Efficient Detection of Robot Kidnapping in Range Finder-Based Indoor Localization Using Quasi-Standardized 2D Dynamic Time Warping
Abstract
Featured Application
Abstract
1. Introduction
2. Related Works for Kidnapping Problem in Localization
- (1)
- The detector should be an online detector [4], such that it may reduce the possibility that the drone wanders around into a possible hazardous point in the map after kidnapping, because an immediate preventive action might be taken if the kidnapping information is obtained immediately after the kidnapping event.
- (2)
- The detector should be able to differentiate normal condition from kidnapping condition as well as possible, i.e., there is a wide gap in the detector’s output when the robot is in normal condition compared to when it is being kidnapped. This criterion should apply to a wide range of kidnapping points (time instances at which kidnapping events might occur). The wide time range application of a detector is important because a kidnapping may occur anytime during a robot’s exploration.
3. Quasi-Standardized 2-D Dynamic Time Warping
3.1. Dynamic Time Warping
3.2. Multidimensional Dynamic Time Warping
| Algorithm 1 MD-DTW algorithm |
| 1. MD-DTW Algorithm |
| 2. Normalize each dimension of and separately to zero mean and unit variance |
| 3. Construct distance matrix according to |
| 4. |
| 5. Find the minimum cost path using the regular DTW under the constraints stated in Remark 1 on this distance matrix |
3.3. Single and Two-Dimensional Dynamic Time Warping
| Algorithm 2 Performance test algorithm |
| 1. Performance Test Algorithm |
