Abstract
Error detection and correction codes based on redundant residue number systems are powerful tools to control and correct arithmetic processing and data transmission errors. Decoding the magnitude and location of a multiple error is a complex computational problem: it requires verifying a huge number of different possible combinations of erroneous residual digit positions in the error localization stage. This paper proposes a modified correcting method based on calculating the approximate weighted characteristics of modular projections. The new procedure for correcting errors and restoring numbers in a weighted number system involves the Chinese Remainder Theorem with fractions. This approach calculates the rank of each modular projection efficiently. The ranks are used to calculate the Hamming distances. The new method speeds up the procedure for correcting multiple errors and restoring numbers in weighted form by an average of 18% compared to state-of-the-art analogs.
1. Introduction
Despite significant efforts, both in industry and science, high fault tolerance remains a serious problem in the management of large-scale IT systems.
The consequences of failures, regardless of their causes, can be eliminated using various methods by introducing data redundancy. Erasure codes, replication, and Resilient Distributed Dataset (RDD) [1] are the most important methods for ensuring fault tolerance in modern data storage and processing systems.
Replication is the simplest-to-implement (therefore, most widespread) method of introducing redundancy [2]. However, replication leads to significant overhead costs expressed in additional resources for duplicating data and functionality. In turn, erasure codes [3,4] are devoid of this drawback. Such codes counteract the partial loss of data and are based on a principle of antinoise coding (parity check). Erasure codes save significant costs and energy [3]. However, data recovery after failures is associated with high reconstruction costs and network traffic. The transition from replication to erasure codes and RDD is complicated by the need to update the hardware–software base and recode the entire volume of stored data. Nevertheless, there are examples of successful adoption of these technologies by Facebook [5] and Microsoft Azure [3].
This paper proposes a new approach to error correction codes based on a redundant residue number system (RRNS) [6,7]. Along with the Reed–Solomon codes [8], the Rabin dispersal algorithm [9], etc., RRNSs provide the functionality implemented by erasure codes and the functionality implemented by RDD algorithms. In addition, an important property of RNSs is the ability to perform arithmetic operations over encoded data. This property can be used in modern distributed data processing systems [10,11,12] and encrypted data processing schemes [13]. Therefore, RRNSs are a unique and versatile tool for a wide range of applications.
There are two main strategies for correcting errors in RRNSs. The first one involves syndrome decoding [14,15,16]: erroneous parts of the data are determined by comparing a special numerical syndrome calculated on the obtained data with the reference values. The second strategy is to restore error-free data based on the obtained code [17,18,19] by calculating the error magnitude and correcting the code during the decoding process. The authors [19] suggested a maximum likelihood decoding (MLD) approach to simplify the corrective decoding method by reducing the enumeration of values during decoding.
This paper proposes a modified method for corrective data decoding in RRNSs using MLD. Unlike the decoding method [19], this approach involves an alternative version of the Chinese Remainder Theorem (CRT) [20,21,22] for more efficient data restoration due to parallel execution of decoding and error correction. The CRT with fractions allows dividing the decoding process into two independent parts: determining the weighted characteristic of a number (a relative estimate of its magnitude) and decoding itself. The weighted characteristic can be directly used for error correction, and data decoding can be performed in parallel. The proposed modified modular projection method with MLD speeds up the procedure of error correction and number restoration in the weighted number system compared to the original method [19]. At the same time, it consumes many more hardware resources.
This paper is organized as follows: In Section 2, the existing research in the field of error correction in RRNSs is surveyed. A detailed introduction to RNSs, including the notations and preliminaries used below, is given in Section 3. Additionally, this section briefly describes MLD [19]. Section 4 presents the proposed method and analyzes its complexity. Section 5 is devoted to the hardware implementation of the proposed method, comparing it with the existing methods. The outcomes of this paper are summarized in Section 6.
2. Related Works
Error detection and correction codes based on a redundant residue number system (RRNS) are modern and powerful tools to control and correct arithmetic processing and data transmission errors. Algorithms that correct only single errors were considered and improved by several authors [6,23,24,25]. Decoding the magnitude and location of a single error is significantly less complex than detecting and correcting errors in multiple bits of RRNSs. It requires verifying a huge number of different possible combinations of erroneous residual digit positions in the error localization stage. The localization stage consumes the most time in the procedure for correcting multiple errors in RRNSs. All known methods for detecting and correcting multiple errors in RRNSs can be divided into three large groups: continuous fractions [26,27], syndrome decoding [14,15,16], and modular projections [17,18,19]. These groups of methods have advantages and drawbacks.
The methods with continuous fractions are based on the Euclidean recursive algorithm. After localization, erroneous remainders are corrected by expanding the moduli system using error-free remainders. For multiple errors in residual digits of large bit depth, the recursive Euclidean algorithm needs many iterations and becomes inefficient in hardware implementation.
The paper [16] presented an approach to correcting multiple errors in RRNSs using syndromes. Later, it was improved in [14,15]. According to [15], the residual digits in syndrome decoding are divided into three groups; seven categories of error positions are determined among them. The error magnitudes are distributed in three syndromes, which are used to categorize the errors accurately and localize the erroneous residual digits simultaneously from the six lookup tables. Syndromes can be calculated in parallel, and operations are performed in small moduli. This feature is an undoubted advantage of the approach, providing high-speed execution of the error correction procedure for RRNSs. Among the drawbacks of this method, note a rather strong constraint on the choice of redundant moduli:
where denotes the number of information moduli in an RRNS, and is the total number of RRNS moduli. A critical shortcoming of methods with syndrome decoding is that the volume of lookup tables sharply grows with an increase in the error multiplicity and the bit width of the residual digits. Searching through large lookup tables is time consuming and negates the benefit of efficiently calculated syndromes. Thus, methods with syndrome decoding are efficient only for small moduli sets.
The method with modular projections was pioneered in [17] and improved and extended to the case of multiple errors in the subsequent works [18,28]. With this approach, erroneous residual digits are localized by reducing the RRNS, deleting the number of remainders equal to the error multiplicity. The value represented in the RRNS falls into the legitimate range after excluding the erroneous residual digits. This process is similar to syndrome decoding. It requires estimating each possible combination of residual digit error locations. Methods with modular projections need no large lookup tables: this is an absolute advantage over methods with syndrome decoding. Other advantages include a weaker constraint on the choice of redundant moduli than in the case of syndrome decoding:
where denotes the number of information moduli in an RRNS, and is the total number of RRNS moduli. A critical shortcoming of such methods is the number of modular projections equal to , where denotes the maximum error multiplicity. Obviously, the number of modular projections grows fast with an increase in the error multiplicity, raising the number of computations accordingly.
