Evaluation of a Framework for Robust Image Reversible Watermarking
Abstract
:1. Introduction
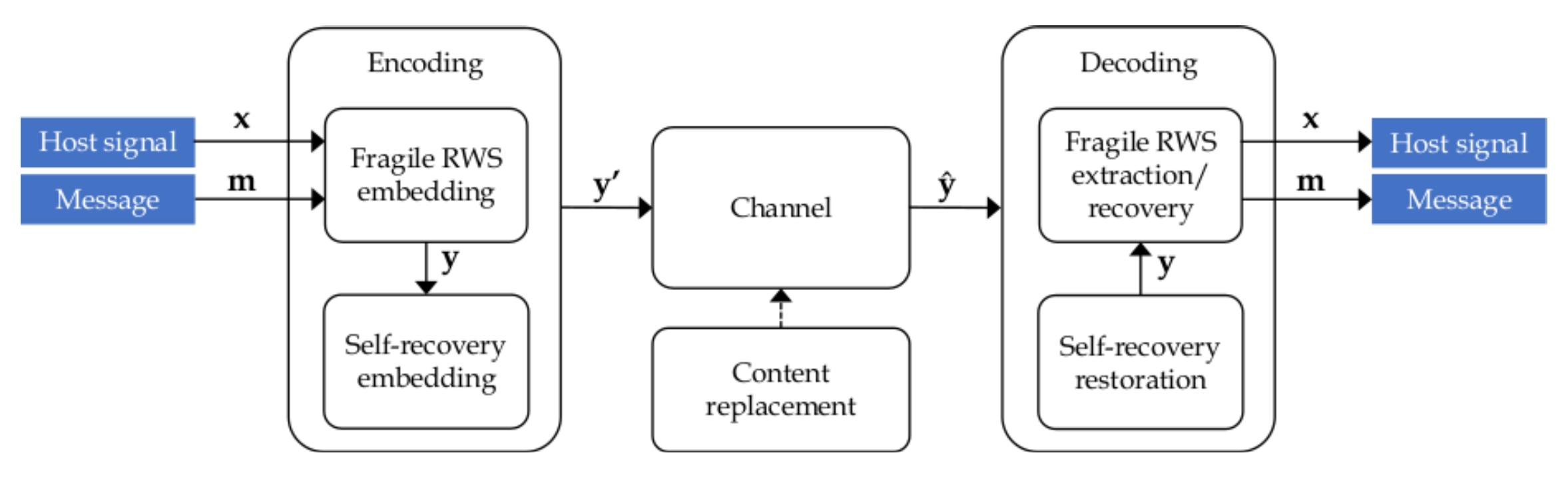
2. Evaluation of the Robust Framework for Robust Reversible Image Watermarking
2.1. Description of the Framework
2.2. Selection of Schemes
2.2.1. Fragile Reversible Watermarking Schemes
- If , there can be three cases:
- Case 1
- ; if 1 is inserted, the histogram from that block is shifted a distance k to the right; if a 0 is inserted, the block is left intact.
- Case 2
- ; if a 1 is inserted, the histogram from that block is shifted a distance to the right; if a 0 is inserted, the block is shifted a distance k to the right.
- Case 3
- ; if a 1 is inserted, the histogram from that block is shifted a distance to the right; if a 0 is inserted, the block is shifted a distance to the right.
- If , there can be three cases:
- Case 1
- ; if 1 is inserted, the histogram from that block is shifted a distance k to the left; if a 0 is inserted, the block is left intact.
- Case 2
- ; if a 1 is inserted, the histogram from that block is shifted a distance to the left; if a 0 is inserted, the block is shifted a distance k to the left.
- Case 3
- ; if a 1 is inserted, the histogram from that block is shifted a distance to the left; if a 0 is inserted, the block is shifted a distance to the left.
