A Survey of CNN-Based Network Intrusion Detection
Abstract
:1. Introduction
2. Research Method
- How can the applied CNN-based IDS be categorized into multiple subcategories?
- How have CNNs been successfully applied to feature selection or feature extraction?
- What kinds of structures/networks/architectures have been applied to CNN methods?
- What methodologies have been used for classification and feature extraction?
- What ML/DL methods have been combined with CNN to create hybrid CNNs?
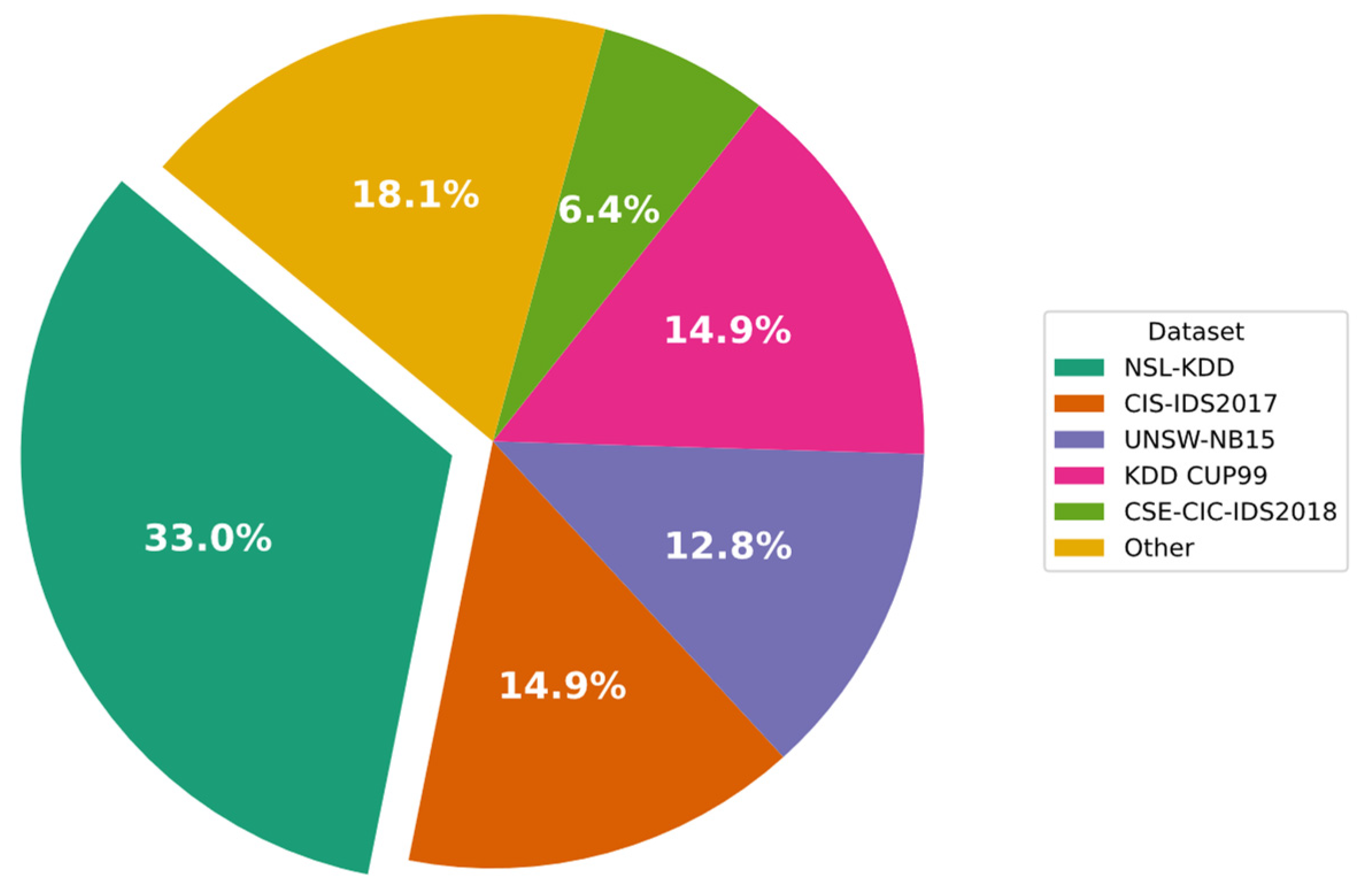
- What datasets are employed by IDS schemes?
- How can the CNN-based IDS be verified, and what evaluation metrics have been employed in IDS schemes?
- What are the current trends and accuracy results?
- What are the advantages and disadvantages of the CNN-based IDS approach?
- Is the paper focused on intrusion detection?
- Does the paper have any contribution to the CNN-based IDS context?
- Was a complete set of experiments applied to confirm the suggested method?
3. Background of Study
3.1. Deep Learning
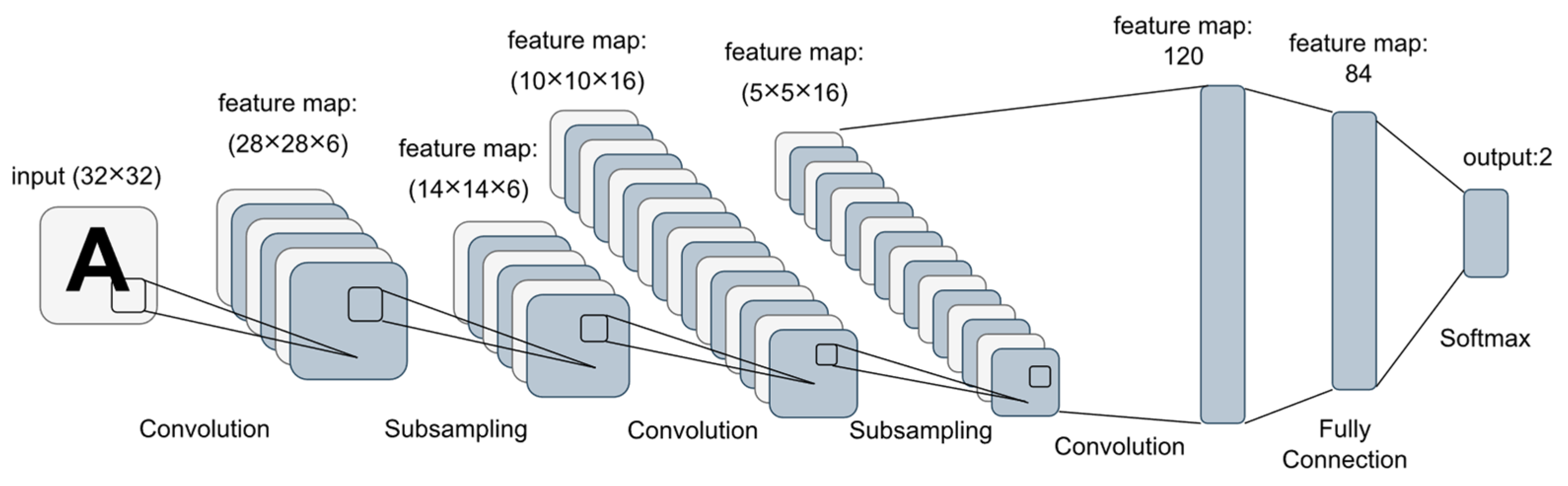
3.2. Convolutional Neural Network
3.2.1. Convolutional Layers
3.2.2. Pooling Layers
3.2.3. Fully Connected Layers
3.3. Recurrent Neural Networks
3.4. IDS Datasets
3.4.1. KDD Cup99
3.4.2. NSL-KDD
3.4.3. UNSW-NB15
3.4.4. CIC-IDS2017
3.4.5. CSE-CIC-DS2018
4. Performance Metrics
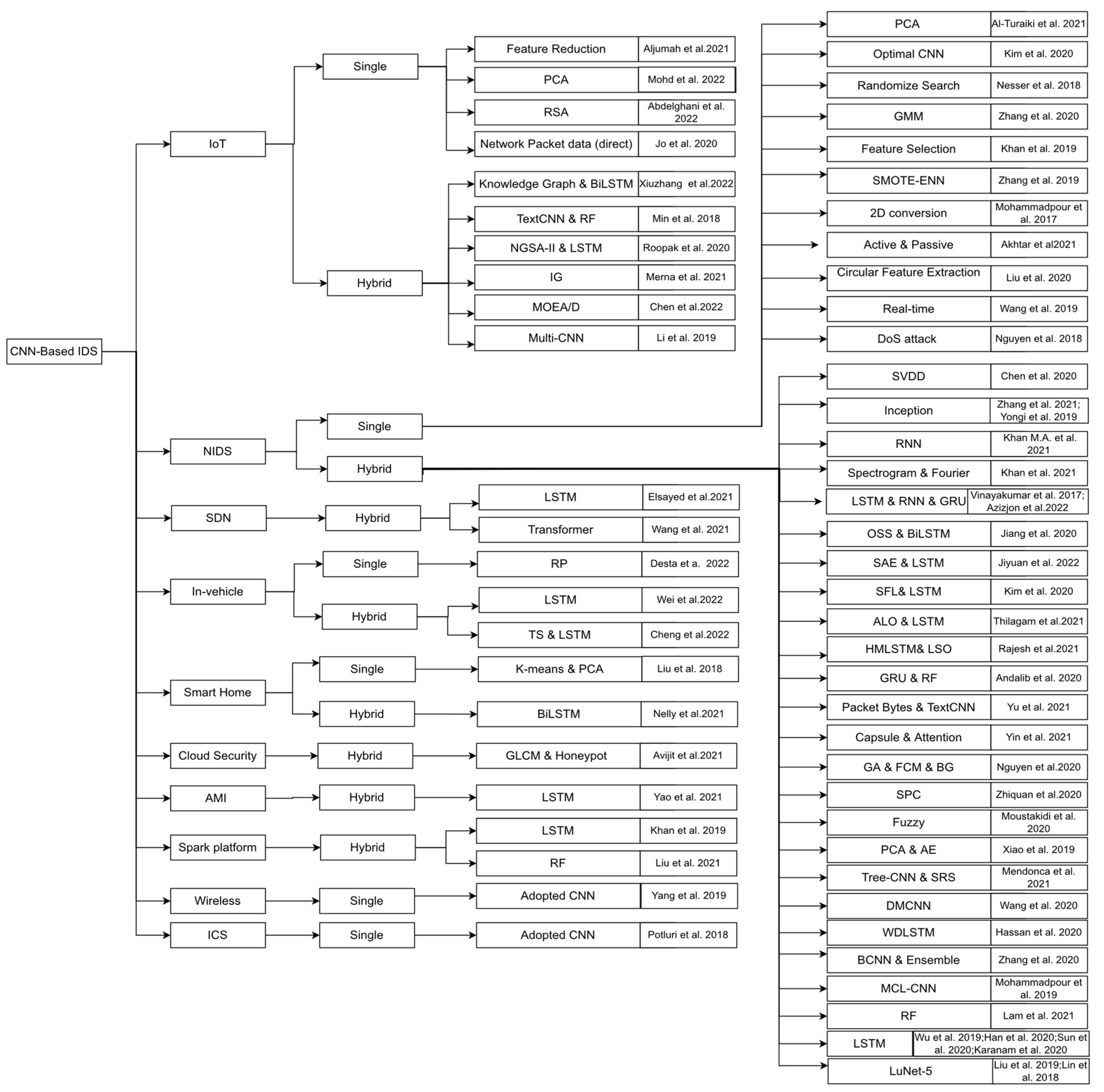
5. CNN-Based IDS Approaches
5.1. Single CNN-Based Schemes
5.2. Hybrid CNN and RNN Schemes
5.3. Hybrid CNN and Deep Learning Schemes
5.4. Hybrid CNN and Other Machine Learning Method Schemes
6. Analytical Investigation
- 10.
