When designing a smart beverage cooler, many factors had to be considered to ensure that the device would function as smoothly as possible during operation. We modelled the architecture after the standard IoT architecture, but introduced several important changes due to specific requirements. Some of the primary requirements that needed to be addressed were: the beverage cooling device should send data to the cloud and be configured and maintained using the mobile service application; it should be able to modify device operating parameters in the event of device part replacements should be ensured; and device control or upgrade via the cloud for security reasons should be disabled. The aim of the project is to improve the device to a smart IoT device according to Industry 4.0 standards.
For this reason, we propose a different software architecture that meets all the device requirements. In this Section, the physical device architecture is presented. Each part of this Section presents different parts of the device in the system architecture model.
4.1. Hardware Layer
The device consists of six separate copper tubes passing through the bath filled with the cooled substance. The copper tubes are filled with the beverage liquid to be cooled and are formed in a coil structure to efficiently increase the tube length. The device uses a bath temperature sensor to directly measure the temperature of the cooled substances. The cooling of the refrigerated substance is achieved by circulating the refrigerant inside the aluminium tube formed as a coil, which is inserted into the bath in parallel with the copper tubes. The cooling effect is based on the transformation of the refrigerant from a liquid state to a gas. This process, known as evaporation, cools the substance in the bath and the copper tubes immersed in the bath. This is the basic principle on which most refrigerators work.
To start the evaporation process and convert the refrigerant from a liquid state to a gas, the pressure on the refrigerant must be reduced through an outlet called the capillary tube. To keep a refrigerator running, the gaseous refrigerant must be converted back to a liquid state, so the refrigerant must be compressed to a higher pressure and temperature. Once the refrigerant is compressed to a higher pressure and temperature, the refrigerant is under high pressure and becomes hot. It must be cooled in the condenser, which is located at the back of the refrigerator, so that the contents can be cooled by the ambient air. This cooling process can be aided by a fan. As the refrigerant in the condenser cools (still under high pressure), it returns to a liquid state. This refrigerant can be reused in the evaporation process. The process described is shown in
Figure 3. To monitor the compressor activity, a temperature sensor measures the temperature of the compressor and condenser to turn on the fan when needed to reduce the unit temperature, thus extending the unit lifetime. In addition, a time delay is added if there is a repeated request for compressor activity.
The cooling process is responsible for the cold drink in the pipes. The user of the device sets the desired beverage temperature through the configuration, which is verified by the temperature sensor immersed in the bath. In addition, a tolerable deviation from the desired temperature is configured. Only when the temperature rises from the desired temperature by the tolerable deviation is the cooling process switched on. Similarly, the cooling process is stopped when the desired liquid temperature in the bath is reached. The frequency of switching on the cooling process depends on the external environmental temperature and the device insulation. It is therefore recommended to store the device in a darker and cooler place.
The inlets of the copper tubes with beverages are connected to the beverage sources. The outlets of the copper tubes are connected to the rotary flow meters. The outlets of the flow meter are connected to tubes arranged to form the python tube. The python tube with six beverage lines and a central return tube is shown in
Figure 4. The python tube connects the copper tubes to the beverage taps, which are mounted for serving beverages. To ensure the cooling of the python tube, the cooling substance is pumped in circulation in the central tubes which are integrated into the python tube.
A temperature sensor is installed at the inlet and outlet of the central tubes to measure the temperature difference. The pump (mixer) is responsible for achieving circulation and to cool the copper tubes in the bath evenly, by distributing the liquid and pressing it into the closed circuit. The temperature difference at the central tubing is used to regulate the power of the pump (mixer) and the operation of the compressor to reduce power consumption. Finally, the last temperature sensor is mounted on the unit casing to measure the ambient temperature. The ambient temperature affects the running time of the compressor and the fan, so this information can be used to detect the malfunctions of the unit.
Temperature and flow sensors are connected to the main processing unit. The passive sensors are connected directly to the 8-bit microcontroller. The temperature sensors are NTC thermistors connected to a 10-bit analogue-to-digital converter, which passes the data to the microcontroller via the I2C bus. Rotating flow sensors are directly connected and counted via the digital input line of the microcontroller.
