Trustworthy Transaction Spreading Using Node Reliability Estimation in IoT Blockchain Networks
Abstract
:Featured Application
Abstract
1. Introduction
2. Previous Studies
3. Transaction Spreading and Consensus
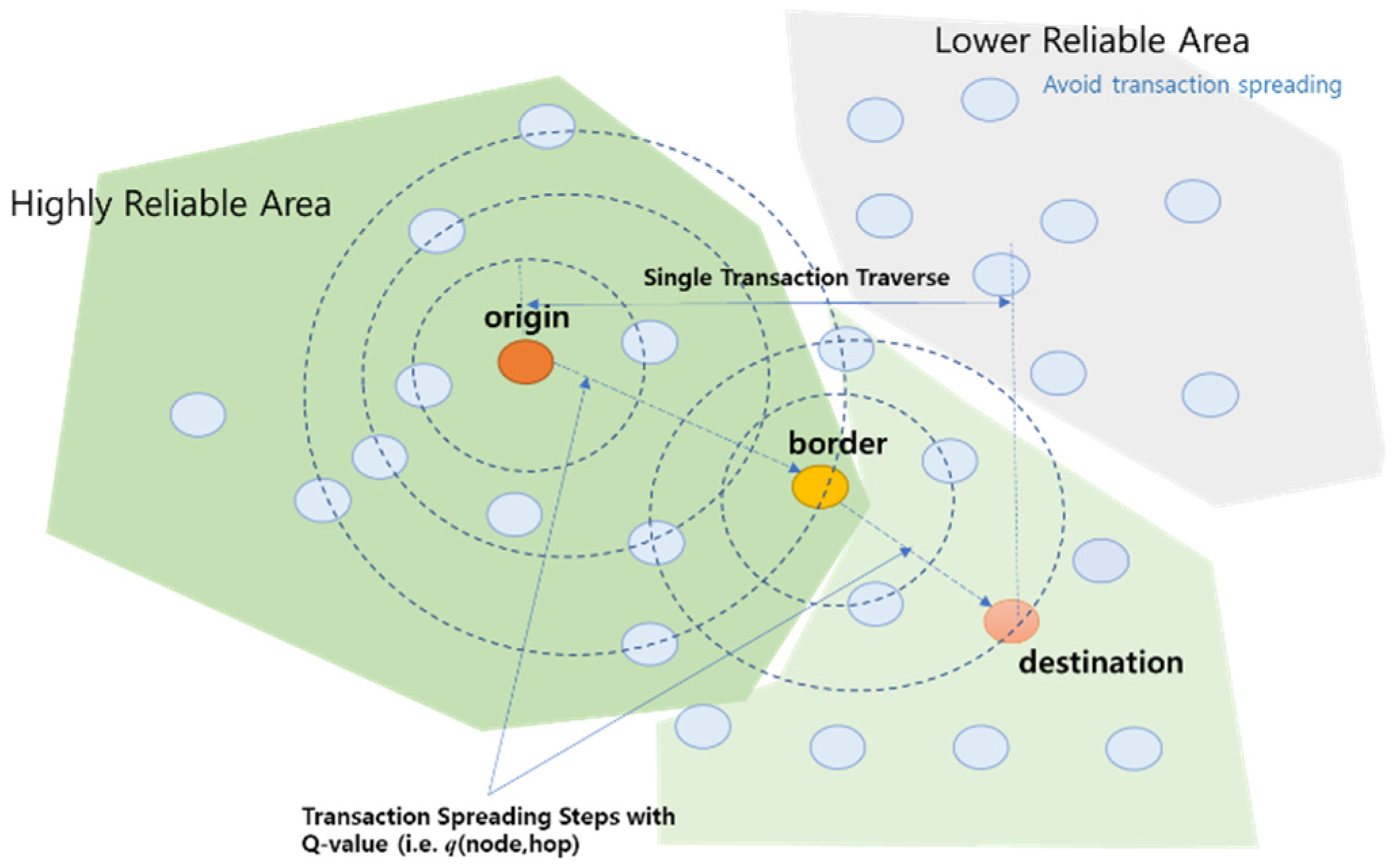
4. Trustworthy Transaction Spreading
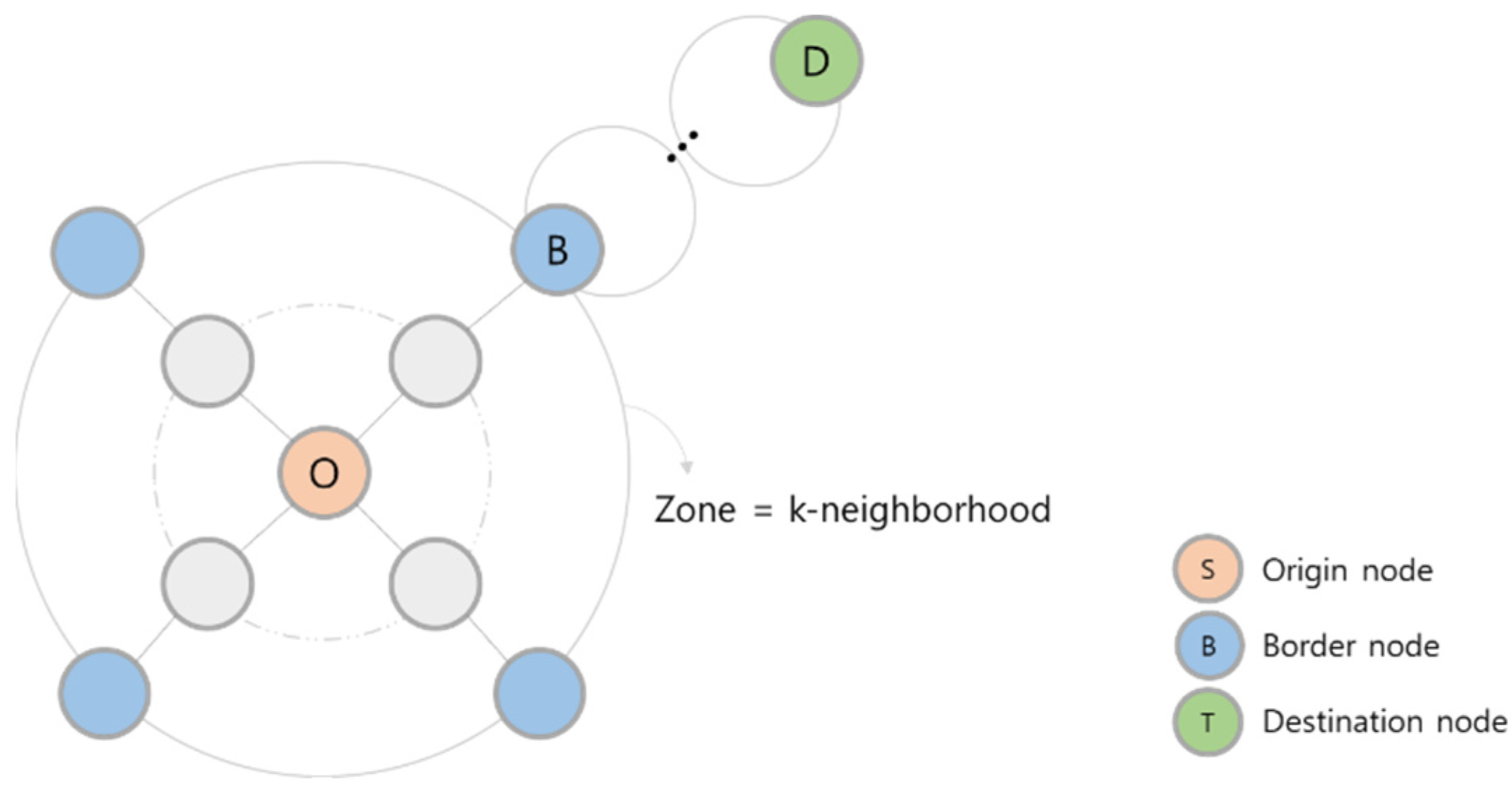
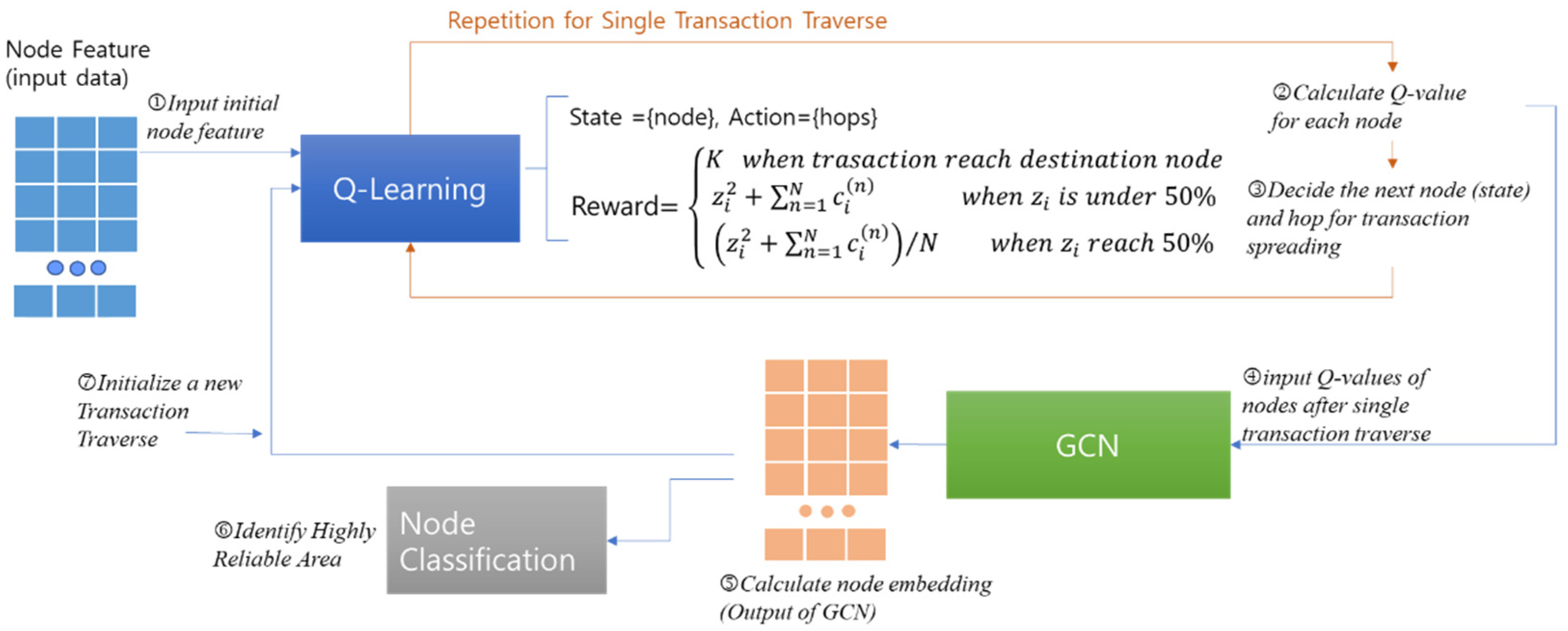