The paper [19] proposed an essentially different method with modular projections: the number of projections was reduced by changing their construction procedure. The idea is to delete remainders instead of ones (the conventional approach). The algorithm for constructing modular projections and their number was refined in [29]. Since , the number of modular projections is significantly reduced, but it becomes necessary to check the Hamming distances according to maximum likelihood decoding (MLD). This approach eliminates the critical shortcoming of the rapidly growing number of projections and seems an optimal choice for correcting multiple errors in modular codes. The ideas and approaches [19] underlie the modified modular projection method with MLD; see Section 4. Using the Chinese Remainder Theorem with fractions [20,21,22] opens up new opportunities for parallelizing the algorithm and speeding up the procedure for correcting RRNS errors. Section 5 presents the hardware implementations of the original method [19] and the modified modular projection method with MLD on Field-Programmable Gate Array (FPGA). The hardware implementations partially involve the authors’ computing modules described in the earlier publications [30,31].
3. Residue Number System and Multiple Error Correction
3.1. Residue Number System
A residue number system (RNS) [7,32,33] is a non-weighted number system. In an RNS, an integer is represented by a -dimensional vector of the remainders in dividing it by positive coprimes called the RNS moduli. The magnitude of belongs to the range , where
and each remainder is the least nonnegative modulo residue of :
Note that when obtaining the RNS representation of , the modulus remainders are calculated independently and in parallel. The paper [30] considered the most effective methods for calculating the remainder of the division and presented schematic diagrams for their hardware implementation.
The inverse conversion, i.e., restoring the weighted representation of a number from its RNS representation, is a much more difficult task than the direct conversion. The weighted representation of a number (its weighted characteristic) can be found using the Chinese Remainder Theorem (CRT) [7], the CRT with fractions (CRTf) [20,21,22], or conversion to a mixed radix number system (MRNS) [34,35].
The modified multiple error correction method proposed below partially involves the CRT and CRTf.
3.2. Chinese Remainder Theorem
According to the Chinese Remainder Theorem (CRT), an integer is calculated from its RNS representation as follows [7]:
or equivalently,
where denotes the multiplicative inversion of , and is the number rank (a value showing how many times the sum in (3) exceeds the RNS range).
3.3. Chinese Remainder Theorem with Fractions
A number is converted to a weighted number system (WNS) using the Chinese Remainder Theorem with fractions (CRTf) [4,24,31]:
where
and denotes taking the fractional part of a number.
The value is called the approximate weighted characteristic of in the RNS representation.
We propose using a binary shift of fractions to implement this algorithm on a hardware base not supporting fractions (e.g., FPGA). The accuracy of the constants in (5), sufficient for correctly reconstructing the weighted representation of , was thoroughly estimated in [20]. A number X is converted to a WNS using the CRTf with the binary shift as follows:
where
and [4].
The CRTf allows converting RNS representations of numbers to the WNS ones efficiently on any computing platform: all calculations are reduced to operations well implemented in hardware. These operations include addition, multiplication, binary shifts, and discarding the most significant digits of a number [31].
3.4. Redundant Residue Number System
The residual representation of an error-free integer is unique for the range . This range is used for detecting and correcting errors in the RNS. Expanding the code space of the residual representation with additional residual bits, we form an -redundant residue number system (RRNS) with correcting properties.
An RRNS with is based on coprime moduli and the full range . The additional moduli, , are called the redundant moduli of the RRNS. The range corresponding to the first k information moduli from the n-dimensional vector is called the legitimate range. The range corresponding to the additional redundant (control) moduli is called the illegitimate range. The legitimate range is the required computational range of the number system, while the illegitimate range is necessary for error detection, localization, and correction.
When an error occurs, an integer within the legitimate range is converted to , where E is the error. The value falls into the illegitimate range if
- 1)
- , ,
- 2)
- the number of erroneous remainders does not exceed .
Thus, to detect an error, we should restore the number X from its RRNS representation . If the resulting value is smaller than the dynamic range of the RRNS (M), the number contains no errors of multiplicity and below; otherwise, the RRNS representation of X contains 1 or 2 or 3,..., or erroneous residual digits.
The number of erroneous residual digits detected and corrected is determined by the number of redundant moduli added. In the general case without special restrictions, the -RRNS with redundant moduli detects and corrects erroneous residual digits [7].
3.5. Modular Projection Method
The modular projection method is used to correct erroneous residual digits of numbers in the RRNS representation. Let an error be detected in a number written in the RRNS. The -RRNS allows correcting erroneous residual digits [7]. According to the classical modular projection method, or fewer errors are corrected in the following steps:
- 1)
- Constructing modular projections. A modular projection is obtained by deleting remainders in the original RRNS representation of the number. Deleting different sets of remainders, we construct different modular projections.
- 2)
- Obtaining the weighted representation (weighted characteristic) of each modular projection. The weighted representation of a number is its magnitude in the WNS. The weighted characteristic of a number depends on the inverse RNS-to-WNS conversion method.
- 3)
- Comparing the weighted representation (weighted characteristic) of each modular projection with the value (weighted characteristic) of the dynamic range. A modular projection whose weighted representation (weighted characteristic) does not exceed that of the dynamic range contains the correct remainders. Note that there can be correct modular projections, where is the number of erroneous digits, . In this case, the remainders deleted when constructing each correct projection will be erroneous.
- 4)
- Calculating the remainders on dividing the correct modular projection’s weighted representation by the moduli corresponding to the erroneous remainders. Note that correcting erroneous remainders is not required to decode correct data from the RRNS: the weighted representation of a correct modular projection is the corrected number written in the WNS. When using the weighted characteristic of a modular projection in step 3), it is necessary to perform an additional step for decoding: obtain the weighted representation of the number from its weighted characteristic.
For each projection, calculations are performed in parallel, which significantly reduces the total time to correct errors in RRNS codes. A critical drawback of this method is the fast-growing number of modular projections with an increase in the error multiplicity. An increase in the number of modular projections does not affect the total execution time of the error-correction procedure in RRNS codes due to the parallel computations for each projection. However, it sharply raises hardware costs [18]. This critical drawback can be overcome using the concept of maximum likelihood decoding (MLD) [19].
