Towards a GDPR-Compliant Blockchain-Based COVID Vaccination Passport
Abstract
:1. Introduction
2. Background
2.1. Blockchain
- (1)
- Public Blockchain: A public blockchain is a non-restrictive, permission-less distributed ledger-based system. Anybody having access to the Internet can register and sign in to the blockchain platform. Each member can check the transaction and verify it. Also, anyone can participate in the process of getting consensus. Bitcoin and Ethereum are the relevant examples [6]. A public blockchain also demands a significant amount of computing capacity, because maintaining a distributed ledger on a wide scale takes a significant amount of processing power. Each node in the network needs to solve a complicated cryptographic puzzle to verify that all nodes in the blockchain have coordinated to reach a consensus [7].
- (2)
- Private Blockchain: It is restrictive in nature and requires permission, which limits it to work only for private networks. It has strict authorization management for accessing data. Only the selected participant has access to the system within an enterprise. Security, authorization, and accessibility are controlled by enterprises unlike public blockchain [9]. Private blockchains are easier to scale up, cut down costs, and feature greater transactions. This approach can enable the organization to have more control over the network and establish integrity by removing anonymity.
- (3)
- Consortium Blockchain: This is another type of permissioned blockchain, which is also referred to as a semi-decentralized blockchain. In this type of blockchain, predefined approved parties (nodes) participate in the block validation process. If a group of enterprises wants to implement a blockchain network and requires only a few approved parties to participate in the process, this type of blockchain platform can be implemented. Consortium blockchain allows the implementation of customized organizational policies. In addition to these characteristics, depending on the requirements of customers (organizations), services of the blockchain (i.e., inquiries about the information in the blockchain) can be open to the public or other authorities who are not part of the blockchain. The proposed architecture is based on elements of consortium blockchain enabling the concerned authorities to perform the needful tasks and inquire about any information residing on the blockchain. Moreover, the network can be easily expanded and if required, the participating authorities can be added [23,24,25]. The factors which further motivate our choice of consortium blockchain are as follows:
- It is a permissioned blockchain, therefore, only authorized nodes can validate the blocks.
- It is highly scalable allowing any party to get involved.
- Though it is a permissioned blockchain, its services can be seen by the public by using customized APIs.
- It allows spreading across a specific area or geographical region, allowing control over data transfer and processing.
- Potential data breaches can also be investigated easily since the participating authorities are fixed and finite.
2.2. Smart Contracts
- A smart contract promotes traceability when it is used to collect the status of the information on the blockchain. The transaction log of the smart contract can also be used as a travel log to trace and limit potential COVID exposures and infections.
- The smart contracts execute automatically and the traveler will not have to provide any extra details for that.
- Verification with the help of a smart contract is faster than manual verification since it does not require human intervention. Moreover, there are no intermediaries involved.
2.3. GDPR
3. Methodology
3.1. Identification of Design Requirements
- The citizens must be registered with local health authorities to get vaccinated.
- The vaccinations are administered in specific hospitals under specific protocols.
- Timestamps would be required to record the date of vaccination to ensure validity.
- The qualitative analysis of the interviews data and existing blockchain solutions revealed the following:
- Facilitation of information flow between different authorities would be required. Different authorities involved in this could include immigration authorities, healthcare authorities, etc. The interview data highlighting this aspect was labeled and the code assigned was ‘information flow’.
- There is a need for increased trust so that the authorities use the service (code: trust).
- Consideration of security mechanisms in cases where it involves storing personally identifiable information (code: security mechanisms).
- A procedure for verification that involves less computation (code: verifiability).
- Complying with the GDPR articles (details discussed in the following sub-section).
3.2. GDPR Requirements
- Access to data should be traced.
- Data subjects’ consent should be collected using a smart contract.
- Blockchain data needs to be deleted or modified upon request.
- Data controllers and processors must be identified.