4.1. Determining the Next Hop for Transaction Traverse: Q-Learning
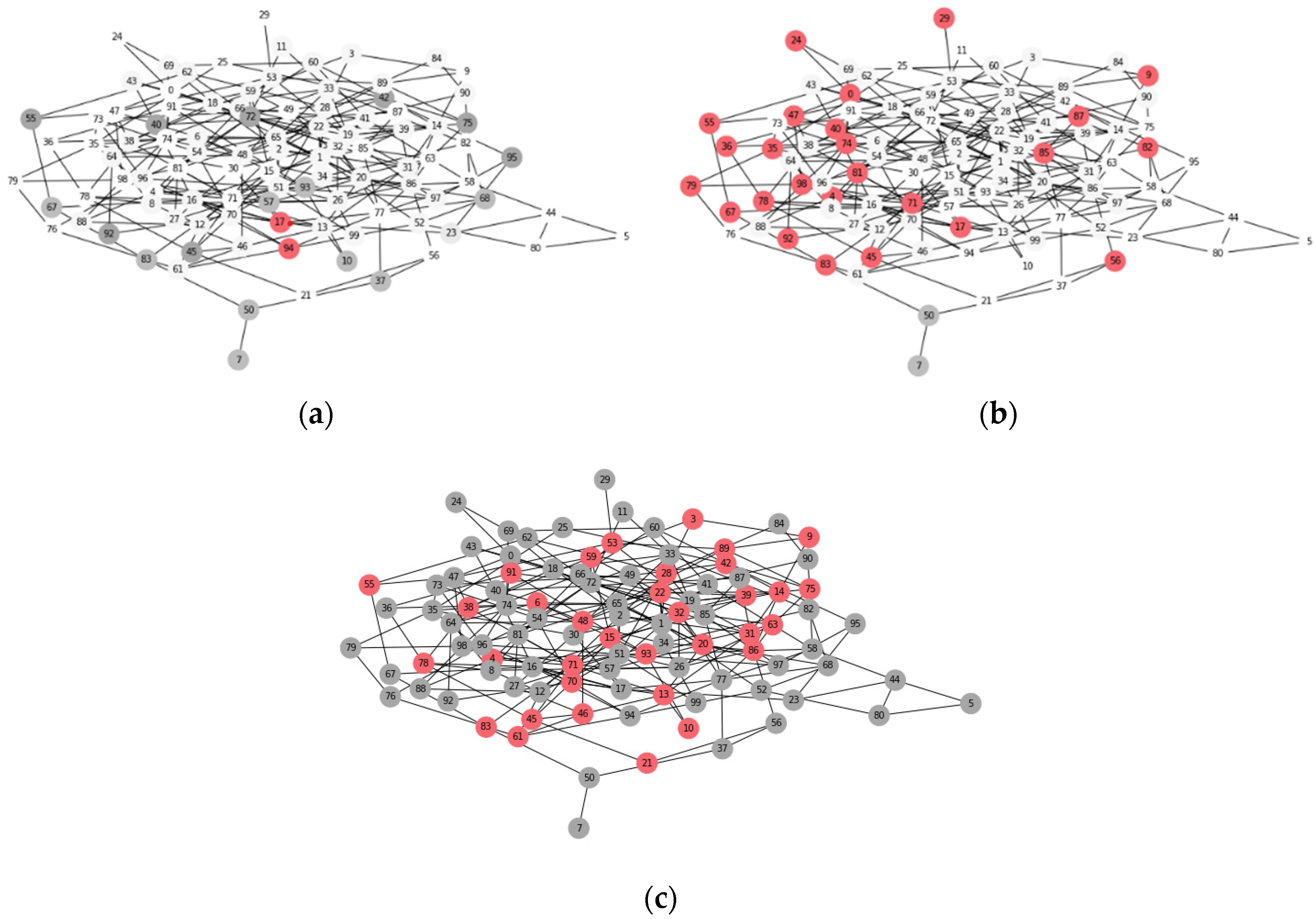
4.2. Finding Node Reliability and Reliable Area: GCN
5. Experiments
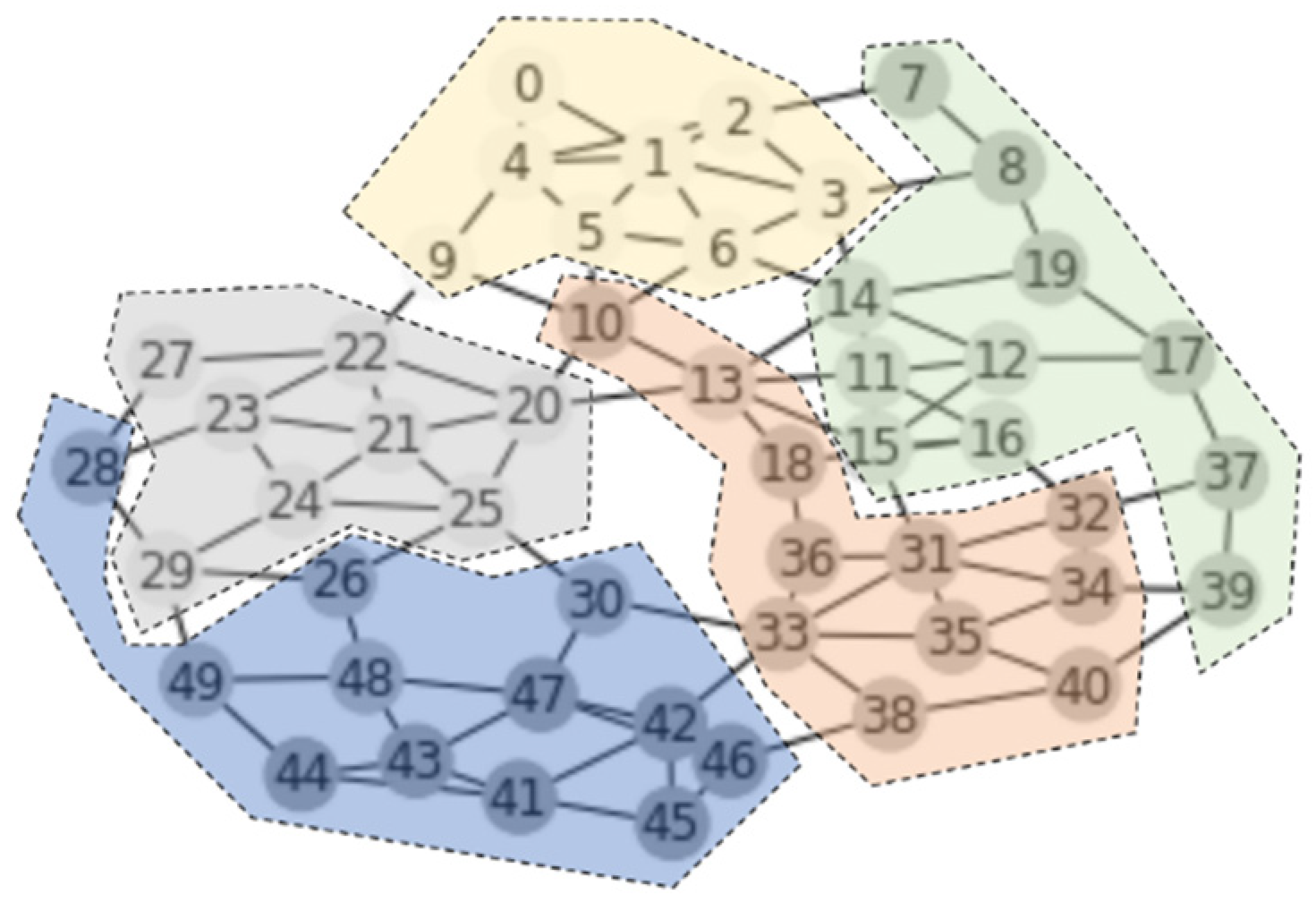
5.1. Experiment Design
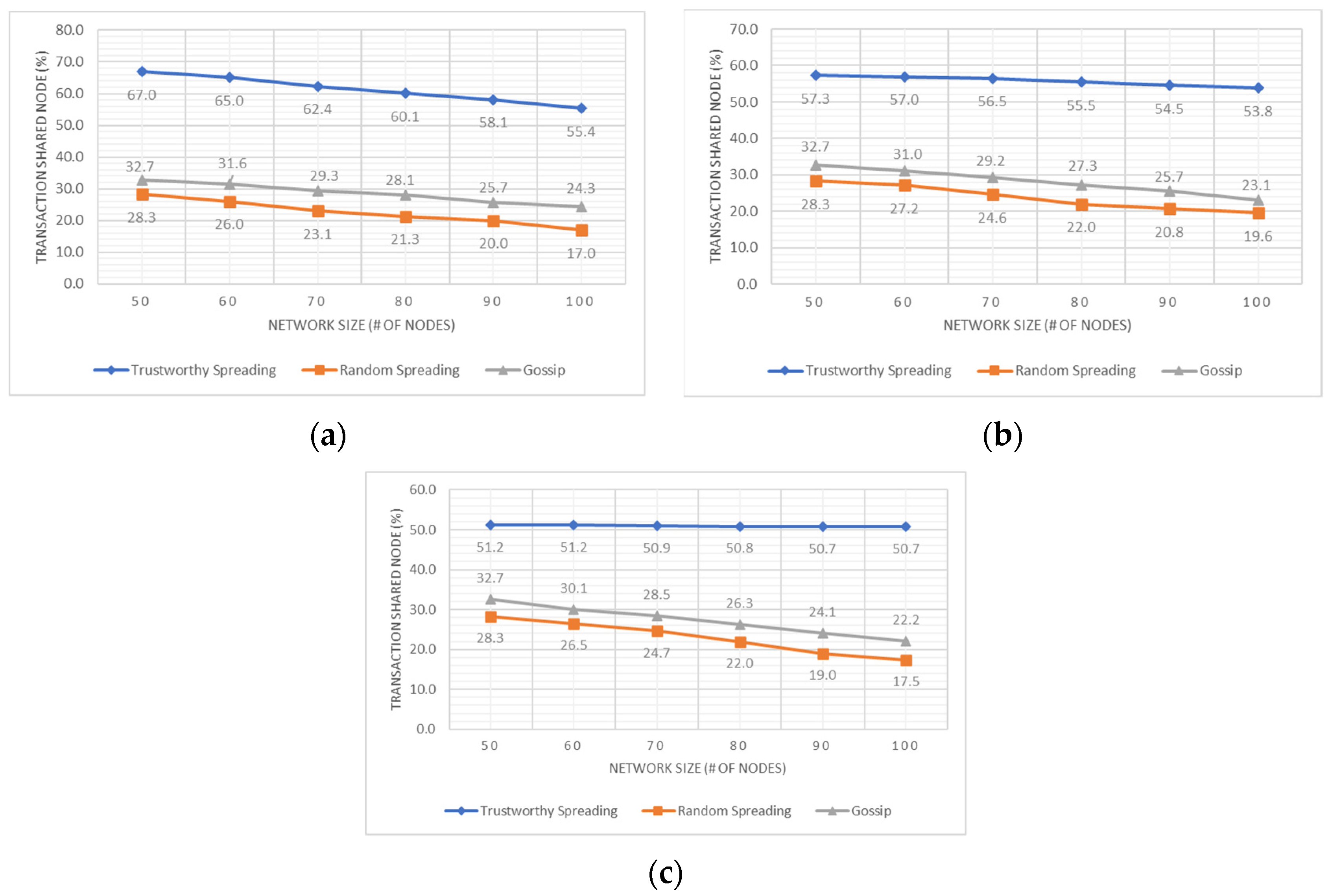
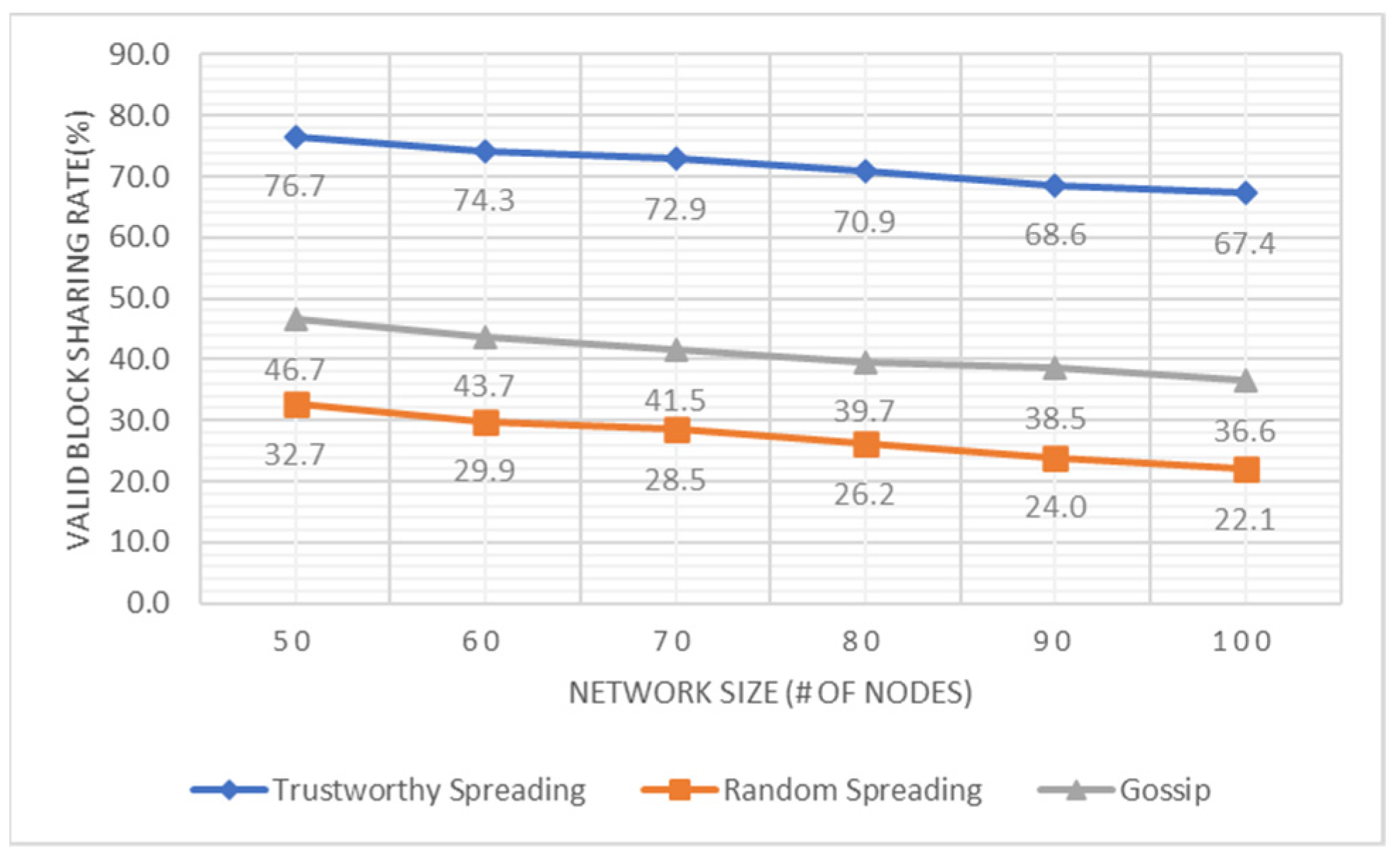
5.2. Performance Evaluations: Valid Transaction Sharing and Valid Block Sharing
