Packet Optical Transport Network Slicing with Hard and Soft Isolation
Abstract
:1. Introduction
2. Network Slicing Concepts
- The Service Instance (SI) is an end-user service or a business service realized in a Network Slice.
- The Network Slice Instance (NSI) as the complete, instantiated logical network that meets specific characteristics required by a Service instance.
2.1. Soft Network Slicing
- Virtual Routing and Forwarding (VRF), that enables multiple routing environments over a shared MPLS transport network.
- Virtual Interfaces (VSI), that enables multiple switching environments over the same shared infrastructure.
2.2. Hard Network Slicing
2.3. 5G Network Slicing
- Radio Access Network (RAN): It covers everything related to the air interface between the user element and the base station. The RAN interfaces and interconnections is specified within 3G PPP Architecture Working Group.
- Mobile Core (MC): Its central role is to act as a gateway for user traffic to and from the internet. The mobile core is composed of a set of network functions (NF) responsible for managing user mobility, access authentication, access authorization, location service management, registration and establish per-user tunnels between base stations for each different traffic type.
- Backhaul Network is the network that interconnects the RAN with the MC. It is not part of the 5G specification, so it is up to each network operator to decide how to implement it. It requires functionalities such as QoS management, synchronization and a stack of protocols like IP/MPLS or segment routing.
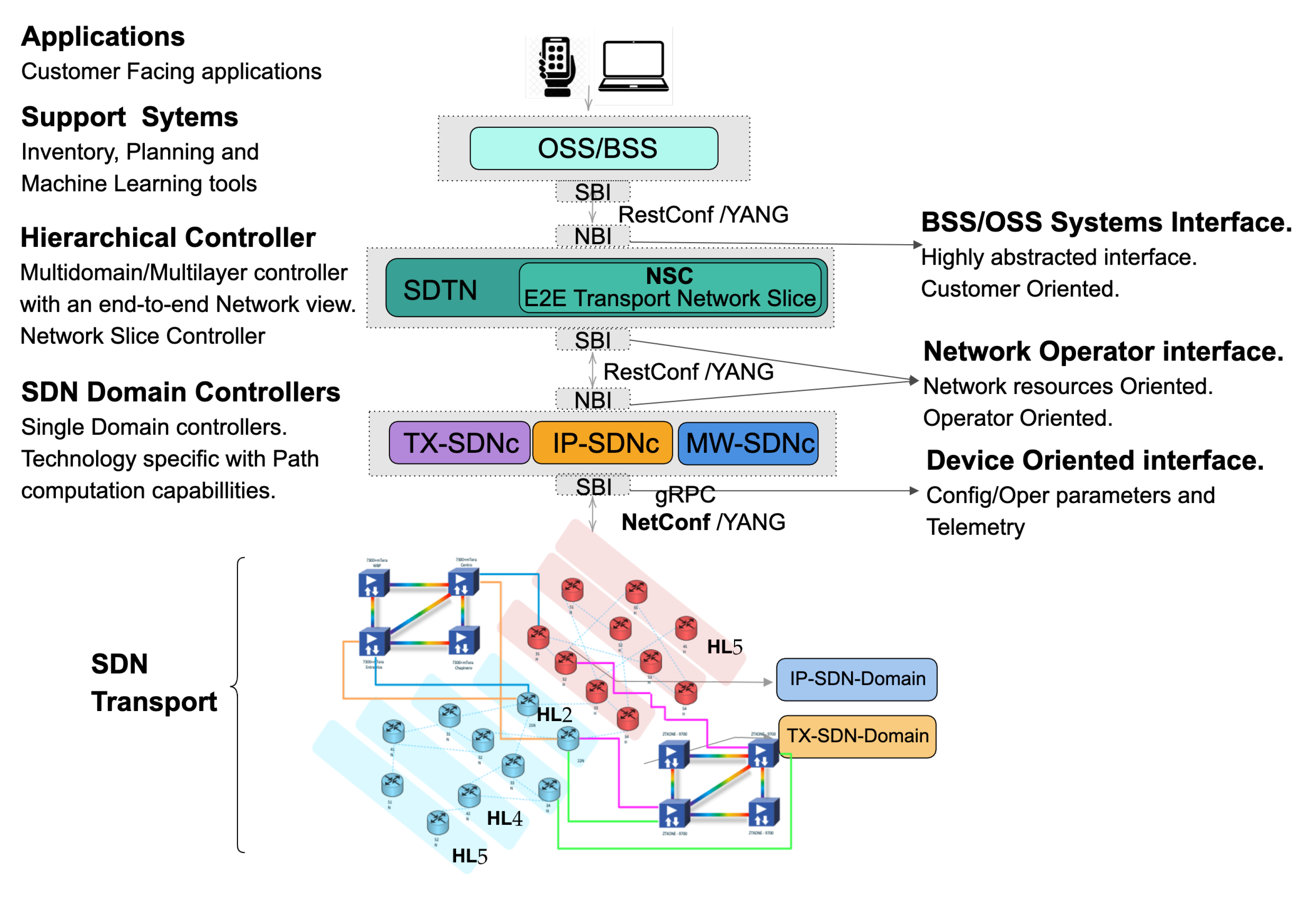
3. Proposed Architecture
3.1. Software Defined Transport Network Controller
3.2. Network Slice Controller
- Map: The NSC must map the Network Slice requests to the underlying technology-specific infrastructure. Accordingly, It maintains a record of the mapping from user requests to slice instantiations, as needed to allow for subsequent control functions like modification or deletion.
