Delegation-Based Personal Data Processing Request Notarization Framework for GDPR Based on Private Blockchain
Abstract
:1. Introduction
2. Background and Related Work
2.1. GDPR
- Data subject (DS): owner of the produced personal data who possesses the right to process his/her personal data; decides on the entrustment of the processing of own personal data to the service provider; requests to view, correct, delete, suspend processing, or transmit personal data stored by the service provider and confirm the result; and can ask the supervisory authority to audit service providers for GDPR compliance.
- Service provider (SP): organization that provides various services by collecting and managing personal information; must comply with the GDPR regulations and prepare legal evidence for all actions involving collecting and managing personal data; and present the evidence upon request from DS and supervisory authorities.
- Data controller (DC): the person who is in charge of personal data management belonging to the SP; determines the purpose and method of the processing of personal data; and is responsible for managing and proving that the data for the DS is processed in a lawful, fair, and transparent manner.
- Supervisory authority (SA): the organization that conducts GDPR compliance audits; has the legal authority to regularly oversee and investigate the compliance of SPs with GDPR regulations; is an independent public authority responsible for monitoring the application of regulations to protect the basic rights and freedoms of natural persons regarding the processing of personal data and to promote the free flow of personal data within the Union.
- Articles 12–23: The DS may request a provision of information on personal data collected in relation to oneself, correction of inaccurate personal data about oneself without delay, deletion of personal data related to oneself without delay, and transmission of personal data provided by oneself to other DCs. Moreover, the DC shall not refuse to act in response to the DS’s request for the exercise of these rights.
- Recital 59: Modalities should be provided for facilitating the exercise of DS’s rights under this Regulation, including mechanisms to request and, if applicable, obtain, free of charge, in particular, access to and rectification or erasure of personal data and the exercise of the right to object. In addition, the DC should provide the means for requests to be made electronically, particularly where personal data are processed via electronic means.
- Recital 66: To strengthen the right to be forgotten in the online environment, the right to erasure should also be extended in such a manner that the DC who has made the personal data public must be obliged to inform the DCs that are processing such personal data to erase any links to, or copies, or replications of those personal data. Consequently, the DC must incorporate reasonable steps, considering the available technology and the means available to DC, including technical measures, to inform the DCs that are processing the personal data of the DS’s request.
2.2. Blockchain
- Decentralization: BC network transactions can be performed between two peers (P2P) without authentication from a central authority.
- Persistence: As each transaction spreading through the network must be verified and recorded in blocks distributed throughout the network, tampering is almost impossible.
- Anonymity: Owing to the absence of a central system to store the personal data of the user, each user can communicate with the BC network using the created address, thus minimizing identity exposure.
- Auditability: In the BC, each transaction can repeatedly trace the previous transaction. This improves the traceability and transparency of the stored data.
2.3. Related Works of Blockchain-Based GDPR
3. Delegation-Based Personal Data Processing Request Notarization Framework
- Confidentiality: Network participants must be able to trust the transaction data that are evidence related to the processing of personal data.
- Integrity: It must be guaranteed that the created and managed transaction data are not illegally forged or altered.
- Non-repudiation: Denying related facts based on the subject of transaction data creation and management is not possible.
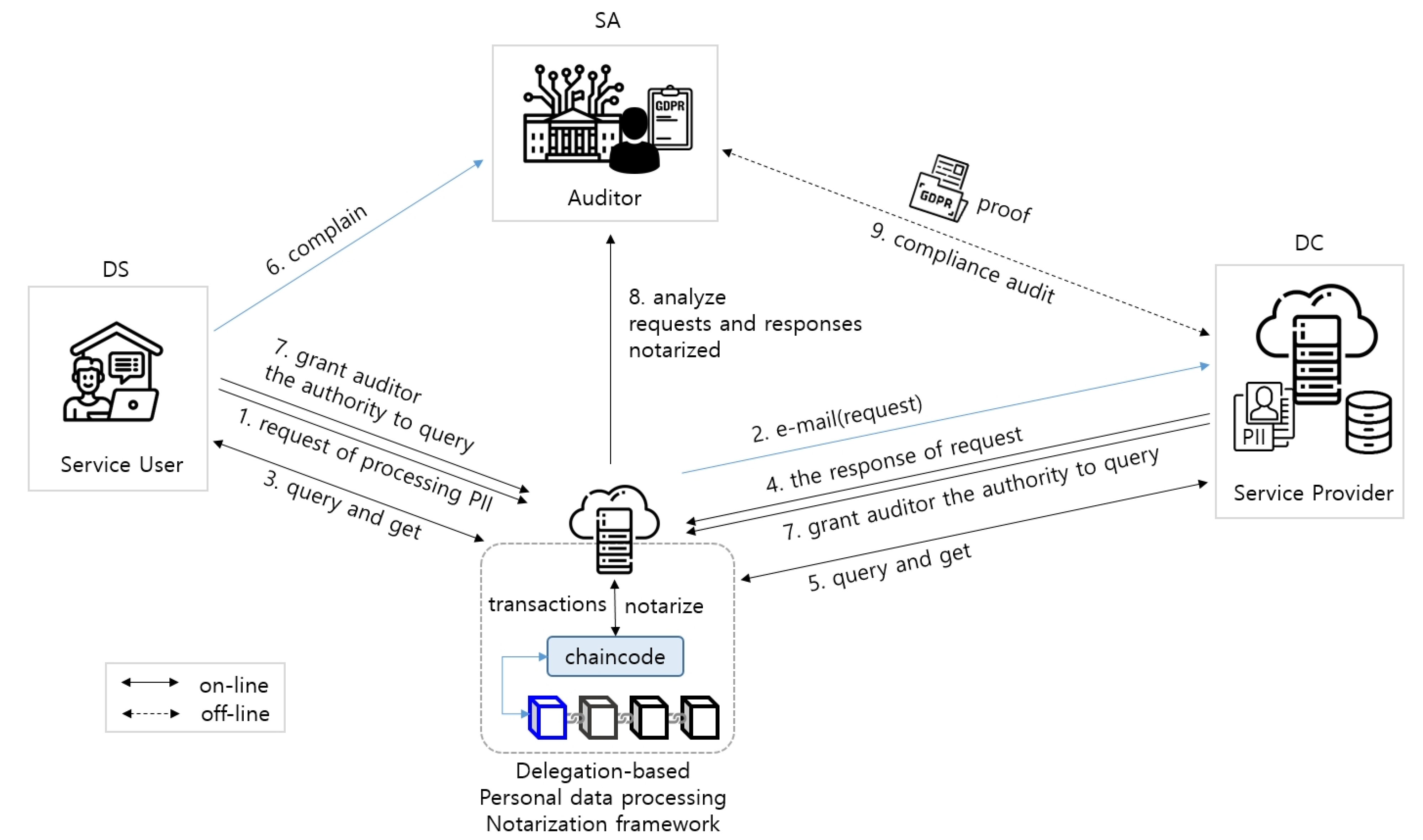
3.1. GDPR Compliance Audit Scenario of Personal Data Processing Request
- The DS must consent to the processing of personal data to utilize the services of an SP and subscribe to services on the system. The SP is the DC of personal data.
- SPs collect and manage the personal data of DSs adhering to GDPR regulations.
- In accordance with GDPR regulations, the DS requests the SP to view, correct, delete, stop, and transmit his/her personal data at any time if needed.
- The SP accepts the request and performs all processes without any delay. After executing the process, the results of the processing are notified to the DS. Particularly, if the DS uses their request on an electronic method, it responds to the request through an electronic method. The SP must record the processing logs and establish legal evidence data to prove GDPR compliance.
