1. Introduction
The Internet of Things (IoT) is a set of interrelated electronic devices, mechanical and digital machines, objects, animals, or people that have unique identifiers. IoT can transfer data over a network without requiring human-to-human interaction or the interposition of a human being with a computer [
1]. With the emergence of IoT, there are multiple devices connected to a telecommunication network, from household appliances to industrial machines. All these devices can be controlled remotely without requiring human presence or interaction. With the advancement and development of IoT, the study of autonomous device networks has been given more priority.
However, IoT devices are expose to a series of threats. The most common threats are viruses and denial of service (DOS) attacks.
Table 1 indicates the category of IoT attacks based on infrastructure components [
2].
The exponential growth of IoT devices is surround by security and privacy risks. IoT implementations must be build ensuring easy and secure control [
3]. The process of developing IoT systems requires in-depth knowledge in various areas, such as risks, threats, and vulnerabilities, to guarantee secure systems. By having massive IoT devices connected, cybersecurity measures must be defined to carry out an in-depth defense of the devices and information that are transmitted. To minimize threats in IoT, fluid policies must apply in the implementation processes.
The International Telecommunication Union (ITU) defines cybersecurity as the set of tools, policies, security concepts, security safeguards, guidelines, risk management methods, actions, training, best practices, insurance, and technologies that can be used to protect the assets of the organization and users in the cyber environment [
4]. Cybersecurity in IoT is a factor that must be considered in the implementation and development of IoT devices, because an IoT device with its default configuration is a notorious victim for cybercriminals.
In this same approach, Center for Internet Security (CIS) defines methodologies based on hardening that increase the security levels of different types of devices, which serve to mitigate the most attacks common against various information systems and networks. There are 20 CIS Controls that are classified as basic, foundational, and organizational that are applied to reduce the attack vectors of network, adjacent, local, and physical [
5]. The hardening process needs a risk assessment to identify the points or elements where hardening should be implemented. So, in addition to the CIS Controls, there are standards that allow processes, such as risk assessment, information security management, and standardization of IoT architectures. One of the main organizations that is responsible for generating and standardizing these standards is the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC).
In the same way, ISO is a worldwide federation of national standards bodies that is responsible for developing international standards. The development of various standards is normally carried out through ISO technical committees. There are multiple ISO standards, such as the ISO/IEC 30,141, ISO/IEC 27,001, ISO/IEC 31,000, and ISO/IEC 25,010 standards, will be used as a basis. The ISO/IEC 30,141 standard is a reference architecture for IoT designers and developers. The ISO/IEC 27,001 standard is a guideline oriented to Information Security Management Systems (ISMS), which allows compliance with the confidentiality and integrity of ISMS [
6]. The ISO/IEC 31,000 standard is a guide that makes it possible to measure the impact of different risks according to the type of activity to be carried out and according to the nature of the risk [
7]. The ISO/IEC 25,010 standard is a model that allows the evaluation of product quality. The characteristics and quality properties of a software product are determined [
8].
In the same vein, Open Web Application Security Project (OWASP) IoT methodology is a project carried out by professionals specialized in the field of cybersecurity for reducing the risks and the impact of various vulnerabilities, both external and internal [
9]. This project indicates the attack surface areas of IoT devices, such as: ecosystem, device memory, device physical interfaces, device web interfaces, device firmware, device network services, administrative interface, local data storage, cloud web interface, third-party backend Application Programming Interfaces (APIs), update mechanism, mobile application, vendor backend APIs, ecosystem communication, network traffic, authentication, authorization, privacy, and hardware. There are elements of the attack surface that are more vulnerable, and they do not depend on third parties. So, the hardening process will be applied to these elements to reduce vulnerabilities and allow the correct functioning of the IoT system. Based on the literature review, there are few proposals that provide a step-by-step guide to validate IoT security. Most of the research related to IoT assessment are based on risks analysis but they do not consider the aspects of attack surface of IoT devices. Therefore, based on this gap, we propose an evaluation of attack surface based on Relative Attack Surface Quotient (RASQ) proposal. A second gap is the adaptation of risk tools for IoT systems, our contribution in this study is defined a risk matrix based on the impact which is define for compliance classes and the probability of occurrence of cyberattacks. A third contribution of this study is providing a 17-step security checklist steps for IoT system to determine the risk and attack surface in each layer of the IoT architecture. Finally, a case study was conducted to validate the security methodology proposal for IoT systems.
