1. Introduction
Digital watermarking refers to a family of methods that embed a signal into a digital object. For example, visible logos in a TV broadcast or on a picture for sale on the web are two applications of visible watermarking. Nonetheless, digital technology allows for more complex applications of the general idea of watermarking, also allowing invisible (to humans) watermarks to be embedded into digital objects. Copyright protection, tracking origin, authentication, and integrity protection are examples of the application of this technology.
It is possible to classify watermarking algorithms according to various characteristics [
1]: the main properties of digital watermarking algorithms will be discussed in the following.
A first, trivial, subjective property of watermarks is imperceptibility, that is the inability of a human being to recognize the presence of a watermark embedded into an object.
A digital watermark may be robust, semi-fragile, or fragile. Robust watermarking refers to the embedding of a signal with the purpose of resisting malicious attempts aimed at its removal, maintaining the possibility to show the presence of the signal; a typical application of this kind of watermarking algorithms is copyright protection. On the other hand, fragile watermarks have the purpose of being altered by minimal modification of the digital object containing them; fields of application are integrity protection and authentication. The class of semi-fragile watermarking algorithms contains those methods that accept a minimal level of modification without flagging a tampering alarm.
On the detection side, watermarking methods may be grouped as informed (non-blind) or blind depending on the necessity or not of the original host object. Moreover, if an algorithm can recover the original data, it is called reversible; otherwise, it is called lossy or non-reversible.
The values of the watermark signal w may be embedded into the host object by modifying the object features in different domains; the most widely used are the spatial domain and the frequency domain (or transformed domain). The spatial domain refers to the values that describe and represent the object; as examples, for an image, they may be the pixel intensities; for a 3D model, they may be the vertices’ (spatial) coordinates. Instead, in the case of embedding in the frequency domain, the object’s data are first transformed with a linear transform, like the discrete Fourier transform, the wavelet transform, the singular value decomposition or the Karhunen–Loève Transform (KLT), then the watermark signal is applied to alter the transform coefficients; after that, the inverse transformation is applied to compute the modified values, which represent the watermarked object. In general, embedding in the frequency domain requires satisfying non-linear constraints (like obtaining integer pixel values or modifying only some parts of the transformed coefficient); thus, computational intelligence algorithms which look for almost optimal solutions in non-linear domains can be a possible embedding method.
Most of the 3D model watermarking works are focused on copyright protection (by inserting robust watermarks), while there are fewer works on integrity protection and authentication. Moreover, existing approaches to fragile watermarking introduce high distortion and/or might require extra information for verification. In this paper, we present a blind, non-reversible fragile watermarking algorithm that adds an extra level of security (by defining a secret embedding space through the KLT transform) and protects the integrity of 3D models, with negligible alterations to the host model vertices’ coordinates.
The host model original file format may be both textual or binary, but the watermarked model file is binary (as in many graphics file formats, like Blender).
The following section recalls some related works in the field of 3D model watermarking.
Section 3 and
Section 4 present two fundamental tools used by the proposed algorithm, discussed in
Section 5, to embed in a secure way a watermark in a 3D model.
Section 6 reports numerical results from experiments applying the method to publicly available models. The results are discussed in
Section 7, and some conclusions are drawn in
Section 8.
2. Related Works
The field of digital watermarking has seen a large development of methods for images and audio, but also the protection of 3D models has received attention from researchers. Several algorithms for robust (see
Table 1) and fragile (see
Table 2) watermarking of 3D models have been developed in recent years. Here, we report a list of the properties declared by the authors, along with their pros and cons.
Our proposed method shares a number of features with the literature and differs substantially in others: the main and more significant difference is the embedding space, which is secret and allows an extra level of security, as it is unfeasible for an attacker to reproduce such a space. Most of the related works in the literature are actually robust watermarking schemes, while our method is an extremely fragile method whose watermark is broken by negligible alterations to the 3D models it protects. Similarly to [
13], we modify the binary float representation of the vertices’ coordinates, but our watermark is not directly inserted into them, as done in [
13]. Moreover, the proposed method is immune to vertex reordering and can tolerate affine transformations to the model when these transformations are stored separately from the vertex coordinates in the output file format (such as done in Blender). Finally, similarly to [
20], we use a genetic algorithm to compute a (quasi)optimal solution to the embedding problem, but again, our watermark is embedded into a secret space and not directly into the vertices’ coordinates.
3. The Karhunen–Loève Transform
The discrete Karhunen–Loève Transform (KLT) (also called Hotelling transform or Principal Component Analysis (PCA)) is a linear transformation that maps vectors from one n-dimensional vector space to another vector space of the same dimension: this mapping is defined by a square matrix of size , called the kernel.
Differently from other linear transformations like the discrete cosine transform or the Fourier transform, one of the characteristics of the KLT is having a kernel that is not fixed a priori, i.e., its transformation matrix is computed from a set of vectors that must be given to define the mapping.
This characteristic of the KLT is exploited in the present algorithm to have a compact, secure, and efficient way to define a secret space of embedding: if the set of vectors used in computing the KLT kernel is kept secret, then also the kernel will be secret, defining a transformed domain in which to embed the watermark securely; for example, using a secret image’s pixel values to define these vectors, then only the entities possessing this image will be able to verify the integrity of the 3D model. Moreover, lacking knowledge of the embedding space does not allow modifying the 3D model without altering the fragile watermark.
