Efficient Mobile Vehicle Data Sharing Scheme Based on Consortium Blockchain
Abstract
:1. Introduction
- We design a mobile vehicle data security sharing model based on the consortium blockchain.
- The Stackelberg game is used to ensure data exchange efficiency between vehicles (data sellers) and demand entities (data buyers, such as traffic scheduling centers and autonomous driving companies). We adopt a special architecture to provide sufficient security for privacy and data sharing of both, to improve the system data transmission efficiency.
- We conduct a set of simulations to show that the proposed data sharing scheme can improve the data transmission efficiency and that the privacy of vehicles is guaranteed.
2. System Model
2.1. System Model
2.2. Assumptions of the Data Sharing Model
- Figure 1 shows the details of the data exchange between different entities. The data demander and the RSU use cables to realize B2R communication, while the RSUs communicate with each other through R2R, which also requires cables. Since the RSU and the moving vehicles communicate with each other through V2R, we assume that there are a set of equally spaced RSUs deployed on the road, and the communicable range radius of the RSUs is described as . represents the position of the RSU , and is the position of the moving vehicle , whenwe set that the moving vehicle and in produce a contact (here, is Euclidean distance, and denote the time points before and after ), the vehicle and the RSU establish a data link;
- Divide the whole time duration into a series of time slots; the data sharing market for vehicles is explored within a specific time period;
- Regulate data sharing through smart contracts on RSU; the RSU is completely neutral between buyers and sellers, but it will also give appropriate assistance when the requests come from legal entities;
- There are several data buyers and sellers active in each time slot. For the convenience of research, only the data sharing activities of buyer and the seller managed by RSU are discussed. Of course, other situations can also be represented by the proposed system model;
- We consider the shared price standard for all data to be unified. In addition, for the buyer, the purpose of the data is to conduct traffic flow analysis, automatic driving analysis training, etc. The larger the amount of data, the more accurate the analysis results and the better the training effect that can be obtained.
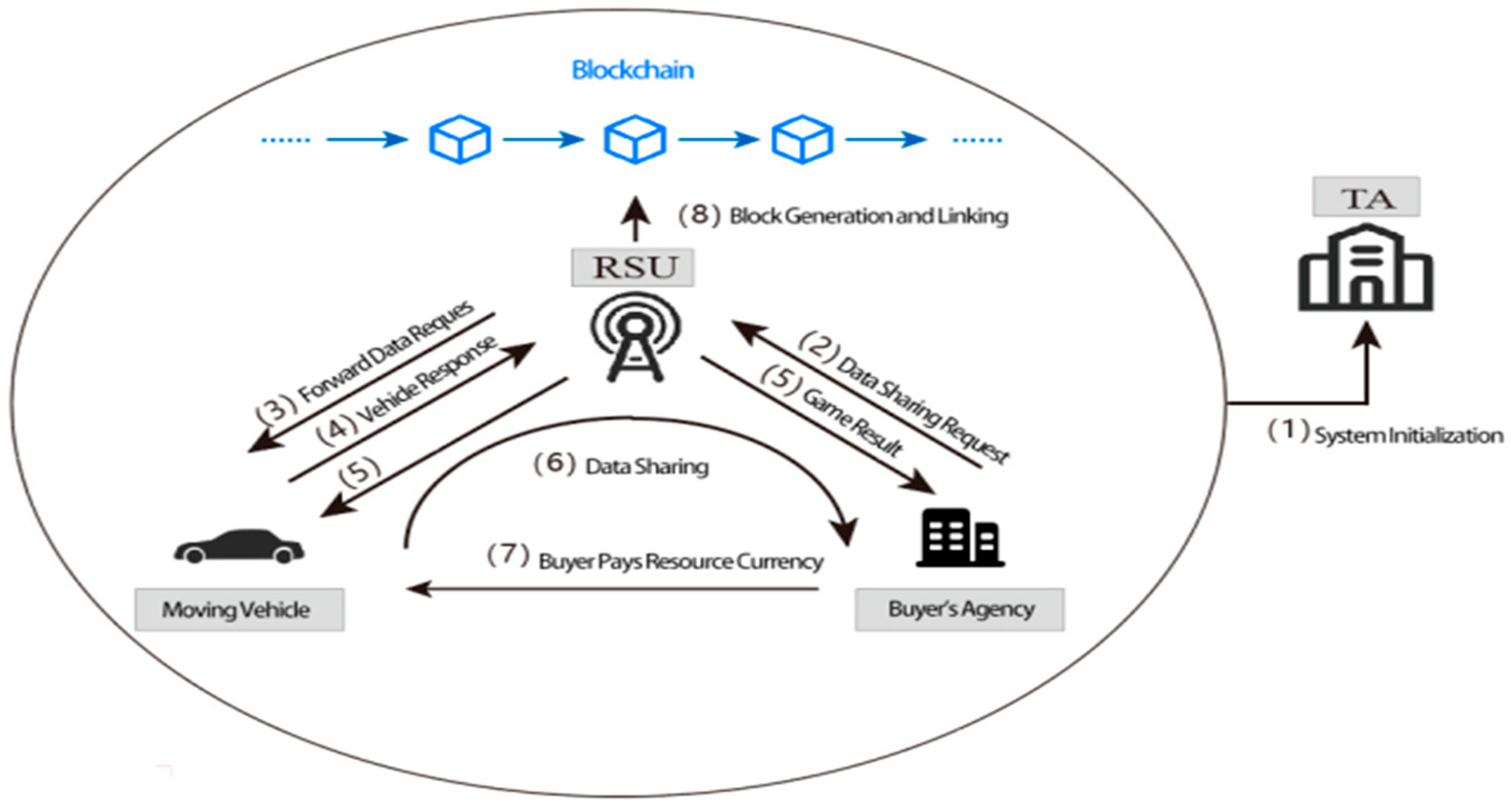
3. Data Sharing Process
- System initialization
- 2.