This paper discusses a review of literature related to cybersecurity, risk analysis, and implementation tests in IoT solutions to know the advantages and disadvantages of IoT. At the end of the literature review, a practicable cybersecurity model is proposed using the best existing norms, standards, guides, and methodologies. This model allows the implementation of secure IoT systems for professionals and researchers. The main objective of the proposed model is to reduce risks, threats, and vulnerabilities in IoT systems.
The rest of the paper is organized, as follows. In
Section 2, a search of related papers to review is presented. In
Section 3, an analysis of previous works is performed.
Section 4 contains the proposed solution where all the development carried out is explained step by step.
Section 5 presents the results found in the development of the proposal.
Section 6 contains the discussion based on the results finally obtained, and
Section 7 presents the conclusions and future work.
2. Related Work
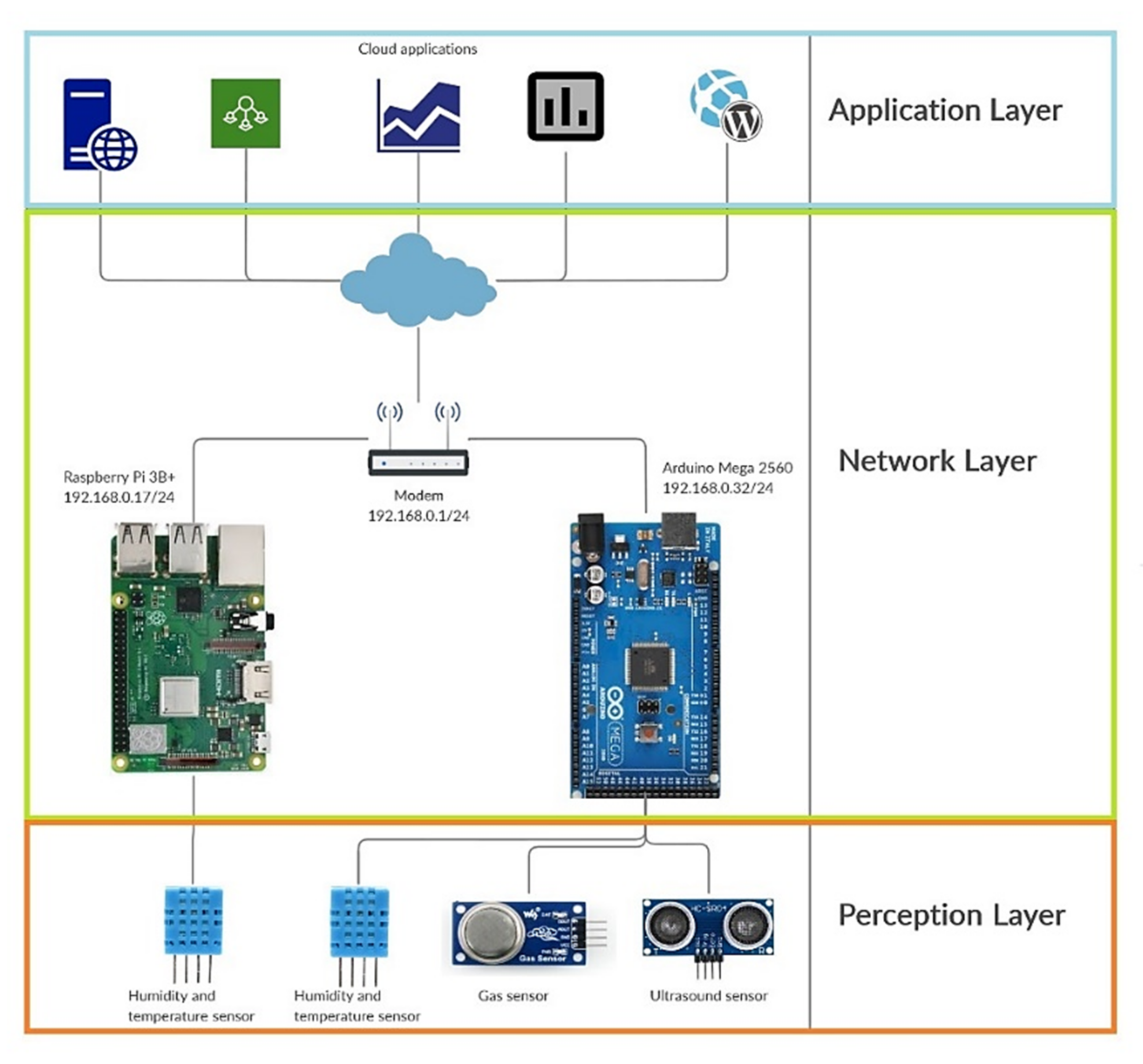
IoT consists of two architectural models that operate through layers, each of which has its specific function, and has its own protocols [
10].
Figure 1 indicates the architectures that exist in IoT.
The three-layer model A consists of the application layer, the network layer, and the perception layer. The B model has the same layers except the network layer, and additionally it consists the business layer, the processing layer, and transport layer; see
Table 2.
Cyberattacks violates the purpose of the IoT system take advantage of vulnerabilities on software or hardware level. Leite et al. [
11] summarizes the main vulnerabilities reported for IoT devices based on the OWASP Internet of Things Project. They classify these vulnerabilities by test routine groups. In this context, Tien et al. [
