SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory
Abstract
:1. Introduction
- We present an ROP attack that implements loops inside the attack payload to leak enclave data. Our ROP attack utilizes page table entries’ access bits so that the PAM can retrieve the enclave’s memory.
- We give a real example of ROP code for attacking SGX. Unlike the usual ROP codes that simply call a specific function with designated parameters, SGXDump walks through the entire memory while accessing the probe array. We demonstrate how to build ROP code for implementing loops with limited gadgets. This will be useful for many researchers who want to devise ROP attacks on SGX.
- We demonstrate successful ROP attacks that could lead to a leak of the entire memory by using SGXDump and PAM to attack two well-known SGX open source projects: mbedTLS-SGX and Graphene-SGX. While mbedTLS-SGX is a very useful tool for SGX applications that need to use an SSL library for secure communication [24]. Graphene-SGX is a tool for running unmodified code on SGX [25]. Therefore, any vulnerable code found in either of these projects could be serious threats for SGX service owners and users.
2. Background
3. Threat Model
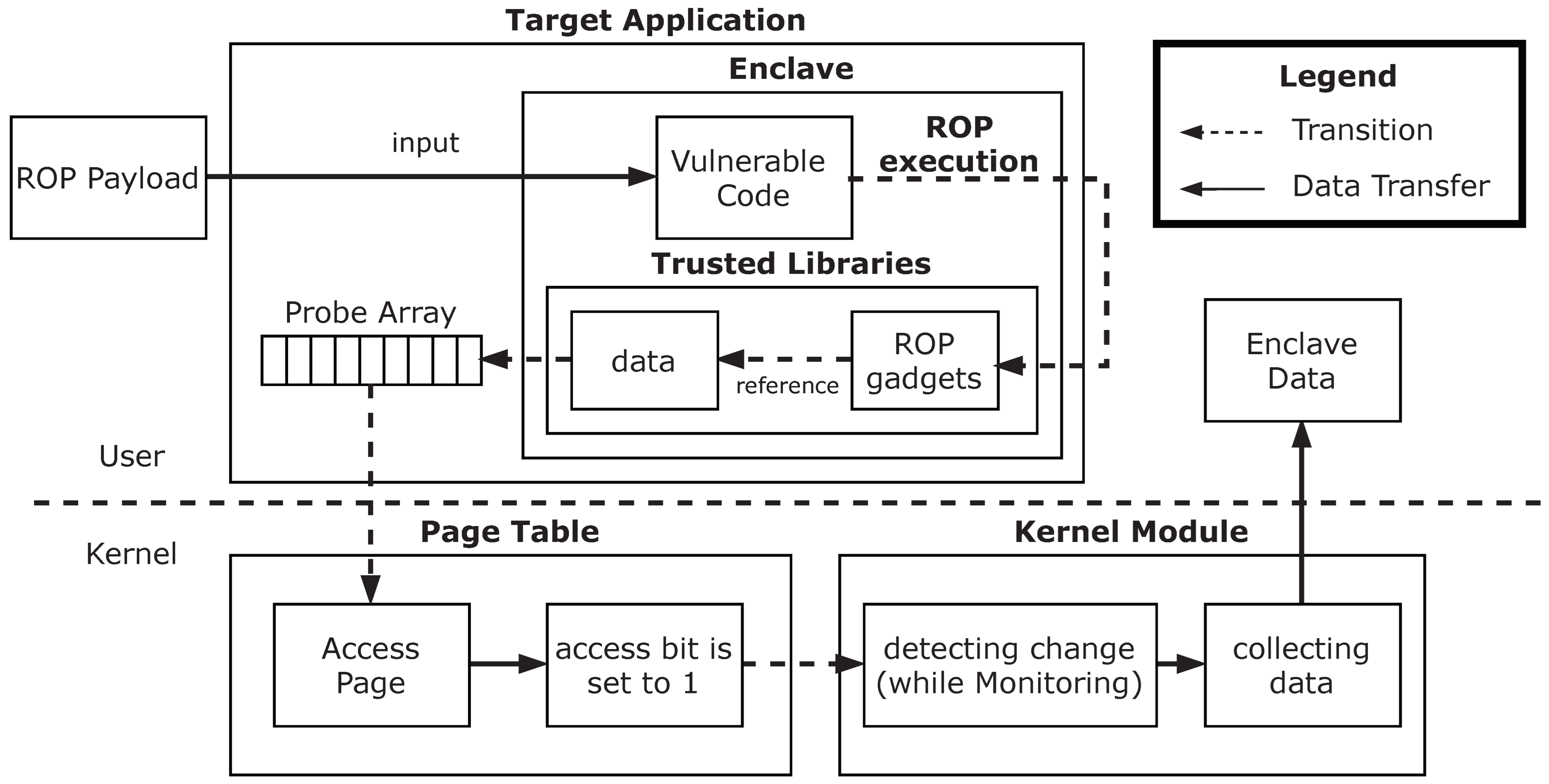
4. SGXDump Attack Overview
4.1. SGXDump
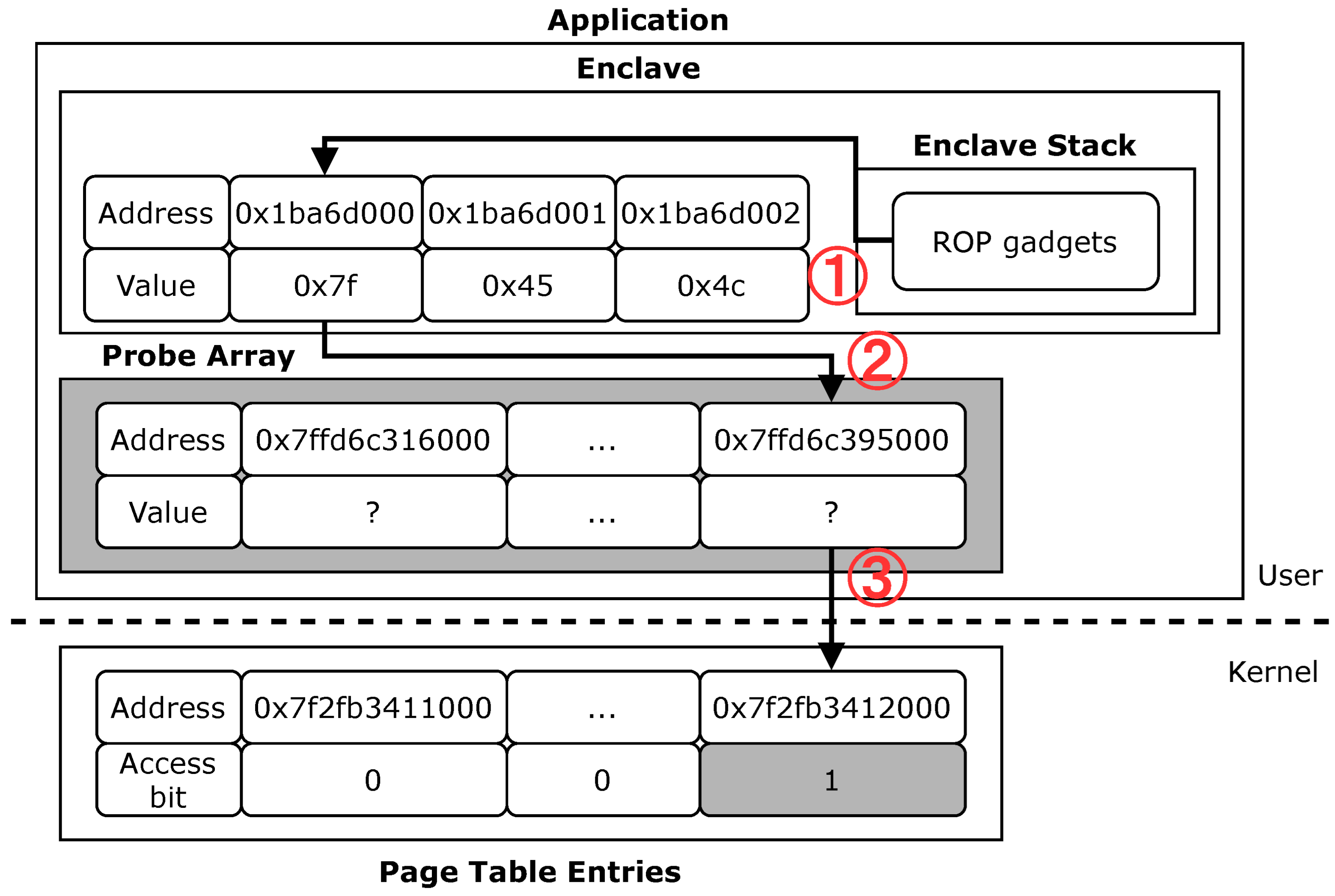
4.2. Probe Array Monitoring
5. Attack Design
5.1. Choosing the Probe Array
- Mapped memory area. If an unmapped memory area is chosen as the probe array, unnecessary exceptions will occur whenever the ROP accesses the probe array. To avoid this situation, we select a mapped memory area for the probe array.