- Realize: The NSC should realize the network slice request using its SBI interface against the domain controllers in either physical or logical connectivity through VPNs or various tunnelling technologies such as Segment Routing, MPLS, etc.
3.3. Network Domain Controller
3.4. Yang Models for Network Controllers
3.5. Instantiating of Network Slices in SDN Transport Networks
- No-isolation, meaning that slices are not separated.
- Logical-isolation, where slices are logically separated, only a certain degree of isolation is performed through QoS mechanisms.
- Service-isolation, where virtual resources and NFs are shared.
- Process-isolation, where slices include process and threads isolation.
- Virtual-resource-isolation, where slices have dedicated virtual resources.
- Network-functions-isolation, where Network Function (NF) are dedicated to a single network slice.
- Physical-isolation, where slices are completely physically separated, for example, in different locations.
- Physical-network-isolation, where slices contain physically separated links.
- (a)
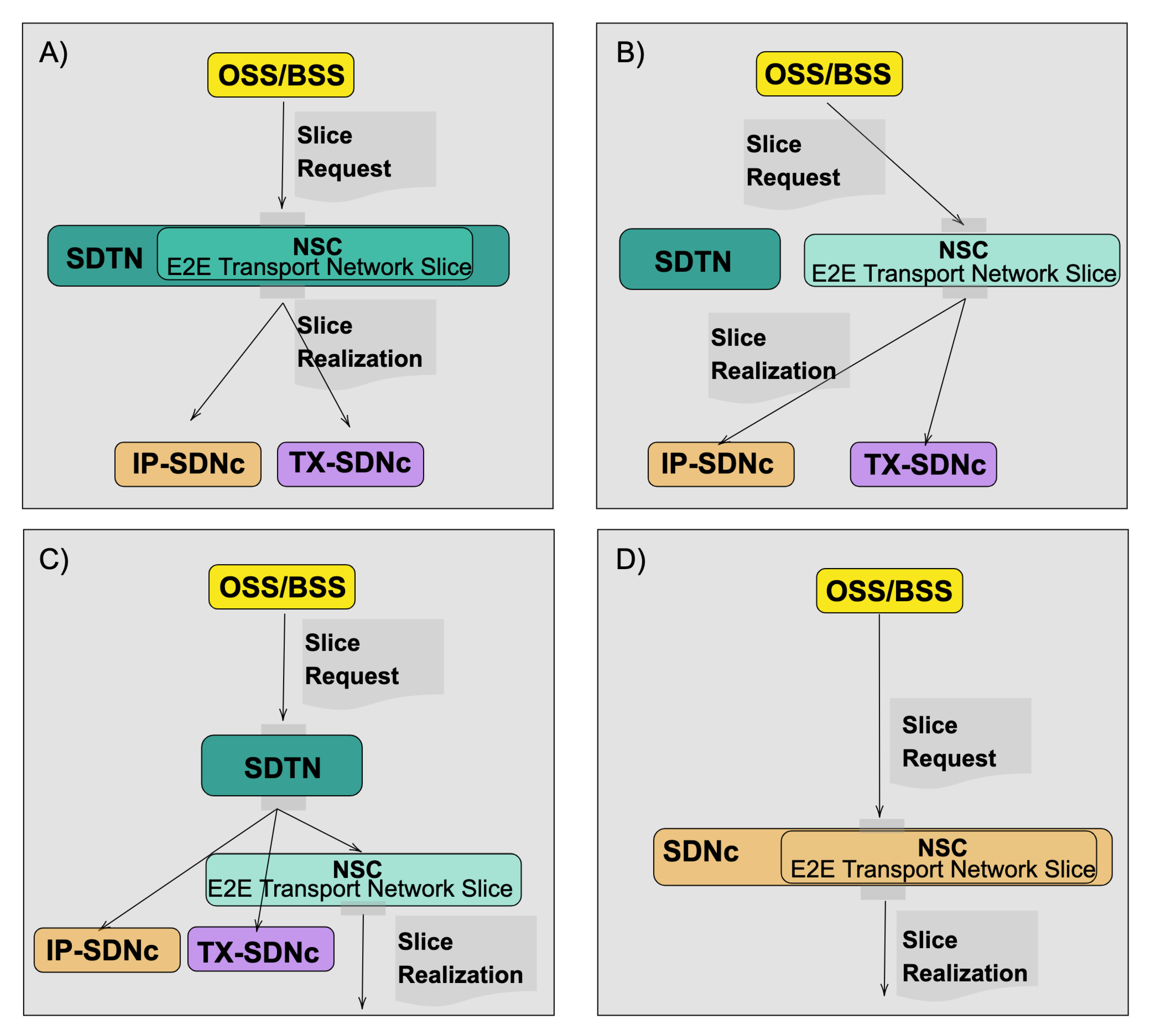
- Network Slice Controller as part of the hierarchical controller: When the Network Slice Controller is a Hierarchical SDN controller module, the NSC’s and the Hierarchical Network Controller should share the same internal data and the same NBI. Thus, to process the customer, view the H-SDN module must be able to:
- Map: The customer request received using the must be processed by the NCS. The mapping process takes the network-slice SLAs selected by the customer to available Routing Policies and Forwarding policies.
- Realize: Create necessary network requests. The slice’s realization can be translated into one or several LXNM Network requests, depending on the number of underlay controllers. Thus, the NCS must have a complete view of the network to map the orders and distribute them across domains. The realization should include the expansion/selection of Forwarding Policies, Routing Policies, VPN policies and Underlay transport preference.