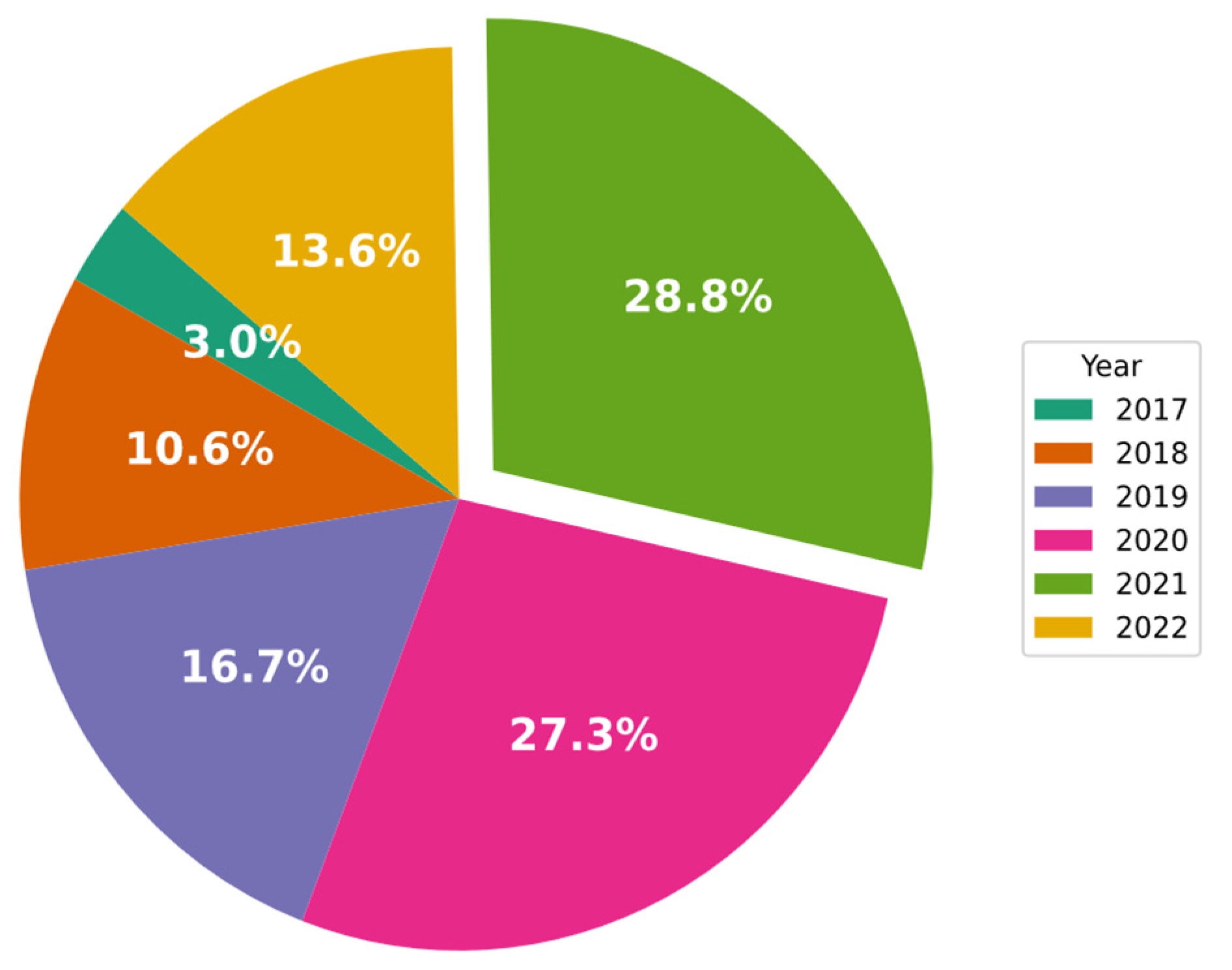
- The annual percentage of CNN-IDS papers published.
- 11.
- The percentage of IDS approaches that have employed 1D and 2D input as the input dimension of the CNN.
- 12.
- The percentage of IDS solutions employed in various intrusion detection datasets to assess performance.
- 13.
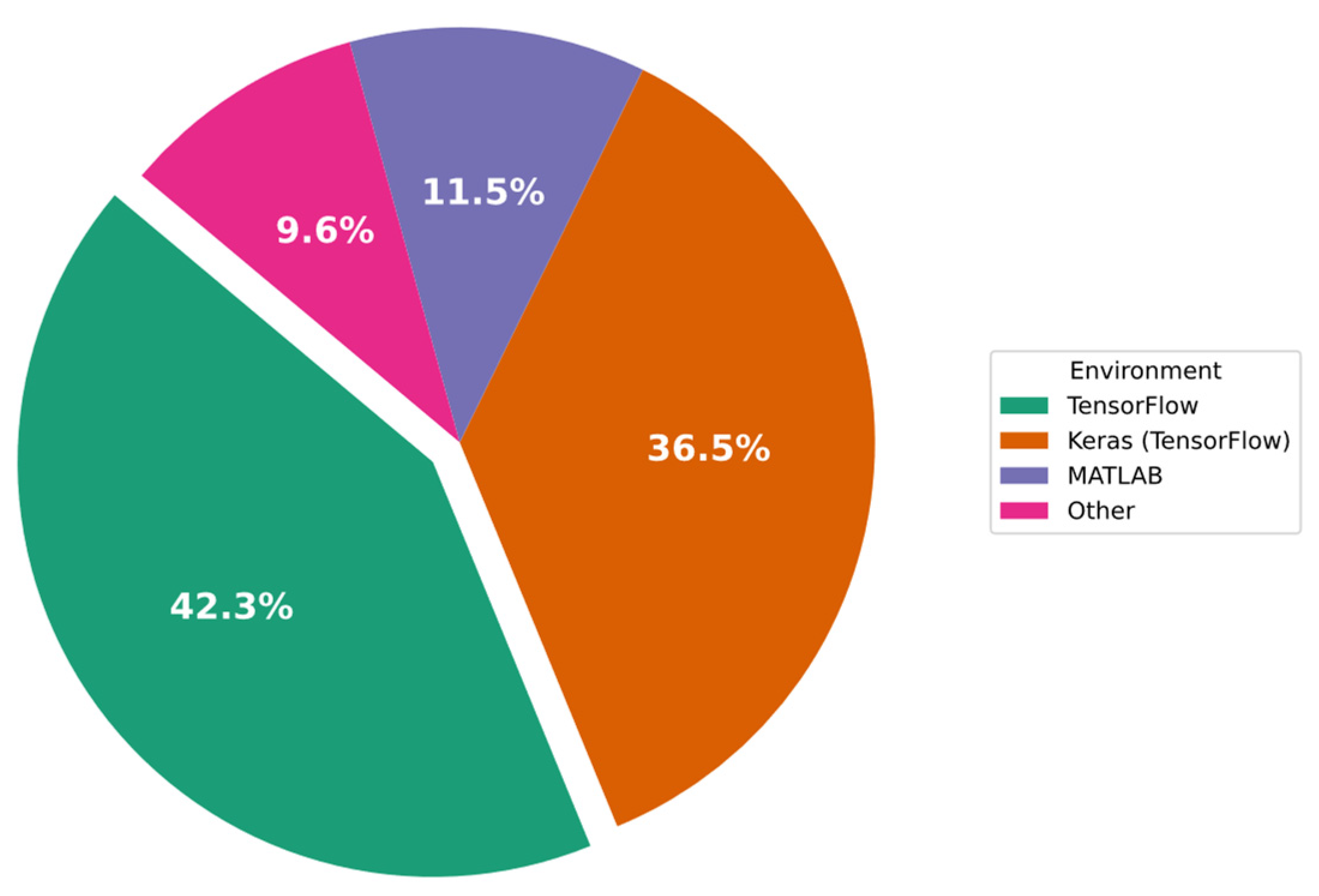
- The percentage of the use of implementation frameworks that have been trialed for IDS schemes.
- 14.
- The number of convolutional layers added in CNN-based models, which indicates the depth of the models.
- 15.
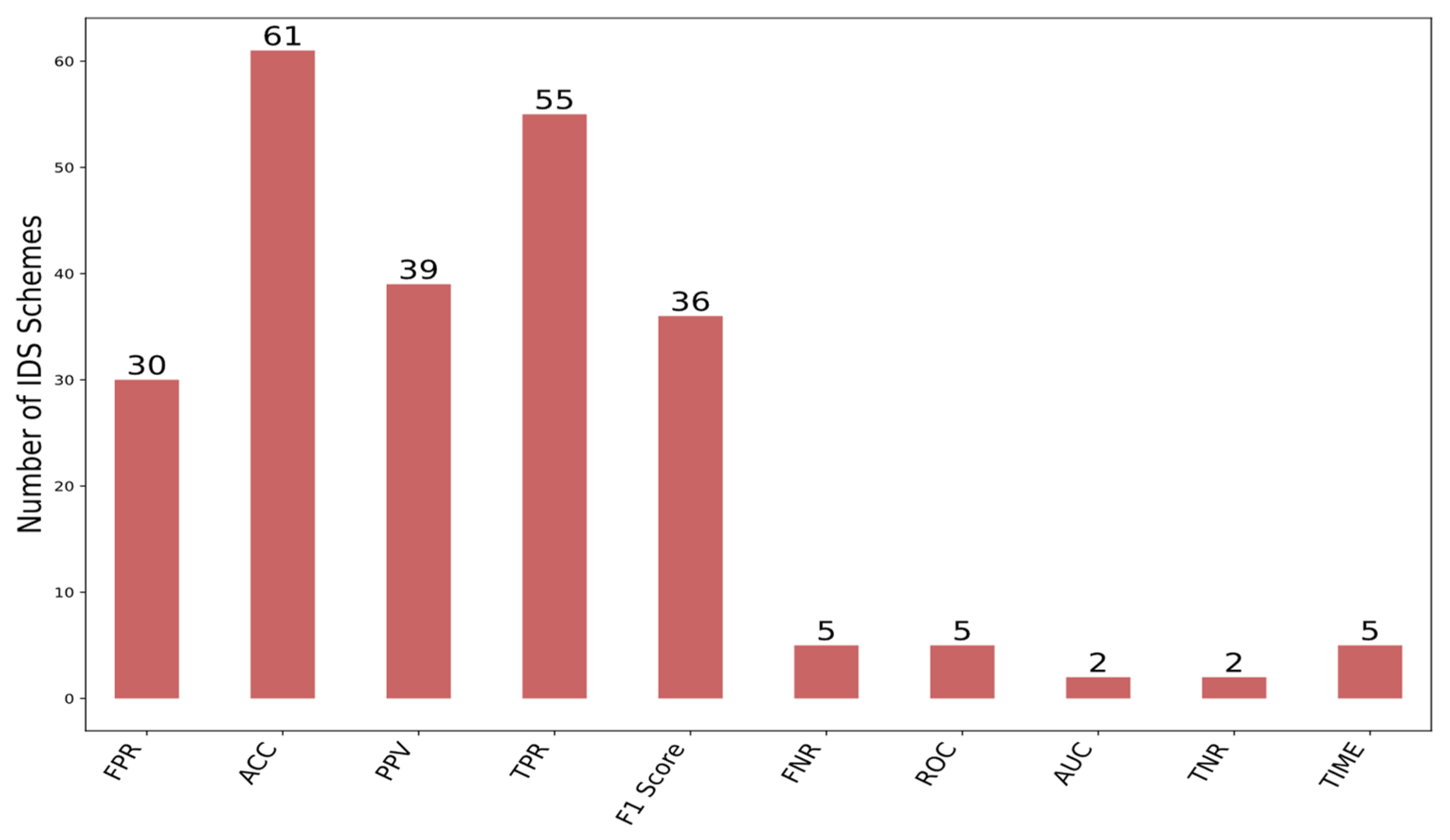
- The percentage of each evaluation metric used to test the IDS schemes.
- 16.
