Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map
Abstract
1. Introduction
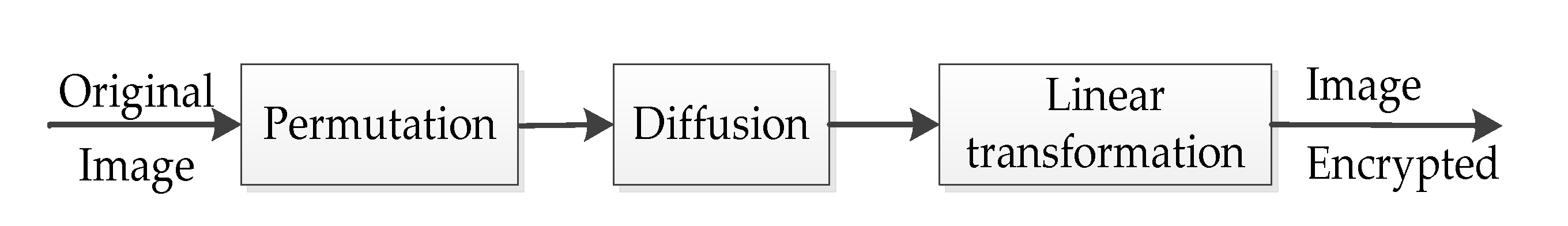
2. Review of the Original Scheme
3. Chosen-Plaintext Attack
3.1. The First Phase of Attack
- Property 1
- Property 2
- If ,
| Algorithm 1 Obtain the Rotation Amount lp and the Diffusion Matrix D |
| 1: Set the plain image Z |
| 2: Obtain the encrypted image pixel sequence C’ after the reshape Cz |
| 3: Obtain the sequence C” |
| 4: |
| 5: |
| 6: Set the plain image Z |
| 7: Obtain the encrypted image pixel sequence after the reshape Cz |
| 8: Obtain the sequence |
| 9: |
| 10: |
| 11: |
| 12: |
3.2. The Second Phase of Attack
| Algorithm 2 Permutation Attack |
| 1: the plain sequence S from the first division and encrypt S |
| 2: |
| 3: |
| 4: set the plain sequence R from the second division and encrypt R |
| 5: from the first phase |
| 6: |
| 7: repeat further division until the element quantity l = 1 |
| 8: |
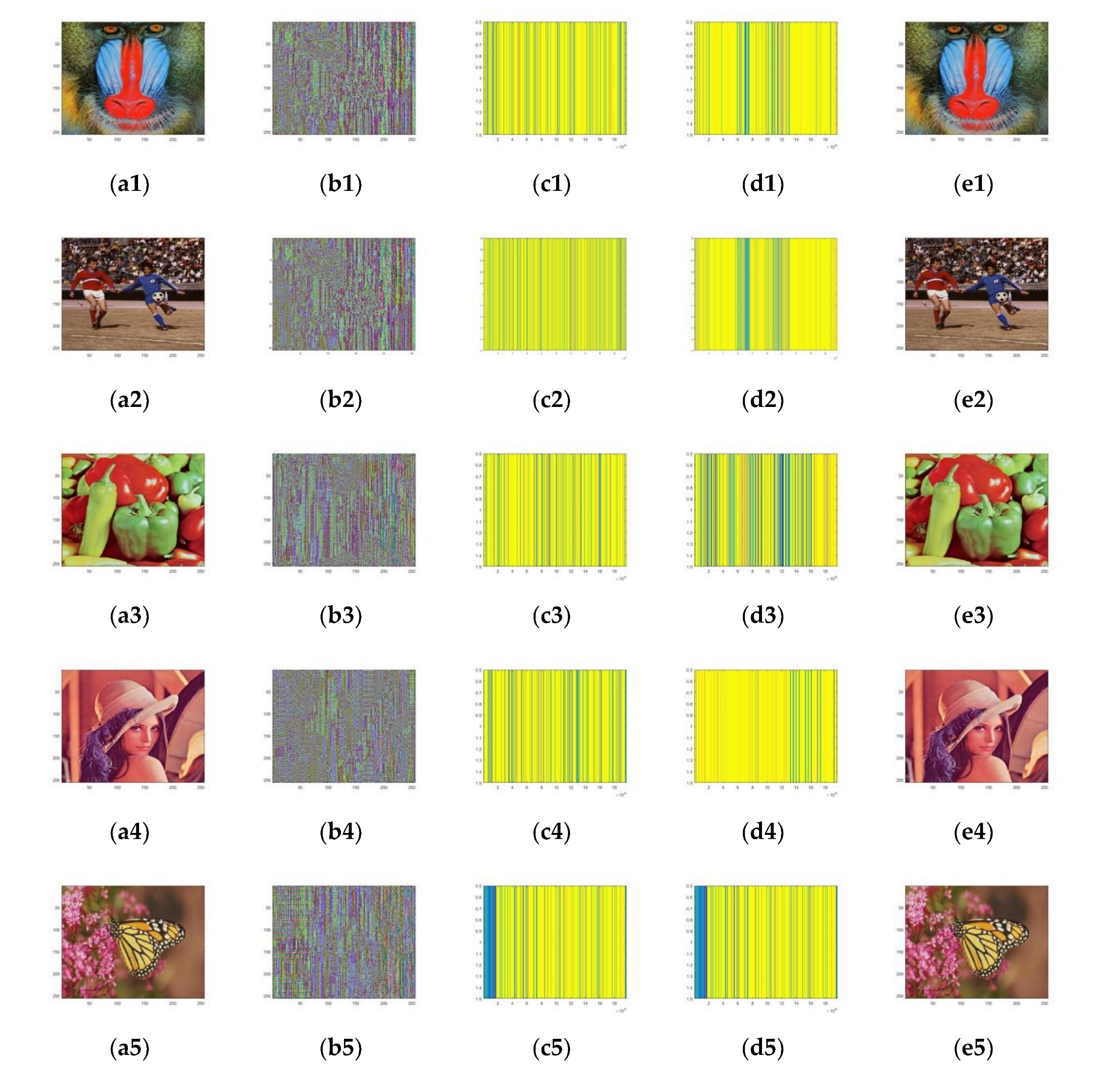
4. Experiments and Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Zhang, Y.S.; Xiao, D.; Shu, Y.L.; Li, J. A novel image encryption scheme based on a linearhyperbolic chaotic sys-tem of partial differential equations. Signal Process. Image Commun. 2013, 28, 292–300. [Google Scholar] [CrossRef]
- Zhang, Y.S.; Xiao, D. Double optical image encryption using discrete Chirikov standard map and chaos-based fractional random transform. Opt. Lasers Eng. 2013, 51, 472–480. [Google Scholar] [CrossRef]
- Ye, G.D.; Wong, K.W. An efficient chaotic image encryption algorithm based on a generalized Arnold map. Nonlinear Dyn. 2012, 69, 2079–2087. [Google Scholar] [CrossRef]
- Mirzaei, O.; Yaghoobi, M.; Irani, H. A new image encryption method: Parallel sub-image encryption with hyperchaos. Nonlinear Dyn. 2011, 67, 557–566. [Google Scholar] [CrossRef]
- Liu, Y.B.; Tian, S.M.; Hu, W.P.; Xing, C.C. Design and statistical analysis of a new chaotic block cipher for wireless sensor networks. Commun. Nonlinear Sci. Numer. Simul. 2012, 17, 3267–3278. [Google Scholar] [CrossRef]