- The data buyer initiates a data sharing request
- 3.
- RSU acquires the buyer’s request and broadcasts it to moving vehicles within the communication area
- 4.
- The mobile vehicle responds to the RSU
- 5.
- RSU plays the game and feeds back the results to both parties
- 6.
- Data sharing and payment
- 7.
- Block generation and linking to the blockchain
- 8.
- After RSU generates a data sharing record, it saves it in the memory pool and then informs all RSU nodes. These nodes will also store the record after being notified. The RSU fuses the data sharing records in the memory pool together to obtain a new block during a time period;
- 9.
- All RSU nodes use the POW workload proof mechanism to compete for accounting rights. The essence of the POW mechanism is to continuously adjust the input value of a hash function to obtain the target value. In the block generation time period, the RSU that obtains the qualified random number in the shortest time is the accounting node;
- 10.
- The accounting node broadcasts its own block within the network range. After other RSUs determine that the accounting node has obtained the qualified value, it will not continue to calculate, and then verifies the latter’s block. The final verification result will be reported to the accounting node in the form of “valid” or “invalid”;
- 11.
- The accounting node counts all notifications. When more than half of the notifications are valid, it proves that the block is valid. At this time, the accounting node establishes a connection between the block and the copy of the local consortium blockchain. It is valid for all RSUs, which perform the same operation of establishing a connection;
- 12.
- After judging the block to be valid, the accounting node successfully “mines”. The system will award resource coins, and in this way, it will be motivated to continue “mining”. In addition, the accounting RSU retrieves the data sharing records contained in the memory pool, identifies all of the mobile vehicles participating in the data sharing, determines the degree of participation and reward resource coins, and directly deposits coins in the vehicle’s wallet to encourage them to continue data sharing. After the current round of consensus is completed, it will enter the next round.
4. Problem Formulation and Solving
4.1. Stackelberg Game Scheme Modeling
4.2. Stackelberg Game Solution
4.2.1. Problem Analysis
4.2.2. Algorithms for Achieving Stackelberg Equalization
- Based on the buyer’s bid , use Formula (8) to find the optimal decision of each seller’s vehicle, and then, based on the decision set of all sellers and the buyer’s bid , the buyer’s benefit function can be calculated. For the sake of convenience and differentiation, we use , which represents the value of the benefit function in the case of the bid from the buyer;
- According to the buyer’s bid , we find the seller’s decision set and the buyer’s benefit, using , which represents the buyer’s benefit;
- Determine the relationship with the size of and ; if , the upper limit of appears in the to interval, the interval is reduced, and . Otherwise, the upper limit of appears in the interval from to , the interval is reduced, and .
5. Simulation Analysis
5.1. Performance Analysis of the Stackelberg Game Solution Scheme
5.1.1. Simulation Setting
- SPRS (Set Price by Response Time Scheme): After the RSU sends the request from the buyer to the vehicle, the shorter the feedback time of the vehicle giving priority to trade with the buyer, and the buyer tends to purchase all the data provided by it . The shorter the vehicle feedback time, the higher the unit price of the data, and the price can be obtained. Prices can be determined by . Here, represents the coefficient of adjusting the price, is the response time of vehicle. Under the scheme, when the seller tends to give feedback faster, the buyer can obtain the data in a shorter time period. In the process of simulation analysis, the response time of the vehicle is set randomly to imitate the feedback situation of each vehicle, which is more consistent with reality;
- POS (Purchase from Other Data Providers Scheme): The buyer trades the data at the market price directly, with other institutions.
5.1.2. Simulation Analysis
- The relationship between the maximum amount of data and income that the seller is willing to sell to the buyer.
- 2.
- The impact of vehicle density on buyers’ income
- 3.
