Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference
Abstract
1. Introduction
2. Background and Motivation
2.1. IEEE 802.11 Distributed Coordination Function Background
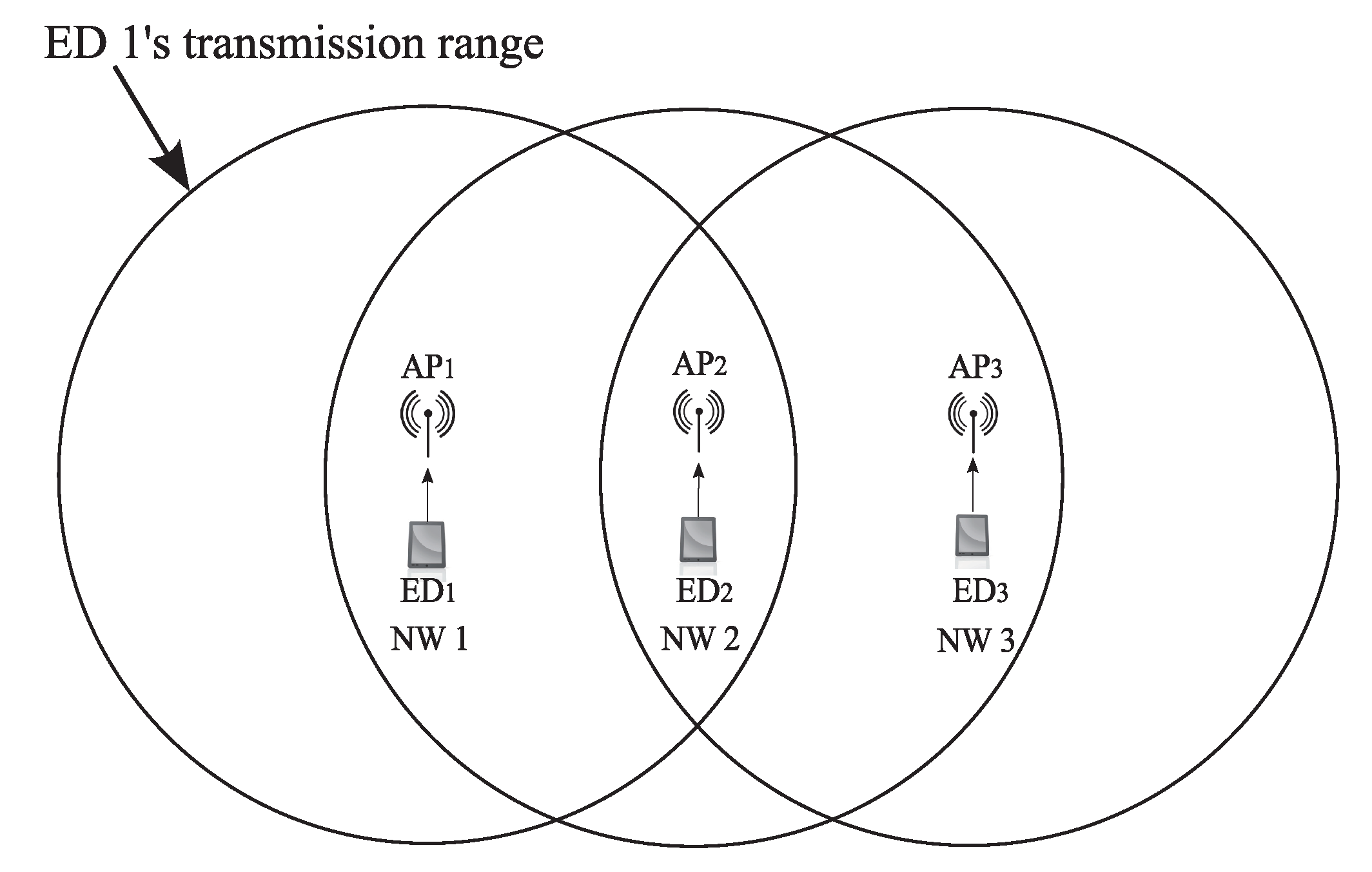
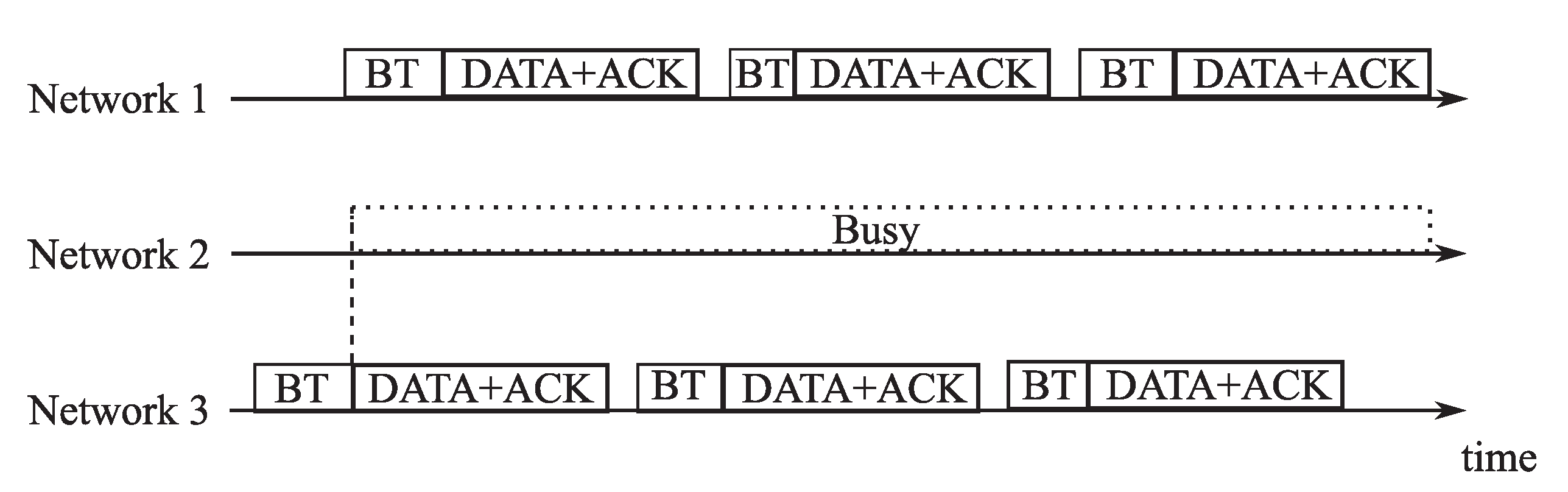
2.2. Inter-Network Interference
2.3. Motivation to Use Airtime Concept
3. General Concept of Throughput Analysis with Inter-Network Interference
- ED in each network generates user datagram protocol (UDP) frames to the AP (uplink) following the Poisson distribution.
- The condition of the physical layer is ideal. Therefore, transmission failures occur due to only frame collisions in the medium access control (MAC) layer.
4. Throughput Analysis of String and Grid Topology Considering Inter-Network Interference
4.1. Analysis of String Network Topology
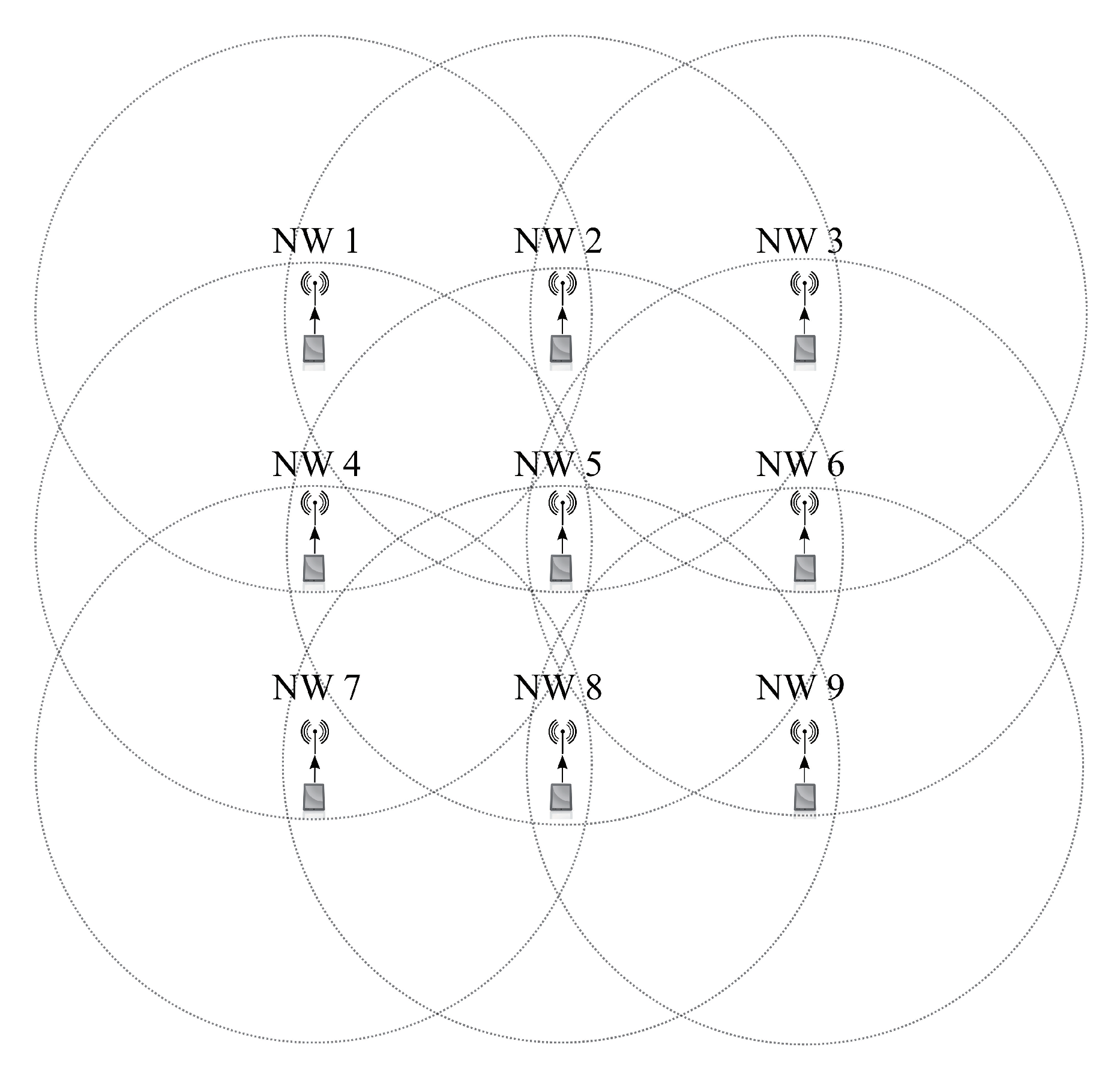
4.2. Analysis of Grid Network Topology
4.2.1. Two Carrier-Sensing Networks
4.2.2. Three Carrier-Sensing Networks
4.2.3. Four Carrier-Sensing Networks
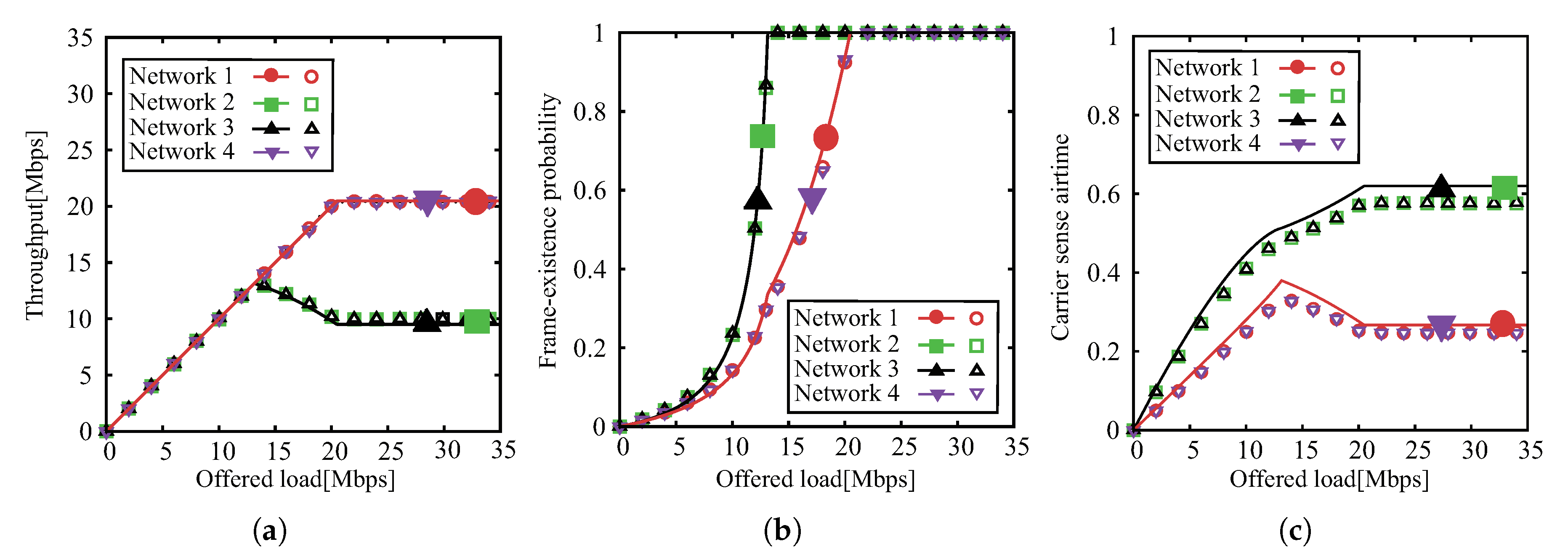
5. Performance Evaluation
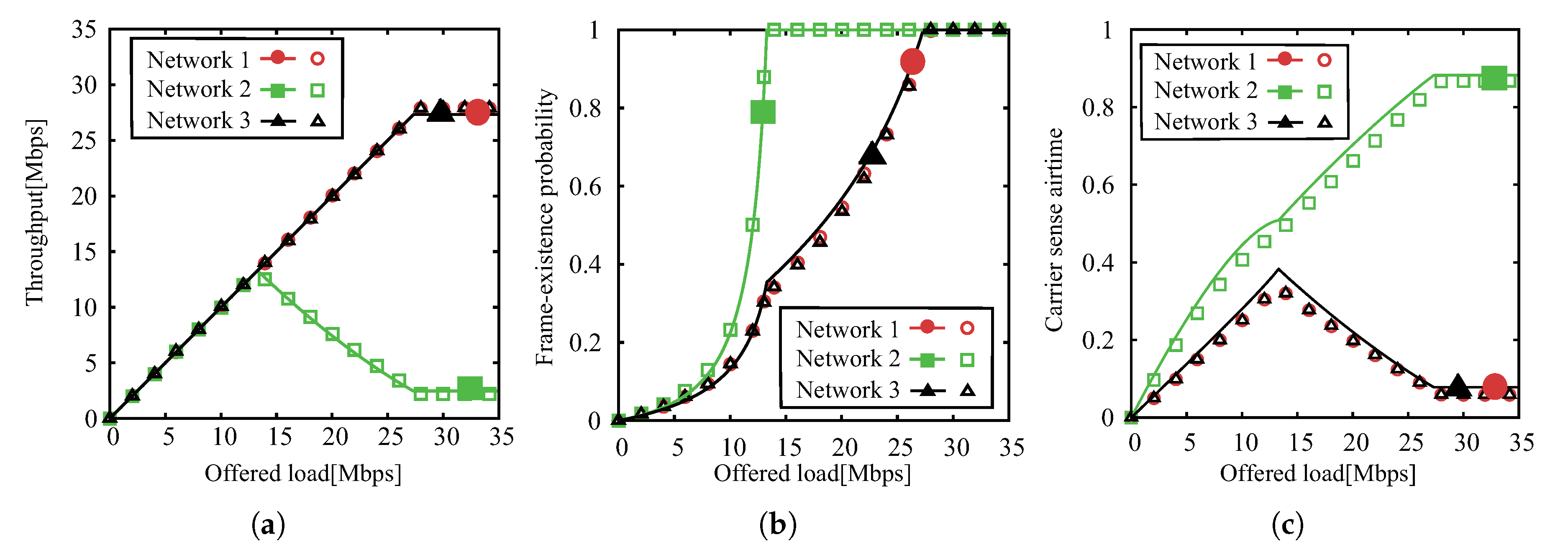
5.1. Scenario 1: String Topology,
