Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain
Abstract
:Featured Application
Abstract
1. Introduction
- methodological level: conception, specification and implementation of an on-chain/off-chain load-balancing solution, thus making it possible for the intimately constrained computing, storage and software resources of any Blockchain to be abstractly extended by general-purpose computing machine resources;
- experimental level: specifying an experimental testbed and carrying out the underlying experiments for achieving the proof-of-concepts for complex Blockchain application execution (namely visual fingerprinting) on lightweight computing resources (namely, a multiprocessor ARM embedded platform, integrated into a Raspberry Pi);
- applicative level: the methodological framework developed in this study makes it possible for a Blockchain of an arbitrarily large number of nodes to be deployed over any combination of computing resources, from cloud servers and PCs to Raspberry Pi; in this way, even low resource devices (Raspberry Pi) can host up to nine nodes executing complex applications (namely visual fingerprinting).
2. State-of-the-Art
2.1. Blockchain at a Glance
2.2. Video Fingerprinting Basic Concepts
2.3. Multimedia Multiprocessor Embedded Architecture
3. The Advanced Solution: On-Chain/Off-Chain Load Balancing
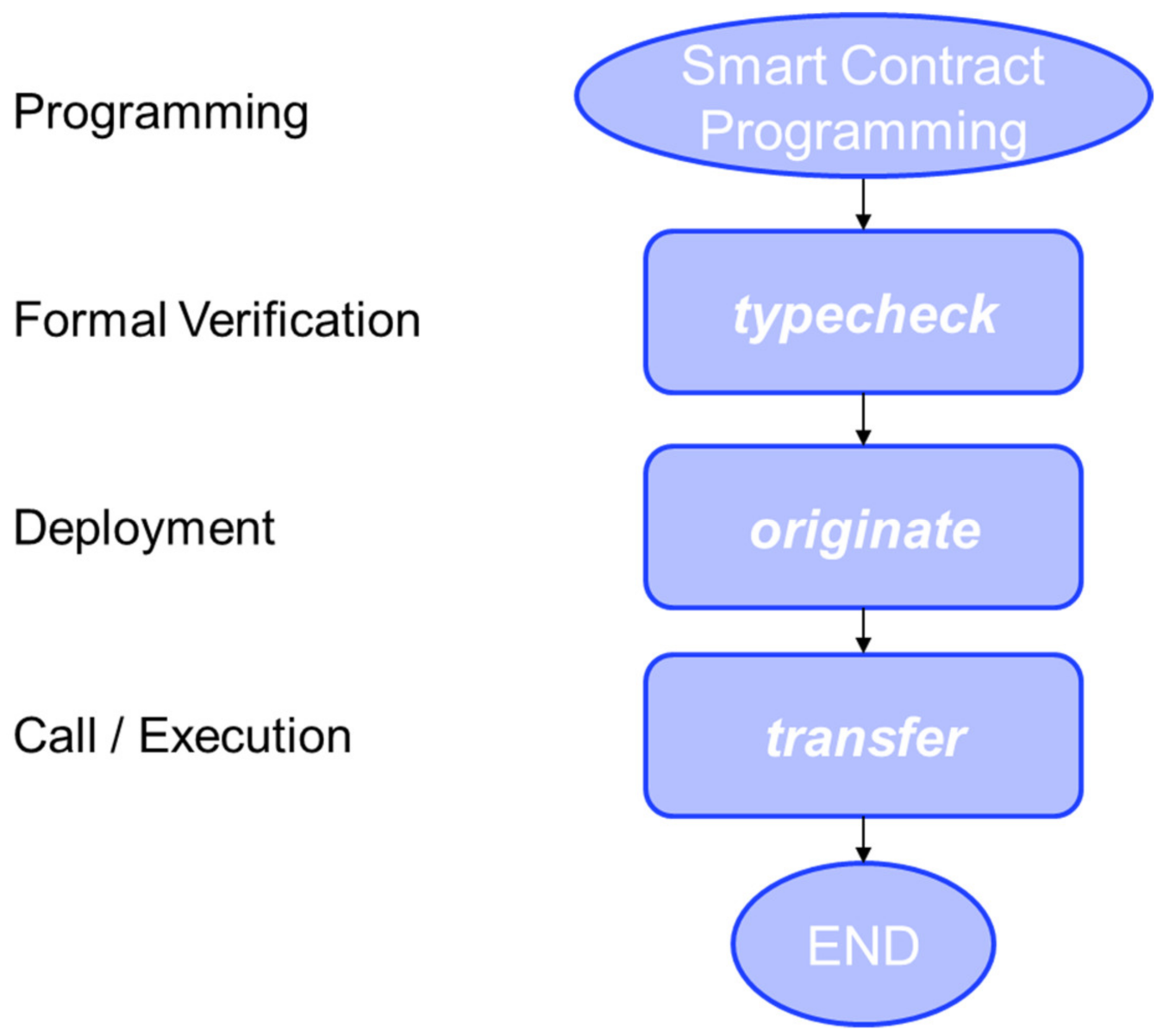
3.1. Conventional Smart Contract Workflow
- The Programming step writes a Michelson program that converts a logical contract (if … then series) into a Tezos script.
