Abstract
It has been challenging to separate the time–frequency (TF) overlapped wireless communication signals with unknown source numbers in underdetermined cases. In order to address this issue, a novel blind separation strategy based on a TF soft mask is proposed in this paper. Based on the clustering property of the signals in the sparse domain, the angular probability density distribution is obtained by the kernel density estimation (KDE) algorithm, and then the number of source signals is identified by detecting the peak points of the distribution. Afterward, the contribution degree function is designed according to the cosine distance to calculate the contribution degrees of the source signals in the mixed signals. The separation of the TF overlapped signals is achieved by constructing a soft mask matrix based on the contribution degrees. The simulations are performed with digital signals of the same modulation and different modulation, respectively. The results show that the proposed algorithm has better anti-aliasing and anti-noise performance than the comparison algorithms.
1. Introduction
1.1. Research Background and Motivation
Blind source separation (BSS), defined as the task of separating the source signals from the observed signals when the source signals and the mixing mode are not known exactly, enables the separation of the mixed signals and the extraction of the source signals without a priori knowledge. As a kind of front-end technology in the field of signal processing, the BSS is of great importance in communication anti-jamming and improving spectrum utilization [1]. Unfortunately, the classical independent component analysis (ICA) and many extended algorithms [2,3,4] are based on the main assumption that the number of observed signals is greater than or equal to the number of source signals, which cannot realize the blind signal separation in underdetermined cases [5]. In practical communication scenarios, the number of observed signals is usually less than the number of source signals on account of system cost or environmental constraints, thus the study of underdetermined blind source separation (UBSS) is of more practical significance. At present, the main approach to tackle the issue of UBSS is based on sparse component analysis (SCA) [6]. The main strategy of the SCA method is solving the UBSS by exploiting the sparsity of the source signal or sparsity in the transform domain. However, with the dramatic increase in RF devices, it is almost inevitable that signals will be overlapped in the time and frequency domains. For communication signals that are not completely sparse in the time and frequency domains, it has been a challenge to solve the UBSS problem using the SCA method. It is of practical importance to separate the TF overlapped signals in underdetermined cases. This paper aims to improve the SCA algorithm for the effective separation of TF overlapped wireless communication signals with unknown source numbers.
1.2. Literature Review
The classical SCA algorithm mainly consists of the two-stage method and the TF masking method. The two-stage method first estimates the mixing matrix and then uses signal sparsity to recover the source signal. Zhen [7] utilized the sparse coding technique to discover the 1-D subspace from the set of TF points, then estimated the mixing matrix by grouping vectors in the subspace through hierarchical clustering, and finally used the least-squares method to achieve source signal recovery; Fang [8] firstly estimated the mixing matrix based on the hyperplane normal vector clustering algorithm, and then used the classical algorithm called orthogonal matching pursuit in compressed sensing to realize the separation of the linear frequency modulated radar mixed signals; Fu [9] realized the recovery of the source signal using a new subspace complementary matching pursuit algorithm. The algorithm reduced the computational complexity by selecting multiple atoms per iteration and also used parametric minimization instead of parametric minimization in order to improve the recovery accuracy.
The other is the TF masking method, i.e., the source signal is separated by designing a TF mask matrix. Yu [10] first detected the peak energy point of the mixed signals and then calculated the cosine distance between all energy points and the peak energy point, afterward obtained the binary mask based on a threshold to realize the reconstruction of the vibration signal; Cobos [11] proposed a maximum a posteriori decision criterion to design a binary mask matrix for the separation of mixed speech signals; Kumar [12] first detected the active single-source points by calculating the mixing ratio, and then found the cluster centers by a dynamic routing algorithm as a way to design a binary mask.
The above algorithms usually assume that the signal is sparse in some domains, such as the time domain, frequency domain, etc. However, in the wireless communication scenarios, the signals are inevitably overlapped in both time and frequency domains. In such cases, it may cause a reduction in separation accuracy or even complete failure when the classical SCA-based method is applied directly to the separation of TF overlapped communication signals. The two-stage method could not guarantee the estimation accuracy of the mixing matrix and the performance of the source signal recovery, while reconstructing the source signals through the TF binary mask will bring certain distortions [13,14,15]. Obviously, for the communication mixed signals with TF aliasing, better separation performance can be obtained by reasonably estimating the TF soft mask to reconstruct the source signals [16].
