Digital Watermarking System for Copyright Protection and Authentication of Images Using Cryptographic Techniques
Abstract
:1. Introduction
2. Literature Survey
3. Preliminaries
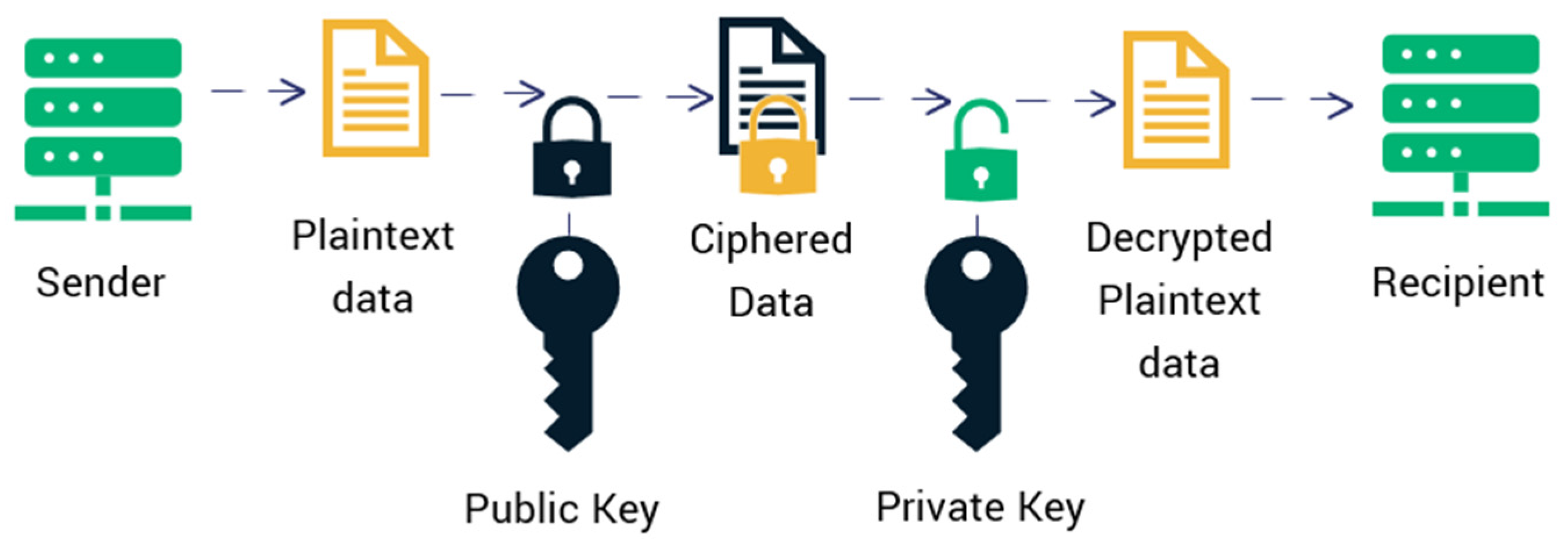
3.1. RSA Algorithm
- Pick two big prime numbers, r, and s.
- Find t = r × s by multiplying these values, where t is referred to as the modulus for encryption and decoding.
- Use a number k less than t so that t is roughly prime to (r − 1) × (s − 1), which indicates that the only factor in common between k and (r − 1) × (s − 1) is 1. Select “k” so that 1 < k < φ (t), k is prime to φ (t), and gcd (e,d(t)) = 1.
- The public key is <e, t> for t = r × s. The public key <e, t> encrypts a plaintext message m. The mathematical methodology is employed to obtain ciphertext C from the original message: C = mk mod t.
- The following formula is employed to calculate the d and set the private key in a way that Dk mod {(r − 1) × (s − 1)} = 1.
- <d, t> is the private key. The private key <d, t> is used to decipher the ciphertext message c. The below formula is used to generate plain text m out from ciphertext c: m = cd mod t.
- Different inputs of x(o), u, prime numbers, and the generated public and private keys with an encrypted message and decrypted messages are shown in Table 1.