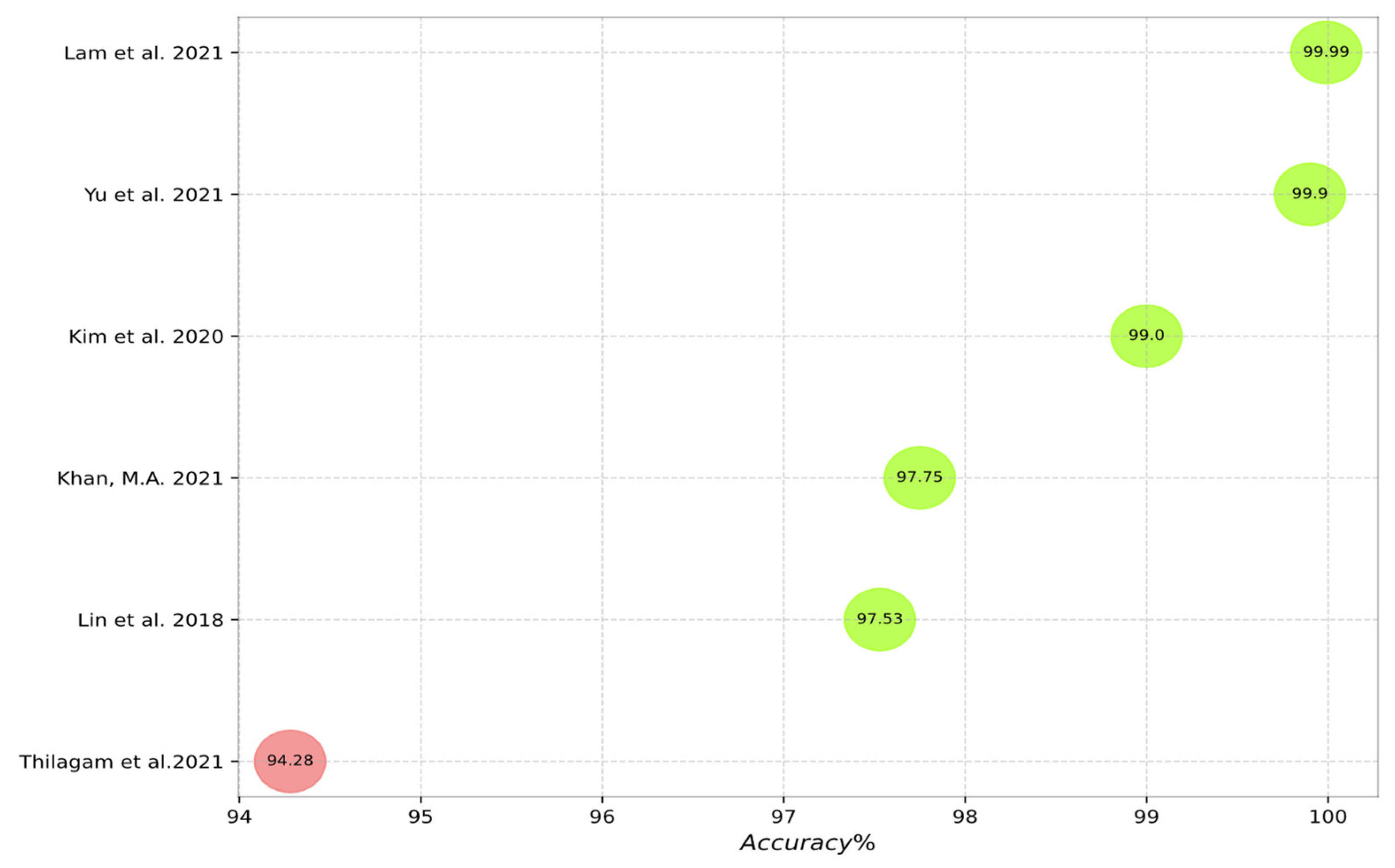
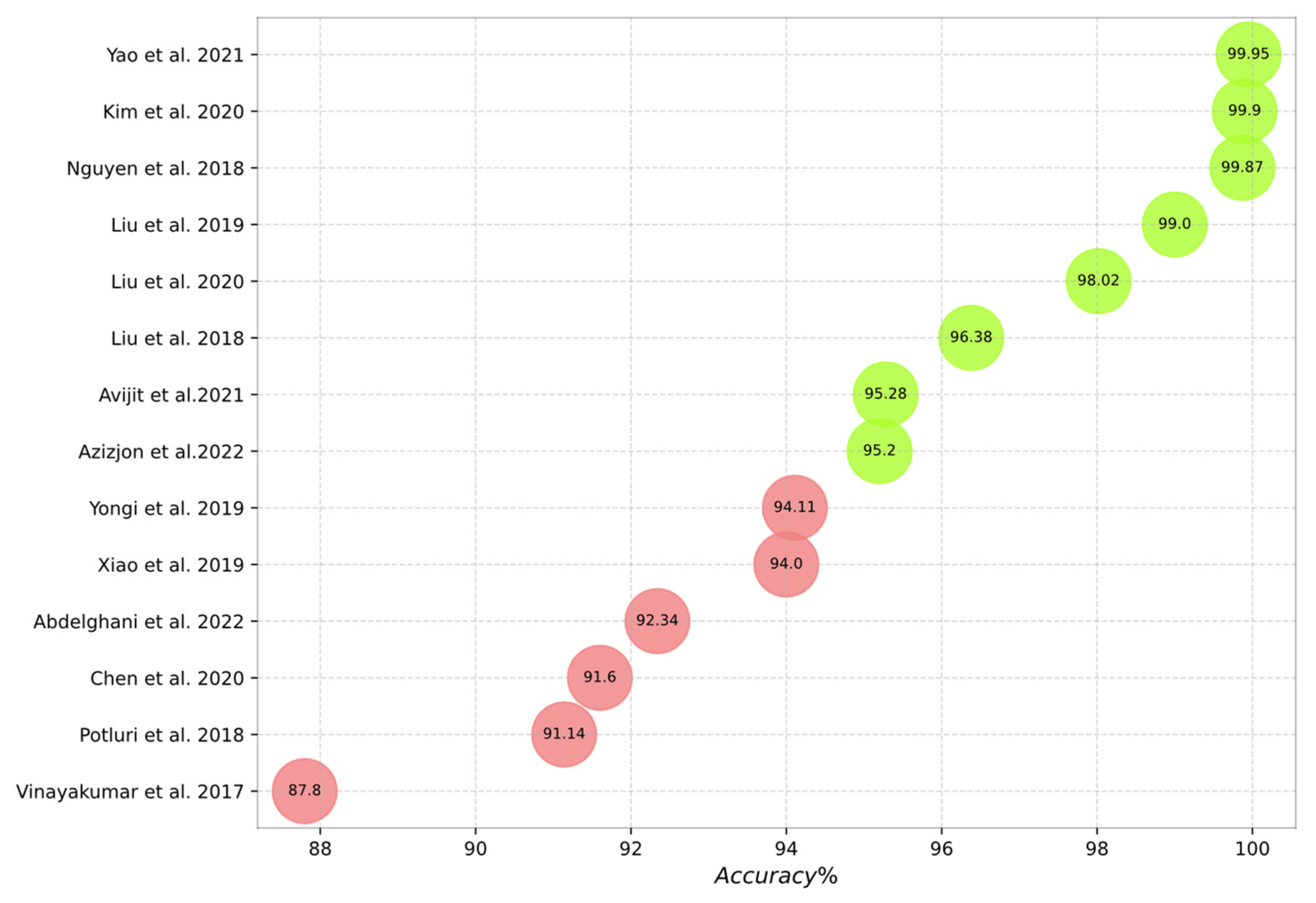
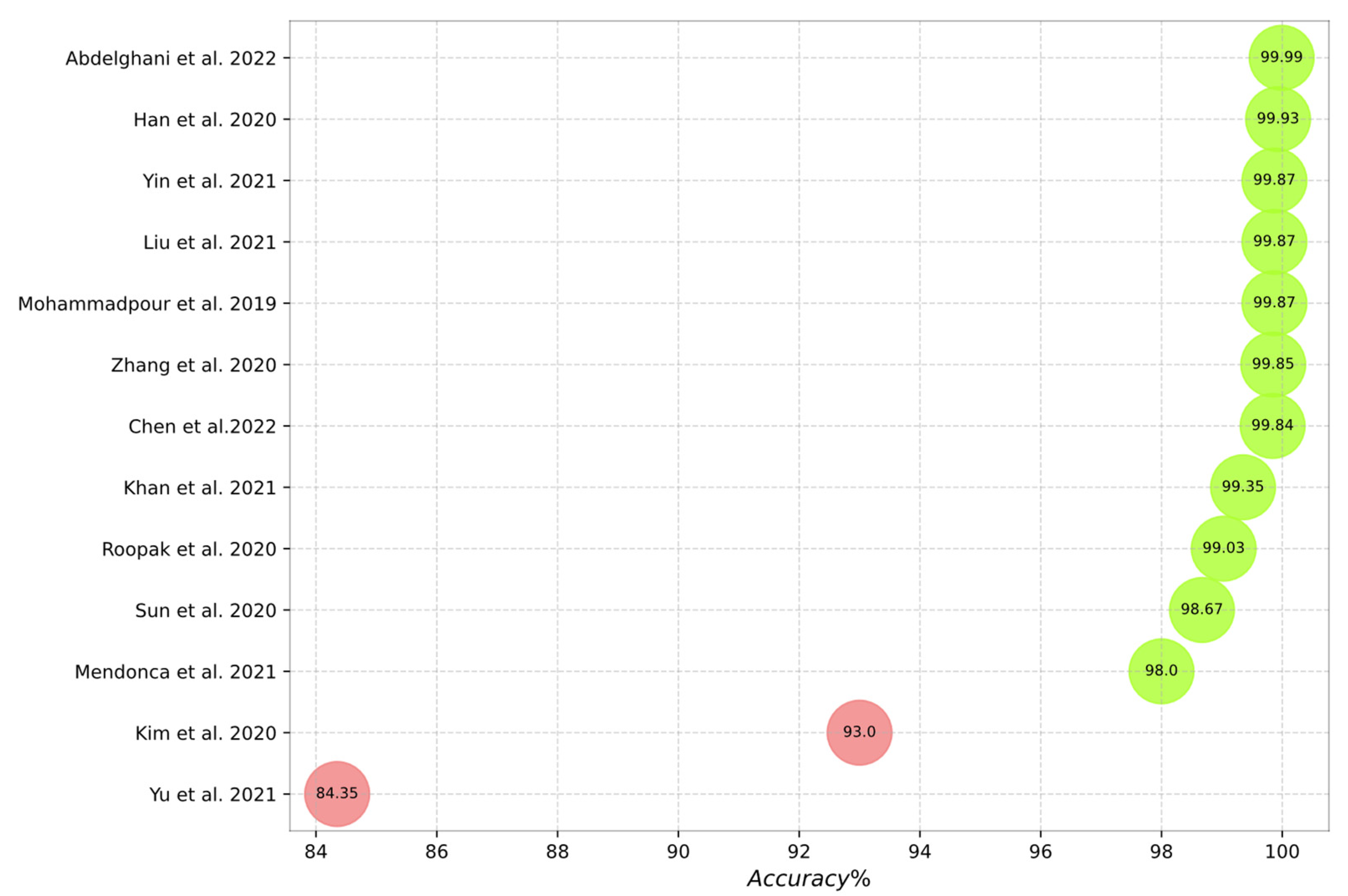
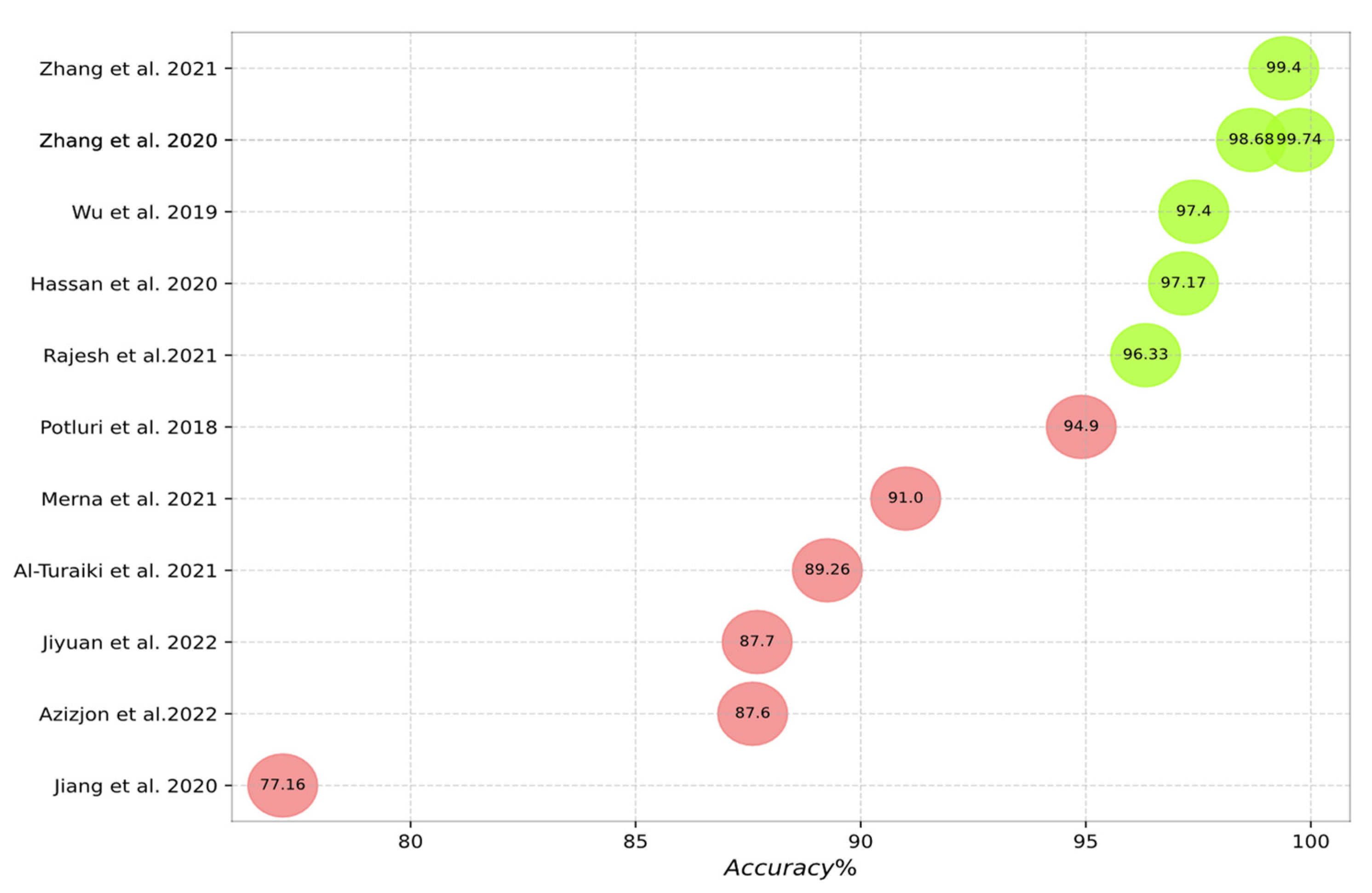
- The accuracy of the studied IDS approaches when using specific datasets.