1.3. Contribution and Paper Organization
Under the framework of the TF masking method, we propose a novel underdetermined convolutional mixing UBSS algorithm for TF overlapped communication signals with an unknown number of sources. Firstly, the observed signals are converted to the sparse domain to obtain the linear clustering characteristic. Consequently, the effects of multipath and time delay are eliminated by calculating short-time spectral power; Secondly, the short-time spectral power ratio of the observed signals is converted into the angular distribution, and the number of source signals can be estimated through the KDE algorithm; Then the contribution degree of the source signal in the observed signal is obtained by the designed contribution degree function. Finally, the TF soft mask is constructed based on the contribution degree, which is employed to separate the mixed signals. The main contribution of the paper can be summarized in the following:
- A source number estimation method based on the KDE algorithm followed by detecting the peak points of the distribution is proposed, which can effectively estimate the number of sources before the signal separation.
- We design a contribution degree function based on the cosine distance, by which the contribution degree of the source signal to the mixed signal can be obtained. The contribution degree clearly reflects the mixing degree of the source signal at each frequency point, and it is of significant importance to improve the separation accuracy.
- The TF soft mask matrix is constructed based on the contribution degree function. Compared with the traditional binary mask, the TF soft mask can improve the separation accuracy for TF overlapped signals.
- The proposed blind source separation method for TF overlapped communication signal extends the application of the SCA algorithm, which reduces the requirement of signal sparsity for the classical SCA blind source separation algorithm.
The rest of this paper is structured as follows. The problem statement is given in Section 2, which includes the introduction of the effect on separation based on the classical SCA methods caused by TF aliasing. Subsequently, Section 3 describes the process of the algorithm in detail, which mainly consists of two parts: source number estimation and source signal recovery. Afterward, the separation performance of this algorithm is tested by the simulations in Section 4. Lastly, the conclusions are drawn in Section 5.
2. Problem Statement
In the wireless communication propagation model, multipath and time delay of signals are inevitable, which can be modeled as the convolutive mixture of the source signals [17]. All variables involved in the problem statement are described in Table 1. Without considering the noise, the mathematical expression of the convolutional mixture model can be expressed as
where represents the source signal; indicates the received mixed signal; is the number of wireless propagation paths; denotes the mixing matrix corresponding to the qth path. Considering the effect of time delay. can be expressed as
where represents the impulse response, and are the amplitude attenuation and time delay of the ith source signal to the kth sensor through the qth path, respectively. In order to obtain the sparse characteristic of the signals, the signal received by the kth sensor after a short-time Fourier transform (STFT) [18] can be written as

Table 1.
Variable definitions involved in the problem statement.
Take the BPSK signal as an example; the TF expression is described as
where denotes the center frequency of the ith source signal. After performing the modulus operation on [19], the power of the kth received signal can be expressed as
where expresses modulus operation. When the spectrum of the source signal is non-aliased, there is only the component of the source signal in the interval () of the received signal. In this case, the power ratio of any two of the received signals and is
Consequently, the short-time spectral power points of the signal will be clustered on the line with a slope of . Figure 1 represents the scatter plot of the power ratio of the two received signals after the convolutive mixture of the four BPSK signals. Due to the sparsity of the observed signals in the power domain, the received signals exhibit linear clustering property. There are four linear clusters in Figure 1 corresponding to the four source signals, and thus the mixed signals can be effectively separated by the traditional single-source-point (SSP) detection method [10]. However, in practical communication systems, it is almost impossible to avoid TF aliasing for communication signals. When the spectrum of the source signal is overlapped, the sparsity of the observed signals in the power domain cannot be guaranteed, thus weakening the linear clustering property of the observed signals (Figure 2). The traditional SSP method will not accurately recover the source signal.
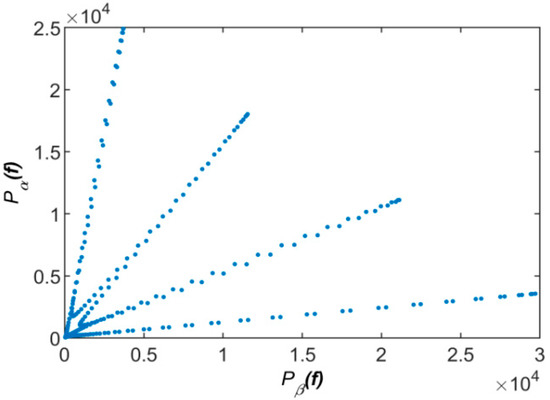
Figure 1.
The power scatters of mixed signals without TF aliasing.
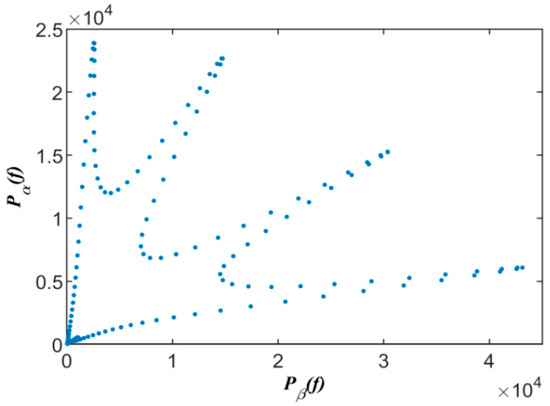
Figure 2.