- The Formal Verification step executes the Tezos command “typecheck script” (with the proper parameters); this command does not apply any action on the Blockchain, yet its output informs the developer about the Smart contract correctness.
- The Deployment step executes the Tezos command “originate” with the proper parameters (Smart contract name, owner, transaction cost, ...). The Smart contract is added to the new block (the Smart contract keys are generated) and is ready to be invoked.
- The Call/Execute step executes the Tezos command “transfer” with its parameters (Smart contract ID, Smart contract monetizing conditions, Smart contract parameters, …); the action is added to the Blockchain, the Smart contract is executed, and the results are stored in the Blockchain.
3.2. New Smart Contract Workflow of On-Chain/Off-Chain Balancing
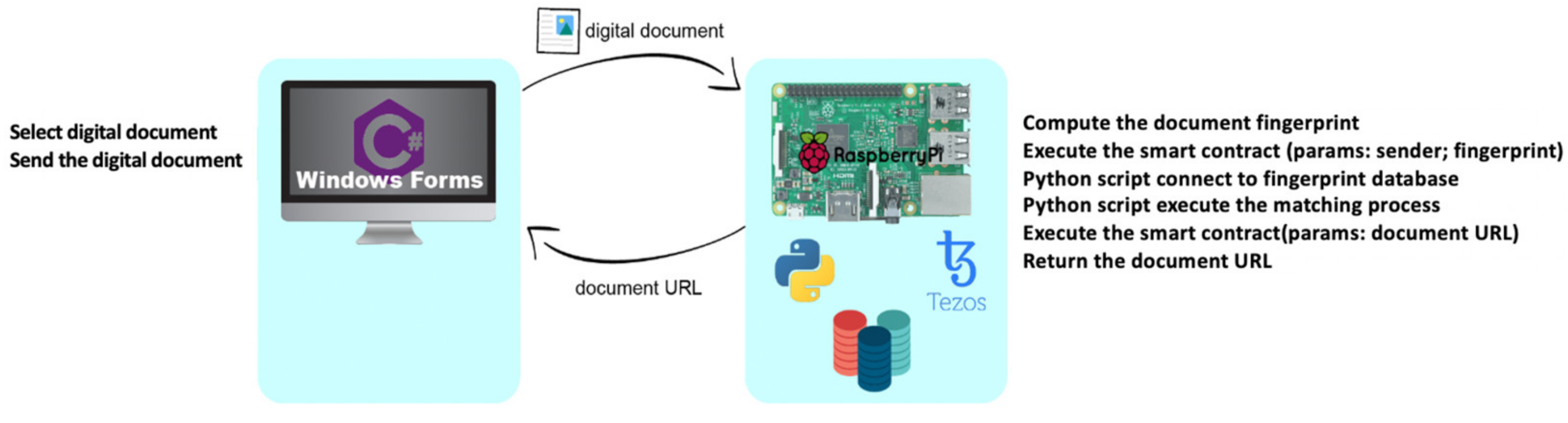
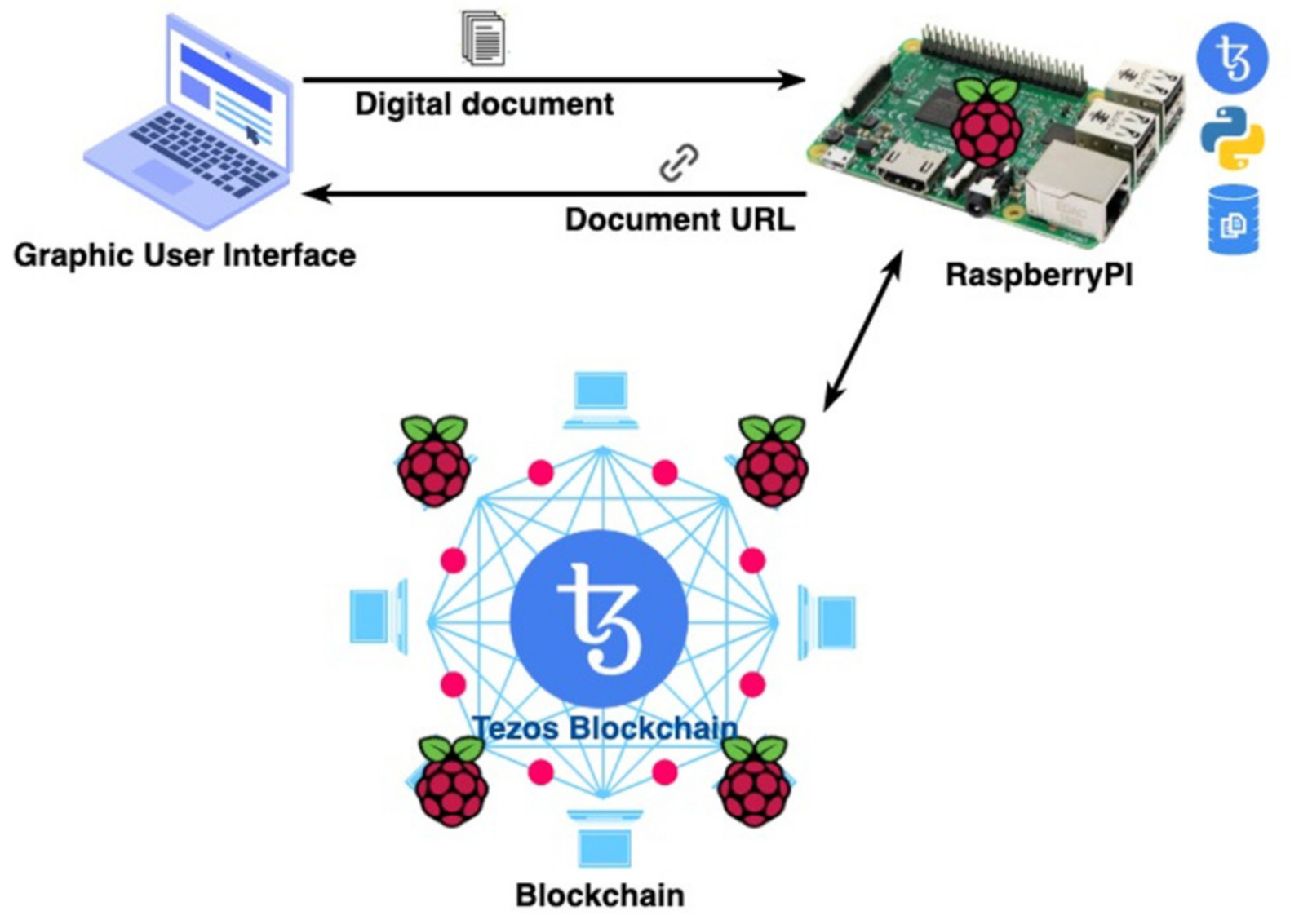
4. Experimental Set-Up
4.1. Hardware/Software Experimental Platform
4.2. On-Chain/Off-Chain Load Balancing Code
4.3. Fingerprinting Method and Database
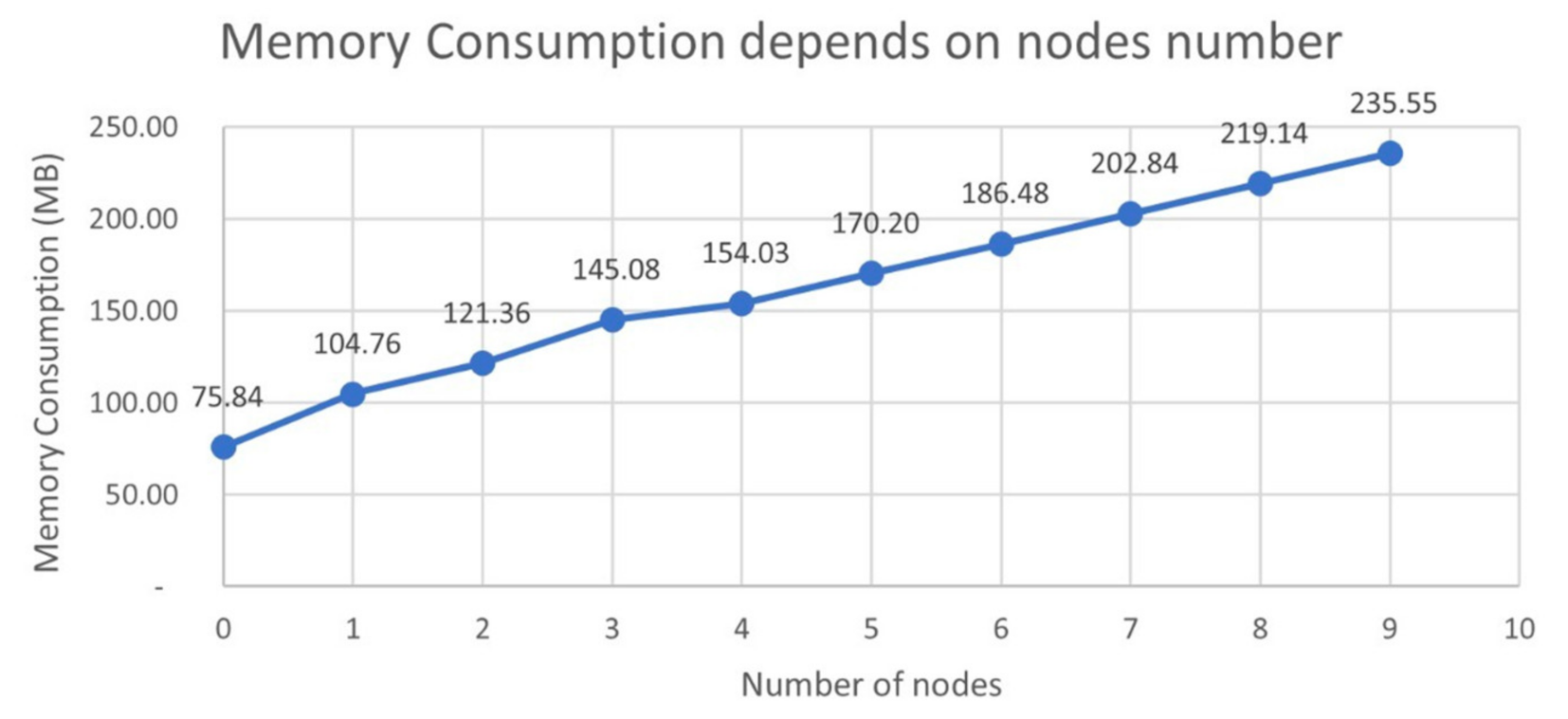
5. Experimental Results
6. Discussion
- the Smart contract code is slightly modified so as to cope with the new applicative logic (yet the functions related to the on-chain/off-chain balancing are unchanged);
- the Secure REST Connector is not expected to suffer any modification;
- of course, the off-chain code will be completely changed so as to correspond to the new application.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Nakamoto, S. Bitcoin Open-Source Implementation of P2P Currency; P2P Foundation: Amsterdam, The Netherlands, 2009. [Google Scholar]
- Available online: www.powercompare.co.uk/bitcoin/ (accessed on 10 May 2021).