- No access by other threads. Our main idea is to detect the access bit of the probe array by executing ROP gadgets. If other threads access the probe array, this access will cause unwanted noise. Therefore, we choose a memory area that is not accessed by other threads.
- Memory area outside of the Enclave. Since SGXDump will read through all the enclave memory, access bits of the memory will change as a consequence. To avoid undesirable noise on the access bits, it is necessary to pick a memory area outside of the enclave.
5.2. Finding Gadgets for the ROP Payload
5.3. SGXDump ROP Payload Structure
| Algorithm 1 Flow of ROP payload. |
|
- Step 1. Calculating sync address. The ROP payload initializes several registers to avoid unpredictable behaviors. After reading the value at the sync address, SGXDump uses the value as a sign to access the next data or to jump back to check the sync address for busy waiting.
- Step 2. Getting protected data. At this stage, the ROP retrieves two values from the index address and the target address and adds the two values to calculate the next address in enclave memory. Then, the ROP reads one byte from the address and stores it in a register temporarily.
- Step 3. Shifting protected data and accessing probe array. The ROP payload leftshifts the data 12 times, multiplying by 4096, and uses the resulting value as an index to access the probe array.
- Step 4. Looping. Before looping back to Step 1, the ROP payload increments the content at the index address and writes an offset value at the sync address to make Step 1 perform a busy waiting.
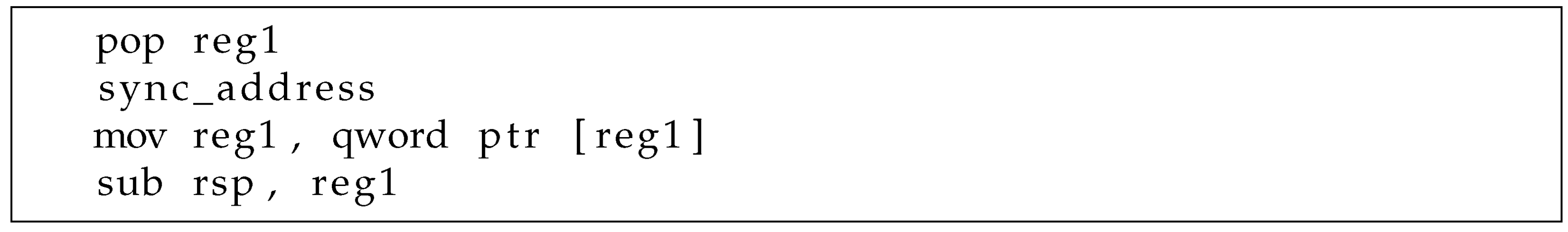

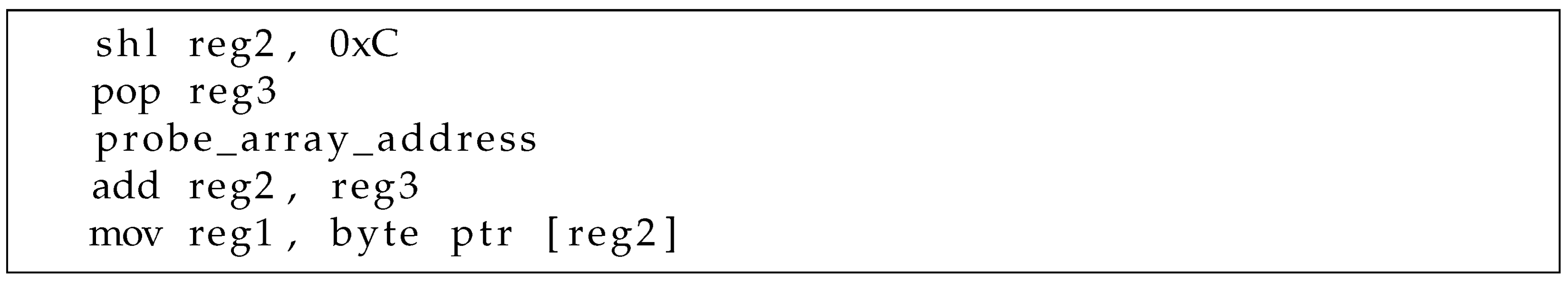

5.4. Synchronization and Data Leak via PAM
| Algorithm 2 Flow of Kernel module. |
|
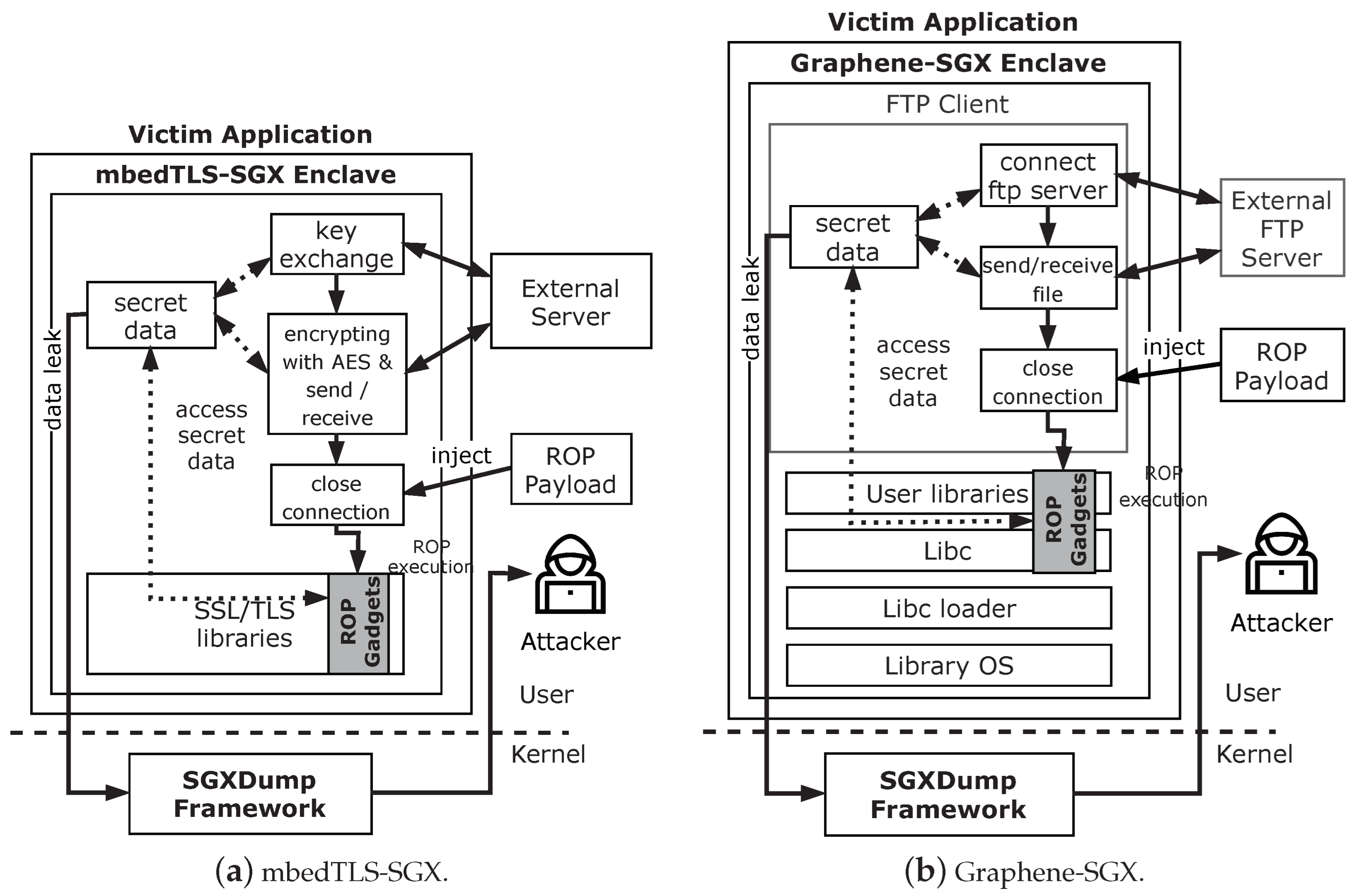
6. Implementation
6.1. mbedTLS-SGX
6.2. Graphene-SGX
6.3. Evaluation
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Gadget List in Open Source Project
| Gadgets | Offset |
|---|---|
| add bl, byte ptr [rcx]; lfence; call rax | 0x1b440b |
| add rcx, rdi; mov rdi, rcx; call rax | 0x28ab7f |
| inc dword ptr [rdx]; ret | 0xa6970e |
| mov qword ptr [rax], rdx; ret | 0x828401 |
| mov rax, qword ptr [rax]; ret | 0x828392 |
| mov rax, rdi; ret | 0x7e4d50 |
| mov rdi, qword ptr [rax]; lfence; call rbx | 0x67fb63 |
| mov rdi, rax; call rbx | 0x050b50 |
| nop; ret | 0x009b68 |
| pop rax; ret | 0x009ac0 |
| pop rbx; ret | 0x404ddc |
| pop rcx; ret | 0x075bdd |
| pop rdi; ret | 0x20d413 |
| pop rdx; ret | 0x07735c |