Consider a set of vectors
of an
n-dimensional vector space, and compute their mean vector
. Then, evaluate the covariance matrix of the centered vectors
, where
represents the conjugate transpose of
. The eigenvectors
, of the covariance matrix
, computed as:
define an orthonormal basis for the
n-dimensional vector space; the
s are the associated eigenvalues. Thus, arranging the eigenvectors as rows of a matrix
in descending sort order of the respective eigenvalues, the KLT
of a vector
is computed as:
Each element of the vector is called the coefficient of the transform; the position of every coefficient in the vector is called the order of the coefficient.
It is possible to reverse the transformation process through the inverse KLT:
which, by the orthonormality of
, may be also written as:
One property of the eigenvectors is that they define the directions of maximum data spread in the data sample, and sorting them according to their associated eigenvalues allows exploiting the energy compaction property of the KLT transform, useful when expressing the elements of the vector space with a reduced number of coefficients: it may be shown that the eigenvalues represent the variance of the coefficients in each dimension.
For more details on the KLT, see [
21].
4. Genetic Algorithms
A Genetic Algorithm (GA) is a computing paradigm that simulates, in a simplified manner, the evolution and selection processes of natural species.
It may be used in solving non-linear optimizations problems when they may be coded in a set of parameters, and it is possible to define a function, called the fitness (function), that measures how close a solution is to the optimum.
A set of instantiated parameters describing the problem at hand is called the individuals: these parameters are put in a sequence similar to a chromosome, which is distinctive for its individual and defines it. Moreover, a fitness function is defined to evaluate the quality of the individual in terms of approximating the optimal solution.
A set of individuals, i.e., a population, is evolved in a way similar to the development of natural species. They mate, reproduce, and possibly have random modifications of their genes.
A chromosome codes a sequence of parameters, typically binary or integer numbers or a mix of them (but any type of data could be used in principle) with the constraint that the operations on them keep the data types consistent in the resulting chromosomes.
A population of individuals is created and (randomly) initialized; in general, a population of a hundred chromosomes is considered adequate.
Then, the GA goes through an iterative process, and in every cycle, the population is evolved according to the following steps:
selection: pairs of individuals are mated for the following reproduction operation; individuals may be selected randomly or given priority depending on fitness; many strategies can be adopted, like roulette wheel or tournament selection [
22];
crossover: the previously selected pairs of chromosomes are mated by exchanging some (homologous) parts of their chromosomes with probability ; one or more “cutting” points are randomly chosen, and the genes between pairs of such points are exchanged to define two new offspring;
mutation: with the aim of better exploring the solution space, each chromosome is mutated with probability ; mutation is performed by choosing at random one of the parameters coded in the chromosome and altering it by a random quantity;
population update: to generate a new population and to keep the number of individuals constant, a selection among the individuals in the set composed by the old population and the new offspring should be performed; many different strategies could be adopted, e.g., two individuals in the set are randomly chosen, and the one with the best fitness is moved to the new population, repeating this process until the output population reaches the desired cardinality.
The described cycle is performed until a termination condition is met. In general, to avoid infinite cycles, an upper limit to the number of generations is fixed. Furthermore, the cycle may be terminated when at least one of the individual’s fitness drops below (in this case, the lower the fitness, the better the individual) a pre-defined threshold. In both cases, the GA returns the best individual, representing the near-optimal solution it was able to find. For a deeper insight into GAs, see [
22,
23].
As will be shown in the following
Section 5, to minimize the embedding noise due to watermark embedding, the watermark bits are stored, modifying the less significant part of the floating point numbers representing the 3D model vertex coordinates. This is obtained by considering the bytes encoding these floating point numbers as unsigned integers and changing the less significant bytes. This mode of operation results in a minimization problem in a non-linear space, a task where GAs, among other algorithms, are flexible and efficient to implement and apply.
5. The Proposed Algorithm
The developed algorithm has the objective to protect the shape and the structure of a 3D model, defined in terms of a mesh of polygons, providing a verification that allows for identification and localization of modifications to the model. In particular, the algorithm that will be presented in this section will protect:
vertex coordinates (i.e., the geometry of the model);
the polygon structure, as defined by the corresponding vertex connections (that is, the topology).
In the present embodiment, vertices’ normal vectors are not considered because it was found that some 3D modeling software (e.g., Blender) alter them according to vertices’ positions; thus, authentication data would be obsoleted by the modeling software at saving or loading time, inducing our verification procedure to flag vertices as forged. Nonetheless, protecting vertices will have as a side effect the protection of normals computed from them.
To allow modifications that maintain the structure of the 3D model to the file representing it, the proposed method permits order alterations to the vertices and to the polygons as they are stored in the file. This provides independence, to some extent, from the particular file format.
