A Scalable Solution to Detect Behavior Changes of Elderly People Living Alone
Abstract
:1. Introduction
“any device or system that allows individuals to perform tasks they would otherwise be unable to do or increases the ease and safety with which tasks can be performed”.[4]
- -
- Physiological monitoring, by collecting and analyzing data about certain physiological parameters like pulse rate, blood pressure, respiration, level of oxygen in the bloodstream, temperature, blood sugar level, etc. This type of application typically relies on wearable or implantable sensors (see Refs. [15,16]).
- -
- Monitoring potential environmental hazards using dedicated equipment (e.g., gas leaks or fire).
- -
- Intrusion detection. Special intrusion detection systems are commercially available, equipped with passive infrared (PIR) motion detectors, glass break detectors, magnetic door contacts, and video surveillance cameras.
- -
- Sensory and cognitive assistance. This type of technology aims to compensate the sensory or memory loss, e.g., by using hearing aids and reminders about taking the medication. Some of these systems are also capable to provide verbal instructions on performing certain tasks, or orientation suggestions (see Ref. [17] for an extensive review on reminder systems).
- -
- Monitoring the level of social interactions by collecting data about the frequency and duration of the phone calls, the number of visitors received, and participation of the users in social activities ([18]). The assistive technology can go beyond the simple monitoring and, in certain applications, aims to facilitate social interactions of the monitored persons by including equipment that mediate the virtual meetings with friends or family, or the participation in group activities (e.g., through games, as in Ref. [19]).
- -
- Detection of emergencies (e.g., falls). A comprehensive review of the existing solutions for fall detection is available in Ref. [20].
- -
- -
- Economic Feasibility. These systems should be affordable for persons with lower socioeconomic status (SES).
- -
- Scalability. Monitoring systems should be designed so that they can be easily replicated in large series.
- -
- Unobtrusiveness. Ideally, the monitoring systems should be totally transparent for the users.
- -
- Continuity of sensing. The systems should be capable to collect and process data continuously over extended periods of time.
- -
- Usability. Such systems should be easy to install and require minimum maintenance to operate.
- -
- Adaptability. The monitoring systems should be easily adaptable to any individual regardless of her/his living environment.
- -
- A good trade-off between high sensitivity and a small number of false alarms.
- -
- Privacy and security. These systems should protect the privacy of the users and caregivers and have a clear and transparent policy regarding the usage of personal data.
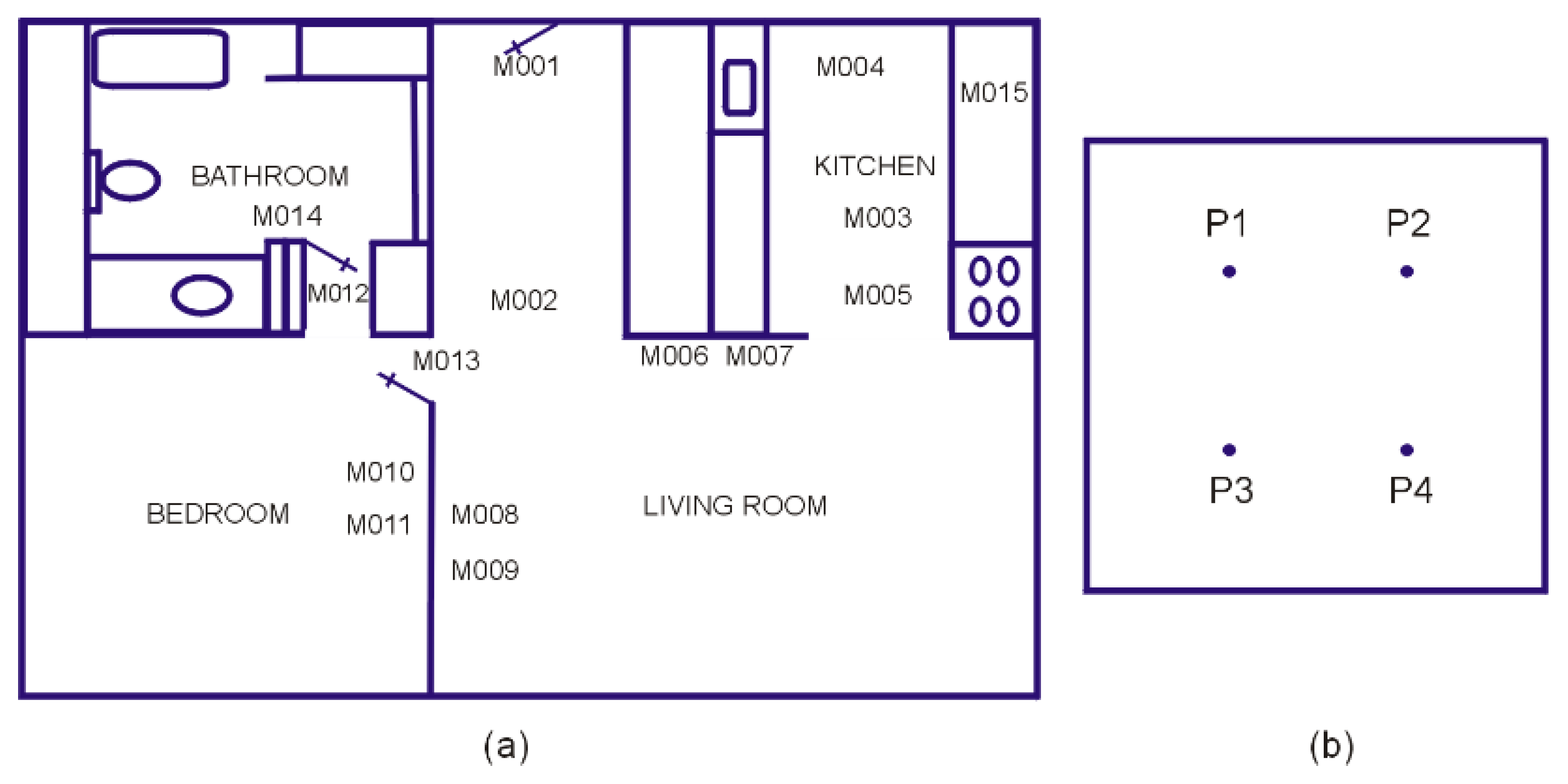
- We propose an abstracted model of the residential living space, reduced to a collection of Behaviorally Meaningful Places (BMPs), represented as points located symmetrically in a generic Cartesian space. By eliminating all the details regarding the surface of the living space, the type and position of the furniture and appliances, and the specific locations of the sensors, this model creates a common ground for monitoring the ADL in almost any residential environment.