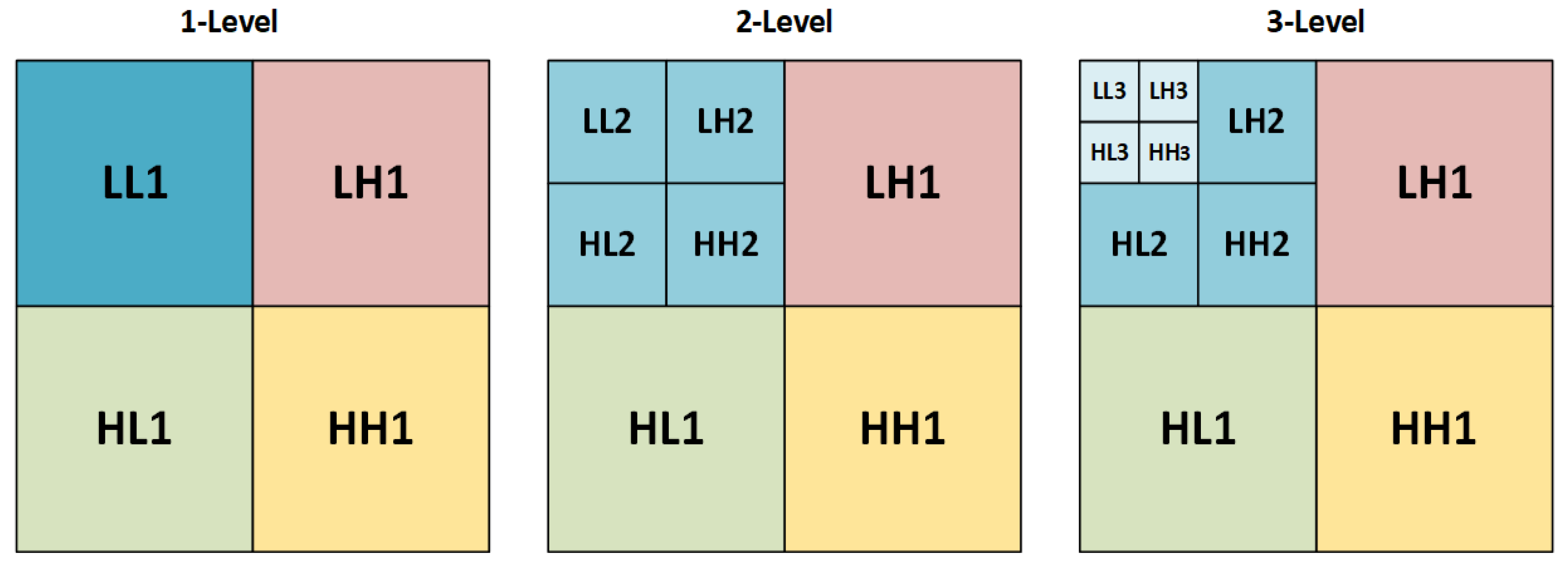
3.2. Discrete Wavelet Transform (DWT)
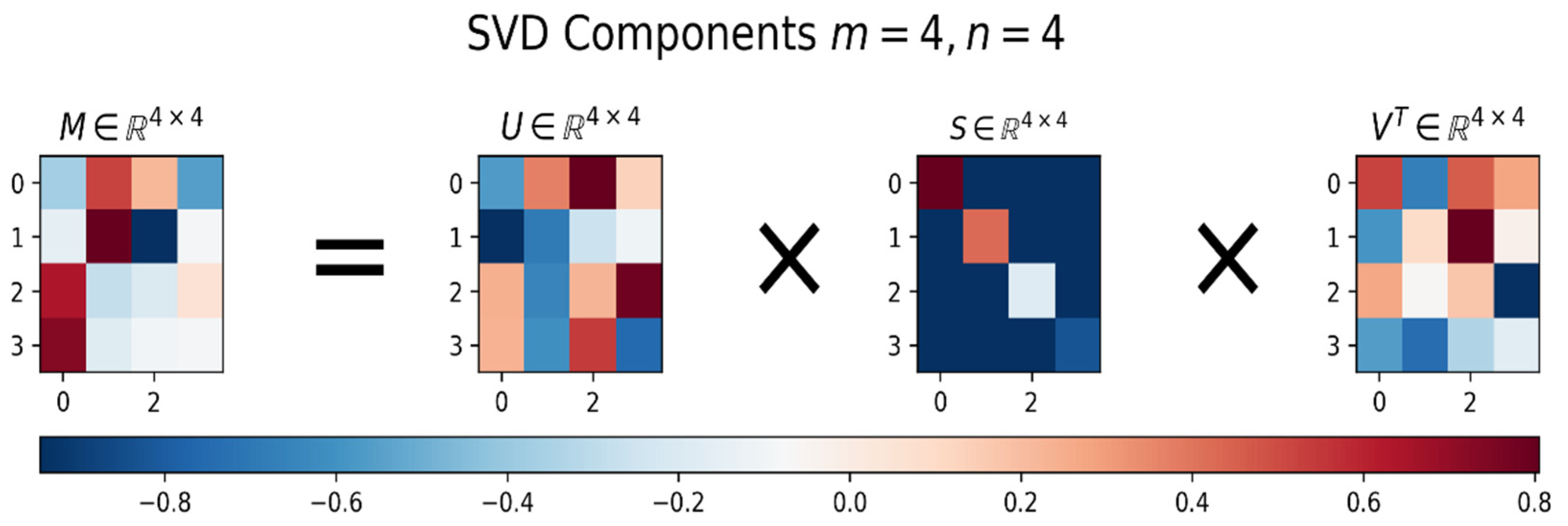
3.3. Singular Value Decomposition (SVD)
