Practical Analysis of Sending or Not-Sending Twin-Field Quantum Key Distribution with Frequency Side Channels
Abstract
:1. Introduction
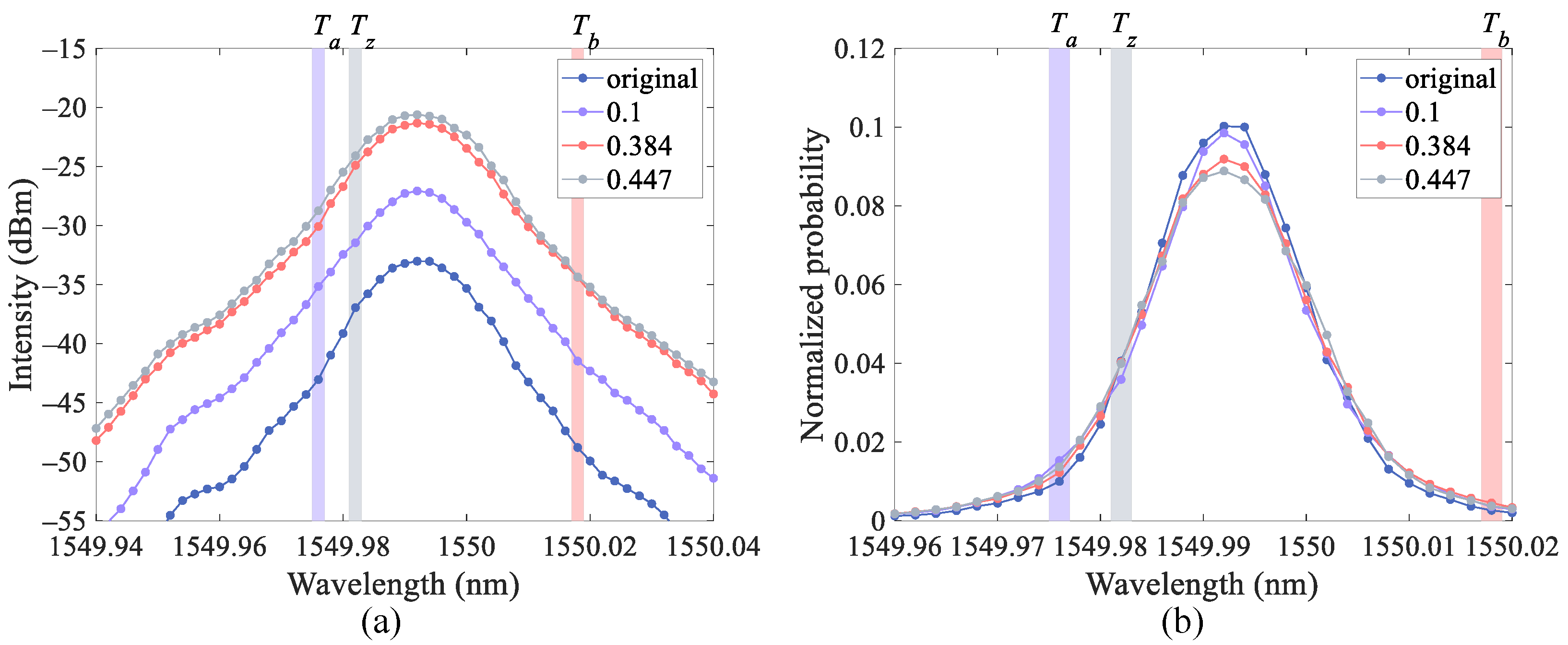
2. Frequency Shift of Intensity Modulators
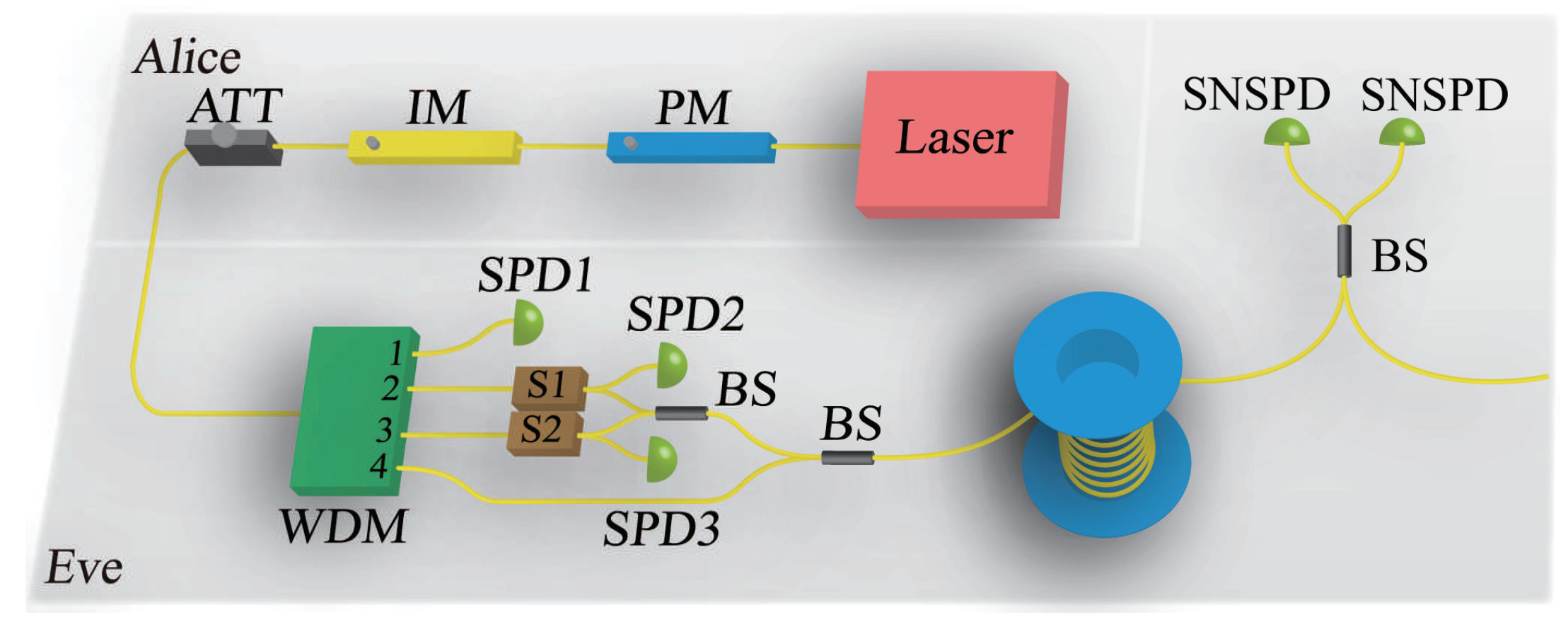
3. Passive Frequency-Shift Attack on Imperfect Implementation of SNS
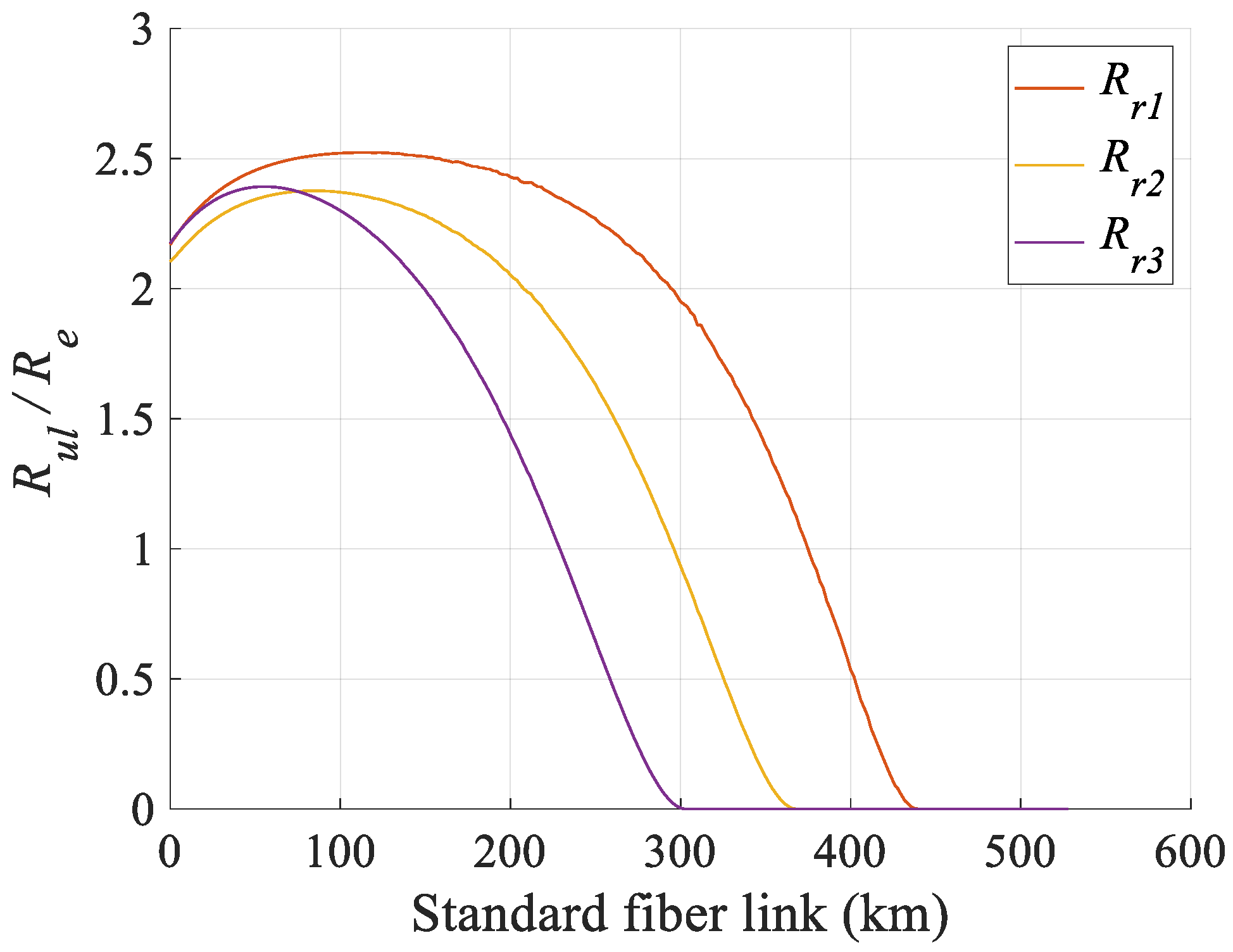
4. Numerical Simulations
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. SNS TF-QKD Protocol with AOPP
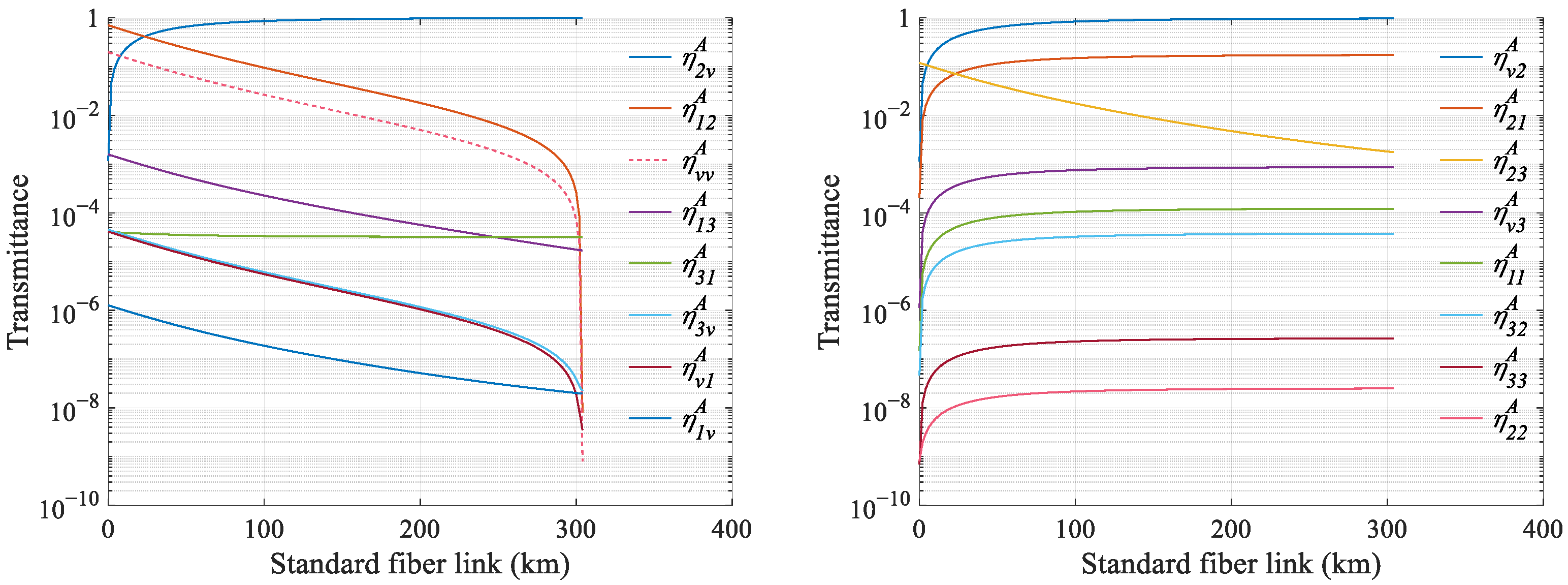
Appendix B. Details of Numerical Simulations
Appendix C. Details of Transmission


References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photon. 2020, 12, 1012–1236. [Google Scholar] [CrossRef] [Green Version]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hwang, W.Y. Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 2003, 91, 057901. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 2005, 94, 230503. [Google Scholar] [CrossRef] [Green Version]
- Takeoka, M.; Guha, S.; Wilde, M.M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 2014, 5, 5235. [Google Scholar] [CrossRef]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 15043. [Google Scholar] [CrossRef] [Green Version]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Zeng, P.; Zhou, H. Phase-Matching Quantum Key Distribution. Phys. Rev. X 2018, 8, 031043. [Google Scholar] [CrossRef] [Green Version]
- Curty, M.; Azuma, K.; Lo, H.K. Simple security proof of twin-field type quantum key distribution protocol. Npj Quant. Inf. 2019, 5, 64. [Google Scholar] [CrossRef]
- Cui, C.; Yin, Z.Q.; Wang, R.; Chen, W.; Wang, S.; Guo, G.C. Twin-Field Quantum Key Distribution without Phase Postselection. Phys. Rev. Appl. 2019, 11, 034053. [Google Scholar] [CrossRef] [Green Version]