| 2. For all , do |
| 3. Let the robot run normally. At the robot is kidnapped to a certain place and after that it continues to run normally until |
| 4. See if the robot can detect that it has been kidnapped at by measuring |
| 5. Add to a vector of size [20 × 1] |
| 6. Repeat this 20 times and measure the performance index by averaging |
3.4. Variance Homogeneity Test
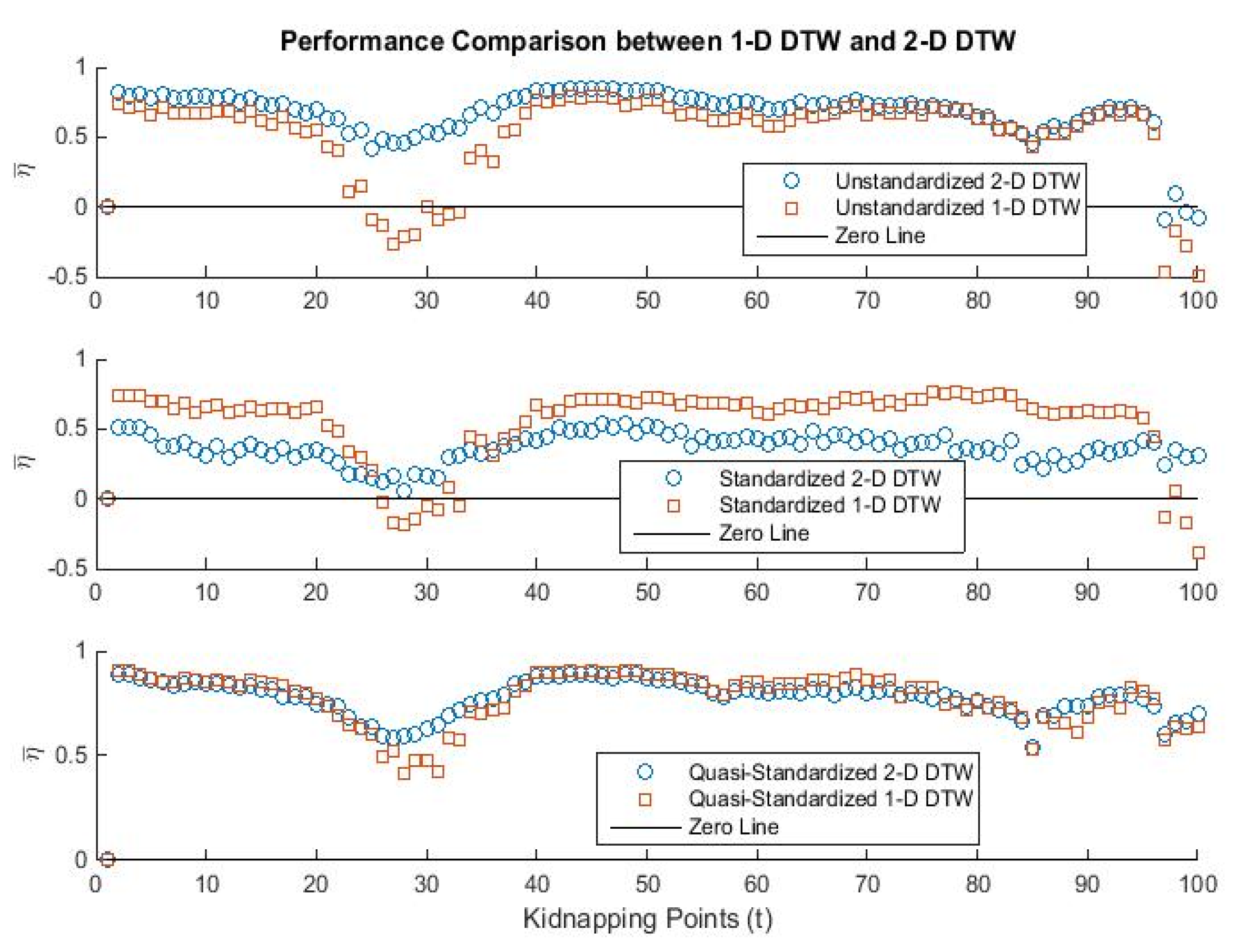
3.5. Quasi-Standardized Two-Dimensional Dynamic Time Warping
| Algorithm 3 QS-2DDTW algorithm |
| 1. QS-2DDTW Algorithm |
| 2. Decompose each dimension of and |
| 3. Perform variance homogeneity test (dedicated test to be employed depends on normality of the noise) on both dimensions |
| 4. if and and and |
| 5. |
| 6. |
| 7. End if |
| 8. Construct distance matrix according to |
| 9. Find the minimum cost path using the regular DTW under the constraints stated in Remark 1 on this distance matrix. |
4. Comparative Analysis with the Existing Online Detection Approaches
4.1. Maximum Current Weight
4.2. Measurement Entropy
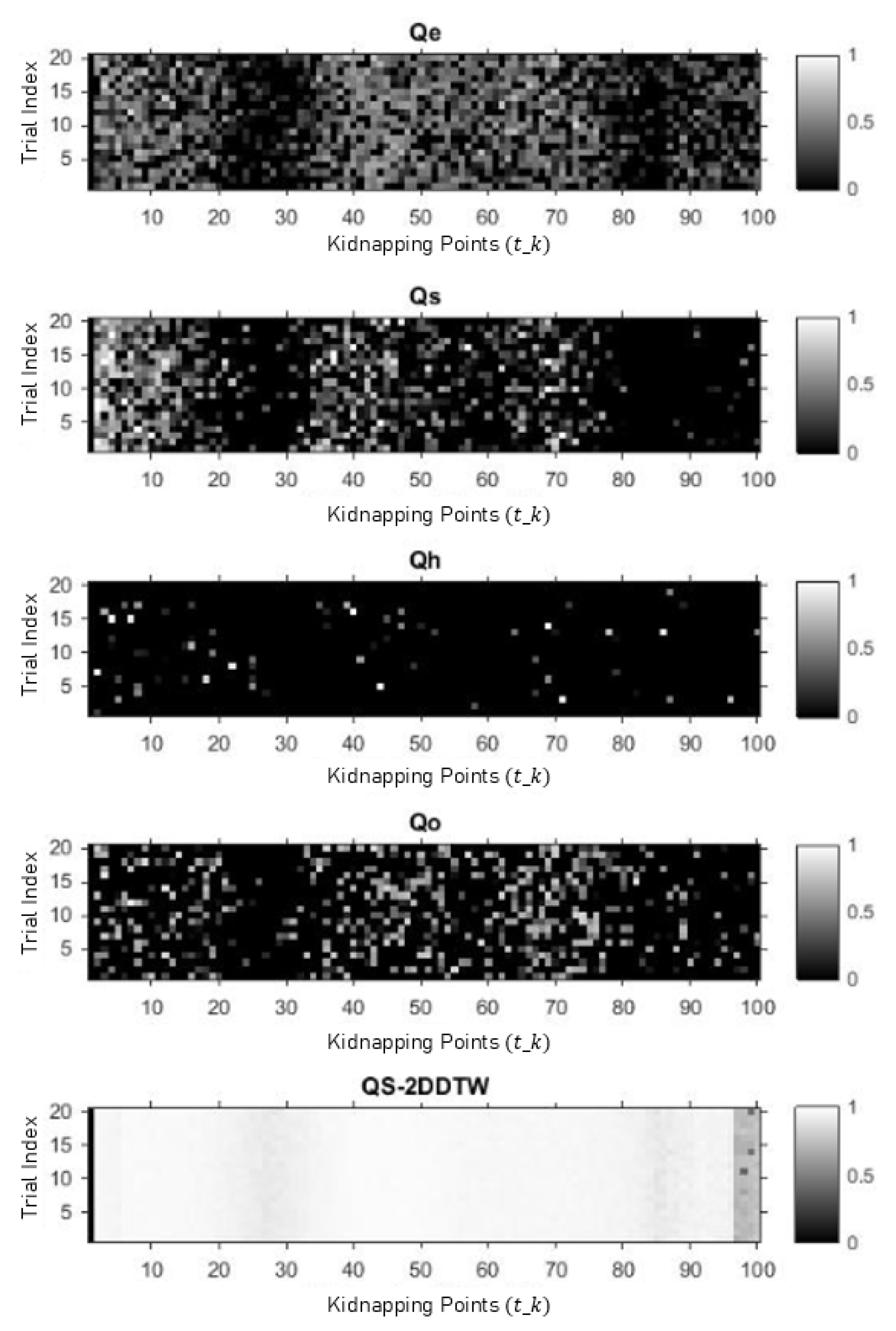
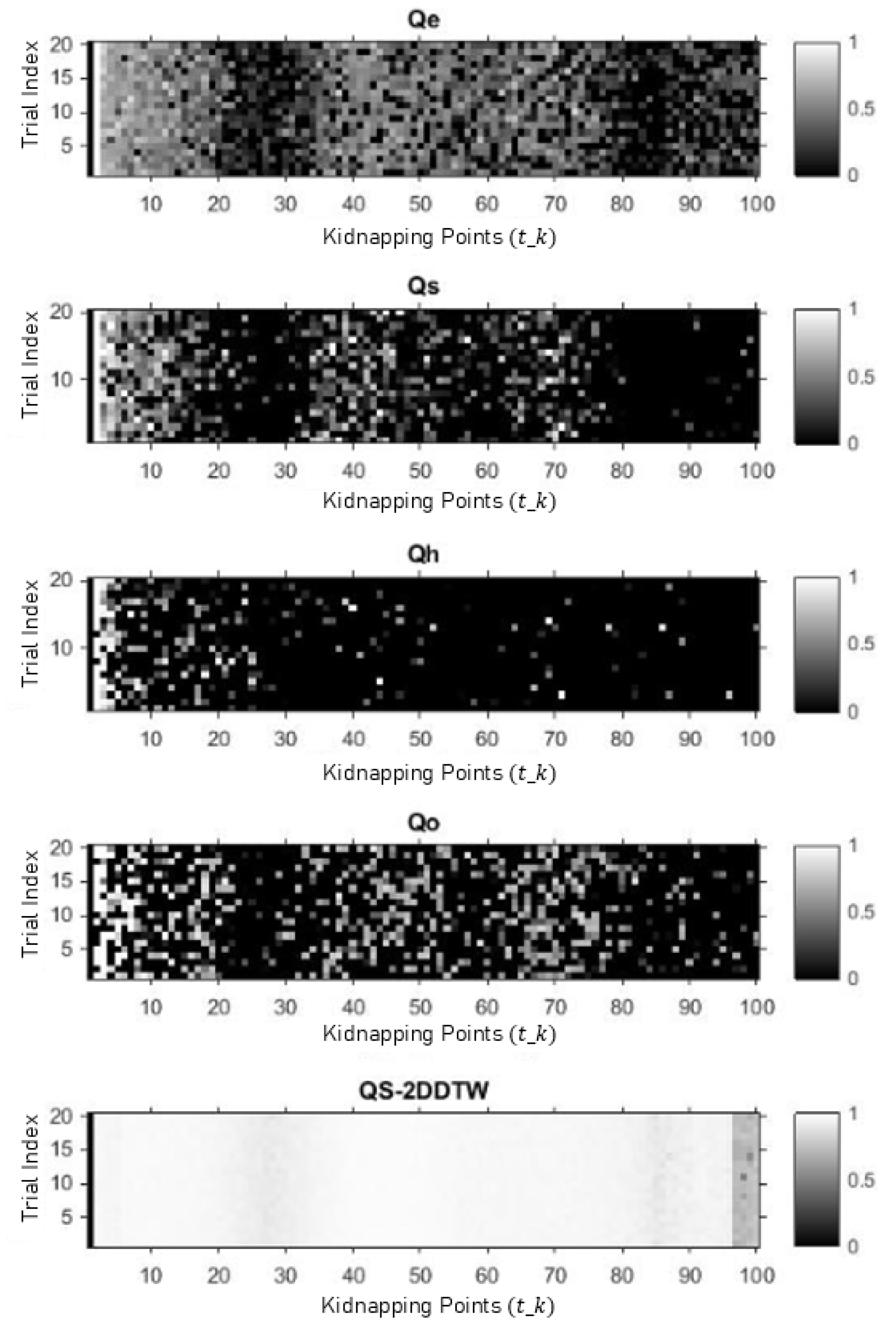
4.3. Metric-Based Detector
- Mean squared error between the two NDT-aligned point clouds, which is written aswhere n is the number of overlapping points, is a point in and the nearest-neighbor point of
- The likelihood that the transformed point cloud lies on the surface of NDT of that iswhere n is the number of points of in
- Standard deviation from the least known pose degree of freedom, calculated from maximum eigenvalue λ of NDT optimization function.where is degree of freedom of a robot’s pose.