4. Proposed Method
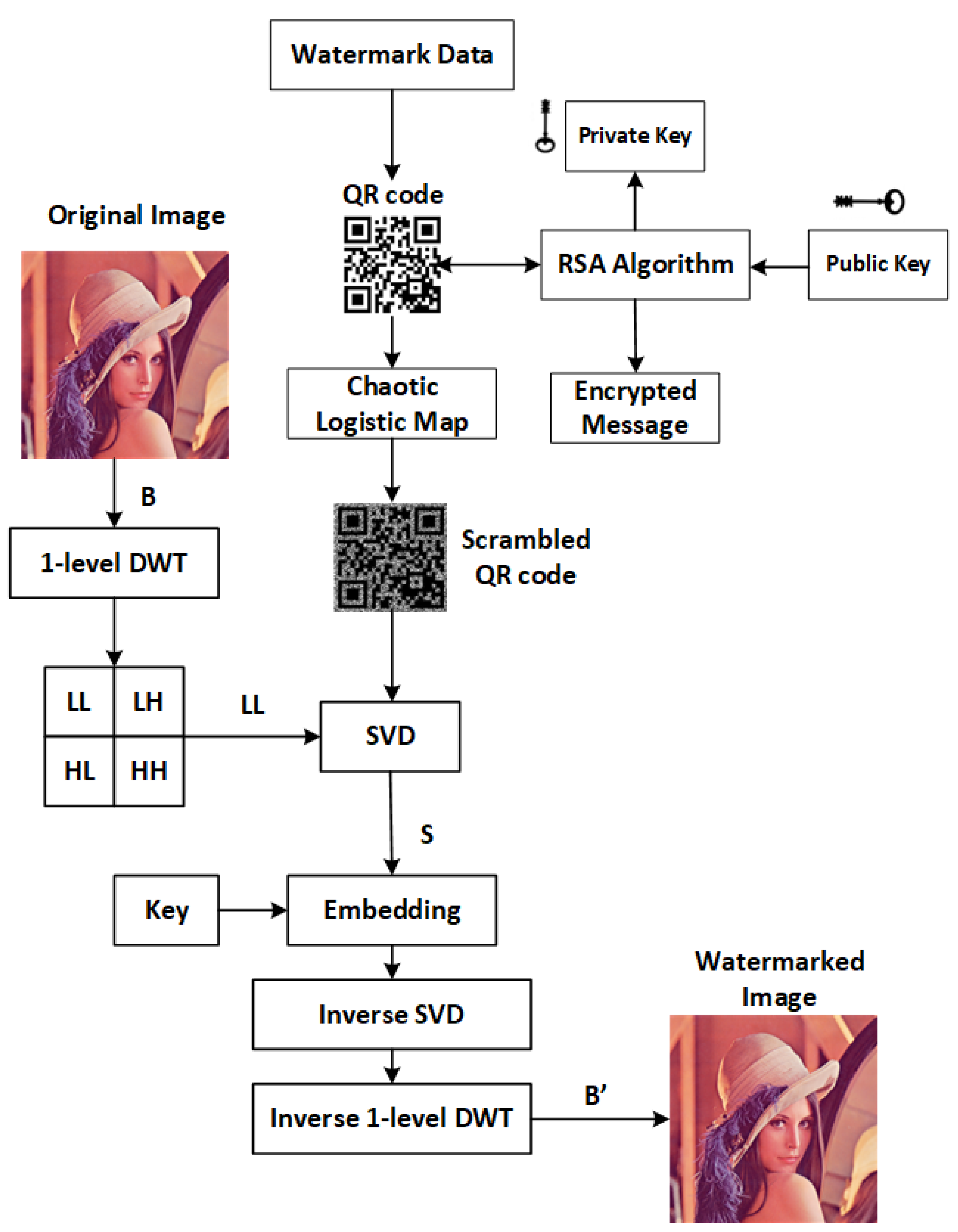
4.1. Embedding
- Step 1:
- The watermark data consisting of name and country is created as a QR code.