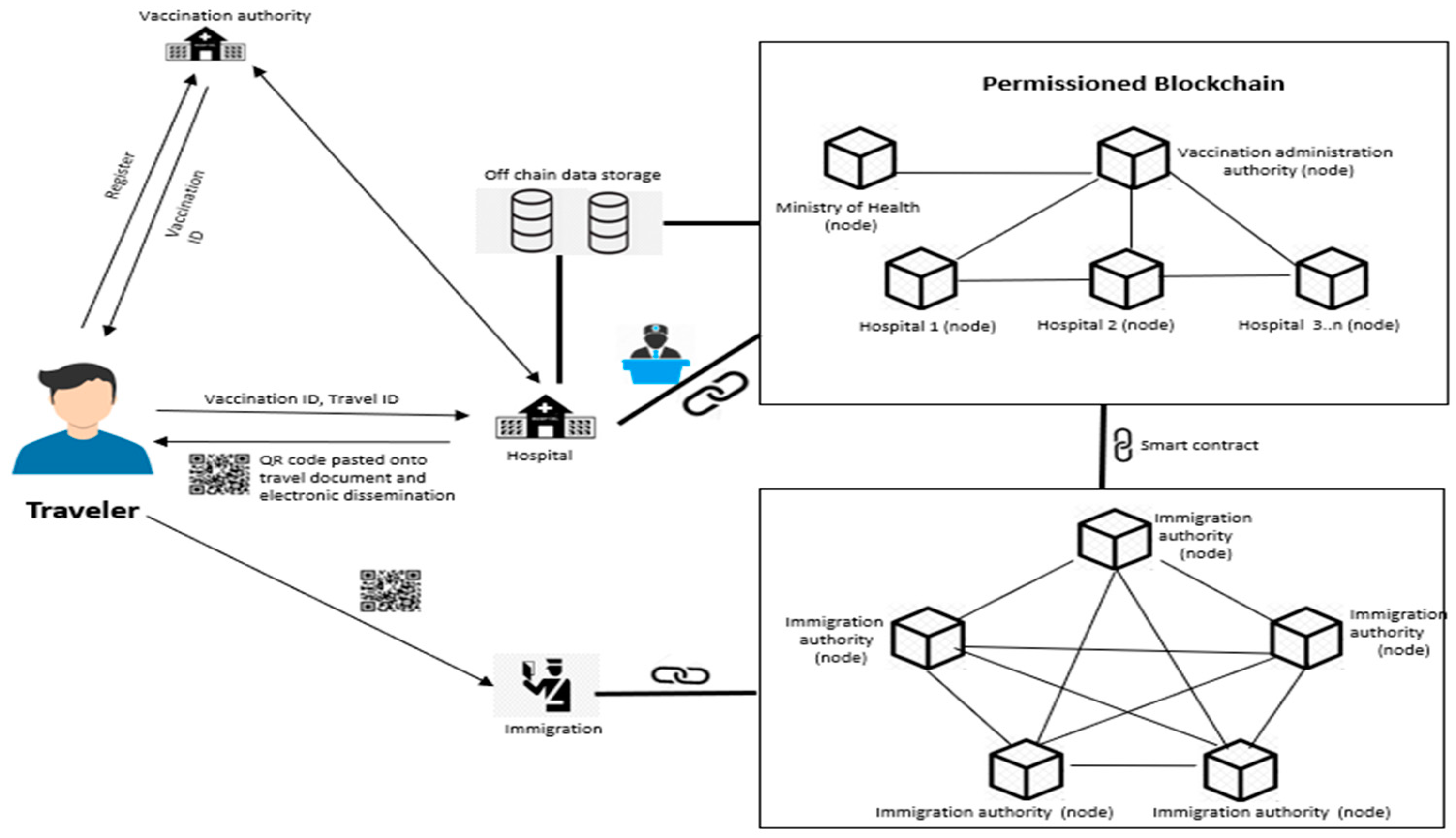
4. Architectural Framework for COVID Vaccination Passport
4.1. Architectural Framework (VacciFi)
- Create: refers to the right for the creation of a new record in the off-chain
- Read: refers to the right to read/view the record
- Update: refers to the right to update the existing record
- Delete: refers to deletion of the record
4.1.1. Registration
4.1.2. Vaccination
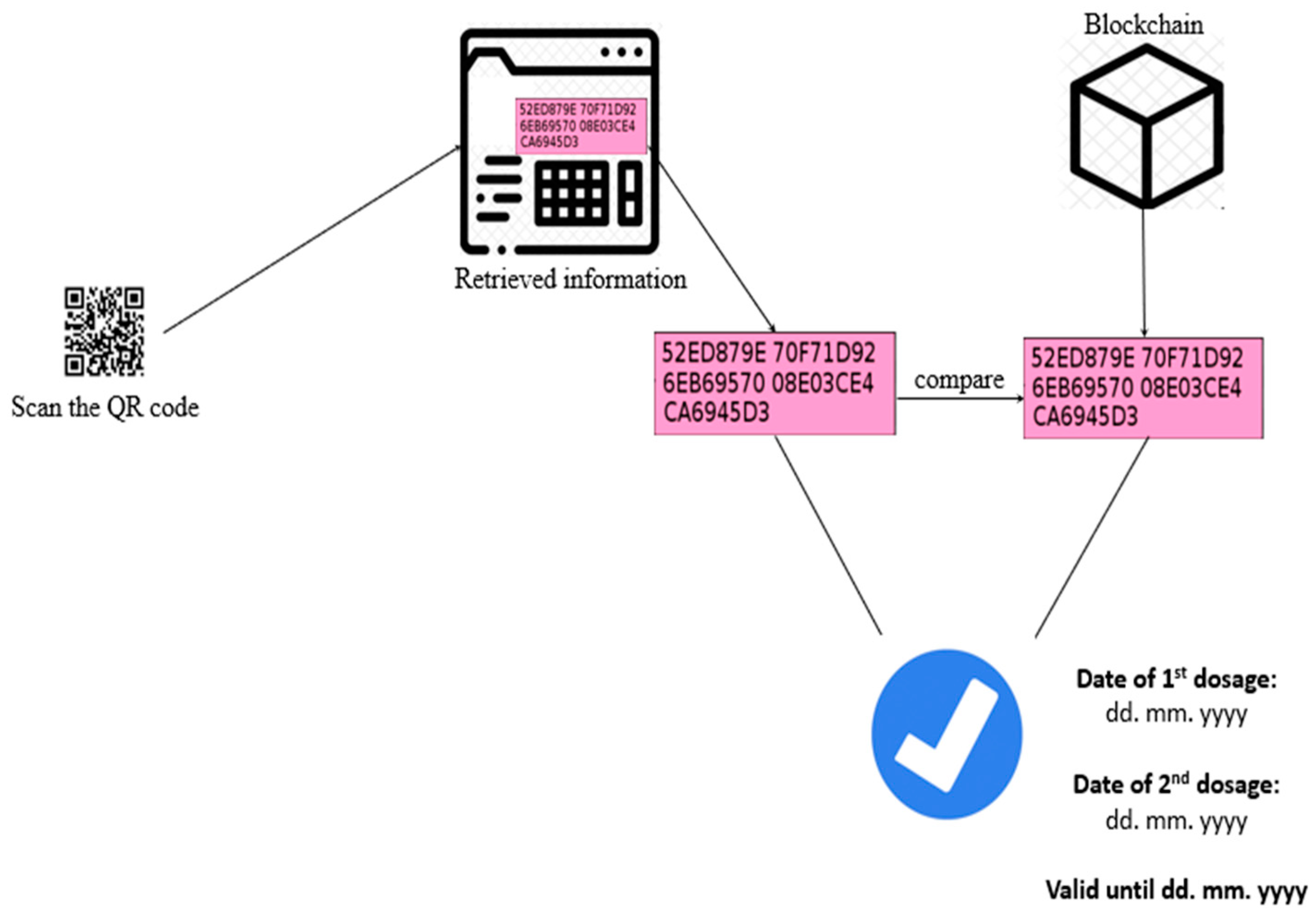
4.1.3. Verification
4.2. Compliance with GDPR
5. Discussion
5.1. Research Contributions
5.2. Limitations
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Ravens-Sieberer, U.; Kaman, A.; Erhart, M.; Devine, J.; Schlack, R.; Otto, C. Impact of the COVID-19 pandemic on quality of life and mental health in children and adolescents in Germany. Eur. Child Adolesc. Psychiatry 2021, 1–11. [Google Scholar] [CrossRef]
- Coronavirus Update (Live): 74,746,810 Cases and 1,659,186 Deaths from COVID-19 Virus Pandemic—Worldometer. Available online: https://www.worldometers.info/coronavirus/ (accessed on 5 May 2021).