2.2.2. Self-Recovery Schemes
2.3. Perceptual Distortion Evaluation
3. Results and Discussions
3.1. Fragile Reversible Watermarking Schemes
3.2. Self-Recovery Schemes
3.3. Framework
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Menendez-Ortiz, A.; Feregrino-Uribe, C.; Hasimoto-Beltran, R.; Garcia-Hernandez, J.J. A Survey on Reversible Watermarking for Multimedia Content: A Robustness Overview. IEEE Access 2019, 7, 132662–132681. [Google Scholar] [CrossRef]
- An, L.; Gao, X.; Yuan, Y.; Tao, D.; Deng, C.; Ji, F. Content-adaptive reliable robust lossless data embedding. Neurocomputing 2012, 79, 1–11. [Google Scholar] [CrossRef]
- An, L.; Gao, X.; Yuan, Y.; Tao, D. Robust lossless data hiding using clustering and statistical quantity histogram. Neurocomputing 2012, 77, 1–11. [Google Scholar] [CrossRef]
- Yang, C.Y.; Lin, C.H.; Hu, W.C. Reversible Watermarking by Coefficient Adjustment Method. In Proceedings of the 2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Darmstadt, Germany, 15–17 October 2010; pp. 39–42. [Google Scholar] [CrossRef]
- Tsai, H.H.; Tseng, H.C.; Lai, Y.S. Robust lossless image watermarking based on α-trimmed mean algorithm and support vector machine. J. Syst. Softw. 2010, 83, 1015–1028. [Google Scholar] [CrossRef]
- An, L.; Gao, X.; Li, X.; Tao, D.; Deng, C.; Li, J. Robust reversible watermarking via clustering and enhanced pixel-wise masking. IEEE Trans. Image Process. 2012, 21, 3598–3611. [Google Scholar] [CrossRef] [PubMed]
- Dai, Z.; Lian, C.; He, Z.; Jiang, H.; Wang, Y. A Novel Hybrid Reversible-Zero Watermarking Scheme to Protect Medical Image. IEEE Access 2022, 10, 58005–58016. [Google Scholar] [CrossRef]
- Soualmi, A.; Alti, A.; Laouamer, L.; Benyoucef, M. A Blind Fragile Based Medical Image Authentication Using Schur Decomposition. In The International Conference on Advanced Machine Learning Technologies and Applications (AMLTA2019); Hassanien, A.E., Azar, A.T., Gaber, T., Bhatnagar, R., Tolba, M.F., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 623–632. [Google Scholar]
- Fridrich, J.; Goljan, M. Protection of digital images using self embedding. In Symposium on Content Security and Data Hiding in Digital Media; New Jersey Institute of Technology: Newark, NJ, USA, 1999. [Google Scholar]
- He, H.; Zhang, J.; Chen, F. A self-recovery fragile watermarking scheme for image authentication with superior localization. Sci. China Ser. F Inf. Sci. 2008, 51, 1487–1507. [Google Scholar] [CrossRef]
- He, H.J.; Zhang, J.S.; Tai, H.M. Self-recovery Fragile Watermarking Using Block-Neighborhood Tampering Characterization. In Information Hiding; Katzenbeisser, S., Sadeghi, A.R., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5806, pp. 132–145. [Google Scholar] [CrossRef]
- Bravo-Solorio, S.; Li, C.T.; Nandi, A. Watermarking with low embedding distortion and self-propagating restoration capabilities. In Proceedings of the 19th IEEE International Conference on Image Processing (ICIP), Orlando, FL, USA, 30 September–3 October 2012; pp. 2197–2200. [Google Scholar] [CrossRef]
- Aminuddin, A.; Ernawan, F. AuSR1: Authentication and self-recovery using a new image inpainting technique with LSB shifting in fragile image watermarking. J. King Saud Univ.-Comput. Inf. Sci. 2022; in press. [Google Scholar] [CrossRef]
- Wu, H.C.; Chang, C.C. Detection and restoration of tampered JPEG compressed images. J. Syst. Softw. 2002, 64, 151–161. [Google Scholar] [CrossRef]
- Zhang, X.; Qian, Z.; Ren, Y.; Feng, G. Watermarking With Flexible Self-Recovery Quality Based on Compressive Sensing and Compositive Reconstruction. IEEE Trans. Inf. Forensics Secur. 2011, 6, 1223–1232. [Google Scholar] [CrossRef]
- Li, C.; Wang, Y.; Ma, B.; Zhang, Z. A novel self-recovery fragile watermarking scheme based on dual-redundant-ring structure. Comput. Electr. Eng. 2011, 37, 927–940. [Google Scholar] [CrossRef]