- Mean squared error of point clouds transformed by and
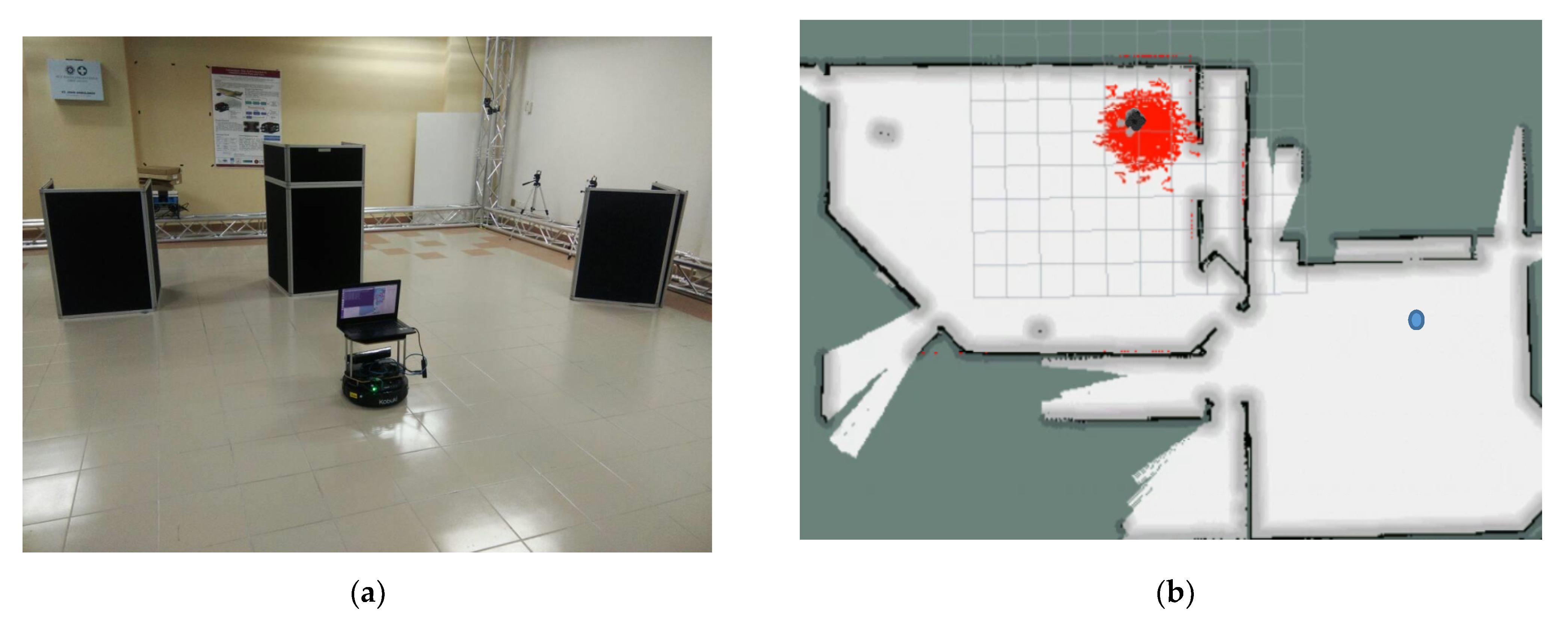
5. Results and Discussion
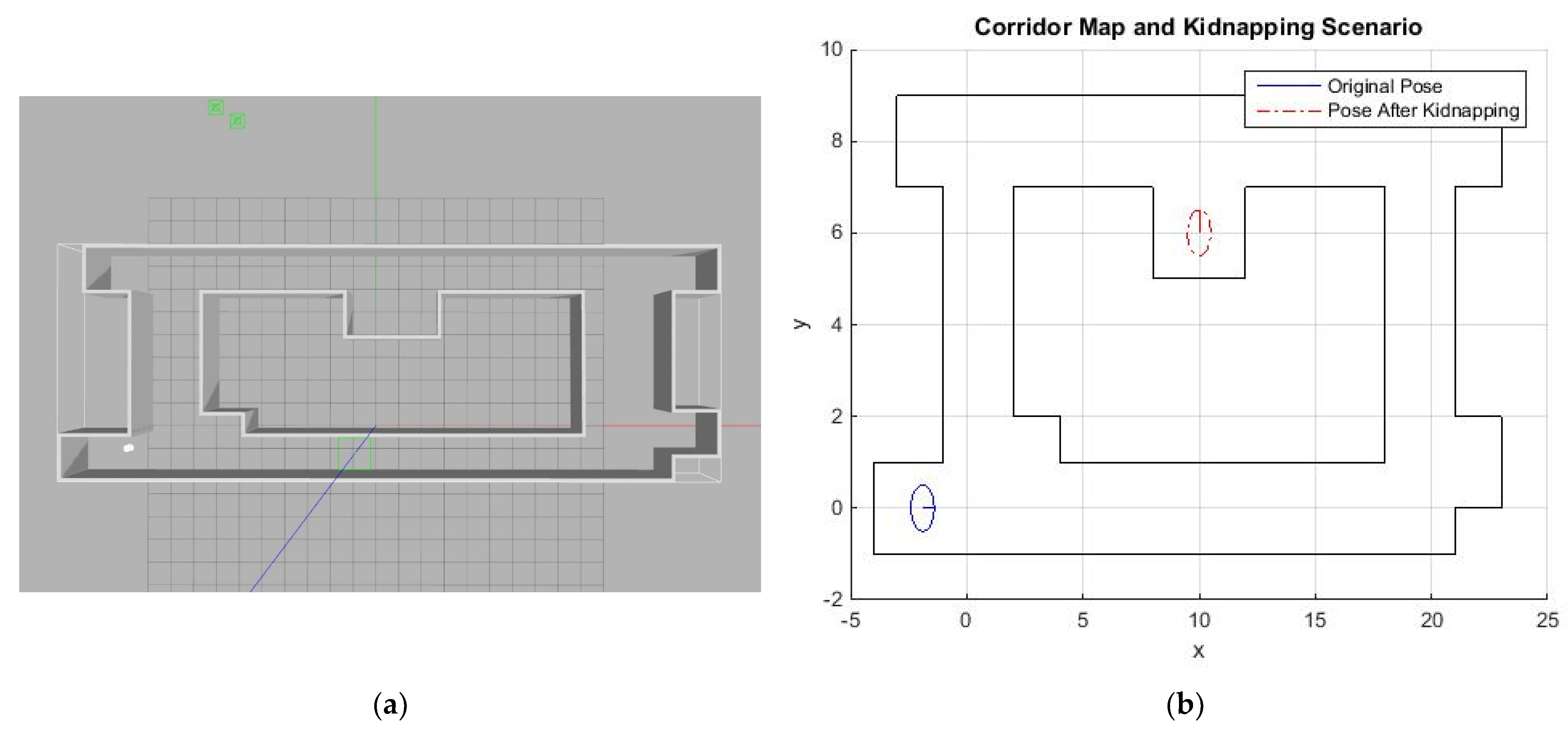
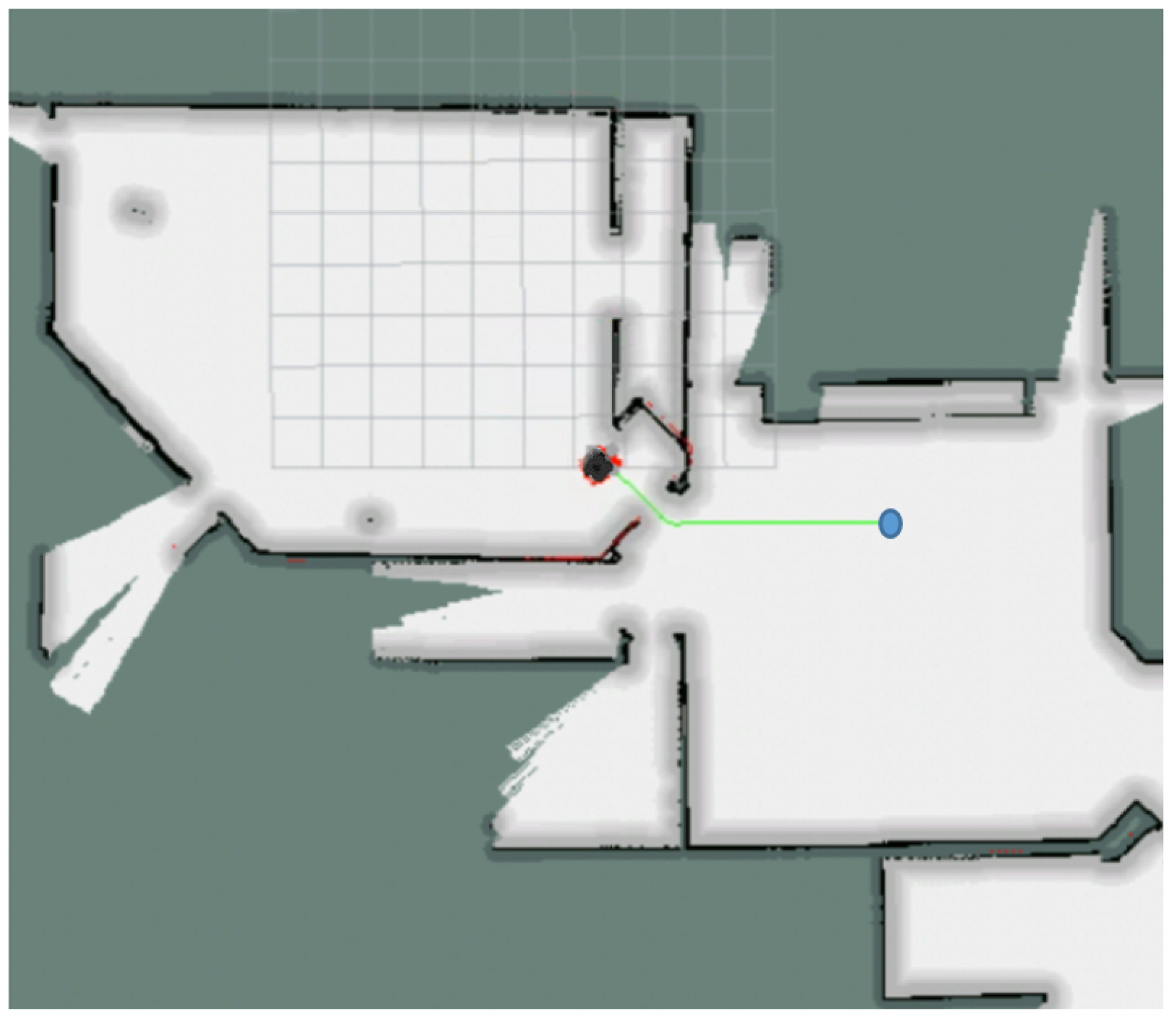
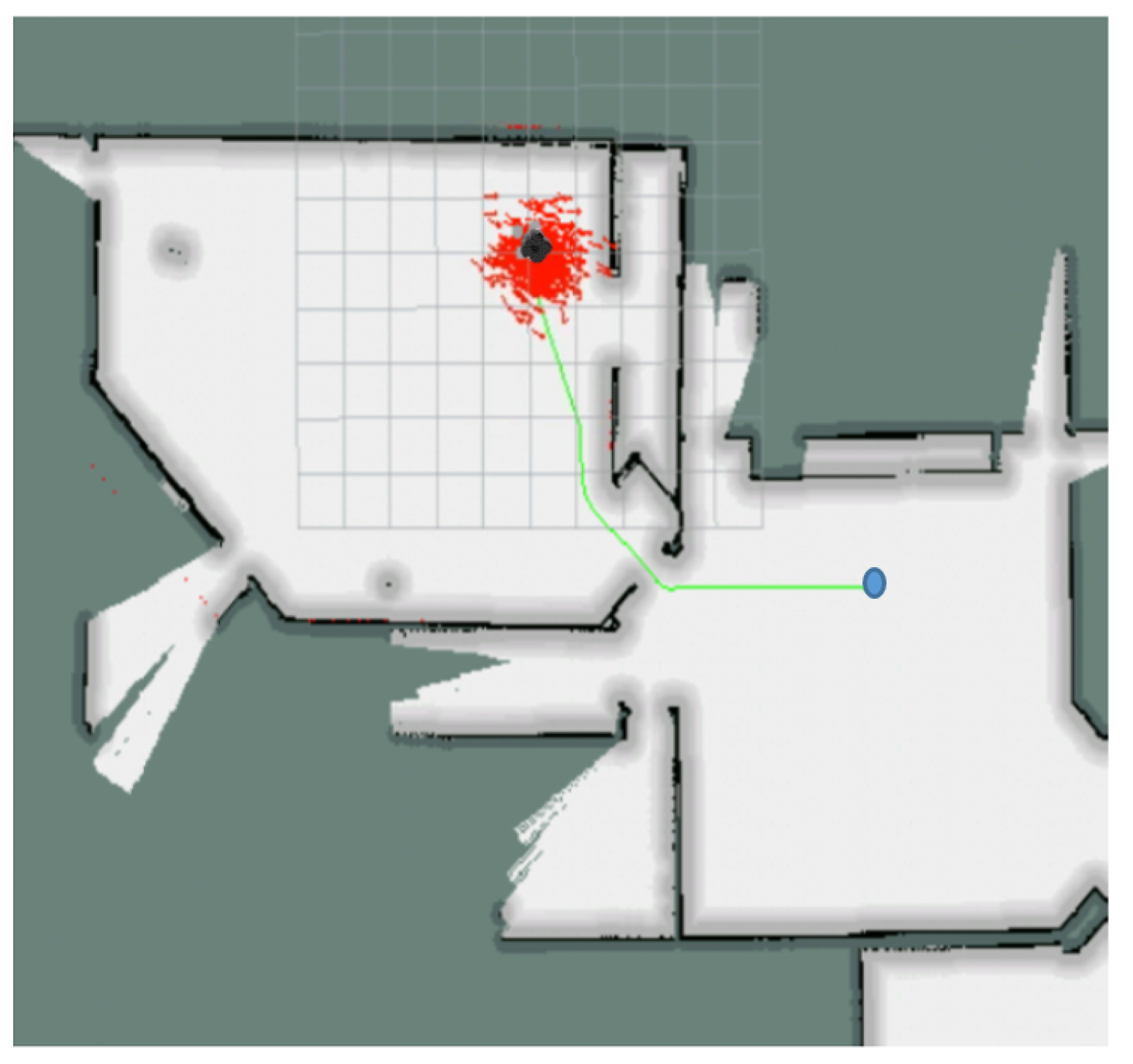
- Let the robot run normally. At the robot is kidnapped to a place indicated in Figure 5 and after that it continues to run normally until (at the robot can be relocalized or not, depending on the type of test)
- See if the robot can detect that it has been kidnapped at .