- The SA manages SP to ensure compliance with GDPR regulations and performs a GDPR compliance audit by analyzing evidence data presented by the SP to certify them.
- DSs may request a GDPR compliance audit of the SP from the SA in the processing of their personal data based on a specific situation.
- SA investigates the operation status of SPs considering the requested GDPR compliance audit and takes appropriate measures based on results obtained from the investigation.
3.2. Challenges and Requirements of the GDPR Compliance Audit for Personal Data Processing Request
- Sealing of data: The sealing of data ensures data integrity and not secrecy. It must produce the same value when the data are sealed and when they are verified. A third party cannot obtain the data, modify it, and produce a new value that is acceptable when the data and value are verified.
- Accessible to all: The notary must be accessible to all who desire to seal data.
- Trusted or certifiable: The notary must either be trusted or certifiable, as must its cryptographic keys.
- Highly trusted communications: If the notary exists in a different domain, then the communication between the notary and user must be highly secure. The client must possess the means of ensuring that the data he/she has notarized are the data that were requested to be notarized.
- Authentication: It is important that the user that starts a transaction is the only user to participate in that transaction or delegate work to other users. Consequently, the user that starts a transaction can be attributed with that transaction when it is committed.
3.3. Design Goals
- Delegation for GDPR: DS must have the ability to delegate requests for the processing of personal data to the notarization system and deliver them to DC in an electronic manner. Data creators who want notarization should be easily accessible anytime, anywhere.
- Audit trail for GDPR: Requests and responses must be recorded in the form of ‘who, when, to whom, and what’ for GDPR compliance, and they must preserve integrity. Records must be stored in a manner such that they can be viewed by an auditor authorized by the DS and DC.
- Notarization of request for the processing of personal data: Verification of the personal data processing request and corresponding data through a number of trusted notaries should be enabled, and furthermore, the ability to notarize the integrity of the stored and retrieved data is important. The authenticity and key management of data creators and notaries should ensure that the reliability of the data cannot be denied.
- Managing permission for audit: Only the author or recipient of the data should have access to the relevant data. DSs and DCs must have the ability to authorize auditors to view data for GDPR compliance audits related to requests for the processing of personal data. However, searching for data other than the data of the approver that the auditor has authorized the inquiry authority to view should be disabled.
- Distribution of trust: The authentication of users using the notarization system and the authority that manages the ledger must be performed and mutually verified by certain trusted institutions across countries rather than one.
- Minimum collection: Personal data other than data related to requests and responses should not be collected, and GDPR compliance audits should be possible for requests from DSs without sharing them with DCs or not being provided them from DCs.
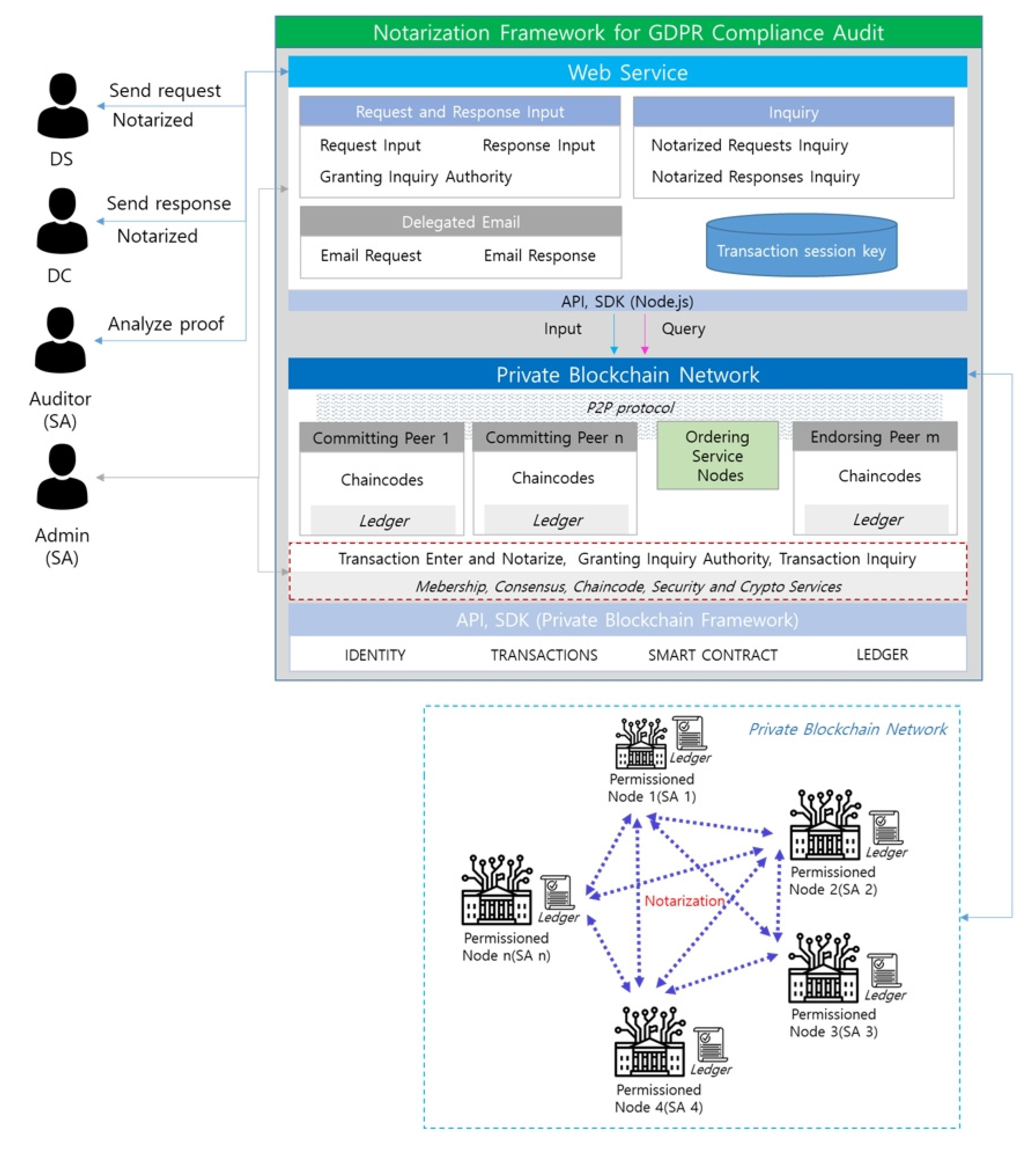
3.4. Notarization Framework
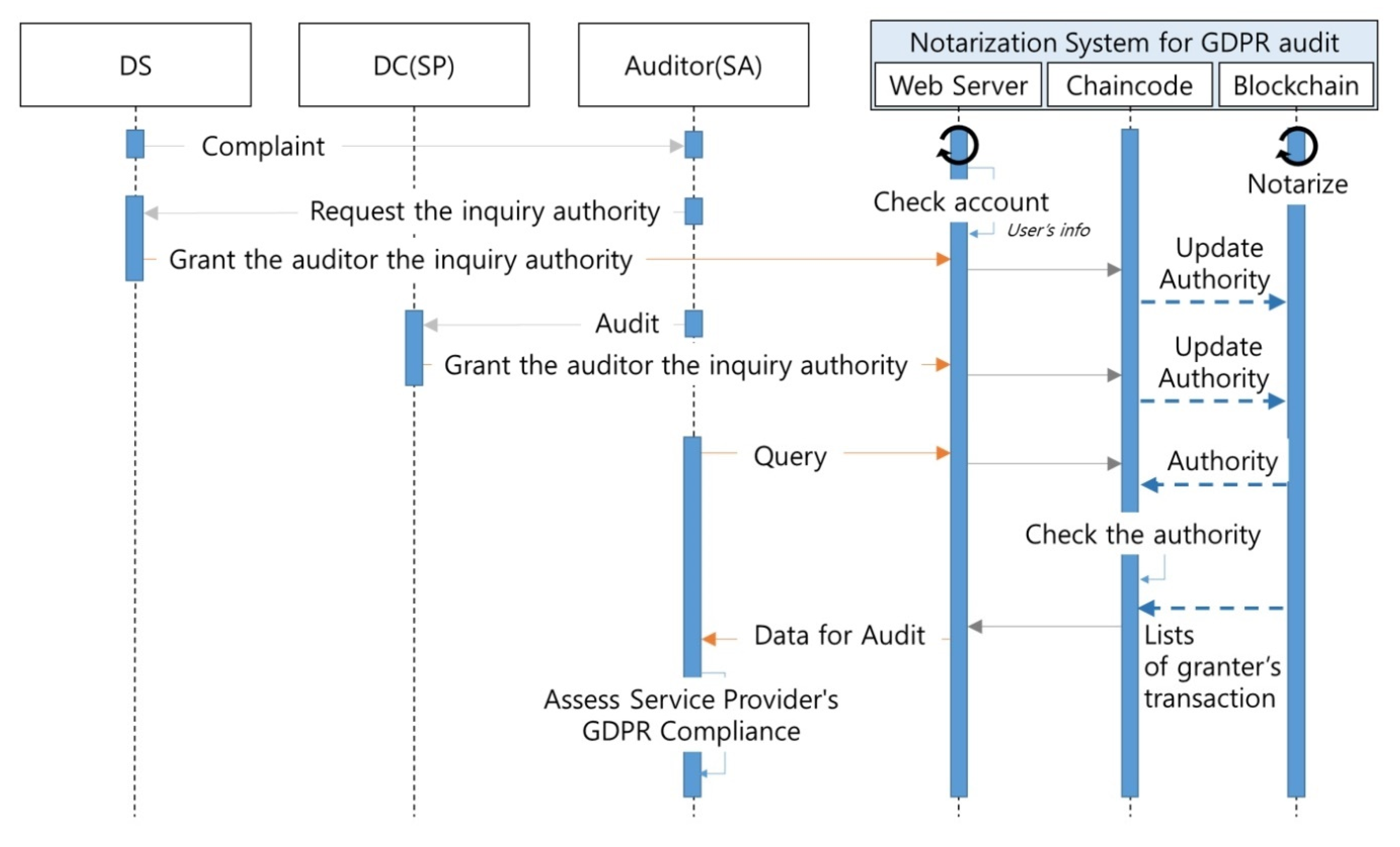
- DS (Service user): To register request information for viewing, correction, deletion, suspension of processing, and transmission of personal information stored by SPs in the system. To query the request and the response records of the DC in the system. To complain to the SA if the DC fails to satisfactorily process the personal data of the DS against the interests and rights of the DS. To grant SAs the authority to query the records of requests for the processing of personal data through the system.
- DC (SP): To respond to requests by the DS for the processing of personal data and register responses in the system. To grant SAs the authority to query response records to requests for the processing of personal data through the system.