To maintain the data coherence between the control layers, the network-slice-id used must be directly mapped to the transport-instance-id at the VPN-Node level. - (b)
- Network Slice Controller as an stand-alone controller:When the Network Slice Controller is a stand-alone controller module, the NSC’s should perform the same two tasks described before:
- Map: Process the customer request. The customer request can be sent using the [draft-liu-teas-transport-network-slice-yang-01]. This draft allows the topology mapping of the Slice request.
- Realize: Create necessary network requests. The slice’s realization will be translated into one LXNM Network request. As the NCS has a topological view of the network, the realization can include the customer’s traffic engineering transport preferences and policies.
- (c)
- Network Slice Controller at the domain controller level:The Network Slice Controller can at the same level as the network domain controllers. The SDTN controller should handle the slices request, and the realization can be done by the NSC directly communicating with the Network Elements. The SDTN controller should create unified network views, including each transport domain and the network slices.
- Map: The SDTN would Process the customer request. The customer request can be sent using the [draft-liu-teas-transport-network-slice-yang-01]. This draft allows the topology mapping of the Slice request.
- Realize: The realization can be done by the NCS controller applying the service logic to create policies directly on the Network elements. The SDTN should handle the shared resources management between domains.
- (d)
- Network Slice Controller as part of the domain controller:When the Network Slice Controller is part of the domain controller, the OSS/BSS systems process the Slices requests and introduce the network abstraction layer. At the network level, the same device data model would be used in the NBI and SBI of the SDN controller. The direct translation would reduce the service logic implemented at the SDN controller level, grouping the mapping and translation into a single task:
- Map & Realize:The mapping and realization can be done by the Domain controller applying the service logic to create policies directly on the Network elements.
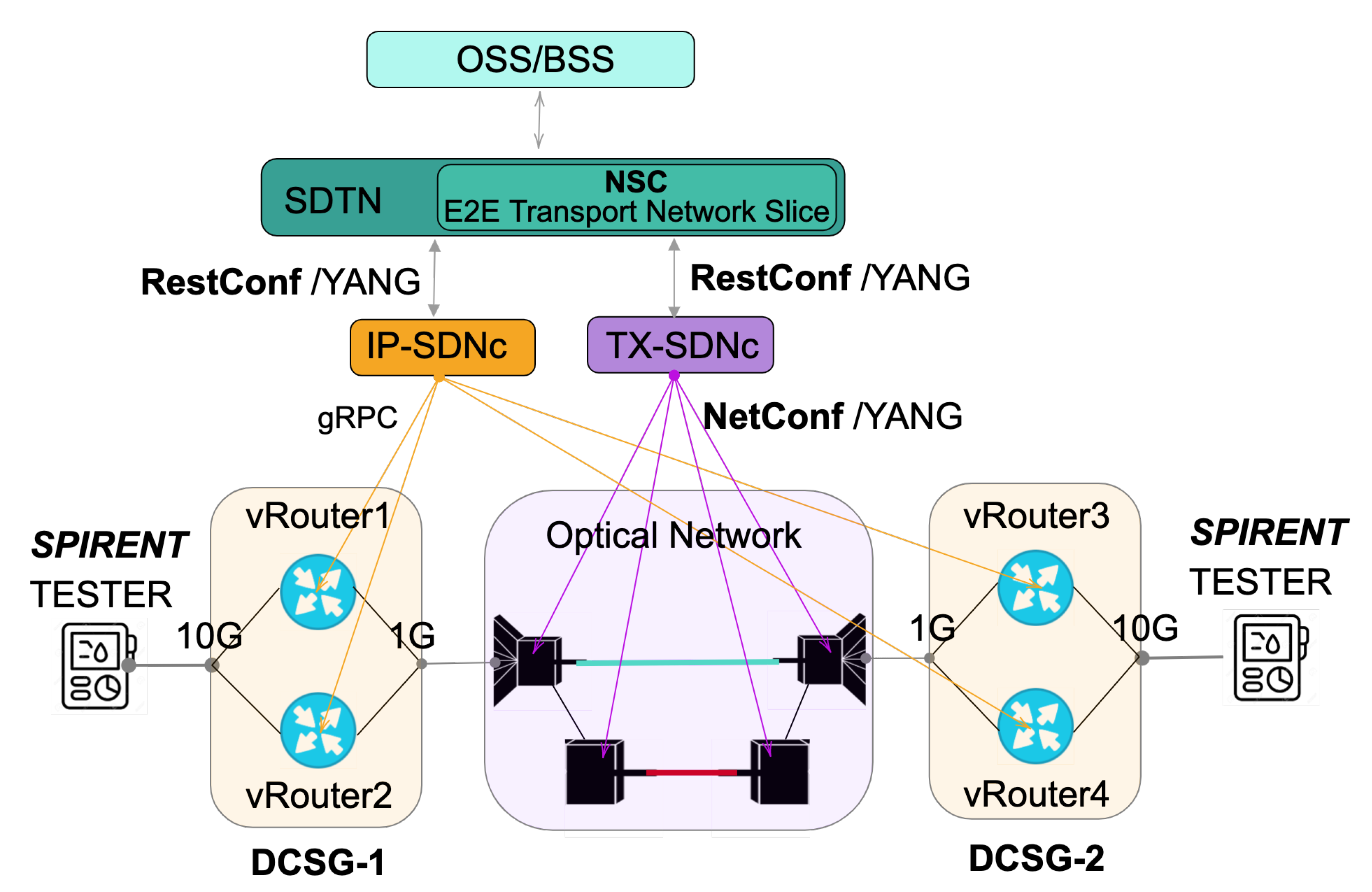
4. Experimental Validation
- Two (2) 7316 Edgecore switches running ONIE.
