Abstract
Along with the growing popularity of online social networks, an environment has been set up with information spreading faster and wider than ever before, which has changed the way of information diffusion. Previous empirical research and propagation models have been conducted to illustrate how information propagates on online social networks. However, due to the complexity of information diffusion, there are still many important issues yet to be resolved. In order to tackle this problem, most studies have assumed that information is transmitted along the edges on online social networks, while most research goals aim to discover nodes that have been affected by information diffusion. However, we found that processes of information diffusion on online social networks vary from one another; some topics such as people’s livelihood and education are long-acting while some entertainment news is short-lived. The scale of propagation may be similar in the end, but the spreading process would be completely different. With the purpose of modeling the propagation process more realistically, we propose a novel model, the Information Diffusion Model, based on Explosion Shock Wave Theory. The Information Diffusion Model compares the propagation process to the explosion of an information bomb at the source, with the information shock waves progressively spread from near to far. Additionally, we establish rules of information transmission between a pair of individuals. The approach we adopted demonstrates four strengths. First, it models information diffusion on OSNs considering the differences between individuals and individual social behaviors, which takes the individual background knowledge and forgetting factors into account. Second, it holds the point that the attractiveness of information to individuals is related to the value of information. Third, it recognizes the role of community in the diffusion process; with a higher sense of trust established in a community, the spread of information would be more convenient. More importantly, the model we put forth is applicable to different types of real online social network datasets. Many experiments with different settings and specifications are conducted to verify the advantages of the model, and the results obtained are very promising.
1. Introduction
Online social networks (OSNs) have greatly transformed Internet ecosystems and penetrated into every aspect of people’s daily lives. These OSNs, such as Weibo, Twitter, and Facebook, have shown impressive values in connecting massive numbers of users worldwide. Users can implement a series of online social activities on OSNs, including posting content, building friendships, and commenting. Based on these characteristics of OSNs, an extensive and real-time form of information diffusion (the process of information flowing from one node to another in the network [1]) featuring new ideas, advertisements, and breaking news can successfully come into reality.
The OSNs provide fundamental access and platform for various types of information, opinions, rumors, and so on [2]. In 2020, since the outbreak of COVID-19, the rapid dissemination on the Internet has also caused panic among the people and influenced rising prices. People’s livelihood is reassured only after the official information was released. This incident fully proves that OSNs have played important roles in our society; thus, it is necessary to conduct in-depth research in this field. Additionally, a more comprehensive understanding of the information dissemination process on OSNs is also needed so as to add more valuable insights into the control of online public opinion.
In previous studies, OSNs are generally represented by graphs, while the users are represented by nodes, with the relationships between users represented by edges. On the one hand, most research studies show the results of diffusion from a macro level, which focuses on the number of nodes in different states at each moment. On the other hand, some studies may analyze the process of information transmission between nodes from a micro level. However, we found that some information diffusion processes on OSNs could have a long-lasting effect, such as topics of people’s livelihood and education, while other processes may be short-lived, for example, entertainment news. These two processes may seem to have the same spreading scale, but in nature they are subject to different diffusion processes. Therefore, it would be difficult to distinguish these processes from the previous models. The major deficiency of the previous information diffusion models lies in the weakness in capturing human social behaviors on OSNs. An efficient model should be able to reflect the true diffusion of information and involve important aspects of the process so as to better understand this phenomenon.
As reaching a consensus that the diffusion model plays a significant role in information propagation, we propose a novel one, the Information Diffusion Model based on Explosion Shock Wave Theory, (the IDBESW model), taking the social behaviors of individuals and the value of information within the diffusion process. Inspired by the explosion shock wave, the individuals will be affected at different distances from the explosion center, with the influence gradually declining with time. The value of information is equivalence to the power of the bomb. It is worth mentioning that we establish rules of information transmission between two individuals, and the advantages of our method are four-fold. First, it can simulate information diffusion on OSNs, considering the differences between individuals and individual social behaviors, with individual background knowledge and forgetting factors included. Second, it holds the view that the attractiveness of information to individuals is related to the value of information. Third, it recognizes the role of community in the diffusion process. The community with a higher level of trust among individuals may provide a more convenient platform for the spread of information. Finally, our model is applicable to different types of real online social network datasets. A number of experiments with different settings and specifications were carried out to examine the advantages of the model, which proves to be quite promising.
The remainder of this paper is organized as follows. Section 2 gives a brief survey over the related work. A detailed description of the proposed information propagation model is presented in Section 3. In Section 4, we display and discuss the results of experiments. Finally, we conclude this paper in Section 5.
2. Related Work
2.1. Information Diffusion Models
With the growing popularity of OSNs, several problems related to it have attracted the attention of researchers. Among these problems, the foundation is to build an information diffusion model that is effectively close to the real situation [3]. Based on a careful classification on the designing conceptions of the existing work, we have summarized two groups: macroscopic and microscopic approaches.
Macroscopic models divide the nodes into different categories (that is, states), focusing on the state evolution of the nodes in each category. An epidemic model is the most common model used to study information propagation from a macro perspective, in which the spreading is similar to that of a disease in a community. Daley and Kendall [4] proposed the classic Daley–Kendall model by studying the similarities between the spread of infectious diseases and the diffusion of information. Later, variants of this classic model were developed, such as susceptible–infected–recovered (SIR) [5], susceptible–infected–susceptible (SIS) [6], susceptible–infected–recovered–susceptible (SIRS) [7], susceptible–exposed–infectious–recovered (SEIR) [8], and other similar epidemic models. Furthermore, researchers have begun to consider the impact of human behaviors and different mechanisms on the process of information diffusion. Wang et al. [5] introduced the trust mechanism between people into the SIR model, and proved through experiments that the trust mechanism can reduce the final size of rumor spreading. Considering the incomplete reading behavior of users during the diffusion process, Su et al. [9] proposed an improved model called microblog–susceptible–infected–removed (Mb-SIR) for information diffusion. Experimental results prove that this model is more accurate in describing the information spread in Weibo. To incorporate the forgetting and remembering mechanism, Zhao et al. [10,11] considered forgetting and memory factors in the diffusion process and proposed the susceptible–infected–hibernator–removed (SIHR) model as an extension of the classical SIR model; Wang et al. [12] analyzed the impact of social reinforcement on the spreading rate. They proposed a rumor diffusion model based on social reinforcements. Xia et al. [13] considered the hesitating mechanism. He et al. [14] proposed a competitive information susceptible–infected–recovered (CISIR) model for studying the competitive information diffusion process on online social networks.
