A Novel Pipeline Leak Recognition Method of Mine Air Compressor Based on Infrared Thermal Image Using IFA and SVM
Abstract
1. Introduction
2. Materials and Methods
2.1. Firefly Algorithm and Its Improvements
2.1.1. Classic Firefly Algorithm
- FA parameters initialization. First, we set the size of the solution space to D, then set an appropriate number of fireflies N according to D. The maximum update number tmax is set appropriately, and the appropriate absorption coefficient is set according to different media, usually 1; the initial step size s is usually set to 0.5. The initial attraction β0 represents the attraction at the light source (distance r = 0), usually set to 1, and the coordinate of the i-th firefly is expressed as Xi= (xi1, xi2, …, xiD).
- Firefly’s attractiveness calculation. According to the coordinates of each firefly and the corresponding fitness evaluation function, the fitness of the firefly is calculated as the brightness of the fireflies. The aim of the firefly algorithm is to find the optimal solution in the objective function, and the brightness of the firefly’s position is the firefly’s solution in the objective function. When the function is known, the brightness of the firefly can be obtained by introducing the position coordinates of the firefly, which can be used to judge the position of the firefly. Then, based on the brightness, the absorption coefficient and the distance between fireflies the attraction β between fireflies is calculated, as shown below:where rij is the distance between two fireflies.
- 3.
- Location update judgment. The brightness of the firefly at the new position is calculated. If the brightness of the firefly is brighter, the firefly’s position will be updated, otherwise, it will not be updated.
- 4.
- Algorithm iteration. According to steps (2)–(4), fireflies will be updated through multiple flights until the maximum number of iterations is reached, and one or more firefly clusters will eventually be formed. The coordinates of the brightest firefly represent the optimal solution that the algorithm finds in this space.
2.1.2. Improved Firefly Algorithm
- Firefly’s update efficiency is improved. When the step size is updated, a fixed distribution step size is used in the classical algorithm. The updated strategy is consistent at different stages of the algorithm. Therefore, it was decided to introduce a step size range to limit the uniform distribution, so that the step size range will decrease as the number of updates increase. In the early stage, the firefly update step size is larger and rapid iterations are performed. As the iterations increase, the firefly update step size becomes smaller, which enhances the local search capability, and finally achieves the purpose of optimizing the algorithm. The updated step method of IFA is as follows:
- The self-search ability of the local optimal firefly is improved. Because all firefly individuals only fly to fireflies which are brighter than themselves, the brightest individual in the group does not move, but there is no guarantee that the individual is in the optimal position. In response to such problems, the firefly in the optimal position is randomly searched in an adaptive circle centered on itself and the radius gradually decreases as the number of iterations increases. If the brightness of the firefly is brighter in the new location, the coordinates of the firefly will be updated, otherwise it is not updated, Therefore, the self-search ability of fireflies to the surrounding environment has been improved, and fireflies can jump out from the local optimal position. The optimal firefly self-search update formula is as follows:where the represents the self-searching range of the optimal firefly at the t-th iteration.
2.1.3. Simulation Analysis
2.2. Principle of Wavelet Threshold Denoising
2.2.1. Wavelet Threshold Denoising
- (1)
- Wavelet transform. For noisy images, we select a suitable wavelet function, and use the wavelet function to perform multi-layer decomposition of noisy images through wavelet transform to obtain a set of wavelet coefficients.
- (2)
- Non-linear threshold. According to the characteristics of the noise in the noisy image, an appropriate noise threshold is selected through a threshold function, and the wavelet coefficients of the noise part in the high-frequency decomposition value are reset to zero. Commonly used threshold functions are hard threshold function, soft threshold function and semi-soft threshold function. The hard threshold function is given as follows:
- (3)
- Inverse wavelet transform to reconstruct the image. The processed wavelet estimation coefficients are subjected to inverse wavelet transform to obtain a noise-removed image.