- Two (2) Spirent traffic generator.
- Four (4) Flexi-grid DWDM nodes.
- 1.
- Slice Creation: To request a Standards-Based and Model-Driven isolated Network Slices using. The SDTN controller would receive and translate the network slice service into specific per domain requests as follows:
- (a)
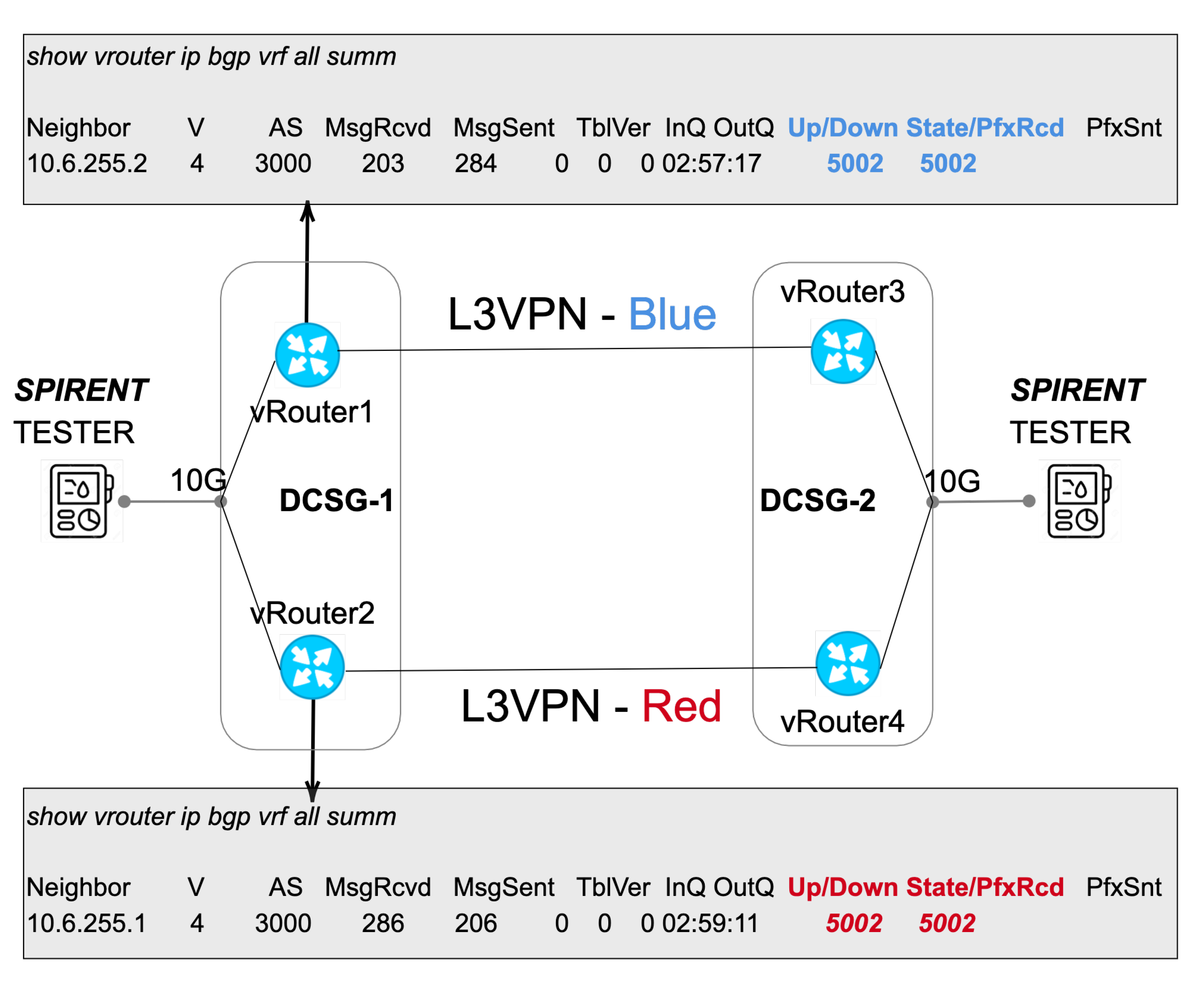
- L3VPN service creation: In this use case, each network slice request requires an L3VPN service creation; thus, each L3VPN service would map to a single network slice. The endpoints defined in the slice request would map to Virtual Router and Forwarding (VRFs) instances on the virtual routers. The Yang data model used for the SDTN requests the L3VPN services to the IP domain controller was the L3NM [4].
- (b)
- DWDM connectivity: The T-API [5] was used to create a new connectivity service in the transport network to enable the L2-L1 communication between the network slice endpoints.
- 2.
- Add Prefixes and destroy: The second use case expects to validate the IP connectivity between the network slices. Hence the Spirent testers announced a set of 5k IP prefixes through the prior created network slices. Afterwards, the testers make an automatic IP reachability test and a CLI route redistribution validation. Once the route propagation was validated, the testing team stopped all the Spirent prefixes’ announcement, and a new automatic connectivity test was done.
- 3.