- 17.
- LSTM is the most frequently used deep learning algorithm to hybridize with CNN in the IDS domain; this hybrid method generates the highest accuracy.
- 18.
- CNNs produce better performance when trained by a larger dataset.
7. Other Factors of CNN-Based IDS Experiments
- 19.
- Data cleaning;
- 20.
- Numerical processing;
- 21.
- Min–max normalization;
- 22.
- Standardization (Gaussian normalization);
- 23.
- Feature reduction;
- 24.
- Dimension reduction;
- 25.
- Imbalanced dataset handling;
- 26.
- Hyperparameter setting;
- 27.
- Vector-to-matrix format conversion;
- 28.
- Cross-validation.
7.1. Feature Reduction
7.2. Dimension Reduction
7.3. Imbalanced Dataset Handling
7.4. Hyperparameter Setting
7.5. Vector-to-Matrix Format Conversion
7.6. Cross-Validation
8. Empirical Experiment
- 29.
- 1D-CNN: Using only 1D convolutional layers followed by dense layers is the basic configuration of the CNN-based IDS [54,62,65,66]. The number of CNN layers in this configuration is a hyperparameter. According to Figure 8, most IDS schemes use one, two, or three layers. Thus, in this experiment, we implemented three 1D-CNN models with one to three CNN layers.
- 30.
- 31.
- 32.
- 33.
9. Conclusions and Research Directions and Gaps
- 34.
- Setting the optimized hyperparameters (i.e., layer structure, learning rate, activation function, and kernel size). These are critical in deep learning approaches, and for this reason, they require further investigation.
- 35.
- Combining misuse detection and anomaly detection through the application of CNN algorithms. This can create hybrid schemes that can effectively manage known and unknown attacks.
- 36.
- Using a comprehensive dataset, including all known and unknown attacks. Big data can now be processed by deep learning, meaning that it is possible to acquire datasets large enough to support all types of known attacks.
- 37.
- Addressing overfitting and underfitting. When data are unbalanced, overfitting can occur, particularly when the SMOTE technique is used. It is essential to identify ways to manage unbalanced data.
- 38.
- Determining an efficient method to reshape 1D features into 2D features for the CNN and generalize the CNN-based IDS.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Nomenclature
| Acronyms | Definition |
| ACCS | Australian Center for Cyber Security |
| Adam | Adaptive Moment Estimation |
| ADASYN | Adaptive Synthetic Sampling |
| AE | Autoencoder |
| AI | Artificial Intelligence |
| ALO | Ant Lion Optimizer |
| AMI | Advanced Metering Infrastructure |
| ANN | Artificial Neural Network |
| AUC | Area Under the ROC Curve |
| BCNN | Bayesian CNN |
| BG | Bagging Classifier |
| CEVR | Cumulative Explained Variance Ratio |
| CIC | Canadian Institute for Cyber Security |
| CNN | Convolutional Neural Network |
| DAE | Denoising Autoencoder |
| DBN | Deep Belief Nets |
| D-CFA | Discrete Cuttlefish Algorithm |
| DDoS | Distributed Denial of Service |
| DFS | Deep Feature Synthesis |
| DL | Deep Learning |
| DMCNN | Deep Multi-Scale CNN |
| DNN | Deep Neural Networks |
| DoS | Denial of Service |
| FC | Fully Connected |
| FCM | Fuzzy C-Means |
| GA | Genetic Algorithm |
| GRU | Gated Recurrent Unit |
| HMLSTM | Hierarchical Multi-scale LSTM |
| ICS | Industrial Control System |
| IDS | Intrusion Detection Systems |
| IG | Information Gain |
| LSO | Lion Swarm Optimization |
| LSTM | Long Short-Term Memory |
| MCL | Means Convolutional Layer |
| ML | Machine Learning |
| MLP | Multilayer Perceptron |
| MOEA | Multi-Objective Evolutionary Algorithm |
| MOEA/D | MMOEA Based on Decomposition |
| MRR | Missing Report Rate |
| NLP | Natural Language Processing |
| NSGA | Non-Dominated Sorting Algorithm |
| OCNN | Optimized CNN |
| OSS | One-Side Selection |
| PBCNN | Packet Bytes CNN |
| PCA | Principal Component Analysis |
| R2L | Remote to Local |
| RF | Random Forest |
| RNN | Recurrent Neural Network |
| ROC | Receiver Operating Characteristic Curve |
| RP | Recurrence Plots |
| RSA | Reptile Search Algorithm |
| SCNN | Siamese Convolutional Neural Networks |
| SDN | Software-Defined Networks |
| SFL | Spatial Feature Learning |
| SGD | Stochastic Gradient Descent |
| SMOTE | Synthetic Minority Oversampling Technique |
| SMOTE-NC | SMOTE-Nominal Continuous |
| SPC | Split-based Plug and Play Convolution |
| SRS | Soft-Root-Sign |
| STIDM | Spatial and Temporal Intrusion Detection Model |
| SVDD | Support Vector Data Description |
| Text-CNN | Text-Convolutional Neural Network |
| U2R | User to Root |
| Vec2im | Vectors to Images |
| WDLSTM | Weight-Dropped LSTM |
| WGAN | Wasserstein Generative Adversarial Network |
References
- Bul’ajoul, W.; James, A.; Shaikh, S. A new architecture for network intrusion detection and prevention. IEEE Access 2018, 7, 18558–18573. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, J.; Zhou, Y.; Han, L.; Lin, J. A Multiple-Layer Representation Learning Model for Network-Based Attack Detection. IEEE Access 2019, 7, 91992–92008. [Google Scholar] [CrossRef]
- Nguyen, M.T.; Kim, K. Genetic convolutional neural network for intrusion detection systems. Future Gener. Comput. Syst. 2020, 113, 418–427. [Google Scholar] [CrossRef]
- Naseer, S.; Saleem, Y.; Khalid, S.; Bashir, M.K.; Han, J.; Iqbal, M.M.; Han, K. Enhanced network anomaly detection based on deep neural networks. IEEE Access 2018, 6, 48231–48246. [Google Scholar] [CrossRef]
- Denning, D.E. An intrusion-detection model. IEEE Trans. Softw. Eng. 1987, 222–232. [Google Scholar] [CrossRef]
- Najafabadi, M.M.; Villanustre, F.; Khoshgoftaar, T.M.; Seliya, N.; Wald, R.; Muharemagic, E. Deep learning applications and challenges in big data analytics. J. Big Data 2015, 2, 1–21. [Google Scholar] [CrossRef]
- Kwon, D.; Kim, H.; Kim, J.; Suh, S.C.; Kim, I.; Kim, K.J. A survey of deep learning-based network anomaly detection. Cluster Comput. 2019, 22, 949–961. [Google Scholar] [CrossRef]
- LeCun, Y.; Bottou, L.; Bengio, Y.; Haffner, P. Gradient-based learning applied to document recognition. Proc. IEEE 1998, 86, 2278–2323. [Google Scholar] [CrossRef]
- Hochreiter, S.; Schmidhuber, J. Long short-term memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef]
- Vincent, P.; Larochelle, H.; Lajoie, I.; Bengio, Y.; Manzagol, P.A. Stacked denoising autoencoders: Learning Useful Representations in a Deep Network with a Local Denoising Criterion. J. Mach. Learn. Res. 2010, 11, 3371–3408. [Google Scholar]
- Rifai, S.; Vincent, P.; Muller, X.; Glorot, X.; Bengio, Y. Contractive auto-encoders: Explicit invariance during feature extraction. In Proceedings of the 28th International Conference on Machine Learning, ICML 2011, Bellevue, WA, USA, 28 June–2 July 2011; pp. 833–840. [Google Scholar]
- Aldweesh, A.; Derhab, A.; Emam, A.Z. Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowl. Based Syst. 2020, 189, 105124. [Google Scholar] [CrossRef]
- Chalapathy, R.; Chawla, S. Deep learning for anomaly detection: A survey. arXiv 2019, arXiv:1901.03407. [Google Scholar]
- Lee, S.-W.; Mohammadi, M.; Rashidi, S.; Rahmani, A.M.; Masdari, M.; Hosseinzadeh, M. Towards secure intrusion detection systems using deep learning techniques: Comprehensive analysis and review. J. Netw. Comput. Appl. 2021, 187, 103111. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, L.; Wu, C.Q.; Li, Z. An effective convolutional neural network based on SMOTE and Gaussian mixture model for intrusion detection in imbalanced dataset. Comput. Netw. 2020, 177, 107315. [Google Scholar] [CrossRef]
- Potluri, S.; Ahmed, S.; Diedrich, C. Convolutional neural networks for multi-class intrusion detection system. In Proceedings of the International Conference on Mining Intelligence and Knowledge Exploration 2018, Cluj-Napoca, Romania, 20–22 December 2018; pp. 225–238. [Google Scholar]
- Liu, P. An intrusion detection system based on convolutional neural network. In Proceedings of the 2019 11th International Conference on Computer and Automation Engineering, Perth, Australia, 23–25 February 2019; pp. 62–67. [Google Scholar]
- Mohammadpour, L.; Ling, T.C.; Liew, C.S.; Aryanfar, A. A Mean Convolutional Layer for Intrusion Detection System. Secur. Commun. Netw. 2020, 2020, 8891185. [Google Scholar] [CrossRef]
- Liu, G.; Zhang, J. CNID: Research of network intrusion detection based on convolutional neural network. Discret. Dyn. Nat. Soc. 2020, 2020, 4705982. [Google Scholar] [CrossRef]
- Al-Turaiki, I.; Altwaijry, N. A Convolutional Neural Network for Improved Anomaly-Based Network Intrusion Detection. Big Data 2021, 9, 233–252. [Google Scholar] [CrossRef]
- Lam, N.T. Detecting Unauthorized Network Intrusion based on Network Traffic using Behavior Analysis Techniques. Int. J. Adv. Comput. Sci. Appl. 2021, 12, 407. [Google Scholar] [CrossRef]
- Jo, W.; Kim, S.; Lee, C.; Shon, T. Packet Preprocessing in CNN-Based Network Intrusion Detection System. Electronics 2020, 9, 1151. [Google Scholar] [CrossRef]
