Strategy Mining for Inferring Business Information System User Intentions
Abstract
:1. Introduction
2. Related Works
2.1. Relevant Concepts
2.2. Intention Mining Applications
2.3. Suggested Future Works by Previous Authors
3. Materials
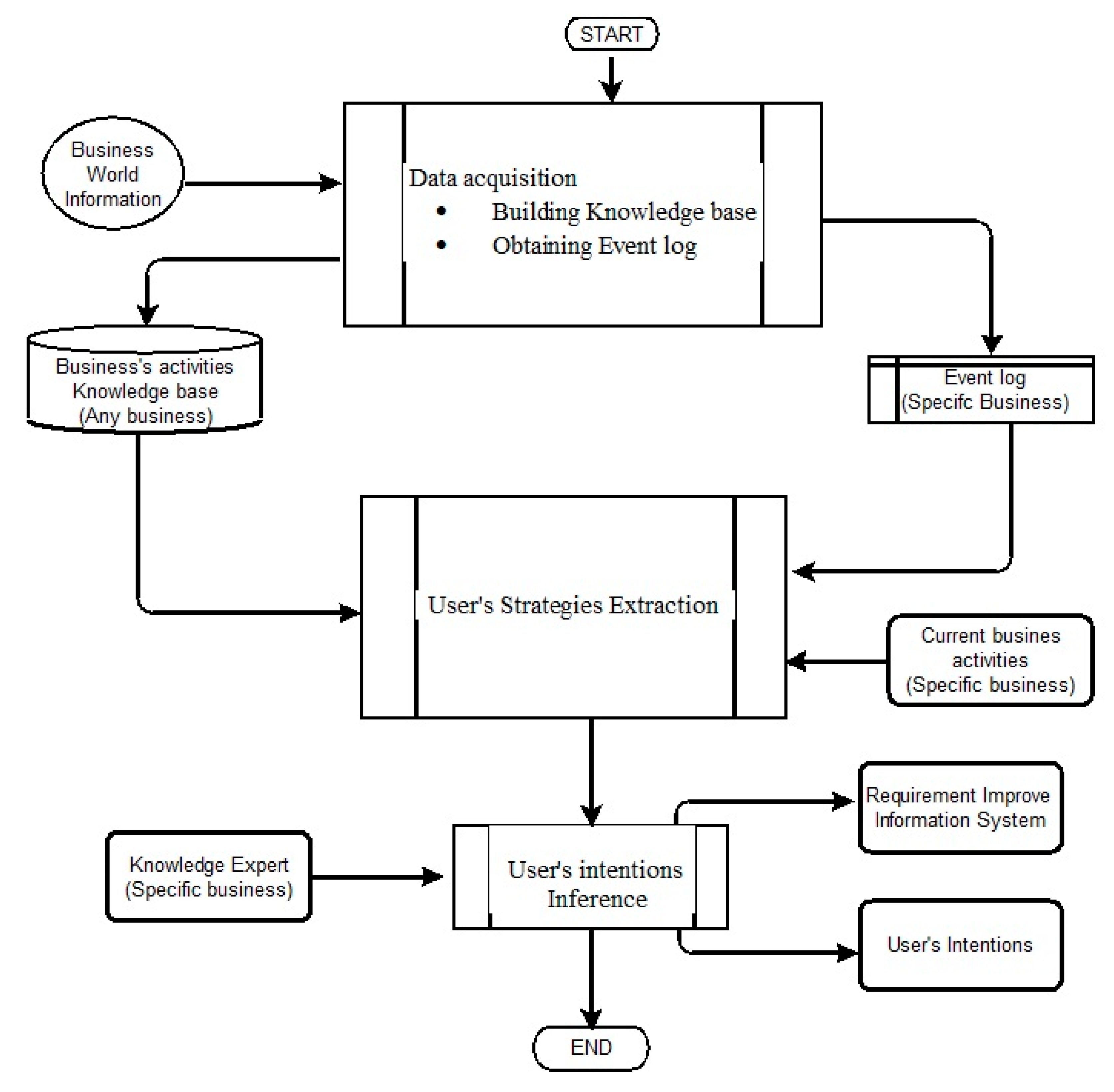
4. Method
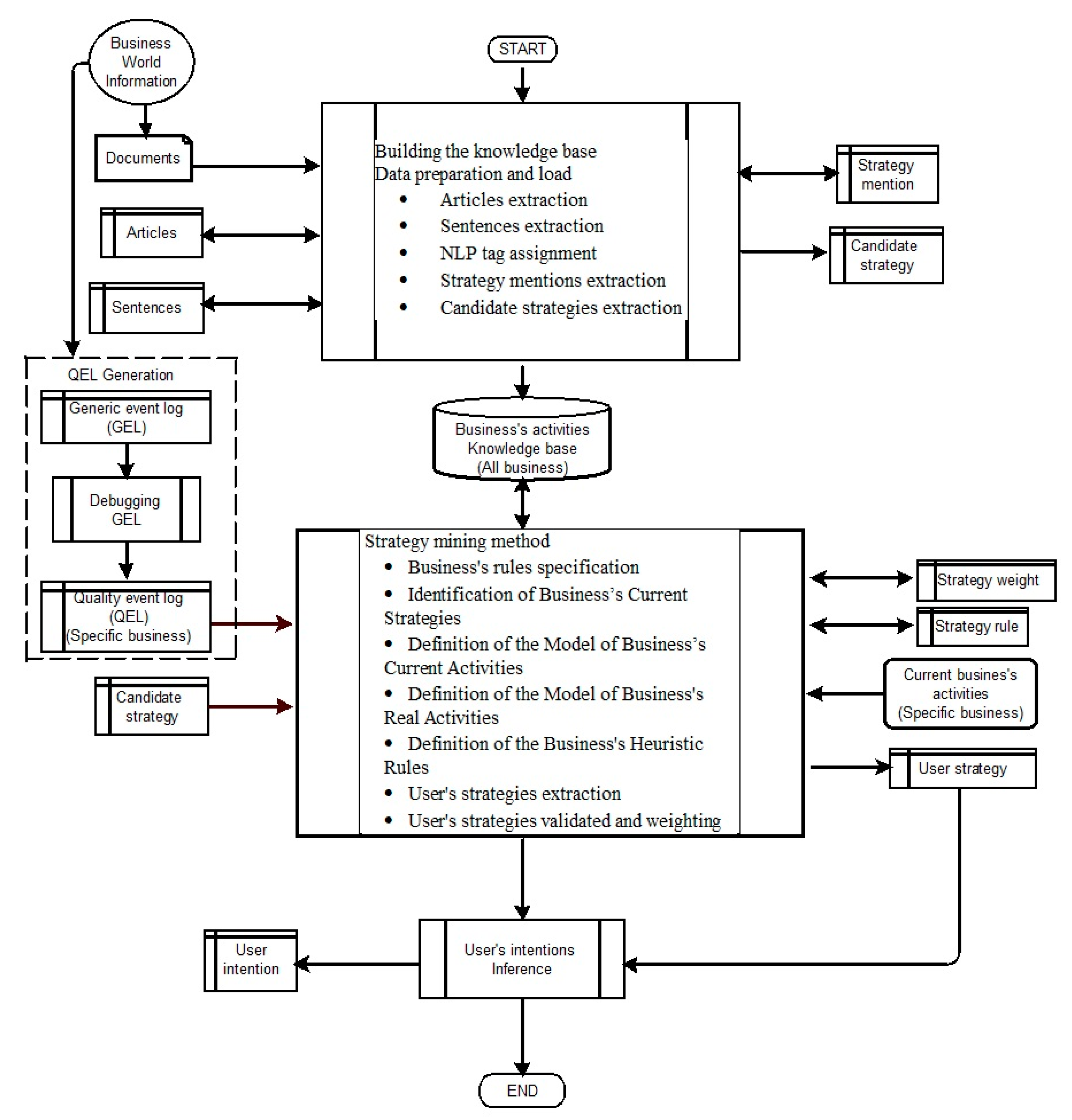
4.1. Building the Knowledge Base
4.1.1. Knowledge Base Structure
4.1.2. Data Preparation and Load
Article Extraction
Sentences Extraction
NLP Tag Assignment (POS Tag and NER Tag)
Strategy Mentions Extraction
Candidate Strategies Extraction
4.2. Quality Event Log Generation
4.3. Strategy Mining Method
4.3.1. Business Rules Specification
4.3.2. Identification of Business’s Current Strategies (BCS)
4.3.3. Definition of the Model of Business’s Current Activities
4.3.4. Definition of the Model of Business’s Real Activities
4.3.5. Definition of the Business’s Heuristic Rules (BHRs)
- The strategy is a sentence that has one of the following structures.