- Auditor (SA): With the authority authorized by the DS, to query the system regarding the records of the requests and response for the processing of personal data. To conduct a GDPR compliance audit of the DC to determine compliance. To ensure that the DC adheres to the GDPR regulations and is authorized by the DC to inquire the data of the DC when performing an audit. To check the records of the response of the DC to the requests made by the DS stored in the system to determine the regulations are being adhered to.
- Notarization system: To provide services to the web through smart contracts, manage the BC ledger, and manage the authority of network participants. To store the data of the request in the BC when the DS registers a request for the processing of personal data in the system.
3.5. Notarized Data Structure
- Request: A structure requests for the processing of personal data sent by the DS to the DC.
- Response: A structure for a response to a request sent by the DC to the DS.
- Authorization: A structure of data access rights granted by the DS or DC.
- Parameters of data structures for transactions are as follows:
- Parameters of Request: The number of requests, DS’s ID, SP’s URL, SP e-mail, processing type, the content of the request and timestamp.
- Parameters of Response: The number of responses, the number of requests, DS’s ID, data SP’s URL, subject’s e-mail, processing type, content of request, content of response, and timestamp.
- Parameters of Authorization: The number of grants, grantor type, auditor’s ID, SP’s URL, grantor’s ID, and authority expiration date.
3.6. Identity Management
3.7. Personal Data Protection
transaction ID = DS’s ID + timestamp
IF transaction type equal ‘response’ THEN
transaction ID = SP’s URL + timestamp
| Algorithm 1. Make Session Key |
| INPUT: DS’s ID, SP’s URL, transaction ID, transaction type, private data, timestamp OUTPUT: session key 1 IF transaction type equal ‘request’ THEN 2 SET session key to result of SUM result of COMPUTE hash encode with transaction ID and result of COMPUTE hash encode with private data 3 SET data array with transaction ID, session key, DS’s ID, SP’s URL, and timestamp 4 ADD data array made key with transaction ID into application database 5 ENDIF 6 RETURN session key |
| Algorithm 2. Inquiry Session Key |
| INPUT: user ID, transaction ID OUTPUT: session key 1 SET user’s type to the result of READ user type of user ID 2 IF user’s type is equal to ‘DS’ THEN 3 SET session key to the result of READ session key from application database where user ID equal DS’s ID in DB and the transaction ID equals the transaction ID in DB 4 ENDIF 5 IF user’s type equals ‘DC’ THEN 6 SET SP’s URL to the result of READ SP’s URL from the user information in the DC’s session 7 SET session key to the result of READ session key from the application database where the SP’s URL equals the SP’s url in DB and the transaction ID equals the transaction ID in DB 8 ELSE 9 SET session key to null 10 ENDIF 11 RETURN session key |
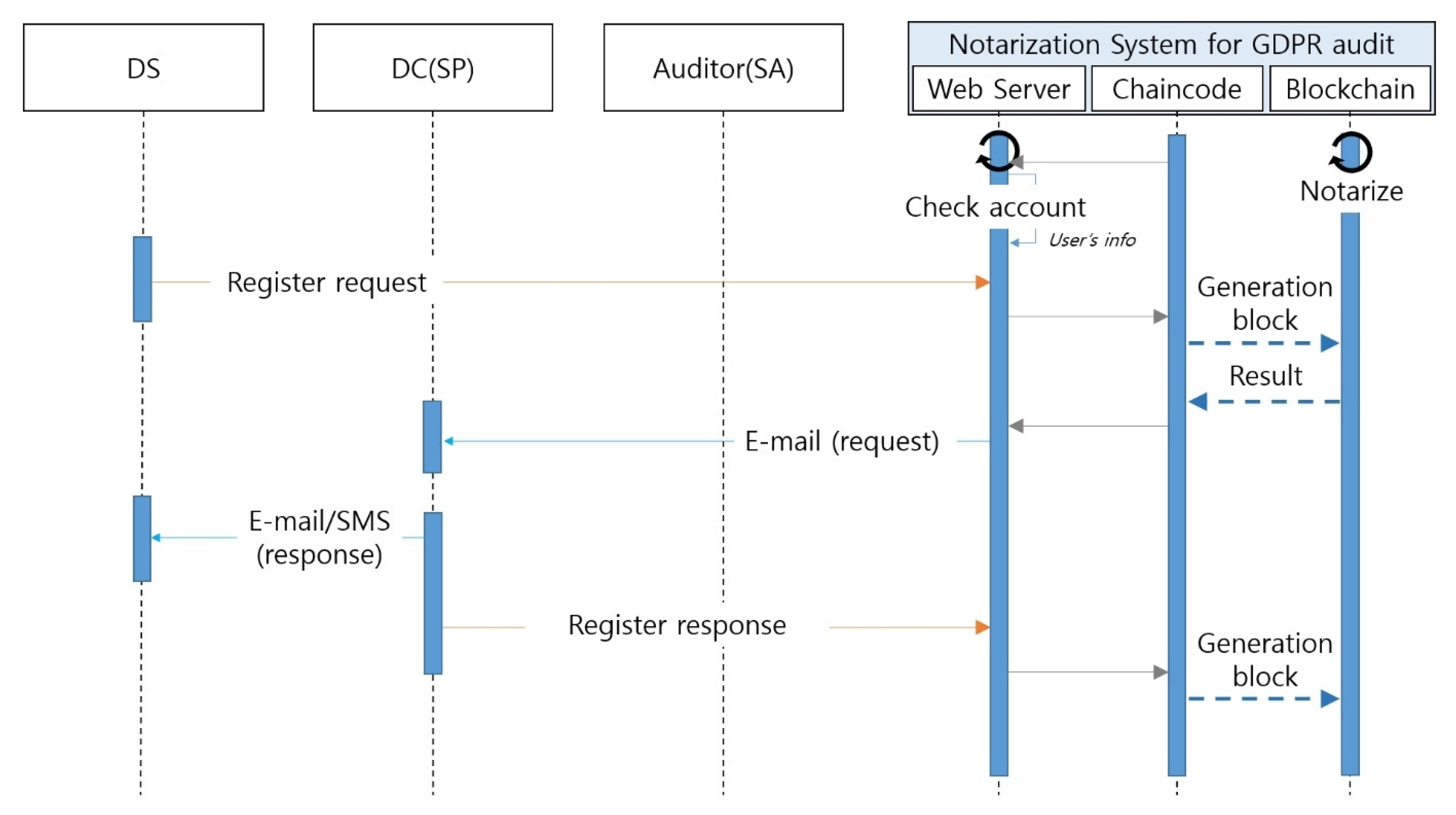
3.8. Notarization Process
| Algorithm 3. Input Request |
| INPUT: DS’s ID, SP’s URL, SP’s e-mail, process type, contents of request, timestamp OUTPUT: transaction // make key 1 SET transaction key to the result of CALL make request number with the DS’s ID and timestamp RETURNING request number 2 SET request structure with the transaction key, DS’s ID, SP’s URL, SP’s e-mail, process type, contents of request, and timestamp 3 SET JSON formed request to the result of CALL transform to JSON with request structure RETURNING JSON formed request 4 RETURN the result of CALL make transaction with transaction key and JSON formed request RETURNING transaction |
| Algorithm 4. Input Response |
| INPUT: request transaction key, DS’s ID, SP’s URL, SP’s e-mail, process type, contents of request, contents of response, timestamp OUTPUT: transaction //check request being 1 SET existing to the result of CALL checks whether it exists with request transaction key RETURNING existing 2 IF existing is false THEN 3 PRINT “the request does not exist” 4 RETURN null 5 ENDIF // make key 6 SET transaction key to the result of CALL make response number with SP’s URL and timestamp RETURNING response number 7 SET response structure with transaction key, DS’s ID, SP’s URL, SP’s e-mail, process type, contents of request, contents of response, timestamp 8 SET JSON formed response to the result of CALL transform to JSON with response structure RETURNING JSON formed response 9 RETURN the result of CALL make transaction with transaction key and JSON formed response RETURNING transaction |