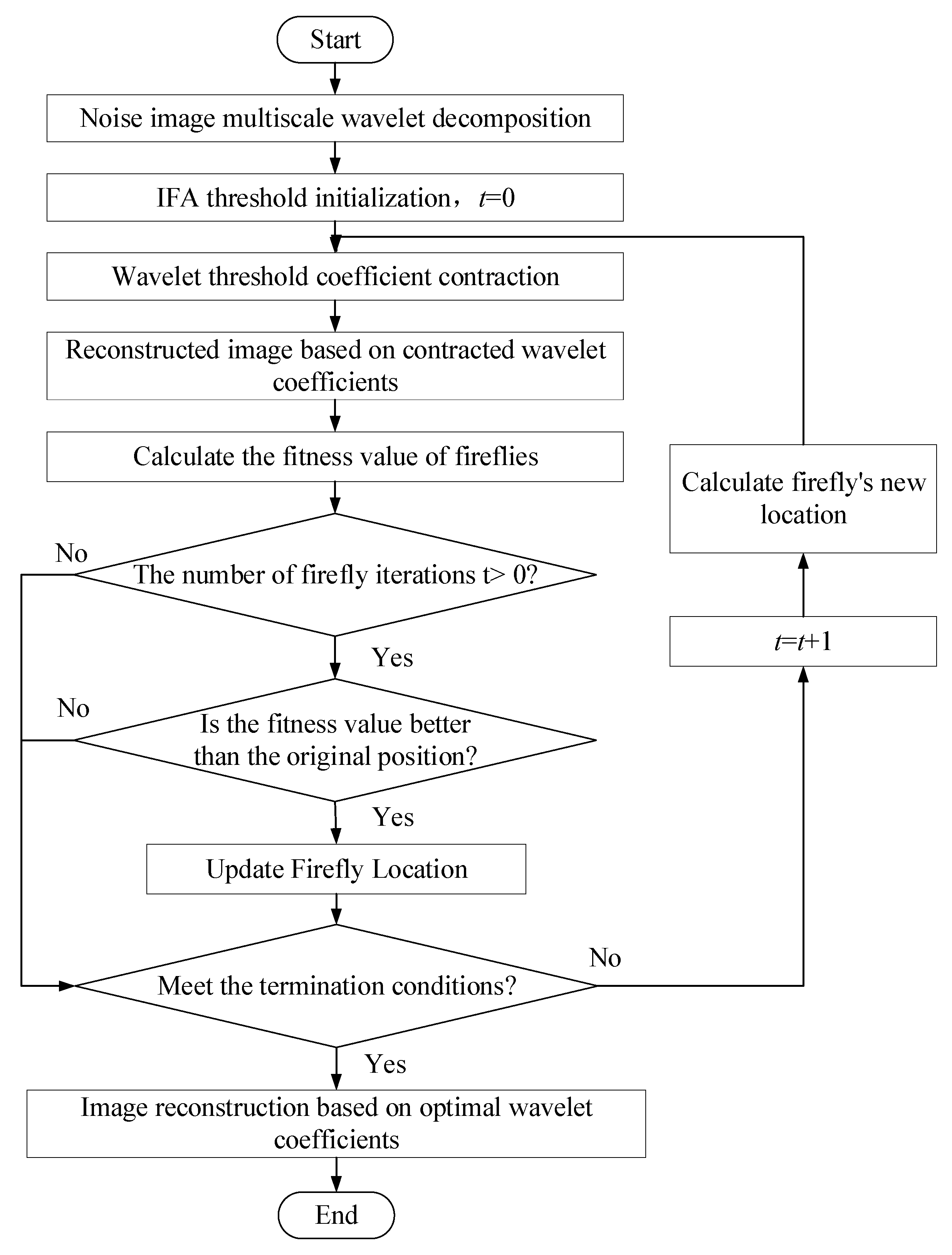
2.2.2. WTD-IFA
- (1)
- Wavelet decomposition. Wavelet transform is used to decompose the infrared image with noise.
- (2)
- Threshold initialization. Initializing the IFA threshold and initializing the firefly position (wavelet threshold).
- (3)
- The wavelet coefficients contract. Equation (6) is used to calculate the wavelet contraction coefficient, and the image is reconstructed based on the wavelet contraction coefficient.