- Yin, H.L.; Fu, Y. Measurement-Device-Independent Twin-Field Quantum Key Distribution. Sci. Rep. 2019, 9, 3045. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lin, J.; Lütkenhaus, N. Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 2018, 98, 042332. [Google Scholar] [CrossRef] [Green Version]
- Tamaki, K.; Lo, H.; Wang, W.; Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv 2018, arXiv:1805.05511v1. [Google Scholar]
- Jiang, C.; Yu, Z.W.; Hu, X.L.; Wang, X.B. Unconditional Security of Sending or Not Sending Twin-Field Quantum Key Distribution with Finite Pulses. Phys. Rev. Appl. 2019, 12, 024061. [Google Scholar] [CrossRef] [Green Version]
- Jiang, C.; Hu, X.L.; Xu, H.; Yu, Z.W.; Wang, X.B. Zigzag approach to higher key rate of sending-or-not-sending twin field quantum key distribution with finite-key effects. New J. Phys. 2020, 22, 053048. [Google Scholar] [CrossRef]
- Currás-Lorenzo, G.; Navarrete, Á.; Azuma, K.; Kato, G.; Curty, M.; Razavi, M. Tight finite-key security for twin-field quantum key distribution. Npj Quant. Inf. 2021, 7, 22. [Google Scholar] [CrossRef]
- Lu, F.Y.; Yin, Z.Q.; Wang, R.; Fan-Yuan, G.J.; Wang, S.; He, D.Y.; Chen, W.; Huang, W.; Xu, B.J.; Guo, G.C.; et al. Practical issues of twin-field quantum key distribution. New J. Phys. 2019, 21, 123030. [Google Scholar] [CrossRef] [Green Version]
- Hu, X.L.; Jiang, C.; Yu, Z.W.; Wang, X.B. Sending-or-not-sending twin-field protocol for quantum key distribution with asymmetric source parameters. Phys. Rev. A 2019, 100, 062337. [Google Scholar] [CrossRef] [Green Version]
- Zhou, X.Y.; Zhang, C.H.; Zhang, C.M.; Wang, Q. Asymmetric sending or not sending twin-field quantum key distribution in practice. Phys. Rev. A 2019, 99, 062316. [Google Scholar] [CrossRef] [Green Version]
- Wang, W.; Lo, H.K. Simple method for asymmetric twin-field quantum key distribution. New J. Phys. 2020, 22, 013020. [Google Scholar] [CrossRef]