3.9. GDPR Compliance Audit Process
| Algorithm 5. Input Authority |
| INPUT: grant key, grant type, auditor’s ID, SP’s URL, grantor’s ID, expiry date OUTPUT: authority transaction 1 IF grant type equal “DS” THEN 2 SET grant key to the result of JOIN auditor’s ID and grantor’s ID 3 ELSE 4 SET grant key to the result of JOIN auditor’s ID and SP’s URL 5 ENDIF //check authority being 6 SET existing to the result of CALL checks whether it exists with grant key RETURNING existing 7 IF existing is true THEN 8 SET authority transaction to the result of CALL update authority with grant key and expire date RETURNING authority transaction 9 ELSE 10 SET authority structure with grant key, grant type, auditor’s ID, SP’s URL, grantor’s ID, and expire date 11 SET JSON formed response to the result of CALL transform to JSON with response structure RETURNING JSON formed response 12 ENDIF 13 RETURN the result of CALL make transaction with transaction key and JSON formed response RETURNING transaction |
| Algorithm 6. Get Notarized Lists |
| INPUT: grant key, grant type, start date for query, end date for query OUTPUT: request transaction list, response transaction list //check authority validation 1 SET validation of authority to the result of CALL authority validation with grant key RETURNING validation of authority 2 IF validation of authority is false THEN 3 PRINT “The authority isn’t valid“ 4 RETURN null 5 ENDIF //separate and extract IDs 6 SET auditor’s ID, DS’s ID, SP’s URL to the result of CALL extract IDs with grant key RETURNING auditor’s ID, DS’s ID, SP’s URL // range query of DS’s request 7 SET list of request to the result of CALL query by range with JOIN DS’s ID and start date for query, JOIN DS’s ID and end date for query RETURNING list of request // range query of SP’s response 8 SET list of response to the result of CALL query by range with JOIN SP’s URL and start date for query, JOIN SP’s URL and end date for query RETURNING list of response 9 RETURN the result of CALL make transaction with list of request and list of response RETURNING list of JSON formed request, list of JSON formed response |
4. Implementation
4.1. Development Environment
4.2. Simulation
5. Analysis and Evaluation
5.1. Analysis of Meeting the Requirements of the Notarization Framework for GDPR Compliance Audits
5.1.1. Security Analysis
- Data security: In the proposed framework, a transaction key was generated by automatically combining the DS’s ID and timestamp in the chaincode when creating a request transaction, and the service provider URL of the DC and timestamp when creating a response transaction. The transaction was stored including the signature created by the private key of the creator. Furthermore, when searching for a stored transaction, the proposed framework compares the user’s information (Uid, SPurl) with the stored transaction key in the chaincode. When the auditor desires to query the transaction of the DS and DC, the proposed framework checks whether the auditor has been granted the inquiry right by the DS and DC and that the authorization period is valid; then, the information (Uid, SPurl) of the approvers DS and DC is compared with the stored transaction key. The transactions are linked to each other using a hash algorithm in blocks, and their integrity is guaranteed due to it being copied and distributed to each peer in the BC network. The request and response contents that may contain sensitive personal data are encrypted and input by creating a symmetric key-type session key for each transaction in the application, and the session key is stored for each transaction in the application database. The creator, receiver, and auditor with inquiry authority can decrypt the data retrieved from the BC by inquiring the session key for each transaction. Thus, even if a transaction is exposed to an unauthorized peer in the BC network, the data cannot be decrypted unless the service is accessed through authentication in the proposed framework.