- Hassan, A.M.; Al-Hamadi, A.; Hasan, Y.M.Y.; Wahab, M.A.A.; Michaelis, B. Secure Block-Based Video Authentication with Localization and Self-Recovery. World Acad. Sci. Eng. Technol. 2009, 2009, 69–74. [Google Scholar]
- Shi, Y.; Qi, M.; Lu, Y.; Kong, J.; Li, D. Object based self-embedding watermarking for video authentication. In Proceedings of the International Conference on Transportation, Mechanical, and Electrical Engineering (TMEE), Changchun, China, 16–18 December 2011; pp. 519–522. [Google Scholar] [CrossRef]
- Mobasseri, B. A spatial digital video watermark that survives MPEG. In Proceedings of the International Conference on Information Technology: Coding and Computing, Las Vegas, NV, USA, 27–29 March 2000; pp. 68–73. [Google Scholar] [CrossRef]
- Menendez-Ortiz, A.; Feregrino-Uribe, C.; Garcia-Hernandez, J.J. Reversible image watermarking scheme with perfect watermark and host restoration after a content replacement attack. In Proceedings of the The 2014 International Conference on Security and Management (SAM’14), Las Vegas, NV, USA, 7–9 April 2014; Volume 13, pp. 385–391. [Google Scholar]
- Coltuc, D. Towards distortion-free robust image authentication. J. Physics: Conf. Ser. 2007, 77, 012005. [Google Scholar] [CrossRef]
- Hu, R.; Xiang, S. Cover-Lossless Robust Image Watermarking Against Geometric Deformations. IEEE Trans. Image Process. 2021, 30, 318–331. [Google Scholar] [CrossRef] [PubMed]
- Huang, L.C.; Tseng, L.Y.; Hwang, M.S. A Reversible Data Hiding Method by Histogram Shifting in High Quality Medical Images. J. Syst. Softw. 2013, 86, 716–727. [Google Scholar] [CrossRef]
- Wang, Z.H.; Lee, C.F.; Chang, C.Y. Histogram-Shifting-Imitated Reversible Data Hiding. J. Syst. Softw. 2013, 86, 315–323. [Google Scholar] [CrossRef]
- Chakraborty, S.; Maji, P.; Pal, A.; Biswas, D.; Dey, N. Reversible Color Image Watermarking Using Trigonometric Functions. In Proceedings of the International Conference on Electronic Systems, Signal Processing and Computing Technologies (ICESC), Nagpur, India, 9–11 January 2014; pp. 105–110. [Google Scholar]
- Zhang, X.; Wang, S. Fragile Watermarking With Error-Free Restoration Capability. IEEE Trans. Multimed. 2008, 10, 1490–1499. [Google Scholar] [CrossRef]
- Bravo-Solorio, S.; Li, C.T.; Nandi, A. Watermarking method with exact self-propagating restoration capabilities. In Proceedings of the IEEE International Workshop on Information Forensics and Security (WIFS), Costa Adeje, Spain, 2–5 December 2012; pp. 217–222. [Google Scholar] [CrossRef]
- Hore, A.; Ziou, D. Image Quality Metrics: PSNR vs. SSIM. In Proceedings of the 20th International Conference on Pattern Recognition (ICPR), Istanbul, Turkey, 23–26 August 2010; pp. 2366–2369. [Google Scholar]
- Ismail Avcıbas, B.S. Statistical Analysis of Image Quality Measures; Technical Report; Department of Electrical and Electronic Engineering, Bogaziçi University: İstanbul, Turkey, 1999. [Google Scholar]
- Garcia-Hernandez, J.J.; Gomez-Flores, W.; Rubio-Loyola, J. Analysis of the impact of digital watermarking on computer-aided diagnosis in medical imaging. Comput. Biol. Med. 2016, 68, 37–48. [Google Scholar] [CrossRef] [PubMed]
- Watson, A.B. DCT quantization matrices visually optimized for individual images. In Human Vision, Visual Processing and Digital Display IV; SPIE: Bellingham, WA, USA, 1993; Volume 1913, pp. 202–216. [Google Scholar]
- Ahumada, A.J.; Peterson, H.A. Luminance-Model-Based DCT Quantization for Color Image Compression. In Human Vision, Visual Processing and Digital Display III; SPIE: Bellingham, WA, USA, 1992; Volume 1666, pp. 365–374. [Google Scholar]
- Rodriguez, T.F.; Cushman, D.A. Optimized Selection of Benchmark Test Parameters for Image Watermark Algorithms based on Taguchi Methods and Corresponding Influence on Design Decisions for Real-World. In SPIE-IS&T Electronic Imaging; SPIE: Bellingham, WA, USA, 2003; Volume 5020, pp. 215–228. [Google Scholar]
- Laboratory, W.V. Break Our Watermarking Systems 2, 2007. Image Data Set. Available online: http://bows2.ec-lille.fr (accessed on 13 June 2022).