- Step 2:
- Generate a public key and an encrypted message by inputting private key values into the RSA algorithm.
- Step 3:
- The QR code is scrambled using a Chaotic Logistic Map (CLM) to provide watermark data security.
- Step 4:
- Import the significant image where the watermark has to be concealed.
- Step 5:
- Convert the imported color image into red, green, and blue components.
- Step 6:
- Consider the blue layer and apply one-level Haar wavelet decomposition to obtain the four subbands (LL, LH, HL, and HH).
- Step 7:
- The LL subband and scrambled QR image are selected and decomposed using SVD decomposition.
- Step 8:
- Both images’ singular values are considered and combined with a key value to generate watermarked singular values.
- Step 9:
- A watermarked LL subband is created using an invertible SVD.
- Step 10:
- By fusing the watermarked LL subband and the other subbands to create the watermarked blue layer, an inverse DWT is implemented for one level.
- Step 11:
- A watermarked color image is created by combining a blue layer with the red, green, and other layers.
- Step 12:
- The watermarked image with the public key and key value are communicated to the receiver.
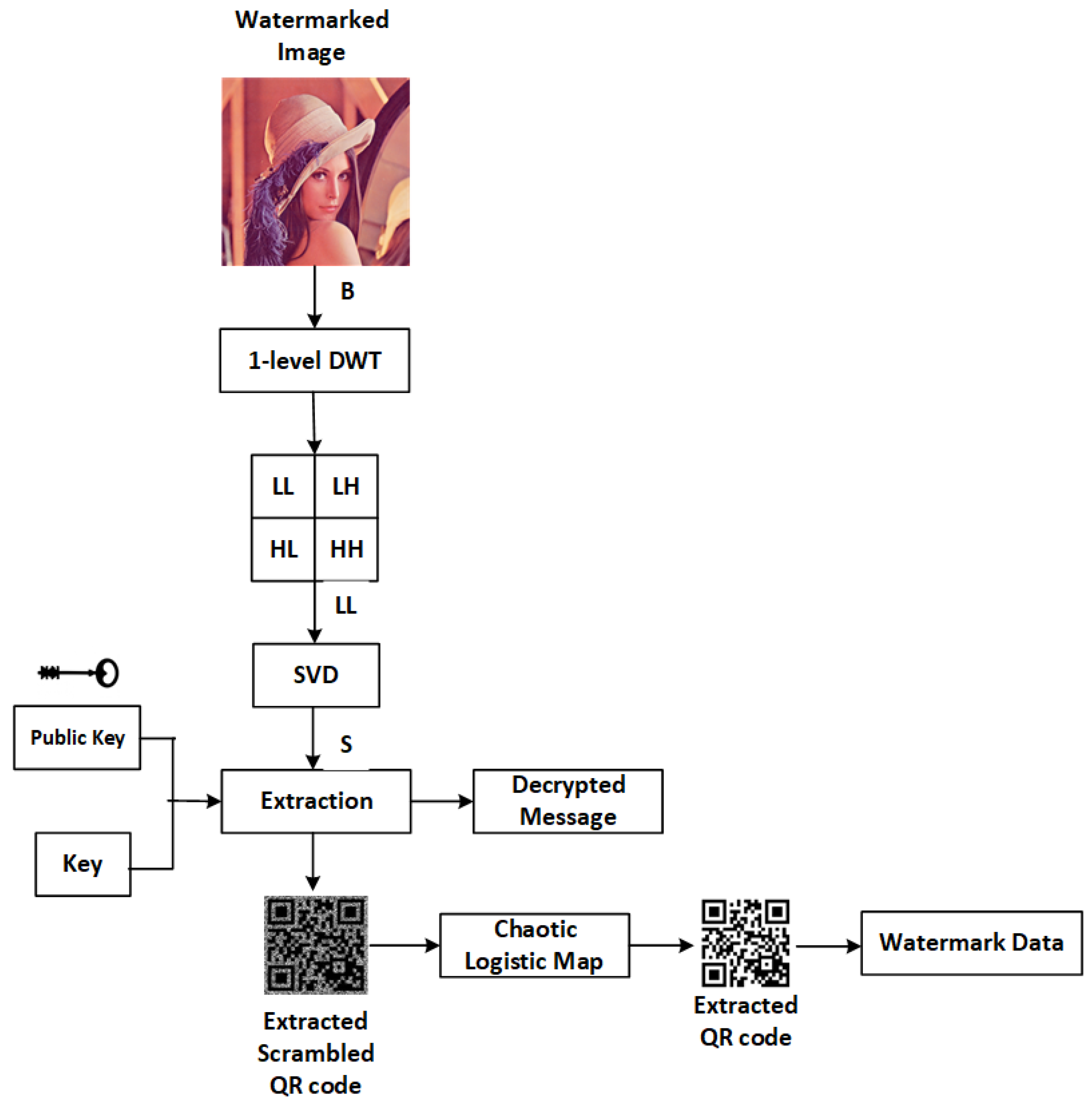
4.2. Extraction
- Step 1:
- Examine the image that is watermarked.