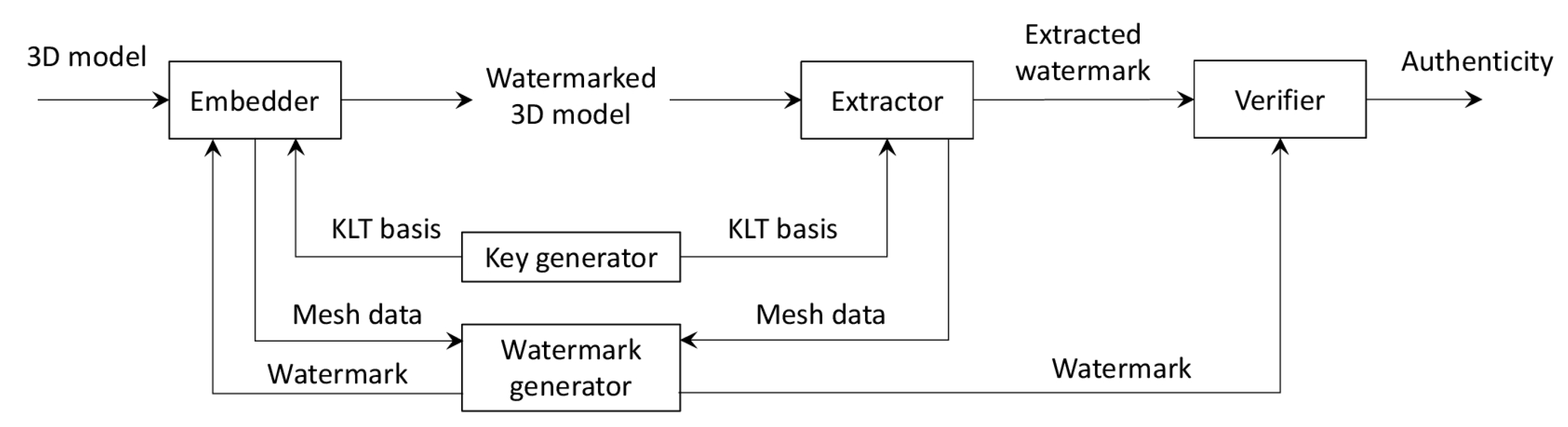
The method is composed of two main modules, namely an embedder and an extractor, and three companion modules, which are a key generator, a watermark generator, and a verifier. The interactions between the modules and the main data interchanged are shown in
Figure 1.
Each vertex is considered an Embedding Unit (EU); in the present embodiment, the vertex is defined by three spatial coordinates (
) and by the polygons to which the vertex belongs; a detailed description of this structure and of the embedding procedure will be given at the end of this section and in
Section 5.2. The use of the EU concept solves the problem in 3D models that is not present in audio and image samples, that is the lack of the total order of the vertices.
A bird’s eye-view of the various modules is the following:
Key generator: defines a secret KLT basis to specify an embedding space;
Watermark generator: creates the watermark bit string to be stored in each EU;
Embedder: stores the watermark in the 3D model, one vertex at a time, using the KLT basis and the watermark provided by the respective modules; a computational intelligence technique, described in
Section 4, is used to alter the vertex components so that the KLT coefficients of the vertex data contain the watermark; the output is a 3D model storing the fragile watermark;
Extractor: extracts the watermark present in a 3D model using the secret KLT basis provided by the key generator module;
Verifier: compares the extracted watermark with the one that should be contained in the vertices, providing the localization of tampered areas.
The input data are a 3D model composed of a set of vertices and a set of polygons. Each vertex is defined by three coordinates (); every component value is considered in binary format, float representation (four bytes) in the IEEE 754 format. Every polygon is defined by the sequence of the indexes of its vertices. The watermark Embedding Unit (EU) is defined by the vertex data () along with a combined fingerprint of the t polygons to which the vertex belongs.
The fingerprint of a polygon is computed as follows: for every pair of vertices
encountered on the perimeter, a cryptographic hash (c. h.) function
H is computed,
; thus, for a polygon of
n vertices,
n cryptographic hashes will be obtained
. To be independent from the starting vertex, these hashes are XORed
, then a c. h. is computed on the result
q; the value
is the fingerprint of a polygon. Finally, a combined fingerprint
F is obtained by XORing (to be independent from the order of the polygons considered) the fingerprints
of the
t polygons the vertex belongs to:
The c. h. function H used is MD5, whose hash length is 16 bytes.
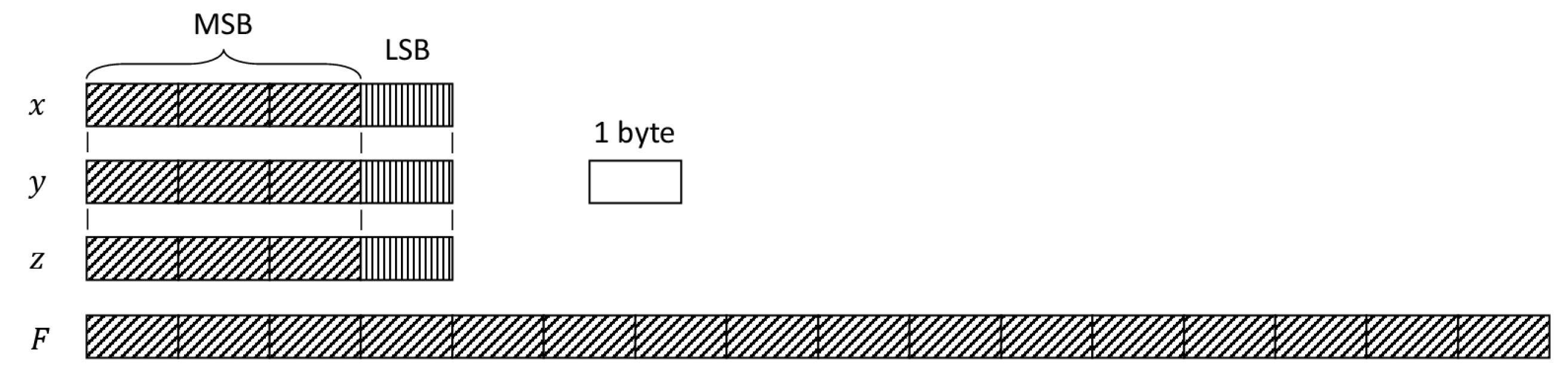
Thus, the EU is composed of
(all floats, each one occupying four bytes) and a fingerprint
F (bit string, 16 bytes), making 28 bytes in total (see
Figure 2).