- (4)
- Firefly algorithm iteration. The fitness of the reconstructed image is calculated according to Equation (12). If the iteration number of the firefly algorithm is greater than 1, it is judged whether the fitness of the firefly is better than the fitness of the original position. If yes, the firefly position is updated, otherwise, the firefly position is kept unchanged. If the image fitness result meets the termination condition, execute step (6), otherwise execute step (5).
- (5)
- Firefly location update. Based on the firefly’s current fitness value and the IFA’s location update rules, the firefly’s new location is calculated. Then go to step (3).
- (6)
- Image reconstruction. The image is reconstructed using the global optimal wavelet threshold searched by WTD-IFA.
2.3. Image Segmentation and Feature Extraction
2.3.1. Otsu-Grabcut Algorithm
2.3.2. Grabcut Algorithm
2.3.3. Otsu-Grabcut Image Segmentation Algorithm
2.4. Image Feature Extraction
2.4.1. Histogram of Oriented Gradient (HOG)
- (1)
- Calculation of pixel distribution gradient. Common forms of simple convolution are [−1,0,1] and [−1,0,1]T. Convolution calculation is performed on the preprocessed image to generate two orthogonal gradient components, and the gradient direction of each pixel can be calculated according to the component. The calculation formula is shown as follow:where G(x, y) is the gradient amplitude of the pixel, M(x, y) is the gradient direction of the pixel, Gx(x, y) is the horizontal gradient of the pixels, Gy(x, y) is the vertical gradient of the pixels, H(x, y) is the gray value of the pixel.
- (2)
- Cell unit division and gradient direction histogram calculation. First, we divide the image into cells of the same size, generally set to 8 × 8 pixels, and limit the gradient direction to [0, π]. The gradient direction is evenly divided into 9 intervals, and the gradient value