The most frequently used microscopic models are the independent cascades (IC) model and the linear threshold (LT) model [15,16]. The IC and LT models are the milestones in studying the issue of information diffusion. The IC model [16] assumes that each node has the ability to activate its neighbors based on probability. Each active node has only one chance to activate the inactive nodes among the neighbors. If a node has already activated one of its neighbors, it then has no further chance to activate others. The LT model [15] assumes that every node has a randomly selected threshold between 0 and 1. In addition, the node will be affected by its neighbor in consideration of a given weight. Given a set of initial active nodes and randomly selected thresholds, if the number of active neighbors of a node exceeds its private threshold, the node will be activated. In order to improve the IC and LT models, many researchers have proposed different algorithms. Chen et al. [17] proposed an IC model with meeting events (IC-M) based on the classic IC model. In IC-M model, activated nodes have a probability to meet the inactive nodes. Compared with the common IC model, this model is closer to the actual situation. Budak et al. [18] studied the notion of competing campaigns on social networks and proposed a multicampaign IC model to simulate the diffusion of multiple pieces of information at the same time. Considering the time dependence of information, Mohammadi et al. [19] developed two models, namely the delay independent cascade (DIC) model and the delay linear threshold (DLT) model. Compared with the general models, a latent active state is added to these two models. Fan et al. [20] proposed the opportunistic one-activate-one (OOAO) model and the deterministic one activation multiple (DOAM) model. In the OOAO model, everyone can only communicate with one another at the same time; the DOAM model has a broadcasting mechanism. Saito et al. [21] developed the asynchronous IC (AsIC) and asynchronous LT (AsLT) models based on previous work. These learning algorithms can estimate the influence of nodes in a network based on relatively few information diffusion results. Guille et al. [22] also proposed an asynchronous model, called the time-based AsIC model, to simulate the information diffusion. Mohamadi-Baghmolaei et al. [23] added the time and trust factors to the IC model, and proposed a trust-based latency-aware independent cascade (TLIC) model, which considered the trust factor in the IC model for the first time. Liu et al. [24] extend the LT model to establish the diffusion-containment model, abbreviated as D-C model, by incorporating the realistic specialties and characteristics of the containment of competitive influence spread. Other studies [25,26,27,28] have improved the classical models in specific aspects as well. Additionally, Ding et al. [29] presented a topologically biased random walk for the diffusion process in social networks, displaying how topological properties affect the diffusion process. Lahiri et al. [30] proposed a diffusion model based on the genetic algorithm, which assumes that individuals in the networks exchange information with others to improve the value of the information held by themselves. Hajibagheri et al. [31] proposed a particle swarm optimization model (PSO) to simulate the process of information diffusion. Mozafari et al. [32] recognized the fact that in the process of information diffusion, individuals can also receive information from the media in addition to receiving it from neighbors, which inspired his work on a multisource information perception model (MSIP) to simulate the process.