- Currás-Lorenzo, G.; Wooltorton, L.; Razavi, M. Twin-Field Quantum Key Distribution with Fully Discrete Phase Randomization. Phys. Rev. Appl. 2021, 15, 014016. [Google Scholar] [CrossRef]
- Zhang, C.M.; Xu, Y.W.; Wang, R.; Wang, Q. Twin-Field Quantum Key Distribution with Discrete-Phase-Randomized Sources. Phys. Rev. Appl. 2020, 14, 064070. [Google Scholar] [CrossRef]
- Zeng, P.; Wu, W.; Ma, X. Symmetry-Protected Privacy: Beating the Rate-Distance Linear Bound Over a Noisy Channel. Phys. Rev. Appl. 2020, 13, 064013. [Google Scholar] [CrossRef]
- Wang, R.; Yin, Z.Q.; Lu, F.Y.; Wang, S.; Chen, W.; Zhang, C.M.; Huang, W.; Xu, B.J.; Guo, G.C.; Han, Z.F. Optimized protocol for twin-field quantum key distribution. Commun. Phys. 2020, 3, 149. [Google Scholar] [CrossRef]
- Xu, H.; Yu, Z.W.; Jiang, C.; Hu, X.L.; Wang, X.B. Sending-or-not-sending twin-field quantum key distribution: Breaking the direct transmission key rate. Phys. Rev. A 2020, 101, 042330. [Google Scholar] [CrossRef]
- Yu, Z.W.; Hu, X.L.; Jiang, C.; Xu, H.; Wang, X.B. Sending-or-not-sending twin-field quantum key distribution in practice. Sci. Rep. 2019, 9, 3080. [Google Scholar] [CrossRef] [Green Version]
- Grasselli, F.; Curty, M. Practical decoy-state method for twin-field quantum key distribution. New J. Phys. 2019, 21, 073001. [Google Scholar] [CrossRef] [Green Version]
- Minder, M.; Pittaluga, M.; Roberts, G.L.; Lucamarini, M.; Dynes, J.F.; Yuan, Z.L.; Shields, A.J. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photon. 2019, 13, 334–338. [Google Scholar] [CrossRef]
- Wang, S.; He, D.Y.; Yin, Z.Q.; Lu, F.Y.; Cui, C.H.; Chen, W.; Zhou, Z.; Guo, G.C.; Han, Z.F. Beating the Fundamental Rate-Distance Limit in a Proof-of-Principle Quantum Key Distribution System. Phys. Rev. X 2019, 9, 021046. [Google Scholar] [CrossRef] [Green Version]