The microcontroller executes the device algorithm to provide temperature hysteresis cooling system based on the bath temperature sensor. The device has a two-line liquid crystal display that shows the readings from the sensors and allows the reading and setting of the bath base temperature and hysteresis differential temperature. Cumulative flow sensor readings and settings are stored in EEPROM and are retained even if the unit loses power. Other sensor readings are displayed in real time and are not stored or transmitted to an output device. The unit uses a simple fault detection algorithm based on compressor temperature and the deviation of the average python tube temperature from the bath temperature.
For power failure detection, the motherboard is equipped with current sensors that provide information about compressor, pump or fan failure. Due to the low resolution of the current sensors, they cannot provide a detailed current measurement or energy footprint of the device.
4.2. Improving the Hardware Layer
The intelligent beverage cooling system was developed in cooperation between the company Oprema d.d. and Zagreb University of Applied Sciences within the project “Development of the new generation Eco Smart product of the company Oprema d.d.”, funded by European Union [
37]. One of the final versions of the device is shown in
Figure 5:
A new type of microcontroller is introduced for the implementation of telemetry in the device. The motherboard is introduced with the ESP32 microcontroller, as it supports two modes of operation of the wireless module and has two CPU cores, one of which is responsible for the operation of the device and data acquisition and processing, and the other is responsible for the connection with the cloud or mobile application. The idea was to introduce a new microcontroller to an existing motherboard, avoiding additional cost. The test phase is shown in
Figure 6.
During implementation, additional fixes were made to the motherboard as the new microcontroller eliminated the need for other electronics required by the previous microcontroller. For example, the new microcontroller has integrated multiple 12-bit analogue/digital converters and has fast EEPROM memory. In order to provide a smart upgrade for previous version devices and simplify service procedures, the goal of the project was to retain all sensors and wiring from the previous device. The upgraded motherboard is shown in
Figure 7. This chapter presents the upgrades that were achieved to meet the proposed goals.
The device uses six NTC thermistor sensors. The testing of temperature deviation was carried out at the Zagreb University of Applied Sciences and in the laboratories of the company Oprema d.d. The measurement was performed by reading data from the microcontroller delivered to a database server. Simultaneously, with the operation of the device, calibrated temperature sensors DS18B20 [
38] were installed via the I2C bus. The sensors were connected to a microcontroller and delivered data to the same database server over the wireless network. The temperature obtained from the device was compared with the actual temperature measured by the calibrated sensor.
Experiments showed that a previous model of the device had slight deviations around the reference temperature of the NTC thermistor (25 degrees Celsius) and significant deviations (several degrees Celsius) around the expected temperature of the bath-cooled substance. The NTC thermistor used by the device is ELIWELL SN8DED11502C0 [
39]. In the component data sheet, the resistance is given as 10 kOhm at 25 degrees. The resistance changes depending on the temperature according to the specification table given by the manufacturer. The slope of the curve depends on the coefficient of the NTC thermistor. To calculate the temperature accurately, the previous device uses the Steinhart–Hart Equation (
1):
The coefficients
A,
B,
C are the Steinhart–Hart coefficients determined by the factory settings of the sensor.
R is the resistance value that will be calculated by the microcontroller.
T is the determined temperature. The voltage on the pin of the microcontroller generated on a resistor of the parallel divider is proportional to the value
R. In the divider, one of the resistors is fixed and accurate while the other resistor is an NTC thermistor. In the device schematic, the NTC thermistor is connected in a divider with a fixed and accurate resistance of 10,000 ohms. The read value is multiplied by 500 (the referenced voltage on previous version microcontroller increased by the required accuracy of two decimal places) and divided by the maximum number value of the analogue/digital converter. The 12-bit analogue/digital converter provides number values ranging from 0 to 4095. The
measured voltage equation is given in (
2):
The
resistance is determined as the maximum magnitude of the analogue/digital converter divided by the
read value from the analogue/digital converter as stated in (
3):
Since the divider fixed value is set to 10,000 ohm, the
resistance is corrected by the fixed amount in (
4):
The amount is then divided by the factory
resistance of the NTC thermistor at a temperature of 25 degrees (10,000 ohms) in (
5):
Finally, the Steinhart–Hart formula (temperature correction) is applied where
B is the coefficient of the NTC thermistor (
B = 3950 according to datasheet) and 25C is the nominal temperature at which the resistance of the thermistor is expressed. The result is obtained in
Kelvin (
6) and degrees
Celsius (
7):
If the Formula (
7) is applied in the range around the nominal temperature (25 degrees Celsius), minimal deviations are obtained. However, when applied in the range of 0 degrees Celsius, deviations of up to 5 degrees Celsius may occur. Since the operating temperature of the device is 0 degrees and the allowable deviations, per project requirements, are two degrees Celsius, the error of the sensor operation is almost twice the expected nominal operation. The error results from the exponential curve of the thermistor, where it can be observed that there is an exponential change in resistance at much lower or higher temperatures. This can be confirmed by analysing the factory table of resistance change with the temperature data given in the sensor data sheet.