5.2. Scenario 2: String Topology,
5.3. Scenario 3: Grid Topology
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Bianchi, G. Performance analysis of IEEE 802.11 distributed coordination function. Proc. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Duffy, K.; Malone, D.; Leith, D. Modeling the 802.11 distributed coordination function in nonsaturared conditions. IEEE Commun. Lett. 2005, 9, 715–717. [Google Scholar] [CrossRef]
- Zhang, H.; Zhang, X.; Chen, G. Performance analysis of IEEE802.11 DCF in non-saturated conditions. In Proceedings of the 2011 International Conference on Business Management and Electronic Information, Guangzhou, China, 13–15 May 2011; pp. 495–498. [Google Scholar]
- Kim, T.; Lim, J.T. Throughput analysis considering coupling effect in IEEE 802.11 networks with hidden stations. IEEE Commun. Lett. 2009, 13, 175–177. [Google Scholar] [CrossRef]
- Qin, Z.; Xiao, J.; Xie, H. A novel model for non-saturated performance analysis of IEEE802.11 DCF. In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), Yichang, China, 21–23 April 2012; pp. 1552–1556. [Google Scholar]
- Iwami, T.; Takaki, Y.; Yamori, K.; Ohta, C.; Tamaki, H. Distributed association control considering user utility and user guidance in IEEE802.11 networks. In Proceedings of the 2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 2125–2130. [Google Scholar]
- Deng, X.; He, T.; He, L.; Gui, J.; Peng, Q. Performance analysis for IEEE 802.11s wireless mesh network in smart grid. Wirel. Pers. Commun. 2017, 96, 1537–1555. [Google Scholar] [CrossRef]
- Li, X.; Narita, Y.; Gotoh, Y.; Shioda, S. Performance analysis of IEEE 802.11 DCF based on a macroscopic state description. IEICE Trans. Commun. 2018, E101-B, 1923–1932. [Google Scholar] [CrossRef]
- Ng, P.C.; Liew, S.C. Throughput analysis of IEEE 802.11 multi-hop ad hoc networks. IEEE/ACM Trans. Netw. 2007, 15, 309–322. [Google Scholar] [CrossRef]
- Barowski, Y.D.; Biaz, S.; Agrawal, P. Towards the performance analysis of IEEE 802.11 in multi-hop ad-hoc networks. In Proceedings of the WCNC, New Orleans, LA, USA, 13–17 March 2005; Volume 1, pp. 100–106. [Google Scholar]
- Shimoyamada, Y.; Sanada, K.; Komuro, N.; Sekiya, H. End-to-end throughput analysis for IEEE 802.11e EDCA string-topology wireless multi-hop networks. Nonlinear Theory Its Appl. 2015, E6-N, 410–432. [Google Scholar] [CrossRef]