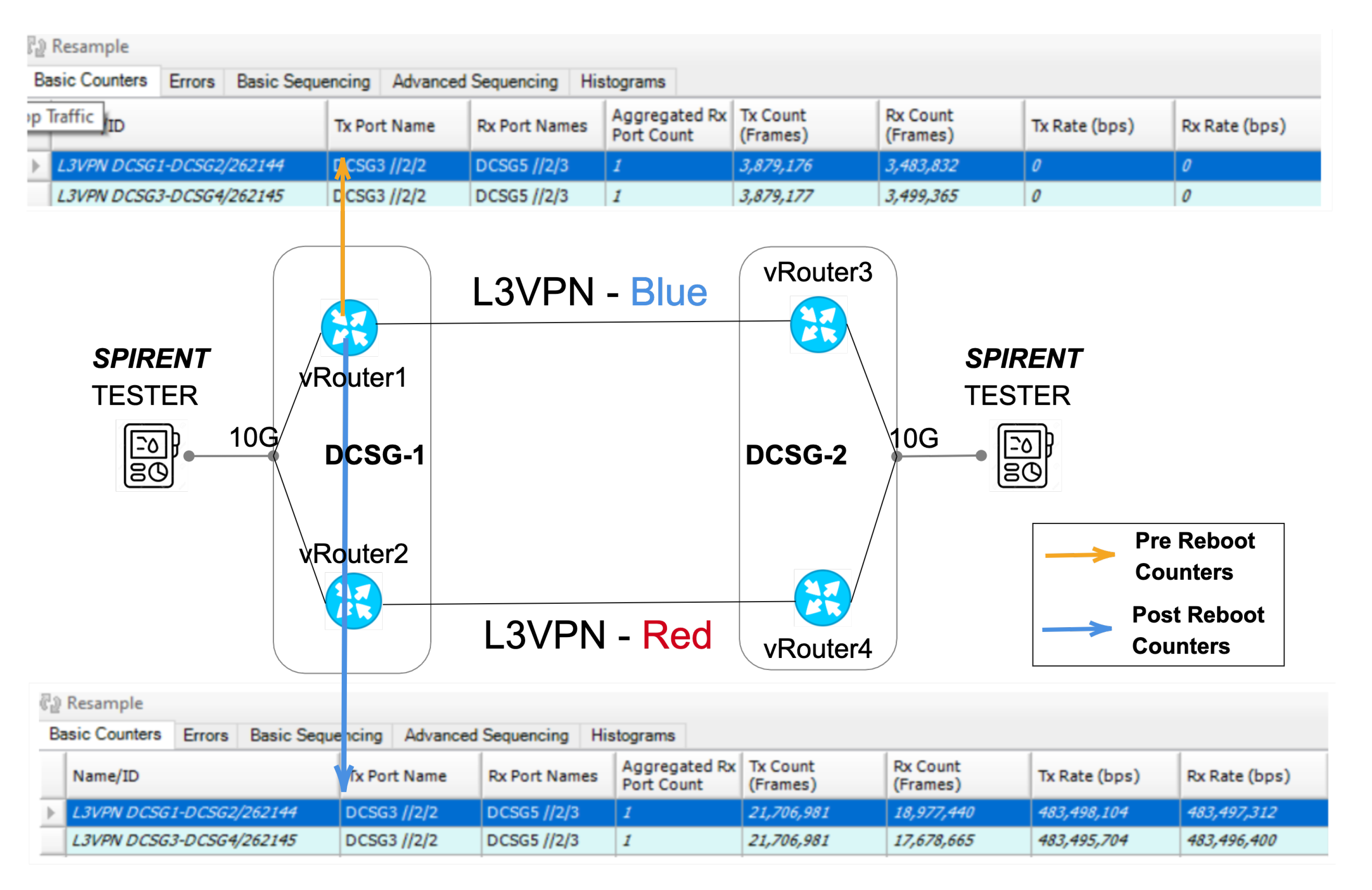
- Device recovery test: The third use case was to verify the network slices service continuity so. The testing team manually rebooted all the DCSGs. Once the devices got online again, we have checked the service status with a measurement of the service restoration time.
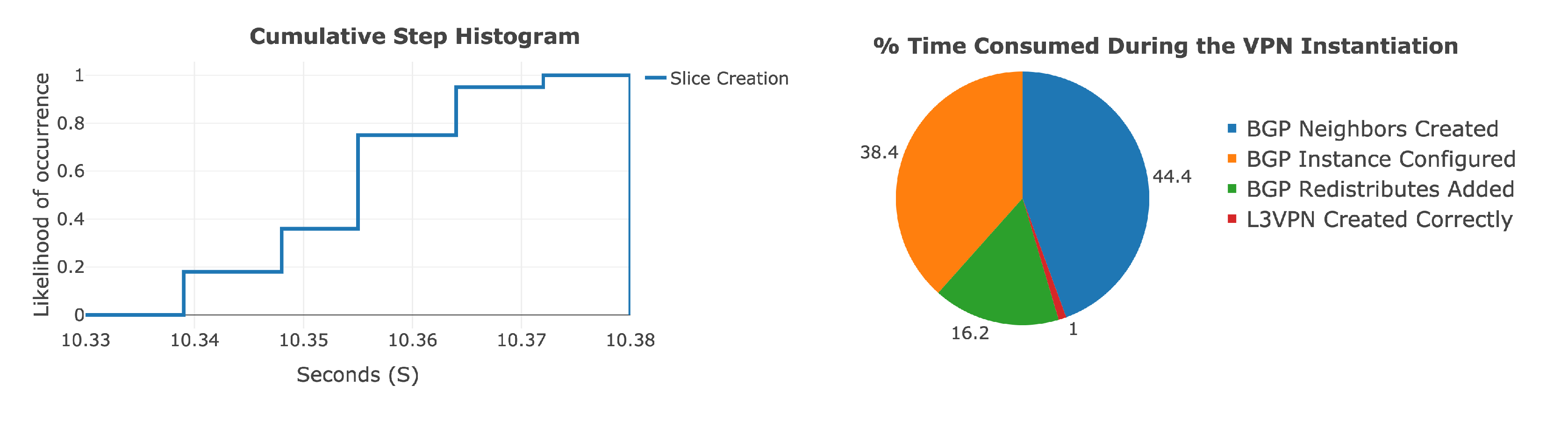
4.1. Slice Creation
4.2. Add Prefixes and Destroy
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| API | Application programming interface |
| BSS | Business Support System |
| BGP | Border Gateway Protocol |
| CE | Customer Edge |
| IETF | Internet Engineering Task Force |
| eMBB | Enhanced Mobile Broadband |
| L2SM | L2VPN Service Model |
| L2NM | L2VPN Network Model |
| L3SM | L3VPN Service Model |
| L3NM | L3VPN Network Model |
| L3VPN | Layer Three Virtual Private Network |
| MC | Mobile Core |
| mMTC | Massive Machine Type Communication |
| MPLS | Multiprotocol Label Switching |
| NASS | Network As A Service |
| NGMN | Next Generation Mobile Networks |
| NSI | Network Slice Instance |
| ODU | Optical Distribution Unit |
| ONF | Open Networking Foundation |
| OSS | Operation Support Systems |
| PE | Provider Edge |
| QoS | Quality of service |
| RAN | Radio Access Network |
| SDN | Software Defined Network |
| SI | Service Instance |
| URLLC | Ultra Reliable Low Latency Communications |
| VSI | Virtual switching Interfaces |
| VPN | Virtual Private Network |
| VRF | Virtual Routing and Forwarding |
| YANG | Yet Another Next Generation |
References
- Ordonez-Lucena, J.; Ameigeiras, P.; Lopez, D.; Ramos-Munoz, J.J.; Lorca, J.; Folgueira, J. Network slicing for 5G with SDN/NFV: Concepts, architectures, and challenges. IEEE Commun. Mag. 2017, 55, 80–87. [Google Scholar] [CrossRef] [Green Version]