- Repeat this 100 times and measure the performance index.
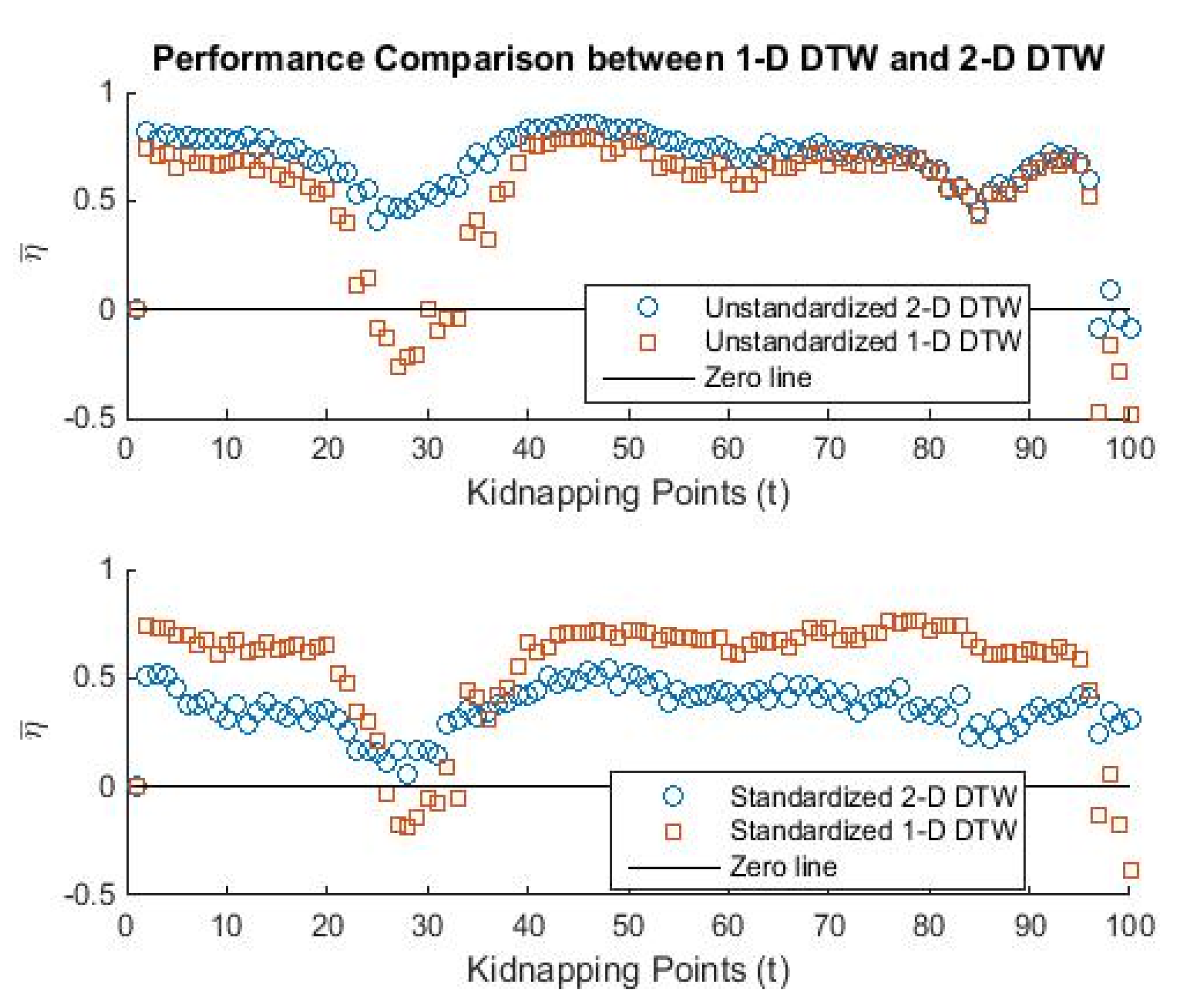
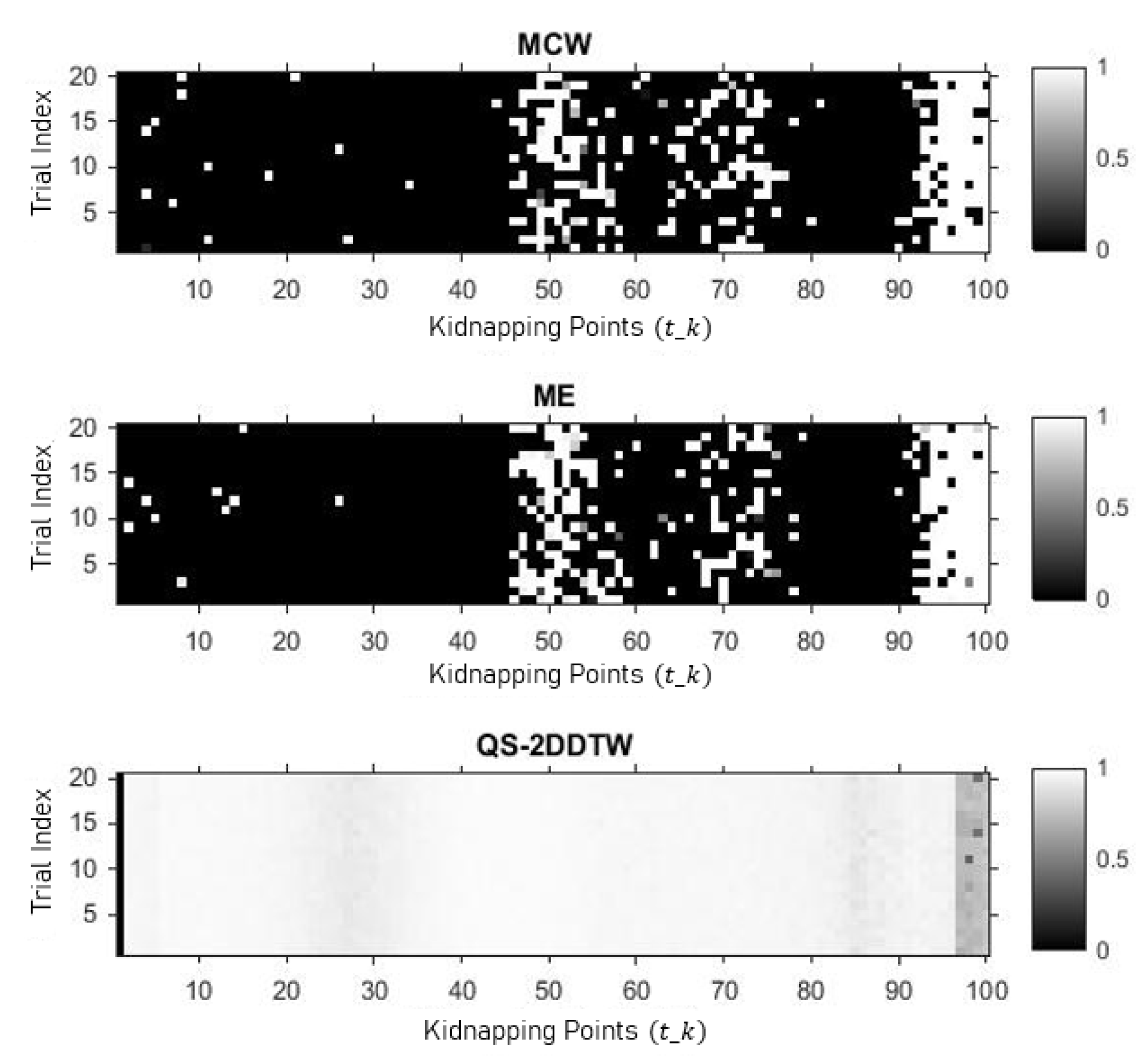
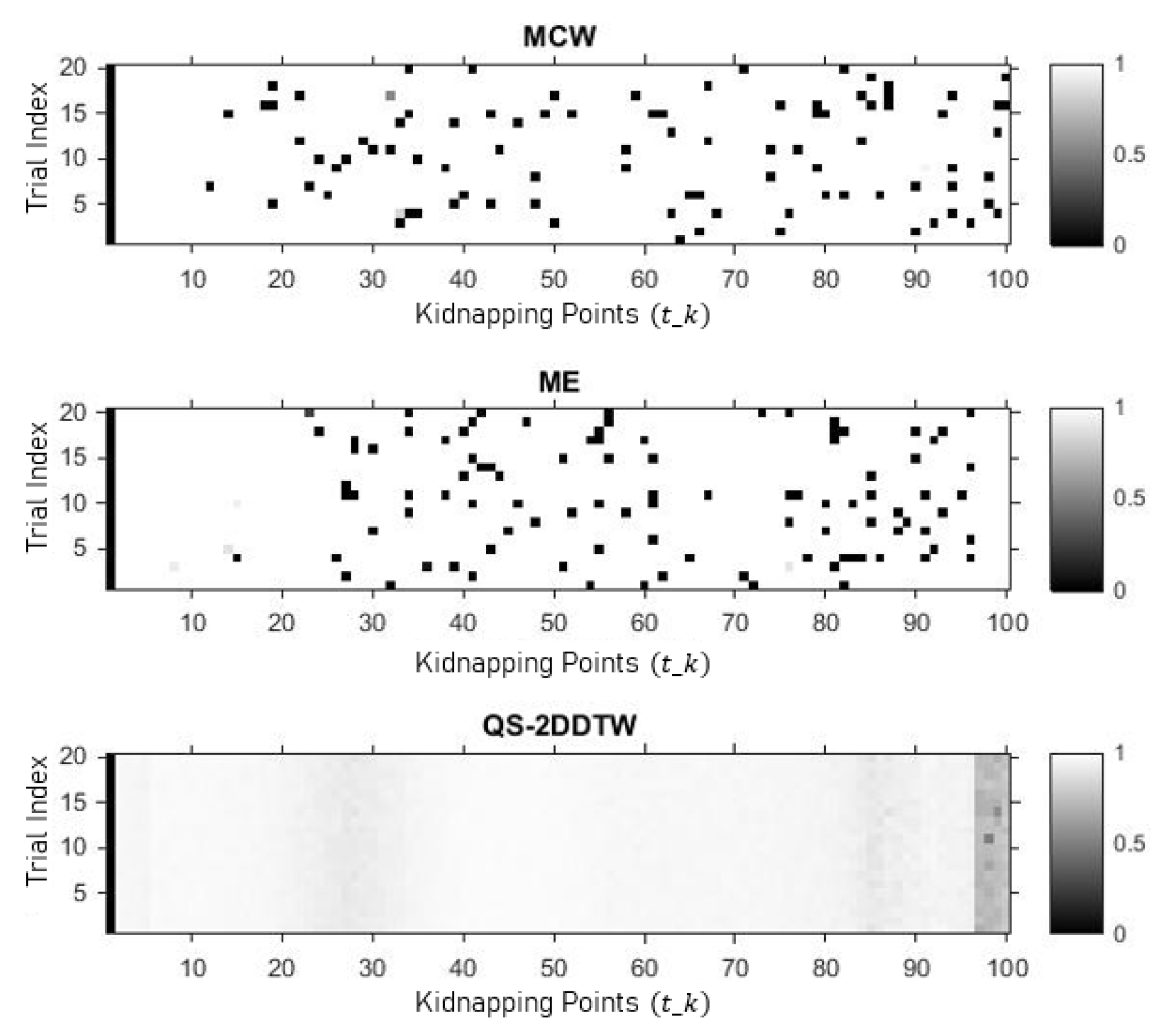
5.1. Performance Evaluation against MCW and ME
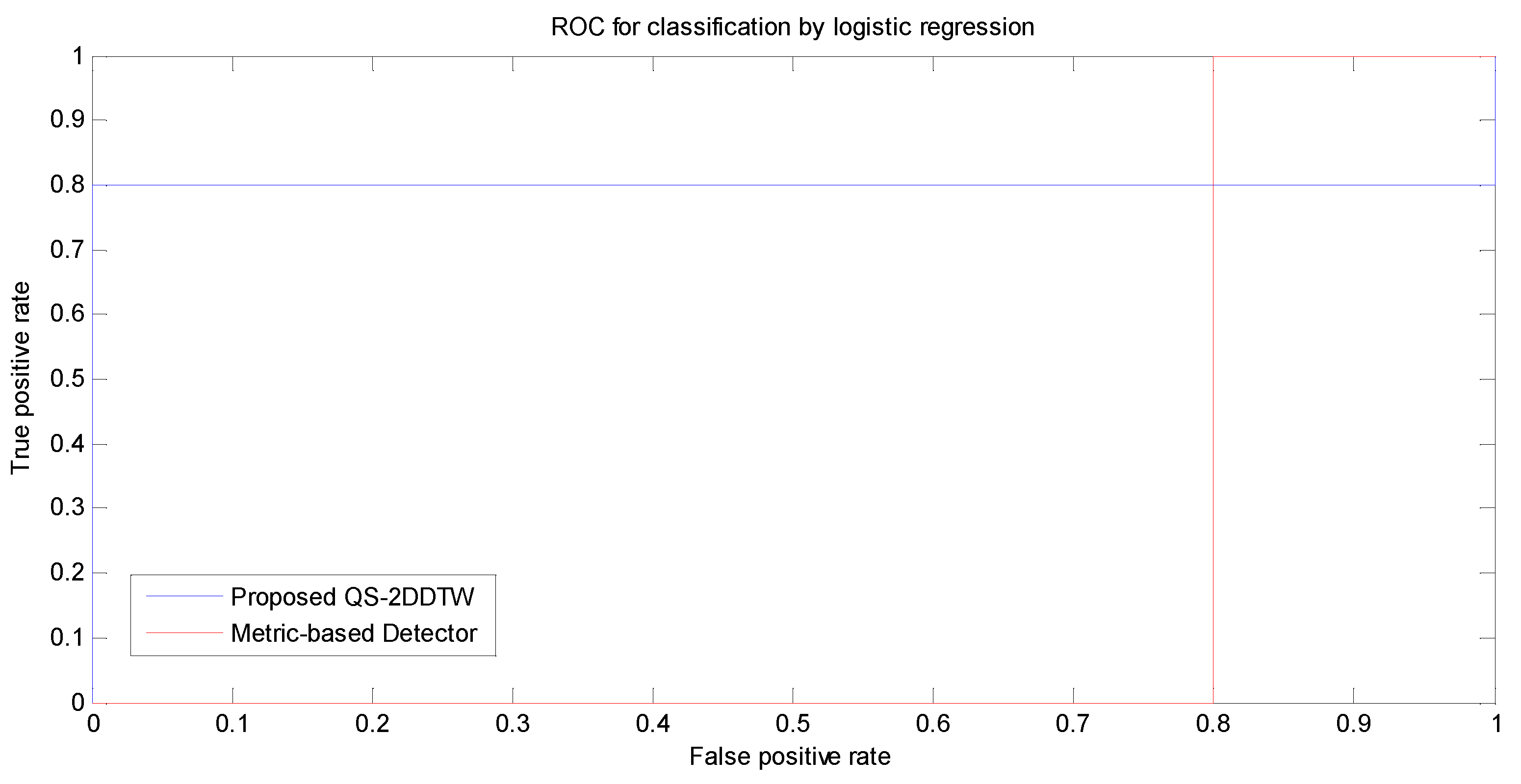
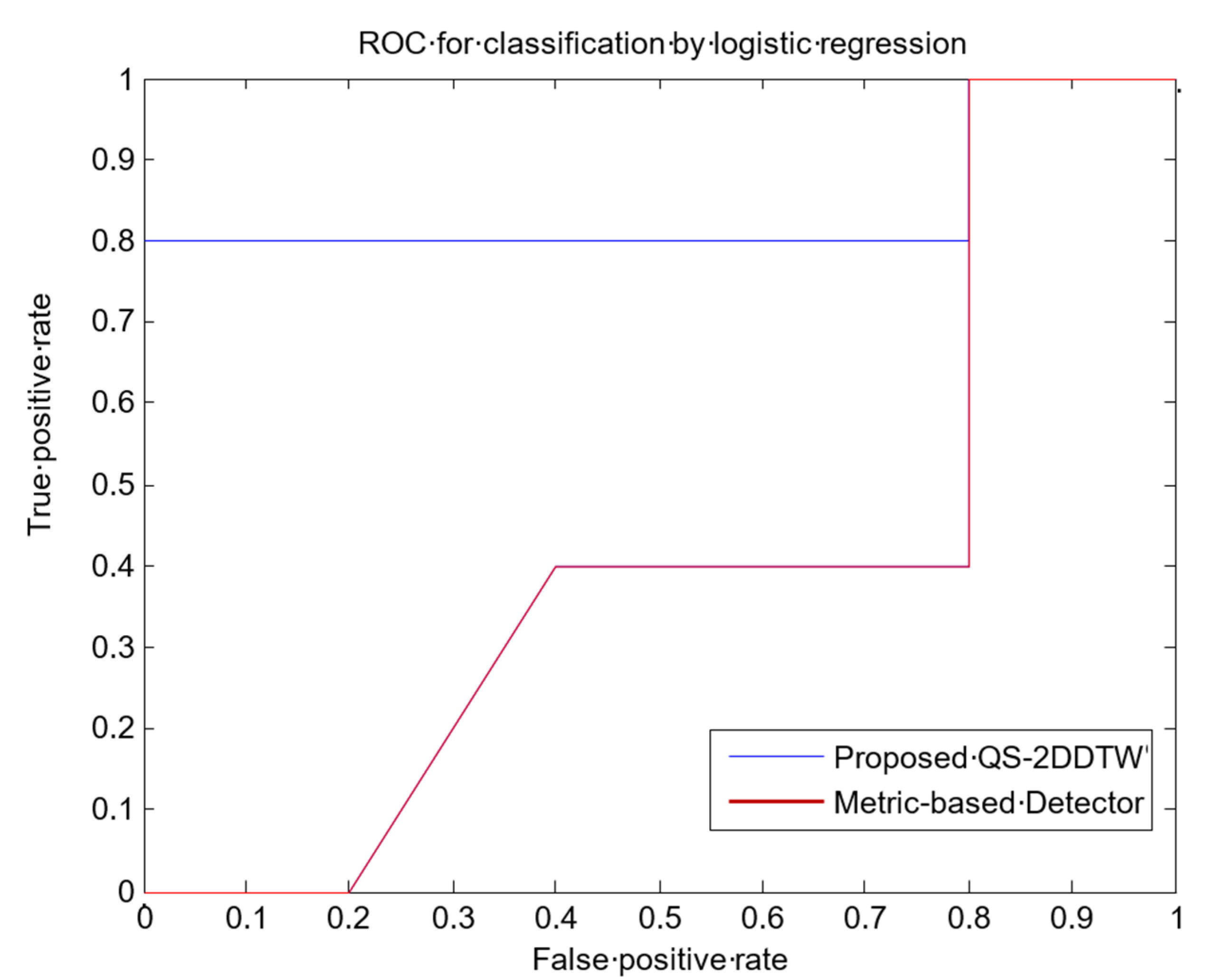
5.2. Performance Evaluation against Metric-Based Detector
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Thrun, S.; Fox, D.; Burgard, W. Probabilistic Robotics; MIT Press: Cambridge, MA, USA, 2005. [Google Scholar]
- Kwok, C.; Fox, D.; Meila, M. Adaptive real-time particle filters for robot localization. In Proceedings of the IEEE International Conference on Robotics and Automation, Taipei, Taiwan, 14–19 September 2003; pp. 2836–2841. [Google Scholar]
- Thrun, S.; Fox, D.; Burgard, D.W.; Dellaert, F. Robust Monte Carlo localization for mobile robots. Artif. Intell. 2001, 128, 99–141. [Google Scholar] [CrossRef]
- Campbell, D.; Whitty, M. Metric-based detection of robot kidnapping. In Proceedings of the European Conference on Mobile Robots, Barcelona, Spain, 25–27 September 2013. [Google Scholar]
- Yi, C.; Choi, B.-U. Detection and recovery for kidnapped-robot problem using measurement entropy. In Grid and Distributed Computing; Springer: Berlin/Heidelberg, Germany, 2011; Volume 261, pp. 293–299. [Google Scholar]
- Roumeliotis, S.I.; Bekey, G.A. Bayesian estimation and Kalman filtering: A unified framework for mobile robot localization. In Proceedings of the International Conference on Robotics and Automation, San Francisco, CA, USA, 24–28 April 2000. [Google Scholar]
- Andreasson, H.; Treptow, A.; Duckett, T. Localization for mobile robots using panoramic vision, local features and particle filter. In Proceedings of the International Conference on Robotics and Automation, Barcelona, Spain, 18–22 April 2005. [Google Scholar]
- Bukhori, Z.; Ismail, H.; Namerikawa, T. Detection strategy for kidnapped robot problem in landmark-based map Monte Carlo localization. In Proceedings of the International Symposium on Robotics and Intelligent Sensors, Langkawi, Malaysia, 18–20 October 2015. [Google Scholar]