The power scatters of mixed signals with TF aliasing.
3. UBSS Algorithm Based on TF Soft Mask
To tackle the above challenge, we propose a new blind separation strategy based on TF soft mask. The process consists of two main stages. The first step is to determine the number of sources through the KDE algorithm, followed by peak detection. After that, the contribution degree of the source signal in the observed signal is calculated by the contribution degree function to construct the TF soft mask matrix, which is used to separate the TF aliasing signals. All variables involved in the section are described in Table 2.

Table 2.
Variable definitions in this section.
3.1. Source Number Estimation
In the problem of UBSS, the source number estimation is an indispensable step. The accurate estimation of the number of sources is the prerequisite for precise source signal recovery [20,21]. In order to estimate the number of sources accurately, the KDE algorithm is used to calculate the angular probability density distribution of the mixed signal in the sparse domain, followed by detecting the number of peak points of the distribution. In order to eliminate the interference of noise on the signal, a threshold needs to be set to screen out the low power points. The set of frequencies after removing the low power points can be obtained by
where is the empirical parameter, which is taken as 0.1 in this paper. In the later expressions, is used to denote the uth element of . Afterward, convert the filtered power points into angular distribution :
The statistical histogram after converting to an angular distribution is shown in Figure 3. As seen from the figure, the angular distribution is more densely distributed around the intervals 0.07, 0.52, 1.15, and 1.48 than the other intervals. Thus the angular distribution is modeled based on the KDE algorithm [22]:
where denotes the angular probability density distribution of ; is the length of the vector ; represents the kernel function with a smoothing factor of the bandwidth. In this paper, we choose the Gaussian kernel as the kernel function and take as 0.25. The angular probability density distribution obtained by the KDE algorithm is shown in Figure 4. The number of peak points of the angular probability density distribution is the number of sources to be estimated. As we can see from Figure 4, there are four peak points marked by red circles, which means that the number of estimated source signals is four.
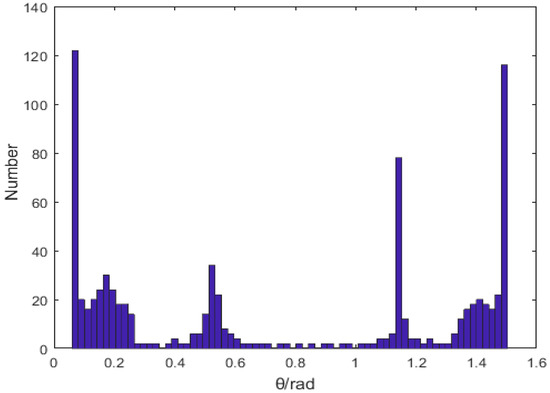
Figure 3.
The statistical histogram of angular distribution.
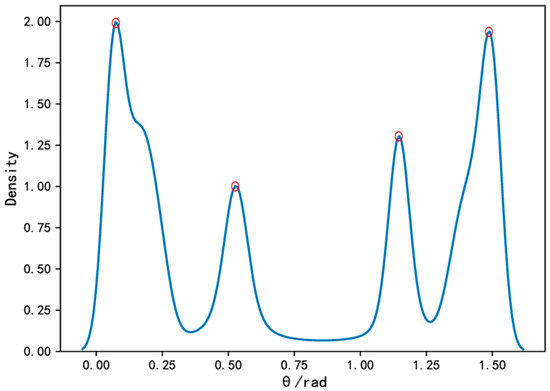
Figure 4.
The angular probability density distribution.
3.2. Source Signal Recovery by TF Soft Mask
Ideally, the reconstruction of the source signal is achieved by inverse short-time Fourier transform (ISTFT) in the frequency band 10. However, the traditional clustering method is only a kind of hard segmentation of power points to obtain the TF binary mask. When the frequency spectrum is overlapped, the short-term spectral power of the observed signals is the superposition of the short-term spectral power of the source signals. The integrity of the source signal reconstruction cannot be guaranteed through the method of hard segmentation. Thus a matching soft mask matrix is required to fully recover the source signal.
where represents the Hadamard product; denotes the ith signal to be reconstructed, and is the corresponding TF soft mask matrix that needs to be constructed.