| pop rsp; ret | 0x40da1d |
| sal ebx, cl; ret | 0x2e8e39 |
| sub esp, dword ptr [rdx − 0x76b80000]; ret | 0x7b6eef |
| Gadgets | Offset |
|---|---|
| add al, byte ptr [rax]; add byte ptr [rbx + 0x5d], bl; ret | 0x036de3 |
| add rax, qword ptr [rcx − 0x77]; retf | 0x139285 |
| inc dword ptr [rcx − 0x77]; ret | 0x027143 |
| jmp rax | 0x027f2b |
| mov dword ptr [rdi + rdx − 0x27], eax; mov rax, rdi; ret | 0x0b4310 |
| mov eax, edi; ret | 0x0b4315 |
| mov qword ptr [rax], rdx; ret | 0x828401 |
| mov rdi, qword ptr [rax]; lfence; call rbx | 0x67fb63 |
| nop; ret | 0x009b68 |
| pop rax; ret | 0x108665 |
| pop rax; ret | 0x009ac0 |
| pop rbx; ret | 0x03475d |
| pop rcx; or eax, dword ptr [rax]; leave; ret | 0x0136eb |
| pop rdi; ret | 0x034401 |
| pop rdx; add byte ptr [rdx], cl; add cl, cl; ret | 0x028fd2 |
| pop rsp; ret | 0x40da1d |
| shl edi, cl; add byte ptr [rax], al; lfence; call rax | 0x3ea393 |
| sub rax, rcx; ret | 0x1bda72 |
References
- Pearson, S.; Balacheff, B. Trusted Computing Platforms: TCPA Technology in Context; Prentice Hall Professional: Hoboken, NJ, USA, 2003. [Google Scholar]
- Mitchell, C. Trusted Computing; LET: London, UK, 2005; Volume 6. [Google Scholar]
- Holdings, A. ARM Security Technology: Building a Secure System Using TrustZone Technology; ARM Ltd.: Cambridge, UK, 2009. [Google Scholar]
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. Hasp@ isca 2013, 10, 1–8. [Google Scholar]
- Costan, V.; Devadas, S. Intel SGX Explained. 2016. Available online: https://eprint.iacr.org/2016/086 (accessed on 12 July 2022).
- Intel(R) Software Guard Extensions (Intel(R) SGX) SDK for Linux OS. 2020. Available online: https://github.com/intel/linux-sgx (accessed on 12 July 2022).
- Brasser, F.; Müller, U.; Dmitrienko, A.; Kostiainen, K.; Capkun, S.; Sadeghi, A.R. Software grand exposure: SGX cache attacks are practical. In Proceedings of the 11th USENIX Workshop on Offensive Technologies (WOOT 17), Vancouver, BC, Canada, 14–15 August 2017. [Google Scholar]
- Götzfried, J.; Eckert, M.; Schinzel, S.; Müller, T. Cache attacks on Intel SGX. In Proceedings of the 10th European Workshop on Systems Security, Belgrade, Serbia, 23 April 2017; pp. 1–6. [Google Scholar]
- Moghimi, D.; Van Bulck, J.; Heninger, N.; Piessens, F.; Sunar, B. CopyCat: Controlled Instruction-Level Attacks on Enclaves. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Washington, DC, USA, 12–14 August 2020; pp. 469–486. [Google Scholar]
