption Algorithm
4.3. Algorithm Testing
4.4. Kasiski Test Cryptanalysis Algorithm
| Algorithm 3: Kasiski Test |
| Input: Ciphertext |
| Output: Identification of Key |
| 1. Ciphertext |
| 2. From the encrypted message, determine the reusable value. |
| 3. Identify the repeating value indexes. |
| 4. Apply Kasiski key length algorithm |
| Calculate the distance between the first value and the nth value “X = Y1 − Yn” |
| Find the greatest common division (GCD) of distances. |
| 5. Verify the LENGTH_OF_KEY by using step 4. |
| 6. IF LENGTH_OF_KEY = CIPHER_TEXT then GOTO step 7 |
| ELSE GOTO step 9. |
| 7. Implement index of coincidence algorithm |
| Yc (Z) = (Favorable case / Total Possible Cases) |
| Yc (Z) = ((Fi)/N) |
| 8. Kasiski key |
| 9. Exit |
Algorithm Efficiency
5. Comparative Analysis
Novelty of Proposed Work
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Akanksha, D.; Samreen, R.; Niharika, G.S.; Shruthi, A.; Kiran, M.J.; Venkatramulu, S. A hybrid cryptosystem based on modified vigenere cipher and polybius cipher. EPRA Int. J. Res. Dev. 2022, 7, 2455–7838. [Google Scholar]
- Cheon, J.H.; Kim, M.; Kim, K.; Lee, J.Y.; Kang, S. Improved Impossible Differential Cryptanalysis of Rijndael and Crypton. In Proceedings of the Information Security and Cryptology—ICISC 2001: 4th International Conference, Seoul, Korea, 6–7 December 2001; Springer: Heidelberg/Berlin, Germany, 2002; pp. 39–49. [Google Scholar]
- Amrita, K.; Gupta, N.; Mishra, R. An Overview of Cryptanalysis on AES. Int. J. Adv. Res. Sci. Eng. 2018, 2014, 368–649. [Google Scholar]
- Nadeem, M.; Arshad, A.; Riaz, S.; Band, S.S.; Mosavi, A. Intercept the Cloud Network from Brute Force and DDoS Attacks via Intrusion Detection and Prevention System. IEEE Access 2021, 9, 152300–152309. [Google Scholar] [CrossRef]
- Kak, A. AES: The Advanced Encryption Standard; Engineering Purdue University: West Lafayette, IN, USA, 2021; pp. 1–92. [Google Scholar]
- Budhwani, T.; Tejaswini, P.; Chowdhury, A.; Bolli Durga, B.; Uddin, F.; Kurapati, C. An Analysis of Cloud Security. Int. Res. J. Eng. Technol. 2022, 9, 2. [Google Scholar] [CrossRef]
- Munoz, P.S.; Tran, N.; Craig, B.; Dezfouli, B.; Liu, Y. Analyzing the Resource Utilization of AES Encryption on IoT Devices. In Proceedings of the 2018 Asia-Pacific Signal and Information Processing Association Annual Summit and Conference, Asia-Pacific, Honolulu, HI, USA, 12–15 November 2018; pp. 1–8. [Google Scholar]
- Kumari, S. A research Paper on Cryptography Encryption and Compression Techniques. Int. J. Eng. Comput. Sci. 2017, 6, 20915–20919. [Google Scholar] [CrossRef]
- Qin, Z.; Liu, D.; Hua, H.; Cao, J. Privacy Preserving Load Control of Residential Microgrid via Deep Reinforcement Learning. IEEE Trans. Smart Grid 2021, 12, 4079–4089. [Google Scholar] [CrossRef]