3.6. Modular Projection Method with MLD
The paper [19] improved the classical modular projection method to reduce the number of projections by changing their construction. When constructing a modular projection, the idea is to delete not residual bits of the -RRNS instead of ones, where is the maximum multiplicity of an error corrected by the -RRNS, and is the number of redundant moduli. The algorithm for constructing modular projections was described in detail in [29].
Such an approach to constructing modular projections allows for reducing their number to [29]. However, some incorrect projections fall into the legitimate RRNS range. To separate correct projections, we propose using maximum likelihood decoding (MLD) [19]. According to the MLD concept, an additional step is to calculate the Hamming distances between the erroneous number in the RRNS representation and each modular projection. In the RNS, the Hamming distance is defined as the number of distinct corresponding remainders. Let and be numbers written in the RNS with bases . Then the Hamming distance is given by
Therefore, we should find the remainders of the moduli deleted when constructing each projection.
Two conditions determine a correct projection:
- -
- The modular projection in the WNS (its weighted characteristic ) is smaller than the RRNS dynamic range (its weighted characteristic ).
- -
- The Hamming distance between the distorted number X′ and the modular projection in the RRNS does not exceed the value of the maximum multiplicity of errors corrected by this RRNS.
The following formula combines these conditions:
The remainders of the moduli deleted when constructing each projection can be calculated by extending the RNS moduli system [32] or restoring the number in the WNS and calculating the remainders of these moduli. These operations are resource-consuming and significantly increase the total time for correcting errors and restoring the number in the WNS.
4. Modified Modular Projection Method with MLD
Now consider a new method combining the advantages of the CRT, CRTf, and maximum likelihood projections [19]. The proposed modification concerns error localization and restoration of a correct number in the WNS; error detection is identical for the original method [19] and the modified method proposed below. In this regard, the description of error detection is omitted.
According to [19], each projection is restored in the WNS using the CRT. The resulting projections are employed to calculate the values of the missing remainders. Next, the Hamming distances are calculated for each projection, and the correct projection is selected (Figure 1a).
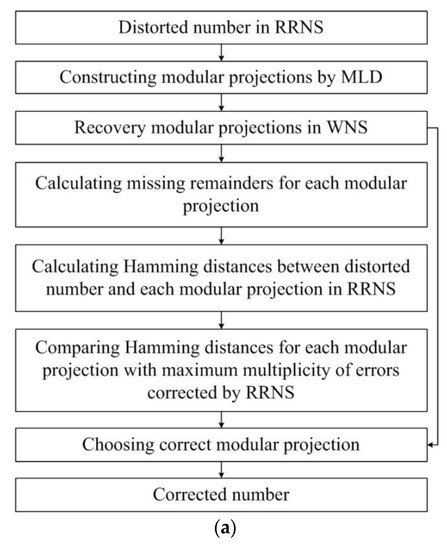
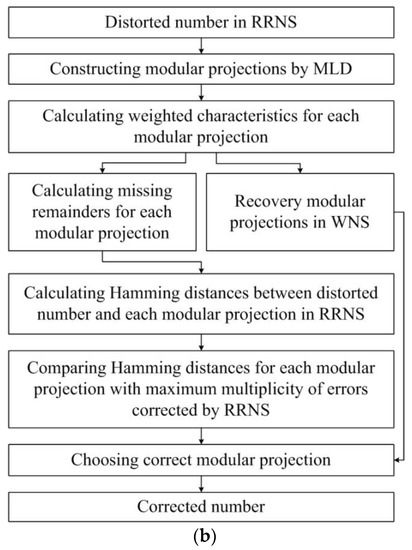
Figure 1.
Modular projection methods with MLD: (a) original, (b) modified.
Reconstructing the weighted representation of projections using the CRT has high time delays. First of all, the delay is due to executing operations on a large modulus comparable to the dynamic range of the RRNS.
In the original method [19], the reconstructed weighted representations of modular projections are used, on the one hand, to calculate the missing remainders subsequently and, on the other hand, to obtain the correct number in the WNS. (One of the projections will be the correct number represented in the WNS.) In the modified method, we propose using (a) the ranks of the modular projections to obtain the missing remainders and (b) the approximate weighted characteristics of the CRTf to restore the modular projections in the WNS. This approach allows for calculating the missing remainders and reconstructing projections in the WNS in parallel (Figure 1b), not sequentially, as was proposed in [19].
The efficiency of the proposed modification largely depends on the efficiency of calculating the rank of a number represented in the RRNS. The choice of the CRTf for reconstructing modular projections in the WNS is not accidental: the approximate weighted characteristic closely relates to the rank of the number written in the RRNS.
According to (3), the rank is given by
Due to (4) and (5),
Recall that denotes taking the fractional part of a number. Hence, the rank of is given by
Note that and are the integer and fractional parts of the same value. We introduce the notation
Calculating , we simultaneously find the weighted characteristic (Equation (5)) and the rank of (Equation (10)).
Similar to the case of the CRTf (Equations (6) and (7)), we propose using a binary shift to implement the calculation of on a hardware base not supporting fractions. The accuracy of the constants in (11) is estimated by analogy with [20]. Then
where [20].
The value is especially convenient for the hardware implementation of the error correction procedure for modular codes. Really, the least significant bits of the binary representation of calculated by Equation (12) will be the shifted weighted characteristic (Equation (7)):
where [20].
The other (most significant) bits will be equal to the rank of :
where [20].
After obtaining the shifted approximate weighted characteristic by Equation (13), the standard CRTf Equation (6) is used for restoration. We discuss in detail the calculation of the missing remainders using the rank .
This operation extends the system of RNS moduli [7] and can be performed efficiently by efficiently calculating the rank of a number.
According to (3),
Introducing the compact notation , we write
Due to (15), for each modular projection, the missing remainders on dividing the number by the moduli deleted when constructing the projection are given by
Performing trivial transformations, we obtain
and, finally,
Note that for each modular projection, the values and differ. However, these values are completely determined by the set of RRNS moduli. Therefore, they are calculated in advance and stored in the memory of the computing device.