- The strategies contain words related to the business’s domain (sales).
4.3.6. User Strategy (US) Extraction
4.3.7. User Strategies—Validated and Weighted (USW)
- W:
- weight of BHRs.
- w:
- BHR compliance weighting by the US.
- n =
- count (BHRs): (“n”: number of business’s heuristic rules).
4.4. User Intentions Inference
5. Results
5.1. Business Knowledge Base
5.2. Quality Event Log
5.3. User strategies—Validated and Weighted
5.4. Inferred User Intentions
- In summary:
- Resources:
- Results:
6. Discussion
6.1. Strategy Mining Method
6.2. User Strategies
6.3. User Strategies Formalization
6.4. User Intentions
6.5. Internal and External Threats to This Work
6.6. Method Implications
- it would be applied in the identification of the gap between a business’s current processes and actual processes;
- defining and structuring user intentions based on their strategies;
- defining levels of abstraction for the executed processes according to user intentions;
- ranking user intentions according to the levels of process abstraction;
- generating intentional process models according to the predefined process abstraction levels;
- intentional process model validation;
- Identifying user behavior, and based on it, providing recommendations for improving business information systems.
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Aalst, W.V.; Adriansyah, A.; Medeiros, A.K.; Arcieri, F.; Baier, T.; Blickle, T.; Bose, J.C.; Brand, P.V.; Brandtjen, R.; Buijs, J.; et al. Process Mining Manifesto. In Business Process Management Workshops. BPM 2011; Daniel, F., Barkaoui, K., Dustdar, S., Eds.; Lecture Notes in Business Information Processing; Springer: Berlin/Heidelberg, Germany, 2012; Volume 99. [Google Scholar] [CrossRef] [Green Version]
- Lloyd, A.D.; Dewar, R.; Pooley, R. Legacy Information Systems and Business Process Change: A Patterns Perspective. Commun. Assoc. Inf. Syst. 1999, 2, 24. [Google Scholar] [CrossRef]
- Van der Aalst, W.M.P. Process Mining: Discovery, Conformance and Enhancement of Business Processes. In Media; Springer: Berlin/Heidelberg, Germany, 2011; Volume 136, Chapter 1. [Google Scholar]
- Teece, D.J. Business models, business strategy and innovation. Long Range Plan. 2020, 43, 172–194. [Google Scholar] [CrossRef]
- Khodabandelou, G.; Hug, C.; Salinesi, C. A novel approach to process mining: Intentional process models discovery. In Proceedings of the International Conference on Research Challenges in Information Science 2014, Marrakesh, Morocco, 28–30 May 2014. [Google Scholar] [CrossRef] [Green Version]
- Olson, K. Process Mining Concepts for Discovering User Behavioral Patterns in Instrumented Software. Ph.D. Thesis, Regis University, Denver, CO, USA, 2017. [Google Scholar]
- Khodabandelou, G. Contextual recommendations using intention mining on process traces: Doctoral consortium paper. In Proceedings of the International Conference on Research Challenges in Information Science 2013, Paris, France, 29–31 May 2013. [Google Scholar] [CrossRef]
- De Sa, C.; Ratner, A.; Ré, C.; Shin, J.; Wang, F.; Wu, S.; Zhang, C. Incremental knowledge base construction using DeepDive. VLDB J. 2017, 26, 81–105. [Google Scholar] [CrossRef] [Green Version]
- Ghasemi, M.; Amyot, D. From event logs to goals: A systematic literature review of goal-oriented process mining. Requir. Eng. 2020, 25, 67–93. [Google Scholar] [CrossRef]