- Zhang, L.; Zapata, R.; Lépinay, P. Self-adaptive Monte Carlo localization for mobile robots using range finders. Robotica 2012, 30, 229–244. [Google Scholar] [CrossRef]
- Biber, P.; Strasser, W. The normal distributions transform: A new approach to laser scan matching. In Proceedings of the IEEE/RSJ International Conference on Intelligent Robots and Systems, Tokyo, Japan, 3–7 November 2013. [Google Scholar]
- Chan, S.; Wu, P.; Fu, L. Robust 2D Indoor Localization Through Laser SLAM and Visual SLAM Fusion. In Proceedings of the 2018 IEEE International Conference on Systems, Man, and Cybernetics, Miyazaki, Japan, 7–10 October 2018; pp. 1263–1268. [Google Scholar]
- Hess, W.; Kohler, D.; Rapp, H.; Andor, D. Real-time loop closure in 2D LIDAR SLAM. In Proceedings of the 2016 IEEE International Conference on Robotics and Automation, Stockholm, Sweden, 16–21 May 2016; pp. 1271–1278. [Google Scholar]
- Zhang, Z.; Zhao, R.; Liu, E.; Yan, K.; Ma, Y. Scale Estimation and Correction of the Monocular Simultaneous Localization and Mapping (SLAM) Based on Fusion of 1D Laser Range Finder and Vision Data. Sensors 2018, 18, 1948. [Google Scholar] [CrossRef] [PubMed]
- Lu, F.; Milios, E. Robot pose estimation in unknown environments by matching 2D range scans. J. Intell. Robot. Syst. 1997, 18, 249–275. [Google Scholar] [CrossRef]
- Kulkarni, K.; Evangelidis, G.; Cech, J.; Horaud, R. Continuous action recognition based on sequence alignment. Int. J. Comput. Vis. 2015, 112, 90–114. [Google Scholar] [CrossRef]
- Sakoe, H.; Chiba, S. Dynamic programming algorithm optimization for spoken word recognition. IEEE Trans. Acoust. Speech Signal Process. 1978, 26, 43–49. [Google Scholar] [CrossRef]
- Rabiner, L.; Juang, B.H. Fundamentals of Speech Recognition; Prentice-Hall International: Upper Saddle River, NJ, USA, 1993. [Google Scholar]