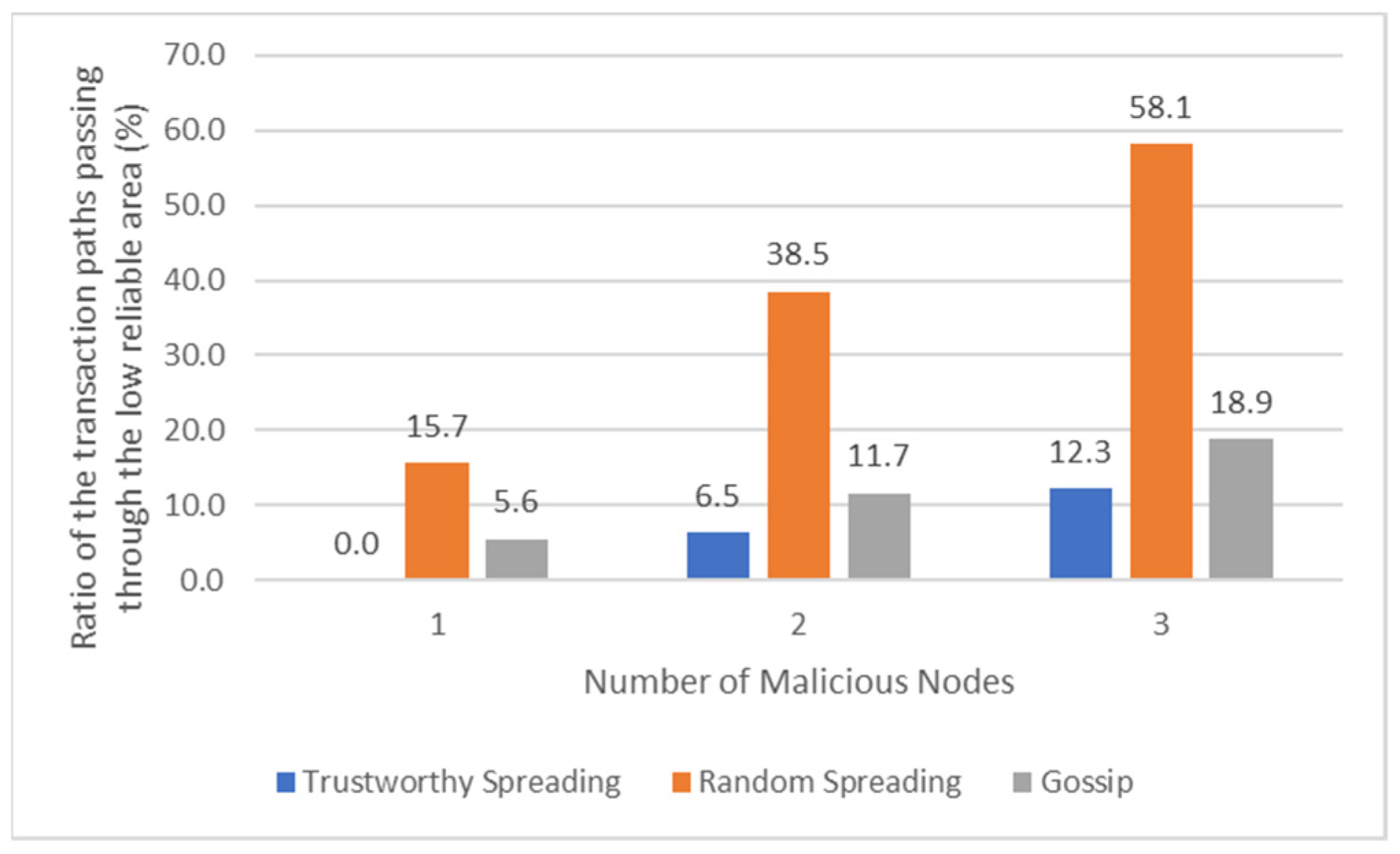
6. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lee, S.C.; Lee, J.; Hong, S.; Kim, J.H. Lightweight End-to-End Blockchain for IoT applications. KSII Trans. Internet Inf. Syst. 2020, 14, 3224–3242. [Google Scholar]
- Kim, J.H.; Lee, S.C.; Hong, S. Autonomous Operation Control of IoT Blockchain Networks. Electronics 2021, 10, 204. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetrò, A.; de Martin, J.C. Peer to Peer for Privacy and Decentralization in the Internet of Things. In Proceedings of the IEEE/ACM 39th International Conference on Software Engineering Companion, Buenos Aires, Argentina, 20–28 May 2017. [Google Scholar]
- Chen, J. Devify: Decentralized internet of things software framework for a peer-to-peer and interoperable IoT device. ACM SIGBED Rev. 2018, 15, 31–36. [Google Scholar] [CrossRef]
- Jiang, C.; Gao, L.; Duan, L.; Huang, J. Scalable Mobile Crowdsensing via Peer-to-Peer Data Sharing. IEEE Trans. Mob. Comput. 2018, 17, 898–912. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetrò, A.; de Martin, J.C. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef]
- Han, D.; Kim, H.; Jang, J. Blockchain based smart door lock system. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 18–20 October 2017; pp. 1165–1167. [Google Scholar]
- Wilkinson, S.; Boshevski, T.; Brandoff, J.; Prestwich, J.; Hall, G.; Gerbes, P.; Hutchins, P.; Pollard, C. Storj a Peer-to-Peer Cloud Storage Network. Available online: https://storj.io/storj.pdf (accessed on 10 April 2018).