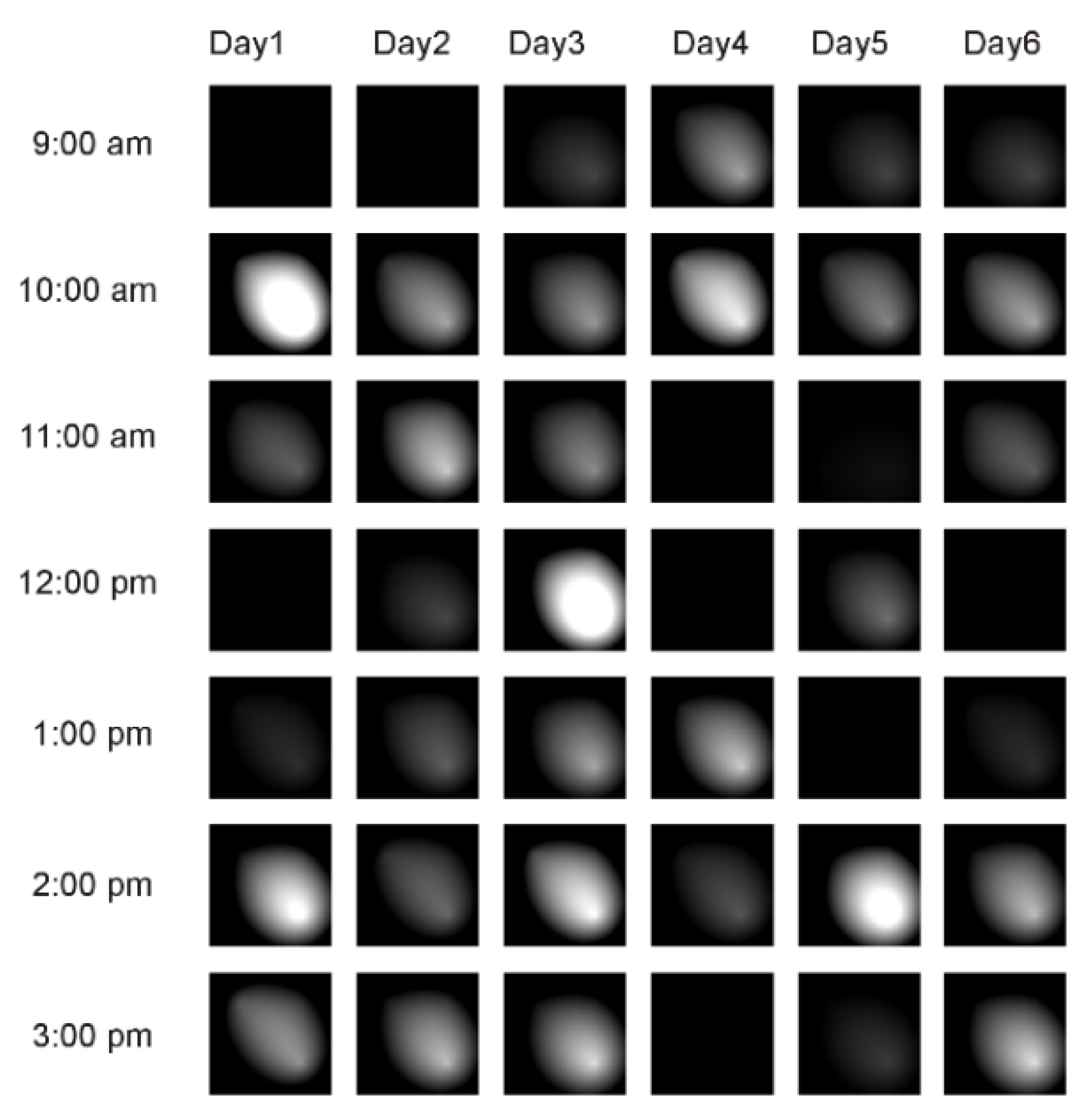
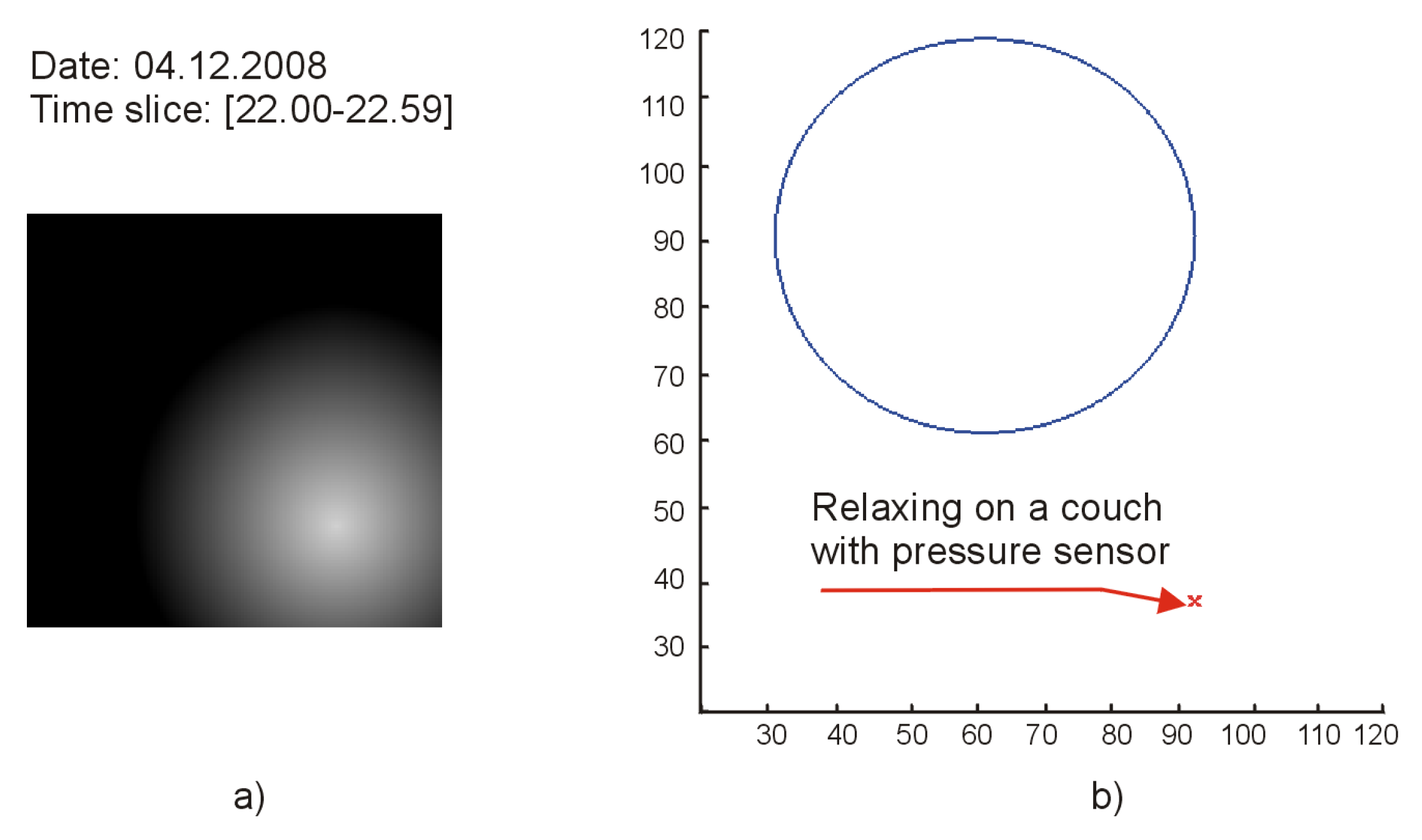
- We describe a method to encode the sensor data in the form of a series of activity maps that embed information about the intensity and the spatial distribution of the activities.
- We show that the respective activity maps can be automatically analyzed to detect changes in the behavior of the monitored persons, by comparing the activity map of the current time slice with the data previously recorded in a reference time interval.
- We propose a method to reduce the number of false alerts based on fuzzy logic.
2. Related Work
- -
- Parallel or interleaved execution of certain activities (e.g., a person may cook dinner, watch TV, and answer the phone at the same time).
- -