- Dash, D.P.; Sethi, N.; Dash, A.K. Infectious disease, human capital, and the BRICS economy in the time of COVID-19. MethodsX 2021, 8, 101202. [Google Scholar] [CrossRef]
- Alfano, V.; Ercolano, S. The Efficacy of Lockdown Against COVID-19: A Cross-Country Panel Analysis. Appl. Health Econ. Health Policy 2020, 18, 509–517. [Google Scholar] [CrossRef] [PubMed]
- Cucinotta, D.; Vanelli, M. WHO Declares COVID-19 a Pandemic. Acta Bio Med. Atenei Parm. 2020, 91, 157–160. [Google Scholar]
- Graham, B.S. Rapid COVID-19 vaccine development. Science 2020, 368, 945–946. [Google Scholar] [CrossRef] [PubMed]
- COVID-19: Digital Green Certificates, European Commission. Available online: https://ec.europa.eu/info/live-work-travel-eu/coronavirus-response/safe-covid-19-vaccines-europeans/covid-19-digital-green-certificates_en (accessed on 5 May 2021).
- Harris, C. COVID Vaccine Rollout: Which Country in Europe Is Leading the Race? Available online: https://www.euronews.com/2021/03/31/covid-19-vaccinations-in-europe-which-countries-are-leading-the-way (accessed on 29 April 2021).
- Bhushan, B.; Khamparia, A.; Sagayam, K.M.; Sharma, S.K.; Ahad, M.A.; Debnath, N.C. Blockchain for smart cities: A review of architectures, integration trends and future research directions. Sustain. Cities Soc. 2020, 61, 102360. [Google Scholar] [CrossRef]
- Haque, A.B.; Bhushan, B. Emergence of Blockchain Technology: A Reliable and Secure Solution for IoT Systems. In Blockchain Technology for Data Privacy Management; CRC Press, Taylor & Francis: Boca Raton, FL, USA, 2021; pp. 159–183. [Google Scholar]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inf. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Liu, Y.; He, D.; Obaidat, M.S.; Kumar, N.; Khan, M.K.; Choo, K.-K.R. Blockchain-based identity management systems: A review. J. Netw. Comput. Appl. 2020, 166, 102731. [Google Scholar] [CrossRef]
- Arif, S.; Khan, M.A.; Rehman, S.U.; Kabir, M.A.; Imran, M. Investigating Smart Home Security: Is Blockchain the Answer? IEEE Access 2020, 8, 117802–117816. [Google Scholar] [CrossRef]
- Pranto, T.H.; Noman, A.A.; Mahmud, A.; Haque, A.B. Blockchain and smart contract for IoT enabled smart agriculture. PeerJ Comput. Sci. 2021, 7, e407. [Google Scholar] [CrossRef]
- Magnani, A.; Calderoni, L.; Palmieri, P. Feather forking as a positive force. In Proceedings of the 2nd Workshop on Deep Learning for Recommender Systems; ACM: New York, NY, USA, 2018; pp. 99–104. [Google Scholar]
- Bera, B.; Chattaraj, D.; Das, A.K. Designing secure blockchain-based access control scheme in IoT-enabled Internet of Drones deployment. Comput. Commun. 2020, 153, 229–249. [Google Scholar] [CrossRef]
- Macrinici, D.; Cartofeanu, C.; Gao, S. Smart contract applications within blockchain technology: A systematic mapping study. Telemat. Inform. 2018, 35, 2337–2354. [Google Scholar] [CrossRef]
- Williams, C.C. Impacts of the coronavirus pandemic on Europe’s tourism industry: Addressing tourism enterprises and workers in the undeclared economy. Int. J. Tour. Res. 2021, 23, 79–88. [Google Scholar] [CrossRef]
- Kelly, S.M. Vaccine Passport Apps Could Help Us Return to Normal. First They Need to Solve the Trust Problem. Available online: https://edition.cnn.com/2021/03/29/tech/vaccine-passport-app-privacy/index.html? (accessed on 10 April 2021).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2009. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 April 2021).