The diffusion process of information on OSNs is closely related to the content, the users, and the structure of the OSNs. Information that matches the users’ background is the most attractive. As the information is time sensitive, the discover time will also be an important factor that may influence the interest of users. However, the macroscopic models, which consider individuals having exactly the same characteristics and the same abilities to influence other users, may ignore the individual differences in the process. Microscopic models focus on the interaction between individuals, but overlook another important factor in the process: information. These micromodels assume that all information shares the same effect on nodes. Individuals may become interested in information when they are activated. However, due to the timeliness of information, individuals tend to receive the latest information, which could explain why the attractiveness of information may vary on account of the discover time.
2.2. Explosive Shock Wave
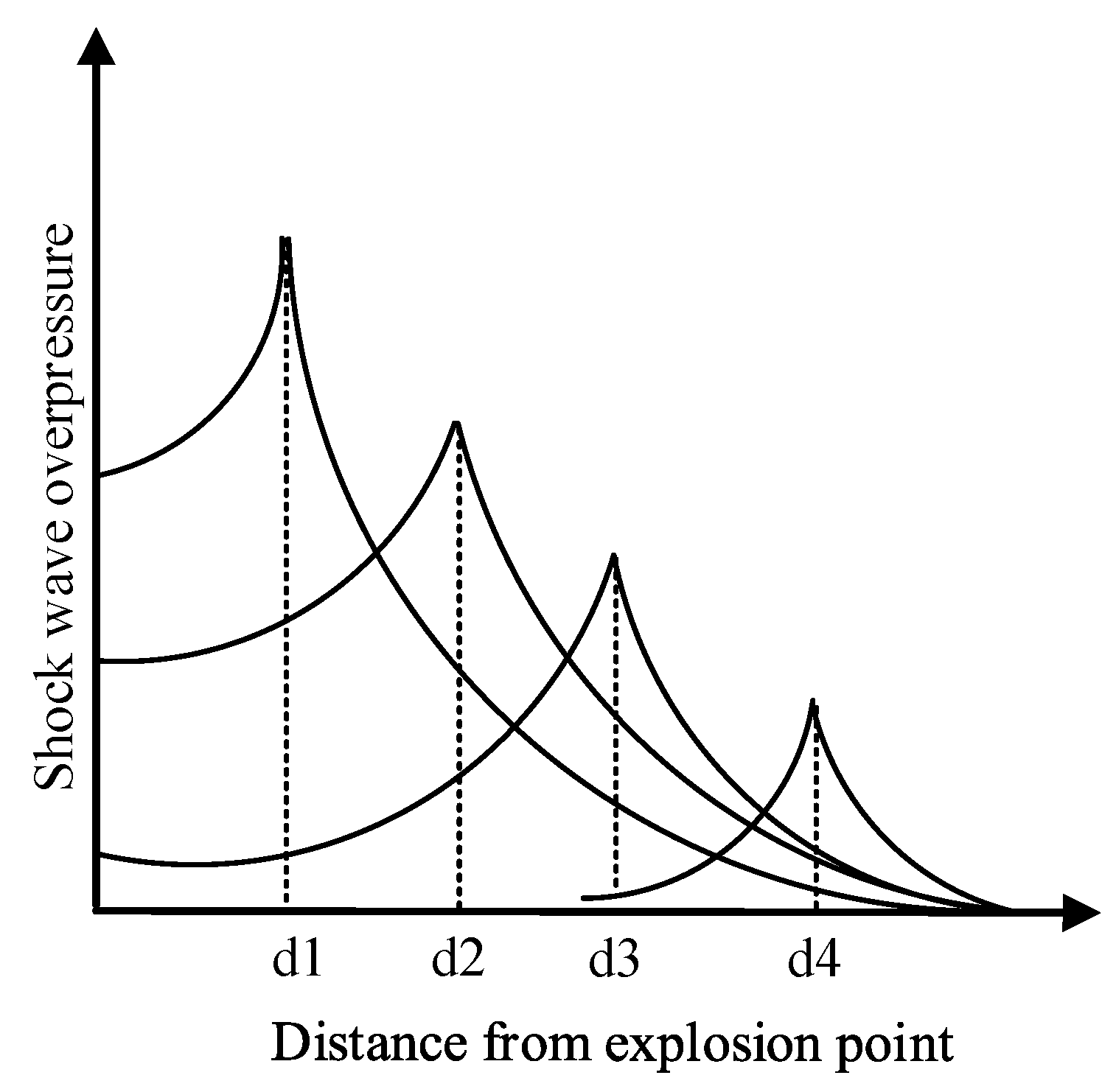
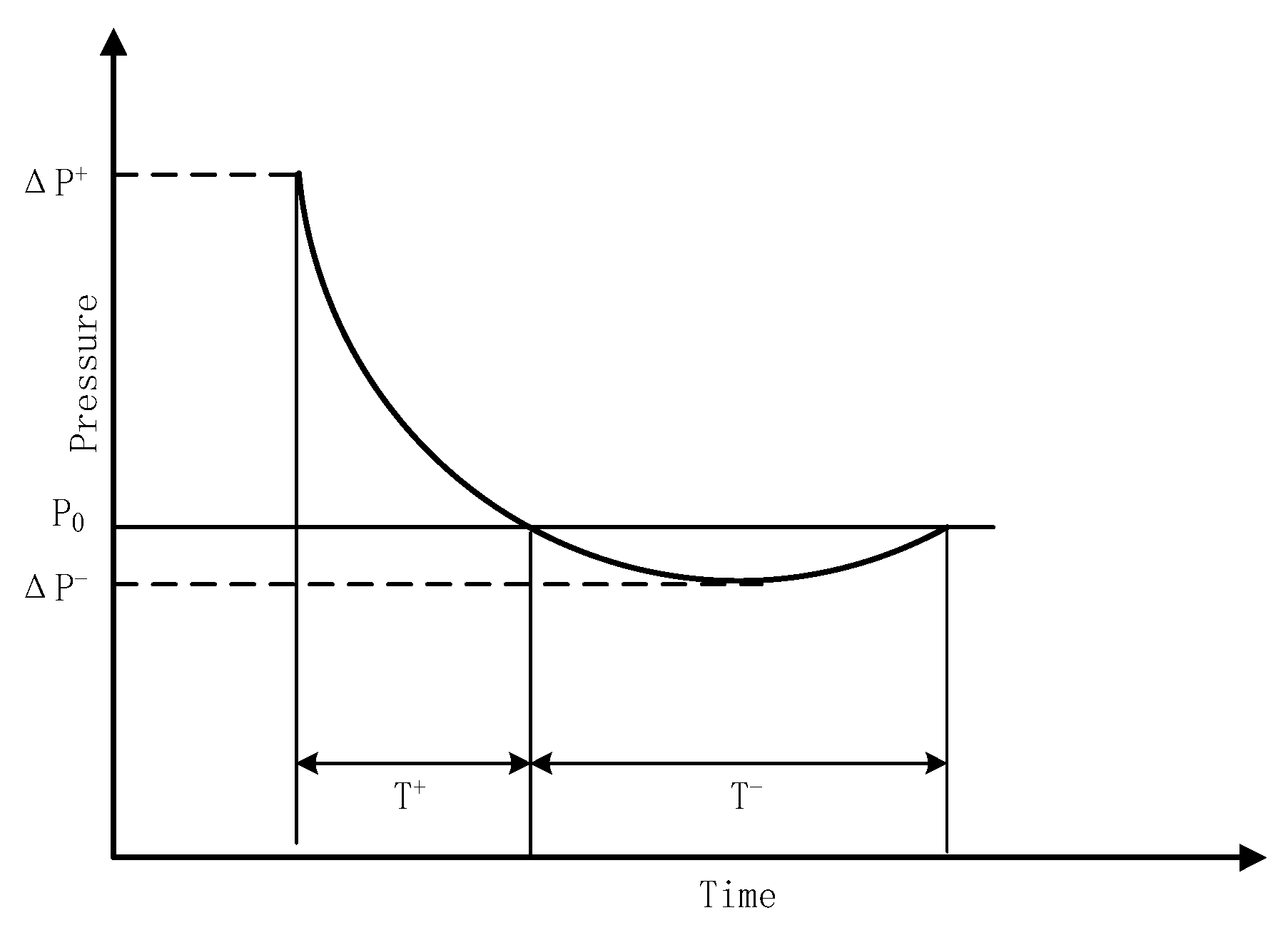
The explosive shock wave is briefly introduced in Section 2.2. An explosion is a process of physical and chemical changes. At the moment of the explosion, high temperature and high-pressure gas is generated in the core area and rapidly expands and spreads around, forming a strong shock wave in the air. The momentary pressure that exceeds the surrounding atmospheric pressure is called overpressure, and it is one of the most important shock wave effects. The shock wave overpressure decays with distance. The farther from the explosion center, the smaller the peak overpressure and the smaller the damage caused by the explosion, as shown in Figure 1. For a fixed point in space, due to various complicated reasons such as damping, the overpressure value decays with time. A typical attenuation curve is shown in Figure 2. At the moment after the explosion, the pressure in this point suddenly rises to the peak value of overpressure , and then the pressure decays to through time, then reaches the peak value of negative pressure , and finally returns to , where is the ambient pressure [33].
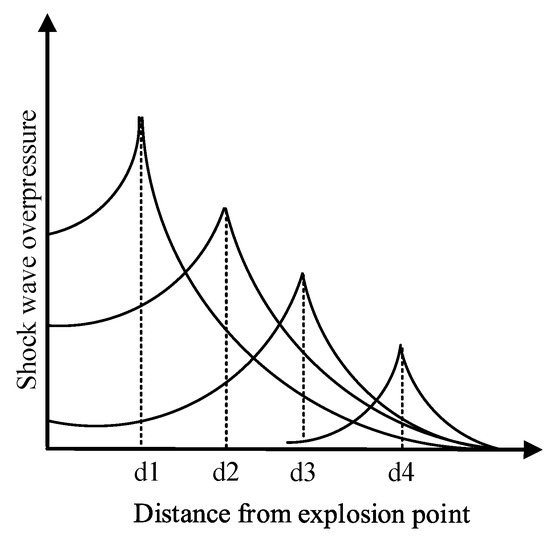
Figure 1.
Explosion shock wave overpressure decays with distance.
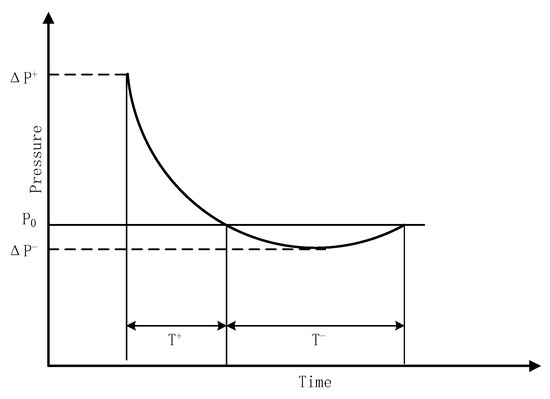
Figure 2.
Explosion shock wave overpressure decays with time.
According to Henrych classical theory, when an explosion occurs in the air, the peak value of shock wave overpressure and the value of overpressure can be represented by the following formula [34]:
where is the equivalence of the explosion, which means the power of the bomb; is the distance from the observation point to the center of the explosion; is the length of time under positive pressure; and is the decay coefficient of during time .
3. Proposed Method
3.1. Information Diffusion Model
In this section, we first specify the definition of the research and then introduce the model, where we focus on three major details: information perception, information evaluation, and information transmission.
Definition 1.
An online social network withusers can be represented by a graph, Set of nodes denotes users, where and the set of edges specifies the relationship between users. is a set of individuals’ characteristics, where ;identifies the characteristics of the individual .
Definition 2.
The state of the nodes on the online social networks is denoted by the set , where , represents the state of node .
Definition 3.
The information diffusion process is a sequence of based on time , where . specifies the state of all nodes on an OSN at time .