- Periodic variations. The structure of the ADLs may be subject to weekly, monthly, or seasonal variations (e.g., sleep hours may be different during winter and summer).
- -
- False starts. Sometimes people start an activity and suddenly abandon it for unexpected reasons.
- -
- Score-based approaches. These solutions involve periodic assessment of the monitored persons from the perspective of possible health conditions that may affect their ADL routine. The clinical expert that conducts the assessment assigns scores for the mobility, cognitive status and other health aspects. The assistive technology is then programmed to map these scores to the data collected from the sensors during the respective period of assessment, with the aim to predict future health scores starting from the sensors data. This strategy is used in Ref. [33].
- -
- Classification approaches. These are entirely similar to the discriminating strategy described above.
- -
- Outlier detection approaches assume that the training data define the normal behavior and compare subsequent ADL data with the baseline defined in the training phase. Significant deviations from this baseline (outliers) are considered abnormal behavior. This approach is used in Ref. [34].
3. Method and Datasets
3.1. Assumptions
3.2. Description of the Proposed Method
3.2.1. An Abstraction of the Living Space
3.2.2. Creating Activity Maps Starting from the Sensor Data
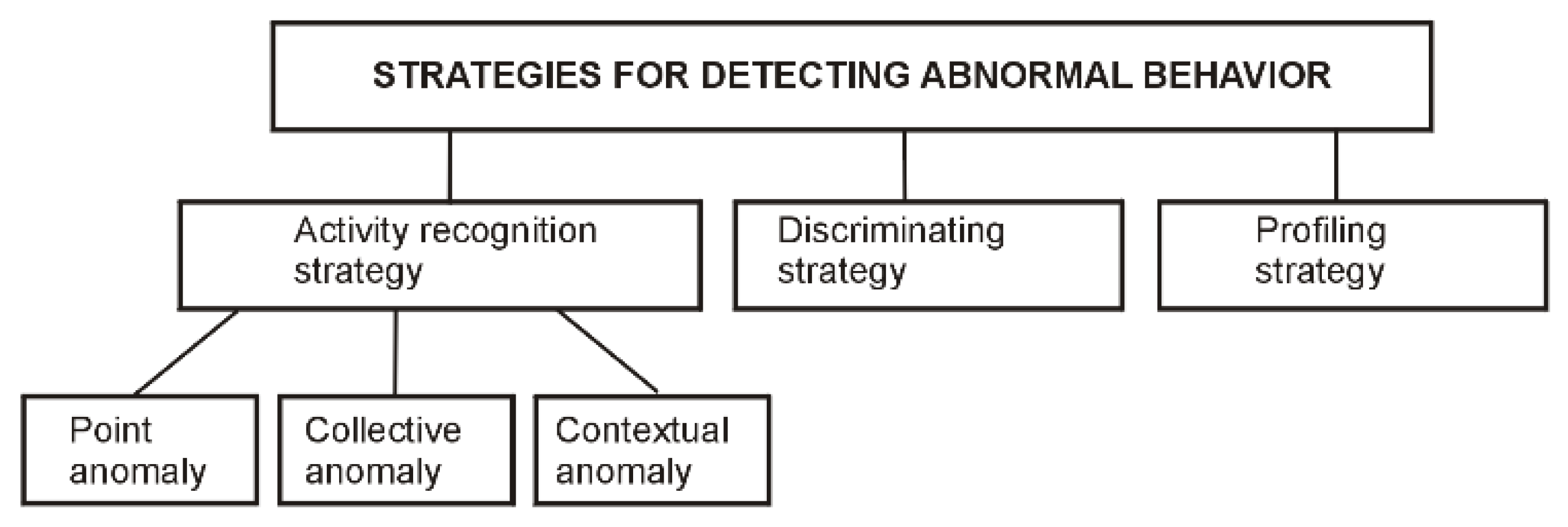
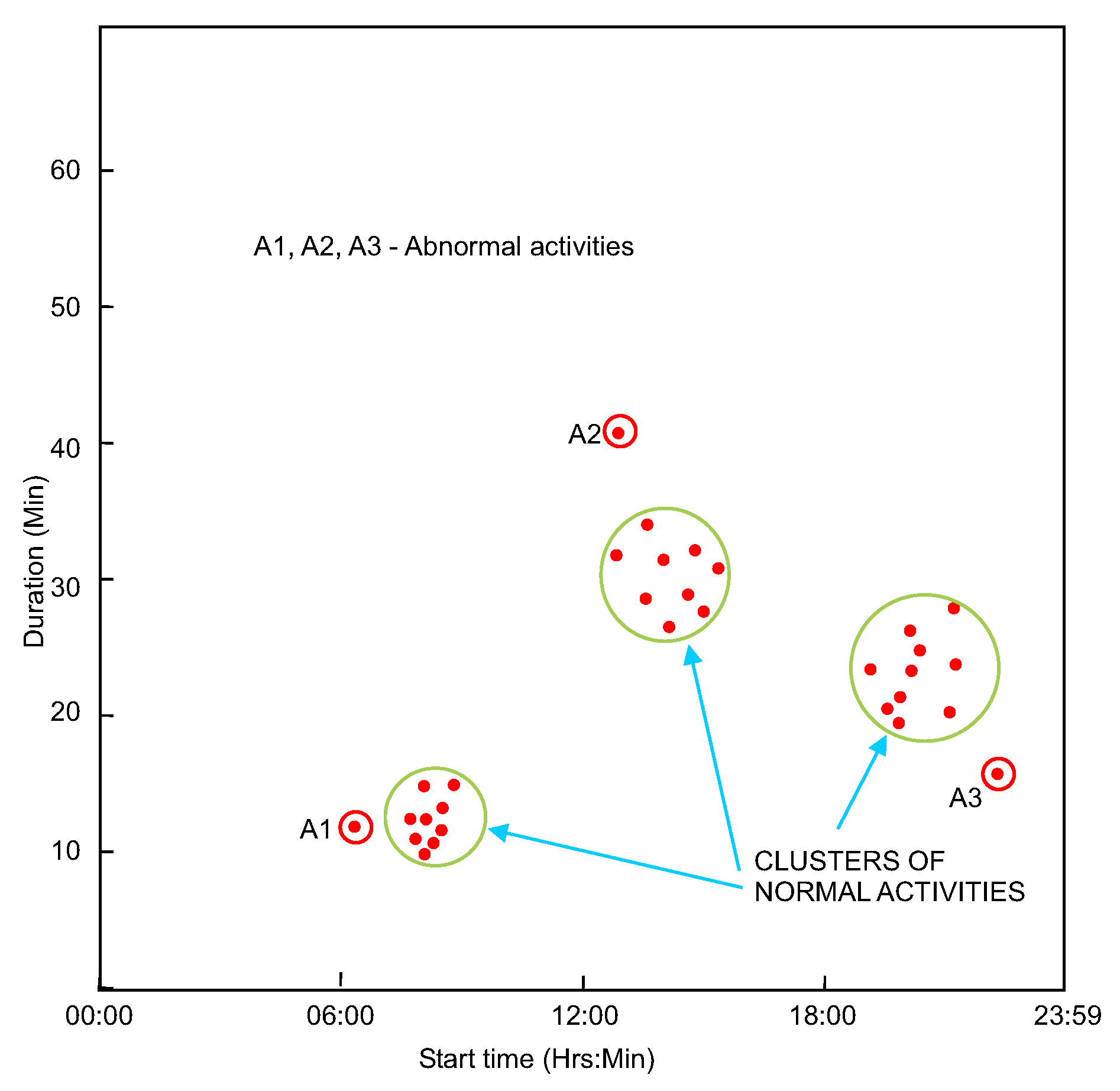
3.2.3. Detection of Abnormal Behavior
3.3. Filtering False Alerts
3.4. Datasets
4. Results
4.1. Results with the CASAS HH126 Dataset