12] presents the Universal Firmware vulnerability Observer (UFO). UFO is a system that discovers vulnerabilities in the firmware of IoT devices. It scrutinizes the embedded file system of the firmware, identifies vulnerabilities, and scans for password leaks. The UFO tool was designed based on IoT firmware verification standards, such as OWASP, UL-2900, and ICSA Labs. Through analysis, the authors concluded that 73% of firmware files contain vulnerabilities in their embedded Linux kernel, 22% of firmware files leak passwords, and 6% of firmware files contain hidden backdoors.
Lee et al. [
13] explore vulnerabilities of IoT services focusing on three aspects: device itself, wearable gateway, and server. They perform the following attack scenarios: namely an illegal device pairing attack, a fake wearable gateway attack, and an insecure code-based attack. The authors analyze these attacks using the OWASP IoT Top 10 attacks in IoT systems guide and propose solutions to prevent these attacks.
W. Zhang et al. [
14] implement three types of honeypots to capture malicious behaviors. Based on the Common Vulnerabilities and Exposures (CVE) CVE-2017-17215 they implement a honeypot that simulates specific UPnP services of the router. Universal Plug and Play (UPnP) details are limited, they used the firmware of a real IoT device to match the vulnerability and allow high interaction in the honeypot. Simple Object Access Protocol (SOAP) service ports were added to the honeypot to provide honeynet capabilities and features. The authors provided a hybrid service of a real device and simulation honeypots.
K. Li et al. [
15] propose an open-source intelligence framework (OSIF) that enables intelligent event-based cyber threats to be analyzed. OSIF performs machine learning through data mining to extract event-related information. It uses vulnerabilities and CVEs to store the profile of threat actors. The authors performed a structural and conceptual evaluation of critical threats on the dataset collected from dozens of websites.