- Zhong, X.; Hu, J.; Curty, M.; Qian, L.; Lo, H.K. Proof-of-Principle Experimental Demonstration of Twin-Field Type Quantum Key Distribution. Phys. Rev. Lett. 2019, 123, 100506. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.; Yu, Z.W.; Zhang, W.; Guan, J.Y.; Chen, J.P.; Zhang, C.; Hu, X.L.; Li, H.; Jiang, C.; Lin, J.; et al. Experimental Twin-Field Quantum Key Distribution through Sending or Not Sending. Phys. Rev. Lett. 2019, 123, 100505. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.L.; Guan, J.Y.; Yu, Z.W.; Xu, H.; Lin, J.; et al. Sending-or-Not-Sending with Independent Lasers: Secure Twin-Field Quantum Key Distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fang, X.T.; Zeng, P.; Liu, H.; Zou, M.; Wu, W.; Tang, Y.L.; Sheng, Y.J.; Xiang, Y.; Zhang, W.; Li, H.; et al. Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photon. 2020, 14, 422–425. [Google Scholar] [CrossRef]
- Liu, H.; Jiang, C.; Zhu, H.T.; Zou, M.; Yu, Z.; Hu, X.L.; Xu, H.; Ma, S.; Han, Z.; Chen, J.; et al. Field Test of Twin-Field Quantum Key Distribution through Sending-or-Not-Sending over 428 km. arXiv 2021, arXiv:2101.00276v1. [Google Scholar]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.J.; Han, Z.Y.; Ma, S.Z.; Hu, X.L.; Li, Y.H.; Liu, H.; et al. Twin-Field Quantum Key Distribution over 511 km Optical Fiber Linking two Distant Metropolitans. arXiv 2021, arXiv:2102.00433v1. [Google Scholar]
- Tang, Y.L.; Yin, H.L.; Ma, X.; Fung, C.H.F.; Liu, Y.; Yong, H.L.; Chen, T.Y.; Peng, C.Z.; Chen, Z.B.; Pan, J.W. Source attack of decoy-state quantum key distribution using phase information. Phys. Rev. A 2013, 88, 022308. [Google Scholar] [CrossRef] [Green Version]
- Tamaki, K.; Curty, M.; Lucamarini, M. Decoy-state quantum key distribution with a leaky source. New J. Phys. 2016, 18, 065008. [Google Scholar] [CrossRef]