- Wong, K.W.; Kwok, B.; Law, W. A fast image encryption scheme based on chaotic standard map. Phys. Lett. A 2008, 372, 2645–2652. [Google Scholar] [CrossRef]
- Norouzi, B.; Mirzakuchaki, S.; Seyedzadeh, S.M.; Mosavi, M.R. A simple, sensitive and secure image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Multimed. Tools Appl. 2014, 71, 1469–1497. [Google Scholar] [CrossRef]
- Kassem, A.; Hassan, H.A.H.; Harkouss, Y.; Assaf, R. Efficient neural chaotic generator for image encryption. Digit. Signal Process. 2014, 25, 266–274. [Google Scholar] [CrossRef]
- Arroyo, D.; Diaz, J.; Rodriguez, F.B. Cryptanalysis of a one round chaos-based substitution permutation network. Signal Process. 2013, 67, 1358–1364. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D. Cryptanalysis of S-box-only chaotic image ciphers against chosen plaintext attack. Nonlinear Dyn. 2013, 72, 751–756. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, C.; Li, Q.; Zhang, D.; Shu, S. Breaking a chaotic image encryption algorithm based on perceptron model. Nonlinear Dyn. 2012, 69, 1091–1096. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D.; Wen, W.; Li, M. Breaking an image encryption algorithm based on hyper-chaotic system with only one round diffusion process. Nonlinear Dyn. 2014, 76, 1645–1650. [Google Scholar] [CrossRef]
- Su, M.; Wen, W.; Zhang, Y. Security evaluation of bilateral-diffusion based image encryption algorithm. Nonlinear Dyn. 2014, 77, 243–246. [Google Scholar] [CrossRef]
- Zhang, Y.; Xiao, D.; Wen, W.; Li, M. Cryptanalyzing a novel image cipher based on mixed transformed logistic maps. Multimed. Tools Appl. 2014, 73, 1885–1896. [Google Scholar] [CrossRef]
- Jain, A.; Rajpal, N. A robust image encrytion algorithm resistant to attacks using DNA and chaotic logistic maps. Mutitimed. Tools Appl. 2016, 75, 5455–5472. [Google Scholar] [CrossRef]
- Ye, G.; Pan, C.; Huang, X.; Zhao, Z.; He, J. A chaotic image encryption algorithm based on information entropy. Int. J. Bifurc. Chaos 2018, 28, 1850010. [Google Scholar] [CrossRef]