- Step 2:
- The color watermarked image is converted to red, green, and blue layers.
- Step 3:
- As the watermark is embedded in the blue component, the same is considered for extraction.
- Step 4:
- The blue component is applied with one-level DWT with a Haar wavelet.
- Step 5:
- The LL subband is considered, and SVD is applied to generate a singular value matrix.
- Step 6:
- A scrambled QR watermark is extracted based on the key values and partial data of the significant image.
- Step 7:
- Inverse scrambling is applied to the extracted watermark using the CLM algorithm.
- Step 8:
- The watermark is extracted with the decrypted message using the public key, which contains the private key values to verify the watermarked data.
5. Experimental Results
5.1. Evaluation Metrics
5.1.1. Peak-Signal-to-Noise Ratio
5.1.2. Normalized Correlation Coefficient
5.2. Noise Attacks
5.2.1. Salt and Pepper Noise
5.2.2. Gaussian Noise Attack
5.2.3. Mean Filtering Attack
5.2.4. JPEG Compression
5.3. Geometric Attacks
5.3.1. Cropping Attack
5.3.2. Rotation Attack
5.3.3. Scaling Attack
5.3.4. Translation Attack
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Vaidya, S.P. Multiple decompositions-based blind watermarking scheme for color images. In Proceedings of the IEEE International Conference on Recent Trends in Image Processing and Pattern Recognition, Solapur, India, 21–22 December 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 132–143. [Google Scholar]
- Hosny, K.M.; Darwish, M.M. Invariant image watermarking using accurate polar harmonic transforms. Comput. Electr. Eng. 2017, 62, 429–447. [Google Scholar] [CrossRef]
- Sanivarapu, P.V.; Rajesh, K.N.V.P.S.; Reddy, N.V.R.; Reddy, N.C.S. Patient data hiding into ECG signal using watermarking in transform domain. Phys. Eng. Sci. Med. 2020, 43, 213–226. [Google Scholar] [CrossRef]
- Vaidya, S.P.; PVSSR, C.M. Adaptive digital watermarking for copyright protection of digital images in wavelet domain. Procedia Comput. Sci. 2015, 58, 233–240. [Google Scholar] [CrossRef]
- Vaidya, P.; PVSSR, C.M. A robust semi-blind watermarking for color images based on multiple decompositions. Multimed. Tools Appl. 2017, 76, 25623–25656. [Google Scholar]
- Hosny, K.M.; Darwish, M.M. Robust color image watermarking using invariant quaternion Legendre-Fourier moments. Multimed. Tools Appl. 2018, 77, 24727–24750. [Google Scholar] [CrossRef]
- Vaidya, P.; PVSSR, C.M. Adaptive, robust, and blind digital watermarking using Bhattacharyya distance and bit manipulation. Multimed. Tools Appl. 2018, 77, 5609–5635. [Google Scholar]
- Hosny, K.M.; Darwish, M.M.; Fouda, M.M. Robust color images watermarking using new fractional-order exponent moments. IEEE Access 2021, 9, 47425–47435. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Li, K.; Salah, A. Parallel multi-core CPU and GPU for fast and robust medical image watermarking. IEEE Access 2018, 6, 77212–77225. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. New geometrically invariant multiple zero watermarking algorithm for color medical images. Biomed. Signal Process. Control 2021, 70, 103007. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. Reversible color image watermarking using fractional-order polar harmonic transforms and a chaotic sine map. Circuits Syst. Signal Process. 2021, 40, 6121–6145. [Google Scholar] [CrossRef]