In
Figure 2, note the bytes marked with vertical stripes: they are the least significant bytes of the mantissa of each float value. The watermark is embedded altering only those bytes; it follows that the polygon hashes do not take into account those bytes in the computation, i.e., if
is the operator that extracts the three most significant bytes, then given two vertices
and
, the c. h.
is:
where the symbol | means string concatenation.
Note that the algorithm can cope with more data related to each vertex, for example uv coordinates: it is sufficient to add them to the EU and modify the KLT basis size.
5.1. Key Generation
The key generator module has the objective to create a secret orthonormal basis to define a secret space of embedding. This space must be known to the embedder and to the extractor; thus, the key generator must provide the basis to both of them during their operations.
In principle, any secret orthonormal basis of the required dimension (in the present embodiment, 28) would suffice; nonetheless, the KLT provides a method to define a basis starting from a set of vectors, so we found that using a secret image to derive a set of vectors from which to compute a KLT basis was a flexible and viable solution.
5.2. Watermark Embedding
The watermark string
w to be embedded into an EU is derived by the key generator module from the fixed part of the EU itself, i.e., the diagonal striped bytes in
Figure 2. This string can be computed as the MD5 hash of the aforementioned data: from the resulting 128 bits, a predefined subset is extracted for embedding. Note that this step is not strictly necessary because the watermark is embedded into a secret space, as will be discussed in the following; thus, also a constant
w bit string would suffice; nonetheless, a variable
w further improves security.
A high level description of the algorithm is the following.
The fragile watermark is stored in the coefficients of every EU KLT: the 28 bytes of the EU are considered as 28 non-negative integer pixel values, which are KLT transformed, producing 28 coefficients. If
m is the payload in bpv (bits-per-vertex), i.e.,
m is the length of the watermark
w for every EU, then a subset of
m KLT coefficients is chosen a priori to store the watermark bits. In the present implementation, a coefficient
c is considered as carrying a watermark bit
b in position
p (the
p value is a parameter of the algorithm) iff:
(see [
24] for a deeper discussion on various methods for embedding the watermark bits into a set of coefficients).
The GA alters the values of the vertical striped bytes in
Figure 2 until the watermark is embedded into the EU KLT coefficients, i.e., if
is the EU, the GA alters
(the vertical striped bytes) so that the predefined coefficients in
contain the respective
m bits watermark. The reason for using a GA in this task is its ability to find the solution of a non-linear problem (bytes representing integer values) looking for the (local) minima of the error w.r.t. the original data.
Referring to Equation (
7), the present implementation of the algorithm considers the first
m coefficients among the 28 transform coefficients and embeds into the bit in position
.
When all the EUs have been processed by the GA, the 3D model with the new modified coordinates contains the fragile watermark allowing for the integrity check by the modules presented in the following section.
5.3. Watermark Extraction and Verification
The extraction of the watermark starts with building the EU for every vertex. Using the KLT basis from the key generator module, 28 coefficients are extracted from every EU: from the subset of coefficients used for watermark embedding, the watermark bits are computed using Equation (
7) and stored in a string
. Note that this operation requires the computation of a forward KLT; the inverse KLT is not used in the proposed algorithm.
After that, the watermark generator module is called for every EU, producing a watermark string w for each of them.
At this point, the verifier module compares the two strings and w for every vertex: if the strings are equal, then the vertex is marked as authentic; otherwise, it is flagged as potentially forged.
The possible forging of a 3D model represented as a set of vertices connected to form polygons may be done by altering or modifying:
at least one of the coordinates of a vertex, or
removing, replacing, or adding a vertex to a polygon, or
shuffling the order of the vertices on the perimeter of a polygon.
According to the integrity protection provided by the proposed algorithm, a vertex can be detected as tampered if:
at least one of the coordinates
has been altered: in this case, if only the lower part (the vertical striped bytes in
Figure 2) of one of the values is modified, then the vertex alone will be flagged as tampered; if the higher part is altered, then the vertex itself and all the vertices belonging to the polygons containing the vertex will be detected as tampered.
one of the polygons containing it is altered, that is:
one of its vertices has been modified in the higher part of the coordinates, or
at least one of its vertices has been substituted by another vertex, or
the order of the vertices on the perimeter has been changed (comprising the clockwise or anti-clockwise order), or
the number of vertices has been changed;
it has been removed from one of the polygons it belongs to, or
it has been added to a polygon (even duplicating a polygon).