- Dou, Y.; Liu, X.; Fan, H.; Li, M. Cryptanalysis of a DNA and chaotic logistic maps based image encryption algorithm. OPTIK 2017, 145, 456–464. [Google Scholar] [CrossRef]
- Li, C.; Lin, D.; Feng, B.; Lü, J.; Hao, F. Cryptanalysis of a Chaotic Image Encryption Algorithm Based on Information Entropy. IEEE Access 2018, 6, 75834–75842. [Google Scholar] [CrossRef]
- Panduranga, H.T.; Kumar, S.N. Image encryption based on permutation-substitution using chaotic map and latin square image cipher. Eur. Phys. J. Spec. Top. 2014, 223, 1663–1677. [Google Scholar] [CrossRef]
- Machkour, M.; Saaidi, A.; Benmaati, M. A novel image encryption algorithm based on the two-dimensional logistic map and the latin square image cipher. 3D Res. 2015, 6, 1–18. [Google Scholar] [CrossRef]
- Chapaneri, S.; Chapaneri, R. Chaos based image encryption using latin rectangle scrambling. 2014 annual IEEE India conference (INDICON), Pune, India, 11–13 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [Google Scholar]
- Hu, G.; Xiao, D.; Wang, Y.; Li, X. Cryptanalysis of a chaotic image cipher using Latin square-based confusion and diffusion. Nonlinear Dyn. 2017, 88, 1305–1316. [Google Scholar] [CrossRef]
- Ge, X.; Lu, B.; Liu, F.; Luo, X. Cryptanalyzing an image encryption algorithm with compound chaotic stream cipher based on perturbation. Nonlinear Dyn. 2017, 90, 1141–1150. [Google Scholar] [CrossRef]
- Lin, J.; Wang, Z. Image block encryption algorithm based on chaotic maps. IET Signal Process. 2017, 12, 22–30. [Google Scholar]
- Ma, Y.; Li, C. Cryptanalysis of an Image Block Encryption Algorithm Based on Chaotic Maps. arXiv 2019, arXiv:1912.12915. [Google Scholar]
- Chai, X.; Fu, X.; Gan, Z.; Lu, Y.; Chen, Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 2019, 155, 44–62. [Google Scholar] [CrossRef]
- Zhu, C.X.; Wang, G.J.; Sun, K.H. Improved cryptanalysis and enhancements of an image encryption scheme us in combined 1D chaotic maps. Entropy 2018, 20, 843. [Google Scholar] [CrossRef]