Thus, the missing remainders are calculated using multiplication by a constant and addition on a small modulus comparable to the RRNS moduli. Both operations are well implemented in hardware. The key feature of the proposed approach is the ability to calculate the first term in the sum (16) independently and in parallel with the second one . We denote them by and , respectively:
Then Equation (16) becomes
Since the values are calculated in parallel to and , the total execution time of the procedure for correcting errors in modular codes and restoring the correct number in the WNS is reduced.
An example demonstrating an approach to extending the system of RNS moduli using the number rank is presented in Appendix A (See, Example A1).
Another example demonstrating the proposed approach to error correction and restoration of the correct number in the WNS is presented in Appendix B (See, Example A2).
The proposed modified modular projection method with MLD for correcting multiple errors in modular codes allows for achieving a high level of parallelism and significantly reducing the total execution time of the multiple error correction procedure.
The proposed method requires calculation of the rank (Equation (14)) for base extension. CRT-I and CRT-II are not directly applicable to do this, while function , used in the article, gives the advantage to calculate the relative size of both the value and simultaneously.
5. Hardware Implementation of Modified Modular Projection Method with MLD
The original [19] and modified modular projection methods for correcting multiple errors in modular codes (Section 4) have the identical error detection stage. For both methods equally, the implementation variability of this stage lies in choosing an appropriate algorithm for calculating the weighted characteristic of the corrected number. The hardware implementation and comparative analysis of such algorithms were presented in [31]. Let us compare the efficiency of error localization and correct data restoration in a WNS.
Using various computing devices for implementing methods and algorithms is often dictated by the need to adapt them to the architectural features of a given hardware base. Support of calculations in the ring of integers is a characteristic feature of FPGA computing devices that increases speed but severely restricts the class of executed tasks.
The original method [19] can be implemented on FPGA without any restrictions. The modified method contains operations with fractions and, therefore, requires adaptation when implemented on FPGA. Equations (12)–(14) are used for passing to integer calculations. This transition is illustrated by an example in Appendix C (See, Example A3).
The result of this example coincides with that of an example in Appendix B. Therefore, the transition to integer calculations by Equations (12)–(14) is correct.
The efficiency of the original [19] and modified methods for correcting multiple errors in modular codes was compared by their implementation in the Very High SpeedIntegrated Circuits Hardware Description Language (VHDL) using Xilinx Vivado 2019.1, a software tool for the design and analysis of HDL structures. For testing, we used a Kintex-7 FPGA (core Xilinx xc7k70tfbg676-2) of a sufficient area without DSP blocks.
This software–hardware base has hardware parallelization at the level of blocks implementing individual procedures and functions and, moreover, at the level of operations within these blocks. Figure 2 shows the schemes for parallelizing the compared methods at the block level: vertical lines separate parallel executed blocks, whereas horizontal lines indicate the synchronization of upper blocks. The schemes in Figure 2 specify the corresponding schemes in Figure 1, considering their hardware implementation.
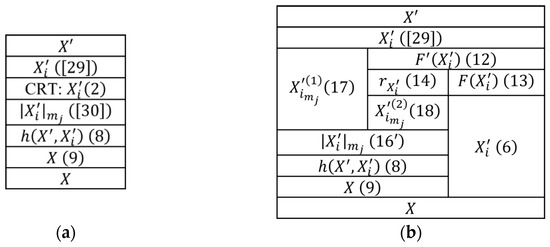
Figure 2.
Scheme of parallelizing modular projection methods with MLD: (a) original, (b) modified.
The original method [19] contains no parallel blocks (Figure 2a); however, calculations for each modular projection are performed in parallel within each block, except for the first and the last ones. In the modified method, calculations for each modular projection are also performed in parallel within each block, except for the first and last ones; in addition, there is parallelism at the block level (Figure 2b).
Let us consider the hardware implementation of each block in Figure 2.
Original modular projection method with MLD [19] is presented in Appendix D.
Modified Modular Projection Method with MLD
Block . When an error is detected, this block receives at the input remainders representing the distorted number in the -RRNS.
Block . This block constructs modular projections. It is implemented in parallel computational threads, where . Each thread corresponds to a modular projection and receives at the input remainders of the distorted number (the outputs of the block ) obtained by the modular projection algorithm [29].
Block . This block calculates the extended weighted characteristics of modular projections in the WNS. According to (12), it is implemented by parallel multiplications of the remainders (the outputs of the block ) by constants modulo and a -operand adder [31].
Block . This block calculates the ranks for each modular projection . It is implemented by extracting the most significant bits with numbers not less than (14) from the extended weighted characteristic (the output of the block ).
Block . This block calculates weighted characteristics for each modular projection . It is implemented by extracting the least significant bits with numbers less than (13) from the extended weighted characteristic (the output of the block ).
Block . This block calculates the missing remainders (the first term) for each modular projection . It is implemented by parallel multiplications of the remainders (the outputs of the block ) by constants modulo and a -operand modulo adder [31]; see Equation (17).
Block . This block calculates the missing remainders (the second term) for each modular projection . It is implemented by multiplying the rank (the output of the block ) by a constant modulo [31]; see Equation (18).
Block . This block calculates the missing remainders for each modular projection . It is implemented by modulo adding the first term (the output of the block ) to the second term (the output of the block ) [31]; see Equation (19).
Block (6). This block calculates the modular projections in the WNS. It is implemented by multiplying the weighted characteristic of the modular projection (the output of the block ) by the dynamic range . Subsequently, the least significant bits with numbers less than are discarded; see Equation (6).
Block . This block calculates Hamming distances between the distorted number and each modular projection . It is implemented by parallel comparisons of the corresponding remainders of the distorted number (the outputs of the block ) and the modular projection (the outputs of the block ). Subsequently, the mismatches are counted by an -operand adder.
Block X (9). This block chooses a correct modular projection. It is implemented by the conjunction of two comparisons: the modular projection in the WNS (the output of the block CRT: ) is smaller than the dynamic range , and the Hamming distance (the output of the block ) is not greater than the maximum multiplicity of errors corrected by the -RRNS. The results for each thread (conjunctions for different modular projections) are glued together into a -bit number, and the number of the first nonzero bit corresponds to the correct modular projection.
Block X. This block outputs the correct number in the WNS. It is implemented by a -input multiplexer with one control input. The common inputs are the modular projections in the WNS (the outputs of the block CRT: ). The control input is the number of the correct modular projection (the output of the block (9)).