6. Experimental Results
This section summarizes the results of a number of experiments we executed to test the performance of the proposed algorithm. In order to measure the resulting quality, we considered four objective parameters, namely the sensitivity, the Mean Absolute Error (MAE), the Root Mean Squared Error (RMSE), and the Peak Signal-to-Noise Ratio (PSNR). Indeed, the sensitivity gives a measure of the capability of the algorithm to detect tampering attacks. Thus, the meanings of the parameters used to measure the performance of the proposed algorithm are:
Sensitivity (defined as in [
24]): the sensitivity of level
is defined as the fraction of vertices that are detected as tampered in the verification phase when one byte of each EU is modified by
; this is a very powerful fragility measure, in particular for small values of
as one or two, because it is actually the least tampering an attacker can perform: any other attack, such as noise addition, adding, removing, or shifting vertices or surfaces, etc., would modify the mantissa values of the vertex coordinates of more than just
;
Mean Absolute Error (MAE): measures the average absolute difference between vertex attributes of the host and the watermarked model,
where
scans the set
of all vertices,
c scans the set
of the attributes that can be modified by the embedder (i.e., in the present embodiment
), the
symbol refers to the modified attribute in the watermarked model, and the function
returns the cardinality of a set;
Root Mean Squared Error (RMSE): measures the distortion between vertex coordinates of the host and the watermarked model,
where
represent the modified vertices and the operator
computes the Euclidean distance;
Peak Signal-to-Noise Ratio (PSNR): measures the distortion with respect to the maximum elongation of the vertices from the centroid of the model,
where
represent the modified vertices,
is the centroid of the host model, and the operator
computes the Euclidean distance.
We chose a setting for the genetic algorithm to be used in all experiments; in particular, we derived the setting values from many experiments devised to have fast convergence to a solution resulting in a high quality watermarked model. The settings were population size = 300, , , maximum generations = 2000.
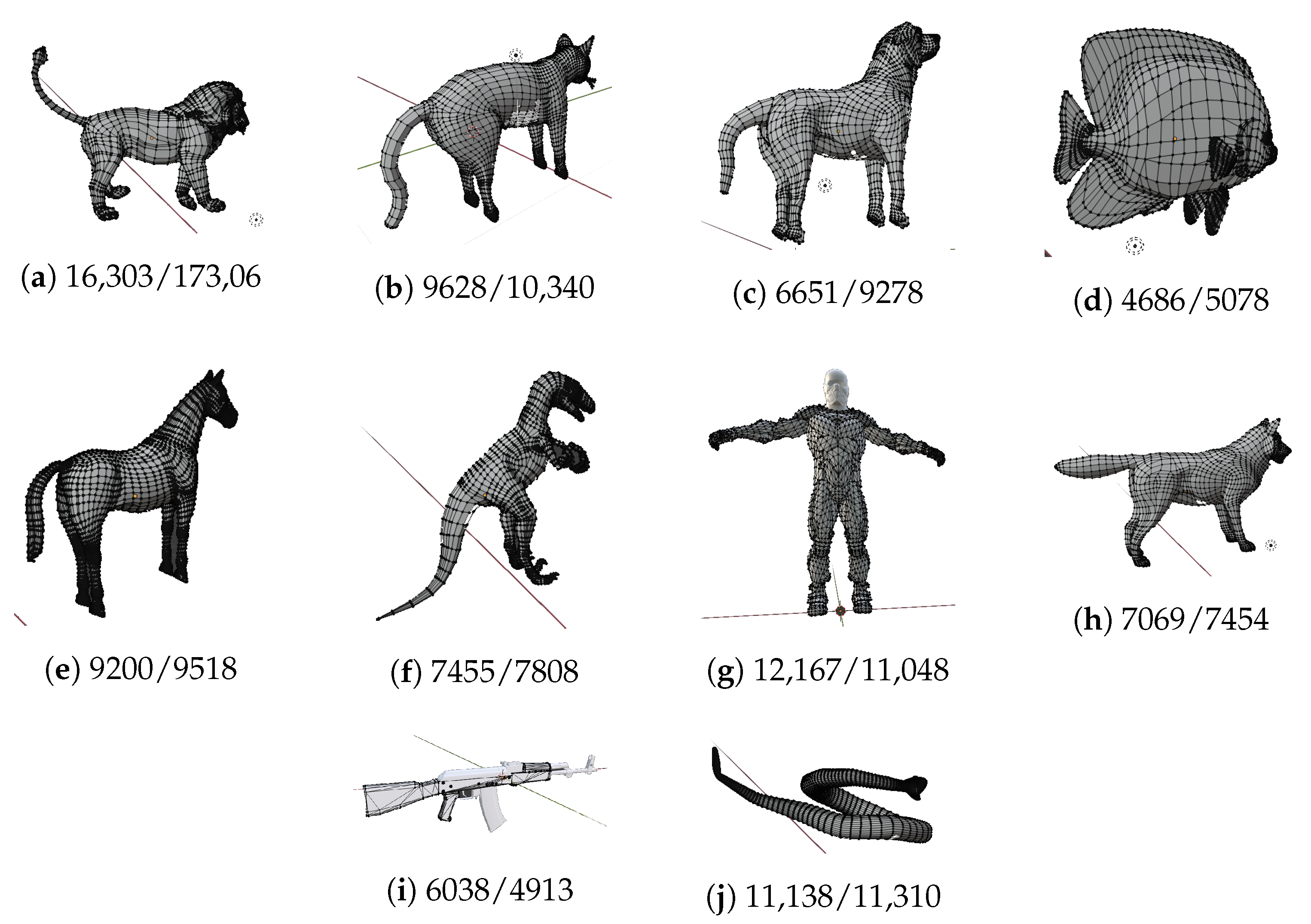
We ran the embedding algorithm on ten 3D models (shown in
Figure 3), and the objective results are reported in
Table 3. The payload in all experiments was set to 5 bpv.