- Huang, A.; Sun, S.H.; Liu, Z.; Makarov, V. Quantum key distribution with distinguishable decoy states. Phys. Rev. A 2018, 98, 012330. [Google Scholar] [CrossRef] [Green Version]
- Sajeed, S.; Radchenko, I.; Kaiser, S.; Bourgoin, J.P.; Pappa, A.; Monat, L.; Legré, M.; Makarov, V. Attacks exploiting deviation of mean photon number in quantum key distribution and coin tossing. Phys. Rev. A 2015, 91, 032326. [Google Scholar] [CrossRef] [Green Version]
- Vakhitov, A.; Makarov, V.; Hjelme, D.R. Large pulse attack as a method of conventional optical eavesdropping in quantum cryptography. J. Mod. Opt. 2001, 48, 2023–2038. [Google Scholar] [CrossRef]
- Gisin, N.; Fasel, S.; Kraus, B.; Zbinden, H.; Ribordy, G. Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 2006, 73, 022320. [Google Scholar] [CrossRef] [Green Version]
- Jain, N.; Anisimova, E.; Khan, I.; Makarov, V.; Marquardt, C.; Leuchs, G. Trojan-horse attacks threaten the security of practical quantum cryptography. New J. Phys. 2014, 16, 123030. [Google Scholar] [CrossRef] [Green Version]
- Lucamarini, M.; Choi, I.; Ward, M.B.; Dynes, J.F.; Yuan, Z.L.; Shields, A.J. Practical Security Bounds Against the Trojan-Horse Attack in Quantum Key Distribution. Phys. Rev. X 2015, 5, 031030. [Google Scholar] [CrossRef] [Green Version]
- Bugge, A.N.; Sauge, S.; Ghazali, A.M.M.; Skaar, J.; Lydersen, L.; Makarov, V. Laser Damage Helps the Eavesdropper in Quantum Cryptography. Phys. Rev. Lett. 2014, 112, 070503. [Google Scholar] [CrossRef] [Green Version]
- Sun, S.H.; Xu, F.; Jiang, M.S.; Ma, X.C.; Lo, H.K.; Liang, L.M. Effect of source tampering in the security of quantum cryptography. Phys. Rev. A 2015, 92, 022304. [Google Scholar] [CrossRef] [Green Version]
- Pang, X.L.; Yang, A.L.; Zhang, C.N.; Dou, J.P.; Li, H.; Gao, J.; Jin, X.M. Hacking Quantum Key Distribution via Injection Locking. Phys. Rev. Appl. 2020, 13, 034008. [Google Scholar] [CrossRef] [Green Version]