4.2. Results with the Kasteren House C Dataset
5. Discussion
- -
- The complexity of the solution;
- -
- The amount and level of the expert knowledge needed for the implementation and installation;
- -
- The type of sensors used;
- -
- The vulnerability to sensor faults;
- -
- The availability of training datasets.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Appendix A
Appendix A.1. Hardware
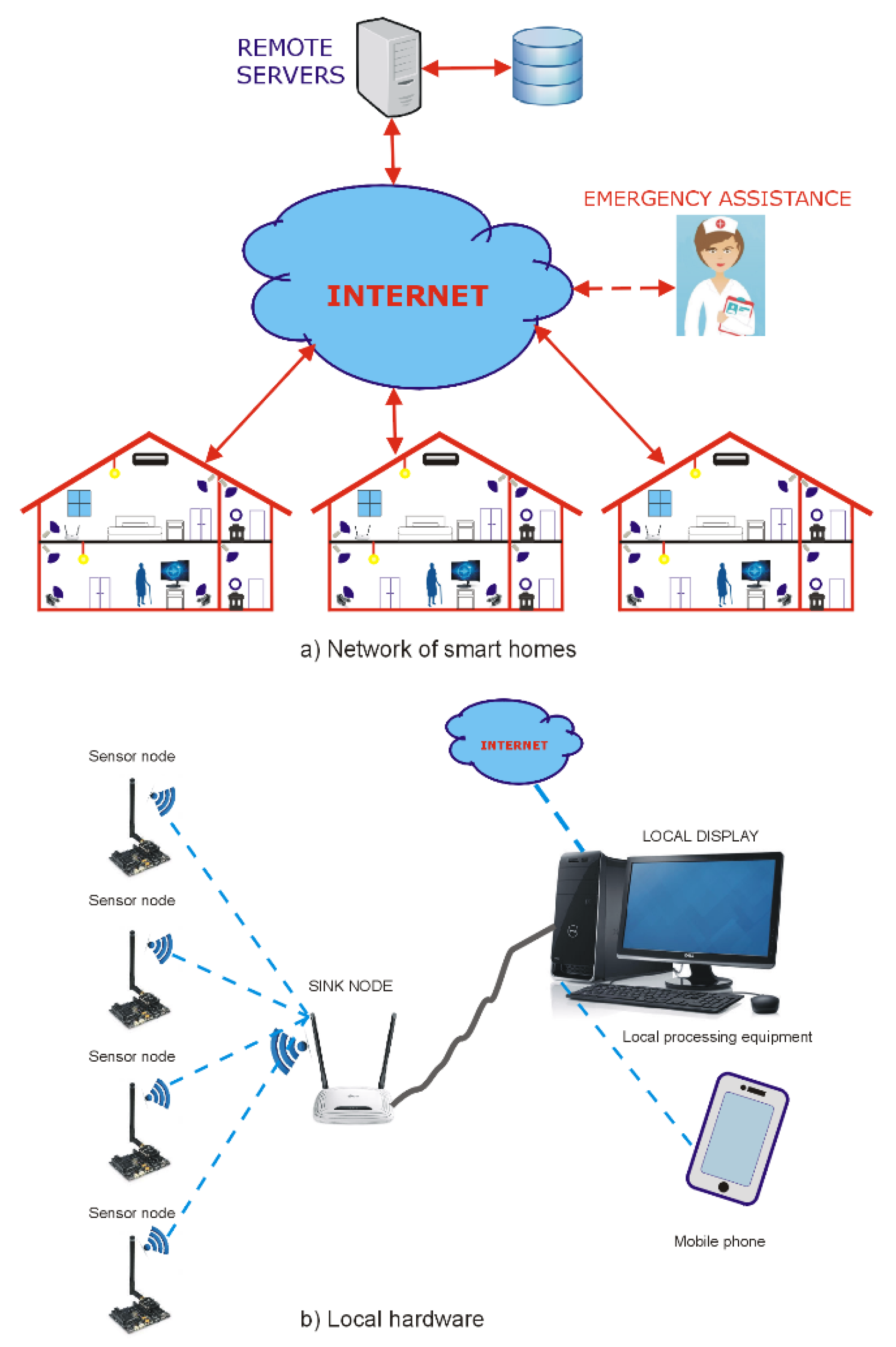
Appendix A.2. Requirements for the Software Components of the System
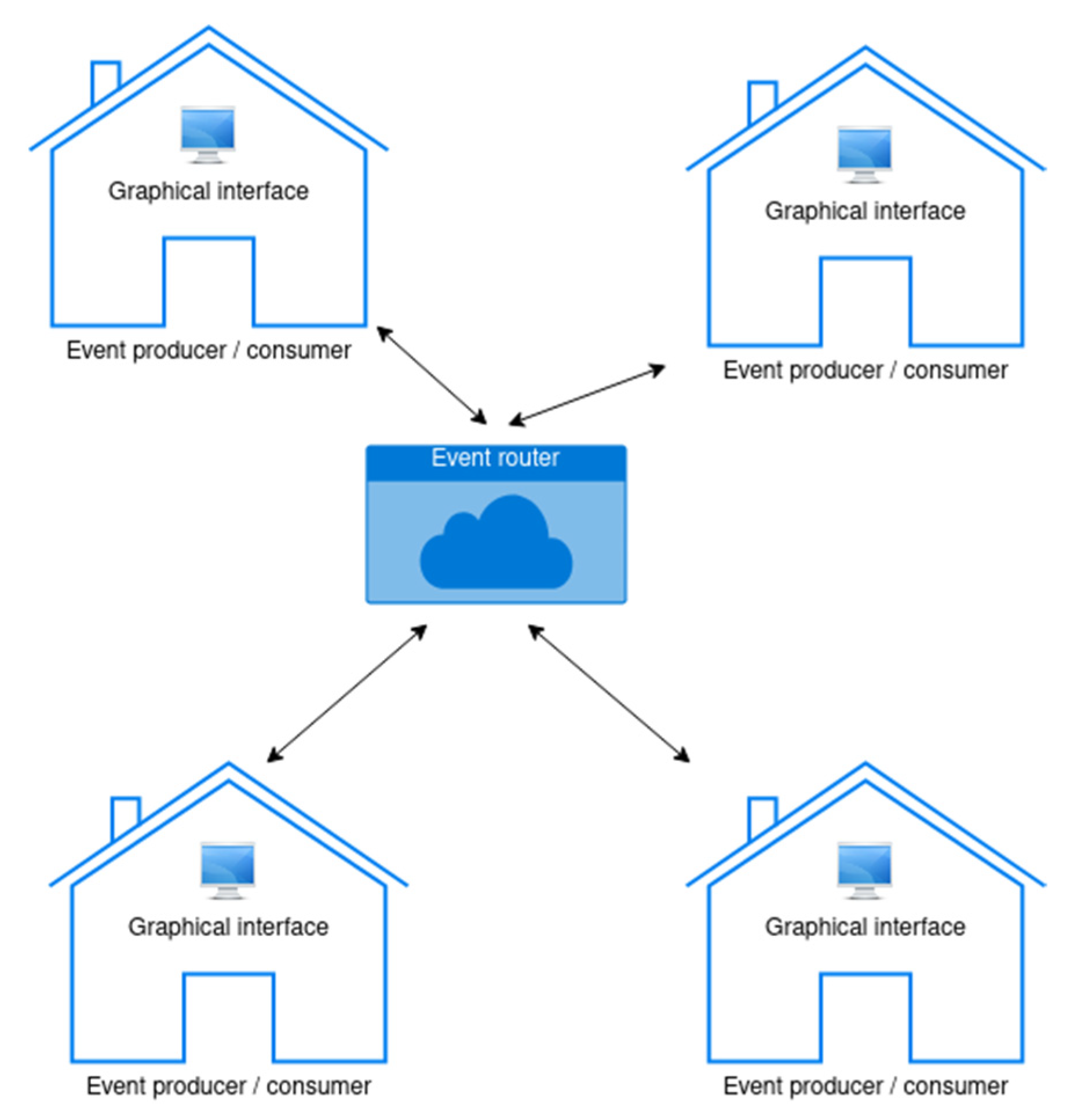
References
- United Nations, Department of Economic and Social Affairs, Population Division. World Population Prospects 2019: Ten Key Findings. Available online: https://population.un.org/wpp/Publications/Files/WPP2019_10KeyFindings.pdf (accessed on 23 October 2021).
