E-mail-Based Phishing Attack Taxonomy
Abstract
1. Introduction
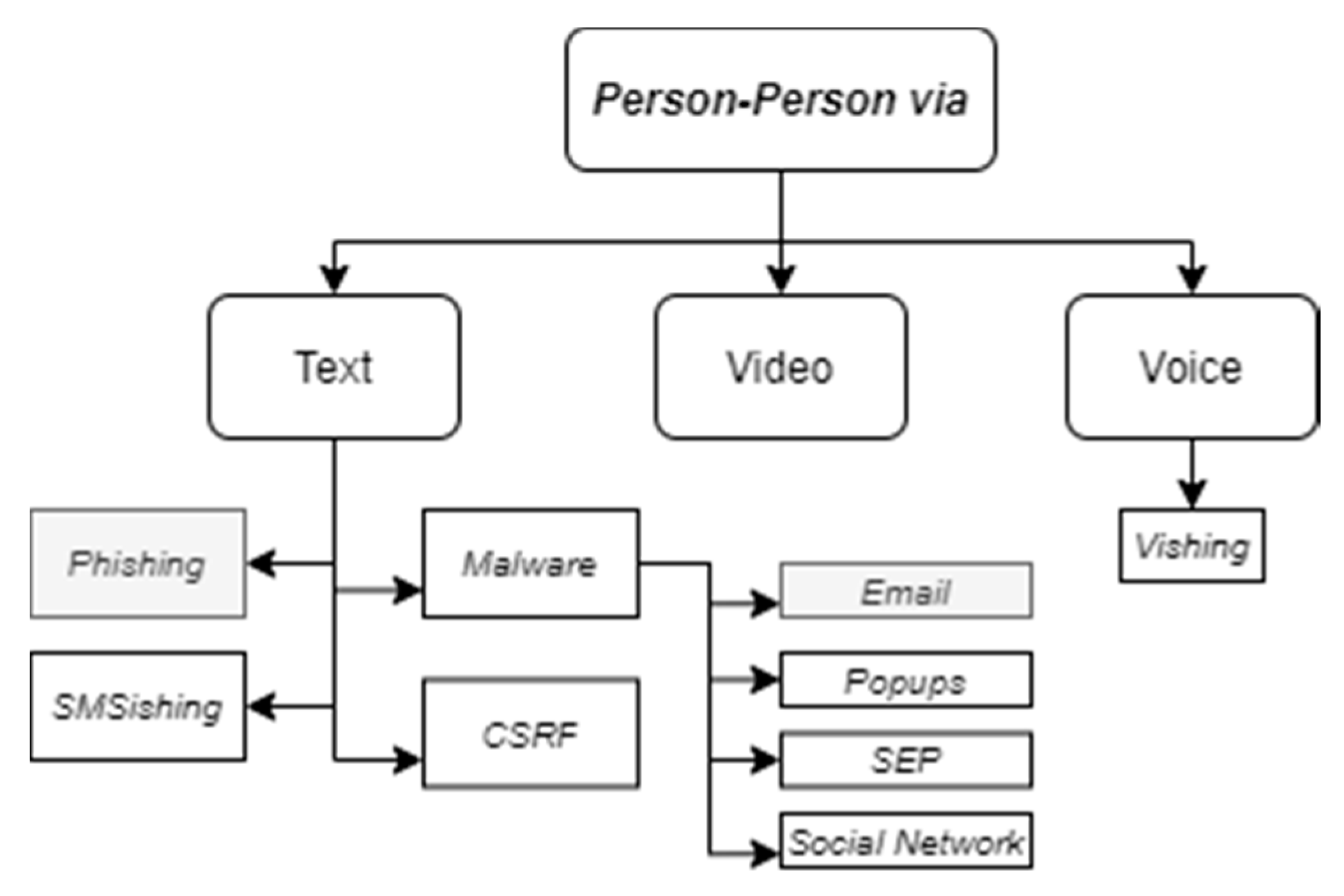
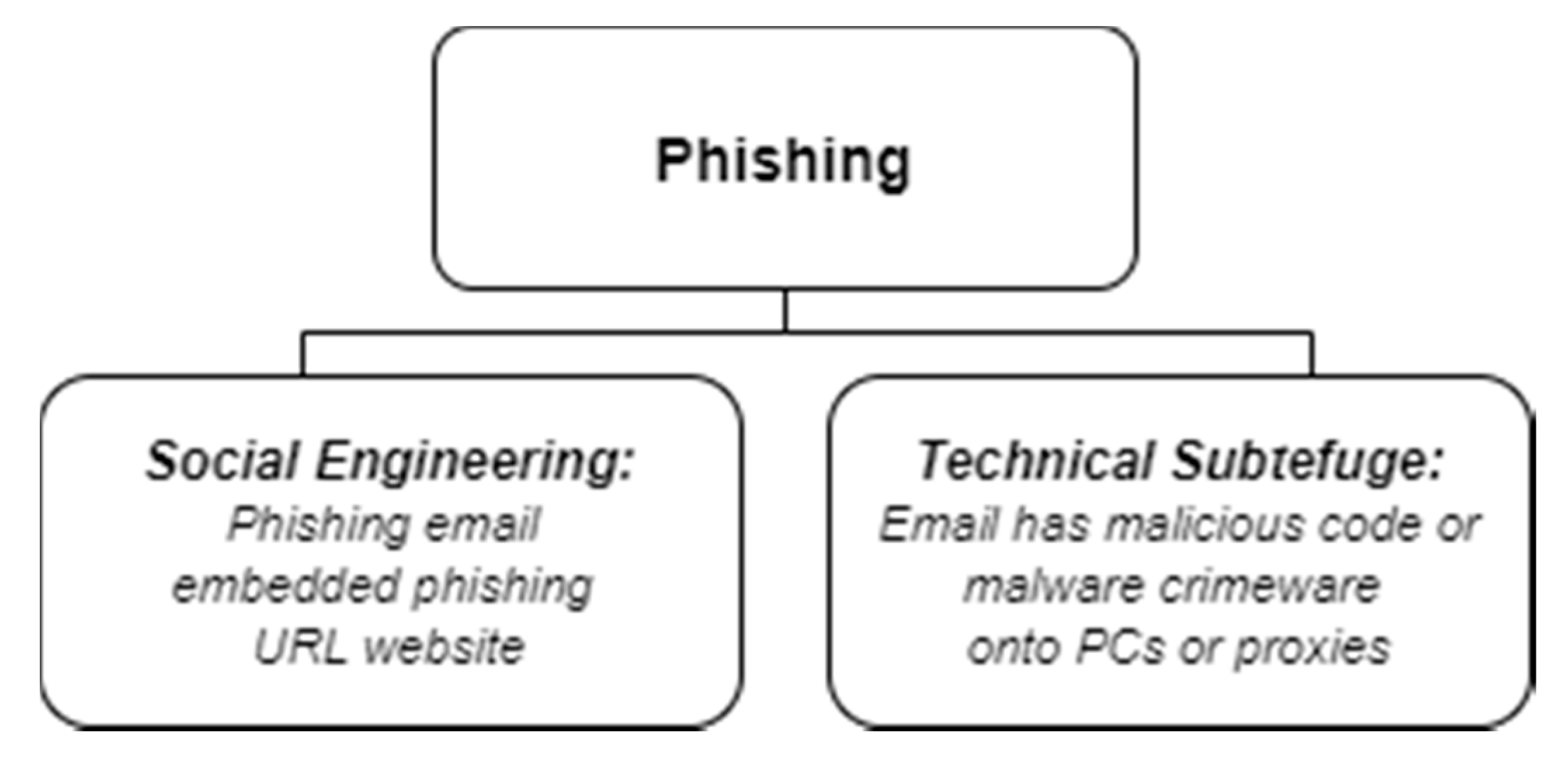
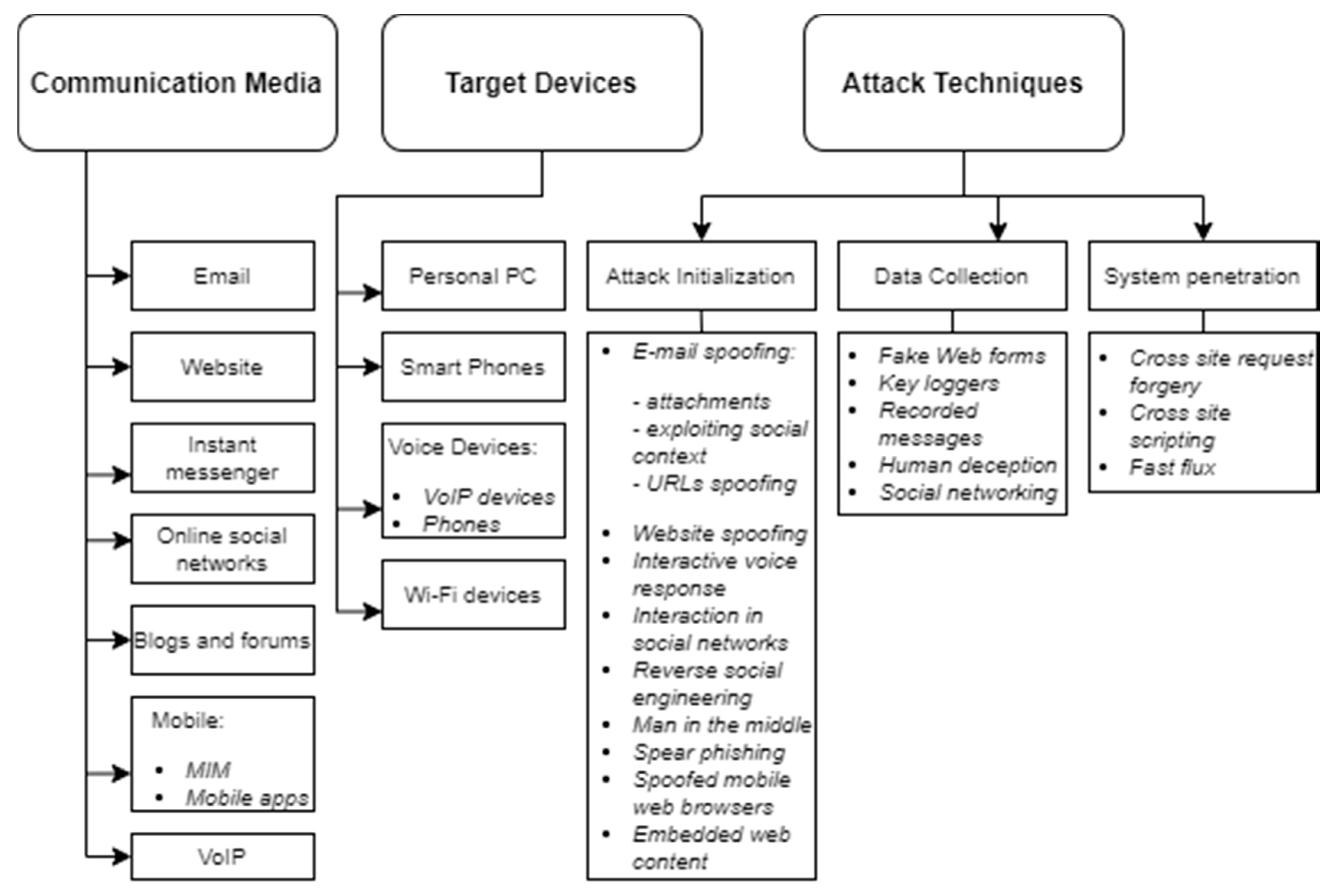
2. Related Works
2.1. Visualization Forms of Phishing Attack Taxonomies