- Díaz-Rodriguez, O.; Perez Hernandez, M. Quality Event Log to Intention Mining: A Study Case. In Proceedings of the 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), Gunupur, India, 13–14 March 2020. [Google Scholar] [CrossRef]
- Rowland Watkins, E. Principles of the business rule approach. Int. J. Inf. Manag. 2004, 24, 196–197. [Google Scholar] [CrossRef]
- Epure, E.V.; Hug, C.; Deneckere, R.; Brinkkemper, S. What Shall I Do Next? Intention Mining for Flexible Process Enactment. In Proceedings of the 26th International Conference on Advanced Information Systems Engineering (CAiSE), Thessalonique, Greece, 16–20 June 2014; pp. 473–487. [Google Scholar]
- Deneckere, R.; Hug, C.; Khodabandelou, G.; Salinesi, C. Intentional Process Mining: Discovering and Modeling the Goals behind Processes using Supervised Learning. Int. J. Inf. Syst. Modeling Des. 2014, 5, 22–47. [Google Scholar] [CrossRef] [Green Version]
- Huang, Q.; Xia, X.; Lo, D.; Murphy, G.C. Automating Intention Mining. IEEE Trans. Softw. Eng. 2018, 46, 1098–1119. [Google Scholar] [CrossRef] [Green Version]
- Cohan-Sujay, C.; Madhulika, Y. Intention Analysis for Sales, Marketing and Customer Service. In Proceedings of the COLING 2012: Demonstration Papers, Mumbai, India, 8–15 December 2012; pp. 33–40. Available online: https://aclanthology.org/C12-3005.pdf (accessed on 20 December 2021).
- Diaz, O.; Perez, M.; Lascano, J. Literature Review about Intention Mining in Information Systems. J. Comput. Inf. Syst. 2021, 61, 295–304. [Google Scholar] [CrossRef]
- Khodabandelou, G.; Hug, C.; Deneckere, R.; Salinesi, C. Unsupervised discovery of intentional process models from event logs. In Proceedings of the 11th Working Conference on Mining Software Repositories, Hyderabad, India, 31 May–1 June 2015. [Google Scholar] [CrossRef] [Green Version]
- Khodabandelou, G.; Hug, C.; Deneckere, R.; Salinesi, C. Enterprise, Business-Process and Information Systems Modeling. Process Min. Versus Intent. Min. 2013, 147, 466–480. [Google Scholar] [CrossRef] [Green Version]
- Khodabandelou, G.; Hug, C.; Deneckere, R.; Salinesi, C. Supervised Intentional Process Models Discovery using Hidden Markov Models. In Proceedings of the IEEE 7th International Conference on Research Challenges in Information Science (RCIS), Paris, France, 29–31 May 2013. [Google Scholar] [CrossRef] [Green Version]
- Khodabandelou, G.; Hug, C.; Deneckere, R.; Salinesi, C. Supervised vs. Unsupervised Learning for Intentional Process Model Discovery. In Enterprise, Business-Process and Information Systems Modeling; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar] [CrossRef] [Green Version]
- Epure, E.; Hug, C.; Deneckere, R.; Brinkkemper, S. Intention Mining: A Solution to Process Participant Support in Process-Aware Information Systems; Department of Information and Computing Sciences, Utrecht University: Utrecht, The Netherlands, 2013. [Google Scholar]
- NewIR’16. 2021. Available online: http://goo.gl/forms/5i4KldoWIX (accessed on 20 March 2021).
- Díaz, O. 2022. Available online: https://github.com/OswaldoDiaz975/PythonCode_IntentionMining (accessed on 7 June 2022).
- Manning, C.; Surdeanu, M.; Bauer, J.; Finkel, J.; Bethard, S.; McClosky, D. Stanford CoreNLP bindings for other languages, The Stanford CoreNLP Natural Language Processing Toolkit. 2015, pp. 55–60. Available online: https://aclanthology.org/P14-5010 (accessed on 20 March 2021).
- Makings, A.; Barnard, B. The Heuristics of Entrepreneurs. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3342170 (accessed on 26 February 2019).