- Wiles, J.L.; Leibing, A.; Guberman, N.; Reeve, J.; Allen, R.E. The Meaning of “Aging in Place” to Older People. Gerontologist 2012, 52, 357–366. [Google Scholar] [CrossRef] [PubMed]
- Dean, A.; Venkataramani, A.; Kimmel, S. Mortality Rates From COVID-19 Are Lower In Unionized Nursing Homes: Study Examines Mortality Rates in New York Nursing Homes. Health Aff. 2020, 39, 1993–2001. [Google Scholar] [CrossRef] [PubMed]
- Andrews, G.; Faulkner, D.; Andrews, M. A Glossary of Terms for Community Health Care and Services for Older Persons; WHO Document; WHO Centre for Health Development: Kobe, Japan, 2004. [Google Scholar]
- Stowe, S.; Harding, S. Telecare, Telehealth and Telemedicine. Eur. Geriatr. Med. 2010, 1, 193–197. [Google Scholar] [CrossRef]
- Bennett, J.; Rokas, O.; Chen, L. Healthcare in the Smart Home: A Study of Past, Present and Future. Sustainability 2017, 9, 840. [Google Scholar] [CrossRef] [Green Version]
- Ullah, I.; Kim, D. An Improved Optimization Function for Maximizing User Comfort with Minimum Energy Consumption in Smart Homes. Energies 2017, 10, 1818. [Google Scholar] [CrossRef] [Green Version]
- Blumendorf, M. Building Sustainable Smart Homes. In Proceedings of the 1st International Conference on Information and Communication Technologies for Sustainability, Zürich, Switzerland, 14–16 February 2013; pp. 151–158. [Google Scholar]
- Ni, Q.; García Hernando, A.; de la Cruz, I. The Elderly’s Independent Living in Smart Homes: A Characterization of Activities and Sensing Infrastructure Survey to Facilitate Services Development. Sensors 2015, 15, 11312–11362. [Google Scholar] [CrossRef]
- Majumder, S.; Aghayi, E.; Noferesti, M.; Memarzadeh-Tehran, H.; Mondal, T.; Pang, Z.; Deen, M. Smart Homes for Elderly Healthcare—Recent Advances and Research Challenges. Sensors 2017, 17, 2496. [Google Scholar] [CrossRef] [Green Version]
- Maswadi, K.; Ghani, N.B.A.; Hamid, S.B. Systematic Literature Review of Smart Home Monitoring Technologies Based on IoT for the Elderly. IEEE Access 2020, 8, 92244–92261. [Google Scholar] [CrossRef]
- Cicirelli, G.; Marani, R.; Petitti, A.; Milella, A.; D’Orazio, T. Ambient Assisted Living: A Review of Technologies, Methodologies and Future Perspectives for Healthy Aging of Population. Sensors 2021, 21, 3549. [Google Scholar] [CrossRef]
- Calvaresi, D.; Cesarini, D.; Sernani, P.; Marinoni, M.; Dragoni, A.F.; Sturm, A. Exploring the Ambient Assisted Living Domain: A Systematic Review. J. Ambient. Intell. Humaniz. Comput. 2017, 8, 239–257. [Google Scholar] [CrossRef]
- Demiris, G.; Hensel, B.K. Technologies for an Aging Society: A Systematic Review of “Smart Home” Applications. Yearb. Med. Inform. 2008, 17, 33–40. [Google Scholar]
- Majumder, S.; Mondal, T.; Deen, M. Wearable Sensors for Remote Health Monitoring. Sensors 2017, 17, 130. [Google Scholar] [CrossRef]
- Darwish, A.; Hassanien, A.E. Wearable and Implantable Wireless Sensor Network Solutions for Healthcare Monitoring. Sensors 2011, 11, 5561–5595. [Google Scholar] [CrossRef] [Green Version]
- Tokunaga, S.; Horiuchi, H.; Takatsuka, H.; Saiki, S.; Matsumoto, S.; Nakamura, M.; Yasuda, K. Towards Personalized and Context-Aware Reminder Service for People with Dementia. In Proceedings of the 2016 International Joint Conference on Neural Networks (IJCNN), Vancouver, BC, Canada, 24–29 July 2016; pp. 2946–2953. [Google Scholar] [CrossRef]
- Matic, A.; Osmani, V.; Mayora, O. Trade-Offs in Monitoring Social Interactions. IEEE Commun. Mag. 2013, 51, 114–121. [Google Scholar] [CrossRef]
- Gamberini, L.; Raya, M.A.; Barresi, G.; Fabregat, M.; Ibanez, F.; Prontu, L. Cognition, Technology and Games for the Elderly: An Introduction to ELDERGAMES Project. PsychNology J. 2006, 4, 285–308. [Google Scholar]
- Wang, Z.; Ramamoorthy, V.; Gal, U.; Guez, A. Possible Life Saver: A Review on Human Fall Detection Technology. Robotics 2020, 9, 55. [Google Scholar] [CrossRef]
- Wang, Z.; Yang, Z.; Dong, T. A Review of Wearable Technologies for Elderly Care That Can Accurately Track Indoor Position, Recognize Physical Activities and Monitor Vital Signs in Real Time. Sensors 2017, 17, 341. [Google Scholar] [CrossRef] [Green Version]
- Li, R.; Lu, B.; McDonald-Maier, K.D. Cognitive Assisted Living Ambient System: A Survey. Digital Communications and Networks 2015, 1, 229–252. [Google Scholar] [CrossRef] [Green Version]
- Peetoom, K.K.B.; Lexis, M.A.S.; Joore, M.; Dirksen, C.D.; De Witte, L.P. Literature Review on Monitoring Technologies, and Their Outcomes in Independently Living Elderly People. Disabil. Rehabil. Assist. Technol. 2015, 10, 271–294. [Google Scholar] [CrossRef] [PubMed]
- Debes, C.; Merentitis, A.; Sukhanov, S.; Niessen, M.; Frangiadakis, N.; Bauer, A. Monitoring Activities of Daily Living in Smart Homes: Understanding Human Behavior. IEEE Signal Process. Mag. 2016, 33, 81–94. [Google Scholar] [CrossRef]
- Pavel, M.; Jimison, H.B.; Wactlar, H.D.; Hayes, T.L.; Barkis, W.; Skapik, J.; Kaye, J. The Role of Technology and Engineering Models in Transforming Healthcare. IEEE Rev. Biomed. Eng. 2013, 6, 156–177. [Google Scholar] [CrossRef] [PubMed]