2.2. The Content of E-mail Phishing Attack-Related Taxonomies
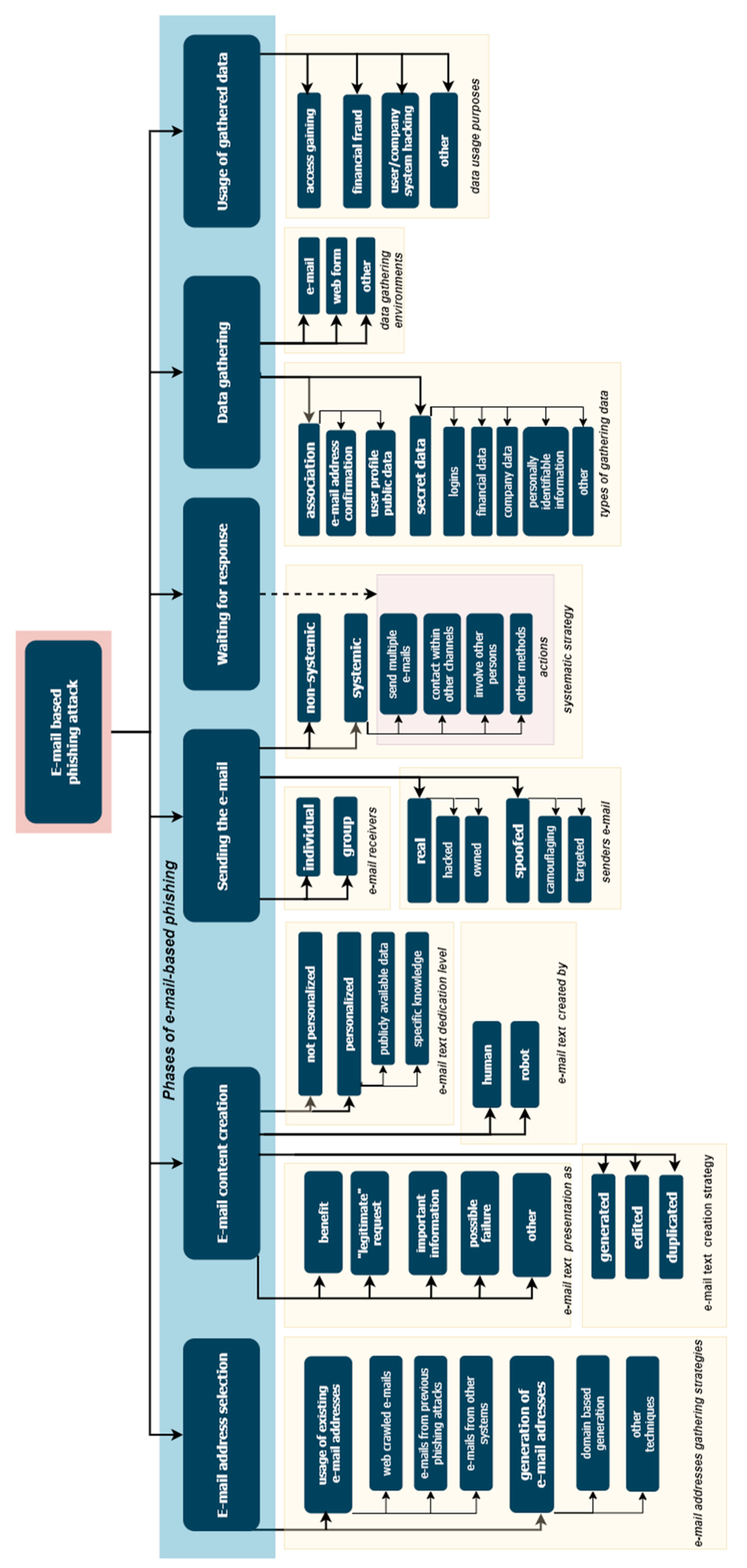
3. The Proposed E-mail-Based Phishing Attack Taxonomy
- E-mail address selection. To execute an e-mail-based phishing attack, an e-mail address or addresses of the potential victim have to be obtained. In this phase, different strategies for e-mail address selection are used; therefore, we divide the address selection phase into strategy types for e-mail address selection (two main classes with subclasses in each of them).