- Goyal, S.; Sharma, N.; Kaushik, I.; Bhushan, B. Blockchain as a Solution for Security Attacks in Named Data Networking of Things. In Security and Privacy Issues in IoT Devices and Sensor Networks; Elsevier BV: Amsterdam, The Netherland, 2021; pp. 211–243. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Bhushan, B.; Sinha, P.; Sagayam, K.M.; Andrew, J. Untangling Blockchain Technology: A Survey on State of the Art, Security Threats, Privacy Services, Applications and Future Research Directions. Comput. Electr. Eng. 2021, 90, 106897. [Google Scholar] [CrossRef]
- Mermer, G.B.; Zeydan, E.; Arslan, S.S. An Overview of Blockchain Technologies: Principles, Opportunities and Challenges. In Proceedings of the 2018 26th Signal Processing and Communications Applications Conference (SIU), Izmir, Turkey, 2–5 May 2018; pp. 1–4. [Google Scholar]
- Attaran, M.; Gunasekaran, A. Blockchain Principles, Qualities, and Business Applications. In Applications of Blockchain Technology in Business; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2019; pp. 13–20. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.-N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Futur. Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef] [Green Version]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Panda, S.S.; Jena, D. An Overview of Smart Contract and Use Cases in Blockchain Technology. In Proceedings of the 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Bengaluru, India, 10–12 July 2018; pp. 1–4. [Google Scholar]
- Lovell, M.; Foy, M.A. General Data Protection Regulation May 2018 (GDPR). Bone Jt. 360 2018, 7, 41–42. [Google Scholar] [CrossRef]
- Krystlik, J. With GDPR, preparation is everything. Comput. Fraud. Secur. 2017, 2017, 5–8. [Google Scholar] [CrossRef]
- Mourby, M.; Mackey, E.; Elliot, M.; Gowans, H.; Wallace, S.E.; Bell, J.; Smith, H.; Aidinlis, S.; Kaye, J. Are “pseudon-ymised” data always personal data? Implications of the GDPR for administrative data research in the UK. Comput. Law Secur. Rev. 2018, 34, 222–233. [Google Scholar] [CrossRef]
- Haque, A.B.; Islam, A.N.; Hyrynsalmi, S.; Naqvi, B.; Smolander, K. GDPR Compliant Blockchains—A Systematic Literature Review. IEEE Access 2021, 9, 50593–50606. [Google Scholar] [CrossRef]
- General Data Protection Regulation. Available online: https://gdpr-info.eu/ (accessed on 8 May 2021).
- Al-Zaben, N.; Onik, M.H.; Yang, J.; Lee, N.-Y.; Kim, C.-S. General Data Protection Regulation Complied Blockchain Archi-tecture for Personally Identifiable Information Management. In Proceedings of the 2018 International Conference on Computing, Electronics & Communications Engineering (iCCECE), Southend, UK, 16–17 August 2018; pp. 77–82. [Google Scholar]
- Tatar, U.; Gokce, Y.; Nussbaum, B. Law versus technology: Blockchain, GDPR, and tough tradeoffs. Comput. Law Secur. Rev. 2020, 38, 105454. [Google Scholar] [CrossRef]
- Bayle, A.; Koscina, M.; Manset, D.; Perez-Kempner, O. When Blockchain Meets the Right to Be Forgotten: Technology versus Law in the Healthcare Industry. In Proceedings of the 2018 IEEE/WIC/ACM International Conference on Web Intelligence (WI), Santiago, Chile, 3–6 December 2018; pp. 788–792. [Google Scholar]
- Buocz, T.; Ehrke-Rabel, T.; Hödl, E.; Eisenberger, I. Bitcoin and the GDPR: Allocating responsibility in distributed networks. Comput. Law Secur. Rev. 2019, 35, 182–198. [Google Scholar] [CrossRef]
- Dutta, R.; Das, A.; Dey, A.; Bhattacharya, S. Blockchain vs. GDPR in Collaborative Data Governance. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), LNCS; Springer Science and Business Media Deutschland GmbH: Berlin/Heidelberg, Germany, 2020; pp. 81–92. [Google Scholar]
- Kondova, G.; Erbguth, J. Self-sovereign identity on public blockchains and the GDPR. In Proceedings of the 35th Annual ACM Symposium on Applied Computing, Brno, Czech Republic, 30 March–3 April 2020; pp. 342–345. [Google Scholar]
- Cassell, C.; Symon, G. Essential Guide to Qualitative Methods in Organizational Research. In Essential Guide to Qualitative Methods in Organizational Research; SAGE Publications Ltd.: New York, NY, USA, 2004; pp. 323–333. [Google Scholar]
- Gibbs, G. Analyzing Qualitative Data; SAGE Publications Ltd.: New York, NY, USA, 2007. [Google Scholar]
- Bowen, G.A. Document Analysis as a Qualitative Research Method. Qual. Res. J. 2009, 9, 27–40. [Google Scholar] [CrossRef] [Green Version]
- Finnish Aviation Authority. Available online: https://www.finavia.fi/en/air-travel-during-covid-19?id= (accessed on 20 June 2021).