On this point, developing a process to reduce these vulnerabilities using cybersecurity approaches is relevant. For instance, Sengan et al. [
16] investigates security issues in smart city infrastructure development. The method used focuses on threats and security data. They provide a high-level Hybrid Smart City Cyber Security Architecture (HSCCA) for the creation of a smart city considering important factors, such as valuable data collection, caching, retrieval, and organization of network resources. The authors recommend a context-specific security configuration for cyber-physical systems.
Visoottiviseth et al. [
17] designed and developed “A System for Preventing IoT Device Attacks on Home Wi-Fi Router” (SPIDAR) to protect home Wi-Fi networks. The elements used for this system were a home Wi-Fi router, a Raspberry Pi, and a web application to prevent attacks and display attack statistics to home users. In addition, they used the Snort Intrusion Prevention System (IPS) that analyzes the behavior of IoT devices in use. SPIDAR prevents five main types of attacks specified in the OWASP IoT Top 10 vulnerabilities 2018.
Additionally, Visoottiviseth, Akarasirwong, and Chaiyasart [
18] develop a penetration testing system for IoT devices called PENTOS. This system automatically collects information from IoT devices through wireless communication. The system allows users to perform various types of penetration testing on their IoT devices, such as password attack, web attack, and wireless attack. This system aims to raise user awareness by providing basic information on OWASP’s top 10 IoT vulnerabilities.
Shu et al. [
19] related with a security and privacy analysis of IoT toys for children. Three IoT toys were examined to gain an understanding of the smart toy security and privacy landscape. Through a static and dynamic analysis, vulnerabilities related to the inappropriate use of encryption and authentication, reuse of the Positive Operating System Test (POST) token, confidential user information in crash reports and secret keys in the source code were discovered. Additionally, a small set of third-party analytics platforms receive data from all examined toys, possibly allowing for detailed user data collection. These vulnerabilities violate individual toy privacy policies, as well as federal Children’s Online Privacy Protection Act (COPPA) regulations for handling children’s data.
M. Mohsin et al. [
20] present the IoTChecker framework that allows IoT configurations to be semantically modeled. The purpose is to stop security configuration anomalies and analyze IoT-specific threat vectors. To perform the analysis of the configurations, the context of interactions and dependencies of the IoT systems is described. The evaluation carried out includes the security classifications and security analysis of the configurations of 954 IoT products. The automated approach used allows it to be scalable, easily manageable, formally verifiable, and free from errors induced by tedious manual configurations.
Similar approach was performed by Akatyev et al. [
21]. The authors conduct a study focused on IoT systems that were used in smart homes. The proposed objective is to anticipate cyber threats to these IoT systems. The authors propose a user centric IoT network model for the near future. The characteristics, devices, services, and data flows of this network are described. This network model describes the most common attacks, such as intrusions, death, privacy failure, and extensible device involvement. To conclude, they carry out a threat analysis based on these use cases, which describes the cyber-physical risks that allow demonstrating the potential for device exploitation.
A. Di Giorgio et al. [
22] propose a security framework and advanced tools to adequately manage vulnerabilities and react in a timely manner to threats. This proposed architecture fills the gap between computing and theoretical control approaches. S. Rizvi et al. [
23] analyze critical devices and associated vulnerabilities and highlights the need for rigorous security controls. It evaluates the attack vectors for IoT devices focused on central, such as healthcare, retail, and home. This paper identifies the threats caused by device-level vulnerabilities, the application of appropriate security controls to close vulnerabilities and minimize the possibility of threats occurring.
However, it is important to improve cybersecurity in IoT systems through guidelines or standards. In that way, Matheu-García et al. [
24] proposes an IoT security certification methodology that allows to evaluate security solutions for large-scale IoT deployments in an automated way. The certification approach is carried out using the security risk assessment and testing methodologies presented by the European Telecommunications Standards Institute (ETSI). The guides and standards presented by ETSI are based on the international standards ISO/IEC 31,000 and ISO/IEC 29,119. The authors carry out a security risk assessment composed of risk identification, risk estimation, and risk assessment activities. The security tests performed consist of design and implementation tests, and the development of test environment. This certification process includes monitoring the devices during their life cycle.