- Kim, J.; Kim, J.; Kim, H.; Shim, M.; Choi, E. CNN-Based Network Intrusion Detection against Denial-of-Service Attacks. Electronics 2020, 9, 916. [Google Scholar] [CrossRef]
- Naseer, S.; Saleem, Y. Enhanced network intrusion detection using deep convolutional neural networks. KSII Trans. Internet Inf. Syst. 2018, 12, 5159–5178. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Nguyen, S.-N.; Nguyen, V.-Q.; Choi, J.; Kim, K. Design and Implementation of Intrusion Detection System using Convolutional Neural Network for DoS Detection. In Proceedings of the 2nd International Conference on Machine Learning and Soft Computing (ICMLSC 2018), Phu Quoc Island, Vietnam, 2–4 February 2018; pp. 34–38. [Google Scholar] [CrossRef]
- Lin, W.-H.H.; Lin, H.-C.C.; Wang, P.; Wu, B.-H.H.; Tsai, J.-Y.Y. Using convolutional neural networks to network intrusion detection for cyber threats. In Proceedings of the 4th IEEE International Conference on Applied System Innovation 2018, ICASI 2018, Tokyo, Japan, 13–17 April 2018; pp. 1107–1110. [Google Scholar] [CrossRef]
- Wang, X.; Yin, S.; Li, H.; Wang, J.; Teng, L. A Network Intrusion Detection Method Based on Deep Multi-scale Convolutional Neural Network. Int. J. Wirel. Inf. Netw. 2020, 27, 503–517. [Google Scholar] [CrossRef]
- Zhang, X.; Ran, J.; Mi, J. An intrusion detection system based on convolutional neural network for imbalanced network traffic. In Proceedings of the 2019 IEEE 7th International Conference on Computer Science and Network Technology (ICCSNT), Dalian, China, 9–20 October 2019; pp. 456–460. [Google Scholar]
- Wang, H.; Cao, Z.; Hong, B. A network intrusion detection system based on convolutional neural network. J. Intell. Fuzzy Syst. 2020, 38, 7623–7637. [Google Scholar] [CrossRef]
- Yang, H.; Wang, F. Wireless network intrusion detection based on improved convolutional neural network. IEEE Access 2019, 7, 64366–64374. [Google Scholar] [CrossRef]
- Khan, R.U.; Zhang, X.; Alazab, M.; Kumar, R. An improved convolutional neural network model for intrusion detection in networks. In Proceedings of the 2019 Cybersecurity and Cyberforensics Conference, Melbourne, Australia, 8–9 May 2019; pp. 74–77. [Google Scholar] [CrossRef]
- Mohammadpour, L.; Ling, T.C.; Liew, C.S.; Chong, C.Y. A Convolutional Neural Network for Network Intrusion Detection System. Proc. Asia Pacific Adv. Netw. 2018, 46, 50–55. [Google Scholar]
- Aljumah, A. IoT-based intrusion detection system using convolution neural networks. PeerJ Comput. Sci. 2021, 7, e721. [Google Scholar] [CrossRef]
- Akhtar, M.S.; Feng, T. Deep Learning-Based Framework for the Detection of Cyberattack Using Feature Engineering. Secur. Commun. Netw. 2021, 2021, 6129210. [Google Scholar] [CrossRef]
- Hu, Z.; Wang, L.; Qi, L.; Li, Y.; Yang, W. A Novel Wireless Network Intrusion Detection Method Based on Adaptive Synthetic Sampling and an Improved Convolutional Neural Network. IEEE Access 2020, 8, 195741–195751. [Google Scholar] [CrossRef]
- Gamal, M.; Abbas, H.M.; Moustafa, N.; Sitnikova, E.; Sadek, R.A. Few-shot learning for discovering anomalous behaviors in edge networks. Comput. Mater. Contin. 2021, 69, 1823–1837. [Google Scholar] [CrossRef]
- Wu, P.; Guo, H. LuNET: A deep neural network for network intrusion detection. In Proceedings of the 2019 IEEE Symposium Series on Computational Intelligence (SSCI), Xiamen, China, 6–9 December 2019; pp. 617–624. [Google Scholar]
- Yao, R.; Wang, N.; Liu, Z.; Chen, P.; Sheng, X. Intrusion Detection System in the Advanced Metering Infrastructure: A Cross-Layer Feature-Fusion CNN-LSTM-Based Approach. Sensors 2021, 21, 626. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Soman, K.P.; Poornachandrany, P. Applying convolutional neural network for network intrusion detection. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics, ICACCI 2017, Udupi, India, 13–16 September 2017; Volume 2017, pp. 1222–1228. [Google Scholar] [CrossRef]
- Han, X.; Yin, R.; Lu, Z.; Jiang, B.; Liu, Y.; Liu, S.; Wang, C.; Li, N. STIDM: A Spatial and Temporal Aware Intrusion Detection Model. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TRUSTCOM 2020), Guangzhou, China, 29 December 2020–1 January 2021; pp. 370–377. [Google Scholar] [CrossRef]
- Hassan, M.M.; Gumaei, A.; Alsanad, A.; Alrubaian, M.; Fortino, G. A hybrid deep learning model for efficient intrusion detection in big data environment. Inf. Sci. 2020, 513, 386–396. [Google Scholar] [CrossRef]
- Khan, M.A.; Karim, M.R.; Kim, Y. A scalable and hybrid intrusion detection system based on the convolutional-LSTM network. Symmetry 2019, 11, 583. [Google Scholar] [CrossRef]
- Liu, C.; Gu, Z.; Wang, J. A Hybrid Intrusion Detection System Based on Scalable K-Means plus Random Forest and Deep Learning. IEEE Access 2021, 9, 75729–75740. [Google Scholar] [CrossRef]
- Kim, A.; Park, M.; Lee, D.H. AI-IDS: Application of Deep Learning to Real-Time Web Intrusion Detection. IEEE Access 2020, 8, 70245–70261. [Google Scholar] [CrossRef]
- Sun, P.; Liu, P.; Li, Q.; Liu, C.; Lu, X.; Hao, R.; Chen, J. DL-IDS: Extracting Features Using CNN-LSTM Hybrid Network for Intrusion Detection System. Secur. Commun. Netw. 2020, 2020, 8890306. [Google Scholar] [CrossRef]
- Karanam, L.; Pattanaik, K.K.; Aldmour, R. Intrusion Detection Mechanism for Large Scale Networks using CNN-LSTM. In Proceedings of the 2020 13th International Conference on Developments in Esystems Engineering (DESE 2020), Liverpool, UK, 4–17 December 2020; pp. 323–328. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. An Intrusion Detection System Against DDoS Attacks in IoT Networks. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 562–567. [Google Scholar]
- Jiang, K.; Wang, W.; Wang, A.; Wu, H. Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access 2020, 8, 32464–32476. [Google Scholar] [CrossRef]
- Andalib, A.; Vakili, V.T. An Autonomous Intrusion Detection System Using an Ensemble of Advanced Learners. In Proceedings of the 2020 28th Iranian Conference on Electrical Engineering (ICEE), Tabriz, Iran, 4–6 August 2020; pp. 828–832. [Google Scholar]
- Khan, M.A. HCRNNIDS: Hybrid Convolutional Recurrent Neural Network-Based Network Intrusion Detection System. Processes 2021, 9, 834. [Google Scholar] [CrossRef]
- Chen, Y.; Lin, Q.; Wei, W.; Ji, J.; Wong, K.-C.; Coello, C.A.C. Intrusion detection using multi-objective evolutionary convolutional neural network for Internet of Things in Fog computing. Knowl. Based Syst. 2022, 244, 108505. [Google Scholar] [CrossRef]
- Cheng, P.; Xu, K.; Li, S.; Han, M. TCAN-IDS: Intrusion Detection System for Internet of Vehicle Using Temporal Convolutional Attention Network. Symmetry 2022, 14, 310. [Google Scholar] [CrossRef]
- Thilagam, T.; Aruna, R. Intrusion detection for network based cloud computing by custom RC-NN and optimization. ICT Express 2021, 7, 512–520. [Google Scholar] [CrossRef]
- Desta, A.K.; Ohira, S.; Arai, I.; Fujikawa, K. Rec-CNN: In-vehicle networks intrusion detection using convolutional neural networks trained on recurrence plots. Veh. Commun. 2022, 35, 100470. [Google Scholar] [CrossRef]
- Elsayed, M.S.; Le-Khac, N.-A.; Jahromi, H.Z.; Jurcut, A.D. A Hybrid CNN-LSTM Based Approach for Anomaly Detection Systems in SDNs. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021. [Google Scholar]
- Lo, W.; Alqahtani, H.; Thakur, K.; Almadhor, A.; Chander, S.; Kumar, G. A hybrid deep learning based intrusion detection system using spatial-temporal representation of in-vehicle network traffic. Veh. Commun. 2022, 35, 100471. [Google Scholar] [CrossRef]
- Yang, X.; Peng, G.; Zhang, D.; Lv, Y. An Enhanced Intrusion Detection System for IoT Networks Based on Deep Learning and Knowledge Graph. Secur. Commun. Netw. 2022, 2022, 4748528. [Google Scholar] [CrossRef]
- Cui, J.; Zong, L.; Xie, J.; Tang, M. A novel multi-module integrated intrusion detection system for high-dimensional imbalanced data. Appl. Intell. 2022, 1–17. [Google Scholar] [CrossRef]
- Elsayed, N.; Zaghloul, Z.S.; Azumah, S.W.; Li, C. Intrusion Detection System in Smart Home Network Using Bidirectional LSTM and Convolutional Neural Networks Hybrid Model. In Proceedings of the 2021 IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Lansing, MI, USA, 9–11 August 2021; pp. 55–58. [Google Scholar]
- Kanna, P.R.; Santhi, P. Unified deep learning approach for efficient intrusion detection system using integrated spatial–temporal features. Knowl. Based Syst. 2021, 226, 107132. [Google Scholar] [CrossRef]
- Meliboev, A.; Alikhanov, J.; Kim, W. Performance Evaluation of Deep Learning Based Network Intrusion Detection System across Multiple Balanced and Imbalanced Datasets. Electronics 2022, 11, 515. [Google Scholar] [CrossRef]
- Min, E.; Long, J.; Liu, Q.; Cui, J.; Chen, W. TR-IDS: Anomaly-based intrusion detection through text-convolutional neural network and random forest. Secur. Commun. Netw. 2018, 2018, 4943509. [Google Scholar] [CrossRef]