In this paper, the construction of the TF soft mask matrix is performed by designing a contribution degree function based on the cosine distance. It can be seen from Figure 2 that among all the power points inside the ith linear cluster, the endpoint is subject to the least interference. That is, when , the contribution degree of the ith source signal to the mixed signal can be taken as 1, and the cosine distance between the endpoint and itself is 1 as well ( is the frequency corresponding to the endpoint of the ith linear clustering cluster). When is further away from , the contribution degree will be decreased. The corresponding cosine distance between the power point and the ith endpoint is decreased as well. Extremely, is taken as 0 when is the frequency of the nearest adjacent endpoint. Hence the contribution degree can be characterized by the cosine distance between all power points and the endpoint of the ith linear cluster. A monotonically increasing contribution function is designed to characterize the positive correlation between contribution degree and cosine distance :
where denotes the maximum of the cosine distance between the endpoint of the ith linear cluster and the endpoints of the remaining linear clusters; denotes the scaling factor of the contribution function, whose different values will affect the separation performance of the algorithm. In Section 4.1, we will discuss the impact of on separation performance. The cosine distance of the uth power point from the endpoint of the ith linear cluster is obtained as
where denotes the cosine distance between two points. The frequencies corresponding to the endpoints of the clustering clusters can be detected by seeking the first peak points in the sum of the power data marked in red Figure 5. The points marked in red are the endpoints of the detected linear clusters to be determined in Figure 6. Therefore, the contribution degree of the uth point to the ith linear cluster can be calculated by the contribution degree function given above.
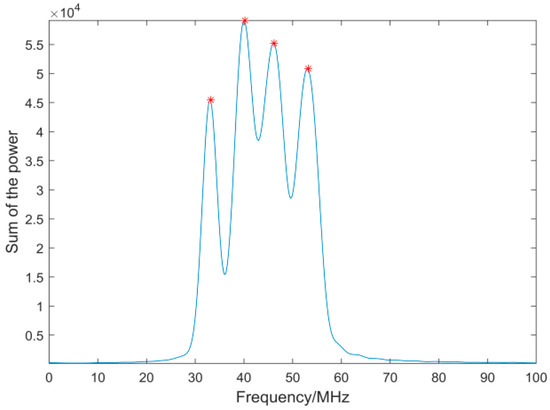
Figure 5.
The sum of the power data.
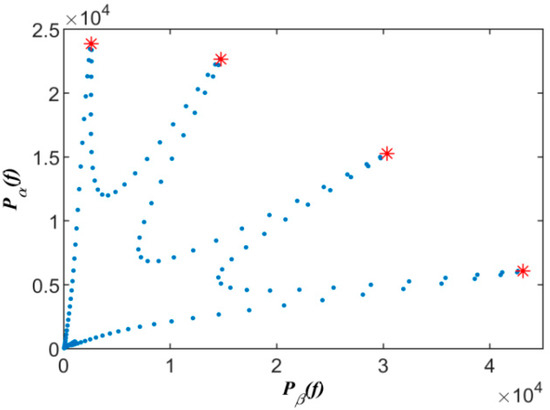
Figure 6.
The power scatters of mixed signals after detection.
Based on the contribution degree obtained from Equation (11), the ith TF soft mask matrix is constructed by the following formula:
where is the number of STFT frequencies; is the number of time series of STFT. soft mask matrices can be constructed in this way.
The ith source signal to be reconstructed is
where indicates the sum of the observed signals.
The flowchart of the proposed strategy is shown in Figure 7. Firstly, the angular distribution is converted from the power ratio by Equation (8); Secondly, the number of source signals is estimated through the KDE algorithm followed by the peak density detection; Afterwards, the contribution degree of the source signal in the observed signal is calculated by the contribution degree function based on the cosine distance . Finally, the TF soft mask matrix is constructed based on the contribution degree , and the separated TF signals are reconstructed.
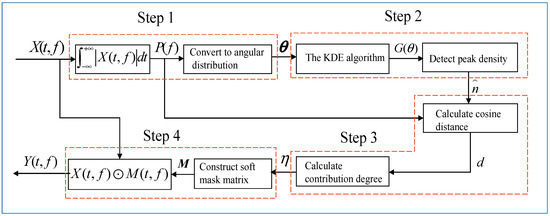
Figure 7.
The flowchart of the proposed method.
4. Experimental Results and Analysis
Our simulations are aimed at investigating the anti-aliasing performance and anti-noise performance of the proposed algorithm. To measure the degree of spectrum aliasing of the source signals, we define the degree of spectrum aliasing :
where represents the source signal spectrum bandwidth, and represents the maximum aliasing width between the source signal spectrum and the adjacent signal spectrum.