Khan et al. [
25] proposes an ontology that allows establishing security guidelines for interoperability and understanding between smart home actors. The authors indicate the security guidelines to be performed to exchange knowledge. This research allows understanding the concepts that interact in the smart home ecosystem. The authors proposed two use cases for demonstrating how the ontology is applied to automate the execution of security guidelines. J. Li [
26] synchronizes in a matrix the vulnerabilities of the OWASP IoT Top 10 project and the 25 most dangerous Common Weakness Enumeration (CWE)/ SysAdmin, Audit, Network, and Security (SANS) software bugs. He realizes a security framework that allows to review code vulnerabilities having a higher accuracy of the findings.
N. Teodoro, C. Serrão [
27] identify the relationship between lack of security and Software Development Life Cycle (SDLC). Based on this analysis, the authors present a set of security automation tools and methodologies that are used in the course of the SDLC to improve the quality of Web applications. In the same vein, J.D.V Mohino et al. [
28] defines a new software development model in which security aspects are evaluated in any phase taking advantage of agile models. This model identifies vulnerabilities from early stages to achieve adequate levels of quality and functionality. In the same line, K. Rindell et al. [
29] perform a study where they identify incompatibilities between security approaches to agile software development, map common activities, processes, practices and artifacts from different guides and standards, such as Microsoft Security Development Lifecycle (SDL), ISO, and OWASP Software Assurance Maturity Model (SAMM).
In the same context, Anderson et al. [
30] demonstrates deficiencies of the ISO/IEC 80,001 standard. This standard due to its outdatedness provides low levels of cybersecurity. This problem occurs due to the evolution of cybersecurity and the long time that exists to review and publish international standards. The authors identified that the following areas require priority in the review of the cybersecurity levels they possess emergency access areas, de-identification of health data, physical locks on devices, data backup, disaster recovery, third-party components in the product life cycle roadmap, transmission confidentiality and transmission integrity. This research presents improvements to the ISO/IEC 80,001 standard to improve security levels and increase the protection provided by cybersecurity.
In the same vein, Azaliah et al. [
31] extensively explore various IoT technologies used in healthcare services and their security challenges. The authors propose an IoT security risk model for healthcare. The goal is to provide a comprehensive risk management process based on ISO/IEC 27,005. This model performs an iterative IoT risk management process, because IoT risks are variable.
I. Skierka [
32] examines the convergence of safety and security risks in healthcare for medical systems in Europe. The analysis conducted indicates that the management of safety and security risks in medical systems require the implementation of existing governance, including regulation, standards, and industry best practices. The authors present policy and industry recommendations for improving the cybersecurity of medical systems in Europe. This paper draws comparisons with cybersecurity guidelines, technical controls, standards, and best practices in the U.S. medical device security arena.
Additionality, Safa et al. [
33] presents an information security management model aimed at mitigating the risk of information security breaches in an industrial environment. Using ISO/IEC 27005, Harmonized Threat and Risk Assessment (HTRA), Conducting Security Risk Analysis (CORAS), and Operationally Critical Threat, Asset and Vulnerability Evaluation (OCTAVE) Allegro, the risks to the organization’s assets are identified. The model presented by the authors mitigates information security risk for both service providers and service consumers in this environment. Huang, S. Nazir [
34] evaluates Internet of Medical Things (IoMT) security using the analytic network process (ANP). The performed approach uses the ISO/IEC 27,002 standard. The results of this research show that handling international standards allows obtaining secure IoMT devices.
V. Casola et al. [
35] propose an approach oriented to the analysis of security of IoT systems through an almost completely automated process of threat modeling and risk assessment. This approach allows identifying the security controls to implement to mitigate existing security risks. This research is based on the ISO/IEC 30,141 standard directives.