- Sharma, N.; Prabhjot; Kaur, H. A Review of Information Security using Cryptography Technique. Int. J. Adv. Res. Comput. Sci. 2017, 8, 323–326. [Google Scholar]
- Tayal, S.; Gupta, N.; Gupta, P.; Goyal, D.; Goyal, M. A Review paper on Network Security and Cryptography. Adv. Comput. Sci. Technol. 2017, 10, 763–770. [Google Scholar]
- Hasan, M.; Ariffin, N.; Sani, N. A review of cryptographic impact in cybersecurity on smart grid: Threat, challenges and countermeasures. J. Theor. Appl. Inf. Technol. 2021, 99, 2458–2472. [Google Scholar]
- Z’aba, M.R.; Maarof, M.A. A Survey on the Cryptanalysis of the Advanced Encryption Standard; 2016 Core Sematic Scholar: Rome, Italy, 2006; pp. 97–102. [Google Scholar]
- Sun, L.; Dai, Z. Research on Framework of Security Service Cloud Computing. J. Comput. Appl. 2012, 32, 13–15. [Google Scholar]
- Heys, H.M. A Tutorial on Linear and Differential Cryptanalysis; Computer Science Department at Boston College: Philadelphia, PA, USA, 2017; pp. 1–33. [Google Scholar]
- Wang, Z.; Sun, L.; Guo, S. Real-time Task Threshold Scheduling Method for Cryptography Cloud based on Rolling Optimization. J. Comput. Appl. 2017, 37, 2780–2786. [Google Scholar]
- Carlin, S.; Curran, K. Study on cloud computing security. J. Softw. 2011, 22, 71–83. [Google Scholar]
- Wang, B.F.; Su, J.S.; Chen, L. Review of the design of data center network for cloud computing. J. Comput. Res. Dev. 2016, 53, 92085–92106. [Google Scholar]
- Trapiello, C.; Puig, V.; Rotondo, D. A zonotopic set-invariance analysis of replay attacks affecting the supervisory layer. Syst. Control Lett. 2021, 157, 105056. [Google Scholar] [CrossRef]
- Vatshayan, S.; Haidri, R.A.; Verma, J.K. Design of Hybrid Cryptography System based on Vigenère Cipher and Polybius Cipher. In Proceedings of the 2020 International Conference on Computational Performance Evaluation (ComPE), Shillong, India, 2–4 July 2020; pp. 848–852. [Google Scholar] [CrossRef]
- Triandi, B.; Ekadiansyah, E.; Puspasari, R.; Iwan, L.T.; Rahmad, F. Improve Security Algorithm Cryptography Vigenere Cipher Using Chaos Functions. In Proceedings of the 2018 6th International Conference on Cyber and IT Service Management (CITSM), Parapat, Indonesia, 7–9 August 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Alisawi, W.C.; Oleiwi, Z.C.; Alawsi, W.A.; Alfoudi, A.S.; Hadi, N.K. Improvement of Classical Cipher Algorithm based on a New Model of Timed-Released Encryption. Int. J. Appl. Eng. Res. 2019, 14, 3531–3536. [Google Scholar] [CrossRef]
- Tan, C.M.S.; Arada, G.P.; Abad, A.C.; Magsino, E.R. A Hybrid Encryption and Decryption Algorithm using Caesar and Vigenère Cipher. J. Phys. Conf. Ser. 2021, 1997, 012021. [Google Scholar] [CrossRef]