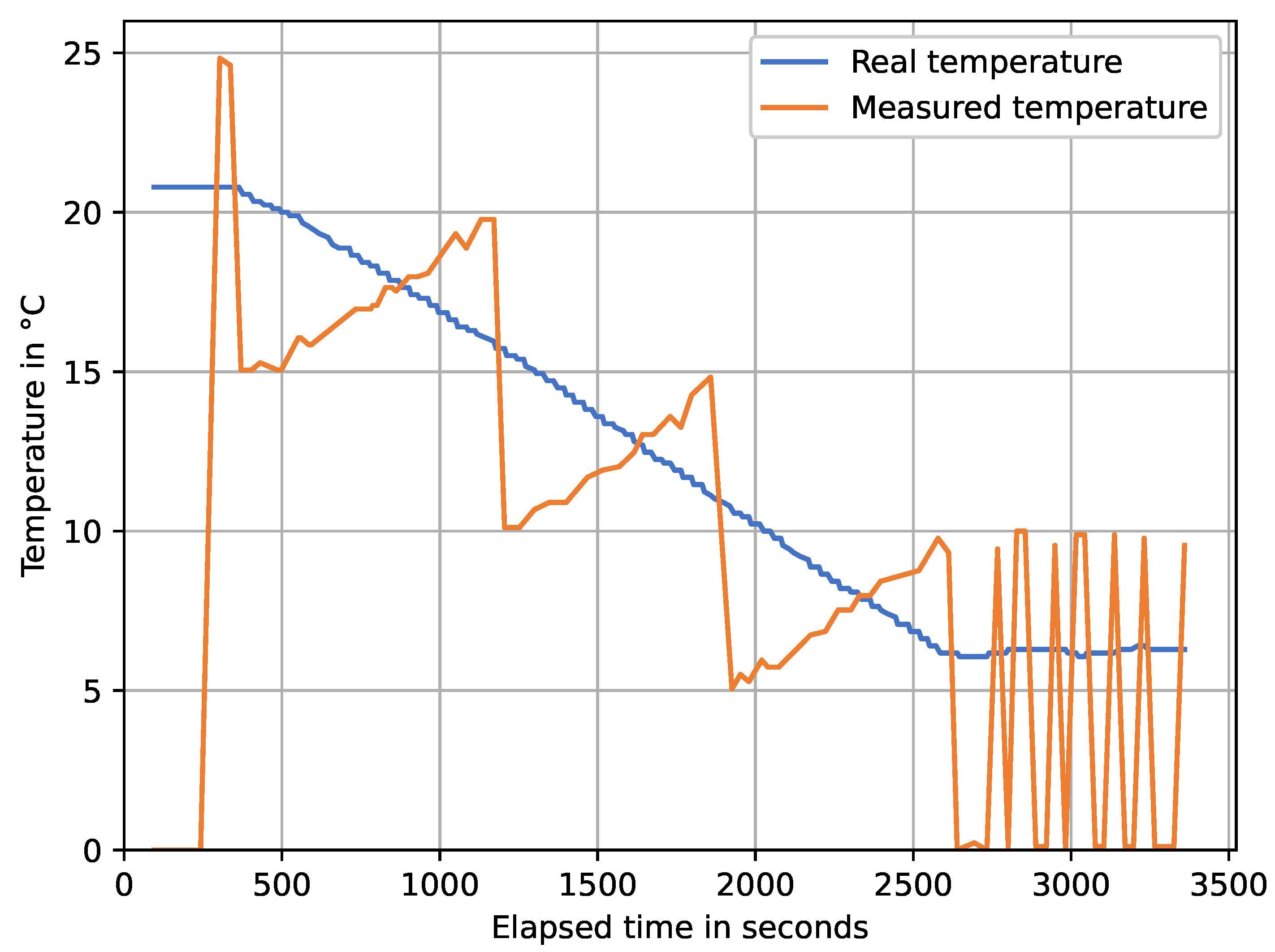
The measured sensor temperature according to real temperature for a previous device model is presented in
Figure 8.