- Foss, N.J.; Saebi, T. Business models and business model innovation: Between wicked and paradigmatic problems. Long Range Plan. 2018, 51, 9–21. [Google Scholar] [CrossRef]
- Vasilev, J.; Kehayova-Stoycheva, M. Sales analysis by the rectangle method. Leonardo Electron. J. Pract. Technol. 2017, 30, 149–160. Available online: http://lejpt.academicdirect.org (accessed on 20 March 2019).
- Tan, Y.; Shi, Y.; Buarque, F.; Gelbukh, A.; Das, S.; Engelbrecht, A. Advances in Swarm and Computational Intelligence. In Proceedings of the 6th International Conference, ICSI 2015 held in conjunction with the Second BRICS Congress, CCI 2015 Beijing, China, 25–28 June 2015; p. 9142. [Google Scholar] [CrossRef]
- MYOB Enterprice Solutions. MYOB EXO Business White Paper. M470—Sales Analysis 2020. 2021, pp. 1–6. Available online: https://www.uil.co.nz/help/MYOBEXOBusiness_SalesAnalysisMatrix_whitepaper.pdf (accessed on 10 December 2021).
- Sales & Marketing Keyword. Columbia Greene Works. List of Resume Keywords and Competencies for Sales and Marketing 2020. Available online: https://www.resumeworld.ca/resume_best_practices/resume-keywords/sales resume-keywords.html (accessed on 20 November 2020).
| Previous Author | Aim | Data and Tools | Result |
|---|---|---|---|
| Present Work | Discovery the user intentions of business information system | NewsIR’16 repository Knowledge base for any business Event log for specific business Business rules Knowledge expert | User intentions, possibility of user behavior inference, and improving information system |
| Epure [12] | Automate the construction of intentional process models | Event log Hidden Markov models | Map Miner Method |
| Khodabandelou [5,7] | Toward the construction of process model topology | Eclipse UDC processes Map Miner Method | Intentional process models |