From
Table 3, it can be seen that, given the very high values of sensitivity for small modifications (more than
of vertices detected when altering them by only
in one of the bytes of their coordinates), the proposed algorithm is highly reliable in tampering detection, i.e., it is very fragile. Moreover, the very small values of MAE and RMSE and the very high values of PSNR proved that the 3D models underwent a negligible modification, which may be generally accepted apart from specific applications, in which case we think that a reversible algorithm should be applied (but this is not the objective of the present proposal).
As concerns the complexity of the proposed method, let us consider separately the preprocessing phase, the embedding phase, and the verification phase. During preprocessing, for every vertex, a signature of the polygons to which it belongs is computed. In the worst case scenario, a vertex is connected to all other vertices, so this computation would take time, where n is the number of vertices. The embedding phase, instead, is linear in the number of vertices of the model, and it is upper bounded because the GA is run for a given predefined number of generations. Finally, the verification phase is very fast, and again, it is linear in the number of vertices (it usually takes a few hundreds of milliseconds on a standard laptop).
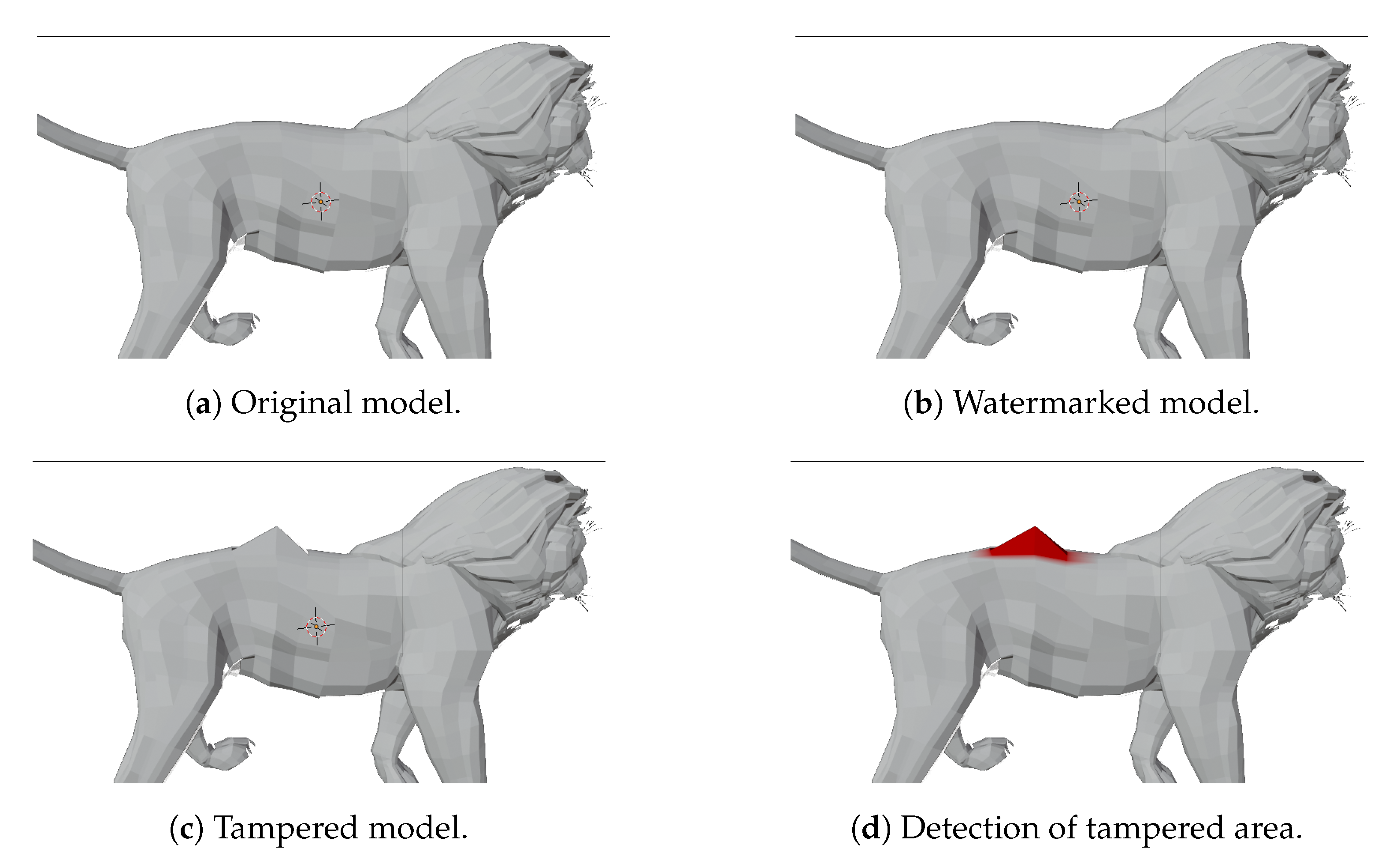
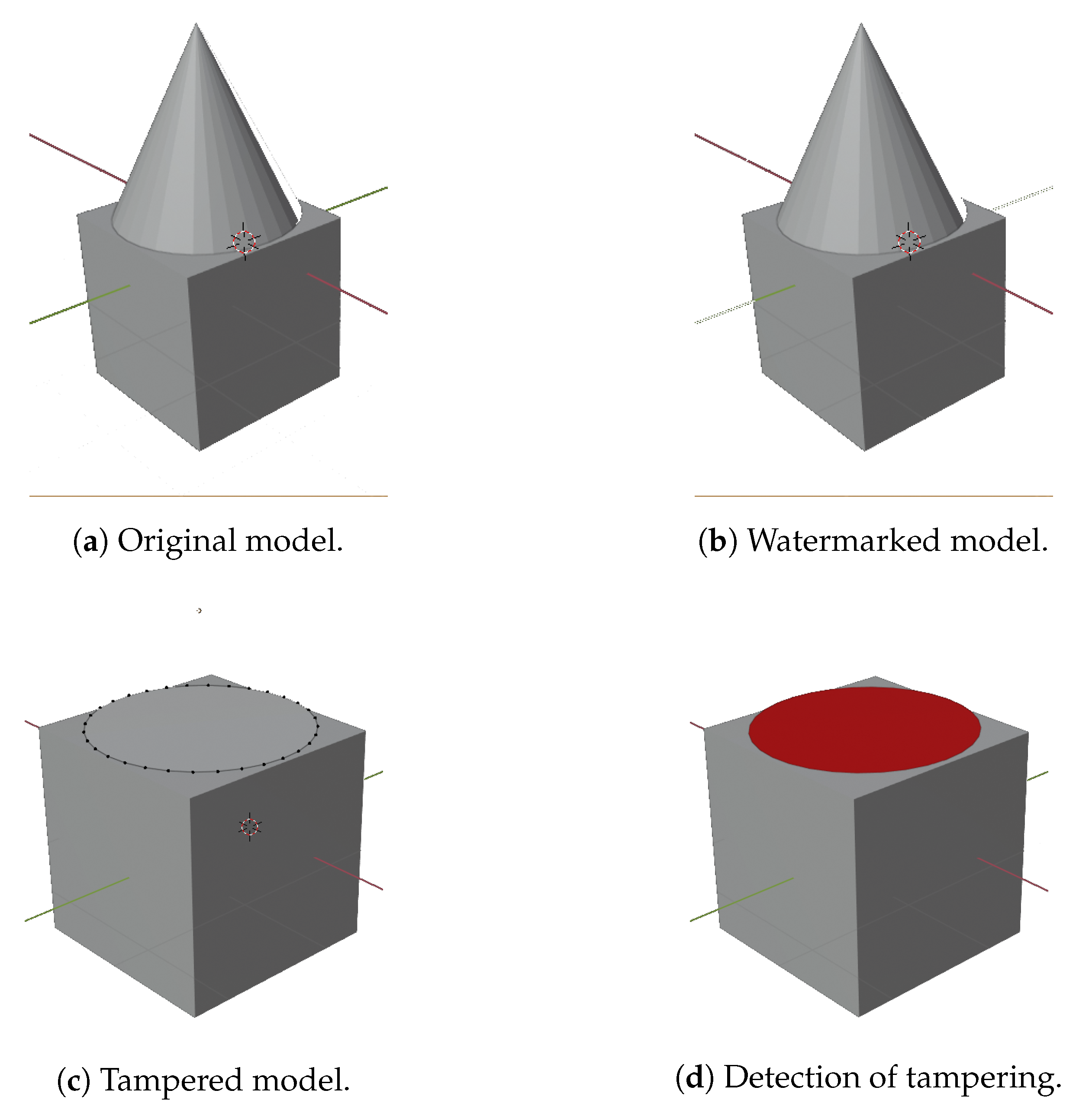
One of the original models (lion) is shown in
Figure 4a. To present how the algorithm operates on the model from a subjective point of view, in
Figure 4b, the same model after the fragile watermark embedding is reported.
An example of tampering is shown in
Figure 4c, and the resulting tamper detection highlights the modified vertices in red color, as can be seen in
Figure 4d.
To give more insights into how the algorithm detects tampering, we report a simple model in
Figure 5a and show how the removal of a single vertex (
Figure 5c) from the watermarked model (
Figure 5b) results in a detection (
Figure 5d) that highlights all the vertices contiguous to the removed one; these vertices are marked as forged because, as said in Item 2. of
Section 5.3, the polygons containing them were altered: indeed, they were removed, deleting the vertex in the cone apex.