- Authentication and authorization: HLF provides Fabric CA as the default CA. Fabric CA is a public key infrastructure (PKI) based and used to generate X.509 digital certificates. All entities in the HLF must be identified by a digital ID before interacting with the BC network. An X.509 digital certificate contains key and related information of an entity and is either signed by the Fabric CA or self-signed. When implementing the proposed framework, we set the initialization value in the docker-compose-ca.yaml file and started Fabric CA using Docker. Furthermore, before interacting with the proposed framework, all entities were registered with the CA server using Fabric CA client or Fabric SDK and received the key and certificate. HLF provides an infrastructure management mechanism called “policy.” Fabric policies represent the manner in which the members agree to accept or reject changes to a network, channel, or smart contract. We set policies in configtx.yaml to control all the actions each member desires to perform on the Fabric network. For example, although the DS and DC organizations allowed access to the transaction registration chaincode, the auditor group SA organization was allowed access only to the audit inquiry chaincode, while access to the notary group SA organization was not granted.
- Prevention of denial: In the proposed framework, transactions were created as blocks through the signature of the creator’s private key, stored in the ledger, and shared in the BC network. In addition, by ensuring that the peers acting as the notary of the block are composed and operated only by SAs, the integrity and reliability of the stored data was increased to prevent the repudiation of notarized data.
- Accountability: In the proposed framework, request and response transactions were stored in the form of {who, when, who, what}. As the proposed framework inherits the integrity characteristics of BC, the data stored in the proposed framework can be used for GDPR compliance audits.
5.1.2. Function Analysis
- Request and response anytime, anywhere (A1): The proposed framework was designed to delegate the DS’s request and DC’s response through the web service, notarize it in the BC network, and send it to the recipient through the e-mail service; thus, the DS and DC can make requests and responses anytime, anywhere. See Figure 6 in Section 3.4 and Figure 11 in Section 4.1.
- Save the information provided by electronic means (A2): The proposed framework stores all transactions related to personal data processing requests from DS and DC as electronic ledgers in BC. See Section 3.5 and Figure 11 in Section 4.1.
- Record of DS’s request and of DC’s response to DS’s request (A3): The proposed framework stores all transactions related to personal data processing requests from DS and DC as electronic ledgers in BC. See Section 3.5 and Figure 11 in Section 4.1.
- Non-repudiation of requests and responses (A4): The DS and DC transmit the transaction together with the private key signature to the proposed framework, and the notary node of the proposed framework notarizes with the private key signature and stores it in BC, so the creator and notary cannot deny the stored data. See ‘Prevention of denial’ in Section 5.1.1.
- Sealing of data (B1): As the proposed framework is based on private BC, network participants can be managed. The proposed framework allows only the peers of the SA to participate in the network. Furthermore, the consensus procedure of HLF, which generates blocks after verification via multiple peers, has the function of notarization. Peers acting as notaries only include the signature generated by their private key in the transaction at the time of verification and do not cause any changes. Thus, the proposed framework using HLF’s RAFT consensus algorithm meets the “sealing of data” requirement. See ‘Data security’ in Section 5.1.1.
- Accessible to all (B2): The proposed framework was designed to delegate the request of the DS and response of the DC through a web service and e-mail service. Both the DS and DC can access and use the framework after being authenticated and authorized by the CA. See Figure 11 in Section 4.1.
- Trusted or certifiable (B3): For the integrity and objective reliability of the ledger, the proposed framework restricts the nodes participating in notarization to authoritative organizations such as SAs. In the proposed framework, the algorithm that allows multiple notaries to participate and notarize inherits the RAFT algorithm of HLF, which has already been verified for stability.
- Highly trusted communications (B4): As the proposed framework uses HLF, a private BC framework, it inherits the integrity and confidentiality of the HLF’s system, network, and data. HLF supports secure communication between nodes by using transport layer security (TLS) protocol, which is applied in the proposed framework.
- Authentication (B5): The proposed framework authenticates all entities using Fabric CA, which is a CA provided by HLF. See ‘Authentication and Authorization’ in Section 5.1.1.
- Data minimization (C1): The proposed framework only stores information for auditing the processing request transaction of the DS and DC’s response to the request in the BC for the GDPR compliance audit, and it does not store any other personal data that the SPs have. See Section 3.5.