In the course of comparative analysis, we obtained data on the time and hardware costs for correcting single and double errors in modular codes. We used the -RRNS (single error) and -RRNS (double error) for numbers of different bit widths (4 bits, 8 bits, 16 bits, 24 bits, 32 bits, 48 bits, and 64 bits). The moduli sets, the time and hardware costs for correcting single and double errors and restoring the number in the WNS using the original modular projection method with MLD [19], and the modified one proposed in this paper are presented in Appendix E (See, Table A7 and Table A8).
Figure 3 shows the operating times of the methods depending on the bit width of the numbers under correction for a single error (see, Figure 3a) and double errors (see, Figure 3b).
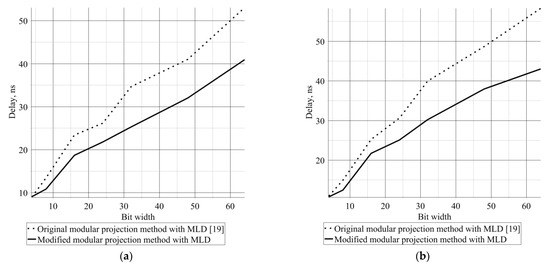
Figure 3.
Time to correct errors and restore numbers in WNS: (a) single error, (b) double error.
According to Figure 3, the modified modular projection method with MLD proposed in this dynamic is faster than the original method [19]. Based on the simulation results on FPGA (see Appendix D), we conclude that the proposed method speeds up the procedure of error correction and number restoration in the WNS by an average of 1.23 times (18%) compared to the original approach [19]. On average, the modified modular projection method with MLD requires 1.55 times (35%) more resources for single errors and 1.76 times (43%) more resources for double errors.
6. Conclusions
Recovery weighted values of modular projections has high time complexity due to computations on a large modulus. The paper proposes a method based on the use of approximate positional characteristics and ranks of modular projections. The use of the Chinese Remainder Theorem with fractions in the procedure for correcting errors and recovery numbers in the weighted number system makes it possible to efficiently calculate the rank of each of the modular projections. The ranks of modular projections are employed to calculate the Hamming distances. This approach allows for parallelizing computations at the levels of operations and computing blocks.
The simulation results on FPGA have demonstrated that the proposed modified modular projection method with MLD speeds up the procedure of error correction and number restoration in the weighted number system by an average of 18% compared to the original method [19]. At the same time, it consumes many more hardware resources.
However, in further study, we are going to research the moduli set selection and the possibility of applying the proposed method for error correction codes with the RNS special moduli sets.
Author Contributions
Conceptualization, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; methodology, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; validation, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; formal analysis, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; investigation, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; writing—original draft preparation, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; writing—review and editing, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T.; supervision, M.B., A.N., M.D., N.K., A.T., N.V.H., A.A. and V.T. The main part of this work was made when Maxim Deryabin was a Senior Researcher at North-Caucasus Federal University. All authors have read and agreed to the published version of the manuscript.
Funding
This work was carried out at the North Caucasus Center for Mathematical Research within agreement no. 075-02-2021-1749 with the Ministry of Science and Higher Education of the Russian Federation. The reported study was funded by RFBR, project number 20-37-70023; Russian Federation President Grant MK-24.2020.9; and SP-1685.2019.5.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Example A1.
An RNS is given by a set of moduli , , and . It is required to find the remainder on dividing the number in this RNS by the modulus . For ease of further consideration, note that in the WNS.
Appendix A.1. Base Extension. Pre-Computation Stage
We obtain the constants for the moduli set .
.
We calculate the constantsby Equation (15):
Next, we calculate the constants for Equation (16):
Finally, we calculate the constants necessary for finding the rank of . According to (10),
Appendix A.2. Base Extension. Computation Stage
Step 1. We obtain by Equation (17):
Calculating the first term in Equation (16), we calculate the rank in parallel. According to (10),
Using Equation (18), we find the second term in Equation (16):
Step 2. We calculate the desired remainder by Equation (19):
This value matches the remainder on dividing by the modulus .
End of example.
Appendix B
Example A2.
An -RRNS, where and , is given by a set of moduli . It is required to find erroneous digits in the number and correct them (if any). For ease of further consideration, note that the correct number is , (The number contains a double error in the 2nd and 5th remainders).
The-RRNS can correct errors.
Appendix B.1. Error Detection. Pre-Computation Stage
To detect an error, we have to restore the number in the WNS and compare it with the dynamic range or calculate the weighted characteristic and compare it with the corresponding weighted characteristic of the dynamic range. To reduce calculations, we detect errors using weighted characteristics yielded by the CRTf. We calculate all necessary constants that can be pre-computed, saving them in memory (See, Table A1).
We calculate the dynamic and full ranges of this RRNS:
The constants for error detection (Equation (5)) are
According to Equation (4),

Table A1.
Pre-computed constants for error detection using CRTf.
Table A1.
Pre-computed constants for error detection using CRTf.
Appendix B.2. Error Detection. Computation Stage
According to Equation (5),
Since , the numbercontains an error.
Appendix B.3. Error Localization and Correction. Pre-Computation Stage
To correct errors, we use the modified modular projection method with MLD. The projections are constructed according to the algorithm [29]:
We calculate constants for each modular projection, saving them in memory (See, Table A2).

Table A2.
Pre-computed constants for each modular projection.
Table A2.
Pre-computed constants for each modular projection.
| Modular Projection | ||||
|---|---|---|---|---|
| 1 | Number | |||
| 2 | ||||
| 3 | ||||
| 4 | ||||
| 5 | ||||
| 6 | }] | |||
| 7 | } | |||
The modular projection , .
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (4):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (11),
The modular projection,.
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (4):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (11),
The modular projection,.
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (4):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (11),
Appendix B.4. Error Localization and Correction. Computation Stage
Step 1. We calculate the extended weighted characteristic for each modular projection (Equation (11)) using the pre-computed constants from Table A2. The weighted characteristic and rank of each modular projection are the fractional and integer parts, respectively, of the extended weighted characteristic.
The modular projection:
The modular projection:
The modular projection:
Step 2. We calculate the second terms for finding the missing remainders for each modular projection (Equation (18)) using the constants from Table A2.