In the same line, M. Ngamboé et al. [
36] assess the risks in implantable cardiac electronic devices (CIED) using the ISO/IEC 27,005 standard and the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-30 guide. Using a methodical approach, they perform the analysis in three parts that are actor-based, scenario-based and combined. These analyzes make it possible to determine the impact of attacks and measure the probability of the occurrence of threats. The results obtained by the authors indicate that vulnerabilities in CIED’s Radio Frequency (RF) interface represent an acceptable risk. Network and Internet connections in the rest of the system represent a potential risk.
Under this context, the use of risk assessment is a key element for enhanced process. In this way, Kieras et al. [
37] performs a modification of the attack tree model to analyze supply chain risks. This model allows to obtain precise data that describes complex systems of critical Information and Communication Technologies (ICT) and IoT infrastructure. Through case studies, it was found that structural uncertainties constitute a major challenge for the usefulness of this model, and therefore require special attention. The use cases allow to determine that the safety of the components and the reliability of the suppliers can be estimated with an accuracy of 50%, these results show a maximum possible error in the risk assessment of 14%. This percentage of the risk assessment reflects a wide variety of discrete structural errors.
K. Kandasamy et al. [
38] conduct a review of the main existing cyber risk assessment methodologies and their suitability for IoT systems. The cybersecurity frameworks analyzed were National Institute of Standards and Technology, Operationally Critical Threat, Asset, and Vulnerability Evaluation, Threat Assessment & Remediation Analysis, and International Standards Organization. Risk vectors for IoT and Internet of Medical Things (IoMT) were analyzed. Through study, analysis and review, the authors present a method for assessing the risks of IoT systems through the quantification of risk vectors. This method leads to effective risk mitigation strategies and techniques.
I. Lee [
39] reviews IoT cybersecurity technologies and cyber risk management frameworks. The author presents a four-layer IoT cyber risk management framework for allocating financial resources to multiple IoT cybersecurity projects. In addition, a proof-of-concept of the management framework is performed.
Ruan [
40] presents various types of risks that span strategic, regulatory, and systemic sectors. The author conducts a cyber risk analysis, the need to measure cyber risk, its current challenges, and a review of the cost of cybercrime. To measure cyber risk, it uses current methods, such as Common Vulnerability Scoring System (CVSS), CORAS, stochastic modeling, Monte Carlo simulation, and Cyber Value at Risk and Factor Analysis of Information Risk (FAIR). Additional classifies risk factors into technological, non-technological, inherent and control factors.
The last step, after development a risk assessment is enhanced cybersecurity IoT systems. In this way, Yigit et al. [
41] mention that IoT devices can have various vulnerabilities that can lead to serious breaches and security compromises. Therefore, the author emphasizes that hardening IoT systems is of vital importance. The author proposes an algorithm that uses compact attack charts to find a cost-effective solution to protect IoT systems. Extract all the attack vectors that affect critical resources and select the exploit that can be used. The results of the experiment indicate that the proposed algorithm is scalable with the size of the network and IoT nodes.
Maillet-Contoz et al. [
42] present an approach to facilitate the integration, verification, and then functional validation of device security based on modeling and simulation. This approach enables you to increase the quality of your design, ensure better overall system performance, and make it easier to expand the number of end devices. The objective of this proposal is to allow the implementation, verification, and validation of an end-to-end security solution.
In this same line, Stine et al. [
43] propose a computer risk scoring system for evaluating medical devices. This system, using the spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege (STRIDE) model, uses a security questionnaire to weight the risks. To test the efficiency of the system, the authors used three test scenarios with medical devices.
Sancho et al. [
44] run a system to classify security threats, computing their criticality according to the Bug Bar technique, in order to address the threats in order of priority. The authors correlated the severity risk values and the results calculated by the new approach. This proposal could complement the information from Security Information and Event Management (SIEM) systems and help in the prediction of criticalities of future threats. B. Javed et al. [
45] focus on recommended design considerations for IoT devices with the goal of achieving security by default. Default security is achieved by design, focusing on features, such as processing power, power availability, memory, and bandwidth requirements.