- Contreras, L.M.; López, D.R. A Network Service Provider Perspective on Network Slicing. IEEE Softwarization: A Collection of Short Technical Articles. 2018. Available online: https://sdn.ieee.org/newsletter/january-2018/a-network-service-provider-perspective-on-network-slicing?highlight=WyJhIiwiJ2EiLCJuZXR3b3JrIiwibmV0d29yaydzIiwiJ25ldHdvcmsiLCJzZXJ2aWNlIiwic2VydmljZScsIiwiJ3NlcnZpY2UiLCJwcm92aWRlciIsInByb3ZpZGVyJ3MiLCJhIG5ldHdvcmsiLCJhIG5ldHdvcmsgc2VydmljZSIsIm5ldHdvcmsgc2VydmljZSIsIm5ldHdvcmsgc2VydmljZSBwcm92aWRlciIsInNlcnZpY2UgcHJvdmlkZXIiXQ== (accessed on 1 July 2021).
- Barguil, S.; de Dios, O.G.; Boucadair, M.; Munoz, L.; Jalil, L.; Ma, J. A Layer 2 VPN Network Yang Model. draft-ietf-opsawg-l2nm-02. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-opsawg-l2nm-02 (accessed on 1 July 2021).
- Barguil, S.; de Dios, O.G.; Boucadair, M.; Munoz, L.; Aguado, A. A Layer 3 VPN Network YANG Model. draft-ietf-opsawg-l3sm-l3nm-05. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-opsawg-l3sm-l3nm (accessed on 1 July 2021).
- Vilalta, R.; Muñoz, R.; Landi, G.; Rodriguez, L.; Capitani, M.; Casellas, R.; Martínez, R. Experimental Demonstration of the BlueSPACE’s NFV MANO Framework for the Control of SDM/WDM-enabled Fronthaul and Packet-based Transport Networks by Extending the TAPI. In Proceedings of the IEEE 2018 European Conference on Optical Communication (ECOC), Rome, Italy, 23–27 September 2018; pp. 1–3. [Google Scholar]
- Shaikh, A. OpenConfig-progress toward vendor-neutral network management. In Proceedings of the North American Network Operators’ Group (NANOG) 71, San Jose, CA, USA, 2–4 October 2017. [Google Scholar]
- Alcalá, A.; Barguil, S.; López, V.; Contreras, L.M.; Manso, C.; Alemany, P.; Casellas, R.; Martínez, R.; Gonzalez-Perez, D.; Liu, X.; et al. Multi-layer Transport Network Slicing with Hard and Soft Isolation. In Proceedings of the 2021 Optical Fiber Conference (OFC), Virtual Event, 6–11 June 2021. [Google Scholar]
- Alliance, N. Description of network slicing concept. NGMN 5G P 2016. Available online: https://www.ngmn.org/publications/description-of-network-slicing-concept.html (accessed on 1 July 2021).