The modular projection:
The modular projection:
The modular projection:
We obtain the weighted representations of modular projections (Equation (4)) in parallel with calculating the second terms.
The modular projection:
The modular projection:
The modular projection:
Step (1–2). We calculate the first terms for finding the missing remainders for each modular projection (Equation (17)) using the constants from Table A2. This is done in parallel with Steps 1–2.
The modular projection:
The modular projection:
The modular projection:
Step 3. We calculate the missing remainders for each modular projection (Equation (19)).
The modular projection:
The modular projection:
The modular projection:
Step 4. We calculate the Hamming distances between each modular projection in the RRNS and the distorted number (Equation (8)):
Step 5. We choose a correct projection (See, Table A3).

Table A3.
Computed modular projections and their characteristics.
Table A3.
Computed modular projections and their characteristics.
| Modular Projection | ||||
|---|---|---|---|---|
| 1 | 2/7 | 5/24 | 67/143 | |
| 2 | ) | 1 | 35/72 | 35/143 |
| 3 | (0,3,2,1,10,10) | (0,1,7,6,4,2) | (2,4,3,4,1,2) | |
| 4 | (0,3,7,6,1,2) | (0,3,7,6,1,2) | (0,3,7,6,1,2) | |
| 5 | 4 | 2 | 4 | |
| 6 | Yes | Yes | No | |
| 7 | No | Yes | No | |
Both correctness conditions (9) are satisfied for the modular projectiononly. Therefore, the corrected number is, and the proposed error correction method works properly.
End of example.
Appendix C
Example A3.
An-RRNS, whereand, is given by a set of moduli. It is required to find erroneous digits in the numberand correct them (if any). For ease of further considerations, note that the correct number is. (The numbercontains a double error in the 2nd and 5th remainders.)
The-RRNS can correcterrors.
Appendix C.1. Error Detection. Pre-Computation Stage
To detect an error, we have to restore the numberin the WNS and compare it with the dynamic range, or calculate the weighted characteristicand compare it with the corresponding weighted characteristicof the dynamic range. To reduce calculations, we detect errors using weighted characteristics yielded by the CRTf. We calculate all necessary constants that can be precomputed, saving them in memory (See, Table A4). In the memory of the computing device, the constants are stored in the binary representation. In this example, we use the decimal representation for clarity.
We calculate the dynamic and full ranges of this RRNS:
The constants for error detection (Equation (5)) are
The weighted characteristic of the dynamic range is obtained by Equation (6):

Table A4.
Pre-computed constants for error detection using CRTf.
Table A4.
Pre-computed constants for error detection using CRTf.
| {5, 7, 8, 9, 11, 13} | {20132660, 19173962, 20971520, 29826162, 18302418, 25811102} | 3259 |
Appendix C.2. Error Detection. Computation Stage
According to Equation (7),
Since, the numbercontains an error.
Appendix C.3. Error Localization and Correction. Pre-Computation Stage
To correct errors, we use the modified modular projection method with MLD. The projections are constructed according to the algorithm [29]:
We calculate constants for each modular projection, saving them in memory (Table A5). In the memory of the computing device, the constants are stored in the binary representation. In this example, we use the decimal representation for clarity.
The modular projection,
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (6):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (12),
The modular projection,
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (6):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (12),
The modular projection,
The weighted characteristic of the dynamic rangefor the projection is obtained by Equation (6):
The constants for Equation (18) are
According to Equation (15),
The constants for Equation (17) are
According to (12),
Appendix C.4. Error Localization and Correction. Computation Stage
Step 1. We calculate the extended weighted characteristic for each modular projection (Equation (12)) using the pre-computed constants from Table A5. The positional characteristic and rank of each modular projection are given by Equations (13) and (14), respectively.

Table A5.
Pre-computed constants for each modular projection.
Table A5.
Pre-computed constants for each modular projection.
| Modular Projection | ||||
|---|---|---|---|---|
| 1 | Number | |||
| 2 | ||||
| 3 | ||||
| 4 | ||||
| 5 | ||||
| 6 | ||||
| 7 | }] | |||
| 8 | } | |||
The modular projection:
The modular projection:
The modular projection:
Step 2. We calculate the second terms for finding the missing remainders for each modular projection (Equation (18)) using the constants from Table A5.
The modular projection:
The modular projection:
The modular projection:
We obtain the weighted representations of modular projections (Equation (6)) in parallel with calculating the second terms. Note that in Equation (6), division by, followed by rounding down, is implemented by simply discarding the lastdigits in the binary representation.
The modular projection:
The modular projection:
The modular projection:
Steps (1–2). We calculate the first terms for finding the missing remainders for each modular projection (Equation (17)) using the constants from Table A5. This is done in parallel with Steps 1–2.
The modular projection:
The modular projection:
The modular projection:
Step 3. We calculate the missing remainders for each modular projection (Equation (19)).
The modular projection:
The modular projection:
The modular projection:
Step 4. We calculate the Hamming distances between each modular projection in the RRNS and the distorted number (Equation (8)):
Step 5. We choose a correct projection (See, Table A6).

Table A6.
Computed modular projections and their characteristics.
Table A6.
Computed modular projections and their characteristics.
| Modular Projection | ||||
|---|---|---|---|---|
| 1 | 148 | 430 | 1921 | |
| 2 | ) | 512 | 996 | 1003 |
| 3 | (0,3,2,1,10,10) | (0,1,7,6,4,2) | (2,4,3,4,1,2) | |
| 4 | (0,3,7,6,1,2) | (0,3,7,6,1,2) | (0,3,7,6,1,2) | |
| 5 | 4 | 2 | 4 | |
| 6 | , | Yes | Yes | No |
| 7 | No | Yes | No | |
Both correctness conditions (9) are satisfied for the modular projectiononly. Therefore, the corrected number is, and the proposed error correction method works properly.
End of example.
Appendix D
Original Modular Projection Method with MLD
Block X′. When an error is detected, this block receives at the input remainders representing the distorted number in the -RRNS.
Block X′. This block constructs modular projections. It is implemented in parallel computational threads, where . Each thread corresponds to a modular projection and receives at the input k remainders of the distorted number (the outputs of the block ) obtained by the modular projection algorithm [29].
Block CRT: . This block calculates the modular projections in the WNS. According to the CRT, it is implemented by parallel multiplications of the remainders (the outputs of the block ) by constants modulo and a -operand modulo adder [31].