- van Schyndel, R.G.; Tirkel, A.Z.; Osborne, C.F. A digital watermark. In Proceedings of the IEEE 1st International Conference on Image Processing, Austin, TX, USA, 13–16 November 1994; Volume 2, pp. 86–90. [Google Scholar]
- Singh, A.K. Robust and distortion control dual watermarking in LWT domain using DCT and error correction code for color medical image. Multimed. Tools Appl. 2019, 78, 30523–30533. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Joint watermarking-encryption-ECC for patient record security in wavelet domain. IEEE MultiMedia 2020, 27, 66–75. [Google Scholar] [CrossRef]
- Kaur, G.; Agarwal, R.; Patidar, V. Crypto-watermarking of images for secure transmission overcloud. J. Inf. Optim. Sci. 2020, 41, 205–216. [Google Scholar]
- Zermi, N.; Khaldi, A.; Kafi, R.; Kahlessenane, F.; Euschi, S. A DWT-SVD based robust digital watermarking for medical image security. Forensic Sci. Int. 2021, 320, 110691. [Google Scholar] [CrossRef] [PubMed]
- Borra, S.; Thanki, R. Crypto-watermarking scheme for tamper detection of medical images. Comput. Methods Biomech. Biomed. Eng. Imaging Vis. 2020, 8, 345–355. [Google Scholar] [CrossRef]
- Lebcir, M.; Awang, S.; Benziane, A. Robust blind watermarking approach against the compression for fingerprint image using 2D-DCT. Multimed. Tools Appl. 2022, 81, 20561–20583. [Google Scholar] [CrossRef]
- Zhou, X.; Tang, X. Research and implementation of RSA algorithm for encryption and decryption. In Proceedings of the IEEE 2011 6th International Forum on Strategic Technology, Harbin, China, 22–24 August 2011; Volume 2, pp. 1118–1121. [Google Scholar]
- Shensa, M.J. The discrete wavelet transform: Wedding the a trous and Mallat algorithms. IEEE Trans. Signal Process. 1992, 40, 2464–2482. [Google Scholar] [CrossRef]
- Vaidya, S.P. A blind color image watermarking using brisk features and contourlet transform. In Proceedings of the International Conference on Recent Trends in Image Processing and Pattern Recognition, Solapur, India, 21–22 December 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 203–215. [Google Scholar]
- Vaidya, S.P.; PVSSR, C.M.; Santosh, K.C. Imperceptible watermark for a game-theoretic watermarking system. Int. J. Mach. Learn. Cybern. 2019, 10, 1323–1339. [Google Scholar] [CrossRef]
- Nason, G.P.; Silverman, B.W. The discrete wavelet transform in s. J. Comput. Graph. Stat. 1994, 3, 163–191. [Google Scholar]
- Van Fleet, P.J. Discrete Wavelet Transformations: An Elementary Approach with Applications; John Wiley & Sons: Hoboken, NJ, USA, 2011. [Google Scholar]
- Chang, C.; Girod, B. Direction-adaptive discrete wavelet transform for image compression. IEEE Trans. Image Process. 2007, 16, 1289–1302. [Google Scholar] [CrossRef]
- Vaidya, S.P.; PVSSR, C.M. A robust and blind watermarking for color videos using redundant wavelet domain and SVD. In Smart Computing Paradigms: New Progresses and Challenges; Springer: Berlin/Heidelberg, Germany, 2020; pp. 11–17. [Google Scholar]