- Sanada, K.; Shi, J.; Komuro, N.; Sekiya, H. End-to-end delay analysis for IEEE 802.11 string-topology multi-hop networks. IEICE Trans. Commun. 2015, E98-B, 1284–1293. [Google Scholar] [CrossRef]
- Wan, Y.; Sanada, K.; Komuro, N.; Motoyoshi, G.; Yamagaki, N.; Shioda, S.; Sakata, S.; Murase, T.; Sekiya, H. Throughput analysis of WLANs in saturation and non-saturation heterogeneous conditions with airtime concept. IEICE Trans. Commun. 2016, E99-B, 2289–2296. [Google Scholar] [CrossRef]
- Sanada, K.; Sekiya, H. Bottom-up analysis concept for throughput and delay analyses of wireless network. Nonlinear Theory Its Appl. 2017, 8, 181–203. [Google Scholar] [CrossRef]
- So, J.; Lee, J. Dynamic carrier-sense threshold selection for improving spatial reuse in dense Wireless LANs. Appl. Sci. 2019, 9, 3951. [Google Scholar] [CrossRef]
- Kanematsu, T.; Nguyen, K.; Sekiya, H. Throughput analysis for IEEE 802.11 multi-Hop networks considering transmission rate. In Proceedings of the IEEE VTC Spring 2019, Kuala Lumpur, Malaysia, 28 April–1 May 2019; pp. 1–5. [Google Scholar]