- E-mail content creation. The content and text of the e-mail for the phishing attack has to be prepared to involve the victim in the phishing attack. This phase is very important and can be classified based on multiple criteria. We define four criteria for e-mail content creation for a phishing attack: idea for victim involvement in the phishing attack; e-mail text generation strategy; e-mail text creator type; e-mail text personalization level. Each of these criteria can obtain classes.
- Sending the e-mail to recipients. The method of how the attacker sends the e-mail to possible phishing victims is an important factor. The selected phishing attack strategy is implemented by sending the phishing e-mails; therefore, we detail the e-mail sending phase based on three criteria: sender’s e-mail address usage; the number of recipients in the phishing attack; usage of systemic phishing attack strategy. Possible classes for each of the criteria are provided in the taxonomy.
- Waiting for the response from the e-mail recipients. In most cases, the attacker just waits for the victim to respond to the phishing e-mail. However, in the case of a systematic strategy of a phishing attack, some additional actions can be executed while waiting for the victim’s response. The possible categories of attacker’s actions while they wait for the victim to respond is a part of e-mail sending systematic strategy; therefore, the classes are shared between those two phases.
- Phishing attack results and data gathering. The main purpose of a phishing attack is to get some specific data from the victim. We recommend defining the phase of gathered data based on the data gathering environment as well as types of gathered data. Possible classes for these criteria are listed in the taxonomy.
- Usage of gathered results and data. While the usage of gathered data is a little bit out of the scope of this work, it is very closely related to gathered data; therefore, we highlight the phase of gathered data usage and list possible purposes the attacker might have by using the phishing-attack-gathered data.
- E-mail address selection strategies can be put into two main categories: usage of existing e-mail addresses and generation of e-mail addresses.
- ○
- The usage of existing e-mail addresses includes: web crawled e-mail addresses (obtained from listed e-mails in different web pages); e-mail addresses, gathered from previously executed phishing attacks (gathering of an e-mail address for phishing attack can be as a purpose of another phishing attack); e-mail addresses gathered from other systems or sources (some specific sources can be used to get an e-mail address for the prepared phishing attack).
- ○
- Generation of e-mail addresses is used as an alternative to the gathering of e-mail addresses if the selection of victims’ e-mail addresses is impossible. The most frequent case involves the generation of the most common e-mail addresses for a specific e-mail domain name (for example admin@domainname, sales@domainname, info@domainname, etc.). However, other different techniques to generate a possible e-mail address (a person’s credentials within different e-mail domain names, random sequences, etc.) are used too.
- Ideas for victim involvement in the phishing attack is the main element of any social engineering attack. We define the main factors that make the victim believe it is a legitimate request and requested data have to be provided:
- ○
- Benefit proposal motivates the victim to provide requested data to get some financial or another benefit from it. However, in most cases, the promised benefit is not provided, while the gathered data are used for different purposes.
- ○
- Impression of legitimate request does not involve additional questions requesting legitimacy, and the victim automatically sends the requested data. However, it is very difficult to generate such an e-mail text that provides a sufficient amount of detail about request management processes and internal data.
- ○
- Impression of an important event. The information request leads to stress for the victim; therefore, some victims do not analyze the e-mail with sufficient attention and proceed with a hurry to execute the requested actions, providing the requested data.
- ○
- Impression of a possible failure in the case of the data not being provided. This is a very similar strategy to the previous one as it activates the same emotions for the victim. At the same time, it is more focused on understanding the internal processes, as the attacker must know or imagine what kind of processes might be associated with failure if information is not provided by the victim.
- ○
- Other strategies are possible too. The phishing attack is much harder to identify if it uses some very specific weaknesses of the victim, as the traditional phishing attack e-mail texts are well known and are easy to recognize as a phishing attack.
- E-mail text generation strategy. In this strategy, the source defines how the e-mail text is generated. There are three main strategies:
- ○
- Generated—a new, case-specific phishing attack text. It might be time-consuming; however, is harder to identify it as a phishing attack by signature-based e-mail filtering systems.
- ○
- Edited—the e-mail text is copied from another e-mail (legitimate or phishing attack e-mail), and some parts of the e-mail are changed (replacing the name of the recipient, etc.).
- ○
- Duplicated—the e-mail text is copied from other sources and is not changed at all.
- E-mail text can be created manually or by using automated solutions; therefore, we define two types of e-mail text creators:
- ○
- Human—e-mail text is written or changed by the person.
- ○
- A bot or computer—e-mail text is generated or modified by a computer program or bot.
- E-mail text personalization level is closely related to the e-mail text generation strategy, and we define two types of personalization:
- ○
- Not personalized—the e-mail text is very abstract, and no personal information is added in the e-mail.
- ○
- Personalized—the e-mail text includes some personalized information about the recipient or the e-mail. The emails can be personalized by using publicly available data (such as recipient’s name, surname, the title of the organization, etc.) or by using some specific knowledge (data about recent user’s visits, financial operations, etc.). In other sources, the use of personalized phishing attacks with publicly available victim data is called spear phishing, while personalized phishing attacks that use some specific knowledge and are usually directed to some higher position persons are classed as whaling attacks.