- Coltuc, D.; Tudoroiu, A. Multibit versus Multilevel Embedding in High Capacity Difference Expansion Reversible Watermarking. In Proceedings of the 20th European Signal Processing Conference (EUSIPCO 2012), Bucharest, Romania, 27–31 August 2012; pp. 1791–1795. [Google Scholar]



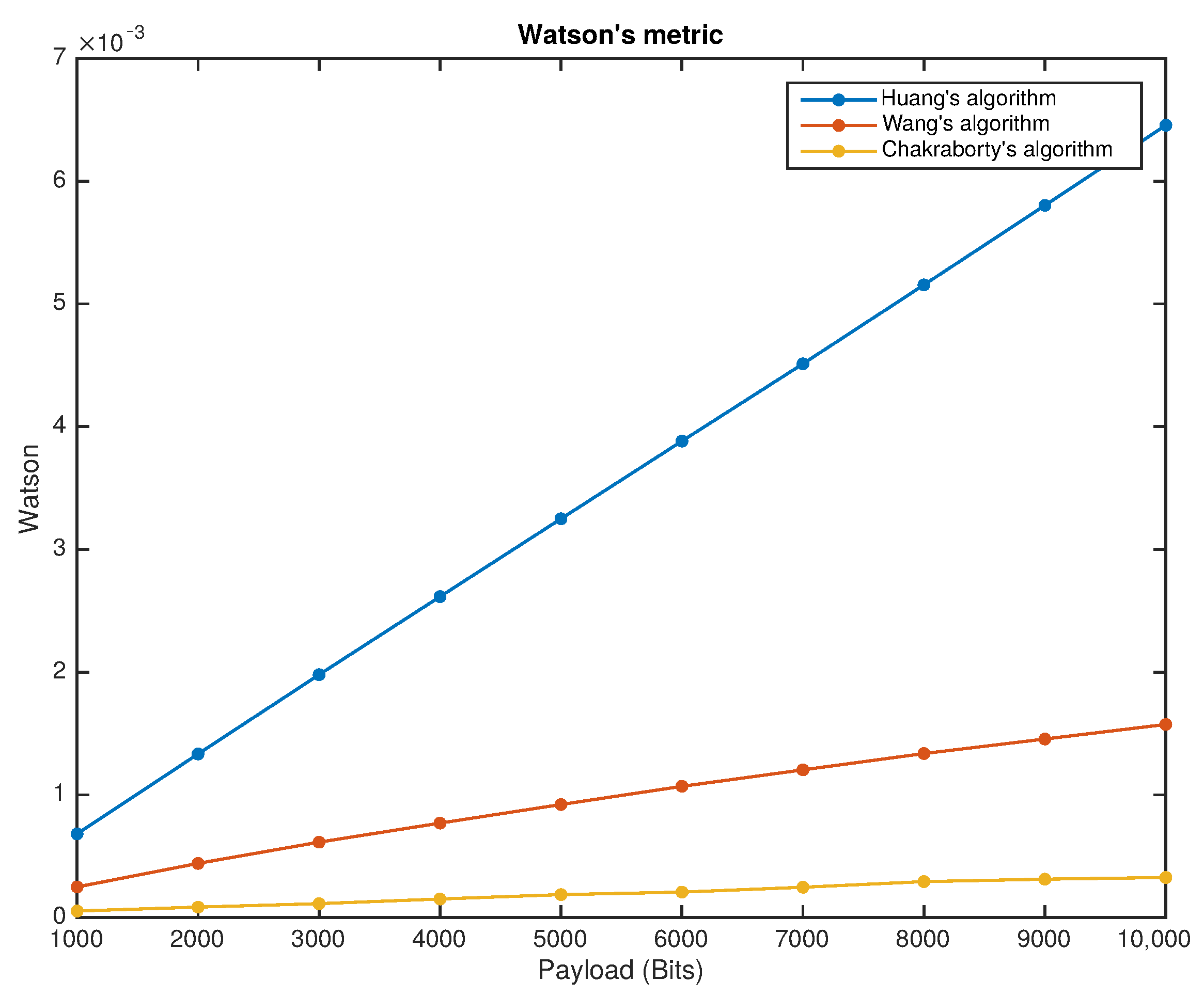


| Algorithm | PSNR dB | Watson | Max Attack | Time Complexity |
|---|---|---|---|---|
| Zhang and Wang [26] | 29.57 | 0.135 | 3.2% | 10 msec |
| Bravo-Solorio et al. [27] | 37.90 | 0.067 | 20.0% | 49.7 min |
| ID | Work | PSNR (dB) | Watson | ||||||
|---|---|---|---|---|---|---|---|---|---|
| min | max | min | max | ||||||
| F1 | [23] | 47.03 | ±2.84 | 39.68 | 56.40 | 0.1433 | ±0.0032 | 0.0007 | 0.0905 |
| F2 | [24] | 65.35 | ±0.03 | 65.21 | 65.48 | 0.0016 | ±0.0015 | 0.0006 | 0.0271 |
| F3 | [25] | 68.84 | ±0.04 | 68.72 | 69.00 | 0.0003 | ±0.0002 | 0.0002 | 0.0027 |
| S1 | [26] | 29.57 | ±4.10 | 20.17 | 46.98 | 0.1350 | ±0.0675 | 0.0169 | 0.4146 |
| S2 | [27] | 37.90 | ±0.12 | 36.78 | 38.71 | 0.0679 | ±0.0316 | 0.0422 | 0.7103 |
| Configurations | PSNR (dB) | Watson | Payload (bits) | ||||||
|---|---|---|---|---|---|---|---|---|---|
| min | max | min | max | ||||||
| F1-S1 | 29.02 | ±4.51 | 20.25 | 40.34 | 0.1433 | ±0.0830 | 0.0271 | 0.3953 | 5k |
| F1-S2 | 37.34 | ±0.33 | 36.34 | 37.90 | 0.0688 | ±0.0497 | 0.0497 | 0.4546 | 5k |
| F2-S1 | 29.56 | ±4.09 | 20.17 | 46.76 | 0.1355 | ±0.0675 | 0.0174 | 0.4145 | 10k |
| F2-S2 | 37.90 | ±0.13 | 36.53 | 38.74 | 0.0678 | ±0.0313 | 0.0419 | 0.7022 | 10k |
| F3-S1 | 32.39 | ±3.87 | 23.10 | 46.13 | 0.0985 | ±0.0459 | 0.0202 | 0.2977 | 10k |
| F3-S2 | 37.89 | ±0.12 | 36.90 | 38.90 | 0.0678 | ±0.0199 | 0.0420 | 0.3357 | 10k |