- Finnish Border Guards. Available online: https://raja.fi/en/guidelines-for-border-traffic-during-pandemic-until-6.6.2021 (accessed on 20 June 2021).
- Swedish Police. Available online: https://polisen.se/en/the-swedish-police/the-coronavirus-and-the-swedish-police/travel-to-and-from-sweden/ (accessed on 20 June 2021).
- Ministry of Justice and Public Security. Travel to Norway. Available online: https://www.regjeringen.no/en/topics/koronavirus-covid-19/travel-to-norway/id2791503/ (accessed on 20 June 2021).
- International Airtransport Assocation. European Travel and Tourism Sector Launches “Destination Summer” Campaign. Available online: https://www.iata.org/en/pressroom/pr/2021-06-03-01/ (accessed on 20 June 2021).
- FINNAIR. Frequently Asked Questions. Available online: https://www.finnair.com/en/frequently-asked-questions/coronavirus/why-finnair-requires-a-coronavirus-test-certificate-when-i-travel-to-finland--2223966 (accessed on 20 June 2021).
- Varghese, B.; Villari, M.; Rana, O.; James, P.; Shah, T.; Fazio, M.; Ranjan, R. Realizing Edge Marketplaces: Challenges and Opportunities. IEEE Cloud Comput. 2018, 5, 9–20. [Google Scholar] [CrossRef] [Green Version]
- Aujla, G.S.; Barati, M.; Rana, O.; Dustdar, S.; Noor, A.; Llanos, J.T.; Carr, M.; Marikyan, D.; Papagiannidis, S.; Ranjan, R. COM-PACE: Compliance-Aware Cloud Application Engineering Using Blockchain. IEEE Internet Comput. 2020, 24, 45–53. [Google Scholar] [CrossRef]
- Zemler, F.; Westner, M. Blockchain and GDPR: Application Scenarios and Compliance Requirements. In Proceedings of the 2019 Portland International Conference on Management of Engineering and Technology (PICMET), Portland, OR, USA, 25–29 August 2019; pp. 1–8. [Google Scholar]
- Jambert, A. Blockchain and the GDPR: A Data Protection Authority Point of View. In Computer Vision; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2019; Volume 11469, pp. 3–6. [Google Scholar]
- Saglam, R.B.; Aslan, C.B.; Li, S.; Dickson, L.; Pogrebna, G. A Data-Driven Analysis of Blockchain Systems’ Public Online Communications on GDPR. In Proceedings of the 2020 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 3–6 August 2020; pp. 22–31. [Google Scholar]
- Giannopoulou, A. Data Protection Compliance Challenges for Self-sovereign Identity. In Advances in Intelligent Systems and Computing; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2020; Volume 1238, pp. 91–100. [Google Scholar]
- Damian, C.; Lazar, I.; Visoiu, D.-G.; Romanescu, S.; Alboaie, L. Applying Blockchain Technologies in Funding of Electrical Engineering Industry Applications. In Proceedings of the 2019 International Conference on Electromechanical and Energy Systems (SIELMEN), Craiova, Romania, 9–11 October 2019. [Google Scholar]
| Article No. | Description |
|---|---|
| Article 5 | This article states the “Principles relating to processing of personal data”. Some of the principles are “lawfulness, fairness and transparency”, “purpose limitation”, “data minimization”, “accuracy”, “ integrity and confidentiality” etc. |
| Article 7 | The article demonstrates the data subjects’ consent collection and management related to data processing behaviour and techniques. The beginning of the article in the regulation is stated as “Where processing is based on consent, the controller shall be able to demonstrate that the data subject has consented to processing of his or her personal data.” |
| Article 9 | The article demonstrates “processing of personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation shall be prohibited” |
| Article 16 | “The data subject shall have the right to obtain from the controller without undue delay the rectification of inaccurate personal data concerning him or her” In addition, the data subject’s right includes providing supplementary resources if it is needed based on the processing purpose. |