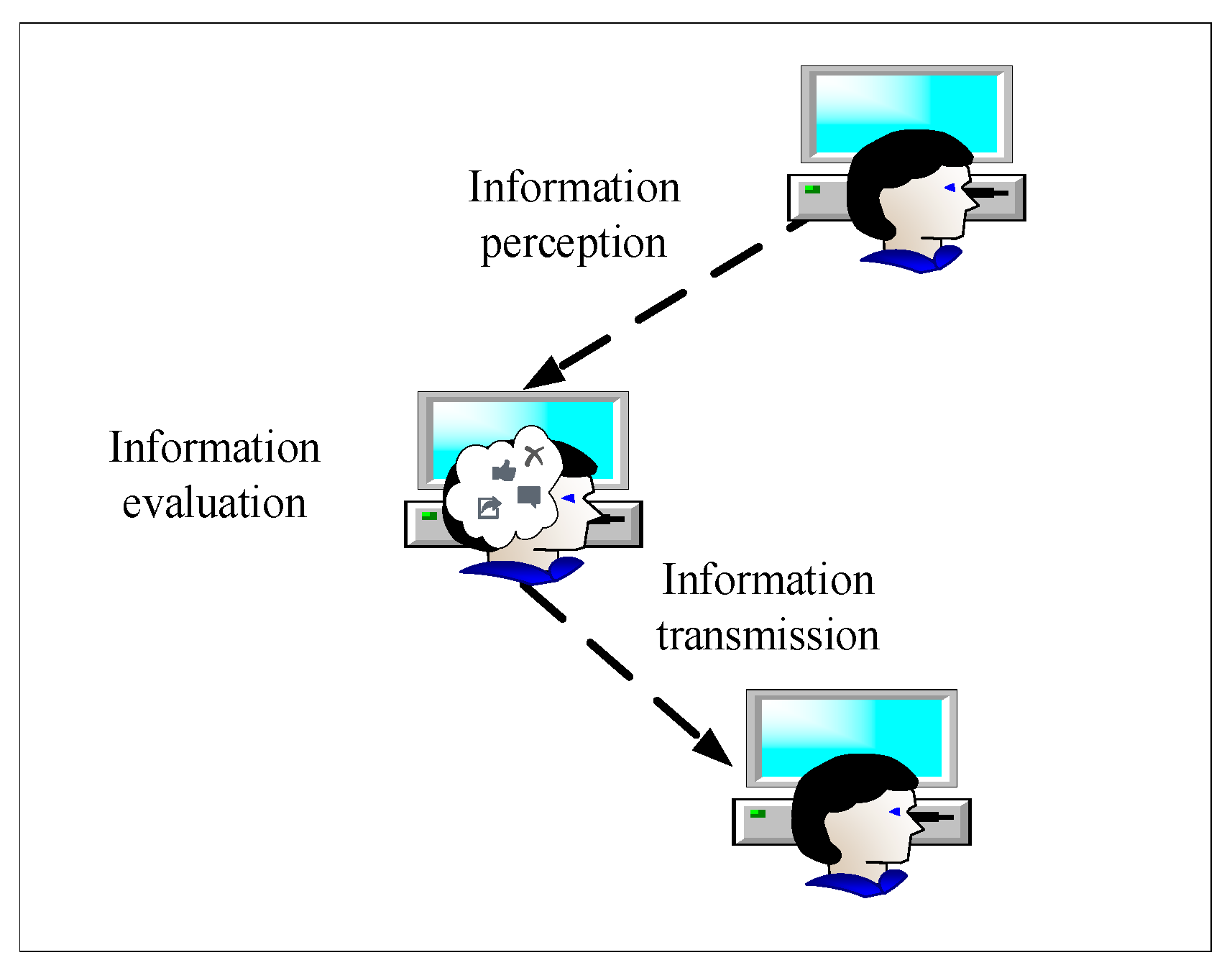
After in-depth analysis of the information diffusion process from one node to another on OSNs, we divide the process into three parts, as shown in Figure 3.
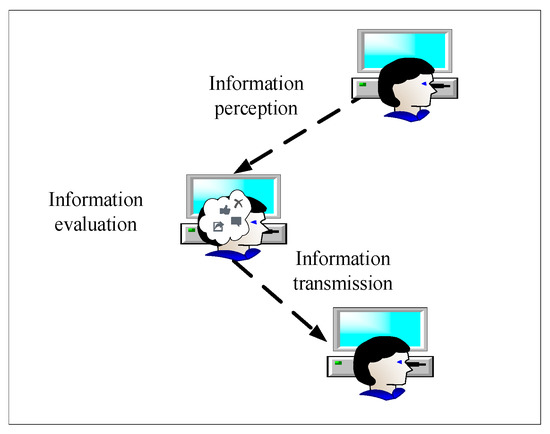
Figure 3.
The process of information diffusion consists of three parts: information perception, information evaluation, and information transmission.
Information perception explains how each node on the OSNs receives information. Individuals can receive a wide variety of information released by neighbors. The individual will decide whether to receive based on the closeness of the relationship between the sender and the receiver.
Information evaluation formulates how the node evaluates the information. The individual chooses his own state (such as knowing, like, comment, forwarding, etc.) based on the evaluation result and the state of neighbors. After the individual is activated, the state may continue to change over time.
Information transmission defines how the information received by each node is transmitted to other nodes. This part defines the transmission rules of information. We assume that the higher attractiveness of the information, the larger probability of forwarding by individuals.
In the following, we describe in detail the specific definitions of these three components in our model. Before analyzing in-depth the information diffusion process on OSNs, we were inspired by the explosion shock wave model in physics. The process of information diffusion is similar to the explosion of an information bomb. The influence of the information spreads outward from the source and decays with the propagation distance. The influence of the information is initially large, and then gradually decreases after the individual is affected. Similarly, the peak of the shock wave overpressure decays with distance, and the overpressure at a certain point in space decays with time.
In this case, the value of information represents the equivalent of explosive . The greater the value of the information, the stronger the influence will be. The length of time under positive pressure indicates the forgetting time of an individual. The decay coefficient represents the degree of aversion to information.
Since distance is proportional to time, , we assume . According to Formulas (1) and (2), we define the value of information influence received by an individual as follows:
represents the maximum influence of information on node and is the time point when the node is activated. represents the influence of information on node at time ; is the characteristic of node and represents the degree of aversion to the information.
The positive pressure action time represents the length of time that the individual is affected. The individual’s attention to information is related to the individual’s forget speed, so we define it as follows, represents the feature of node :
In the information perception part of our proposed model, individuals will trust people who are closely related to them, considering the effects of social communication; the higher the degree of trust, the larger the probability of acceptance. The community is a way to distinguish the degree of closeness, and the internal nodes of the community are close. Previous studies [35] have proved that the more common neighbors between two nodes, the higher the probability that they will exist in the same community. Therefore, the probability that the node accepts the information sent by the neighbor node is defined as:
where indicates the accept probability, represents the degree of node , and represents the number of common neighbors about node and node .
In the information evaluation part, individuals evaluate the information and update their status based on the evaluation. Due to the different background knowledge and the time of receiving, the evaluations of information will be different. In addition, affected by the herd mentality, individuals tend to maintain the same state with their neighbors, especially those living in the same community. In this work, we define the information evaluation function as follows:
where represents the evaluation value of the received information by node at time and represents the neighbors of node . According to the behavior of the users on OSNs, the result of information evaluation can also indicate the state of the node. The higher the evaluation result, the more active the node will be.
Since personal interest in information declines over time and individuals tend to share fresh and higher value information, in the last stage of the process we define the probability of individuals sending information to neighbors as:
where specifies the probability of node sending information to node .
3.2. Information Diffusion Process
According to the analysis and formulas above, we can employ our model to simulate the process of information diffusion. At the beginning, we randomly assign a different state to each seed node. According to , each time when a node accepts information, it has a single chance to transmit the information to its inactive neighbors. In the process, if a node decides to accept the information according to the probability of , it will be a spreader, and simultaneously, its state is updated. Any node has a single chance to spread a piece of accepted information. When the spreader’s attraction to the information fades away, it then becomes stifled. Finally, when the information popularity fades to , the diffusion process ends:
where indicates the accumulative influence of all the individuals considering their authority and is the connection degree of the node . The information popularity is a metric, which illustrates the evolution of the diffusion in view of the impact of each user. Algorithm 1 summarizes our proposed model.
| Algorithm 1 Information diffusion based on IDBESW model |
| Input: An OSN , initial state of all nodes , the Information value , the queue of seed nodes |
| Output: The state of all nodes at the end |
| 1: while do |
| 2: for do |
| 3: for do |
| 4: // sends information with , accepts with |
| 5: if is activated) |
| 6: // add in queue |
| 7: end if |
| 8: end for |
| 9: poll // remove from the queue |
| 10: end for |
| 11: update |
| 12: end while |
4. Experiments and Discussion
In this section, we conducted experiments to highlight the performance of the IDBESW model, and it is divided into two parts. The first part introduces the datasets used in the experiment and the evaluation measures, while the other part displays and analyzes the experimental results.
4.1. Experimental Setup
The datasets and the evaluation measures used in our experiments are introduced in this section.
4.1.1. Dataset Description
In order to evaluate the performance of the IDBESW model, we carried out different experiments using three real OSNs datasets. Table 1 illustrates the datasets used in the experiments. The second column indicates the common name of the dataset used. The third and fourth columns show the number of nodes and edges of the OSNs datasets used. As shown in the table, we use a different number of nodes and edges. The average degree column indicates the average degree of nodes in the OSN.

Table 1.
Dataset description.