of each pixel in the cell unit is weighted and projected in the histogram. The gradient direction histogram of the cell unit is generated, and each interval corresponds to a one-dimensional feature vector.
- (3)
- HOG feature vector calculation. In the image, the four cells in the cube are combined into a block, and the block corresponds to a total of 36-dimensional feature vectors. In order to reduce the influence of the local illumination on the image on the feature vector, all the calculated feature vectors are normalized and combined to generate the HOG feature vector of the entire image.
2.4.2. Gray-Level Co-Occurrence Matrix (GLCM)
2.5. Support Vector Machine Based on IFA
2.5.1. Support Vector Machines
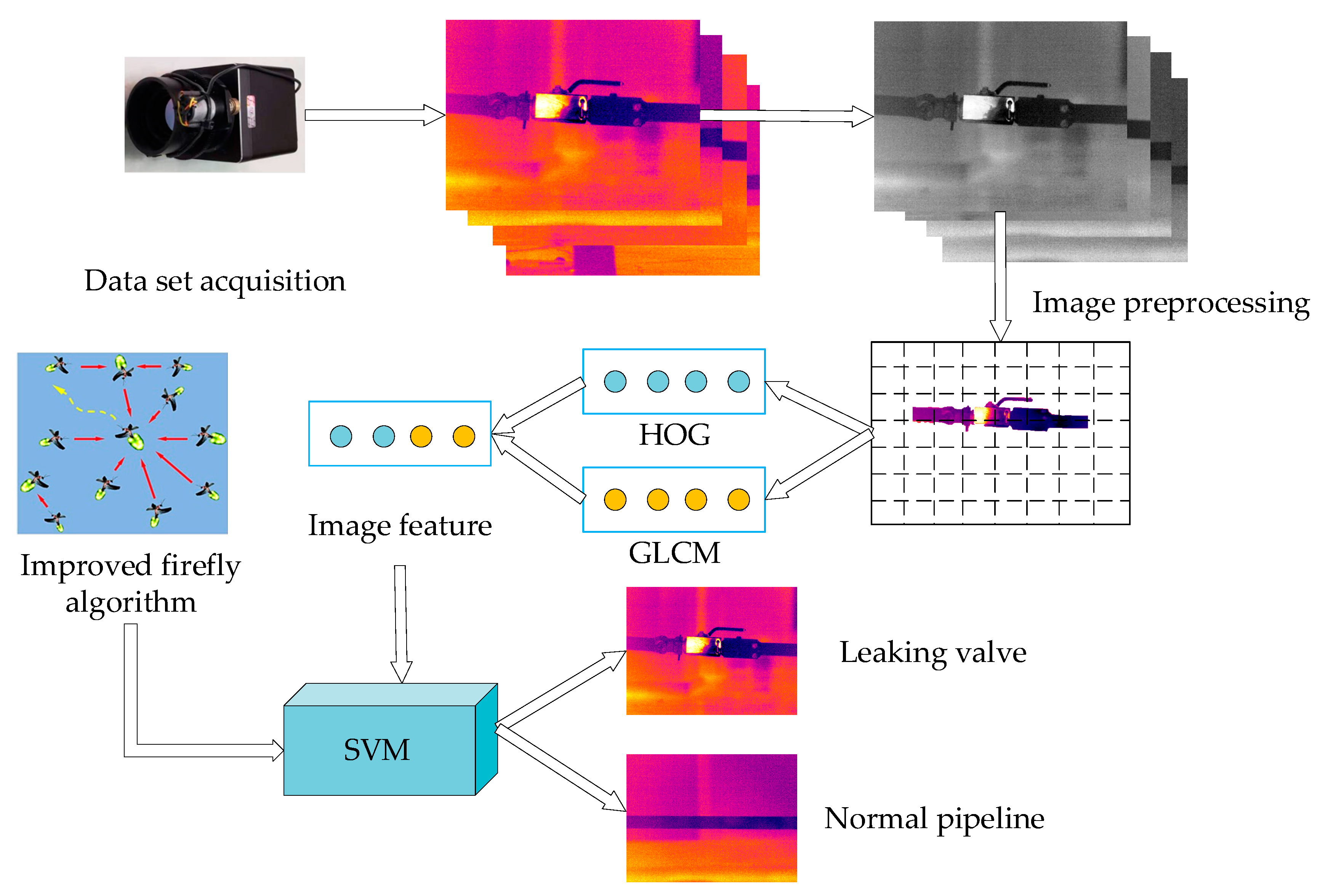
2.5.2. The Pipeline Leak Recognition Method Based On SVM and IFA
- (1)
- Data set acquisition. The data set is acquired and labeled, and the data set is divided into a training data set and a test data set.