- Zhang, Y.; Ran, X. A Step-Based Deep Learning Approach for Network Intrusion Detection. C. Model. Eng. Sci. 2021, 128, 1231–1245. [Google Scholar] [CrossRef]
- Yong, L.; Bo, Z. An Intrusion Detection Model Based on Multi-scale CNN. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC 2019), Chengdu, China, 15–17 March 2019; pp. 214–218. [Google Scholar]
- Yu, L.; Dong, J.; Chen, L.; Li, M.; Xu, B.; Li, Z.; Qiao, L.; Liu, L.; Zhao, B.; Zhang, C. PBCNN: Packet Bytes-based Convolutional Neural Network for Network Intrusion Detection. Comput. Netw. 2021, 194, 108117. [Google Scholar] [CrossRef]
- Wang, H.; Li, W. DDosTC: A transformer-based network attack detection hybrid mechanism in SDN. Sensors 2021, 21, 5047. [Google Scholar] [CrossRef]
- Yin, S.; Zhang, X.; Liu, S. Intrusion detection for capsule networks based on dual routing mechanism. Comput. Netw. 2021, 197, 108328. [Google Scholar] [CrossRef]
- Xiao, Y.; Xing, C.; Zhang, T.; Zhao, Z. An Intrusion Detection Model Based on Feature Reduction and Convolutional Neural Networks. IEEE Access 2019, 7, 42210–42219. [Google Scholar] [CrossRef]
- Moustakidis, S.; Karlsson, P. A novel feature extraction methodology using Siamese convolutional neural networks for intrusion detection. Cybersecurity 2020, 3, 1–13. [Google Scholar] [CrossRef]
- Mendonca, R.V.; Teodoro, A.A.; Rosa, R.L.; Saadi, M.; Melgarejo, D.C.; Nardelli, P.H.; Rodríguez, D.Z. Intrusion Detection System Based on Fast Hierarchical Deep Convolutional Neural Network. IEEE Access 2021, 9, 61024–61034. [Google Scholar] [CrossRef]
- Liu, K.; Fan, Z.; Liu, M.; Zhang, S. Hybrid Intrusion Detection Method Based on K-means and CNN for Smart Home. In Proceedings of the 2018 IEEE 8th Annual International Conference on Cyber Technology in Automation, Control, and Intelligent Systems (IEEE-Cyber), Tianjin, China, 19–23 July 2018; pp. 312–317. [Google Scholar]
- Khan, A.S.; Ahmad, Z.; Abdullah, J.; Ahmad, F. A Spectrogram Image-Based Network Anomaly Detection System Using Deep Convolutional Neural Network. IEEE Access 2021, 9, 87079–87093. [Google Scholar] [CrossRef]
- Chen, X.; Cao, C.; Mai, J. Network Anomaly Detection Based on Deep Support Vector Data Description. In Proceedings of the 2020 5th IEEE International Conference on Big Data Analytics (IEEE ICBDA 2020), Xiamen, China, 8–11 May 2020; pp. 251–255. [Google Scholar]
- Zhang, J.; Li, F.; Ye, F. An Ensemble-based Network Intrusion Detection Scheme with Bayesian Deep Learning. In Proceedings of the ICC 2020-2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar]
- Dahou, A.; Abd Elaziz, M.; Chelloug, S.A.; Awadallah, M.A.; Al-Betar, M.A.; Al-qaness, M.A.; Forestiero, A. Intrusion Detection System for IoT Based on Deep Learning and Modified Reptile Search Algorithm. Comput. Intell. Neurosci. 2022, 2022, 6473507. [Google Scholar] [CrossRef]
- Mondal, A.; Goswami, R.T. Enhanced Honeypot cryptographic scheme and privacy preservation for an effective prediction in cloud security. Microprocess. Microsyst. 2021, 81, 103719. [Google Scholar] [CrossRef]
- Haq, M.A.; Khan, M.A.R.; Talal, A.-H. Development of PCCNN-Based Network Intrusion Detection System for EDGE Computing. C. Mater. Contin. 2022, 71, 1769–1788. [Google Scholar]
- Deng, L.; Yu, D. Deep learning: Methods and applications. Found. Trends® Signal Process. 2014, 7, 197–387. [Google Scholar] [CrossRef]
- Chouhan, N.; Khan, A. Network anomaly detection using channel boosted and residual learning based deep convolutional neural network. Appl. Soft Comput. 2019, 83, 105612. [Google Scholar] [CrossRef]
- Mrazova, I.; Kukacka, M. Can deep neural networks discover meaningful pattern features? Procedia Comput. Sci. 2012, 12, 194–199. [Google Scholar] [CrossRef]
- Tian, C.; Fei, L.; Zheng, W.; Xu, Y.; Zuo, W.; Lin, C.-W. Deep learning on image denoising: An overview. Neural Netw. 2020, 131, 251–275. [Google Scholar] [CrossRef]
- Song, Z. English speech recognition based on deep learning with multiple features. Computing 2020, 102, 663–682. [Google Scholar] [CrossRef]
- Yadav, A.; Vishwakarma, D.K. Sentiment analysis using deep learning architectures: A review. Artif. Intell. Rev. 2020, 53, 4335–4385. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef]
- Bjornson, E.; Giselsson, P. Two applications of deep learning in the physical layer of communication systems [lecture notes]. IEEE Signal Process. Mag. 2020, 37, 134–140. [Google Scholar] [CrossRef]
- Guo, G.; Zhang, N. A survey on deep learning based face recognition. Comput. Vis. Image Underst. 2019, 189, 102805. [Google Scholar] [CrossRef]
- Wallach, I.; Dzamba, M.; Heifets, A. AtomNet: A deep convolutional neural network for bioactivity prediction in structure-based drug discovery. arXiv 2015, arXiv:1510.02855. [Google Scholar]
- Hubel, D.H.; Wiesel, T.N. Receptive fields and functional architecture of monkey striate cortex. J. Physiol. 1968, 195, 215–243. [Google Scholar] [CrossRef]
- Yamashita, R.; Nishio, M.; Do, R.K.G.; Togashi, K. Convolutional neural networks: An overview and application in radiology. Insights Imaging 2018, 9, 611–629. [Google Scholar] [CrossRef] [PubMed]
- Albawi, S.T.; Mohammed, A.; Al-Zawi, S. Understanding of a convolutional neural network. In Proceedings of the 2017 International Conference on Engineering and Technology (ICET), Antalya, Turkey, 21–23 August 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Zhang, Q.; Zhang, M.; Chen, T.; Sun, Z.; Ma, Y.; Yu, B. Recent advances in convolutional neural network acceleration. Neurocomputing 2019, 323, 37–51. [Google Scholar] [CrossRef]
- Hinton, G.E.; Srivastava, N.; Krizhevsky, A.; Sutskever; Salakhutdinov, R.R. Improving neural networks by preventing co-adaptation of feature detectors. arXiv 2012, arXiv:1207.0580. [Google Scholar]
- Zeiler, M.D.; Fergus, R. Visualizing and understanding convolutional networks. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics, Proceedings of the 13th European Conference 2014, Zurich, Switzerland, 6–12 September 2014; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8689, pp. 818–833. [Google Scholar] [CrossRef]
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition. In Proceedings of the 3rd International Conference on Learning Representations, Conference Track Proceedings, ICLR 2015, San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- Duchi, J.; Hazan, E.; Singer, Y. Adaptive subgradient methods for online learning and stochastic optimization. In Proceedings of the 23rd Annual Conference on Learning Theory (COLT 2010), Haifa, Israel, 27–29 June 2010; Volume 12, pp. 257–269. [Google Scholar]
- Zeiler, M.D. ADADELTA: An Adaptive Learning Rate Method. 2012. Available online: http://arxiv.org/abs/1212.5701 (accessed on 1 February 2022).
- Kingma, D.P.; Ba, J. Adam: A Method for Stochastic Optimization. arXiv 2014, arXiv:1412.6980. [Google Scholar]
- Gulshan, V.; Peng, L.; Coram, M.; Stumpe, M.C.; Wu, D.; Narayanaswamy, A.; Venugopalan, S.; Widner, K.; Madams, T.; Cuadros, J.; et al. Development and validation of a deep learning algorithm for detection of diabetic retinopathy in retinal fundus photographs. JAMA 2016, 316, 2402–2410. [Google Scholar] [CrossRef]
- Yu, Y.; Si, X.; Hu, C.; Zhang, J. A review of recurrent neural networks: LSTM cells and network architectures. Neural Comput. 2019, 31, 1235–1270. [Google Scholar] [CrossRef]
- KDD Cup; UCI KDD Archiv: Irvine, CA, USA, 28 October 1999. Available online: https://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 1 February 2022).
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the IEEE Symposium on Computational Intelligence for Security and Defense Applications, CISDA 2009, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Revathi, D.a.M.S.; Revathi, S.; Malathi, A. A detailed analysis on NSL-KDD dataset using various machine learning techniques for intrusion detection. Int. J. Eng. Res. Technol. 2013, 2, 1848–1853. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.680.6760&rep=rep1&type=pdf (accessed on 1 February 2022).
- Kayacik, H.G.; Zincir-Heywood, A.N.; Heywood, I.M. Selecting features for intrusion detection: A feature relevance analysis on KDD 99 intrusion detection datasets. In Proceedings of the Third Annual Conference on Privacy, Security and Trust, San Francisco, CA, USA, 20–22 October 2010; Volume 94, pp. 1722–1723. [Google Scholar]
- Moustafa, N.; Jill, S. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; IEEE: Manhattan, NY, USA; pp. 1–6. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. The evaluation of Network Anomaly Detection Systems: Statistical analysis of the UNSW-NB15 data set and the comparison with the KDD99 data set. Inf. Secur. J. 2016, 25, 18–31. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. In Proceedings of the ICISSP 2018–Proceedings of the 4th International Conference on Information Systems Security and Privacy, Funchal, Portugal, 22–24 January 2018; Volume 2018, pp. 108–116. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Gharib, A.; Lashkari, A.H.; Ghorbani, A.A. Towards a reliable intrusion detection benchmark dataset. Softw. Netw. 2018, 2018, 177–200. [Google Scholar] [CrossRef]