- Feasibility in real environment (D1): As the proposed framework was designed to delegate the DS’s request and DC’s response through a web service and an e-mail service, the SPs need not modify the legacy personal information processing system or install a separate third party module. Therefore, it can be applied as a GDPR compliance audit framework in a real environment.
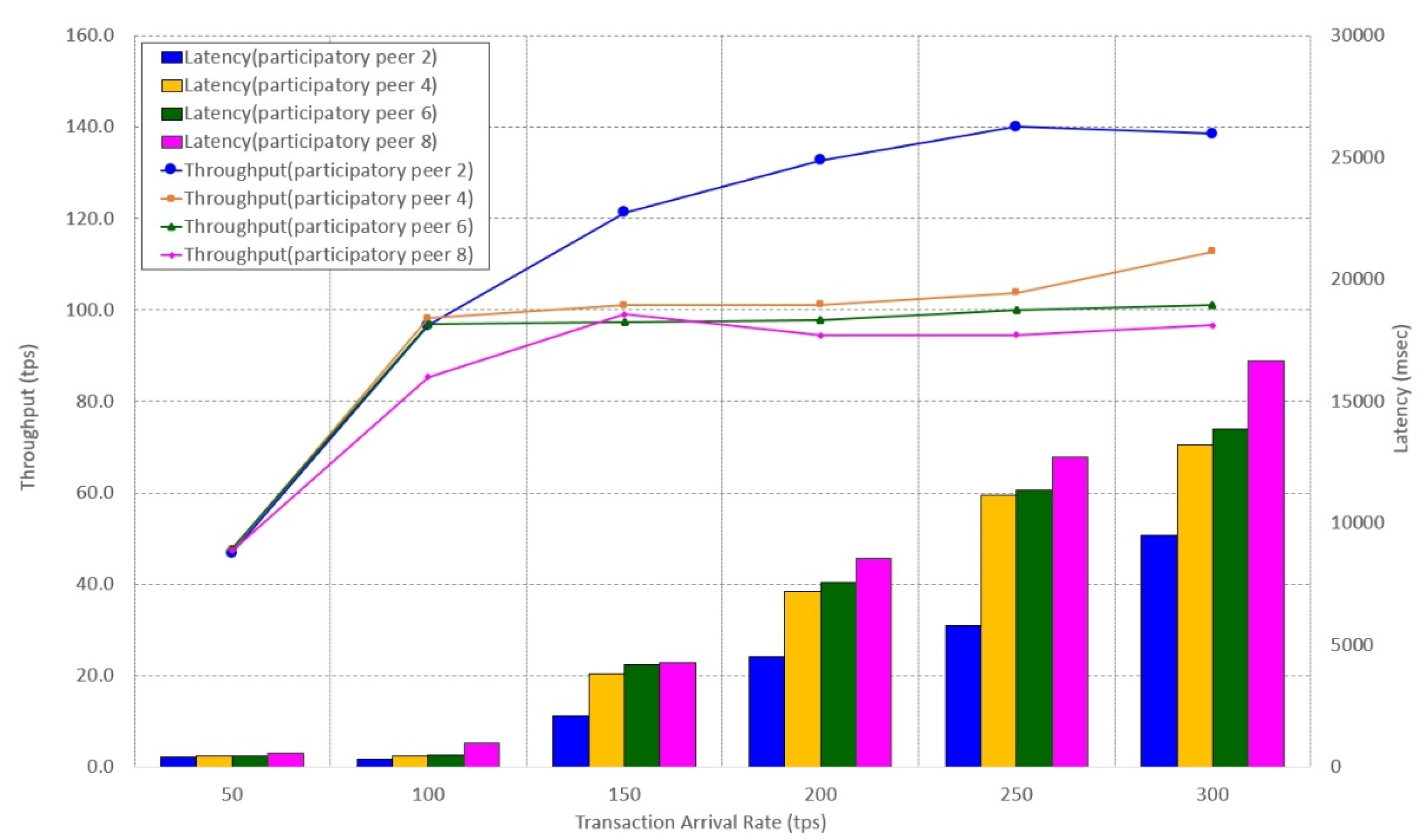
5.2. Performance Evaluation
5.3. Comparative Analysis of Related Works
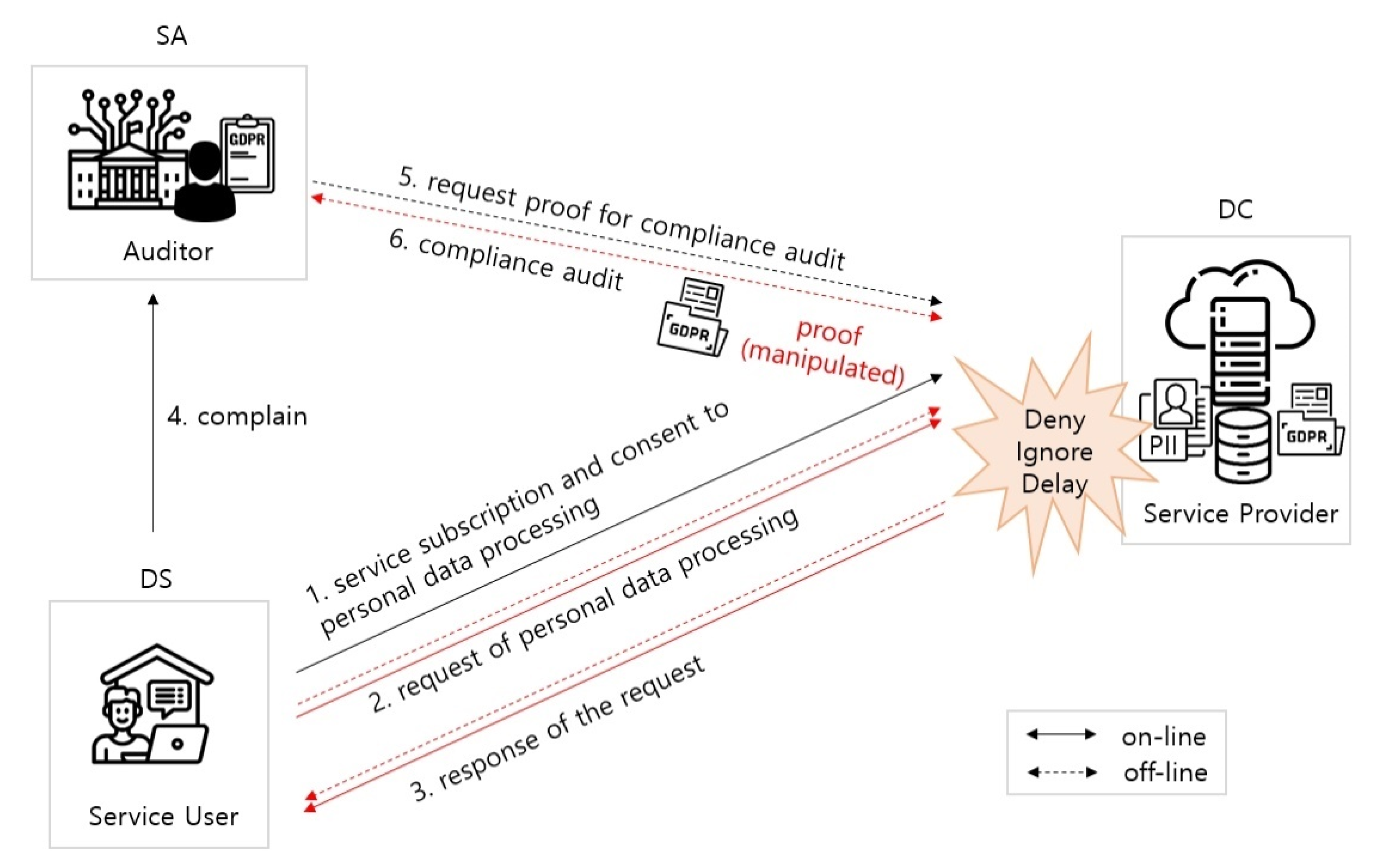
- Record of DS’s request and of DC’s response to DS’s request (A3): For an end user to request data processing to a resource server with personal data, the SP’s system is the only means to achieve it. However, this has the potential to allow the SP in the middle to ignore or manipulate the end user’s request. In addition, the proposed framework was designed around access control, such that although the access request for personal data processing is stored in the block chain before processing, the personal data processing is not stored until the resource server processes it. Furthermore, it is not designed to store the request contents of the DS because the scenario wherein the DS requests the SP to process it is not considered.
- Sealing of data (B1): It is possible for an end user to request data processing to a resource server with personal data only through the SP’s system. However, this has the potential to allow the SP in the middle to manipulate the end user’s request. Furthermore, as the proposed framework has been designed around access control, thus, the sealing and notarization process for end-user requests is not clearly presented.
- Trusted or certifiable (B3): It was assumed that a DS is “honest-but-curious”, whereas SPs follow a malicious model. This indicates that the DS executes the required protocols, even though it might be curious about the results it receives after the operations. Most of the records of the processing of personal data are stored in the proposal framework by the resource server; however, if the resource server is not trusted, the data also cannot be trusted.
- Data minimization (C1): The proposed framework stores all personal data processing history of the SP. When the DS subscribes to the service of the SP, it delegates the processing of personal data to the SP. Therefore, owing to the excessive nature amount, all personal data processing of the SP delegated by DS for GDPR compliance audit and personal data related to personal data processing is also stored. Furthermore, considering the characteristics of the BC where data are replicated, distributed, and stored, and deletion is not easy, the more personal data are stored, the greater the risk of exposure and the greater the possibility of violating the principle of data minimization.
- Feasibility in real environment (D1): To apply the proposed framework, SPs must modify the legacy personal data processing system or install a separate third-party module. However, the application of the proposed framework to the real environment is difficult because enforcing it on all SPs in the real environment is a challenge.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Farahani, B.; Firouzi, F.; Luecking, M. The convergence of IoT and distributed ledger technologies (DLT): Opportunities, challenges, and solutions. J. Netw. Comput. Appl. 2021, 177, 102936. [Google Scholar] [CrossRef]
- Sellami, M.; Mezni, H.; Hacid, S. On the use of big data frameworks for big service composition. J. Netw. Comput. Appl. 2020, 166, 102732. [Google Scholar] [CrossRef]
- Campanile, L.; Iacoco, M.; Marulli, F.; Mastroianni, M. Designing a GDPR compliant blockchain-based IoV distributed information tracking system. Inf. Process. Manag. 2021, 58, 102511. [Google Scholar] [CrossRef]
- Tamburri, D.A. Design principles for the General Data Protection Regulation (GDPR): A formal concept analysis and its evaluation. Inf. Syst. 2020, 91, 101469. [Google Scholar] [CrossRef]
- Yang, X. Business big data analysis based on microprocessor system and mathematical modeling. Microprocess. Microsyst. 2021, 82, 103846. [Google Scholar] [CrossRef]
- Bhattacharya, M.; Islam, R.; Abawajy, J. Evolutionary optimization: A big data perspective. J. Netw. Comput. Appl. 2016, 59, 416–426. [Google Scholar] [CrossRef]
- Singh, A.; Click, K.; Parizi, R.M.; Zhang, Q.; Dehghantanha, A.; Choo, K.R. Sidechain technologies in blockchain networks: An examination and state-of-the-art review. J. Netw. Comput. Appl. 2020, 149, 102471. [Google Scholar] [CrossRef]
- Parra Freund, G.; Fagundes, P.B.; Macedo, D.D.J. An analysis of blockchain and GDPR under the data lifecycle perspective. Mob. Netw. Appl. 2020, 26, 266–276. [Google Scholar] [CrossRef]
- Eugenia, P.; Efthimios, A.; Constantinos, P. Forgetting personal data and revoking consent under the GDPR: Challenges and proposed solutions. J. Cybersecur. 2018, 4, 1–20. [Google Scholar]
- Korea Legislation Research Institute. Personal Information Protection Act. Act No. 16930. 2020. Available online: https://elaw.klri.re.kr/eng_service/lawView.do?hseq=53044&lang=ENG (accessed on 29 May 2021).