- Kukliński, S.; Tomaszewski, L. Business models of network slicing. In Proceedings of the 2018 9th International Conference on the Network of the Future (NOF), Poznan, Poland, 19–21 November 2018; pp. 19–21. [Google Scholar]
- Zhang, N.; Liu, Y.F.; Farmanbar, H.; Chang, T.H.; Hong, M.; Luo, Z.Q. Network slicing for service-oriented networks under resource constraints. IEEE J. Sel. Areas Commun. 2017, 35, 2512–2521. [Google Scholar] [CrossRef] [Green Version]
- Khan, L.U.; Yaqoob, I.; Tran, N.H.; Han, Z.; Hong, C.S. Network slicing: Recent advances, taxonomy, requirements, and open research challenges. IEEE Access 2020, 8, 36009–36028. [Google Scholar] [CrossRef]
- Foukas, X.; Patounas, G.; Elmokashfi, A.; Marina, M.K. Network slicing in 5G: Survey and challenges. IEEE Commun. Mag. 2017, 55, 94–100. [Google Scholar] [CrossRef] [Green Version]
- Huang, S.; Guo, B.; Liu, Y. 5G-Oriented optical underlay network slicing technology and challenges. IEEE Commun. Mag. 2020, 58, 13–19. [Google Scholar] [CrossRef]
- Rosen, E.; Rekhter, Y. BGP/MPLS IP Virtual Private Networks (VPNs). RFC 4364. Available online: https://www.rfc-editor.org/info/rfc8049 (accessed on 1 July 2021). [CrossRef] [Green Version]
- Litkowski, S.; Tomotaki, L.; Ogaki, K. YANG Data Model for L3VPN Service Delivery. RFC 8049. Available online: https://www.rfc-editor.org/info/rfc4364 (accessed on 1 July 2021). [CrossRef] [Green Version]
- Marotta, A.; Cassioli, D.; Tornatore, M.; Hirota, Y.; Awaji, Y.; Mukherjee, B. Reliable slicing with isolation in optical metro-aggregation networks. In Proceedings of the IEEE 2020 Optical Fiber Communications Conference and Exhibition (OFC), San Diego, CA, USA, 8–12 March 2020; pp. 1–3. [Google Scholar]
- Contreras, L.M.; Barguil, S.; Vilalta, R.; López, V. Architecture for integrating vertical customer’s programmability control of network functions and connectivity in a slice-as-a-service schema. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 1–16. [Google Scholar] [CrossRef]
- 3GPP TS 23.501. System Architecture for the 5G System (3GPP TS 23.501 Version 15.3. 0 Release 15), September 2018. Available online: https://www.etsi.org/deliver/etsi_ts/123500_123599/123501/15.03.00_60/ts_123501v150300p.pdf (accessed on 1 July 2021).
- Redana, S.; Bulakci, Ö.; Zafeiropoulos, A.; Gavras, A.; Tzanakaki, A.; Albanese, A.; Kousaridas, A.; Weit, A.; Sayadi, B.; Jou, B.T.; et al. 5G PPP Architecture Working Group: View on 5G Architecture. 2019. Available online: https://bura.brunel.ac.uk/bitstream/2438/18546/1/FullText.pdf (accessed on 1 July 2021).
- Ferrús, R.; Sallent, O.; Pérez-Romero, J.; Agusti, R. On the automation of RAN slicing provisioning and cell planning in NG-RAN. In Proceedings of the IEEE 2018 European Conference on Networks and Communications (EuCNC), Ljubljana, Slovenia, 18–21 June 2018; pp. 37–42. [Google Scholar]
- Contreras, L.; González, Ó.; López, V.; Fernández-Palacios, J.; Folgueira, J. iFUSION: Standards-based SDN Architecture for Carrier Transport Network. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–7. [Google Scholar]
- Bierman, A.; Bjorklund, M.; Watsen, K. RESTCONF protocol. RFC 8040. Available online: https://www.rfc-editor.org/info/rfc8040 (accessed on 1 July 2021). [CrossRef]
- Enns, R.; Bjorklund, M.; Schoenwaelder, J.; Bierman, A. Network configuration protocol (NETCONF). RFC 6241. Available online: https://www.rfc-editor.org/info/rfc6241 (accessed on 1 July 2021). [CrossRef] [Green Version]
- Vilalta, R.; Muñoz, R.; Casellas, R.; Martínez, R.; López, V.; González-de-Dios, O.; Pastor, A.; Katsikas, G.; Klaedtke, F.; Monti, P.; et al. TeraFlow: Secured Autonomic Traffic Management for a Tera of SDN Flows. In Proceedings of the IEEE 2021 European Conference on Networks and Communications (EuCNC), Virtual Event, 8–11 June 2021. [Google Scholar]
- Rokui, R.; Homma, S.; Makhijani, K.; Contreras, L.; Tantsura, J. Definition of IETF Network Slices. draft-ietf-teas-ietf-network-slice-definition-01. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-teas-ietf-network-slice-definition (accessed on 1 July 2021).
- Gray, E.; Drake, J. Framework for IETF Network Slices. draft-ietf-teas-ietf-network-slice-framework-00. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-teas-ietf-network-slice-framework (accessed on 1 July 2021).
- Available online: http://www.claise.be/YANGPageMain.html (accessed on 3 April 2021).
- Wen, B.; Fioccola, G.; Xie, C.; Jalil, L. A YANG data model for layer 2 virtual private network (L2VPN) service delivery. RFC 8466. Available online: https://www.rfc-editor.org/info/rfc8466 (accessed on 1 July 2021). [CrossRef]
- Saad, T.; Gandhi, R.; Liu, X.; Beeram, V.; Bryskin, I. A YANG Data Model for Traffic Engineering Tunnels, Label Switched Paths and Interfaces. draft-ietf-teas-yang-te-25. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-teas-yang-te-25 (accessed on 1 July 2021).
- Liu, X.; Bryskin, I.; Beeram, V.; Saad, T.; Shah, H.; de Dios, O.G. YANG Data Model for Traffic Engineering (TE) Topologies. RFC 8795. Available online: https://www.rfc-editor.org/info/rfc8795 (accessed on 1 July 2021). [CrossRef]
- Liu, X.; Bryskin, I.; Beeram, V.; Saad, T.; Shah, H.; de Dios, O.G. YANG Data Model for Traffic Engineering (TE) Topologies. draft-ietf-teas-yang-l3-te-topo-10. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-teas-yang-l3-te-topo (accessed on 1 July 2021).