- Ikuma, S.; Li, Z.; Pei, T.; Choi, Y.; Sekiya, H. Rigorous analytical model of saturated throughput for the IEEE 802.11p EDCA. IEICE Trans. Commun. 2019, E102-B, 699–707. [Google Scholar] [CrossRef]
- Kelley, C.T. Iterative Methods for Linear and Nonlinear Equations; North Carolina State University: Raleigh, NC, USA, 1995. [Google Scholar]
- Gao, Y.; Chui, D.; Lui, J.C.S. Determining the end-to-end throughput capacity in multi-hop networks: Methodology applications. In Proceedings of the SIGMETRICS/Performance 2006, Saint Malo, France, 26–30 June 2006; pp. 39–50. [Google Scholar]
- Inaba, M.; Tsuchiya, Y.; Sekiya, H.; Sakata, S.; Yagyu, K. Analysis and experiments of maximum throughput in wireless multi-hop networks for VoIP application. IEICE Trans. Commun. 2009, E92-B, 3422–3431. [Google Scholar] [CrossRef]
- Kumar, A.; Altman, E.; Miorandi, D.; Goyal, M. New insights from a fixed point analysis of single cell IEEE 802.11 Wireless LANs. IEEE/ACM Trans. Netw. 2007, 15, 588–600. [Google Scholar] [CrossRef]
- Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE Std. 802.11; IEEE: Piscataway, NJ, USA, 2012.