| Deneckere [13] | Design a technique to mine intentional models from traces of non-deterministic activities that follow a stochastic process | Activity traces Supervised machine learning | Intentional process models |
| Huang [14] | Classifying intentions by category | Linguistic patterns Issue reports | Intention categories Recommendations for software developers |
| Cohan-Sujay [15] | Analysis of intentional business functions that can be performed effectively on short texts | Short texts (simple sentences) Machine learning | Words that express intentions |
| De Sa [8] | Knowledge base construction | Deep Dive (databases and machine learning) | Knowledge base |
| Token Tag | Named Entity Recognition | Meaning |
|---|---|---|
| VB, VBD, VBG, VBN, VBP, VBZ | ACTIVITY | Verbs in all modes and times |
| NN, NNS | NOUN | Common nouns |
| NNP, NNPS | PERSON/ORGANIZATION | Nouns |
| JJ | ADJECTIVE | Adjectives |
| JJR | COMPARATIVE ADJECTIVE | Comparative adjectives |
| JJS | SUPERLATIVE ADJECTIVES | Superlative adjectives |
| RB | ADVERB | Adverbs |
| RBR | ADVERB ADJECTIVE | Comparative adverbs |
| RBS | ADVERB ADJECTIVES | Superlative adverbs |
| Strategy Name |
|---|
| 10-min |
| 22-year-old |
| 39-year-old |
| 6-foot-2 |
| ability |
| ability to accept |
| accept |
| accomplish goal |
| American news sales |
| approach |
| business show |
| business performance tdameritrade.com |
| busy |
| buy |
| economically |
| economy |
| efficient business show |
| forward-looking information involved |
| forward-looking statement is |
| forward-looking statement includes |
| negotiation for effective preparation |
| problem-solving negotiation |
| problem-solving techniques |
| quota set |
| sale |
| sale say |
| sell |
| seller amount |
| sensitive information included |
| technologically improve system |
| traditional custom |
| weakness knows best |
| work collaboratively |
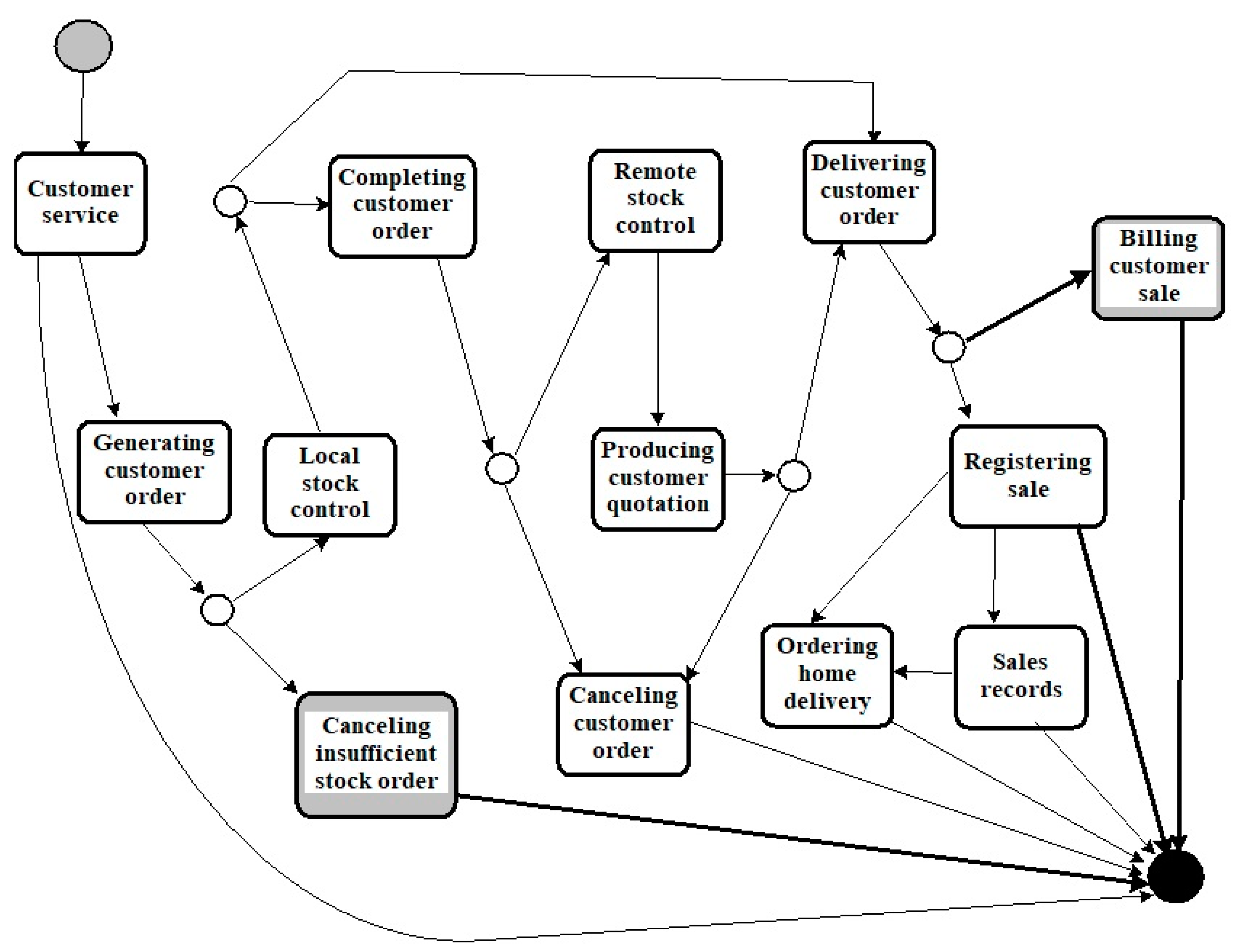
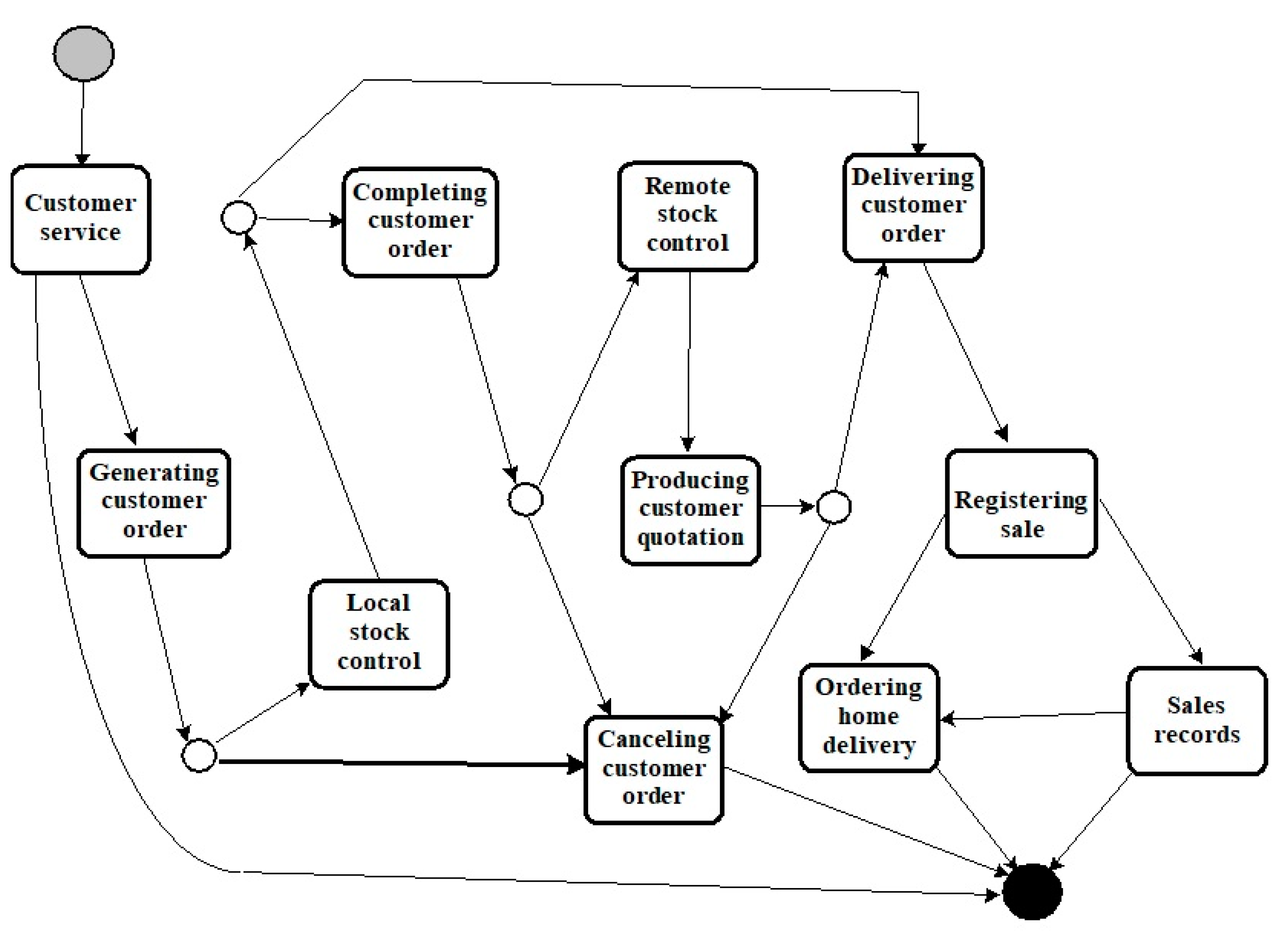
| Trace ID | Timestamp | Activity |