- D’hooge, L.; Wauters, T.; Volckaert, B.; De Turck, F. Classification hardness for supervised learners on 20 years of intrusion detection data. IEEE Access 2019, 7, 167455–167469. [Google Scholar] [CrossRef]
- Jaganathan, V.; Cherurveettil, P.; Sivashanmugam, P.M. Using a prediction model to manage cyber security threats. Sci. World J. 2015, 2015, 703713. [Google Scholar] [CrossRef] [PubMed]
- Ding, Y.; Zhai, Y. Intrusion detection system for NSL-KDD dataset using convolutional neural networks. In Proceedings of the 2018 2nd International Conference on Computer Science and Artificial Intelligence, Shenzhen, China, 8–10 December 2018; pp. 81–85. [Google Scholar]
- Wu, K.; Chen, Z.; Li, W. A novel intrusion detection model for a massive network using convolutional neural networks. IEEE Access 2018, 6, 50850–50859. [Google Scholar] [CrossRef]




| Layer | Parameter | Hyperparameters |
|---|---|---|
| Convolutional | Kernels | Kernel size, number of kernels, activation function, stride, and padding |
| Pooling | None | Pooling method, filter size, stride, and padding |
| Fully connected | Weights | Number of weights and activation function |
| Others | None | Model architecture, optimizer, learning rate, loss function, mini-batch size, epochs, regularization, weight initialization, and dataset splitting |
| Data Type | Attack Name | Training Set | Test Set |
|---|---|---|---|
| Normal | ---- | 97,278 | 60,593 |
| Attack | DoS | 391,458 | 223,298 |
| Probe | 4107 | 2377 | |
| R2L | 1126 | 5993 | |
| Total | ----- | 494,021 | 292,300 |
| File | Description | Num. of Samples | Num. of Normal |
|---|---|---|---|
| Train+ | Full training set | 125,973 | 67,343 |
| Train20 | 20% of the training set | 251,92 | 13,499 |
| Test+ | Full testing set | 22,544 | 9711 |
| Test− | A subset of training set | 11,850 | 2152 |
| Terminology | Other Terminologies or Explanation | Equation |
|---|---|---|
| ACC | Accuracy | |
| PPV | Precision and positive predictive value | |
| TPR | Recall, sensitivity, true positive rate, and detection rate | |
| FNR | Miss rate and miss false negative rate | |
| TNR | Specificity, selectivity, and true negative rate | |
| FPR | False alarm and false positive rate | |
| F1 Score | F1 Score and F Measure | |
| ROC | ROC curve: a graph with the x-axis shows FPR, and y-axis shows TPR | |
| AUC | The area under the curve or area under the ROC curve | |
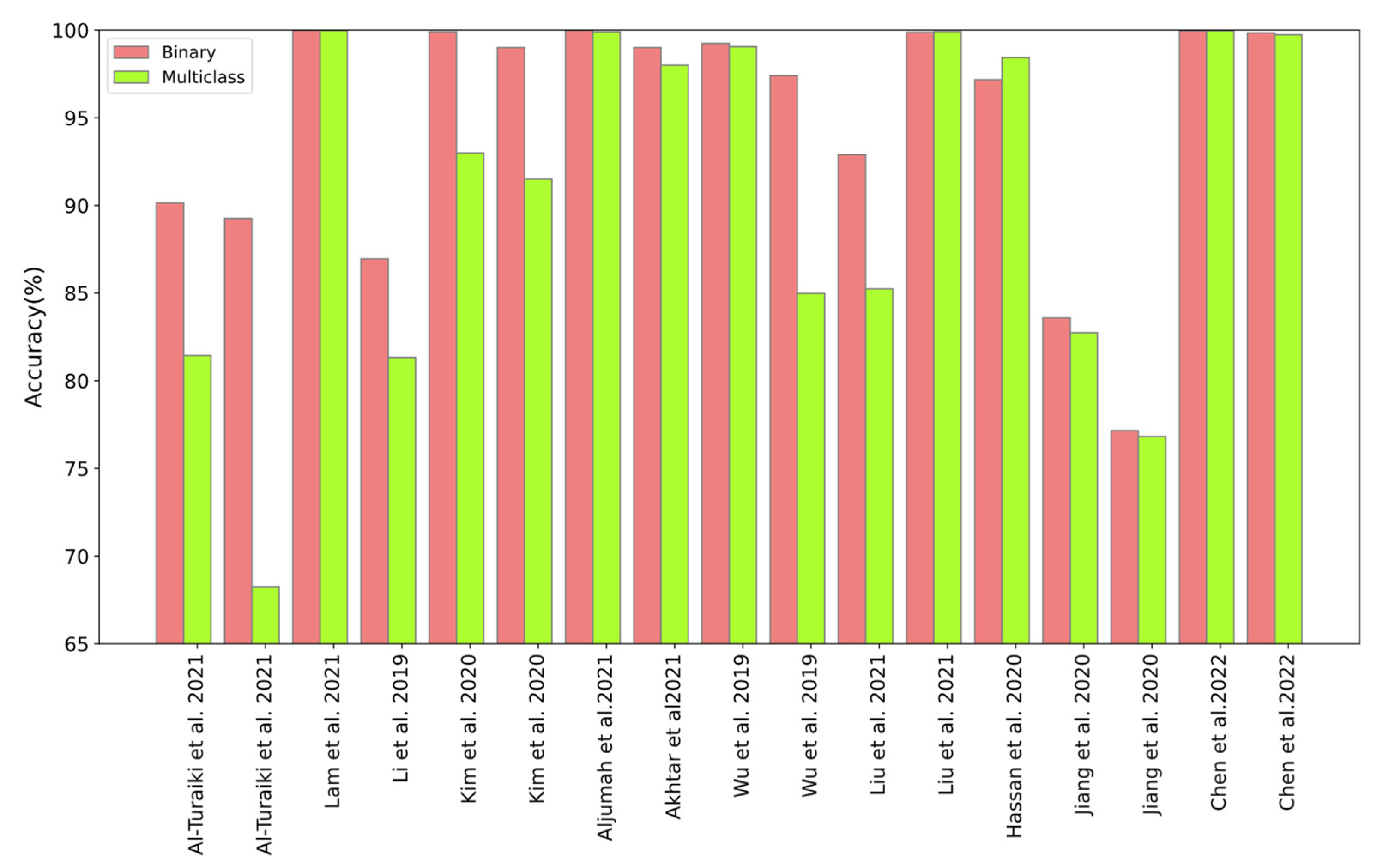
| Authors | Year | ENV | Datasets | Binary Accuracy (%) | Multiclass Accuracy (%) | Evaluation Metrics |
|---|---|---|---|---|---|---|
| Potluri et al. [16] | 2018 | M | KDD Cup99 UNSW-NB15 | 91.14 94.90 | --- | ACC, PPV, TPR, F1 Score |
| Mohammadpour et al. [18] | 2019 | T | CIC-IDS2017 | 99.87 | --- | ACC, PPV, TPR, F1 Score, FPR |
| Liu et al. [17] | 2019 | T | KDD Cup99 | 99.00 | --- | ACC, TPR, FPR |
| Liu et al. [19] | 2020 | T | KDD Cup99 NSL-KDD | --- | 98.02 97.09 | ACC, PPV, TPR, F1 Score, FPR |
| Al-Turaiki et al. [20] | 2021 | KT | NSL-KDD UNSW-NB15 | 90.14 89.26 | 81.44 68.25 | ACC, PPV, TPR, F1 Score |
| Lam et al. [21] | 2021 | --- | CSE-CIC-IDS2018 | 99.99 | 99.98 | ACC, PPV, TPR, F1 Score |
| Jo et al. [22] | 2020 | T | NSL-KDD | 88.82 | --- | ACC, PPV, TPR, F1 Score |
| Kim et al. [23] | 2020 | T | KDD Cup99 CSE-CIC-IDS2018 | 99.90 99.00 | 93.00 91.50 | ACC, PPV, TPR |
| Nesser et al. [24] | 2018 | KH | NSL-KDD | 85.22 | --- | ROC, AUC, PPV, TPR |
| Li et al. [25] | 2019 | KT | NSL-KDD | 86.95 | 81.33 | FPR, ACC, PPV, TPR |
| Nguyen et al. [26] | 2018 | T | KDD Cup99 | 99.87 | --- | ACC, Time |
| Lin et al. [27] | 2018 | T | CSE-CIC-IDS2018 | 97.53 | --- | F1 Score |
| Wang et al. [28] | 2020 | T | NSL-KDD | 98.00 | --- | ACC |
| Ding et al. [111] | 2018 | KT | NSL-KDD | 80.13 | --- | ACC, TPR, FPR |
| Zhang et al. [29] | 2019 | T | NSL-KDD | 83.31 | --- | ACC, TPR, FPR |
| Wang et al. [30] | 2019 | T | NSL-KDD | 97.70 | --- | ACC, TPR |
| Yang et al. [31] | 2019 | T | NSL-KDD | --- | 95.36 | ACC, TPR, FPR |
| Khan et al. [32] | 2019 | --- | NSL-KDD | 99.23 | --- | ACC |
| Mohammadpour et al. [33] | 2017 | T | NSL-KDD | 99.79 | --- | ACC |
| Aljumah et al. [34] | 2021 | KT | Bot-IoT | 99.99 | 99.90 | ACC, PPV, TPR, F1 Score |
| Akhtar et al. [35] | 2021 | --- | NSL-KDD | 99.00 | 98.00 | ACC, PPV, TPR, F1 Score |
| Zhiquan et al. [36] | 2020 | --- | NSL-KDD | --- | 84.08 | ACC, FPR, TPR |
| Merna et al. [37] | 2021 | K | UNSW-NB15 Bot-IoT | 91.00 99.90 | --- | FPR, TPR, ROC |
| Authors | Architecture | Input Shape | Feature Extraction | Classifier |
|---|---|---|---|---|
| Potluri et al. [16] | 3 Conv, 2 MaxPool, 1 FC | 2D (8 × 8) | CNN | SoftMax |
| Mohammadpour et al. [18] | 3 Conv, 3 MaxPool, 2 FC | 2D (11 × 11) | CNN | SoftMax |
| Liu et al. [17] | 3 Conv, 2 MaxPool, 2 FC | 2D (32 × 32) | CNN | SoftMax |
| Liu et al. [19] | 2 Conv, 2 MaxPool, 1 FC | 1D (32) | CNN | SoftMax |
| Al-Turaiki et al. [20] | 5 Conv, 2 MaxPool, 4 FC | 2D (11 × 11) 2D (14 × 14) | CNN | SoftMax |
| Lam et al. [21] | 3 Conv, 2 MaxPool, 2 FC | 1D | CNN | SoftMax |
| Jo et al. [22] | 1 Conv, 1 MaxPool,1 FC | 2D (28 × 28) | CNN, weighted & compressed | SoftMax |
| Kim et al. [23] | 3 Conv, 2 MaxPool | 2D (13 × 9), 2D (13 × 9 × 3) | CNN | SoftMax |
| Nesser et al. [24] | 4 Conv, 2 MaxPool, 1 Dropout, 2 FC | 2D (32 × 32) | CNN | SoftMax |
| Li et al. [25] | 2 Conv, 2 MaxPool, 3 FC | 2D (9 × 10) | CNN | SoftMax |
| Nguyen et al. [26] | 2 Conv, 3 FC | 2D (7 × 7) | CNN | SoftMax |
| Lin et al. [27] | 2 Conv, 2 MaxPool, 1 FC | 2D (32 × 32) | CNN | SoftMax |
| Wang et al. [28] | 3 MSConv, 2 Conv,2 AvgPool, 3 FC | 2D (11 × 11) | CNN | SoftMax |
| Ding et al. [111] | 3 Conv, 3 MaxPool,3 FC | 1D (122) | CNN | SoftMax |
| Zhang et al. [29] | 2 Conv, 2 MaxPool, 1 FC | 2D (11 × 11) | CNN | SoftMax |
| Wang et al. [30] | 2 Conv, 1 MaxPool, 2 FC | 2D (6 × 6) | CNN | SoftMax |
| Yang et al. [31] | 5 Conv, 2 MaxPool, 4 FC | 1D (122) | CNN | SoftMax |
| Khan et al. [32] | 3 Conv, 3 MaxPool, 1 FC | 1D (84) | CNN | SoftMax |
| Mohammadpour et al. [33] | 2 Conv, 2 MaxPool, 3 FC | 2D (11 × 11) | CNN | SoftMax |
| Aljumah et al. [34] | 2 Conv, 1MaxPool, 1 BatchNo, 2 FC, 1 Dropout | 1D | CNN, attribute transformation and reduction | SoftMax |
| Akhtar et al. [35] | 2 Conv, 1 MaxPool, 1 Flatten, 2 FC | 1D (157) | Minimum redundancy Maximum relevance | SoftMax |
| Zhiquan et al. [36] | 2 Conv, 1 FC | 2D | ADASYN, feature fusion | SoftMax |
| Merna et al. [37] | 3 Conv, 3 MaxPool, 1 Flatten, 2 Fc | 1D | IG, CNN | SoftMax |
| Authors | Year | ENV | Datasets | Binary Accuracy (%) | Multiclass Accuracy (%) | Evaluation Metrics |
|---|---|---|---|---|---|---|
| Wu et al. [38] | 2019 | KT | NSL-KDD UNSW-NB15 | 99.24 97.40 | 99.05 84.98 | ACC, TPR, FPR |
| Yao et al. [39] | 2021 | T | KDD Cup99 NSL-KDD | 99.95 99.79 | --- --- | ACC, PPV, TPR, F1 Score, FPR |
| Vinayakumar et al. [40] | 2017 | T | KDD Cup99 | 87.80 | --- | ACC, TPR, FPR |
| Han et al. [41] | 2020 | T | ISCX2012 CIC-IDS2017 | 99.69 99.93 | --- --- | PPV, TPR, F1 Score |
| Hassan et al. [42] | 2020 | --- | UNSW-NB15 | 97.17 | 98.43 | ACC, PPV, ROC, TPR, F1 Score, |
| Khan et al. [43] | 2019 | KT | ISCX-UNB | 97.29 | --- | PPV, TPR, ACC, F1 Score, FPR |
| Liu et al. [44] | 2021 | KT | NSL-KDD CIC-IDS2017 | 92.90 99.87 | 85.24 99.91 | ACC, TPR, Time |
| Kim et al. [45] | 2020 | T | CSIC-2010 CIC-IDS2017 | 91.54 93.00 | --- | ACC, PPV, TPR, F1 Score |
| Sun et al. [46] | 2020 | KT | CIC-IDS2017 | 98.67 | --- | FPR, F1 Score, PPV, TPR |
| Karanam et al. [47] | 2020 | KT | NSL-KDD | --- | 99.60 | ACC |
| Roopak et al. [48] | 2020 | KT | CIC-IDS2017 | 99.03 | --- | ACC, PPV, TPR, F1 Score, |
| Jiang et al. [49] | 2020 | T | NSL-KDD UNSW-NB15 | 83.58 77.16 | 82.74 76.82 | ACC, PPV, TPR, F1 Score, |
| Andalib et al. [50] | 2020 | T, S | NSL-KDD | 87.28 | --- | ACC, FPR, TPR |
| Khan, M.A. [51] | 2021 | J | CSE-CIC-IDS2018 | 97.75 | --- | ACC, PPV, TPR, F1 Score, TPR, FPR |
| Chen et al. [52] | 2022 | KT | AWID CIC-IDS2017 | 99.96 99.84 | 99.96 99.73 | ACC, PPV, TPR, F1 Score |
| Cheng et al. [53] | 2022 | K | CAN Signal Extraction and Translation | 99.97 | --- | ACC, PPV, TPR, F1 Score, ER |
| Thilagam et al. [54] | 2021 | M | DARPA CSE-CIC-IDS2018 | --- --- | 94.01 94.28 | ACC, PPV, TPR, F1 Score, ER |
| Desta et a. [55] | 2022 | --- | Collected data CAR-HACKING | 99.50 99.90 | --- | TPR, FPR, ROC |
| Elsayed et al. [56] | 2021 | K | InSDN | 96.32 | --- | ACC, PPV, TPR, F1 Score, ROC |
| Wei et al. [57] | 2022 | k | Car-hacking | 100.00 | --- | ACC, PPV, TPR, F1 Score, FPR, FNR |
| Xiuzhang et al. [58] | 2022 | KT | NSL-KDD | 90.01 | --- | ACC, PPV, TPR, F1 Score, FPR |