4.1.2. Evaluation Measure
As we all know, one of the important characteristics of OSNs is the community structure [36]. Nodes in the same community are closely connected, interact frequently, and exchange information smoothly [37]. If the information diffusion model has a more realistic view of propagating information, it should have superior community detection accuracy [31]. Suppose that a person publishes a message on the OSN. As people in the same community have close relationships and higher levels of trust, they may tend to demonstrate a higher probability of receiving information after the propagating process. In this way, a message is given to different seed nodes randomly. Information is spread through the network according to the given information diffusion model. Each time a node accepts information from a neighbor node, the weight of the corresponding edge increases by one. When the process of information spread is over, we can obtain the weights of these edges. After that, these edges can be used to form a weighted network. This weighted network is used as the input of the community detection method. Note that the SLPA [38] algorithm is used for community detection in our experiments. If an information diffusion model can find better communities, then it would be a better information propagation model for OSNs.
In order to evaluate the communities obtained, we use modularity [31] to measure the accuracy of the communities found in the experiment. This measure is the most popular qualitative measure for detecting communities in social network analysis. The higher the modularity is, the finer the discovered communities are. The higher the degree of modularity of the community detection results, the more accurate the community division is. The more accurate the community division, the closer the diffusion process simulated by the model is to reality. The definition of modularity follows:
where is the found partition, refers to the number of communities, is the total number of edges in the social network; and are the number of edges and degrees in community according to , respectively.
4.1.3. Baseline Algorithms
We compare the performance of the proposed IDBESW model with several existing models as follows:
Independent Cascades Model (IC): This model is the most classic information diffusion model and is often used as a standard for research and comparison.
Genetic Algorithm Diffusion Model (GAD): This model is an information diffusion model based on the genetic algorithm. Individuals in the network transfer information through crossover operations.
Particle Swarm Optimization Model (PSO): This model maps the individual in the process of information diffusion to a particle, which continuously maximizes its own information value.
Multisource Information Perception Model (MSIP): This model assumes that besides obtaining information from neighbors, individuals can also gain information from the outside, such as radio, TV, etc.
4.2. Result and Discussion
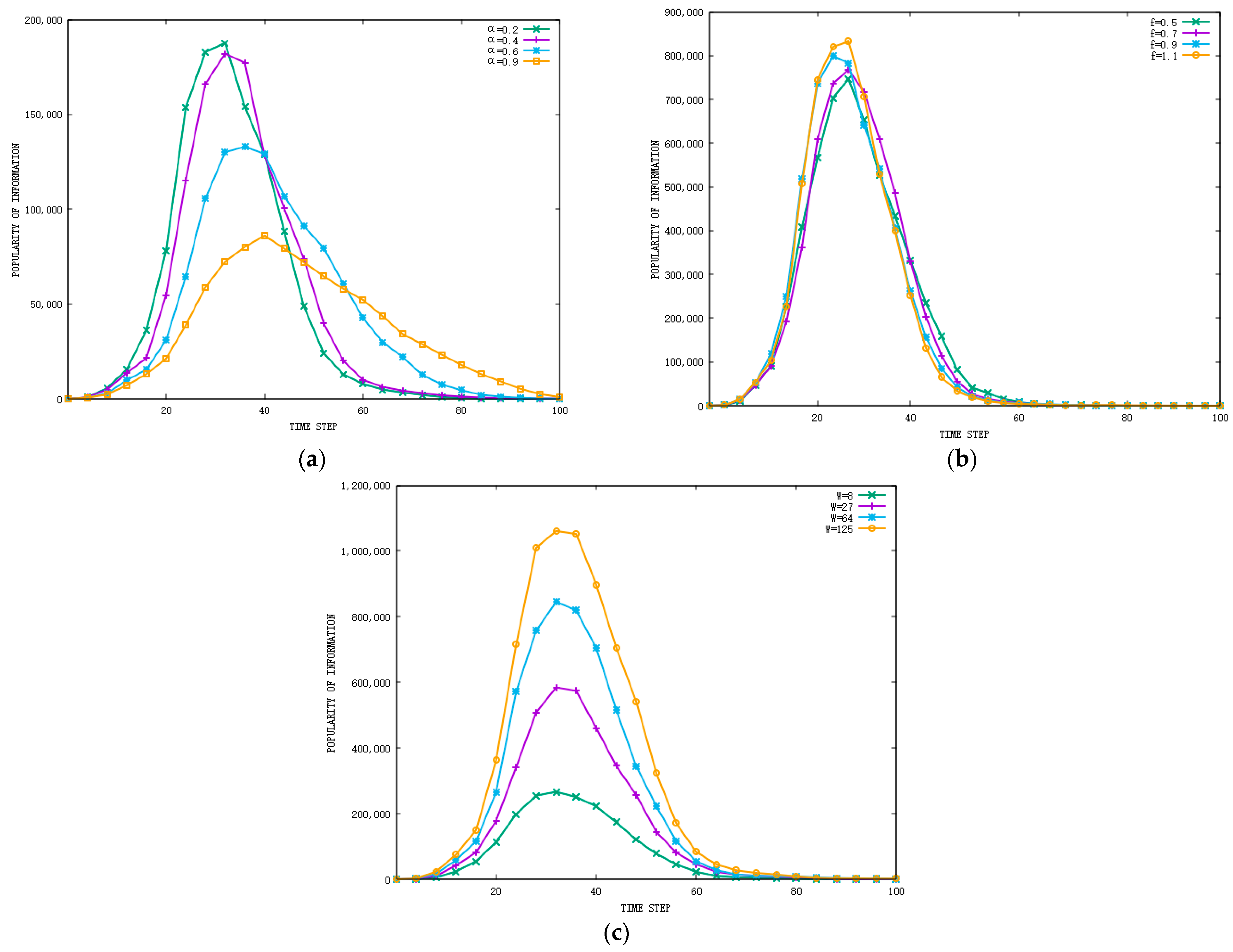
In the first experiment to assess the performance of the IDBESW model, the impacts of , , and on information diffusion in the Facebook network are illustrated through changing one while fixing the other two factors. The values of , , and are selected from the corresponding normal distribution. The variance of the normal distribution is set to 0.1, with different mean values set according to the studied interval. The results of these experiments are shown in Figure 4 and Figure 5, illuminating the impact of these factors on the popularity of the information and the rate of infected individuals. Note that for avoiding randomness in the results, we performed 100 simulations.