According to the graph shown, using the Steinhart–Hart equation near 0 degrees Celsius is not an option for accurate temperature telemetry. Since the factory resistance settings in the data sheet are in increments of 5 degrees Celsius, the interpolation of the values between each 5 degrees Celsius is performed. The code shown in
Listing 1 first determines the membership of a set of two points: the upper value of the resistor and the lower value of the thermistor temperature resistance. An interpolation of the values between these two points is performed to determine the exact temperature. In
Figure 9, it can be seen that after our corrections, the calculated temperatures follow relatively well the real temperature measured with the reference sensor. We calculated the mean absolute error (MAE) for each measured data point. The MAE for the graph represented by
Figure 8 was calculated as 3.802, while the MAE for a graph represented by
Figure 9 is 0.341, which corresponds to a 11.34-fold temperature precision measurement increase.
The most important group of sensors are flow sensors, which enable flow measurement on all copper tubing inside the python tube. With the help of these sensors, it is possible to measure the consumption of beverages and determine the amount of liquid that has flown through the device. The device is equipped with flow sensors shaped in the form of blades that rotate under water pressure and send a pulse to the microcontroller when a complete rotation is achieved. The microcontroller allows the support of interrupts on all 30 pins. Pins 5, 17, 16, 4, 2 and 15 were chosen as the digital input pins for pulse detection on the flow sensors since the device can support six simultaneous beverage lines. These pins were chosen because they have no other important role (I2C, SPI or Serial) on the microcontroller.
The previous version of the device used interrupt routines. Each pin triggered its interrupt routine upon the detection of a signal change (pulse) on the pin itself. The signal change was due to a pulse from the flow sensor. In the interrupt routine, the value of the variable was increased. In the new version of the code with the specified method, a large number of measurements were made that did not correspond to the actual flow during the measurements. A detailed experimental investigation of the signal and the microcontroller work traced the problem to the speed of the microcontroller itself. The previous version microcontroller operated at a speed of 8 MHz and detected the signal pulse much better. The new microcontroller detected many more signals in the same amount of time for the same amount of fluid. At the operating frequency of 250 MHz, the microcontroller manages to register the transit noise in the pulse. An example of the noise visible on the oscilloscope is shown in
Figure 10.
Resetting the number of microseconds to zero for every pulse (subtracting the first value from all values) gives the timeline of detected pulses. Based on the information obtained, two solutions were proposed based on: begin itemize item double pulse isolation item pulse isolation according to time base end itemize.
The expected order of correct signal readout is the successive iteration of high value and low value. Double pulse isolation operates by discarding pulses that have reported a high value without going to a low value in the meantime. These are extremely fast pulses that occur in immediate succession. The isolation of double pulses has not proved satisfactory and cannot be improved.
Time-based isolation ignores detected high-value pulses for a specified period of time after the occurrence of a high-value pulse. All pulses detected immediately after the occurrence of the first pulse were discarded for the pause period. This approach improved the results somewhat, but the effectiveness depended on the time pause value. The time pause value of 15,000 s approached the theoretical maximum. This time is defined by the number of pulses per litre of fluid during maximum turbine flow. At faster tapping, the results are satisfactory, but at slower tapping, the error becomes larger. Slower tapping is defined by 1 L metered in 60 s, while faster tapping is defined by 1 L metered in 10 s. This definition is based on experimental results with previous Oprema d.d. device models.
To solve the problem, a new algorithm is proposed based on the time prediction of the pulses and the previous interrupt logic on pins is abandoned. The proposed algorithm is shown in
Listing 2.
The timer is set to 4 ms, which was calculated to be the shortest signal period on the fastest tap, according to the flow meter specifications from the datasheet [
40]. Interrupt timer time is calculated upon maximum flow measurement based on device maximum python pipe capacity. This capacity determines the number of impulses per second using the datasheet data for the number of litres per second in maximum flow. When interrupts occur (every 4 ms), the flow line state is read and the previous two states are taken into account. A flow pulse is added only if the previous two states were in a high logical unit. In this way, errors caused by noise when a logic zero occurs are ignored. Satisfactory measurement accuracy was achieved using the above algorithm. The results are shown in
Table 1 and
Table 2. The results presented are satisfactory over the entire operating range of the flow meter (slow and fast tapping). Positive deviation ranges from 2.12% to 4.5% for slow tapping and from 4.2% to 6.8% for fast tapping. The results shown are averages for multiple measurements taken on multiple flow meters. The minimum (Python #1) and maximum (Python #2) flow meter deviations are presented. The flow meter deviations are compared to calibrated flow meters (Multicon V7x [
41]).