- Silva, T.B.; Morais, E.S.; Almeida, L.F.F.; Rosa Righi, R.; Alberti, A.M. Blockchain and Industry 4.0: Overview, Convergence, and Analysis. In Blockchain Technology for Industry 4.0. Blockchain Technologies; Rosa Righi, R., Alberti, A., Singh, M., Eds.; Springer: Singapore, 2020. [Google Scholar]
- Issaoui, Y.; Khiat, A.; Bahnasse, A.; Ouajji, H. Smart logistics: Study of the application of Blockchain technology. Procedia Comput. Sci. 2019, 160, 266–271. [Google Scholar] [CrossRef]
- Torky, M.; Hassanein, A.E. Integrating Blockchain and the internet of things in precision agriculture: Analysis, opportunities, and challenges. Comput. Electron. Agric. 2020, 178, 105476. [Google Scholar] [CrossRef]
- Alonso, S.G.; Arambarri, J.; López-Coronado, M.; de la Torre Díez, I. Proposing New Blockchain Challenges in eHealth. J. Med. Syst. 2019, 43, 64. [Google Scholar] [CrossRef] [PubMed]
- Chen, Q.; Srivastava, G.; Parizi, R.M.; Aloqaily, M.; Al Ridhawi, I. An incentive-aware Blockchain-based solution for internet of fake media things. Inf. Process. Manag. 2020, 57, 102370. [Google Scholar] [CrossRef]
- Jiang, S.; Li, Y.; Lu, Q.; Hong, Y.; Dabo, G.; Xiong, Y.; Wang, S. Policy assessments for the carbon emission flows and sus-tainability of Bitcoin Blockchain operation in China. Nat. Commun. 2021, 12, 1938. [Google Scholar] [CrossRef]
- Garboan, A.; Mitrea, M. Live camera recording robust video fingerprinting. Multimed. Syst. 2016, 22, 229–243. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Mingxiao, D.; Xiaofeng, M.; Zhe, Z.; Xiangwei, W.; Qijun, C. A review on consensus algorithm of Blockchain. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 2567–2572. [Google Scholar] [CrossRef]
- Hellani, H.; Sliman, L.; Hassine, M.B.; Samhat, A.E.; Exposito, E.; Kmimech, M. Tangle the Blockchain: Toward IOTA and Blockchain Integration for IoT Environment. In Hybrid In-Telligent Systems. HIS 2019; Advances in Intelligent Systems and Computing; Abraham, A., Shandilya, S., Garcia-Hernandez, L., Varela, M., Eds.; Springer: Cham, Switzerland, 2021; Volume 1179. [Google Scholar] [CrossRef]
- Frikha, T.; Chaabane, F.; Aouinti, N.; Cheikhrouhou, O.; Ben Amor, N.; Kerrouche, A. Implementation of Blockchain Con-sensus Algorithm on Embedded Architecture. Secur. Commun. Netw. 2021, 2021, 9918697. [Google Scholar] [CrossRef]
- Frikha, T.; Chaari, A.; Chaabane, F.; Cheikhrouhou, O.; Zaguia, A. Healthcare and Fitness Data Management Using the IoT-Based Blockchain Platform. J. Healthc. Eng. 2021, 2021, 9978863. [Google Scholar] [CrossRef] [PubMed]
- Durand, A.; Hébert, G.; Toumi, K.; Memmi, G.; Anceaume, E. The StakeCube Blockchain: Instantiation. In Proceedings of the 2020 Second International Conference on Blockchain Computing and Applications (BCCA), Antalya, Turkey, 2–5 November 2020. [Google Scholar]
- Available online: https://entethalliance.org/wp-content/uploads/2018/05/EEA-Architecture-Stack-Spring-2018.pdf (accessed on 21 June 2021).
- Su, X.; Huang, T.; Gao, W. Robust video fingerprinting based on visual attention regions. In Proceedings of the 2009 IEEE International Conference on Acoustics, Speech and Signal Processing, Taipei, Taiwan, 19–24 April 2009; Volume 109, pp. 1525–1528. [Google Scholar] [CrossRef]
- Lee, S.; Yoo, C.D. Robust video fingerprinting for content-based video identification. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 938–988. [Google Scholar] [CrossRef] [Green Version]
- Douze, M.; Gaidon, A.; Jegou, H.; Marszałek, M.; Schmid, C. INRIA-LEAR’s Video Copy Detection System. TRECVID, 2008. Available online: https://hal.inria.fr/inria-00548664/ (accessed on 28 July 2021).
- Haji Rassouliha, A.; Taberner, A.J.; Nash, M.P.; Nielsen, P.M.F. Suitability of recent hardware accelerators (DSPs, FPGAs, and GPUs) for computer vision and image processing algorithms. Signal Process. Image Commun. 2018, 68, 101–119. [Google Scholar] [CrossRef]
- Available online: https://www.intel.com/content/www/us/en/programmable/products/fpga/features/stx-power-about.html (accessed on 12 May 2021).
- Zynq. Zynq Ultrascale+ mpsoc. 2018. Available online: https://www.xilinx.com/support/documentation/user_guides/ug1213-zynq-migration-guide.pdf (accessed on 7 July 2021).