|---|---|---|
| 1 | 2019-11-20:10.20.30 | Customer service |
| 1 | 2019-11-20:15.20.31 | Generating customer order |
| 1 | 2019-11-20:23.10.34 | Canceling insufficient stock order |
| 2 | 2019-11-20:11.10.35 | Customer service |
| 3 | 2019-11-20:11.10.35 | Customer service |
| 3 | 2019-11-20:11.10.36 | Generating customer order |
| 3 | 2019-11-20:11.10.37 | Local stock control |
| 3 | 2019-11-20:11.10.38 | Delivering customer order |
| 3 | 2019-11-20:11.10.39 | Registering sale |
| 3 | 2019-11-20:11.10.40 | Sales records |
| 4 | 2019-11-20:10.21.41 | Customer service |
| 4 | 2019-11-20:15.21.42 | Generating customer order |
| 4 | 2019-11-20:16.21.43 | Local stock control |
| 4 | 2019-11-20:22.21.44 | Delivering customer order |
| 4 | 2019-11-21:08.21.46 | Registering sale |
| 4 | 2019-11-21:23.21.45 | Ordering home delivery |
| 5 | 2019-11-20:15.30.31 | Customer service |
| 5 | 2019-11-20:18.30.32 | Generating customer order |
| 5 | 2019-11-20:19.30.33 | Local stock control |
| 5 | 2019-11-20:20.30.34 | Delivering customer order |
| 5 | 2019-11-21:10.30.37 | Billing custom sale |
| 7 | 2019-11-21:14.30.43 | Customer service |
| 7 | 2019-11-21:14.35.44 | Generating customer order |
| 7 | 2019-11-21:14.50.45 | Local stock control |
| 7 | 2019-11-21:16.30.46 | Completing customer order |
| 7 | 2019-11-21:16.45.47 | Remote stock control |
| 7 | 2019-11-21:17.30.48 | Producing customer quotation |
| 8 | 2019-11-21:14.30.49 | Customer service |
| 8 | 2019-11-21:15.30.50 | Generating customer order |
| 8 | 2019-11-21:17.30.51 | Local stock control |
| 8 | 2019-11-21:18.30.52 | Completing customer order |
| 8 | 2019-11-21:19.30.53 | Remote stock control |
| 8 | 2019-11-21:17.50.54 | Producing customer quotation |
| 8 | 2019-11-21:17.55.55 | Canceling customer order |
| 9 | 2019-11-21:16.55.56 | Customer service |
| 9 | 2019-11-21:17.55.57 | Generating customer order |
| 9 | 2019-11-21:19.55.58 | Local stock control |