- Pirzada, P.; Wilde, A.; Doherty, G.H.; Harris-Birtill, D. Ethics and Acceptance of Smart Homes for Older Adults. Inform. Health Soc. Care 2021, 1–28. [Google Scholar] [CrossRef] [PubMed]
- Bakar, U.A.B.U.A.; Ghayvat, H.; Hasanm, S.F.; Mukhopadhyay, S.C. Activity and Anomaly Detection in Smart Home: A Survey. In Next Generation Sensors and Systems; Mukhopadhyay, S.C., Ed.; Smart Sensors, Measurement and Instrumentation; Springer International Publishing: Cham, Switzerland, 2016; Volume 16, pp. 191–220. ISBN 978-3-319-21670-6. [Google Scholar]
- Zekri, D.; Delot, T.; Thilliez, M.; Lecomte, S.; Desertot, M. A Framework for Detecting and Analyzing Behavior Changes of Elderly People over Time Using Learning Techniques. Sensors 2020, 20, 7112. [Google Scholar] [CrossRef] [PubMed]
- Lotfi, A.; Langensiepen, C.; Mahmoud, S.M.; Akhlaghinia, M.J. Smart Homes for the Elderly Dementia Sufferers: Identification and Prediction of Abnormal Behaviour. J. Ambient. Intell. Humaniz. Comput. 2012, 3, 205–218. [Google Scholar] [CrossRef]
- Arifoglu, D.; Bouchachia, A. Detection of Abnormal Behaviour for Dementia Sufferers Using Convolutional Neural Networks. Artif. Intell. Med. 2019, 94, 88–95. [Google Scholar] [CrossRef] [PubMed]
- Ordóñez, F.J.; de Toledo, P.; Sanchis, A. Sensor-Based Bayesian Detection of Anomalous Living Patterns in a Home Setting. Pers. Ubiquit. Comput. 2015, 19, 259–270. [Google Scholar] [CrossRef]
- Yahaya, S.W.; Lotfi, A.; Mahmud, M. Detecting Anomaly and Its Sources in Activities of Daily Living. SN Comput. Sci. 2021, 2, 14. [Google Scholar] [CrossRef]
- Alberdi Aramendi, A.; Weakley, A.; Aztiria Goenaga, A.; Schmitter-Edgecombe, M.; Cook, D.J. Automatic Assessment of Functional Health Decline in Older Adults Based on Smart Home Data. J. Biomed. Inform. 2018, 81, 119–130. [Google Scholar] [CrossRef]
- Fahad, L.G.; Rajarajan, M. Anomalies Detection in Smart-Home Activities. In Proceedings of the 2015 IEEE 14th International Conference on Machine Learning and Applications (ICMLA), Miami, FL, USA, 9–11 December 2015; pp. 419–422. [Google Scholar]
- Sprint, G.; Cook, D.; Fritz, R.; Schmitter-Edgecombe, M. Detecting Health and Behavior Change by Analyzing Smart Home Sensor Data. In Proceedings of the 2016 IEEE International Conference on Smart Computing (SMARTCOMP), St. Louis, MO, USA, 18–20 May 2016; pp. 1–4. [Google Scholar]
- Kealy, A.; McDaid, K.; Loane, J.; Walsh, L.; Doyle, J. Derivation of Night Time Behaviour Metrics Using Ambient Sensors. In Proceedings of the ICTs for Improving Patients Rehabilitation Research Techniques, Venice, Italy, 5–8 May 2013. [Google Scholar]
- Barsocchi, P.; Cimino, M.G.C.A.; Ferro, E.; Lazzeri, A.; Palumbo, F.; Vaglini, G. Monitoring Elderly Behavior via Indoor Position-Based Stigmergy. Pervasive Mob. Comput. 2015, 23, 26–42. [Google Scholar] [CrossRef]
- Tan, Z.; Xu, L.; Zhong, W.; Guo, X.; Wang, G. Online Activity Recognition and Daily Habit Modeling for Solitary Elderly through Indoor Position-Based Stigmergy. Eng. Appl. Artif. Intell. 2018, 76, 214–225. [Google Scholar] [CrossRef]
- Palumbo, F.; La Rosa, D.; Ferro, E. Stigmergy-based long-term monitoring of indoor users mobility in ambient assisted living environments: The DOREMI project approach. In Proceedings of the BT—2nd Italian Workshop on Artificial Intelligence for Ambient Assisted Living (AI*AAL @ AI*IA 2016), Genova, Italy, 28 November 2016; Volume 1803, pp. 18–32. [Google Scholar]
- Aran, O.; Sanchez-Cortes, D.; Do, M.-T.; Gatica-Perez, D. Anomaly Detection in Elderly Daily Behavior in Ambient Sensing Environments. In Human Behavior Understanding; Chetouani, M., Cohn, J., Salah, A.A., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2016; Volume 9997, pp. 51–67. ISBN 978-3-319-46842-6. [Google Scholar]
- Pazhoumand-Dar, H.; Armstrong, L.J.; Tripathy, A.K. Detecting Deviations from Activities of Daily Living Routines Using Kinect Depth Maps and Power Consumption Data. J. Ambient. Intell Human Comput 2020, 11, 1727–1747. [Google Scholar] [CrossRef]
- Nurmi, P.; Koolwaaij, J. Identifying meaningful locations. In Proceedings of the 2006 Third Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services, San Jose, CA, USA, 17–21 July 2006; pp. 1–8. [Google Scholar] [CrossRef]
- Susnea, I.; Dumitriu, L.; Talmaciu, M.; Pecheanu, E.; Munteanu, D. Unobtrusive Monitoring the Daily Activity Routine of Elderly People Living Alone, with Low-Cost Binary Sensors. Sensors 2019, 19, 2264. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Susnea, I. Engineering Human Stigmergy. Int. J. Comput. Commun. Control. 2015, 10, 420–427. [Google Scholar] [CrossRef] [Green Version]
- MATLAB Central File Exchange. John D’Errico A Suite of Minimal Bounding Objects. Available online: https://www.mathworks.com/matlabcentral/fileexchange/34767-a-suite-of-minimal-bounding-objects (accessed on 24 September 2021).