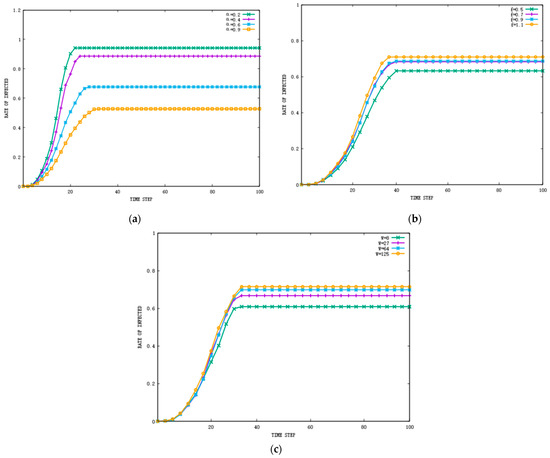
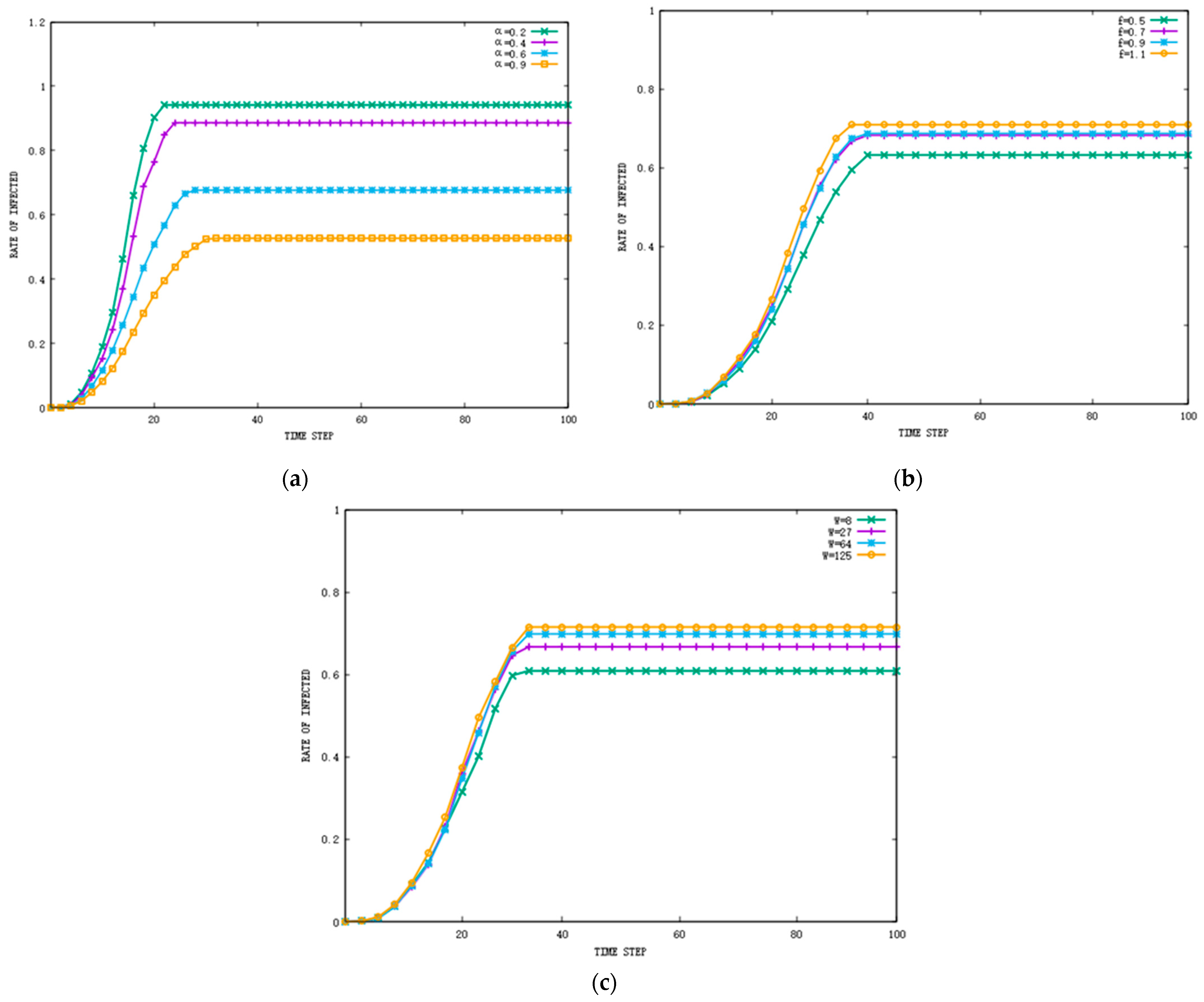
Figure 4.
The impact of individual features on the rate of infected individuals in the Facebook dataset: (a) the impact of on the rate of infected individuals, (b) the impact of on the rate of infected individuals, and (c) the impact of on the rate of infected individuals.
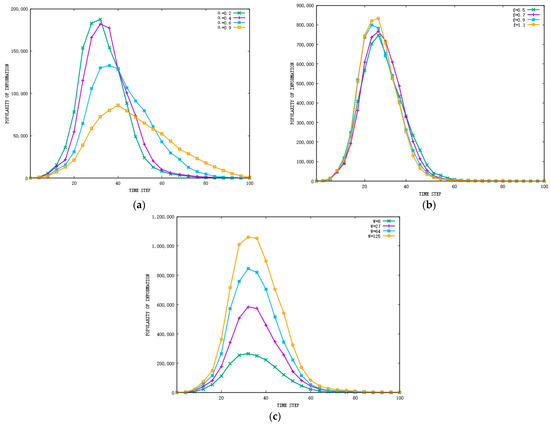
Figure 5.
The impact of individual features on the popularity of the information in the Facebook dataset: (a) the impact of on the popularity of the information, (b) the impact of on the popularity of the information, and (c) the impact of on the popularity of the information.
Overall, the results indicate that these factors have an important impact on the popularity of information and the rate of infected nodes. We found that has the greatest impact on the rate of infected nodes. The larger is, the greater the difference between the information and the individuals, and the fewer infected nodes there will be. Since the individual has the largest probability of sending information when he or she has just received it, when is small, the increase in has an obvious impact on the rate of infected nodes. When exceeds 0.7, the change in f has less impact on the result. Information of different values, , spreads at the same speed, but information with a high value of lasts for a long time, and the rate of infected nodes increases accordingly. From Figure 5, we can observe that has the greatest impact on the popularity of information. The higher the popularity of the information, the higher the activity of nodes on OSNs will be. Since affects the rate of infected nodes, it also has a significant impact on the popularity of information.
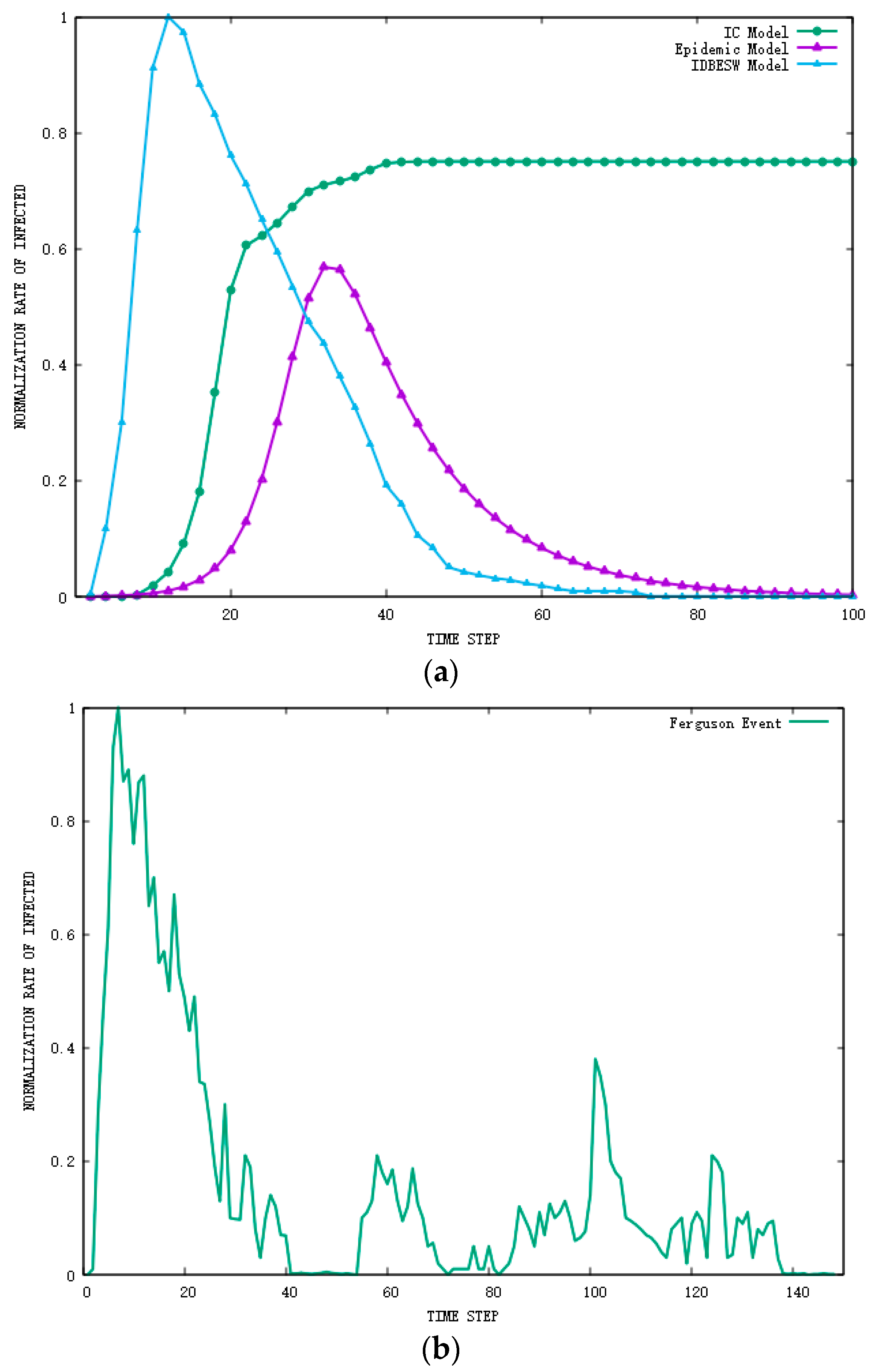
In order to explore the performance of the IDBESW model, the trends of information diffusion among the IDBESW, IC, and the Epidemic models are compared at a macro level. The classic SIR model is chosen as the baseline of the Epidemic model, and we set the model parameters according to [10]. For the IC model, we choose the model of [39], which is an improvement of the IC model that takes personal preferences into account. The results, shown in Figure 6a, indicate the evolution of propagator normalized density for the three models, which represents the trend of information dissemination. We demonstrate an actual event in Figure 6b, the Ferguson event on Twitter [40]. Through careful observation and comparison, the evolution of information diffusion usually reveals a pattern of rise and fall, with a rapid increase and a slight decrease. The experimental results show that the Epidemic model describes the two phases of growth and decline in the process. However, the rise and fall trend is basically the same in the two stages. Second, the IC model can only simulate the rising phase of the diffusion process because it assumes that once a person is activated, the state will remain unchanged. Finally, the model we proposed includes two stages of rapid growth and slow decline in diffusion. This information diffusion model is consistent not only with the diffusion trend described in the literature, but also with the real-world diffusion process, as shown in Figure 6. Therefore, our model would be the more truthfully model that describes the mode of information diffusion.
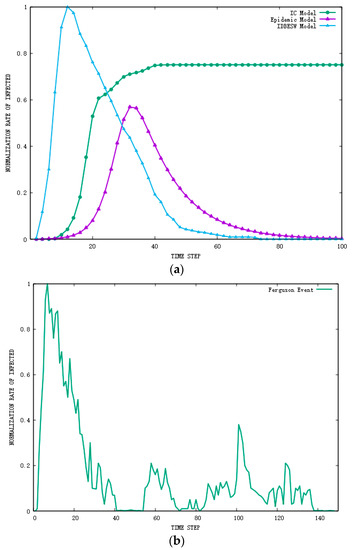
Figure 6.