- Bhavana, V.; Banushree, J.; Bhumika, D.; Chaitanya, B.; Prof, R. A CRYPTO SYSTEM USING VIGENERE AND POLYBIUS CIPHER. Int. J. Eng. Appl. Sci. Technol. 2021, 6. [Google Scholar] [CrossRef]
- Nahar, K.; Chakraborty, P. A Modified Version of Vigenere Cipher using 95 × 95 Table. Int. J. Eng. Adv. Technol. 2020, 9, 1144–1148. [Google Scholar] [CrossRef]
- Agustini, S.; Rahmawati, W.M.; Kurniawan, M. Modified Vegenere Cipher to Enhance Data Security Using Monoalphabetic Cipher. Int. J. Artif. Intell. Robot. (IJAIR) 2019, 1, 25–30. [Google Scholar] [CrossRef]
- Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Dutta, A.K.; Almotairi, S. A Secure Architecture to Protect the Network from Replay Attacks during Client-to-Client Data Transmission. Appl. Sci. 2022, 12, 8143. [Google Scholar] [CrossRef]









| Symbol | Description |
|---|---|
| [xi] | Static key |
| m | Static key length |
| [Ki] | Position of static keys |
| [yi] | Plaintext |
| n | Text length |
| [Ti] | Position of text |
| δ | GCD |
| Z⊕[i] | XOR result (encrypted text) |
| E[i] | Vigenère Key |
| F[i] | ASCII values of Vigenère key |
| I[z] | ASCII values of encrypted text |
| Encrypted Text | Ƞ | Ѧ | + | Ì | ⌰ | Ʋ | n | Ȅ | ƪ | b | o | 4 |
| Vigenere Key [F[i]] | Ì | Ƹ | . | Ջ | ⟒ | Ƣ | q | ⌰ | Ȅ | e | r | 7 |
| CipherText [C] | % | ƪ | Y | + | ) | ₤ | d | # | ∅ | f | g | k |
| CipherText [C] | % | ƪ | Y | + | ) | ₤ | d | # | ∅ | f | g | k |
| Vigenere Key [F[i]] | Ì | Ƹ | . | Ջ | ⟒ | Ƣ | q | ⌰ | Ȅ | e | r | 7 |
| Vigenere Results [V[i]] | Ƞ | Ѧ | + | Ì | ⌰ | Ʋ | n | Ȅ | ƪ | b | o | 4 |
| Testing | Plaintext | Plaintext Length | Static Key | Static Key Length | Vigenère Key | Vigenère Key Length | Ciphertext |
|---|---|---|---|---|---|---|---|
| 1 | This i$ 2022 Crypt0gr@phic P@peR | 32 | N@deeM | 6 | Ԏ*dCG¬?bXWYapȣ⟟^Ջ ʡÇ)⟟’Ջ℘)%E7^î-Ì | 32 | ₤(ƪdgℑ=‘bvt_jל⟒\¥࿓~’⟒%¥Ѧ’#b5%Ø+§ |
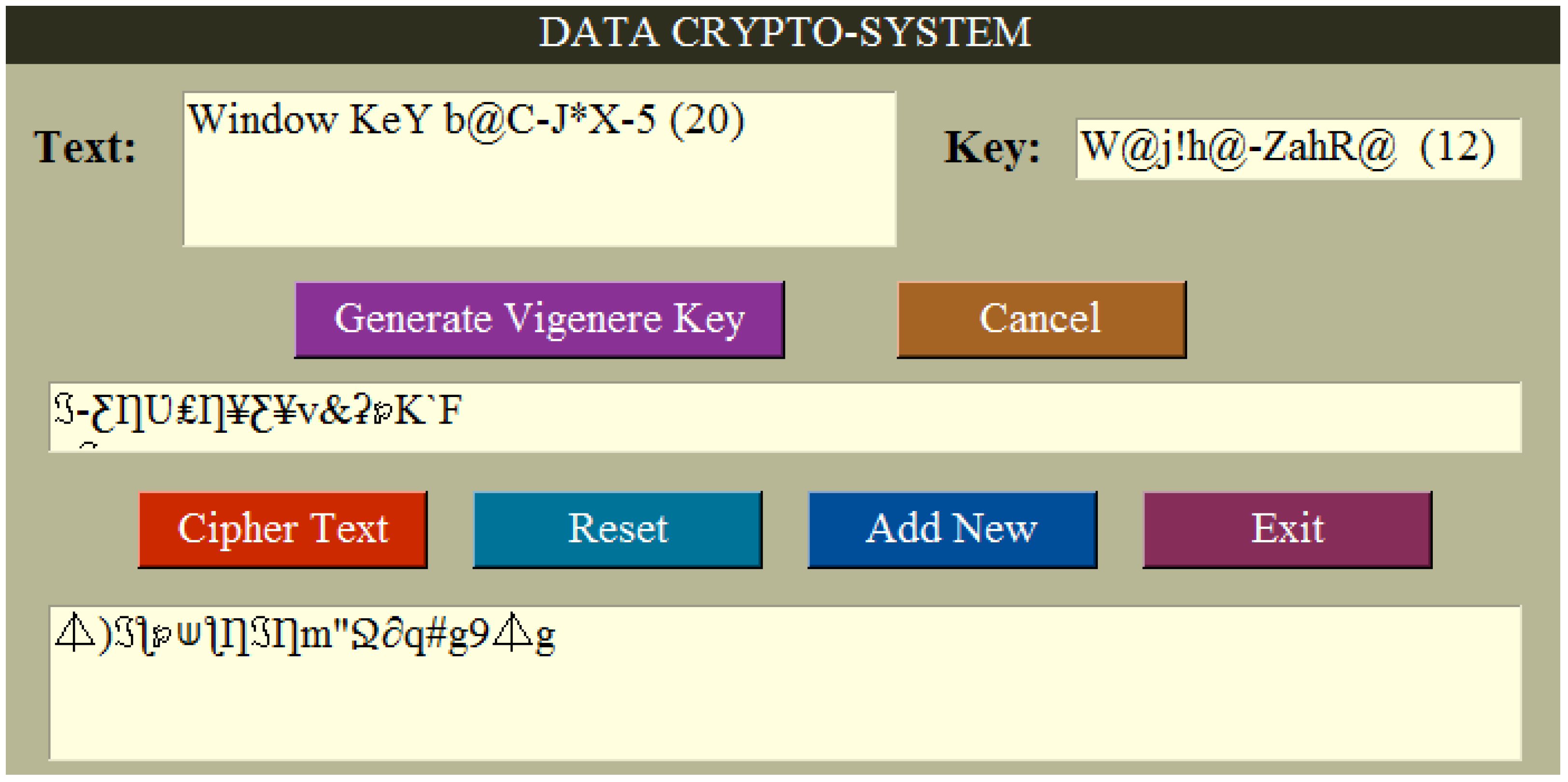
| 2 | Window KeY b@C-J*X-5 | 20 | W@j!h@-ZahR@ | 12 | ℑ-ƸȠƲ₤Ƞ¥Ƹ¥v&ʡ℘K‘F=ℑs | 20 | ⏃)ℑƪ℘⟒ƪȠℑȠm”Ջ∂q#g9⏃g |
| 3 | W!FI P@ssw0rd N@dEeM | 20 | GX5$6j | 6 | §{uo⟟<Δ-HUƸ₤%Z}fT ࿓$7 | 20 | Ȅsgt⟒:℘+zr¬⟟#c{wlՋ”5 |
| 4 | KEY5@CX-98/F | 12 | Z@r!sH654 | 9 | ÌƸ.Ջ⟒Ƣq⌰Ȅer7 | 12 | ȠѦ+Ì⌰ƲdȄƪff4 |
| 5 | MoB!LE-C0De94&T$ | 16 | G%D#S9 | 6 | ƮLƸℑ!~₤hvi©¤uѦ§Ѧ | 17 | ƻu¬¤î|⟟mooÂ⏃m∂Ȅ∂ |
| Proposed Algorithm | Kasiski Test | |||||
|---|---|---|---|---|---|---|
| Testing | Ciphertext Length | Vigenère Key Length (V) | Kasiski Key Length Algorithm Results (K) | Length Equalization (V, K) | Index of Coincidence Algorithm | Key Identify |
| 1 | 17 | 17 | 4 | V ≠ K | No | No |
| 2 | 6 | 6 | 1 | V ≠ K | No | No |
| 3 | 6 | 6 | 1 | V ≠ K | No | No |
| 4 | 6 | 6 | 3 | V ≠ K | No | No |
| Paper References | Encryption Key | Decryption Key | Key Cryptanalysis |
|---|---|---|---|
| [1] | 1 | 1 | Possible |