3. Analysis of Previous Works
As we have analyzed the hardening process needs to follow a proper methodology. Research shows that there are different approaches that can be adopted to develop the hardening process. Under this context, our research question arises which are the most used leverages to perform a hardening of IoT solutions under a proper methodology and following the best practices established by the specialized organizations in the field of cybersecurity.
To answer the research question, we have conducted a Systematic Literature Review (SLR) based on Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) methodology; see
Figure 2. We select the following scientific databases: MDPI, IEEE Xplorer, Elsevier, and Springer, and define the following search queries:
“IoT” AND “hardening”
“IoT” AND “risk Analysis”
“IoT” AND “cybersecurity testing”
“IoT” AND “cybersecurity assessment”
“IoT” AND “risk” AND “best practice”
In the identification stage, we found 1645 articles, and then we removed 150 duplicates records. In the screening stage, we excluded 1495 records. Then, in the eligibility stage, we excluded 90 records. Finally, in the included stage, we included 60 studies for quality synthesis; see
Figure 2.
Once the 1645 records have been loaded, we can see, in
Figure 3, the most relevant keywords, according to the Rayyan tool used for the screening process.
Based on the qualitative analysis carried out using the systematic review tool Rayyan, we identified nine proposals based on OWASP, ISO, risk analysis, among others, used in research conducted from 2016 to 2021; see
Table 3.
Based on the analysis of the literature review, we can see in
Figure 4 that there are more contributions based on risk analysis, followed by research using OWASP guidelines and ISO standards. There are not a favorable number of contributions related to hardening in IoT systems. This has motivated the present research to focus on the topic of hardening.
One aspect that caught our attention from the literature review is that we did not find in the identified records any leverages for the enhancement of IoT solutions based on CIS (Critical Security Controls). CIS proposals by SysAdmin, Audit, Network, and Security (SANs) institute presents hardening guides developed by cybersecurity professionals. Leveraging CIS is very practical to bring security hardening to a very practical and technical level. CIS helps to strengthen security against the most common attack vectors and its focus on establishing specific controls helps to control hardware and software assets; see
Table 4.
The application of CIS allows to quickly cover security issues versus times that can be long in risk analysis processes, especially in IoT systems that are dynamic and grow in number of devices daily, so waiting for the processes that lead identification of vulnerabilities, qualitative or quantitative analysis can generate a considerable time gap where you can receive an attack. Unlike traditional systems, those based on IoT even have a capacity to amplify the attack due to their level of complexity, which leads to more practical solutions, without obviously neglecting the risk analysis processes, which undoubtedly need to adapt to this new reality.
6. Discussion
In this work, a model has been presented that allows to reduce the risk levels in the IoT system, attack surface, and vulnerabilities by means of the correct execution of the hardening process. IoT systems without a prior procedure contain multiple weaknesses, to know the weaknesses of the system is done through a risk analysis and vulnerability assessments. These procedures are crucial to understand the risks that surround the system. To mitigate these risks, the hardening process is carried out in the layers of the IoT system.
According to the study carried out, most of the improvement models are based on risk analysis based on specific ISO standards. These models pursue policy compliance within specific timeframes, while CIS is agile and fast implementation with effective results. Risk analysis applied to IoT systems are slow and do not adapt to the constant changes that arise. It evaluates more policy compliance with a larger number of controls [
61]. CIS uses fewer controls, and its exploitation is more practical, so it is compatible with development cycles, such as DevOps.
Table 27 shows the comparison between CIS and risks.
To calculate the attack surface of the IoT system, a model based on the RASQ proposal was presented. The risk is calculated in each step of the IoT system elements checklist (
Table 8). To obtain the attack surface of the entire IoT system, the attack surface of each layer is added up and divided by 3. A scale is used to determine whether the attack surface value is adequate. This scale has the values of critic, high, medium, low, and null.