Comparison of the IDBESW model with traditional models and real diffusion propagation. (a) Comparison between our model with the traditional model using the Twitter dataset. (b) Actual information propagation trends of the Ferguson event in the Twitter dataset.
In addition, we used modularity to evaluate the performance of the IDBESW model and other different models on three real datasets. Table 2 shows the comparison between our model and the other models. Each row in the table represents the modularity accuracy of different models under different datasets. In order to ensure the stability of the results, we simulate 100 times and put the average value as the final result.

Table 2.
Comparison of the proposed model with four rival models.
As shown in Table 2, the IDBESW model is superior to other models because it considers the common neighbor nodes. The more common the neighbors are, the closer the relationship between nodes, and the higher the probability of accepting information. The IC model is the weakest in terms of reflecting the community structure. The nodes activated by the IC model have only one chance to spread information, and the probability of information transfer among nodes is completely random. However, for the Epinions dataset, all the model results are worse than the results for the other two datasets. Through the analysis of the datasets, we found that, owing to the sparse network structure of the Epinions, the average node degree is only 6.71, while the average node degree in the Facebook and Twitter datasets is 43.7 and 43.5, respectively.
5. Conclusions
Online social networks are becoming increasingly more important in human life. It enables individuals to share information with others in a timely manner. In recent years, online social networking sites such as Twitter and Facebook have become very popular because they allow people to interact with friends, share information, and disseminate opinions regardless of time and space. A major feature of social networks is to spread information, such as news, rumors, and opinions, through connections between each other. The research on the process of information diffusion has always been a focus in the field of social network analysis, owing to its importance to society and people’s daily lives. Modeling the diffusion of information in the OSNs can make us understand the process of spreading. Although many models of information diffusion have been proposed, additional work needs to be performed to optimize this process.
In this paper, we are inspired by the explosion shock wave and propose an information diffusion model on OSNs. The value of information in the process of diffusion and the social behavior of individuals are taken into consideration. This new model also gains inspiration from the explosive shock wave, which allows each individual to have their own characteristics. Additionally, the effect of forget and the trust within neighbors are considered as well. In order to explore the advantages of our model, many experiments with different settings and specifications were carried out using different datasets. The results show that our model simulates information diffusion closer to the actual spread process on OSNs.
In the future, we would like to continue to conduct research on the analysis of the online social networks based on our current work. One potential expansion is to carry out influence maximization, in which this diffusion model is used to mine influential Top-k nodes. Another potential direction is to perform link prediction on online social networks based on information diffusion.