- Yin, H.L.; Liu, P.; Dai, W.W.; Ci, Z.H.; Gu, J.; Gao, T.; Wang, Q.W.; Shen, Z.Y. Experimental composable security decoy-state quantum key distribution using time-phase encoding. Opt. Express 2020, 28, 29479–29485. [Google Scholar] [CrossRef]
- Jiang, M.S.; Sun, S.H.; Li, C.Y.; Liang, L.M. Wavelength-selected photon-number-splitting attack against plug-and-play quantum key distribution systems with decoy states. Phys. Rev. A 2012, 86, 032310. [Google Scholar] [CrossRef] [Green Version]
- Jiang, M.S.; Sun, S.H.; Li, C.Y.; Liang, L.M. Frequency shift attack on ‘plug-and-play’ quantum key distribution systems. J. Mod. Opt. 2014, 61, 147–153. [Google Scholar] [CrossRef]
- Winzer, P.J.; Essiambre, R. Advanced Optical Modulation Formats. Proc. IEEE 2006, 94, 952–985. [Google Scholar] [CrossRef]
- Gottesman, D.; Lo, H.K.; Lütkenhaus, N.; Preskill, J. Security of quantum key distribution with imperfect devices. Quantum Inf. Comput. 2004, 4, 325–360. [Google Scholar]
- Inamori, H.; Lütkenhaus, N.; Mayers, D. Unconditional security of practical quantum key distribution. Eur. Phys. J. D 2007, 41, 599. [Google Scholar] [CrossRef]
- Zhang, W.; Kadosawa, Y.; Tomita, A.; Ogawa, K.; Okamoto, A. State preparation robust to modulation signal degradation by use of a dual parallel modulator for high-speed BB84 quantum key distribution systems. Opt. Express 2020, 28, 13965–13977. [Google Scholar] [CrossRef] [PubMed]
- Nakata, K.; Tomita, A.; Fujiwara, M.; Yoshino, K.I.; Tajima, A.; Okamoto, A.; Ogawa, K. Intensity fluctuation of a gain-switched semiconductor laser for quantum key distribution systems. Opt. Express 2017, 25, 622–634. [Google Scholar] [CrossRef] [PubMed]