| 9 | 2019-11-21:23.15.02 | Completing customer order |
| 9 | 2019-11-21:23.35.31 | Remote stock control |
| 9 | 2019-11-22:09.55.42 | Producing customer quotation |
| 9 | 2019-11-22:11.55.25 | Delivering customer order |
| 9 | 2019-11-22:11.55.08 | Registering sale |
| 9 | 2019-11-22:12.55.33 | Sales records |
| 9 | 2019-11-22:20.55.12 | Ordering home delivery |
| Strategy Name | Weighting |
|---|---|
| billing custom sale | 0.75 |
| ordering home delivery | 0.5 |
| sale register | 0.33 |
| sale say | 0.33 |
| American news sales | 0.25 |
| pay seller amount | 0.25 |
| couple sales | 0.17 |
| news sales | 0.17 |
| sale | 0.17 |
| seller amount | 0.17 |
| buy | 0.08 |
| sell | 0.08 |
| Strategy | Intention |
|---|---|
| billing custom sale | Win over the customer |
| ordering home delivery | Customer satisfaction |
| sale register | Control the business |
| sale say | Advertising, promotion |
| American news sales | Listen to the competition cautiously |
| pay seller amount | Timely payments |
| couple sales | Complement yourself with a partner |
| news sales | |
| sale | |
| seller amount | Awards, incentives |
| buy | |
| sell |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Diaz, O.; Pérez, M. Strategy Mining for Inferring Business Information System User Intentions. Appl. Sci. 2022, 12, 5949. https://doi.org/10.3390/app12125949
Diaz O, Pérez M. Strategy Mining for Inferring Business Information System User Intentions. Applied Sciences. 2022; 12(12):5949. https://doi.org/10.3390/app12125949
Chicago/Turabian StyleDiaz, Oswaldo, and Maria Pérez. 2022. "Strategy Mining for Inferring Business Information System User Intentions" Applied Sciences 12, no. 12: 5949. https://doi.org/10.3390/app12125949
APA StyleDiaz, O., & Pérez, M. (2022). Strategy Mining for Inferring Business Information System User Intentions. Applied Sciences, 12(12), 5949. https://doi.org/10.3390/app12125949