- Van Bulck, J.; Minkin, M.; Weisse, O.; Genkin, D.; Kasikci, B.; Piessens, F.; Silberstein, M.; Wenisch, T.F.; Yarom, Y.; Strackx, R. Foreshadow: Extracting the keys to the intel SGX kingdom with transient out-of-order execution. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 991–1008. [Google Scholar]
- Aldaya, A.C.; Brumley, B.B. When one vulnerable primitive turns viral: Novel single-trace attacks on ECDSA and RSA. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2020, 2020, 196–221. [Google Scholar] [CrossRef]
- Weiser, S.; Spreitzer, R.; Bodner, L. Single trace attack against RSA key generation in Intel SGX SSL. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security, Incheon, Korea, 4–8 June 2018; pp. 575–586. [Google Scholar]
- Van Bulck, J.; Piessens, F.; Strackx, R. SGX-Step: A practical attack framework for precise enclave execution control. In Proceedings of the 2nd Workshop on System Software for Trusted Execution, Shanghai, China, 28 October 2017; pp. 1–6. [Google Scholar]
- Lee, J.; Jang, J.; Jang, Y.; Kwak, N.; Choi, Y.; Choi, C.; Kim, T.; Peinado, M.; Kang, B.B. Hacking in darkness: Return-oriented programming against secure enclaves. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 523–539. [Google Scholar]
- Roemer, R.; Buchanan, E.; Shacham, H.; Savage, S. Return-oriented programming: Systems, languages, and applications. ACM Trans. Inf. Syst. Secur. 2012, 15, 1–34. [Google Scholar] [CrossRef]
- Checkoway, S.; Davi, L.; Dmitrienko, A.; Sadeghi, A.R.; Shacham, H.; Winandy, M. Return-oriented programming without returns. In Proceedings of the 17th ACM Conference On Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 559–572. [Google Scholar]
- Bletsch, T.; Jiang, X.; Freeh, V.W.; Liang, Z. Jump-oriented programming: A new class of code-reuse attack. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, 22–24 March 2011; pp. 30–40. [Google Scholar]
- Mabon, R. Sigreturn oriented programming is a real threat. In Informatik 2016; Lecture Notes in Informatics (LNI); Gesellschaft fr Informatik: Bonn, Germany, 2016. [Google Scholar]
- Bittau, A.; Belay, A.; Mashtizadeh, A.; Mazières, D.; Boneh, D. Hacking blind. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Washington, DC, USA, 18–21 May 2014; pp. 227–242. [Google Scholar]
- Schwarz, M.; Weiser, S.; Gruss, D. Practical enclave malware with Intel SGX. In International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment; Springer: Berlin/Heidelberg, Germany, 2019; pp. 177–196. [Google Scholar]