- Tamaki, K.; Curty, M.; Kato, G.; Lo, H.K.; Azuma, K. Loss-tolerant quantum cryptography with imperfect sources. Phys. Rev. A 2014, 90, 052314. [Google Scholar] [CrossRef] [Green Version]
- Pereira, M.; Curty, M.; Tamaki, K. Quantum key distribution with flawed and leaky sources. Npj Quant. Inf. 2019, 5, 62. [Google Scholar] [CrossRef] [Green Version]
- Mizutani, A.; Sasaki, T.; Takeuchi, Y.; Tamaki, K.; Koashi, M. Quantum key distribution with simply characterized light sources. Npj Quant. Inf. 2019, 5, 87. [Google Scholar] [CrossRef] [Green Version]
- Navarrete, Á.; Pereira, M.; Curty, M.; Tamaki, K. Practical Quantum Key Distribution That is Secure Against Side Channels. Phys. Rev. Appl. 2021, 15, 034072. [Google Scholar] [CrossRef]
- Pereira, M.; Kato, G.; Mizutani, A.; Curty, M.; Tamaki, K. Quantum key distribution with correlated sources. Sci. Adv. 2020, 6, 4487. [Google Scholar] [CrossRef]
- Dynes, J.F.; Lucamarini, M.; Patel, K.A.; Sharpe, A.W.; Ward, M.B.; Yuan, Z.L.; Shields, A.J. Testing the photon-number statistics of a quantum key distribution light source. Opt. Express 2018, 26, 22733–22749. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wang, X.B.; Hu, X.L.; Yu, Z.W. Practical Long-Distance Side-Channel-Free Quantum Key Distribution. Phys. Rev. Appl. 2019, 12, 054034. [Google Scholar] [CrossRef] [Green Version]
- Yu, Z.W.; Zhou, Y.H.; Wang, X.B. Three-intensity decoy-state method for measurement-device-independent quantum key distribution. Phys. Rev. A 2013, 88, 062339. [Google Scholar] [CrossRef] [Green Version]
- Tomamichel, M.; Lim, C.C.W.; Gisin, N.; Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun. 2012, 3, 634. [Google Scholar] [CrossRef]
- Chernoff, H. A Measure of Asymptotic Efficiency for Tests of a Hypothesis Based on the sum of Observations. Ann. Math. Stat. 1952, 23, 493–507. [Google Scholar] [CrossRef]