| ID | Expansion n | PSNR (dB) | Watson | ||||||
|---|---|---|---|---|---|---|---|---|---|
| min | max | min | max | ||||||
| C1 | 2 | 26.51 | ±6.76 | 7.93 | 49.92 | 0.1673 | ±0.1657 | 0.0118 | 2.8645 |
| C2 | 12 | 15.24 | ±3.37 | 6.25 | 27.83 | 0.7331 | ±0.3117 | 0.1402 | 4.3541 |
| Configurations | PSNR (dB) | Watson | ||||||
|---|---|---|---|---|---|---|---|---|
| min | max | min | max | |||||
| C1-S1 | 21.74 | ±5.11 | 7.89 | 40.70 | 0.3164 | ±0.2309 | 0.0351 | 3.3922 |
| C1-S2 | 25.78 | ±5.88 | 7.92 | 37.65 | 0.1983 | ±0.1686 | 0.0539 | 2.9249 |
| C2-S1 | 12.40 | ±2.59 | 6.15 | 22.66 | 1.0504 | ±0.3784 | 0.2753 | 4.9221 |
| C2-S2 | 15.21 | ±3.34 | 6.55 | 27.44 | 0.7391 | ±0.3116 | 0.1518 | 4.3353 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Garcia-Hernandez, J.J.; Feregrino-Uribe, C.; Menendez-Ortiz, A.; Robledo-Cruz, D.W. Evaluation of a Framework for Robust Image Reversible Watermarking. Appl. Sci. 2022, 12, 7242. https://doi.org/10.3390/app12147242
Garcia-Hernandez JJ, Feregrino-Uribe C, Menendez-Ortiz A, Robledo-Cruz DW. Evaluation of a Framework for Robust Image Reversible Watermarking. Applied Sciences. 2022; 12(14):7242. https://doi.org/10.3390/app12147242
Chicago/Turabian StyleGarcia-Hernandez, Jose Juan, Claudia Feregrino-Uribe, Alejandra Menendez-Ortiz, and Dan Williams Robledo-Cruz. 2022. "Evaluation of a Framework for Robust Image Reversible Watermarking" Applied Sciences 12, no. 14: 7242. https://doi.org/10.3390/app12147242
APA StyleGarcia-Hernandez, J. J., Feregrino-Uribe, C., Menendez-Ortiz, A., & Robledo-Cruz, D. W. (2022). Evaluation of a Framework for Robust Image Reversible Watermarking. Applied Sciences, 12(14), 7242. https://doi.org/10.3390/app12147242