- Biondo, A.; Conti, M.; Davi, L.; Frassetto, T.; Sadeghi, A.R. The Guard’s Dilemma: Efficient {Code-Reuse} Attacks Against Intel {SGX}. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 1213–1227. [Google Scholar]
- Toffalini, F.; Graziano, M.; Conti, M.; Zhou, J. SnakeGX: A sneaky attack against SGX Enclaves. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 333–362. [Google Scholar]
- Cui, J.; Yu, J.Z.; Shinde, S.; Saxena, P.; Cai, Z. SmashEx: Smashing SGX Enclaves Using Exceptions. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, 15–19 November 2021; pp. 779–793. [Google Scholar]
- Aublin, P.L.; Kelbert, F.; O’keeffe, D.; Muthukumaran, D.; Priebe, C.; Lind, J.; Krahn, R.; Fetzer, C.; Eyers, D.; Pietzuch, P. TaLoS: Secure and Transparent TLS Termination inside SGX Enclaves. 2017. Available online: https://www.researchgate.net/publication/315715902_TaLoS_Secure_and_Transparent_TLS_Termination_inside_SGX_Enclaves (accessed on 12 July 2022).
- Tsai, C.C.; Porter, D.E.; Vij, M. Graphene-sgx: A practical library OS for unmodified applications on SGX. In Proceedings of the 2017 USENIX Annual Technical Conference (USENIX ATC 17), Santa Clara, CA, USA, 4 May 2017; pp. 645–658. [Google Scholar]
- Team, P. PaX Address Space Layout Randomization. Available online: http://pax.grsecurity.net/docs/aslr.txt (accessed on 12 July 2022).
- Seo, J.; Lee, B.; Kim, S.M.; Shih, M.W.; Shin, I.; Han, D.; Kim, T. SGX-Shield: Enabling Address Space Layout Randomization for SGX Programs; NDSS: New York, NY, USA, 2017. [Google Scholar]
- Talluri, M.; Hill, M.D.; Khalidi, Y.A. A new page table for 64-bit address spaces. In Proceedings of the Fifteenth ACM Symposium on Operating Systems Principles, Copper Mountain, CO, USA, 3–6 December 1995; pp. 184–200. [Google Scholar]
- Arpaci-Dusseau, R.H.; Arpaci-Dusseau, A.C. Operating Systems: Three Easy Pieces; Arpaci-Dusseau Books LLC.: Boston, MA, USA, 2018. [Google Scholar]
- Zheng, W.; Wu, Y.; Wu, X.; Feng, C.; Sui, Y.; Luo, X.; Zhou, Y. A survey of Intel SGX and its applications. Front. Comput. Sci. 2021, 15, 153808. [Google Scholar] [CrossRef]
- JonathanSalwan. ROPgadget. 2021. Available online: https://github.com/JonathanSalwan/ROPgadget (accessed on 12 July 2022).
- Google. Asylo: An Open and Flexible Framework for Enclave Applications. Available online: https://asylo.dev/ (accessed on 12 July 2022).
- deislabs. Mystikos. 2021. Available online: https://github.com/deislabs/mystikos (accessed on 12 July 2022).
- Bowden, T.; Bauer, B.; Nerin, J.; Feng, S.; Seibold, S. The/proc filesystem. Linux Kernel Documentation 2000.