Since the “boundary effect” of STFT has an impact on the separation performance [10], we selected the Kaiser window as the window function. The evaluation criteria of separation performance were applied in our simulations, which include the source-to-distortion ratio (SDR), the source-to-interferences ratio (SIR), the source-to-artifacts ratio (SAR) [23], and the separated bit error rate (BER). In order to obtain bitstream information, the coherent demodulation method was used to demodulate the separated source signals. The mixed signals were separated by the SCA algorithm proposed in this paper and the literatures [8,10]. The comparison algorithm in [8] belonged to the classic two-stage method, and [10] used the TF masking method to separate the source signal.
4.1. Simulation 1: The Selection of Scaling Factor in the Contribution Degree Function
In this simulation, we verified the impact of the scaling factor on the separation performance of the proposed algorithm. The simulation was conducted under the condition of additive white Gaussian noise with a signal-to-noise ratio (SNR) of 16.4 dB. It is assumed that the three signals with different modulation (2ASK/BPSK/QPSK) are mixed instantaneously, in which the symbol rate of the signals are 5 × 106, 5 × 106, 10 × 106 B, respectively. The modulation carrier frequencies are 13.5, 20, and 26.5 MHz, respectively, with the of each signal being 35%. The mixing matrix is
The separation performance with different is shown in Figure 8; the bigger value is, the better the separation performance is. It can be seen that, with increasing, the SIR decreased significantly while the SAR and SDR remained almost constant. Thus we take as 0.5 in the following simulation experiments. Figure 9 and Figure 10 show the waveforms of the source signals and their mixed signals, respectively. Comparatively, Figure 11 shows the waveforms of the signals separated by the proposed algorithm with . It can be seen that the waveforms of the separated signals are basically consistent with the source signals. Although the waveforms have some distortion at the junction of bit 0 and bit 1, which is caused by the “boundary effect” of STFT, it does not affect the subsequent demodulation and judgment. Figure 12 represents the waveforms after coherent demodulation. The bit data can be recovered by setting the appropriate judgment level.
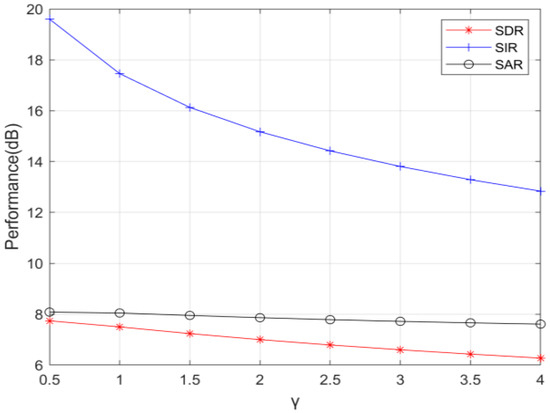
Figure 8.
The separation performance with different .
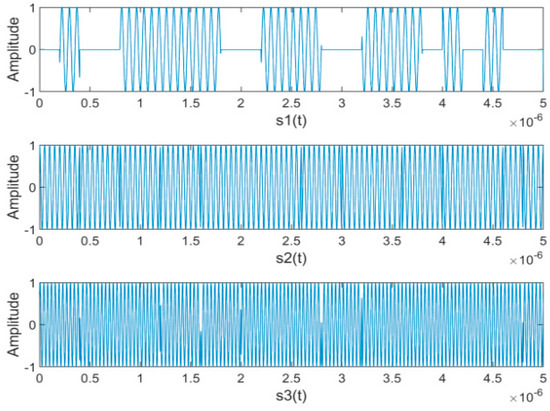
Figure 9.
The waveforms of source signals.
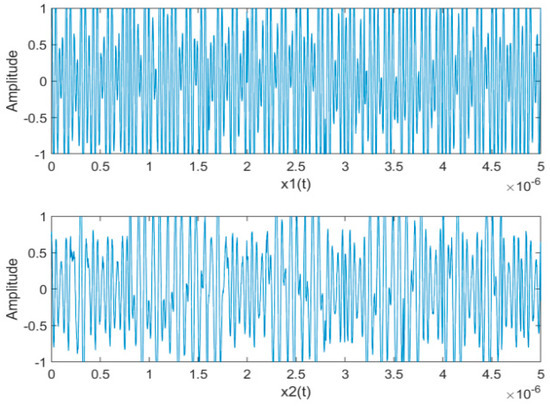
Figure 10.
The waveforms of mixed signals.