To model all the threats that surround IoT systems, the analysis carried out by the OWASP IoT Top 10 project was considered. This project allows us to identify the threats that generate the most risks in IoT devices. As IoT systems are vulnerable to various attack vectors, compliance classes were used, which can more accurately determine system risks based on levels of confidentiality, integrity, and availability.
When using an embedded system for IoT purposes, the communication protocols to be used must be considered. Today, most embedded systems use protocols that do not contain adequate encryption. In the proposed methodology, to reduce notable risks, the use of protocols with high encryption levels and making the port change of the protocols used stand out.
In a usual port scan with the Nmap tool, the range of known ports (
Table 21) exposed is obtained. In the present methodology to reduce the probability of determining the exposed ports in the IoT system, it is proposed to use a range of ports different from the known ports. Without applying the proposed methodology, four exposed ports were found using the SSH, HTTP, and VNC protocols. When applying the proposed methodology, the port changes were made, so, when performing the scan again with Nmap, it was not determined which ports are exposed.
To determine the weaknesses of the IoT system, the Nessus tool was used. This tool allows to know the vulnerabilities caused by bad configurations, default installations, buffer overflows, lack of patches, design defects, operating system defects, application defects, open services, and default passwords found in the IoT system. When performing the vulnerability analysis without applying the proposed methodology, ten vulnerabilities were found with critical, high, and medium risk levels. Through a due process of hardening, the vulnerabilities found were mitigated, and, to verify that there are no risks and weaknesses, the vulnerability analysis was carried out again where no risk was found in the system.
When using default configurations, IoT systems have always been vulnerable to various types of attacks that seek to compromise the system and prevent its continuity. Some of these attacks aim to achieve full control of the IoT device. To find out how vulnerable IoT devices are, denial of service attacks, IpV6 flooding, dictionary, and man in the middle (MITM) were carried out. Without applying the proposed methodology, ten attacks were carried out, where eight were effective and two were ineffective. When applying the proposed methodology, no attack was effective.
In response to the research question that initiated this paper, this work identified the relationship between IoT and inadequate levels of system maturity. To evaluate the effectiveness of the proposed methodology, a case study was conducted. Without applying the hardening process, the maturity level is equal to 3 because the risk is equal to 7, the attack surface is equal to 7.3, and the vulnerabilities in CVSSv3 scale is equal to 7.5. Applying the hardening process, the maturity level is equal to 0 because the risk is equal to 4, the attack surface is equal to 1.42, and the vulnerabilities in CVSSv3 scale is equal to 0.
7. Conclusions
The qualitative analysis conducted on the scientific submissions of “IoT” AND “risk” AND “best practice” from 2016 to 2021 indicates that these papers were aligned to cover specific needs related to risk and threat analysis. However, the analysis reflects that there is a lack of research papers related to hardening and security validations. The contributions of the research analyzed allow the risks to be determined by means of standards proposed by international organizations, such as ISO, OWASP, and NIST.
IoT devices are growing exponentially, they register more risks and multiple threats, such as DOS, distributed denial of service (DDOS), MITM, buffer overflow, flooding attacks, malware, etc. Given this problem and the lack of IoT security validations, a solution was generated. The proposed solution is a cybersecurity model based on hardening for secure IoT implementations. This model consists of three phases. In the first phase, a threat modeling is performed to identify the risks and the communication protocols to be used. In the second phase, a vulnerability analysis is performed, and, in the third phase, the hardening process based on CIS controls is applied to reduce existing risks.
The fundamental axis of the proposed solution is hardening. The best hardening guides are proposed by CIS. The CIS controls guide was analyzed, where the most relevant controls are distributed to the three layers of the IoT architecture. If a deeper hardening is needed, CIS offers specific hardening guides oriented to cloud providers, desktop software, server software, mobile devices, network devices, and operating systems.
In future research, a mathematical analysis of the checklist of the attack surface will be performed, performing random tests to know the minimum parameters that the IoT system needs to have an adequate level of maturity.