- Impact of the inconvenience parameters on the buyer’s benefit and cost
5.2. Performance Analysis of the Consortium Blockchain Framework
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Lv, Z.; Qiao, L.; Hossain, M.S.; Choi, B.J. Analysis of Using Blockchain to Protect the Privacy of Drone Big Data. IEEE Netw. 2021, 35, 44–49. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, B.; Wu, S. An architecture of cloud-assisted information dissemination in vehicular networks. IEEE Access 2016, 4, 2764–2770. [Google Scholar] [CrossRef]
- Guru, D.; Perumal, S.; Varadarajan, V. Approaches towards Blockchain Innovation: A Survey and Future Directions. Electronics 2021, 10, 1219. [Google Scholar] [CrossRef]
- Peng, C.; Wu, C.; Gao, L.; Zhang, J.; Yau, K.A.; Ji, Y. Blockchain for Vehicular Internet of Things: Recent Advances and Open Issues. Sensors 2020, 20, 5079. [Google Scholar] [CrossRef] [PubMed]
- Li, C.; Fu, Y.; Yu, F.R.; Luan, T.H.; Zhang, Y. Vehicle Position Correction: A Vehicular Blockchain Networks-Based GPS Error Sharing Framework. IEEE Trans. Intell. Transp. Syst. 2021, 22, 898–912. [Google Scholar] [CrossRef]
- Rongxing, L.; Xiaodong, L.; Xuemin, S. SPRING: A social-based privacy-preserving packet forwarding protocol for vehicular delay tolerant networks. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Verma, M.; Huang, D. SeGCom: Secure group communication in VANETs. In Proceedings of the 2009 6th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 10–13 January 2009; pp. 1–5. [Google Scholar]
- Singh, M.; Kim, S. Trust bit: Reward-based intelligent vehicle commination using blockchain paper. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 62–67. [Google Scholar]
- Ming, Y.; Cheng, H. Efficient certificateless conditional privacy-preserving authentication scheme in VANETs. Mob. Inf. Syst. 2019, 2019, 7593138. [Google Scholar] [CrossRef] [Green Version]
- Liu, H.; Zhang, Y.; Yang, T. Blockchain-enabled security in electric vehicles cloud and edge computing. IEEE Netw. 2018, 32, 78–83. [Google Scholar] [CrossRef]
- Zhu, J.; Xu, W. Real-Time Data Filling and Automatic Retrieval Algorithm of Road Traffic Based on Deep-Learning Method. Symmetry 2021, 13, 1. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling Localized Peer-to-Peer Electricity Trading among Plug-in Hybrid Electric Vehicles Using Consortium Blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Lal, N.; Kumar, S.; Chaurasiya, V.K. A Road Monitoring Approach with Real-Time Capturing of Events for Efficient Vehicles Safety in Smart City. Wirel. Pers. Commun. 2020, 114, 657–674. [Google Scholar] [CrossRef]
- Cheng, X.; Huang, Z.; Chen, S. Vehicular communication channel measurement, modeling, and application for beyond 5G and 6G. IET Commun. 2020, 14, 3303–3311. [Google Scholar] [CrossRef]
- Wang, Q.; Zhao, H.; Wang, Q.; Cao, H.; Aujla, G.S.; Zhu, H. Enabling secure wireless multimedia resource pricing using consortium blockchains. Future Gener. Comput. Syst. 2020, 110, 696–707. [Google Scholar] [CrossRef]
- Wu, Q.; Hao, J.K. A clique-based exact method for optimal winner determination in combinatorial auctions. Inf. Sci. 2016, 334, 103–121. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2018, 126, 45–58. [Google Scholar] [CrossRef]
- Pappalardo, G.; Cafiso, S.; Di Graziano, A.; Severino, A. Decision Tree Method to Analyze the Performance of Lane Support Systems. Sustainability 2021, 13, 846. [Google Scholar] [CrossRef]
- Jiang, Y.; Shen, X.; Zheng, S. An Effective Data Sharing Scheme Based on Blockchain in Vehicular Social Networks. Electronics 2021, 10, 114. [Google Scholar] [CrossRef]
- Xu, C.; Zhu, K.; Yi, C.; Wang, R. Data Pricing for Blockchain-based Car Sharing: A Stackelberg Game Approach. In Proceeding of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2021; pp. 1–5. [Google Scholar]






Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, Y.; Yang, C.; Yang, J.; Nie, X. Efficient Mobile Vehicle Data Sharing Scheme Based on Consortium Blockchain. Appl. Sci. 2022, 12, 6152. https://doi.org/10.3390/app12126152
Tian Y, Yang C, Yang J, Nie X. Efficient Mobile Vehicle Data Sharing Scheme Based on Consortium Blockchain. Applied Sciences. 2022; 12(12):6152. https://doi.org/10.3390/app12126152
Chicago/Turabian StyleTian, Yaping, Chao Yang, Junjie Yang, and Xinming Nie. 2022. "Efficient Mobile Vehicle Data Sharing Scheme Based on Consortium Blockchain" Applied Sciences 12, no. 12: 6152. https://doi.org/10.3390/app12126152
APA StyleTian, Y., Yang, C., Yang, J., & Nie, X. (2022). Efficient Mobile Vehicle Data Sharing Scheme Based on Consortium Blockchain. Applied Sciences, 12(12), 6152. https://doi.org/10.3390/app12126152