| Jiyuan et al. [59] | 2022 | --- | NSL-KDD UNSW-NB15 | 86.59 87.70 | --- | ACC, PPV, TPR, F1 Score |
| Nelly et al. [60] | 2021 | KT | IoT Intrusion | 98.93 | --- | ACC, PPV, TPR, F1 Score |
| Rajesh et al. [61] | 2021 | M | NSL-KDD ISCX-IDS UNSW-NB15 | --- --- --- | 90.67 95.33 96.33 | ACC, PPV, TPR, F1 Score, FPR, FNR |
| Azizjon et al. [62] | 2022 | KT | UNSW-NB15 KDD Cup99 NSL-KDD | 87.60 95.20 82.60 | --- --- --- | ACC, PPV, TPR, F1 Score |
| Authors | Architecture | Input Shape | Feature Extraction | Classifier |
|---|---|---|---|---|
| Wu et al. [38] | 4 Conv, 3 MaxPool, 1 AvgPooling, 3 LSTM, 1 FC | 1D | CNN, LSTM | SoftMax |
| Yao et al. [39] | 4 Conv, 2 MaxPool, 2 FC,1 LSTM | 2D (10 × 10) | LSTM, CNN | SoftMax |
| Vinayakumar et al. [40] | 1 Conv, 1 MaxPool, 1 LSTM, 1 FC | 1D (41) | CNN | SoftMax |
| Han et al. [41] | 2 Conv, 2 Pooling, 1 FC | 1D | CNN, LSTM | SoftMax |
| Hassan et al. [42] | 2 Conv, 1 MaxPool, 1 FC | 2D | CNN-WDLSTM | SoftMax |
| Khan et al. [43] | 2 Conv, 2 Pool, 2 LSTM, 2 FC | 1D | CNN, LSTM | SoftMax |
| Liu et al. [44] | 3 Conv, 3 MaxPool, 3 LSTM, 1 FC | 2D (11 × 11) | CNN, LSTM | SoftMax |
| Kim et al. [45] | 2 Conv, 2 MaxPool, 1 LSTM, 9 FC | 1D (1000) | CNN, LSTM | DNN |
| Sun et al. [46] | 2 Conv,2 MaxPool, 2 FC,2 LSTM | 2D | CNN | SoftMax |
| Karanam et al. [47] | 2 Conv, 2 MaxPool, 2 LSTM, 1 FC | 2D (11 × 11) | CNN, LSTM | SoftMax |
| Roopak et al. [48] | 1 CNN, 1 MaxPool, 1 LSTM | 1D (81) | CNN, NSGA-II multi-objective | SoftMax |
| Jiang et al. [49] | 2 Conv, 2 Pooling, 2 BiLSTM, 1FC | 2D (11 × 11) | CNN, BiLSTM | SoftMax |
| Andalib et al. [50] | 2 Conv, 3 MaxPool, 1 FC | 1D (41) | CNN, GRU | Decision maker |
| Khan, M.A. [51] | 2 Conv, 2 MaxPool, 2 RNN, 1 Flatten, 1FC | 2D | CNN, RN | SoftMax |
| Chen et al. [52] | Defined by the MECNN algorithm | 1D (74) 1D (77) | MOEA/D, CNN | SoftMax |
| Cheng et al. [53] | 6 Conv, 6 Dropout, 1 Flatten, 1 FC | 2D (64 × 19) | CNN, LSTM | SoftMax |
| Thilagam et al. [54] | --- | 1D | CNN, LSTM | SoftMax |
| Desta et a. [55] | 2 Conv, 2 MaxPool, 1 Dropout, 2 FC | 2D (128 × 128) | CNN, LSTM | SoftMax |
| Elsayed et al. [56] | 2 Conv, 2 MaxPool, 1 Dropout, 1 LSTM, 1 FC | 2D (8 × 6) | CNN, LSTM | SoftMax |
| Wei et al. [57] | 1 Conv, 1 BatchNo, 1MaxPool, 2 Dropout, 1 LSTM, 1 Flatten, 2 FC | 1D (128) | CNN, LSTM | SoftMax |
| Xiuzhang et al. [58] | 1 Conv, 1 MaxPool, 1 BiLSTM, 1 Attention, 1 FC | 2D | CNN-BiLSTM + knowledge graph | LSTM+SoftMax |
| Jiyuan et al. [59] | 2 Conv, 2 LSTM, 1 FCC | 2D | stacked autoencoder | CNN-LSTM |
| Elsayed et al. [60] | 1 BatchNo, 1 AvgPool, 2 BilSTM, 1 Conv, 1 Flatten, 2 FC | 1D (128) | BiLSTM, CNN | SoftMax |
| Rajesh et al. [61] | 3 Conv, 2 FC | 2D (512 × 521) | HMLSTM, CNN | SoftMax |
| Azizjon et al. [62] | 2 Conv, 2 MaxPool, 1 Dropout, 1 BatchNo, 1 LSTM, 1 Flatten, 2 FC | 1D (41) | CNN, LSTM | SoftMax |
| Authors | Year | ENV | Datasets | Binary Accuracy (%) | Multiclass Accuracy (%) | Evaluation Metrics |
|---|---|---|---|---|---|---|
| Zhang et al. [15] | 2020 | KT | UNSW-NB15 CIC-IDS2017 | 99.74 96.54 | 96.54 99.85 | ACC, PPV, TPR, F1 Score, FPR, TPR |
| Min et al. [63] | 2018 | P | ISCX2012 | 99.13 | --- | ACC, TPR, FPR |
| Zhang et al. [64] | 2021 | T | NSL-KDD UNSW-NB15 | 99.50 99.40 | --- --- | ACC, FPR, FNR |
| Yongi et al. [65] | 2019 | KT | KDD Cup99 | 94.11 | --- | ACC, FPR, TPR |
| Yu et al. [66] | 2021 | T | CIC-IDS2017 CSE-CIC-IDS2018 | 84.35 99.90 | --- --- | PPV, TPRF1 Score, ACC, Time |
| Xiao et al. [69] | 2019 | KT | KDD Cup99 | 94.00 | --- | ACC, FPR, TPR, Time |
| Wang et al. [67] | 2021 | KT | CICDDoS2019 | 99.82 | --- | ACC, PPV, TPR, F1 Score |
| Yin et al. [68] | 2021 | --- | NSL-KDD CIC-IDS2017 | --- --- | 99.78 99.87 | ACC, PPV, TPR, F Score, FPR |
| Authors | Architecture | Input Shape | Feature Extraction | Classifier |
|---|---|---|---|---|
| Zhang et al. [15] | 4 Conv,2 MaxPool, 1 FC | 1D | CNN, DAE | SoftMax |
| Min et al. [63] | 2 Cov, 2MaxPool, 1 FC | 1D | CNN | RF |
| Zhang et al. [64] | 2 Conv, 2 MaxPool | 2D (11 × 11), 2D (38 × 38) | CNN | SoftMax, GoogLeNet |
| Yongi et al. [65] | 2 Inception, 2 Conv, 2 MaxPool, 1 FC | 2D (11 × 11) | CNN | SoftMax |
| Yu et al. [66] | 6 Conv, 3 MaxPool, 1 flatten, 2 FC | 2D (256 × 256) | CNN | SoftMax |
| Xiao et al. [69] | 2 Conv, 2 MaxPool, 2 FC | 2D (10 × 10) | CNN, PCA, AE | SoftMax |
| Wang et al. [67] | 1 Transformer, 1 Conv, 1 MaxPool, 1 GAP, 3 FC | 2D | Transformer, CNN | FC (Sigmoid) |
| Yin et al. [68] | --- | 2D | Attention, CNN | Capsule, SoftMax |
| Authors | Year | ENV | Datasets | Binary Accuracy (%) | Multiclass Accuracy (%) | Evaluation Metrics |
|---|---|---|---|---|---|---|
| Nguyen et al. [3] | 2020 | M | NSL-KDD | 98.24 | 98.20 | ACC, TPR, FPR |
| Moustakidi et al. [70] | 2020 | M | NSL-KDD | 86.64 | --- | ACC |
| Mendonca et al. [71] | 2021 | W, T | CIC-IDS2017 | 98.00 | --- | ACC, PPV, TPR, F1 Score |
| Liu et al. [72] | 2018 | T | KDD Cup99 | 96.38 | --- | ACC, FNR |
| Khan et al. [73] | 2021 | M | CIC-IDS2017 | 99.35 | 98.76 | ACC, PPV, TPR, F1 Score, FPR, TNR |
| Chen et al. [74] | 2020 | --- | KDD Cup99 | 91.6 | --- | ACC, FPR, PPV, TNR, FNR |
| Zhang et al. [75] | 2020 | --- | NSL-KDD UNSW-NB15 | 99.39 98.68 | 99.02 94.76 | TPR, FPR, ACC |
| Abdelghani et al. [76] | 2022 | P | KDD Cup99 NSL-KDD CIC-IDS2017 BoT-IoT | 92.34 77.81 99.99 99.993 | 92.04 76.11 99.02 99.91 | ACC, PPV, TPR, F1 Score |
| Avijit et al. [77] | 2021 | --- | KDD Cup99 | 95.28 | --- | ACC, PPV, TPR, F1 Score, Time |
| Mohd et al. [78] | 2022 | KT | NSL-KDD | 99.34 | 99.13 | ACC, F1 Score |
| Authors | Architecture | Input Shape | Feature Extraction | Classifier |
|---|---|---|---|---|
| Nguyen et al. [3] | 5 Conv, 1 MaxPool, 1 FC | 2D | GA, KNN, FCM, CNN | BG classifier |
| Moustakidi et al. [70] | 1 Conv, 4 FC | 2D (7 × 7) | Deep Siamese CNN | AdaBoost |
| Mendonca et al. [71] | 4 Conv,1 FC | 2D | CNN | SoftMax |
| Liu et al. [72] | 1 Conv, 1 MaxPool, 2 FC | 2D (6 × 7) | K-means, PCA, CNN | FC, SoftMax |
| Khan et al. [73] | 2 Conv, 2 MaxPool, 1 Flatten, 2 FC | 2D (28 × 28 × 3) | CNN | FC, SoftMax |
| Chen et al. [74] | 1 Conv, 1 FC | 2D (11 × 11) | CNN+SVDD | One-class |
| Zhang et al. [75] | 2 Conv, 2 MaxPool, 1 FC | 2D | CNN, FC | Ensemble |
| Abdelghani et al. [76] | 2 Conv, 2 MaxPool, 2 Dropout, 3 FC, 1 Batch No | 1D | RSA, CNN | SoftMax |
| Avijit et al. [77] | --- | --- | GLCM, fuzzy K-means, CNN | SoftMax |
| Mohd et al. [78] | 2 Conv 2 BatchNo, 2 MaxPool, 3 Dropout, 1 Flatten, 2 FC | 1D | PCA, CNN | SoftMax |
| Model Type | Num. of CNN Layers | Num. of Trainable Params | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) | False Alarm (%) |
|---|---|---|---|---|---|---|---|
| Basic 1D-CNN | 1 | 254,721 | 97.99 | 89.54 | 99.75 | 94.37 | 2.37 |
| 2 | 156,609 | 98.08 | 92.48 | 96.51 | 94.45 | 1.6 | |
| 3 | 119,937 | 97.66 | 88.38 | 99.2 | 93.48 | 2.65 | |
| Basic 2D-CNN | 1 | 152,513 | 98.1 | 91.3 | 98.09 | 94.58 | 1.9 |
| 2 | 78,977 | 97.61 | 91.92 | 94.14 | 93.01 | 1.68 | |
| 3 | 95,553 | 97.74 | 88.64 | 99.37 | 93.7 | 2.59 | |
| Hybrid LSTM with 1D-CNN | 2 | 76,101 | 98.02 | 90.38 | 98.81 | 94.41 | 2.14 |
| Hybrid LSTM with 2D-CNN | 2 | 59,850 | 97.55 | 87.65 | 99.54 | 93.21 | 2.85 |
| Hybrid Autoencoder with CNN | 2 | 133,285 | 95.24 | 90.76 | 79.97 | 85.02 | 1.66 |
| Model Type | Num. of CNN Layers | Num. of Trainable Params | Accuracy (%) | Precision (%) | Recall (%) | F1 Score (%) | False Alarm (%) |
|---|---|---|---|---|---|---|---|
| Basic 1D-CNN | 1 | 258,817 | 82.67 | 92.62 | 75.58 | 83.23 | 7.96 |
| 2 | 156,609 | 84.9 | 93.34 | 79.13 | 85.65 | 7.47 | |
| 3 | 119,937 | 88.87 | 94.93 | 84.98 | 89.68 | 5.99 | |
| Basic 2D-CNN | 1 | 152,513 | 85.22 | 93.35 | 79.71 | 85.99 | 7.51 |
| 2 | 78,977 | 85.59 | 97.18 | 76.92 | 85.87 | 2.95 | |
| 3 | 95,553 | 84.43 | 93.48 | 78.09 | 85.09 | 7.2 | |
| Hybrid LSTM with 1D-CNN | 2 | 76,101 | 89.93 | 95.47 | 86.42 | 90.72 | 5.42 |
| Hybrid LSTM with 2D-CNN | 2 | 59,850 | 82.05 | 93.02 | 74.03 | 82.44 | 7.34 |
| Hybrid Autoencoder with CNN | 2 | 134,673 | 84.39 | 93.35 | 78.13 | 85.07 | 7.35 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mohammadpour, L.; Ling, T.C.; Liew, C.S.; Aryanfar, A. A Survey of CNN-Based Network Intrusion Detection. Appl. Sci. 2022, 12, 8162. https://doi.org/10.3390/app12168162
Mohammadpour L, Ling TC, Liew CS, Aryanfar A. A Survey of CNN-Based Network Intrusion Detection. Applied Sciences. 2022; 12(16):8162. https://doi.org/10.3390/app12168162
Chicago/Turabian StyleMohammadpour, Leila, Teck Chaw Ling, Chee Sun Liew, and Alihossein Aryanfar. 2022. "A Survey of CNN-Based Network Intrusion Detection" Applied Sciences 12, no. 16: 8162. https://doi.org/10.3390/app12168162
APA StyleMohammadpour, L., Ling, T. C., Liew, C. S., & Aryanfar, A. (2022). A Survey of CNN-Based Network Intrusion Detection. Applied Sciences, 12(16), 8162. https://doi.org/10.3390/app12168162