- Curty, M.; Xu, F.; Cui, W.; Lim, C.C.; Tamaki, K.; Lo, H.K. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 2014, 5, 3732. [Google Scholar] [CrossRef] [Green Version]



| M | N | ||||||
|---|---|---|---|---|---|---|---|
| 0.2 | 56% | 0.1 | 1.1 | 16 |
| 0.1 | 0.384 | 0.447 | 0.776 | 0.85 | 0.073 | 0.732 |
| Width | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 1 ns | 3.996 | 1.367 | 0.376 | 3.592 | 1.531 | 0.357 | 4.033 | 1.225 | 0.454 |
| 2 | 300 ps | 2.071 | 6.910 | 2.071 | 1.325 | 8.563 | 1.325 | 1.958 | 6.994 | 1.958 |
| 3 | 100 ps | 1.791 | 6.028 | 1.616 | 0.963 | 8.544 | 0.911 | 1.522 | 6.420 | 1.618 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, Y.-F.; Jiang, M.-S.; Wang, Y.; Zhang, X.-X.; Liu, F.; Zhou, C.; Li, H.-W.; Tang, S.-B.; Wang, J.-Y.; Bao, W.-S. Practical Analysis of Sending or Not-Sending Twin-Field Quantum Key Distribution with Frequency Side Channels. Appl. Sci. 2021, 11, 9560. https://doi.org/10.3390/app11209560
Lu Y-F, Jiang M-S, Wang Y, Zhang X-X, Liu F, Zhou C, Li H-W, Tang S-B, Wang J-Y, Bao W-S. Practical Analysis of Sending or Not-Sending Twin-Field Quantum Key Distribution with Frequency Side Channels. Applied Sciences. 2021; 11(20):9560. https://doi.org/10.3390/app11209560
Chicago/Turabian StyleLu, Yi-Fei, Mu-Sheng Jiang, Yang Wang, Xiao-Xu Zhang, Fan Liu, Chun Zhou, Hong-Wei Li, Shi-Biao Tang, Jia-Yong Wang, and Wan-Su Bao. 2021. "Practical Analysis of Sending or Not-Sending Twin-Field Quantum Key Distribution with Frequency Side Channels" Applied Sciences 11, no. 20: 9560. https://doi.org/10.3390/app11209560
APA StyleLu, Y.-F., Jiang, M.-S., Wang, Y., Zhang, X.-X., Liu, F., Zhou, C., Li, H.-W., Tang, S.-B., Wang, J.-Y., & Bao, W.-S. (2021). Practical Analysis of Sending or Not-Sending Twin-Field Quantum Key Distribution with Frequency Side Channels. Applied Sciences, 11(20), 9560. https://doi.org/10.3390/app11209560