- Ateniese, G.; Goodrich, M.T.; Lekakis, V.; Papamanthou, C.; Paraskevas, E.; Tamassia, R. Accountable storage. In Proceedings of the International Conference on Applied Cryptography and Network Security, Kanazawa, Japan, 10–12 July 2017; pp. 623–644. [Google Scholar]
- Gipp, B.; Meuschke, N.; Gernandt, A. Decentralized trusted timestamping using the crypto currency Bitcoin. In Proceedings of the iConference 2015, Newport Beach, CA, USA, 24–27 March 2015; pp. 1–5. [Google Scholar]
- Wörner, D.; von Bomhard, T. When your sensor earns money: Exchanging data for cash with Bitcoin. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Seattle, WA, USA, 13–17 September 2014; pp. 295–298. [Google Scholar]
- Zhang, Y.; Wen, J. An IoT electric business model based on the protocol of Bitcoin. In Proceedings of the 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; pp. 184–191. [Google Scholar]
- Wilson, D.; Ateniese, G. From pretty good to great: Enhancing PGP using Bitcoin and the blockchain. In Proceedings of the International Conference on Network and System Security, New York, NY, USA, 3–5 November 2015; pp. 368–375. [Google Scholar]
- Kshetri, N. Can blockchain strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Tanas, C.; Delgado-Segura, S.; Herrera-Joancomartí, J. An integrated reward and reputation mechanism for MCS preserving users’ privacy. In Proceedings of the 10th International Workshop on Quantitative Aspects in Security Assurance; Springer: New York, NY, USA, 2016; Volume 9481, pp. 83–99. [Google Scholar]
- Siddiqi, M.; All, S.T.; Sivaraman, V. Secure lightweight context-driven data logging for bodyworn sensing devices. In Proceedings of the 5th International Symposium on Digital Forensic and Security (ISDFS), Tirgu Mures, Romania, 26–28 April 2017; pp. 1–6. [Google Scholar]
- Kshetri, N. Blockchain’s roles in strengthening cybersecurity and protecting privacy. Telecommun. Policy 2017, 41, 1027–1038. [Google Scholar] [CrossRef]
- Wright, A.; De Filippi, P. Decentralized Blockchain Technology and the Rise of Lex Cryptographia. 2015. Available online: https://ssrn.com/abstract=2580664 (accessed on 10 April 2018).
- Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology. In Proceedings of the 13th International Conference on Service Systems and Service Management (ICSSSM), Kunming, China, 24–26 June 2016. [Google Scholar]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 19th International Conference on Advanced Communication Technology (ICACT), Bongpyeong, Korea, 19–22 February 2017; pp. 464–467. [Google Scholar]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Ahmed, B.S.; Bures, M.; Frajtak, K.; Cerny, T. Aspects of quality in Internet of Things (IoT) solutions: A systematic mapping study. IEEE Access 2019, 7, 13758–13780. [Google Scholar] [CrossRef]
- Park, J.; Kim, K. TM-Coin: Trustworthy management of TCB measurements in IoT. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 654–659. [Google Scholar]
- Li, C.; Zhang, L.-J. A blockchain based new secure multi-layer network model for Internet of Things. In Proceedings of the IEEE International Congress on Internet of Things (ICIOT), Honolulu, HI, USA, 25–30 June 2017; pp. 33–41. [Google Scholar]
- Samaniego, M.; Deters, R. Blockchain as a service for IoT. In Proceedings of the IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016; pp. 433–436. [Google Scholar]
- Corallo, M. Compact Blocks on the Wire as a Way to Save Bandwidth for Nodes on the P2P Network. Available online: https://github.com/bitcoin/bips/blob/master/bip-0152.mediawiki (accessed on 24 August 2022).
- Ozisik, A.P.; Andersen, G.; Bissias, G.; Houmansadr, A.; Levine, B. Graphene: A New Protocol for Block Propagation Using Set Reconciliation. In Data Privacy Management, Cryptocurrencies and Blockchain Technology; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Dagur. Xthin vs. Compact Blocks. Available online: https://speakerdeck.com/dagurval/xthin-vs-compact-blocks (accessed on 24 August 2022).
- Basu, S.; Eyal, I.; Sirer, E.G. A Fast New Bitcoin Backbone Relay Network. Available online: https://www.falcon-net.org/ (accessed on 24 August 2022).
- Public highly-optimized FIBRE (Fast Internet Bitcoin Relay Engine) Network. Available online: http://bitcoinfibre.org/public-network.html (accessed on 24 August 2022).
- Panikkar, S.; Nair, S.; Brody, P.; Pureswaran, V. ADEPT: An IoT Practitioner Perspective; IBM Institute for Business Value: New York, NY, USA, 2015; pp. 1–18. [Google Scholar]
- Yaffe, L. Lightweight Contracts: The Ardor Answer to Smart Contracts. Available online: https://medium.com/coinmonks/lightweight-contracts-b738b6e29377 (accessed on 24 August 2022).
- IOST. Internet of Services Technical White Paper. Available online: https://github.com/iost-official/Documents/blob/master/Technical–White–Paper/EN/Tech–white–paper–EN.md#consensus-mechanism (accessed on 7 February 2021).
- Yang, H.; Choi, D.S. A Study on the Application of Block Chain to Ensure Data Integrity in MANET Environment. J. Converg. Secur. 2018, 18, 53–58. (In Korean) [Google Scholar]
- Velas. Velas Technologies: AIDPOS. Medium.com. Available online: https://velasblockchain.medium.com/velas-technologies-aidpos-70d0244467db (accessed on 12 May 2021).
- Kwon, H.; Shin, J.; Lee, B.; Choi, J.; Nam, S.; Lim, S. Technical Trends on Mobile Ad Hoc Networks. Electron. Telecommun. Trends 2003, 18, 11–14. (In Korean) [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the 3rd Symposium on Operating Systems Design and Implementation, New Orleans, LA, USA, 22–25 February 1999; pp. 1–14. [Google Scholar]
- Ongaro, D.; Ousterhout, J. In search of an understandable consensus algorithm. In Proceedings of the USENIX Annual Technical Conference, Philadelphia, PA, USA, 19–20 June 2014; pp. 305–320. [Google Scholar]
- Sawtooth: About Dynamic Consensus. Available online: https://sawtooth.hyperledger.org/docs/1.2/sysadmin_guide/about_dynamic_consensus.html (accessed on 24 August 2022).