- Mun, S.-M.; Nam, S.-H.; Jang, H.-U.; Kim, D.; Lee, H.-K. A robust blind watermarking using convolutional neural network. arXiv 2017, arXiv:1704.03248. [Google Scholar]
- Agoyi, M.; C¸elebi, E.; Anbarjafari, G. A watermarking algorithm based on chirp z-transform, discrete wavelet transform, and singular value decomposition. Signal Image Video Process. 2015, 9, 735–745. [Google Scholar] [CrossRef]




| Inputs and Outputs of RSA Algorithm | ||||||
|---|---|---|---|---|---|---|
| X(o) (0–1) | U (3.56–4) | Prime Numbers | Public Key | Private Key | Encrypted Message | Decrypted Message |
| 0.2 | 3.6 | (3, 5) | (1, 15) | (1, 15) | 31514649 | (0.2, 3.6) |
| 0.4 | 3.7 | (5, 7) | (23, 35) | (27, 55) | 2716334111620 | (0.4, 3.7) |
| 0.5 | 3.6 | (5, 13) | (19, 65) | (43, 65) | 226273451624 | (0.5, 3.6) |
| 0.6 | 3.8 | (5, 11) | (11, 55) | (11, 55) | 3746544451461 | (0.6, 3.8) |
| 0.8 | 3.9 | (7, 13) | (35, 91) | (35, 91) | 55249602528 | (0.8, 3.9) |
| Images | PSNR and NCC Values without Attacks | ||
|---|---|---|---|
| House | 42.25, 1.00 | Lake | 41.68, 1.00 |
| Tree | 43.56, 1.00 | Pepper | 40.35, 1.00 |
| Girl | 42.85, 1.00 | House 2 | 41.74, 1.00 |
| Mandrill | 43.12, 1.00 | Einstein | 43.36, 1.00 |
| Lena | 42.22, 1.00 | Monalisa | 43.81, 1.00 |
| Jetplane | 41.81, 1.00 | Monarch | 42.65, 1.00 |
| Images | PSNR and NCC Values after Attacks | |||
|---|---|---|---|---|
| Salt and Pepper | Gaussian | Mean Filtering | JPEG Compression | |
| House | 36.11, 0.9789 | 39.01, 0.9898 | 33.12, 0.9901 | 37.12, 0.9938 |
| Tree | 36.05, 0.9796 | 38.87, 0.9885 | 33.25, 0.9905 | 37.28, 0.9942 |
| Girl | 35.56, 0.9898 | 38.86, 0.9896 | 33.18, 0.9908 | 37.25, 0.9935 |
| Mandrill | 35.66, 0.9899 | 38.96, 0.9901 | 33.22, 0.9906 | 37.24, 0.9932 |
| Lena | 35.28, 0.9887 | 38.15, 0.9914 | 33.15, 0.9910 | 37.16, 0.9949 |
| Jetplane | 35.47, 0.9815 | 38.42, 0.9912 | 33.16, 0.9903 | 37.21, 0.9936 |
| Lake | 35.22, 0.9829 | 38.36, 0.9908 | 33.11, 0.9907 | 37.27, 0.9937 |
| Pepper | 35.84, 0.9867 | 38.51, 0.9925 | 33.08, 0.9915 | 37.28, 0.9932 |
| House 2 | 36.24, 0.9814 | 39.12, 0.9904 | 33.13, 0.9911 | 37.24, 0.9941 |
| Einstein | 36.05, 0.9885 | 39.21, 0.9916 | 33.17, 0.9916 | 37.28, 0.9934 |
| Monalisa | 35.69, 0.9829 | 39.11, 0.9892 | 33.22, 0.9914 | 37.22, 0.9914 |
| Monarch | 35.88, 0.9785 | 39.05, 0.9845 | 33.20, 0.9909 | 37.24, 0.9909 |
| Images | PSNR and NCC Values after Attacks | |||
|---|---|---|---|---|
| Cropping | Rotation | Scaling | Translation | |
| House | 28.36, 0.9801 | 29.06, 0.9896 | 38.66, 0.9964 | 36.42, 0.9777 |
| Tree | 29.05, 0.9815 | 28.58, 0.9889 | 38.59, 0.9948 | 36.28, 0.9765 |
| Girl | 29.23, 0.9836 | 29.12, 0.9885 | 39.28, 0.9947 | 36.19, 0.9787 |
| Mandrill | 29.26, 0.9885 | 29.14, 0.9889 | 39.22, 0.9957 | 36.33, 0.9789 |
| Lena | 28.21, 0.9869 | 28.12, 0.9904 | 38.92, 0.9954 | 36.23, 0.9778 |
| Jetplane | 29.60, 0.9878 | 27.86, 0.9911 | 37.99, 0.9958 | 36.19, 0.9781 |
| Lake | 29.35, 0.9886 | 28.26, 0.9919 | 38.84, 0.9961 | 36.28, 0.9776 |
| Pepper | 29.48, 0.9891 | 27.87, 0.9921 | 37.94, 0.9955 | 36.22, 0.9785 |
| House 2 | 29.54, 0.9912 | 28.56, 0.9902 | 38.65, 0.9961 | 36.18, 0.9788 |