- Hsu, E.; Pulli, K.; Popović, J. Style translation for human motion. ACM Trans. Graph. 2005, 24, 1082–1089. [Google Scholar] [CrossRef]
- Holt, G.A.T.; Reinders, M.J.T.; Hendriks, E.A. Multi-dimensional dynamic time warping for gesture recognition. In Proceedings of the 13th Annual Conference of the Advanced School for Computing and Imaging, Holland, The Netherlands, 13–15 June 2007. [Google Scholar]
- Chen, Y.; Keogh, E.; Hu, B.; Begum, N.; Bagnall, A.; Mueen, A.; Batista, G. The UCR Time Series Classification Archive. Available online: http://www.cs.ucr.edu/~eamonn/time_series_data/ (accessed on 15 July 2015).
- Sankoff, D.; Kruskal, J. The symmetric time-warping problem: From continuous to discrete. In Time Warps, String Edits, and Macromolecules: The Theory and Practice of Sequence Comparison; Addison Wesley Publishing Company: Boston, MA, USA, 1983; pp. 125–161. [Google Scholar]
- Keogh, E.; Ratanamahatana, C.A. Exact indexing of dynamic time warping. Knowl. Inf. Syst. 2005, 7, 358–386. [Google Scholar] [CrossRef]
- Brown, M.B.; Forsythe, A.B. Robust tests for equality of variances. J. Am. Stat. Assoc. 1974, 69, 364–367. [Google Scholar] [CrossRef]
- O’Brien, R.G. Robust techniques for testing heterogeneity of variance effects in factorial designs. Psychometrika 1978, 43, 327–342. [Google Scholar] [CrossRef]
- Bartlett, M.S. Properties of sufficiency and statistical tests. Proceedings of the Royal Society of London. Ser. A Math. Phys. Sci. 1937, 160, 268–282. [Google Scholar]
- Levene, H. Robust Tests for Equality of Variances. In Contributions to Probability and Statistics: Essays in Honor of Harold Hotelling; Stanford University Press: Palo Alto, CA, USA, 1960; pp. 278–292. [Google Scholar]
- Thrun, S.; Fox, D.; Burgard, W. Monte Carlo localization with mixture proposal distribution. In Proceedings of the AAAI/IAAI, Austin, TX, USA, 30 July 2000. [Google Scholar]
- Magnusson, M.; Lilienthal, A.; Duckett, T. Scan registration for autonomous mining vehicles using 3D-NDT. J. Field Robot. 2007, 24, 803–827. [Google Scholar] [CrossRef]