- Schwarz, M. PTEditor. 2021. Available online: https://github.com/misc0110/PTEditor (accessed on 12 July 2022).
- Moghimi, A.; Wichelmann, J.; Eisenbarth, T.; Sunar, B. MemJam: A False Dependency Attack Against Constant-Time Crypto Implementations. Int. J. Parallel Program. 2019, 47, 538–570. [Google Scholar] [CrossRef] [Green Version]
- Gyselinck, J.; Bulck, J.V.; Piessens, F.; Strackx, R. Off-Limits: Abusing Legacy X86 Memory Segmentation to Spy on Enclaved Execution; Springer: Berlin/Heidelberg, Germany, 2018; Volume 10953, pp. 44–60. [Google Scholar]
- Evtyushkin, D.; Riley, R.; Abu-Ghazaleh, N.; Ponomarev, D. Branchscope: A new side-channel attack on directional branch predictor. ACM Sigplan Not. 2018, 53, 693–707. [Google Scholar] [CrossRef]
- Huo, T.; Meng, X.; Wang, W.; Hao, C.; Zhao, P.; Zhai, J.; Li, M. Bluethunder: A 2-level Directional Predictor Based Side-Channel Attack against SGX. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2020, 321–347. [Google Scholar] [CrossRef]
- Lee, S.; Shih, M.W.; Gera, P.; Kim, T.; Kim, H.; Peinado, M. Inferring fine-grained control flow inside SGX enclaves with branch shadowing. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 557–574. [Google Scholar]
- Skarlatos, D.; Yan, M.; Gopireddy, B.; Sprabery, R.; Torrellas, J.; Fletcher, C.W. MicroScope: Enabling Microarchitectural Replay Attacks. In Proceedings of the 46th International Symposium on Computer Architecture, Phoenix, AZ, USA, 22–26 June 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 318–331. [Google Scholar] [CrossRef]
- Xiao, Y.; Li, M.; Chen, S.; Zhang, Y. STACCO: Differentially Analyzing Side-Channel Traces for Detecting SSL/TLS Vulnerabilities in Secure Enclaves. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 859–874. [Google Scholar] [CrossRef] [Green Version]
- Bulck, J.V.; Piessens, F.; Strackx, R. Nemesis: Studying Microarchitectural Timing Leaks in Rudimentary CPU Interrupt Logic. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 178–195. [Google Scholar] [CrossRef]
- Intel. Intel Analysis of Speculative Execution Side Channels. 2018. Available online: https://newsroom.intel.com/wp-content/uploads/sites/11/2018/01/Intel-Analysis-of-Speculative-Execution-Side-Channels.pdf (accessed on 12 July 2022).
- Weichbrodt, N.; Kurmus, A.; Pietzuch, P.; Kapitza, R. AsyncShock: Exploiting Synchronisation Bugs in Intel SGX Enclaves. In Proceedings of the Computer Security—ESORICS 2016, Heraklion, Greece, 26–30 September 2016; Askoxylakis, I., Ioannidis, S., Katsikas, S., Meadows, C., Eds.; Springer: Cham, Switzerland, 2016; pp. 440–457. [Google Scholar]


| Gadgets | Function | Offset |
|---|---|---|
| adc ecx, dword ptr [rax − 0x7d]; ret; | init_global_object | 0x19be1 |
| add cl, byte ptr [rax − 0x7d]; ret; | __vfprintf | 0x80f92 |
| add eax, ecx; ret; | get_dynamic_layout_by_idt | 0x17388 |
| add rax, rcx; ret; | get_dynamic_layout_by_idt | 0x17387 |
| inc dword ptr [rcx + 1]; ret; | __strtodg | 0xa4a37 |
| mov eax, dword ptr [rax + 8]; ret; | get_enclave_size | 0x18778 |
| mov qword ptr [rdi + 0x10], 0; ret; | typedef basic_string | 0x9228f |
| mov qword ptr [rdi], rax; ret; | _exception | 0x91467 |
| mov qword ptr [rdx], rax; xor eax, eax; ret; | elf_tls_info | 0x195d3 |
| mov rdi, qword ptr [rdi + 0x68]; ret; | _Ux86_64_setcontext | 0x9ccbe |
| nop; ret; | free | 0x861ef |
| pop rax; ret; | _ULx86_64_r_uc_addr | 0x9c4a3 |
| pop rcx; ret; | __dtoa | 0x8842d |
| pop rdi; ret; | __find_arguments | 0x0ec67 |
| pop rdx; pop rcx; pop rbx; ret; | do_egetkey | 0xa8a33 |
| pop rsp; ret; | _trts_ecall | 0x17d84 |
| shl eax, 0xc; ret; | get_heap_min_size | 0x18888 |
| sub rax, 1; ret; | _ZNKSt3__112basic_... | 0x92831 |