- European Union. Directive 95/46/EC of the European Parliament and of the Council on the Protection of Individuals with Regard to the Processing of Personal Data and on the Free Movement of Such Data. Available online: https://eur-lex.europa.eu/legal-content/en/TXT/?uri=CELEX%3A31995L0046 (accessed on 29 May 2021).
- ICLG. USA: Data Protection Laws and Regulations. 2020. Available online: https://iclg.com/practice-areas/data-protection-laws-and-regulations/usa (accessed on 29 May 2021).
- Gobeo, A.; Fowler, C.; Buchanan, W.J. 4 Cyber Security and the GDPR. In GDPR and Cyber Security for Business Information Systems; River Publishers: Gistrup, Denmark, 2018; pp. 93–116. [Google Scholar]
- Greenleaf, G. Global data privacy laws 2019: 132 national laws & many bills. Priv. Laws Bus. Int. Rep. 2019, 157, 14–18. [Google Scholar]
- Team, I.P. EU General Data Protection Regulation (GDPR): An Implementation and Compliance Guide; IT Governance Ltd.: Ely, UK, 2017. [Google Scholar]
- Cimina, V. The data protection concepts of ‘controller’, ‘processor’ and ‘joint controllership’ under Regulation (EU) 2018/1725. ERA Forum 2021, 21, 639–654. [Google Scholar] [CrossRef]
- Wirth, C.; Kolain, M. Privacy by blockchain design: A blockchain enabled GDPR-compliant approach for handling personal data. In Proceedings of the 1st ERCIM Blockchain Workshop 2018, European Society for Socially Embedded Technologies (EUSSET), Amsterdam, The Netherlands, 8 May 2018. [Google Scholar]
- Bernabe, J.B.; Canovas, J.L.; Hernandez-Ramos, J.L.; Moreno, R.T.; Skarmeta, A. Privacy-preserving solutions for blockchain: Review and challenges. IEEE Access 2019, 7, 164922–164923. [Google Scholar] [CrossRef]
- Sutton, A.; Samavi, R. Blockchain Enabled Privacy Audit Logs. In Proceedings of the International Semantic Web Conference, Vienna, Austria, 21–25 October 2017; pp. 645–660. [Google Scholar]
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentland, A. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 18–20 May 2015; pp. 180–184. [Google Scholar]
- Hillmann, P.; Knupfer, M.; Heiland, E.; Karcher, A. Selective Deletion in a Blockchain. In Proceedings of the International Workshop on Blockchain and Mobile Applications (BlockApp 2020) during the International Conference on Distributed Computing Systems (ICDCS 2020), Singapore, 29 November–1 December 2020. [Google Scholar]
- Tatar, U.; Gokce, Y.; Nussbaum, B. Law versus technology: Blockchain, GDPR, and tough tradeoffs. Comput. Law Secur. Rev. 2020, 38, 105454. [Google Scholar] [CrossRef]
- Carvalho, R.M.; Prete, C.D.; Martin, Y.S.; Rivero, R.M.A.; Onen, M.; Schiavo, F.P.; Rumin, A.C.; Mouratidis, H.; Yelmo, J.C.; Koukovini, M.N. Protecting Citizens’ Personal Data and Privacy: Joint Effort from GDPR EU Cluster Research Projects. SN Comput. Sci. 2020, 1, 217. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Rieger, A.; Guggenmos, F.; Lockl, J.; Fridgen, G.; Urbach, N. Building a Blockchain Application that Complies with the EU General Data Protection Regulation. MIS Q. Exec. 2019, 18, 263–279. [Google Scholar] [CrossRef] [Green Version]
- Hewa, T.; Ylianttila, M.; Liyangage, M. Survey on blockchain based smart contracts: Applications, opportunities and challenges. J. Netw. Comput. Appl. 2021, 177, 102857. [Google Scholar] [CrossRef]
- Asaf, K.; Rehman, R.A.; Kim, B.S. Blockchain technology in Named Data Networks: A detailed survey. J. Netw. Comput. Appl. 2020, 171, 102840. [Google Scholar] [CrossRef]
- Liang, X.; Shetty, S.; Tosh, D.; Kamhoua, C.; Kwiat, K.; Njilla, L. ProvChain: A Blockchain-Based Data Provenance Architecture in Cloud Environment with Enhanced Privacy and Availability. In Proceedings of the 2017 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Madrid, Spain, 14–17 May 2017; pp. 468–477. [Google Scholar]
- Yan, Z.; Gan, G.; Riad, K. BC-PDS: Protecting Privacy and Self-Sovereignty through BlockChains for OpenPDS. In Proceedings of the 2017 IEEE Symposium on Service-Oriented System Engineering, San Francisco, CA, USA, 6–9 April 2017; pp. 138–144. [Google Scholar]
- Chowdhury, M.J.M.; Colman, A.; Kabir, M.A.; Han, J.; Sarda, P. Blockchain as a Notarization Service for Data Sharing with Personal Data Store. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1330–1335. [Google Scholar]
- Agarwal, S.; Steyskal, S.; Antunovic, F.; Kirrane, S. Legislative Compliance Assessment: Framework, Model and GDPR Instantiation. In Annual Privacy Forum; Springer: Berlin/Heidelberg, Germany, 2018; pp. 131–149. [Google Scholar]
- Truong, N.B.; Sun, K.; Guo, Y. Blockchain-Based Personal Data Management: From Fiction to Solution. In Proceedings of the 2019 IEEE 18th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 26–28 September 2019; pp. 1–8. [Google Scholar]
- Truong, N.B.; Lee, G.M.; Lee, G.M.; Guo, Y. GDPR-Compliant Personal Data Management: A Blockchain-based Solution. IEEE Trans. Inf. Forensics Secur. 2019, 15, 1746–1761. [Google Scholar] [CrossRef] [Green Version]
- Vargas, J.C. Blockchain-Based Consent Manager for GDPR Compliance. In Open Identity Summit; Gesellschaft für Informatik: Bonn, Germany, 2019; pp. 165–170. [Google Scholar]
- Kassem, J.A.; Sayeed, S.; Marco-Gisbert, H.; Pervez, Z.; Dahal, K. DNS-IdM: A blockchain identity management system to secure personal data sharing in a network. Appl. Sci. 2019, 9, 2953. [Google Scholar] [CrossRef] [Green Version]
- Rantos, K.; Drosatos, G.; Demertzis, K.; Ilioudis, C.; Papanikolaou, A.; Kritsas, A. ADvoCATE: A consent management platform for personal data processing in the iot using blockchain technology. In Proceedings of the International Conference on Security for Information Technology and Communications (SecITC), Bucharest, Romania, 8–9 November 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 300–313. [Google Scholar]
- Faber, B.; Michelet, G.; Weidmann, N.; Mukkamala, R.R.; Vatrapu, R. BPDIMS: A blockchain-based personal data and identity management system. Int. Conf. Syst. Sci. 2019, 45, 254–264. [Google Scholar]
- Piras, L. DEFeND architecture: A Privacy by Design Platform for GDPR Compliance. In Proceedings of the 16th International Conference on Trust and Privacy in Digital Business (TrustBus), Linz, Austria, 26–29 August 2019; pp. 78–93. [Google Scholar]
- Mahindrakar, A.; Joshi, K.P. Automating GDPR Compliance using Policy Integrated Blockchain. In Proceedings of the 2020 IEEE 6th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing, (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS), Baltimore, MD, USA, 25–27 May 2020; pp. 86–93. [Google Scholar]
- Casaleiro, R. Protection and control of personal identifiable information: The PoSeID-on approach. J. Data Prot. Priv. 2020, 3, 199–228. [Google Scholar]
- Daudén-Esmel, C.; Castellà-Roca, J.; Viejo, A.; Domingo-Ferrer, J. Lightweight Blockchain-based Platform for GDPR-Compliant Personal Data Management. In Proceedings of the 5th International Conference on Cryptography, Security and Privacy, Zhuhai, China, 4 May 2021; pp. 68–73. [Google Scholar]
- Haque, A.B.; Islam, A.N.; Hyrynsalmi, S.; Naqvi, B.; Smolander, K. GDPR Compliant Blockchains—A Systematic Literature Review. IEEE Access 2021, 9, 50593–50606. [Google Scholar] [CrossRef]
- Low, M.R. The Notary, University of Hertfordshire Computer Science Technical Report; University of Hertfordshire: Hertfordshire, UK, 1992; Volume 153, pp. 2–5. [Google Scholar]
- Hyperledger Caliper Project. Hyperledger Caliper. Available online: https://www.hyperledger.org/projects/caliper (accessed on 30 October 2021).