- Wang, M.X.; Wang, X.Y.; Zhang, Y.Q.; Gao, Z.G. A novel chaotic encryption scheme based on image segmentation an multiple diffusion models. Opt. Laser Tecnnol. 2018, 108, 558–573. [Google Scholar] [CrossRef]
- Hua, Z.; Yi, S.; Zhou, Y. Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process. 2018, 144, 134–144. [Google Scholar] [CrossRef]
- Norouzi, B.; Seyedzadeh, S.M.; Mirzakuchaki, S.; Mosavi, M.R. A novel image encryption based on hash function with only two-round diffusion process . Multimed. Syst. 2014, 20, 45–64. [Google Scholar] [CrossRef]
- Chen, J.X.; Zhu, Z.L.; Fu, C.; Zhang, L.B.; Zhang, Y.S. An efficient image encryption scheme using lookup table-base confusion and diffusion. Nonlinear Dyn. 2015, 81, 1151–1166. [Google Scholar] [CrossRef]
- Belazi, A.; Abd Ellatif, A.A.; Belghith, S. A novel image encryption scheme based on substitution–permutation network and chaos. Signal Process. 2016, 128, 155–170. [Google Scholar] [CrossRef]
- Li, M.; Lu, D.; Xiang, Y.; Zhang, Y.; Ren, H. Cryptanalysis and improvement in a chaotic image cipher using two-round permutation and diffusion. Nonlinear Dyn. 2019, 96, 31–47. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C.L.P. A new 1d chaotic system for image encryption. Signal Process. 2014, 97, 172–182. [Google Scholar] [CrossRef]
- Wen, W.; Zhang, Y.; Fang, Z.; Chen, J.X. Infrared target-based selective encryption by chaotic maps. Opt. Commun. 2015, 341, 131–139. [Google Scholar] [CrossRef]
- Lv-Chen, C.; Yu-Ling, L.; Sen-Hui, Q.; Jun-Xiu, L. A perturbation method to the tent map based on Lyapunov exponent and its application. Chin. Phys. B 2015, 24, 78–85. [Google Scholar]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Wang, H.; Xiao, D.; Chen, X.; Huang, H. cryptanalysis and enhancements of image encryption using combination of the 1D chaotic map. Signal Process. 2018, 144, 444–452. [Google Scholar] [CrossRef]
- Li, C.; Lo, K.T. Optimal quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process. 2011, 91, 949–954. [Google Scholar] [CrossRef]