In order to store the instrument settings and recorded flow on all pipes, the previous model had a fast EEPROM on the main board. This EEPROM was added because the microcontroller internal EEPROM was too slow to allow memory operation during power failure. The new device model uses a microcontroller EEPROM because the writing speed was significantly improved.
The previous device model had sensors to establish the energy balance of the device. A voltage transformer was used to measure the main voltage and frequency. Current sensors were used to measure fan, compressor and pump (mixer) current. The voltage transformer and current sensors were not able to measure voltage and current accurately. In order to improve the motherboard reliability, the values for the maximum current range were predefined, which resulted in a relatively large error in the current measurements. In addition, the voltage transformer used was not sufficiently calibrated, so detailed voltage information was missing. Measurement accuracy was not a problem as it was not used for precise telemetry. Current sensors allowed the implementation of compressor, fan, and pump (mixer) monitoring that provided information on the current flow present. Alarming events were shown on the unit display.
The new motherboard has a connection capability for current meters between the main power supply and the device. The current meter provides voltage, current, frequency, and power factor information over the serial line. This meter provides accurate measurements that can be used as telemetry for the unit. For each unit, compressor, fan, and pump (mixer) startup is performed to calculate the average current flow in various combinations. This information is later used to detect compressor, fan or pump (mixer) malfunctions. These malfunctions are introduced to the system as alerts through cloud connectivity. Based on the alert, it can additionally shut down the unit before the malfunction causes major damage. This adjustment simplifies the motherboard, provides an accurate power balance, and maintains fault detection and alerting.
An important concept related to ecology and health is the sanitation of the device. The decision about the required sanitation is made based on previous sanitation schedule, the length of the python, the wrong temperatures in the system (leading to the possible growth of bacteria), the flow rate and the summary flow statistics. Based on the information obtained, the mandatory sanitation is ordered.
The flow sensors monitor the sanitation process and ensure that it is performing correctly by measuring the flow rate through the device itself during sanitation. Since the sanitation is performed with aggressive liquids, it is necessary to cleanse the device tubes by sending a significant volume of liquid before the device is restored to general use. The flow measurements obtained during sanitation are not included in the total flow statistics.
4.6. Service Mobile Application
A service mobile application was developed to support the service technician in the field. The application allows the technician to read raw values from devices that have not yet been processed by the cloud, which can help the service technician troubleshoot the smart device. For example, the liquid flow sensor is stuck. After the service technician drains a certain amount of fluid through the python tube, a fault can be easily detected. A service mobile application is shown in
Figure 13.
In order for the service mobile app to connect to the device, a cloud service technician account is required to retrieve the secret key for the device so that no one can access it without authorisation. An additional security feature is the mobile application connection window of only 5 min after the device was powered on. This creates a new application layer that is the only access point for changing device parameters and prevents unauthorised access to the device through two-tier security.
Using the mobile application, it is possible to set all the internal parameters of the device as well as update the firmware running on the device. After launching the mobile application, it is necessary to read the public key of the smart device, which is located on the device in the form of a QR code, after which the application contacts the cloud to see if the service technician logged into the application has the authorisation to service the device. When the mobile application is connected and the smart device is in service mode, any action from the mobile device to the smart device must be signed with the public and private keys. Parameters that can be loaded and configured on the device are wireless connection settings, GSM connection settings, firmware update, manual device control, sensor constants, and cloud connection settings. Parameters that cannot be set, but only loaded, are real-time sensor data. All communication between the service mobile application and the cloud is done over an HTTPS connection via RESTful web services.
The service mobile application is not only used for service purposes but also for the regular maintenance of the device. The regular maintenance of the device mainly includes the sanitation of the device and calibration of the flow sensor of the device. During the periodic maintenance, which is required by the authorities, the service technician enters the date of maintenance and the actions performed through the application, which are sent to the cloud. In this way, the condition of the device is monitored and the organisation of the regular maintenance of the device is simplified. The regular maintenance of the device must take into account the flow that has occurred since the last maintenance, in addition to the time interval.