- Magnusson, M. The Three-Dimensional Normal-Distribution Transform—An Efficient Representation for Registration, Surface Analysis, and Loop Detection. Ph.D. Thesis, Orebro University, Orebro, Sweden, 2009. [Google Scholar]
- Mishra, R.; Javed, A. ROS based service robot platform. In Proceedings of the 2018 4th International Conference on Control, Automation and Robotics (ICCAR), Auckland, New Zealand, 20–23 April 2018; pp. 55–59. [Google Scholar]
- Ladosz, P.; Coombes, M.; Smith, J.; Hutchinson, M. A Generic ROS Based System for Rapid Development and Testing of Algorithms for Autonomous Ground and Aerial Vehicles. In Robot Operating System (ROS), Studies in Computational Intelligence; Koubaa, A., Ed.; Springer: Berlin, Germany, 2018; Volume 778. [Google Scholar]
- Linder, T.; Arras, K.O. People Detection, Tracking and Visualization Using ROS on a Mobile Service Robot. In Robot Operating System (ROS), Studies in Computational Intelligence; Koubaa, A., Ed.; Springer: Berlin, Germany, 2016; Volume 625. [Google Scholar]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ismail, Z.H.; Bukhori, I. Efficient Detection of Robot Kidnapping in Range Finder-Based Indoor Localization Using Quasi-Standardized 2D Dynamic Time Warping. Appl. Sci. 2021, 11, 1580. https://doi.org/10.3390/app11041580
Ismail ZH, Bukhori I. Efficient Detection of Robot Kidnapping in Range Finder-Based Indoor Localization Using Quasi-Standardized 2D Dynamic Time Warping. Applied Sciences. 2021; 11(4):1580. https://doi.org/10.3390/app11041580
Chicago/Turabian StyleIsmail, Zool H., and Iksan Bukhori. 2021. "Efficient Detection of Robot Kidnapping in Range Finder-Based Indoor Localization Using Quasi-Standardized 2D Dynamic Time Warping" Applied Sciences 11, no. 4: 1580. https://doi.org/10.3390/app11041580
APA StyleIsmail, Z. H., & Bukhori, I. (2021). Efficient Detection of Robot Kidnapping in Range Finder-Based Indoor Localization Using Quasi-Standardized 2D Dynamic Time Warping. Applied Sciences, 11(4), 1580. https://doi.org/10.3390/app11041580