Block . This block calculates the missing remainders for each modular projection . It is implemented by parallel computations of the remainders of the division of the number (the output of the block CTR: ) by the missing moduli [30].
Block . This block calculates Hamming distances between the distorted number and each modular projection . It is implemented by parallel comparisons of the corresponding remainders of the distorted number (the outputs of the block ) and the modular projection (the outputs of the block ). Subsequently, the mismatches are counted by an -operand adder.
Block (9). This block chooses a correct modular projection. It is implemented by the conjunction of two comparisons: the modular projection in the WNS (the output of the block CRT: ) is smaller than the dynamic range , and the Hamming distance (the output of the block ) is not greater than the maximum multiplicity of errors corrected by the -RRNS. The results for each thread (conjunctions for different modular projections) are glued together into a -bit number, and the number of the first nonzero bit corresponds to the correct modular projection.
Block . This block outputs the correct number in the WNS. It is implemented by a -input multiplexer with one control input. The common inputs are the modular projections in the WNS (the outputs of the block CRT: ). The control input is the number of the correct modular projection (the output of the block (9)).
Appendix E

Table A7.
Hardware and time costs for correcting single errors and restoring numbers in WNS.
Table A7.
Hardware and time costs for correcting single errors and restoring numbers in WNS.
| Bit Width | (2,4)-RRNS | Original Modular Projection Method with MLD [19] | Modified Modular Projection Method with MLD | |||
|---|---|---|---|---|---|---|
| LUT | Delay, ns | LUT | Delay, ns | |||
| 1 | 4 | {5, 7, 8, 9} | 45 | 9.012 | 84 | 9.079 |
| 2 | 8 | {16, 17, 19, 21} | 108 | 13.459 | 161 | 10.853 |
| 3 | 16 | {256, 257, 259, 261} | 323 | 23.428 | 480 | 18.709 |
| 4 | 24 | {4096, 4097, 4099, 4101} | 601 | 26.173 | 996 | 21.803 |
| 5 | 32 | {65536, 65537, 65539, 65541} | 998 | 34.677 | 1526 | 25.305 |
| 6 | 48 | {16777216, 16777217, 16777219, 16777221} | 1932 | 41.042 | 2698 | 32.047 |
| 7 | 64 | {4294967296, 4294967297, 4294967299, 4294967301} | 3304 | 53.05 | 4606 | 40.942 |

Table A8.
Hardware and time costs for correcting double errors and restoring numbers in WNS.
Table A8.
Hardware and time costs for correcting double errors and restoring numbers in WNS.
| Bit Width | (2,6)-RRNS | Original Modular Projection Method with MLD [19] | Modified Modular Projection Method with MLD | |||
|---|---|---|---|---|---|---|
| LUT | Delay, ns | LUT | Delay, ns | |||
| 1 | 4 | {5, 7, 8, 9, 11, 13} | 145 | 10.961 | 251 | 10.751 |
| 2 | 8 | {16, 17, 19, 21, 23, 25} | 277 | 14.963 | 464 | 12.467 |
| 3 | 16 | {256, 257, 259, 261, 263, 265} | 811 | 25.261 | 1414 | 21.744 |
| 4 | 24 | {4096, 4097, 4099,4101, 4103, 4105} | 1612 | 30.616 | 3154 | 25.092 |
| 5 | 32 | {65536, 65537, 65539,65541, 65543, 65545} | 2633 | 39.965 | 4960 | 30.23 |
| 6 | 48 | {16777216,16777217,16777219,16777221, 16777223, 16777225} | 5309 | 48.673 | 9048 | 37.962 |
| 7 | 64 | {4294967296, 4294967297, 4294967299, 4294967301, 4294967303, 4294967305} | 9102 | 58.294 | 14709 | 43.015 |
References
- Zaharia, M.; Chowdhury, M.; Franklin, M.J.; Shenker, S.; Stoica, I. Spark: Cluster computing with working sets. HotCloud 2010, 10, 95. [Google Scholar]
- Li, W.; Yang, Y.; Yuan, D. A Novel Cost-Effective Dynamic Data Replication Strategy for Reliability in Cloud Data Centres. In Proceedings of the 2011 IEEE Ninth International Conference on Dependable, Autonomic and Secure Computing, Sydney, NSW, Australia, 12–14 December 2011; pp. 496–502. [Google Scholar]
- Huang, C.; Simitci, H.; Xu, Y.; Ogus, A.; Calder, B.; Gopalan, P.; Li, J.; Yekhanin, S. Erasure coding in windows azure storage. In Proceedings of the 2012 USENIX Annual Technical Conference (USENIXATC 12), Boston, MA, USA, 13–15 June 2012; pp. 15–26. [Google Scholar]
- Sathiamoorthy, M.; Asteris, M.; Papailiopoulos, D.; Dimakis, A.G.; Vadali, R.; Chen, S.; Borthakur, D. XORing Elephants: Novel Erasure Codes for Big Data. arXiv 2013, arXiv:1301.3791. [Google Scholar] [CrossRef]
- Muralidhar, S.; Lloyd, W.; Roy, S.; Hill, C.; Lin, E.; Liu, W.; Pan, S.; Shankar, S.; Sivakumar, V.; Tang, L.; et al. f4: Facebook’s Warm BLOB Storage System. In Proceedings of the 11th USENIX Symposium on Operating Systems Design and Implementation (OSDI 14), Broomfield, CO, USA, 6–8 October 2014; pp. 383–398. [Google Scholar]
- Goh, V.T.; Tinauli, M.; Siddiqi, M.U. A novel error correction scheme based on the Chinese remainder theorem. In Proceedings of the Ninth International Conference on Communications Systems, ICCS 2004, Singapore, 7 September 2004; pp. 461–465. [Google Scholar]
- Ding, C.; Pei, D.; Salomaa, A. Chinese Remainder Theorem: Applications in Computing, Coding, Cryptography; World Scientific: Singapore, 1996; 213p. [Google Scholar]
- Wicker, S.B.; Bhargava, V.K. Reed-Solomon Codes and Their Applications; John Wiley & Sons: New York, NY, USA, 1999; 336p. [Google Scholar]
- Rabin, M.O. Efficient dispersal of information for security, load balancing, and fault tolerance. J. ACM 1989, 36, 335–348. [Google Scholar] [CrossRef]