- Zhang, L.Y.; Liu, Y.; Wang, C.; Zhou, J.; Zhang, Y.; Chen, G. Improved known-plaintext attack to permutation-only multimedia ciphers. Inf. Sci. 2018, 430, 228–239. [Google Scholar] [CrossRef]
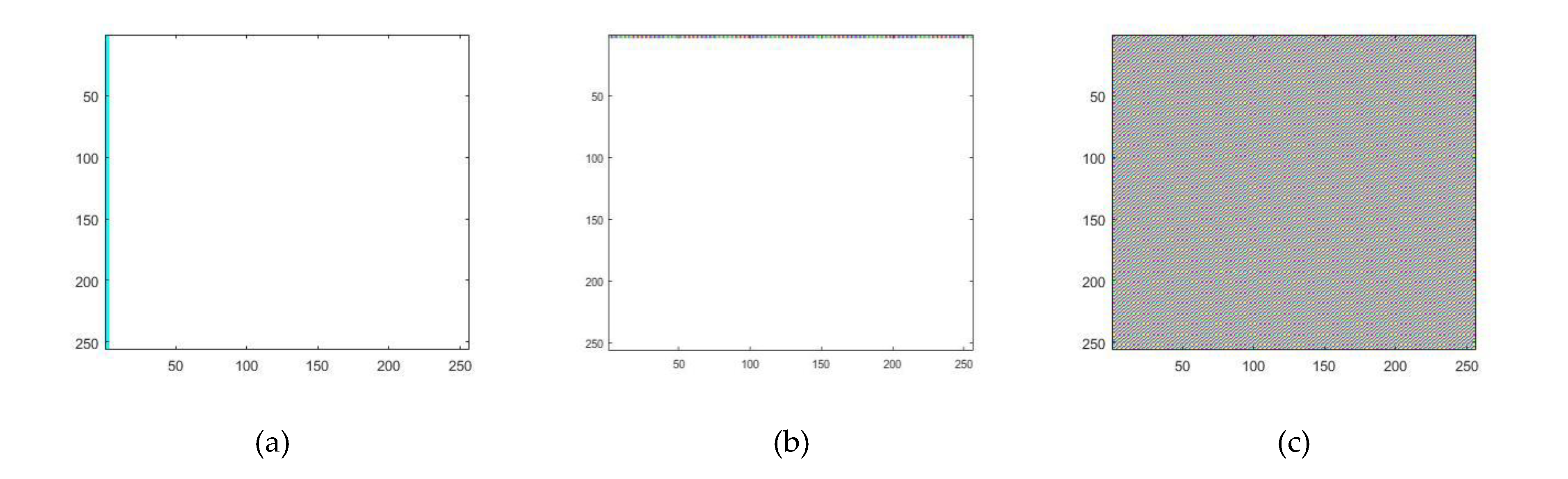
| Image Size | ||||||
|---|---|---|---|---|---|---|
| 3 | 3 | 3 | 4 | 5 | 6 | |
| 3 | 3 | 3 | 4 | 5 | 6 | |
| 3 | 3 | 4 | 4 | 5 | 7 |
| Image Size | Image | The Proposed Scheme | Chen’s Scheme | ||||
|---|---|---|---|---|---|---|---|
| Attack lp and Diffusion | Attack Permutation | Total Time | Attack lp and Diffusion | Attack Permutation | Total Time | ||
| Lena | 1.2386 | 2.7358 | 3.9744 | 1.2173 | 3.8253 | 5.0426 | |
| Baboon | 1.0537 | 2.8356 | 3.8893 | 1.1562 | 3.9376 | 5.0938 | |
| Pepper | 0.9697 | 2.9121 | 3.8818 | 1.0127 | 4.5862 | 5.5989 | |
| Average time | 1.0873 | 2.8278 | 3.9151 | 1.1287 | 4.1164 | 5.2451 | |
| Lena | 1.5413 | 10.0327 | 11.574 | 1.7135 | 13.7236 | 15.4371 | |
| Baboon | 1.6331 | 11.7731 | 13.4062 | 1.5233 | 13.1027 | 14.626 | |
| Pepper | 1.6975 | 10.9173 | 12.6148 | 1.5872 | 14.3379 | 15.9251 | |
| Average time | 1.6240 | 10.9077 | 12.5317 | 1.6080 | 13.7214 | 15.3294 | |
| Lena | 2.5136 | 32.4377 | 34.9513 | 2.4759 | 47.7536 | 50.2295 | |
| Baboon | 2.7572 | 35.7728 | 38.53 | 2.8364 | 58.5927 | 61.4291 | |
| Pepper | 2.6673 | 39.8154 | 42.4827 | 2.6581 | 56.3619 | 59.02 | |
| Average time | 2.6460 | 36.0086 | 38.6546 | 2.6568 | 54.2361 | 56.8929 | |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dou, Y.; Li, M. Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map. Appl. Sci. 2020, 10, 2187. https://doi.org/10.3390/app10062187
Dou Y, Li M. Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map. Applied Sciences. 2020; 10(6):2187. https://doi.org/10.3390/app10062187
Chicago/Turabian StyleDou, Yuqiang, and Ming Li. 2020. "Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map" Applied Sciences 10, no. 6: 2187. https://doi.org/10.3390/app10062187
APA StyleDou, Y., & Li, M. (2020). Cryptanalysis of a New Color Image Encryption Using Combination of the 1D Chaotic Map. Applied Sciences, 10(6), 2187. https://doi.org/10.3390/app10062187