| Einstein | 29.22, 0.9905 | 29.14, 0.9919 | 39.19, 0.9951 | 36.19, 0.9781 |
| Monalisa | 29.35, 0.9897 | 29.04, 0.9901 | 39.21, 0.9968 | 36.24, 0.9782 |
| Monarch | 29.32,0.9856 | 28.87, 0.9842 | 38.92, 0.9964 | 36.28, 0.9778 |
| Image Attacks | Schemes | Lena | Mandrill | Peppers | Airplane |
|---|---|---|---|---|---|
| No Attack | Vaidya et al. [4] | 1.00 | 1.00 | 1.00 | 1.00 |
| Mun et al. [27] | 0.9885 | 0.9886 | 0.9895 | 0.9879 | |
| Agoyi et al. [28] | 0.8694 | 0.8837 | 0.9030 | 0.9025 | |
| Hosny et al. [6] | 0.9995 | 0.9995 | 0.9995 | 0.9995 | |
| Proposed Method | 1.00 | 1.00 | 1.00 | 1.00 | |
| Salt and Pepper noise | Vaidya et al. [4] | 0.8458 | 0.7156 | 0.9465 | 0.9325 |
| Mun et al. [27] | - | - | - | - | |
| Agoyi et al. [28] | - | - | - | - | |
| Hosny et al. [6] | 0.9916 | 0.9916 | 0.9916 | 0.9916 | |
| Proposed Method | 0.9887 | 0.9899 | 0.9867 | 0.9815 | |
| Gaussian noise | Vaidya et al. [4] | 0.8489 | 0.8053 | 0.9279 | 0.9114 |
| Mun et al. [27] | - | - | - | - | |
| Agoyi et al. [28] | 0.7955 | 0.7796 | 0.8083 | 0.7956 | |
| Hosny et al. [6] | 0.9905 | 0.9905 | 0.9905 | 0.9905 | |
| Proposed Method | 0.9914 | 0.9901 | 0.9925 | 0.9912 | |
| Cropping | Vaidya et al. [4] | 0.8944 | 0.8946 | 0.8942 | 0.8965 |
| Mun et al. [27] | 0.9921 | 0.9860 | 0.9948 | 0.9888 | |
| Agoyi et al. [28] | - | - | - | - | |
| Hosny et al. [6] | - | - | - | - | |
| Proposed Method | 0.9869 | 0.9885 | 0.9891 | 0.9878 | |
| Scaling | Vaidya et al. [4] | 0.9827 | 0.9956 | 0.9980 | 0.9963 |
| Mun et al. [27] | 0.9837 | 0.9742 | 0.9768 | 0.9879 | |
| Agoyi et al. [28] | 0.9263 | 0.9675 | 0.9644 | 0.9381 | |
| Hosny et al. [6] | 0.9940 | 0.9940 | 0.9940 | 0.9940 | |
| Proposed Method | 0.9954 | 0.9957 | 0.9955 | 0.9958 | |
| JPEG Compression (90) | Vaidya et al. [4] | 0.9053 | 0.8983 | 0.8819 | 0.8956 |
| Mun et al. [27] | 0.9457 | 0.6537 | 0.9194 | 0.9472 | |
| Agoyi et al. [28] | 0.8469 | 0.8469 | 0.8901 | 0.8854 | |
| Hosny et al. [6] | 0.9928 | 0.9928 | 0.9928 | 0.9928 | |
| Proposed Method | 0.9949 | 0.9932 | 0.9932 | 0.9936 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sanivarapu, P.V.; Rajesh, K.N.V.P.S.; Hosny, K.M.; Fouda, M.M. Digital Watermarking System for Copyright Protection and Authentication of Images Using Cryptographic Techniques. Appl. Sci. 2022, 12, 8724. https://doi.org/10.3390/app12178724
Sanivarapu PV, Rajesh KNVPS, Hosny KM, Fouda MM. Digital Watermarking System for Copyright Protection and Authentication of Images Using Cryptographic Techniques. Applied Sciences. 2022; 12(17):8724. https://doi.org/10.3390/app12178724
Chicago/Turabian StyleSanivarapu, Prasanth Vaidya, Kandala N. V. P. S. Rajesh, Khalid M. Hosny, and Mostafa M. Fouda. 2022. "Digital Watermarking System for Copyright Protection and Authentication of Images Using Cryptographic Techniques" Applied Sciences 12, no. 17: 8724. https://doi.org/10.3390/app12178724
APA StyleSanivarapu, P. V., Rajesh, K. N. V. P. S., Hosny, K. M., & Fouda, M. M. (2022). Digital Watermarking System for Copyright Protection and Authentication of Images Using Cryptographic Techniques. Applied Sciences, 12(17), 8724. https://doi.org/10.3390/app12178724