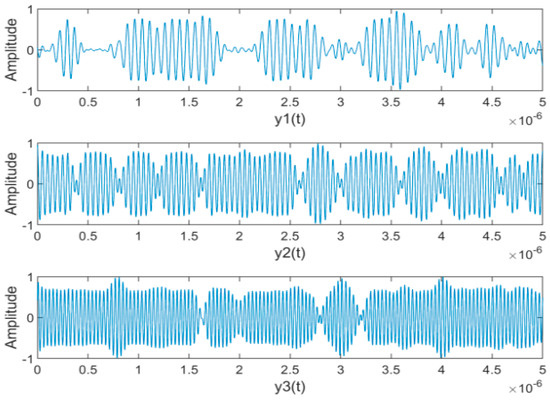
Figure 11.
The waveforms of separated signals.
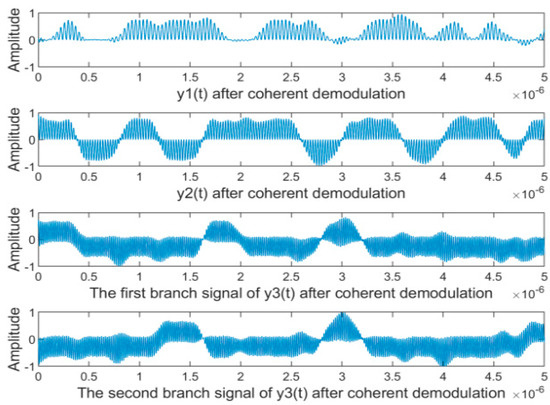
Figure 12.
The waveforms of separated signals after coherent demodulation.
4.2. Simulation 2: The Anti-Aliasing Performance Simulation
In order to analyze the anti-aliasing performance for signals with different modulation methods, two sets of signals were used as the source signals, which respectively were three signals with the same BPSK modulation and three signals with different modulation (2ASK/BPSK/QPSK). The symbol rate of a single source signal is 5 × 106 B. The modulation carrier frequencies were designed according to different . In this simulation, it is assumed that the source signals propagate in two channels before being received by the sensors, and the SNR is 15 dB. The first channel of signals arrived instantaneously, and the corresponding mixing matrix is
The second channel of signals arrived with delay; the signal propagation delay matrix and the corresponding mixing matrix are
The SDR and BER of the separated signals with the increase in are shown in Figure 13 and Figure 14. From the simulation results, it can be seen that in the environment with the SNR of 15 dB, as the source signal spectrum aliasing gradually intensifies, the separation performance of the proposed algorithm and the comparison algorithms are reduced to varying degrees. However, for signals with the same BPSK modulation (Figure 13), the average of the separated signals by the proposed algorithm is increased by 1.05 and 2.35 dB compared with the comparison algorithms. For signals with different modulation (Figure 14), the average of the separated signals by the proposed algorithm is increased by 0.68 and 2.48 dB. The BER is significantly lower than that of the comparison algorithms. As a result, the anti-aliasing performance of the algorithm in this paper is excellent.
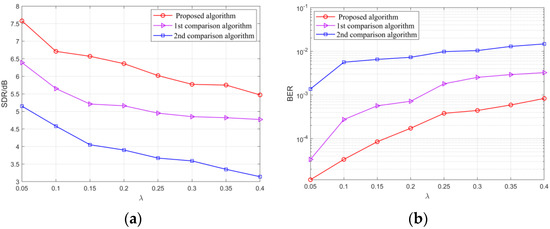
Figure 13.
(a) The SDR of three BPSK signals with different ; (b) The BER of three BPSK signals with different . The 1st and 2nd comparison algorithms are given in literatures [8,10], respectively.
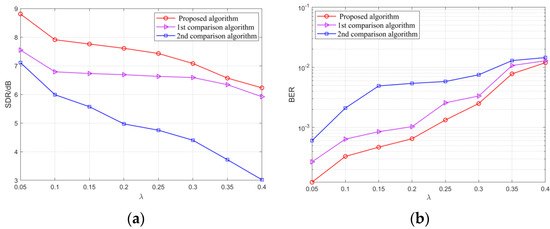
Figure 14.
(a) The SDR of different modulation signals with different ; (b) The BER of different modulation signals with different . The 1st and 2nd comparison algorithms are given in literatures [8,10], respectively.
4.3. Simulation 3: Simulation of Algorithm Anti-Noise Performance
In this simulation, the carrier frequency of each of the two groups of source signals was set to 14 MHz, 20 MHz, and 26 MHz, and the was fixed at 40% correspondingly. In the environment of the SNR from 5 to 30 dB, the method in simulation two was used to mix the source signals. The SDR and BER of the separated signals with the increase in the SNR are shown in Figure 15 and Figure 16:
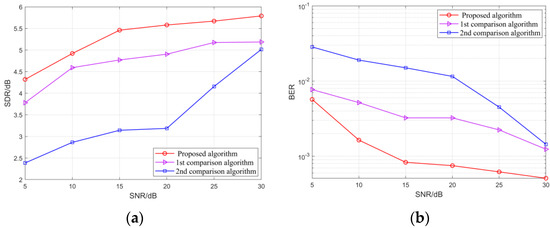
Figure 15.