| Article 17 | “The data subject shall have the right to obtain from the controller the erasure of personal data concerning him or her without undue delay and the controller shall have the obligation to erase personal data without undue delay” Data deletion causes can be consent withdrawal, no legitimate grounds for data retention, data storage not needed. Moreover, the data controller also has to make sure of the appropriate technical measures for deleting the personal data before displaying it. |
| Article 18 | “The data subject shall have the right to obtain from the controller restriction of processing” under a few scenarios, for example, unlawful and illegitimate data processing, data storing is no longer required, etc. |
| Article 24 | “Taking into account the nature, scope, context, and purposes of processing as well as the risks of varying likelihood and severity for the rights and freedoms of natural persons, the controller shall implement appropriate technical and organizational measures to ensure and to be able to demonstrate that processing is performed in accordance with this Regulation. Those measures shall be reviewed and updated where necessary.” |
| Article 25 | Data protection mechanisms should be embedded during the design stages of a system. A stated in the regulation “implement appropriate technical and organizational measures, such as pseudonymization, which are designed to implement data-protection principles, such as data minimization, in an effective manner and to integrate the necessary safeguards into the processing in order to meet the requirements of this Regulation and protect the rights of data subjects” In addition to that, the controller must ensure the protection of personal data (collected and analyzed) by default. |
| Article 26 | This article talks about the joint controller if needed in a system. The regulation says “Where two or more controllers jointly determine the purposes and means of processing, they shall be joint controllers. They shall in a transparent manner determine their respective responsibilities for compliance with the obligations under this Regulation,” |
| Article 28 | This article specifies the data processor’s responsibility. The processor needs to perform the task lawfully and legitimately with appropriate measures. One of the sections of Article 28-GDPR states “Where the processing is to be carried out on behalf of a controller, the controller shall use only processors providing sufficient guarantees to implement appropriate technical and organizational measures in such a manner that processing will meet the requirements of this Regulation and ensure the protection of the rights of the data subject” In addition, there are other regulations exists regarding the processing behavior and techniques of the processor |
| Create | Read | Update | Delete | |
|---|---|---|---|---|
| Immigration authority | x | |||
| Vaccination authority | x | x | x | |
| Hospital authority | x | x | ||
| Ministry of health | x |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Haque, A.B.; Naqvi, B.; Islam, A.K.M.N.; Hyrynsalmi, S. Towards a GDPR-Compliant Blockchain-Based COVID Vaccination Passport. Appl. Sci. 2021, 11, 6132. https://doi.org/10.3390/app11136132
Haque AB, Naqvi B, Islam AKMN, Hyrynsalmi S. Towards a GDPR-Compliant Blockchain-Based COVID Vaccination Passport. Applied Sciences. 2021; 11(13):6132. https://doi.org/10.3390/app11136132
Chicago/Turabian StyleHaque, AKM Bahalul, Bilal Naqvi, A. K. M. Najmul Islam, and Sami Hyrynsalmi. 2021. "Towards a GDPR-Compliant Blockchain-Based COVID Vaccination Passport" Applied Sciences 11, no. 13: 6132. https://doi.org/10.3390/app11136132
APA StyleHaque, A. B., Naqvi, B., Islam, A. K. M. N., & Hyrynsalmi, S. (2021). Towards a GDPR-Compliant Blockchain-Based COVID Vaccination Passport. Applied Sciences, 11(13), 6132. https://doi.org/10.3390/app11136132