- The sender’s e-mail address is one of the main factors in identifying a phishing attack. The attacker can use his real or spoofed e-mail address:
- ○
- A real e-mail address uses no specific techniques to change itself. The attacker might use hacked e-mail account or register and create an untraceable e-mail account for phishing e-mail distribution.
- ○
- Spoofed e-mail addresses are changed to trick the victim by showing a specific e-mail address that is not possible to obtain legitimately. In some cases, the e-mail address is spoofed to mimic a specific, targeted e-mail address, while another type is e-mail address camouflage, where the aim is to generate a very similar e-mail address to a legitimate one, but no identical match is needed.
- The number of recipients in the phishing attack can be used for phishing attack identification and should be associated with the number of recipients only (not based on the text of the e-mail):
- ○
- Individual—the e-mail recipient is one address. Multiple e-mails are sent at the same time, but it is classed as individual if the victim can see his or her own e-mail address as the recipient.
- ○
- Group—the e-mail recipients are multiple e-mail addresses. The usage of multiple addresses might be an additional method to illustrate that the sender knows multiple, related e-mails in the organization or multiple e-mails of the same person or to stimulate concurrency between several victims to obtain trust before somebody else does.
- Usage of a systematic phishing attack strategy allows higher phishing attack success probability; however, it requires additional actions and knowledge about the victim:
- ○
- Non-systematic strategy requires no additional actions and usually involves sending one phishing attack e-mail and then waiting for the results.
- ○
- Systematic phishing attacks require additional actions and knowledge. The simplest case is the sending of multiple e-mails to the same victim by remembering or adding some additional information in the later e-mails. Another solution is to contact the victim through other channels (phone call, social networks, etc.). Other communication channels are used to remind the recipient about the e-mail or to motivate them to act and convince them of the legitimacy of the request. The motivation and convincing can be achieved by involving other persons too (contacting different persons individually and motivating them to collaborate or exchange information between them). There may be other specific cases (related to information publishing in the media, etc.) where some additional attacker actions are executed to implement attack strategy.
- Data gathering environment defines how the attacker gets the information and what kind of environment is used for it:
- ○
- An e-mail reply is one of the main victim actions, as it requires no additional investment for data gathering tools—the user replies to the received e-mail by providing requested data.
- ○
- Webforms are very popular too. The attacker creates a web page with a data input functionality. Some web sites are unique, while others mimic or spoof other systems and trick the user into thinking they are using a legitimate web site while submitting the data to the attacker.
- ○
- Other types of data gathering during phishing attacks are used too. Attackers can use social networks, phones, etc.
- Types of gathered data vary in different phishing attacks. We define the gathered information using two types:
- ○
- Association—data needed to generate the victim’s profile from publicly available data; however, because of the large quantity of related data, the data have to be associated, to ensure the integrity of the user profile. In some cases, the existence of such an e-mail is enough from the victim; in other cases, some publicly available personal data are gathered from the victim’s response.
- ○
- Secret data are more valuable in a phishing attack, but at the same time are harder to get from the victim. The phishing-attack-targeted secret data might include user credentials, the victim’s financial data, enterprise-related secrets, personally identifiable information (date of birth, social security number, etc.) or others.
- The purpose of phishing attack data usage is closely related to the type of gathered data during the phishing attack. The main categories are:
- ○
- Gaining access to a specific system. If login data are gathered during a phishing attack, the same logins might apply to gain access to this or even other systems of the same victim.
- ○
- Financial fraud is related to the victim’s financial and personal data. In some cases, the phishing attack leads to victim actions where the victim transfers their money to the attacker as a result of their belief that they are executing a legitimate money transfer to a different source.
- ○
- User/company system hacking is related to gaining access, but sometimes the phishing attack is oriented towards collecting specific data on enterprise management structure, used technologies, etc.
- ○
- Other types of purposes of the phishing attack exist; however, they are not as common and vary a lot; therefore, the other class was added to include all of them.