- Sugeno, M. Industrial Applications of Fuzzy Control; Elsevier Science Inc.: Amsterdam, The Netherlands, 1985. [Google Scholar]
- CASAS Activity Recognition Datasets. Available online: https://data.casas.wsu.edu/download/ (accessed on 24 September 2021).
- Kasteren Activity Recognition Datasets. Available online: https://sites.google.com/site/tim0306/datasets (accessed on 21 February 2019).
- Naslund, J.A.; Aschbrenner, K.A.; Marsch, L.A.; Bartels, S.J. The Future of Mental Health Care: Peer-to-Peer Support and Social Media. Epidemiol. Psychiatr. Sci. 2016, 25, 113–122. [Google Scholar] [CrossRef] [Green Version]
- Hosim, M.; Sulaiman, M.N. A Review on Evaluation Metrics for Data Classification Evaluations. IJDKP 2015, 5, 1–11. [Google Scholar] [CrossRef]



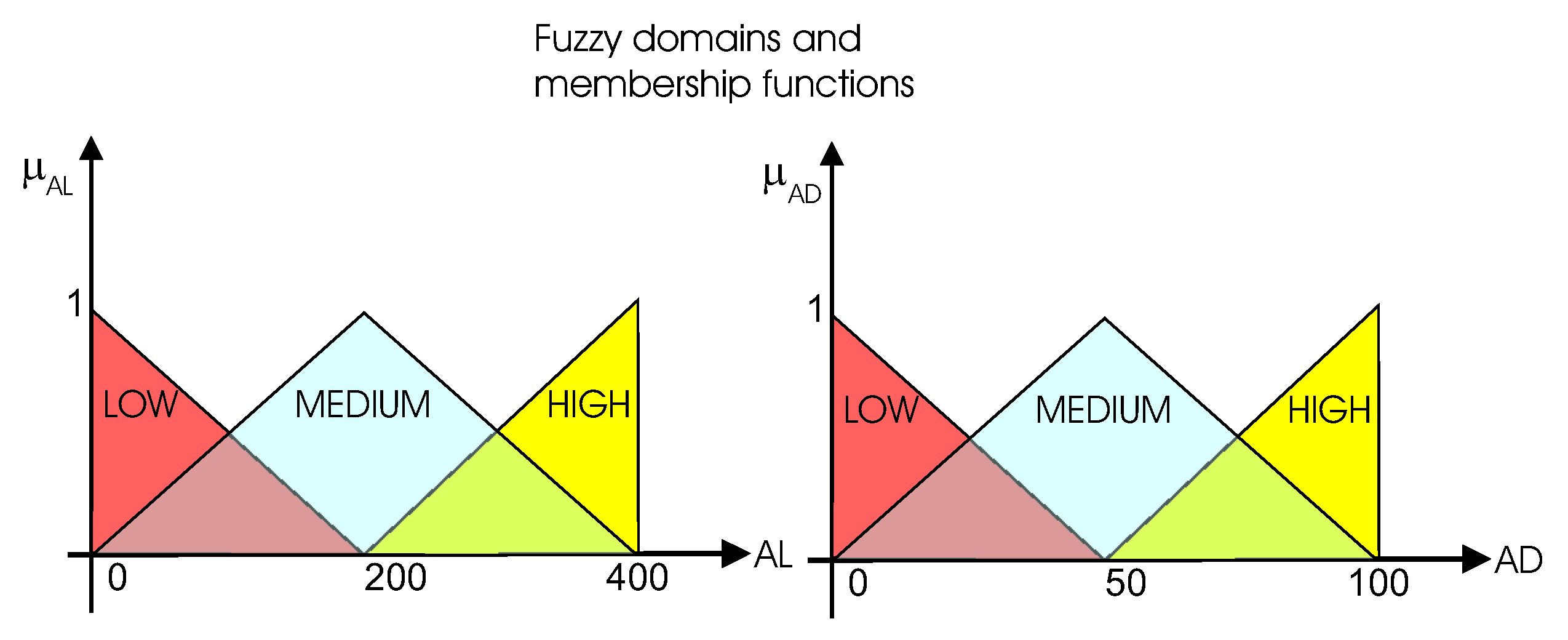



| Activity Level (AL) | Activity Deviation (AD) | Probability of False Alerts (PFA) |
|---|---|---|
| LOW | LOW | MEDIUM |
| LOW | MEDIUM | LOW |
| LOW | HIGH | LOW |
| MEDIUM | LOW | MEDIUM |
| MEDIUM | MEDIUM | MEDIUM |
| MEDIUM | HIGH | LOW |
| HIGH | LOW | HIGH |
| HIGH | MEDIUM | HIGH |
| HIGH | HIGH | HIGH |
| Criterion\Study | Zekri et al. Ref. [28] | Aran et al. Ref [40] | Pazhoumand et al. Ref. [41] | This Work |
|---|---|---|---|---|
| Complexity/Cost | High | High | High | Low |
| Scalability | Low | Low | Low | High |
| Unobtrusivenes | High | High | High | High |
| Usability | Low | Medium | Medium | High |
| Adaptability | Low | Medium | Medium | High |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Susnea, I.; Pecheanu, E.; Sandu, C.; Cocu, A. A Scalable Solution to Detect Behavior Changes of Elderly People Living Alone. Appl. Sci. 2022, 12, 235. https://doi.org/10.3390/app12010235
Susnea I, Pecheanu E, Sandu C, Cocu A. A Scalable Solution to Detect Behavior Changes of Elderly People Living Alone. Applied Sciences. 2022; 12(1):235. https://doi.org/10.3390/app12010235
Chicago/Turabian StyleSusnea, Ioan, Emilia Pecheanu, Cristian Sandu, and Adina Cocu. 2022. "A Scalable Solution to Detect Behavior Changes of Elderly People Living Alone" Applied Sciences 12, no. 1: 235. https://doi.org/10.3390/app12010235
APA StyleSusnea, I., Pecheanu, E., Sandu, C., & Cocu, A. (2022). A Scalable Solution to Detect Behavior Changes of Elderly People Living Alone. Applied Sciences, 12(1), 235. https://doi.org/10.3390/app12010235