| No | Research Works | Proposed Technology |
|---|---|---|
| R01 | Liang et al. in [29] | BC-based data provenance architecture in cloud environment with privacy |
| R02 | Yan et al. in [30] | Protecting privacy and self-sovereignty through blockchains for OpenPDS |
| R03 | Chowdhury et al. in [31] | BC as a notarization service for data sharing with personal data store |
| R04 | Agarwal et al. in [32] | GDPR legislative compliance assessment |
| R05 | Truong et al. in [33] | BC-based personal data management |
| R06 | Truong et al. in [34] | GDPR-compliant personal data management |
| R07 | Vargas in [35] | BC-based consent manager for GDPR compliance |
| R08 | Kassem et al. in [36] | BC identity management system to secure personal data sharing in a network |
| R09 | Rantos et al. in [37] | Consent management platform for personal data processing using BC |
| R10 | Faber et al. in [38] | BC-based personal data and identity management system |
| R11 | Piras in [39] | Privacy by design platform for GDPR compliance |
| R12 | Mahindrakar and Joshi in [40] | Automating GDPR compliance using policy integrated BC |
| R13 | Casaleiro in [41] | Protection and control of personal identifiable information |
| R14 | Daudén-Esmel et al. in [42] | BC-based platform for GDPR-compliant personal data management |
| Major Research Field | Related Work’s Number |
|---|---|
| Data provenance | R01 |
| Access control | R05, R06 |
| Notarization | R02, R03, R09 |
| Identity management | R08, R10 |
| Compliance assessment | R04, R12 |
| Consent management | R07, R09, R14 |
| GDPR compliance management | R06, R07, R11, R13 |
| Limitations | Related Work’s Number |
|---|---|
| Lack of proposal of measures considering detailed regulations for GDPR compliance | R01, R02, R03, R05, R07, R08, R09, R10, R11 |
| Lack of support for outer auditors | R05, R06, R08, R09, R10 |
| Lack of consideration of scalability issues due to legacy system linkage | R01, R02, R03, R04, R05, R06, R09, R10, R12, R13, R14 |
| Lack of consideration of personal data protection issues in BC (risk of privacy violations due to storage of personal data and all access records) | R01, R05, R06, R07, R13 |
| Lack of presentation of a practical BC system implementation method | R02, R03, R07, R08, R10, R11, R12, R13, R14 |
| Lack of research on GDPR compliance with personal data processing request | All except R06, R07, and R14 |
| Attack | Description | Countermeasure |
|---|---|---|
| Race attack | Send two conflicting transactions in rapid succession. | Since it is different from cryptocurrency, multiple recipients who receive the same transaction will not be harmed if their own transaction is canceled. |
| Brute force attack | Attempt to decrypt any encrypted data. | Data are encrypted with an encryption algorithm recognized for stability that uses a key length of 256 bytes or more, such as AES-256. Brute force attacks on 256-byte keys are almost statistically impossible with current technology. |
| 51% attack | After securing more than 50% of the hash computing power among all nodes, the transaction information is manipulated. | Authorizes only SAs as BC network nodes and controls malicious participants. It is possible that the proposed network is a private BC. |
| DoS (Denial-of-Service) attack | Sending massive amounts of traffic paralyzes BC networks and nodes. | Revokes access and authority of a party that mounts a DOS on the system since they are known identities rather than anonymous. |
| Unauthorized access attack | Access or modify a function or variable that should not be accessed. | Checks authentication and authority in web service and BC network. Respectively, manages authority for smart contract functions by the user group. Allows only own transaction to be accessed. |
| Replay attack | Copy a transaction that was added to the BC in the past and replay it in the network to distort its operation. | Users submitting a transaction with a transaction certificate should include in the transaction a random nonce, that would guarantee that two transactions do not result into the same hash. |
| Sniffing and capture attack | Monitoring and capturing all data packets passing through network. | TLS is used for all network sections. Encrypts the main data of the transaction based on the session key. |
| A1 | A2 | A3 | A4 | B1 | B2 | B3 | B4 | B5 | C1 | D1 |
|---|---|---|---|---|---|---|---|---|---|---|
| Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| A1 | A2 | A3 | A4 | B1 | B2 | B3 | B4 | B5 | C1 | D1 |
| Y | Y | N | Y | N | Y | N | Y | Y | N | N |
| Work | A1 | A2 | A3 | A4 | B1 | B2 | B3 | B4 | B5 | C1 | D1 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| Proposed | Y | Y | Y | Y | Y | Y | N | Y | Y | Y | Y |
| Truong et al. | Y | Y | N | Y | N | Y | N | Y | Y | N | N |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jung, S.-S.; Lee, S.-J.; Euom, I.-C. Delegation-Based Personal Data Processing Request Notarization Framework for GDPR Based on Private Blockchain. Appl. Sci. 2021, 11, 10574. https://doi.org/10.3390/app112210574
Jung S-S, Lee S-J, Euom I-C. Delegation-Based Personal Data Processing Request Notarization Framework for GDPR Based on Private Blockchain. Applied Sciences. 2021; 11(22):10574. https://doi.org/10.3390/app112210574
Chicago/Turabian StyleJung, Sung-Soo, Sang-Joon Lee, and Ieck-Chae Euom. 2021. "Delegation-Based Personal Data Processing Request Notarization Framework for GDPR Based on Private Blockchain" Applied Sciences 11, no. 22: 10574. https://doi.org/10.3390/app112210574
APA StyleJung, S.-S., Lee, S.-J., & Euom, I.-C. (2021). Delegation-Based Personal Data Processing Request Notarization Framework for GDPR Based on Private Blockchain. Applied Sciences, 11(22), 10574. https://doi.org/10.3390/app112210574