4. Validation of the Proposed E-mail-based Phishing Attack Taxonomy
4.1. Proposed E-mail-Based Phishing Attack Taxonomy Comparison with Existing Taxonomies
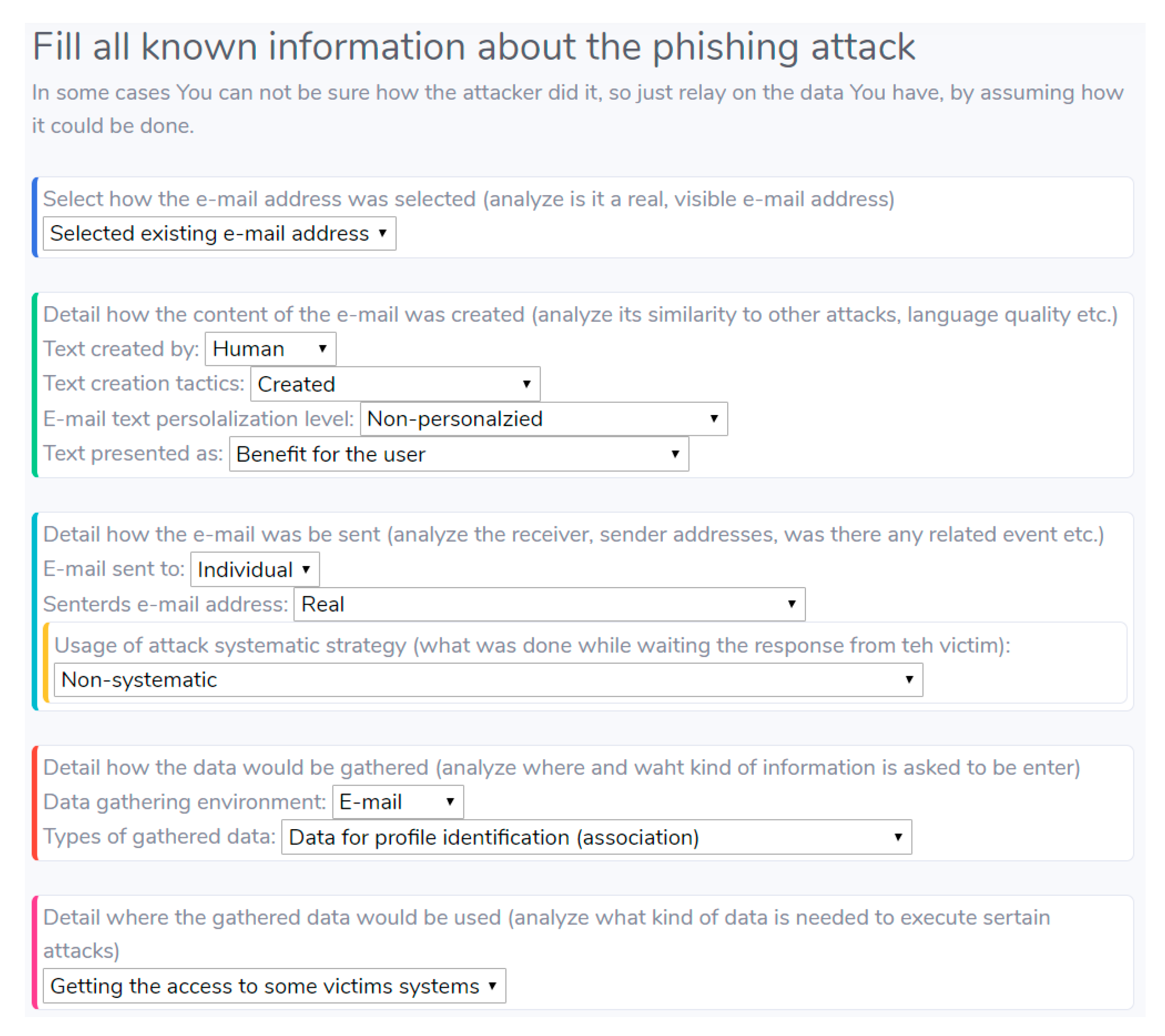
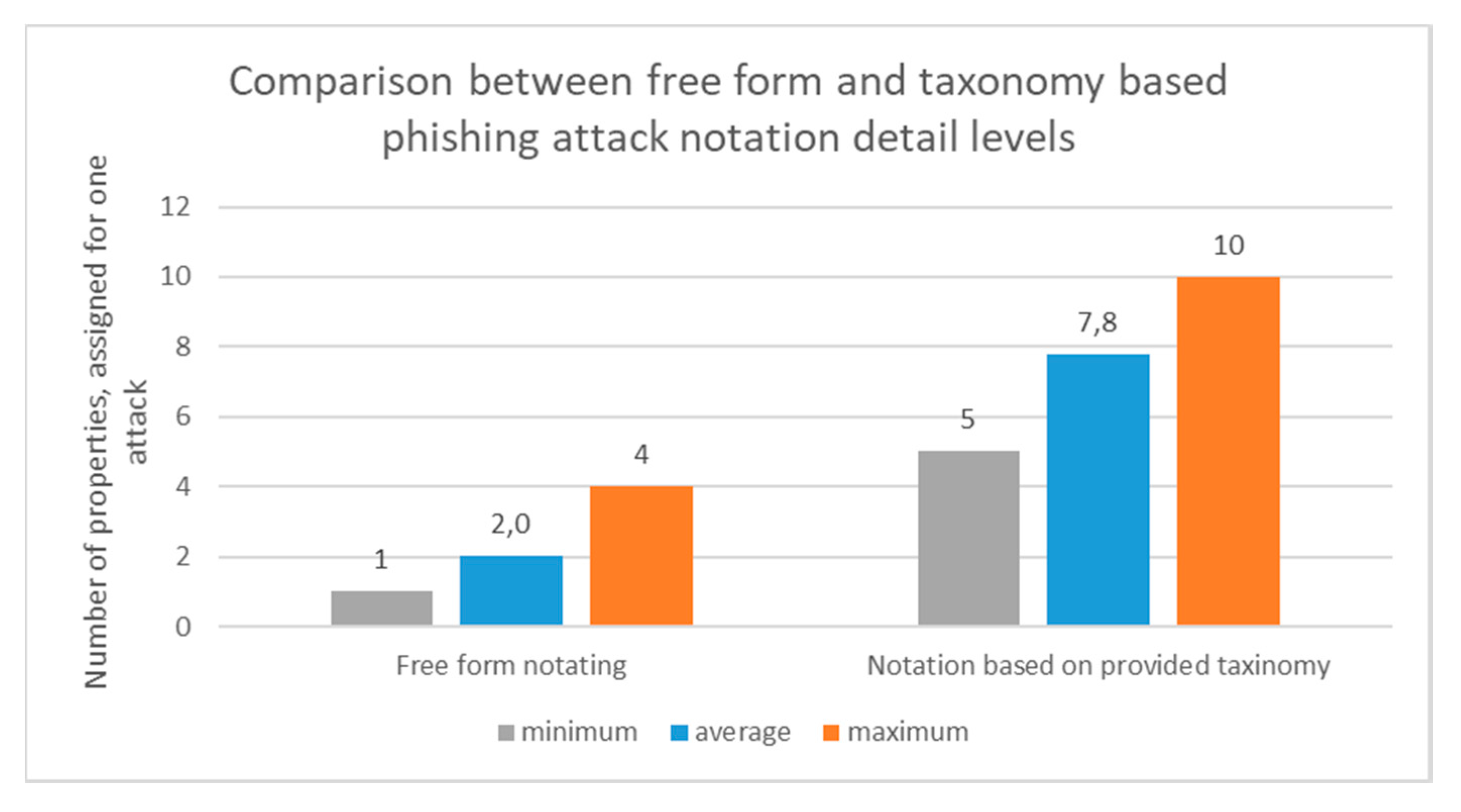
4.2. Phishing Attack Notating by Using Proposed E-mail-based Phishing Attack Taxonomy
- Unambiguity of assigned description—whether the description is understandable and needs additional explanation to another person or even machine to understand the description. The unambiguity can be evaluated by measuring whether the description is clear or uses blurry expressions.