Comparison with Related Works
Among the related works, we selected for comparison the ones that reported numerical (objective) measures of distortion introduced by their algorithms, as there were no visible modifications to the model after watermark embedding. It should be pointed out that an exact comparison was not really possible as every paper used different sets of models with respect to one another, so we only compared with the best results they reported. Moreover, we emphasize that there were not many works on fragile watermarking reporting parameters to compare to in a fair way.
All in all, we can say that our proposed method was superior to all the compared methods in terms of quality (in many cases, more than two orders of magnitude of the considered measure) of the resulting models and the fragility of the watermark.
In [
14], the authors reported the best PSNR value of
dB, which was far less than the smallest PSNR (>299 dB) our algorithm produced.
In [
12], the authors reported distortion (the same as our MAE values) for various settings of their method’s parameters; again, an exact comparison was difficult for two main reasons. First, the set of models they used was different from our set, and the model precision was
, whereas the precision of our models was
. Anyway, their best result was
, which was worse than our worst result (horse,
) by one order of magnitude. In [
18], the same authors reported a distortion of
, four orders of magnitude worse than our distortion results.
In [
10], the authors reported a mean distance error (averaged over five models) of
, which was two orders of magnitude greater than the mean distance error (averaged over 10 models) computed by our models (
).
In [
15], the authors reported an average RMS error (
) that was two orders of magnitude greater than our reported RMSE (
), while our
RMSRatio (
) was comparable with theirs. It should be pointed out, anyway, that our payload (five bits per vertex) was five times that of [
15], but the distortion induced was the same. Moreover, the work in [
15] had the disadvantage of requiring the centroid of the original model to perform the integrity verification, thus requiring out-of-band information to be kept per-model.
In [
20], the authors reported an average (over five models) SNR of
dB that was far smaller than our average (over 10 models) SNR of
dB.
Finally, we performed several other experiments on the same models with different precisions, and in general, we could say that the proposed method resulted in a distortion that was in the order of of the precision of the original model.
7. Discussion
The proposed fragile watermarking algorithm for 3D models performed a watermark bit string embedding by modifying the least significant part of some vertices’ attributes (in the present embodiment, coordinates): the watermark was stored in a secret space defined by a secret KLT basis and protected the integrity of the structure of the 3D model, that is the polygon mesh and the vertices of these polygons. Thus, the security of the method lied in the secrecy of the vectors used to derive the KLT kernel.
The main advantages of the method were:
the proposed method was very general because it worked on single vertices and may be extended to protect any number of vertex attributes (like normals, texture properties, etc.), even without modifying the KLT basis size: for example, by applying the cryptographic hash function also on these attributes and XORing the result to the fingerprint F;
the watermark was embedded into the vertices without tying to a particular representation of the model, i.e., vertices could be changed in order as long as the polygons were updated accordingly;
modifications to the data were limited to the least significant bits of the mantissa value, so keeping the relative error as small as possible;
affine transformations to the 3D models were allowed (no tampering was shown), as long as they were represented and stored as matrix operations to be applied to vertex coordinates (this is the default Blender behavior).
At the same time, the disadvantages of the method were:
a slight change to the vertices’ coordinates was performed;
if a vertex was duplicated in the 3D model, after watermark embedding, two vertices with different coordinates and/or normal components would be created; thus, small holes or changes in illumination in the vertex area were created; this issue could be solved by recognizing coincident vertices and modifying them in the same manner during watermark embedding; it was possible to perform this action because it was highly probable that both vertices allowed for an equal modification embedding different watermark strings.
Security Considerations
The security of the method was based on the secrecy of the KLT basis. Thus, this set of orthonormal vectors constituted the secret key. This basis may be derived from any sample of vectors belonging to a vector space of the right dimension: in our case, the EU was composed of 28 bytes; thus, the vector space should be of dimension 28.
For example, considering a grayscale image and building vectors from pixel values taken in raster scan order allowed the computation of a covariance matrix from which to derive an orthonormal basis (as shown in
Section 3): if the image were kept secret, so would be the KLT basis and consequently the embedding space of the watermark bit string. This prevented an attacker from creating forged vertices embedding a correct watermark given that she/he would not know the kernel basis of the transform.
If the length of the watermark stored in each EU were m bits (i.e., the payload was m bpv), then the probability that a forged vertex would not be detected as such would be . Nonetheless, as previously said, if the modification were in the higher part of the vertex data, then all the polygons sharing that vertex would detect the modification: given that for each polygon, the probability to fail detection would be , if the forged vertex were shared amongst k polygons, then the probability that the tampering went undetected by all polygons would be .
8. Conclusions
The proposed method performed an integrity protection of 3D models in a more secure embedding space of the watermark while reducing the distortion induced to the model. It applied a small modification to some attributes of the vertices of the model (in the current implementation, vertices’ coordinates, but it could be extended to other vertex features). The error introduced w.r.t. the original attribute values was in the order of
(average MAE for the models analyzed in
Table 3) and was not noticeable from the rendered model (as subjectively judged from a sample of 10 observers).
The security of the whole process lied in the secrecy of the KLT basis, which, in turn, was based on the secrecy of the vectors used to compute it. Public parameters of the algorithm were the cryptographic hash function, the payload m (in bpv), the orders of the m KLT coefficients, and the embedding position p.
As future work, we plan to extend the algorithm to protect other vertex attributes, like coordinates and normals.