- Kshemkalyani, A.D.; Singhal, M. Distributed Computing: Principles, Algorithms, and Systems; Cambridge University Press: Cambridge, UK, 2011; 756p. [Google Scholar]
- Tel, G. Introduction to Distributed Algorithms; Cambridge University Press: Cambridge, UK, 2000; 596p. [Google Scholar]
- Van Steen, M.; Tanenbaum, A. Distributed systems principles and paradigms. Network 2002, 2, 28. [Google Scholar]
- Gentry, C.; Halevi, S.; Smart, N.P. Fully Homomorphic Encryption with Polylog Overhead. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Cambridge, UK, 15–19 April 2012; pp. 465–482. [Google Scholar]
- Sun, J.-D.; Krishna, H. A coding theory approach to error control in redundant residue number systems. II. Multiple error detection and correction. IEEE Trans. Circuits Syst. II Analog Digit. Signal Process. 1992, 39, 18–34. [Google Scholar] [CrossRef]
- Tay, T.F.; Chang, C.-H. A new algorithm for single residue digit error correction in Redundant Residue Number System. In Proceedings of the 2014 IEEE International Symposium on Circuits and Systems (ISCAS), Melbourne, Australia, 1–5 June 2014; pp. 1748–1751. [Google Scholar]
- Yau, S.S.-S.; Li, Y.-C. Error Correction in Redundant Residue Number Systems. IEEE Trans. Comput. 1973, 100, 5–11. [Google Scholar] [CrossRef]
- Barsi, F.; Maestrini, P. Error Correcting Properties of Redundant Residue Number Systems. IEEE Trans. Comput. 1973, 100, 307–315. [Google Scholar] [CrossRef]
- Chervyakov, N.I.; Lyakhov, P.A.; Babenko, M.G.; Lavrinenko, I.N.; Lavrinenko, A.V.; Nazarov, A.S. The architecture of a fault-tolerant modular neurocomputer based on modular number projections. Neurocomputing 2018, 272, 96–107. [Google Scholar] [CrossRef]
- Goh, V.T.; Siddiqi, M.U. Multiple error detection and correction based on redundant residue number systems. IEEE Trans. Commun. 2008, 56, 325–330. [Google Scholar] [CrossRef]
- Chervyakov, N.I.; Molahosseini, A.S.; Lyakhov, P.A.; Babenko, M.G.; Deryabin, M.A. Residue-to-binary conversion for general moduli sets based on approximate Chinese remainder theorem. Int. J. Comput. Math. 2017, 94, 1833–1849. [Google Scholar] [CrossRef]
- Soderstrand, M.; Vernia, C.; Chang, J.-H. An improved residue number system digital-to-analog converter. IEEE Trans. Circuits Syst. 1983, 30, 903–907. [Google Scholar] [CrossRef]
- Van Vu, T. Efficient Implementations of the Chinese Remainder Theorem for Sign Detection and Residue Decoding. IEEE Trans. Comput. 1985, 100, 646–651. [Google Scholar] [CrossRef]
- Tang, Y.; Boutillon, E.; Jego, C.; Jezequel, M. A new single-error correction scheme based on self-diagnosis residue number arithmetic. In Proceedings of the 2010 Conference on Design and Architectures for Signal and Image Processing (DASIP), Edinburgh, UK, 26–28 October 2010; pp. 27–33. [Google Scholar]
- Tchernykh, A.; Babenko, M.; Chervyakov, N.; Miranda-Lopez, V.; Avetisyan, A.; Drozdov, A.Y.; Rivera-Rodriguez, R.; Radchenko, G.; Du, Z. Scalable Data Storage Design for Nonstationary IoT Environment with Adaptive Security and Reliability. IEEE Internet Things J. 2020, 7, 10171–10188. [Google Scholar] [CrossRef]
- Yin, P.; Li, L. A new algorithm for single error correction in RRNS. In Proceedings of the 2013 International Conference on Communications, Circuits and Systems (ICCCAS), Chengdu, China, 15–17 November 2013; pp. 178–181. [Google Scholar]
- Goldreich, O.; Ron, D.; Sudan, M. Chinese remaindering with errors. In Proceedings of the Thirty-First Annual ACM Symposium on Theory of Computing, Atlanta, Georgia, 1–4 May 1999; pp. 225–234. [Google Scholar]
- Mandelbaum, D. On a class of arithmetic codes and a decoding algorithm (Corresp.). IEEE Trans. Inf. Theory 1976, 22, 85–88. [Google Scholar] [CrossRef]
- Jenkins, W.K.; Altman, E.J. Self-checking properties of residue number error checkers based on mixed radix conversion. IEEE Trans. Circuits Syst. 1988, 35, 159–167. [Google Scholar] [CrossRef]
- Nazarov, A.; Babenko, M.; Tchernykh, A.; Pulido-Gaytand, B.; Cortés-Mendozad, J.M.; Vashchenko, I. Algorithm for constructing modular projections for correcting multiple errors based on a redundant residue number system using maximum likelihood decoding. Program. Comput. Softw. 2021, 47, 839–848. [Google Scholar] [CrossRef]
- Nazarov, A.; Babenko, M.; Golimblevskaia, E. Efficient Hardware Implementation of forward Conversion WNS-RNS on FPGA. In Proceedings of the 2020 International Conference Engineering and Telecommunication (En & T), Dolgoprudny, Russia, 25–26 November 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Nazarov, A.; Babenko, M.; Golimblevskaia, E. Hardware Implementation of the Reverse Conversion RNS-WNS on FPGA. In Proceedings of the 2020 International Conference Engineering and Telecommunication (En & T), Dolgoprudny, Russia, 25–26 November 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Ananda Mohan, P.V. Residue Number Systems: Theory and Applications; Birghauser Math: Basel, Switzerland, 2016. [Google Scholar] [CrossRef]
- Omondi, A.R.; Premkumar, A.B. Residue Number Systems: Theory and Implementation; World Scientific: Singapore, 2007. [Google Scholar]
- Menezes, A.J.; Van Oorschot, P.C.; Vanstone, S.A. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Nazarov, A.; Chervyakov, N.; Tchernykh, A.; Babenko, M. Reliability improvement of information systems by residue number system code. Int. J. Comb. Optim. Probl. Inform. 2018, 9, 81. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).