- The Simulator’s Source Code. Available online: http://www.s-lab.nd.chiba-u.jp/link/simulator.htm (accessed on 24 January 2020).


| The Limit Value as Approaches ∞ | |
|---|---|
| The transmission duration of Network i in | |
| The transmission airtime of Network i | |
| The carrier-sensing airtime of Network i | |
| The function to represent | |
| ine | The set of networks within the carrier-sensing of Network i |
| The number of elements of set | |
| is the s-th smallest element of | |
| The sum over all elements h in the set | |
| The product over all elements h in the set | |
| The idle airtime of Network i | |
| The throughput of Network i | |
| P | The payload size of a data frame |
| T | The period of successful transmission of a data packet |
| The BT-decrement for one frame-transmission success of Network i | |
| The transmission probability when Network i is in the idle state under the saturation condition | |
| The minimum contention-window value | |
| The slot time | |
| The frame-existence probability of Network i in the non-saturation condition | |
| The frame-existence probability of Network i | |
| The offered load of Network i | |
| The frame occurrence rate in Network i | |
| The frame transmission probability at the idle state of Network i | |
| The sum over all elements k in the set | |
| The product over all elements k in the set | |
| The probability that Network i is in the idle state when its neighbor Network h is in the idle state | |
| The simultaneous transmission probability of Network i and Network h | |
| Only Network 5 is within the carrier-sensing range of Network a and b |
| Data payload | 1500 bytes |
| PHY header | 24 bytes |
| MAC header | 24 bytes |
| ACK size | 10 bytes |
| Data rate | 54 Mbps |
| ACK bit rate | 24 Mbps |
| DATA | |
| DIFS | |
| SIFS | |
| Slot time () | |
| 15 | |
| 1023 | |
| Retry limit (K) | 7 |
| Inter-network distance | 30 m |
| Transmission range | 40 m |
| Carrier-sensing range | 40 m |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, J.; Aoki, T.; Li, Z.; Pei, T.; Choi, Y.-j.; Nguyen, K.; Sekiya, H. Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference. Appl. Sci. 2020, 10, 2192. https://doi.org/10.3390/app10062192
Liu J, Aoki T, Li Z, Pei T, Choi Y-j, Nguyen K, Sekiya H. Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference. Applied Sciences. 2020; 10(6):2192. https://doi.org/10.3390/app10062192
Chicago/Turabian StyleLiu, Jingwei, Takumi Aoki, Zhetao Li, Tingrui Pei, Young-june Choi, Kien Nguyen, and Hiroo Sekiya. 2020. "Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference" Applied Sciences 10, no. 6: 2192. https://doi.org/10.3390/app10062192
APA StyleLiu, J., Aoki, T., Li, Z., Pei, T., Choi, Y.-j., Nguyen, K., & Sekiya, H. (2020). Throughput Analysis of IEEE 802.11 WLANs with Inter-Network Interference. Applied Sciences, 10(6), 2192. https://doi.org/10.3390/app10062192