| sub rsp, rdi; mov rax, rsp; jmp rdx; | alloca | 0x7f3ac |
| Gadgets | Function | Offset |
|---|---|---|
| add cl, byte ptr [rax − 0x77]; ret; | _IO_wstr_seekoff | 0x77fb1 |
| add eax, ecx; ret; | _fitoa_word | 0x4f2cd |
| add ecx, dword ptr [rax + 0x29]; ret; | _int_free | 0x85521 |
| add rax, rcx; ret; | __memchr_sse2 | 0x963a8 |
| add rax, rsi; ret; | __memrchr_sse2 | 0x96bcc |
| mov qword ptr [rdi + 8], rax; ret; | _IO_switch_to_main_get_area | 0x806b6 |
| mov qword ptr [rdx], rax; ret; | __GI___ctype_init | 0x32c4c |
| mov rax, qword ptr [rax]; ret; | __GI___res_state | 0x11a258 |
| movzx eax, byte ptr [rax]; ret; | __getc_unlocked | 0x7d352 |
| pop rax; ret; | mblen | 0x3cdb8 |
| pop rcx; pop rbx; ret; | _getopt_internal | 0xe2bea |
| pop rdi; ret; | init_cacheinfo | 0x25522 |
| pop rsi; ret; | strip | 0x25e42 |
| pop rsp; ret; | check_one_fd | 0x25c1a |
| shl rsi, 4; lea rax, [rdi + rsi + 8]; ret; | inet6_rth_getaddr | 0x11654b |
| sub esp, edi; dec dword ptr [rax + 0x39]; ret; | __tzfile_read | 0xbac9d |
| xchg eax, edi; ret; | strfromd | 0x3ff8e |
| xchg eax, esi; ret; | check_node_accept | 0xd65d9 |
| Attacks | Type | Victim | Bit per Sec | Number of Attempts | Noise |
|---|---|---|---|---|---|
| MemJam [36] | -arch contention | Data | 0.42 | 2,000,000 | Yes |
| CopyCat [9] | Ctrl channel | Control flow | 102 | 39,400 | Yes |
| SGXDump (mbedTLS-SGX) | Ctrl channel | Code and data | 2730 | 1 | No |
| SGXDump (Graphene-SGX) | Ctrl channel | Code and data | 682 | 1 | No |
| Attacks | Victim | Data Acquisition Channel | Noise | Root Privilege | Granularity | Attack Precondition |
|---|---|---|---|---|---|---|
| SGXDump | Code and data | PTE’s access bit | No | Yes | 1 Byte | Binary code, overflow vulnerabilities |
| Foreshadow | Code and data | PTE’s present bit, Cache timing | Yes | No (mprotect) | 1 Byte | Secrets in the L1 cache |
| CopyCat | Control flow | APIC timer manipulation, the number of executed instruction | Yes | Yes (Loadable kernel module for APIC event call back) | Instruction | (Compiled) source code |
| Nemesis | Control flow | APIC timer manipulation, Interrupt latency | Yes | Yes | Instruction within one cache line | (Compiled) source code |
| MemJam | Data | 4K Aliasing, False dependency of memory read-after-write event, Cache line timing | Yes | Yes | Word or cache line | Virtual memory offset of critical data |
| Single Trace | RSA key generation code | PTE’s present bit | No | Yes (SGX-Step) | Page | (Compiled) source code |
| Off-Limits | Control flow, one instruction | Segmentation and paging | No | Yes | Page | (Compiled) source code, only 32-bit mode |
| BranchScope | Control flow | Pattern history table | Yes | Yes | Instruction | Virtual address of victim’s code |
| Bluethunder | Control flow | Global history register | Yes | Yes | Instruction | (Compiled) source code |
| Branch shadowing | Control flow | Branch prediction | Yes (Unconditional) No (Conditional and indirect) | Yes | Instruction | (Compiled) source code |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yoon, H.; Lee, M. SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory. Appl. Sci. 2022, 12, 7655. https://doi.org/10.3390/app12157655
Yoon H, Lee M. SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory. Applied Sciences. 2022; 12(15):7655. https://doi.org/10.3390/app12157655
Chicago/Turabian StyleYoon, HanJae, and ManHee Lee. 2022. "SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory" Applied Sciences 12, no. 15: 7655. https://doi.org/10.3390/app12157655
APA StyleYoon, H., & Lee, M. (2022). SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory. Applied Sciences, 12(15), 7655. https://doi.org/10.3390/app12157655