- Lee, Y.; Dhody, D.; Fioccola, G.; Wu, Q. Traffic Engineering (TE) and Service Mapping Yang Model. draft-ietf-teas-te-service-mapping-yang-07. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-teas-te-service-mapping-yang-07 (accessed on 1 July 2021).
- Jethanandani, M.; Agarwal, S. YANG Data Model for Network Access Control Lists (ACLs). RFC 8519. Available online: https://www.rfc-editor.org/info/rfc8519 (accessed on 1 July 2021). [CrossRef]
- Qu, Y.; Tantsura, J.; Lindem, A.; Liu, X. A YANG Data Model for Routing Policy. draft-ietf-rtgwg-policy-model-27. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-rtgwg-policy-model-27 (accessed on 1 July 2021).
- Jethanandani, M.; Patel, K.; Hares, S.; Haas, J. BGP YANG Model for Service Provider Networks. draft-ietf-idr-bgp-model-10. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-idr-bgp-model-10 (accessed on 1 July 2021).
- Zheng, H.; Busi, I.; Guo, A.; Lopez, V. Framework and Data Model for OTN Network Slicing. draft-zheng-ccamp-yang-otn-slicing-01. Available online: https://datatracker.ietf.org/doc/html/draft-zheng-ccamp-yang-otn-slicing-01 (accessed on 1 July 2021).
- Liu, X.; Tantsura, J.; Bryskin, I.; Contreras, L.; Wu, Q.; Belotti, S.; Rokui, R. IETF Network Slice YANG Data Model. draft-liu-teas-transport-network-slice-yang-02. Available online: https://datatracker.ietf.org/doc/html/draft-liu-teas-transport-network-slice-yang-02 (accessed on 1 July 2021).


| Applications | Definition | Example |
|---|---|---|
| Ultra Reliable Low Latency Communications (uRLLC) | Requires support for 1 ms latencies, 0.001% packet loss, user mobility up to 100 km/h | Autonomous driving or Industrial automation |
| Massive Machine Type Communications (mMTC) | Requires support for 1 million devices per square kilometer, tens of bps bandwidth, and latency minimization for battery life optimization | Massive IoT |
| Enhanced Mobile Broadband (eMBB) | Requires Gbps bandwidth, real time or not | Immersive UIs based Augmented Reality Virtual Reality. Streaming of High Quality Video |
| Models | Description | Example |
|---|---|---|
| LxVPN | These models describe a VPN service from the customer or network operator point of view. | L3SM: [15] L2SM: [28] L3NM: [4] L2SM: [3] |
| Traffic Engineering | These models allow to manipulate Traffic Engineering tunnels within the network segment. Technology-specific extensions allow to work with a desired technology (e.g., MPLS RSVP-TE tunnels, Segment Routing paths, OTN tunnels, etc.) | TE: [29] TE Topology: [30,31] |
| TE Service Mapping extensions | These extensions allow to specify for LxVPN the details of an underlay based on Traffic Engineering | Service Mapping: [32] |
| ACLs and Routing policies | Even though ACLs and routing policies are device models, It’s exposure in the NBI of a domain controller allows to provide an additional granularity that the network domain controller is not able to infer on its own. | ACL: [33] Routing Policy: [34,35] |
| OTN | As a part of the transport network, OTN can provide hard pipes with guaranteed data isolation and deterministic low latency, which are highly demanded in the Service Level Agreement (SLA). | OTN Slice: [36] |
| Slicing | Set of data models available to map and realize the network Slices. | Network Slice NBI: [25,26] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Barguil, S.; Lopez Alvarez, V.; Contreras Murillo, L.M.; Gonzalez de Dios, O.; Alcala Alvarez, A.; Manso, C.; Alemany, P.; Casellas, R.; Martinez, R.; Gonzalez-Perez, D.; et al. Packet Optical Transport Network Slicing with Hard and Soft Isolation. Appl. Sci. 2021, 11, 6219. https://doi.org/10.3390/app11136219
Barguil S, Lopez Alvarez V, Contreras Murillo LM, Gonzalez de Dios O, Alcala Alvarez A, Manso C, Alemany P, Casellas R, Martinez R, Gonzalez-Perez D, et al. Packet Optical Transport Network Slicing with Hard and Soft Isolation. Applied Sciences. 2021; 11(13):6219. https://doi.org/10.3390/app11136219
Chicago/Turabian StyleBarguil, Samier, Victor Lopez Alvarez, Luis Miguel Contreras Murillo, Oscar Gonzalez de Dios, Alejandro Alcala Alvarez, Carlos Manso, Pol Alemany, Ramon Casellas, Ricardo Martinez, David Gonzalez-Perez, and et al. 2021. "Packet Optical Transport Network Slicing with Hard and Soft Isolation" Applied Sciences 11, no. 13: 6219. https://doi.org/10.3390/app11136219
APA StyleBarguil, S., Lopez Alvarez, V., Contreras Murillo, L. M., Gonzalez de Dios, O., Alcala Alvarez, A., Manso, C., Alemany, P., Casellas, R., Martinez, R., Gonzalez-Perez, D., Liu, X., Pulido, J.-M., Fernandez-Palacios, J. P., Muñoz, R., & Vilalta, R. (2021). Packet Optical Transport Network Slicing with Hard and Soft Isolation. Applied Sciences, 11(13), 6219. https://doi.org/10.3390/app11136219