| [23] | 1 | 1 | Possible |
| [20] | 1 | 1 | Possible |
| [24] | 1 | 1 | Possible |
| Proposed paper | 1 | 2 | Not Possible |
| Sr# | 1 | 2 | 3 | 4 | Proposed Work |
|---|---|---|---|---|---|
| Year | 2022 | 2021 | 2020 | 2020 | 2022 |
| Reference | [1] | [23] | [20] | [24] | |
| Proposed Algorithm | Vigenère cipher, Polybius cipher | Vigenère cipher, Caesar cipher | Vigenère cipher, Polybius cipher | Vigenère cipher, Polybius cipher | Encrypted text key, Vigenère cipher |
| Novelty | Implement Polybius algorithm on Vigenère results | Identified the accuracy of hybrid algorithms by MATLAB | Implement Vigenère results on Polybius results | Web-based encryption and decryption | Two-layer security. Layer-1 proposed an encrypted text and Vigenère key. Layer-2 implements the Layer-1 results on the Vigenère cipher algorithm |
| Implement on a Predefined Table | Vigenère cipher | Vigenère cipher, ASCII table | Vigenère cipher, ASCII table | Vigenère cipher | Vigenère cipher |
| Keys for Encryption (E)/ Decryption (D) | 01 (E), 01 (D) | 01 (E), 01 (D) | 01 (E), 01 (D) | 01 (E), 02 (D) | 01 (E), 02 (D) |
| Research Gap | Developing a secure key the mechanism can increase key security compared to increasing the length of the key | Developing a key from text can enhance the algorithm efficiency compared to using the same key twice | An efficient algorithm can provide better security instead of using hybrid algorithms | Instead of merged pre-built techniques, the latest technique can provide better accuracy | Identified all problems that existed |
| Problem Solution in proposed work | Vigenère key algorithm | Vigenère key | Two-layer encryption Algorithm | Encrypted text key algorithm | Solved all existing problems |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nadeem, M.; Arshad, A.; Riaz, S.; Zahra, S.W.; Dutta, A.K.; Alruban, A.; Almutairi, B.; Almotairi, S. Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace. Appl. Sci. 2022, 12, 9736. https://doi.org/10.3390/app12199736
Nadeem M, Arshad A, Riaz S, Zahra SW, Dutta AK, Alruban A, Almutairi B, Almotairi S. Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace. Applied Sciences. 2022; 12(19):9736. https://doi.org/10.3390/app12199736
Chicago/Turabian StyleNadeem, Muhammad, Ali Arshad, Saman Riaz, Syeda Wajiha Zahra, Ashit Kumar Dutta, Abdulrahman Alruban, Badr Almutairi, and Sultan Almotairi. 2022. "Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace" Applied Sciences 12, no. 19: 9736. https://doi.org/10.3390/app12199736
APA StyleNadeem, M., Arshad, A., Riaz, S., Zahra, S. W., Dutta, A. K., Alruban, A., Almutairi, B., & Almotairi, S. (2022). Two-Layer Security Algorithms to Prevent Attacks on Data in Cyberspace. Applied Sciences, 12(19), 9736. https://doi.org/10.3390/app12199736