Author Contributions
Conceptualization, J.L.; formal analysis, J.L.; investigation, L.Z.; methodology, J.L.; project administration, K.L.; resources, K.L.; software, L.Z.; supervision, K.L.; writing—original draft, L.Z.; writing—review and editing, L.Z., K.L. and J.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the Beijing Natural Science Foundation, China (No. L181010, 4172054) and National Key R&D Program of China (No. 2016YFB0801100).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The dataset can be downloaded at http://snap.stanford.edu/data/, accessed on 6 January 2021.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Wang, F.; Wang, H.; Xu, K. Diffusive logistic model towards predicting information diffusion in online social networks. In Proceedings of the 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012; pp. 133–139. [Google Scholar]
- Rogers, E.M. Diffusion of Innovations, 4th ed.; Free Press: New York, NY, USA, 1995; p. 453. [Google Scholar]
- Li, K.; Zhang, L.; Huang, H. Social Influence Analysis: Models, Methods, and Evaluation. Engineering 2018, 4, 40–46. [Google Scholar] [CrossRef]
- Daley, D.J.; Kendall, D.G. Epidemics and Rumours. Nat. Cell Biol. 1964, 204, 1118. [Google Scholar] [CrossRef]
- Wang, Y.-Q.; Yang, X.-Y.; Han, Y.-L.; Wang, X.-A. Rumor Spreading Model with Trust Mechanism in Complex Social Networks. Commun. Theor. Phys. 2013, 59, 510–516. [Google Scholar] [CrossRef]
- Shi, H.; Duan, Z.; Chen, G. An SIS model with infective medium on complex networks. Phys. A Stat. Mech. Its Appl. 2008, 387, 2133–2144. [Google Scholar] [CrossRef]
- Xia, C.Y. Epidemics of SIRS model with non-uniform transmission on scale-free networks. Int. J. Mod. Phys. B 2009, 23, 2203–2213. [Google Scholar] [CrossRef]
- Biswas, M.H.A.; Paiva, L.T.; de Pinho, M. A SEIR model for control of infectious diseases with constraints. Math. Biosci. Eng. 2014, 11, 761–784. [Google Scholar] [CrossRef]
- Su, Q.; Huang, J.; Zhao, X. An information propagation model considering incomplete reading behavior in microblog. Phys. A Stat. Mech. Its Appl. 2015, 419, 55–63. [Google Scholar] [CrossRef]
- Zhao, L.; Wang, J.; Chen, Y.; Wang, Q.; Cheng, J.; Cui, H. SIHR rumor spreading model in social networks. Phys. A Stat. Mech. Its Appl. 2012, 391, 2444–2453. [Google Scholar] [CrossRef]
- Zhao, L.; Qiu, X.; Wang, X.; Wang, J. Rumor spreading model considering forgetting and remembering mechanisms in inhomogeneous networks. Phys. A 2013, 392, 987–994. [Google Scholar] [CrossRef]
- Wang, H.; Deng, L.; Xie, F.; Xu, H.; Han, J. A new rumor propagation model on SNS structure. In Proceedings of the 2012 IEEE International Conference on Granular Computing, Hangzhou, China, 11–13 August 2012; pp. 499–503. [Google Scholar]
- Xia, L.-L.; Jiang, G.-P.; Song, B.; Song, Y.-R. Rumor spreading model considering hesitating mechanism in complex social networks. Phys. A Stat. Mech. Its Appl. 2015, 437, 295–303. [Google Scholar] [CrossRef]
- He, D.; Liu, X. Novel competitive information propagation macro mathematical model in online social network. J. Comput. Sci. 2020, 41, 101089. [Google Scholar] [CrossRef]
- Kempe, D.; Kleinberg, J.; Tardos, E. Maximizing the spread of influence through a social network. In Proceedings of the Ninth ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, Washington, DC, USA, 24–27 August 2003; pp. 137–146. [Google Scholar]
- Kempe, D.; Kleinberg, J.; Tardos, E. Influential nodes in a diffusion model for social networks. In Proceedings of the 32nd International Conference on Automata, Languages and Programming, Lisbon, Portugal, 11–15 July 2005; pp. 1127–1138. [Google Scholar]
- Chen, W.; Lu, W.; Zhang, N. Time-critical influence maximization in social networks with time-delayed diffusion process. In Proceedings of the 26th AAAI Conference on Artificial Intelligence, Toronto, ON, Canada, 22–26 July 2012; pp. 592–598. [Google Scholar]
- Budak, C.; Agrawal, D.; Abbadi, A.E. Limiting the spread of misinformation in social networks. In Proceedings of the 20th International Conference on World Wide Web, Hyderabad, India, 28 March–1 April 2011; pp. 665–674. [Google Scholar]
- Mohammadi, A.; Saraee, M.; Mirzaei, A. Time-sensitive influence maximization in social networks. J. Inf. Sci. 2015, 41, 765–778. [Google Scholar] [CrossRef] [Green Version]
- Fan, L.; Lu, Z.; Wu, W.; Thuraisingham, B.; Ma, H.; Bi, Y. Least cost rumor blocking in social networks. In Proceedings of the 2013 IEEE 33rd Internationa Conference on Distributed Computing Systems, Philadelphia, PA, USA, 8–11 July 2013; pp. 540–549. [Google Scholar]
- Saito, K.; Ohara, K.; Yamagishi, Y.; Kimura, M.; Motoda, H. Learning diffusion probability based on node attributes in social networks. In Proceedings of the 19th International Conference on Foundations of Intelligent Systems, Warsaw, Poland, 28–30 June 2011; pp. 153–162. [Google Scholar]
- Guille, A.; Hacid, H. A predictive model for the temporal dynamics of information diffusion in online social networks. In Proceedings of the 21st International Conference on World Wide Web, Lyon, France, 16–20 April 2012; pp. 1145–1152. [Google Scholar]
- Mohamadi-Baghmolaei, R.; Mozafari, N.; Hamzeh, A. Trust based latency aware influence maximization in social networks. Eng. Appl. Artif. Intell. 2015, 41, 195–206. [Google Scholar] [CrossRef]
- Liu, W.; Yue, K.; Wu, H.; Li, J.; Liu, D.; Tang, D. Containment of competitive influence spread in social networks. Knowl. Based Syst. 2016, 109, 266–275. [Google Scholar] [CrossRef]
- Lee, W.; Kim, J.; Yu, H. CT-IC: Continuously activated and time-restricted independent cascade model for viral marketing. In Proceedings of the 2012 IEEE 12th International Conference on Data Mining, Brussels, Belgium, 10–13 December 2012; pp. 960–965. [Google Scholar]
- Jing, W.; Kan, L. Community structure exploration considering latent link patterns in complex networks. Neurocomputing 2021, 459, 10–22. [Google Scholar]
- Wang, Y.; Wang, H.; Li, J.; Gao, H. Efficient influence maximization in weighted independent cascade model. In Proceedings of the 21st International Conference on Database Systems for Advanced Applications, Dallas, TX, USA, 27–30 March 2016; pp. 49–64. [Google Scholar]
- Pathak, N.; Banerjee, A.; Srivastava, J. A generalized linear threshold model for multiple cascades. In Proceedings of the 2010 IEEE International Conference on Data Mining, Sydney, Australia, 13–17 December 2010; pp. 965–970. [Google Scholar]
- Cangfeng, D.; Kan, L. Topologically biased random walk for diffusions on multiplex networks. J. Comput. Sci. 2018, 28, 343–356. [Google Scholar]
- Lahiri, M.; Cebrian, M. The genetic algorithm as a general diffusion model for social networks. In Proceedings of the 24th Association for the Advancement of Artificial Intelligence Conference, Atlanta, GA, USA, 11–15 July 2010; pp. 494–499. [Google Scholar]
- Hajibagheri, A.; Hamzeh, A.; Sukthankar, G. Modeling information diffusion and community membership using stochastic optimization. In Proceedings of the IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining, Niagara, ON, Canada, 25–28 August 2013; pp. 175–182. [Google Scholar]
- Mozafari, N.; Hamzeh, A. An enriched social behavioural information diffusion model in social networks. J. Inf. Sci. 2015, 41, 273–283. [Google Scholar] [CrossRef]
- Al’Tshuler, L.V.; Trunin, R.F.; Krupnikov, K.K.; Panov, N.V. Explosive laboratory devices for shock wave compression studies. Physics-Uspekhi 1996, 39, 539. [Google Scholar] [CrossRef]
- Henrych, J. The Dynamics of Explosion and Its Use; Elsevier: Amsterdam, The Netherlands, 1979. [Google Scholar]
- Li, K.; Pang, Y. A unified community detection algorithm in complex network. Neurocomputing 2014, 130, 36–43. [Google Scholar] [CrossRef]
- Guidi, B.; Michienzi, A.; Rossetti, G. Towards the Dynamic Community Discovery in Decentralized Online Social Networks. J. Grid Comput. 2019, 17, 23–44. [Google Scholar]
- Guidi, B.; Michienzi, A.; De Salve, A. Community evaluation in Facebook groups. Multimed. Tools Appl. 2020, 79, 33603–33622. [Google Scholar] [CrossRef]
- Jierui, X.; Boleslaw, K.; Xiaoming, L. SLPA: Uncovering overlapping communities in social networks via a speaker–Listener interaction dynamic process. In Proceedings of the Data Mining Technologies for Computational Collective Intelligence Workshop at IEEE International Conference on Data Mining, Vancouver, BC, Canada, 11 December 2011; pp. 344–349. [Google Scholar]
- Wang, B.; Chen, G.; Fu, L.; Song, L.; Wang, X. DRIMUX: Dynamic Rumor Influence Minimization with User Experience in Social Networks. IEEE Trans. Knowl. Data Eng. 2017, 29, 2168–2181. [Google Scholar] [CrossRef]
- Hosni, A.; Li, K. Minimizing the influence of rumors during breaking news events in online social networks. Knowl. Based Syst. 2020, 193, 105452. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).