- Kipf, T.N.; Welling, M. Semi-supervised classification with graph convolutional networks. In Proceedings of the International Conference on Learning Representations (ICLR), Toulon, France, 24–26 April 2017. [Google Scholar]
- IPFS Whitepaper. Concepts. Available online: https://docs.ipfs.io/concepts/ (accessed on 28 November 2021).
- KBLOCK. IPFS (Inter Planetary File System). Available online: https://steemit.com/kr/@kblock/8-ipfs-interplanetary-file-system-1-http-web-ipfs-web (accessed on 11 November 2021).
- Linux Foundation, Hyperledger Sawtooth Project. Available online: https://www.hyperledger.org/use/sawtooth (accessed on 24 August 2022).
- Boettiger, C. An introduction to Docker for reproducible research. ACM SIGOPS Oper. Syst. Rev. 2015, 49, 71–79. [Google Scholar] [CrossRef]
- Bernstein, D. Containers and cloud: From lxc to docker to kubernetes. IEEE Cloud Comput. 2014, 1, 81–84. [Google Scholar] [CrossRef]
- Heilman, E.; Kendler, A.; Zohar, A.; Goldberg, S. Eclipse attacks on bitcoin’s peer-to-peer network. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 12–14 August 2015; pp. 129–144. [Google Scholar]
- Gomez, K.; Riggio, R.; Rasheed, T.; Miorandi, D.; Chlamtac, I.; Granelli, F. Analysing the energy consumption behavior of WiFi networks. In Proceedings of the IEEE Online Conference on Green Communications, Piscataway, NJ, USA, 26–29 September 2011. [Google Scholar]


| Action | 0 | 1 | 2 | 3 | Action | 0 | 1 | 2 | 3 | |||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| State | State | |||||||||||
| 3 | 28 | 0 | −383 | −398 | 23 | 82 | 61 | 151 | 0 | |||
| 4 | 39 | 0 | −146 | 0 | 35 | 224 | 237 | 321 | 91 | |||
| 9 | 27 | 0 | 0 | −124 | 76 | 64 | 62 | 59 | 71 | |||
| 31 | 23 | 54 | −376 | 0 | 79 | 30 | 37 | 19 | 8 | |||
| (a) Lower reliable node set | (b) Highly reliable node set | |||||||||||
| Q Table | Node Embedding (After Applying GCN) | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Action | 0 | 1 | 2 | 3 | ID | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | ||
| State | |||||||||||||||
| 0 | 206 | −107 | −74 | −130 | 0 | −17.5 | −142.9 | 93.2 | −24.8 | −103.2 | 115.8 | 104 | −84.8 | ||
| 1 | 45 | 0 | 0 | 0 | 1 | 52.5 | −10.7 | 39.7 | −18.6 | 19.4 | −129 | 24 | 22.1 | ||
| 2 | 74 | 0 | 0 | −90 | 2 | 61.4 | 19.7 | 5.1 | 18 | −13.4 | −135.7 | −9.3 | −26.7 | ||
| 3 | 28 | 0 | −384 | −398 | 3 | 43.6 | 199.2 | 16.8 | 29.8 | −110 | −275.5 | −0.3 | −81.7 | ||
| 4 | 39 | 0 | −146 | 0 | 4 | 69.3 | −33.7 | 101.1 | −72.8 | 116.8 | −194.4 | 39.1 | 68.1 | ||
| … | … | … | … | … | … | … | … | … | … | … | … | … | … | ||
| 95 | 31 | 31 | 31 | 20 | 95 | −29.8 | 16.5 | −22 | 34.9 | −49.1 | −11.3 | 39.3 | −0.3 | ||
| 96 | 28 | 20 | 29 | 30 | 96 | 32 | −23.6 | 28.8 | −15.5 | 6.1 | −59 | 22.9 | 28.5 | ||
| 97 | 31 | 24 | 24 | 28 | 97 | 0.9 | 2.4 | 17.6 | −6 | 23.4 | −76.4 | 34.8 | 27.7 | ||
| 98 | 28 | 20 | 4 | 18 | 98 | 24.2 | −133.8 | 100.5 | −31.2 | −99.7 | 63.1 | 110.2 | −22.1 | ||
| 99 | 34 | 38 | 29 | 28 | 99 | 9.4 | −38.7 | 57 | −46.8 | 17.5 | −87.7 | 69.3 | 104.8 | ||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, J.; Kim, J.-H. Trustworthy Transaction Spreading Using Node Reliability Estimation in IoT Blockchain Networks. Appl. Sci. 2022, 12, 8737. https://doi.org/10.3390/app12178737
Kim J, Kim J-H. Trustworthy Transaction Spreading Using Node Reliability Estimation in IoT Blockchain Networks. Applied Sciences. 2022; 12(17):8737. https://doi.org/10.3390/app12178737
Chicago/Turabian StyleKim, Juyeon, and Jae-Hoon Kim. 2022. "Trustworthy Transaction Spreading Using Node Reliability Estimation in IoT Blockchain Networks" Applied Sciences 12, no. 17: 8737. https://doi.org/10.3390/app12178737
APA StyleKim, J., & Kim, J.-H. (2022). Trustworthy Transaction Spreading Using Node Reliability Estimation in IoT Blockchain Networks. Applied Sciences, 12(17), 8737. https://doi.org/10.3390/app12178737