- The detail level in the description—whether the description reflects all properties of the phishing attack and there is no need to analyze the e-mail again. The detail level can be evaluated by measuring how many different properties or categories are assigned to the phishing attack.
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Cybersecurity Threatscape: Q3 2019. Available online: https://www.ptsecurity.com/ww-en/analytics/cybersecurity-threatscape-2019-q3/?sphrase_id=70070 (accessed on 3 February 2020).
- Salahdine, F.; Kaabouch, N. Social engineering attacks: A survey. Future Internet 2019, 11, 89. [Google Scholar] [CrossRef]
- Garshol, L.M. Metadata? Thesauri? Taxonomies? Topic maps! Making sense of it all. J. Inf. Sci. 2004, 30, 378–391. [Google Scholar] [CrossRef]
- Medelyan, O.; Witten, I.H.; Divoli, A.; Broekstra, J. Automatic construction of lexicons, taxonomies, ontologies, and other knowledge structures. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2013, 3, 257–279. [Google Scholar] [CrossRef]
- Yeboah-Boateng, E.O.; Amanor, P.M. Phishing, SMiShing & Vishing: An assessment of threats against mobile devices. J. Emerg. Trends Comput. Inf. Sci. 2014, 5, 297–307. [Google Scholar]
- Grégio, A.R.A.; Afonso, V.M.; Filho, D.S.F.; Geus, P.L.D.; Jino, M. Toward a taxonomy of malware behaviors. Comput. J. 2015, 58, 2758–2777. [Google Scholar] [CrossRef]
- Miloslavskaya, N.; Tolstoy, A.; Zapechnikov, S. Taxonomy for unsecure digital information processing. In Proceedings of the 2016 Third International Conference on Digital Information Processing, Data Mining, and Wireless Communications (DIPDMWC), Moscow, Russia, 6–8 July 2016; pp. 81–86. [Google Scholar]
- Singh, M.M.; Siang, S.S.; San, O.Y.; Hashimah, N.; Malim, A.H.; Shariff, A.R.M. Security attacks taxonomy on bring your own devices (BYOD) model. Int. J. Mob. Netw. Commun. Telemat. (IJMNCT) 2014, 4, 1–17. [Google Scholar] [CrossRef]
- Chanti, S.; Chithralekha, T. Classification of Anti-phishing Solutions. SN Comput. Sci. 2020, 1, 11. [Google Scholar] [CrossRef]
- Hussain, N.; Turab Mirza, H.; Rasool, G.; Hussain, I.; Kaleem, M. Spam Review Detection Techniques: A Systematic Literature Review. Appl. Sci. 2019, 9, 987. [Google Scholar] [CrossRef]
- Gupta, B.B.; Tewari, A.; Jain, A.K.; Agrawal, D.P. Fighting against phishing attacks: State of the art and future challenges. Neural Comput. Appl. 2017, 28, 3629–3654. [Google Scholar] [CrossRef]
- Liu, H.; Lang, B. Machine Learning and Deep Learning Methods for Intrusion Detection Systems: A Survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef]
- Disha, D.N.; Rachana, N.B.; Kumari Deepika, N.S.G. Phishing & Anti-Phishing: A Review. Int. J. Eng. Tech. Res. (IJETR) 2014, 2, 278–283. [Google Scholar]
- Narwal, B.; Mohapatra, A.K.; Usmani, K.A. Towards a taxonomy of cyber threats against target applications. J. Stat. Manag. Syst. 2019, 22, 301–325. [Google Scholar] [CrossRef]
- Mohd Foozy, F.; Ahmad, R.; Abdollah, M.F.; Yusof, R.; Mas’ud, M.Z. Generic Taxonomy of Social Engineering Attack and Defence Mechanism for Handheld Computer Study. J. ICACT 2012. [Google Scholar]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Advanced social engineering attacks. J. Inf. Secur. Appl. 2015, 22, 113–122. [Google Scholar] [CrossRef]
- Ivaturi, K.; Janczewski, L. A taxonomy for social engineering attacks. In International Conference on Information Resources Management; Centre for Information Technology, Organizations, and People; Association for Information Systems, 2011; pp. 1–12. [Google Scholar]
- Pienta, D.; Thatcher, J.B.; Johnston, A.C. Taxonomy of Phishing: Attack Types Spanning Economic, Temporal, Breadth, and Target Boundaries. In Proceedings of the 13th Pre-ICIS Workshop on Information Security and Privacy, San Francisco, CA, USA, 13 December 2018; Volume 1. [Google Scholar]