(a) The SDR of three BPSK signals under different SNR; (b) The BER of three BPSK signals under different SNR. The 1st and 2nd comparison algorithms are given in literatures [8,10], respectively.
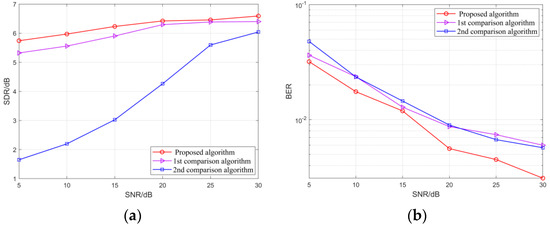
Figure 16.
(a) The SDR of different modulation signals under different SNR; (b) The BER of different modulation signals under different SNR. The 1st and 2nd comparison algorithms are given in literatures [8,10], respectively.
It can be seen from Figure 15 and Figure 16 that, with the SNR increases, the separation performance of the algorithm proposed in this paper and the comparison algorithms have been effectively improved. However, compared with the comparison algorithms, the SDR and BER of the separated signals by the proposed algorithm are higher and lower, respectively, indicating that the signal separation performance is better. Especially for signals with the same BPSK modulation (Figure 15), when the SNR is 10, the BER of the separated signals is lower than 10−2. For signals with different modulation (Figure 16), the BER drops below 10−2 when the SNR reaches 20 dB.
5. Conclusions
In this paper, we have discussed an underdetermined mixed blind signal separation method with the application of TF overlapped communication signals. The classical SCA methods to solve the UBSS problem require high sparsity of the signal. For TF overlapped signals, the classical SCA methods cannot be applied to such problems. To tackle this issue, we propose a novel method for separating TF overlapped signals based on the SCA algorithm. The core idea of the method is to construct a reasonable TF soft mask matrix by designing a contribution degree function. In the proposed method, we utilize the KDE algorithm to obtain the angle probability density distribution, followed by which the source number is estimated by detecting the peak points of the distribution. Then the contribution degree function is designed to generate the contribution degree, based on which the TF soft mask matrix is constructed to obtain the reconstructed TF signal. The sparsity requirement of the algorithm is reduced by constructing a reasonable TF soft mask matrix, which makes the separation algorithm suitable for separating TF overlapped signals. Compared with the classical SCA algorithm, the most significant contribution of the proposed algorithm is to expand the application scope of the SCA algorithm, which no longer requires the signal to have sparsity in the TF domain. In addition, the source estimation process prior to separation enables it to adapt to the case in which the number of sources is unknown. The algorithm’s anti-aliasing ability and anti-noise ability are simulated and verified by simulation, which demonstrates that the proposed method enables to overcome the poor performance of blind separation for TF aliasing communication signals by classical separation algorithms.
Author Contributions
Conceptualization, H.M. and X.Z.; methodology, H.M. and X.Z.; writing—original draft preparation, H.M.; writing—review and editing, X.Z., L.Y., X.W. and Y.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
Acknowledgments
The authors would like to thank the anonymous reviewers and the editors for helping improve this work.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
| TF | Time–frequency |
| KDE | Kernel density estimation |
| BSS | Blind source separation |
| ICA | Independent component analysis |
| UBSS | Underdetermined blind source separation |
| SCA | Sparse component analysis |
| RF | Radio frequency |
| STFT | Short-time Fourier transform |
| SSP | Single-source-point |
| ISTFT | Inverse short-time Fourier transform |
| SDR | Source-to-distortion ratio |
| SIR | Source-to-interferences ratio |
| SAR | Source-to-artifacts ratio |
| BER | Bit error rate |
| SNR | Signal-to-noise ratio |
References
- Wei, C.; Hua, P.; Junhui, F. A Blind Separation Method of PCMA Signals Based on MSGibbs Algorithm. J. Phys. Conf. Ser. 2019, 1168, 052050. [Google Scholar]
- Miao, W.; Xiao-xia, C.; Ke-fan, Z. A Blind Separation of Variable Speed Frequency Hopping Signals based on Independent Component Analysis. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 144–148. [Google Scholar] [CrossRef]