- Irgens, P.; Bader, C.; Lé, T.; Saxena, D.; Ababei, C. An efficient and cost effective FPGA based implementation of the Viola-Jones face detection algorithm. HardwareX 2017, 1, 68–75. [Google Scholar] [CrossRef]
- Gao, F.; Huang, Z.; Wang, S.; Ji, X. Optimized parallel implementation of face detection based on embedded heterogeneous many-core architecture. Int. J. Pattern Recognit. Artif. Intell. 2017, 31, 1756011. [Google Scholar] [CrossRef]
- Zhao, X.; Liang, X.; Zhao, C.; Tang, M.; Wang, J. Real-Time Multi-Scale Face Detector on Embedded Devices. Sensors 2019, 19, 2158. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Raspberrypi. Raspberry Pi 3 Model b+. 2018. Available online: https://www.raspberrypi.org/products/raspberry-pi-4-model-b/ (accessed on 1 July 2021).
- Dolas, P.R.; Ghogare, P.; Kshirsagar, A.; Khadke, V.; Bokefode, S. Face Detection and Recognition Using Raspberry Pi. In Techno-Societal 2020; Pawar, P.M., Balasubramaniam, R., Ronge, B.P., Salunkhe, S.B., Vibhute, A.S., Melinamath, B., Eds.; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Laila, U.; Khan, M.A.; Shaikh, M.K.; bin Mazhar, S.A.; Mehboob, K. Comparative analysis for a real time face recognition system using Raspberry Pi. In Proceedings of the 2017 IEEE 4th International Conference on Smart Instrumentation, Measurement and Application (IC-SIMA), Putrajaya, Malaysia, 28–30 November 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Shah, A.A.; Zaidi, Z.A.; Chowdhry, B.S. Daudpoto Real time face detection/monitor using raspberry pi and MATLAB. In Proceedings of the 2016 IEEE 10th International Conference on Application of Information and Communication Technologies (AICT), Baku, Azerbaijan, 12–14 October 2016; pp. 1–4. [Google Scholar] [CrossRef]
- Tezos. Available online: https://Tezos.com/ (accessed on 11 May 2021).
- “What Is Tezos,” Blockgeeks. Available online: https://blockgeeks.com/guides/what-is-Tezos/ (accessed on 11 May 2021).
- Goodman, L. Tezos—A Self-Amending Crypto-Ledger White Paper. 2014. Available online: https://academy.bit2me.com/wp-content/uploads/2021/04/tezos-whitepaper.pdf (accessed on 28 July 2021).
- Investopedia. Available online: https://www.investopedia.com/terms/b/blockchain.asp (accessed on 19 December 2019).



| PC | Raspberry Pi 3 | |
|---|---|---|
| 1 | 7 ms | 264 ms |
| 10 | 42.2 ms | 320 ms |
| 50 | 69.1 ms | 637 ms |
| 100 | 103 ms | 960 ms |
| 500 | 375 ms | 3.65 s |
| 1000 | 704 ms | 6.92 s |
| 5000 | 3.41 s | ---- |
| 10,000 | 6.78 s | ---- |
| 11,557 | 7.77 s | ---- |
| PC | Raspberry Pi 3 | |
|---|---|---|
| Bake | 0.994 s | 2.216 s |
| Coin transfer | 1.261 s | 4.575 s |
| Typecheck | 0.505 s | 3.167 s |
| Deploy a Smart contract | 1.836 s | 7.263 s |
| PC | Raspberry Pi | |
|---|---|---|
| Time | 13.6 s | 23.7 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Allouche, M.; Frikha, T.; Mitrea, M.; Memmi, G.; Chaabane, F. Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain. Appl. Sci. 2021, 11, 7169. https://doi.org/10.3390/app11157169
Allouche M, Frikha T, Mitrea M, Memmi G, Chaabane F. Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain. Applied Sciences. 2021; 11(15):7169. https://doi.org/10.3390/app11157169
Chicago/Turabian StyleAllouche, Mohamed, Tarek Frikha, Mihai Mitrea, Gérard Memmi, and Faten Chaabane. 2021. "Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain" Applied Sciences 11, no. 15: 7169. https://doi.org/10.3390/app11157169
APA StyleAllouche, M., Frikha, T., Mitrea, M., Memmi, G., & Chaabane, F. (2021). Lightweight Blockchain Processing. Case Study: Scanned Document Tracking on Tezos Blockchain. Applied Sciences, 11(15), 7169. https://doi.org/10.3390/app11157169