- Gupta, B.B.; Arachchilage, N.A.; Psannis, K.E. Defending against phishing attacks: Taxonomy of methods, current issues and future directions. Telecommun. Syst. 2018, 67, 247–267. [Google Scholar] [CrossRef]
- Almomani, A.; Gupta, B.B.; Atawneh, S.; Meulenberg, A.; Almomani, E. A survey of phishing e-mail filtering techniques. IEEE Commun. Surv. Tutor. 2013, 15, 2070–2090. [Google Scholar] [CrossRef]
- Aleroud, A.; Zhou, L. Phishing environments, techniques, and countermeasures: A survey. Comput. Secur. 2017, 68, 160–196. [Google Scholar] [CrossRef]
- Beals, M.; DeLiema, M.; Deevy, M. Framework for a Taxonomy of Fraud; Stanford Longevity Center/FINRA Financial Investor Education Foundation/Fraud Research Center: Washington, DC, USA, 2015; Volume 25, p. 2016. [Google Scholar]
- Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A. Credulity to Phishing Attacks: A Real-World Study of Personnel with Higher Education. In Proceedings of the 2019 Open Conference of Electrical, Electronic and Information Sciences (eStream), Vilnius, Lithuania, 25 April 2019; pp. 1–5. [Google Scholar]
| Criteria | Classes | Disha et al. [13] | Pienta et al. [18] | Almo-mani et al. [20] | Kromb-holz et al. [16] | Aleroud et al. [21] | Gupta et al. [19] |
|---|---|---|---|---|---|---|---|
| Phases of the attack | E-mail address selection | + | - | - | - | + | - |
| E-mail text generation | + | - | |||||
| E-mail sending | + | + | + | ||||
| Waiting for response | - | - | - | ||||
| Data gathering | + | + | + | ||||
| Data usage | - | - | + | ||||
| E-mail address selection | Existing addresses | + | - | - | - | - | - |
| Generated addresses | |||||||
| E-mail text presentation as | Benefit for the user | - | - | - | - | - | - |
| Legitimate request | + | + | |||||
| Important information | - | - | |||||
| Possible failure | - | - | |||||
| Other | - | - | |||||
| E-mail text creation strategy | Created | + | - | - | - | - | - |
| Edited | - | ||||||
| Duplicated | - | ||||||
| E-mail created by | Human | - | - | - | + | - | - |
| Computer | |||||||
| E-mail dedication level | Not personalized | + | + | - | - | - | - |
| Personalized | |||||||
| E-mail recipients | Individual | - | + | - | - | - | + |
| Group | |||||||
| Sender’s e-mail | Real | - | - | - | - | + | - |
| Spoofed | + | + | |||||
| Systemic strategy | Non-systemic | - | - | - | - | - | - |
| Systemic | |||||||
| Actions while waiting for the response | Send multiple e-mails | - | - | - | - | - | - |
| Contact within other channels | |||||||
| Involve other persons | |||||||
| Other methods | |||||||
| Types of gathered data | Profile associations | - | - | - | - | - | - |
| Secret data | + | + | + | + | |||
| Data gathering environment | - | - | - | + | + | - | |
| Webform | + | + | + | + | |||
| Other | - | + | - | + | |||
| Purpose of gathered data usage | Access granting | - | - | - | - | - | + |
| Financial fraud | - | - | |||||
| User/company system hacking | - | - | |||||
| Other | + | + | |||||
| Criteria coverage, % | 69 | 31 | 31 | 15 | 31 | 46 | |
| Class coverage, % | 38 | 18 | 13 | 13 | 26 | 26 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rastenis, J.; Ramanauskaitė, S.; Janulevičius, J.; Čenys, A.; Slotkienė, A.; Pakrijauskas, K. E-mail-Based Phishing Attack Taxonomy. Appl. Sci. 2020, 10, 2363. https://doi.org/10.3390/app10072363
Rastenis J, Ramanauskaitė S, Janulevičius J, Čenys A, Slotkienė A, Pakrijauskas K. E-mail-Based Phishing Attack Taxonomy. Applied Sciences. 2020; 10(7):2363. https://doi.org/10.3390/app10072363
Chicago/Turabian StyleRastenis, Justinas, Simona Ramanauskaitė, Justinas Janulevičius, Antanas Čenys, Asta Slotkienė, and Kęstutis Pakrijauskas. 2020. "E-mail-Based Phishing Attack Taxonomy" Applied Sciences 10, no. 7: 2363. https://doi.org/10.3390/app10072363
APA StyleRastenis, J., Ramanauskaitė, S., Janulevičius, J., Čenys, A., Slotkienė, A., & Pakrijauskas, K. (2020). E-mail-Based Phishing Attack Taxonomy. Applied Sciences, 10(7), 2363. https://doi.org/10.3390/app10072363