- Sharma, R. Musical Instrument Sound Signal Separation from Mixture using DWT and Fast ICA Based Algorithm in Noisy Environment. Mater. Today Proc. 2020, 29, 536–547. [Google Scholar] [CrossRef]
- Ziani, S.; Jbari, A.; Bellarbi, L.; Farhaoui, Y. Blind maternal-fetal ECG separation based on the time-scale image TSI and SVD–ICA methods. Procedia Comput. Sci. 2018, 134, 322–327. [Google Scholar] [CrossRef]
- Luo, Z.; Li, C.; Zhu, L. A comprehensive survey on blind source separation for wireless adaptive processing: Principles, perspectives, challenges and new research directions. IEEE Access 2018, 6, 66685–66708. [Google Scholar] [CrossRef]
- Ma, B.; Zhang, T. Single-channel blind source separation for vibration signals based on TVF-EMD and improved SCA. IET Signal Process. 2020, 14, 259–268. [Google Scholar] [CrossRef]
- Zhen, L.; Peng, D.; Yi, Z.; Xiang, Y.; Chen, P. Underdetermined blind source separation using sparse coding. IEEE Trans. Neural Netw. Learn. Syst. 2016, 28, 3102–3108. [Google Scholar] [CrossRef] [PubMed]
- Fang, B.; Huang, G.; Gao, J. Underdetermined blind source separation for LFM radar signal based on compressive sensing. In Proceedings of the 2013 25th Chinese Control and Decision Conference (CCDC), Guiyang, China, 25–27 May 2013; pp. 1878–1882. [Google Scholar]
- Fu, W.; Chen, J.; Yang, B. Source recovery of underdetermined blind source separation based on SCMP algorithm. IET Signal Process. 2014, 11, 877–883. [Google Scholar] [CrossRef]
- Yu, G. An Underdetermined Blind Source Separation Method with Application to Modal Identification. Shock. Vib. 2019, 2019, 1637163. [Google Scholar] [CrossRef]
- Cobos, M.; Lopez, J.J. Maximum a posteriori binary mask estimation for underdetermined source separation using smoothed posteriors. IEEE Trans. Audio Speech Lang. Process. 2012, 20, 2059–2064. [Google Scholar] [CrossRef]
- Kumar, M.; Jayanthi, V.E. Underdetermined blind source separation using CapsNet. Soft Comput. 2020, 24, 9011–9019. [Google Scholar] [CrossRef]
- Li, Y.; Nie, W.; Ye, F.; Lin, Y. A mixing matrix estimation algorithm for underdetermined blind source separation. Circuits Syst. Signal Process. 2016, 35, 3367–3379. [Google Scholar] [CrossRef]
- Liu, Z.; Li, L.; Lv, D.; Pan, N. Novel source recovery method of underdetermined time-frequency overlapped signals based on submatrix transformation and multi-source point compensation. IEEE Access 2019, 7, 29610–29622. [Google Scholar] [CrossRef]
- Reju, V.G.; Koh, S.N.; Soon, I.Y. Underdetermined convolutive blind source separation via time-frequency masking. IEEE Trans. Audio Speech Lang. Process. 2009, 18, 101–116. [Google Scholar] [CrossRef]
- Reddy, A.M.; Raj, B. Soft mask methods for single-channel speaker separation. IEEE Trans. Audio Speech Lang. Process. 2007, 15, 1766–1776. [Google Scholar] [CrossRef]
- Duan, T.; Zhang, X. A solution to blind separation of convolutive communication mixtures in frequency domain. In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, China, 21–23 April 2012; pp. 2330–2333. [Google Scholar]
- Ma, B.; Zhang, T.; An, Z.; Song, T.; Zhao, H. A blind source separation method for time-delayed mixtures in underdetermined case and its application in modal identification. Digit. Signal Process. 2021, 112, 103007. [Google Scholar] [CrossRef]
- Li, C.; Zhu, L.; Luo, Z. Underdetermined blind source separation of adjacent satellite interference based on sparseness. China Commun. 2017, 14, 140–149. [Google Scholar] [CrossRef]
- Lu, J.; Cheng, W.; He, D.; Zi, Y. A novel underdetermined blind source separation method with noise and unknown source number. J. Sound Vib. 2019, 457, 67–91. [Google Scholar] [CrossRef]
- Özbek, M.E. Determining the Number of Sources with Diagonal Unloading in Single-Channel Mixtures. Circuits Syst. Signal Process. 2021, 40, 5483–5499. [Google Scholar] [CrossRef]
- Węglarczyk, S. Kernel density estimation and its application. ITM Web Conf. 2018, 23, 00037. [Google Scholar] [CrossRef]
- Vincent, E.; Gribonval, R.; Fevotte, C. Performance measurement in blind audio source separation. IEEE Trans. Audio Speech Lang. Process. 2006, 14, 1462–1469. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).