- (2)
- Data preprocessing and feature extraction. The acquired data are preprocessed, and appropriate feature extraction methods are used to extract the features of the data.
- (3)
- Training and establishment of support vector machine model. Support vector machines are trained according to the extracted data features, and IFA is used to optimize the kernel function parameters of the SVM, and the optimal hyperplane of the corresponding data are found by calculating the training data.
- (4)
- Test data classification and result analysis. The test data are classified and tested by the support vector machine, and the test results are generated. The model is analyzed as to whether it can achieve a better classification effect.
3. Results and Discussion
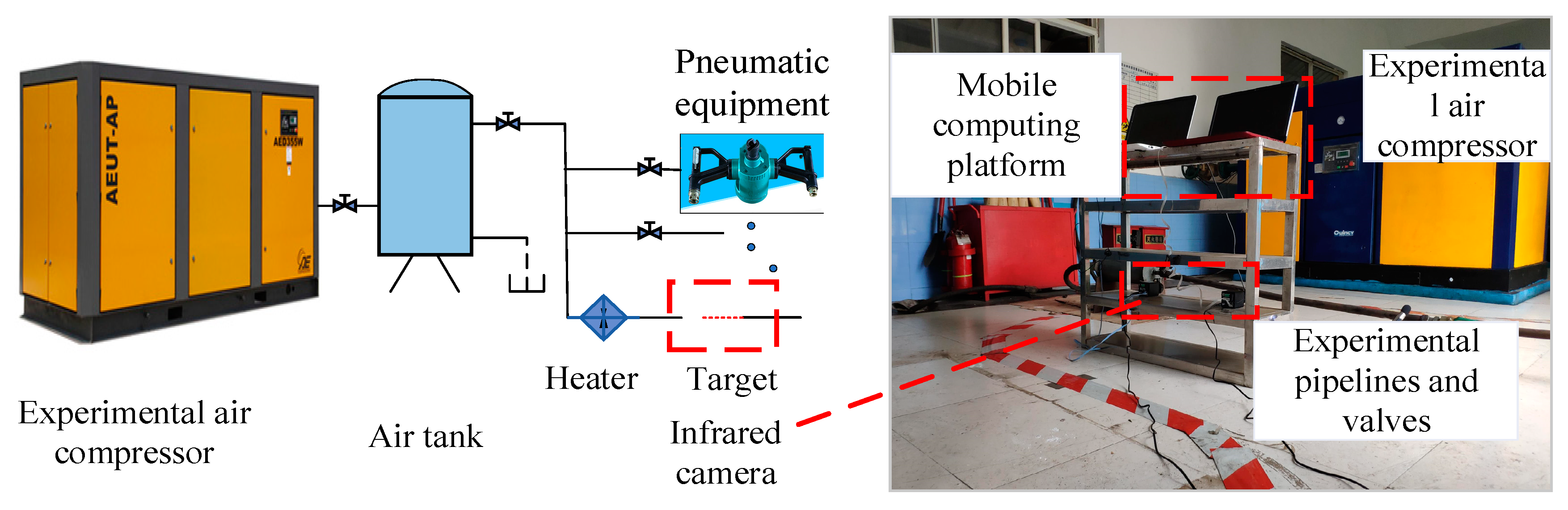
3.1. Experimental Platform Construction
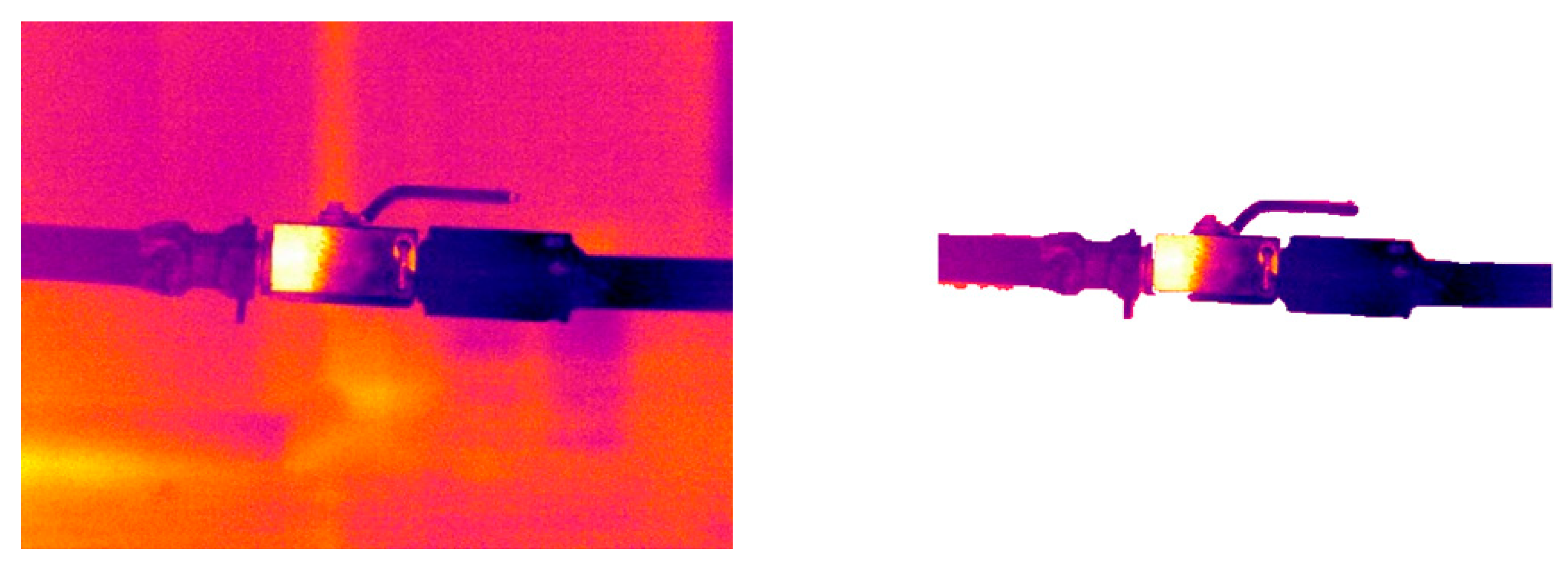
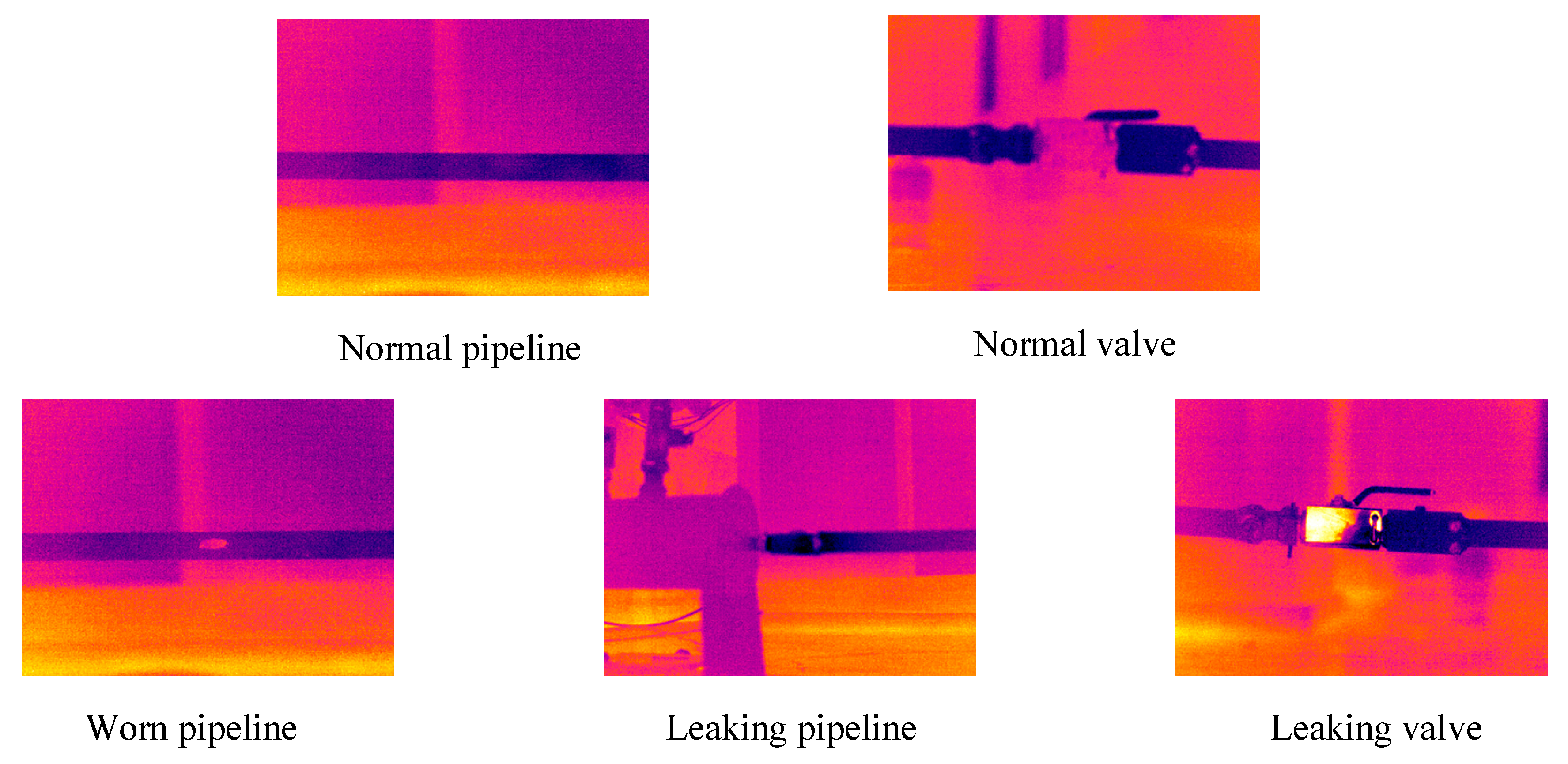
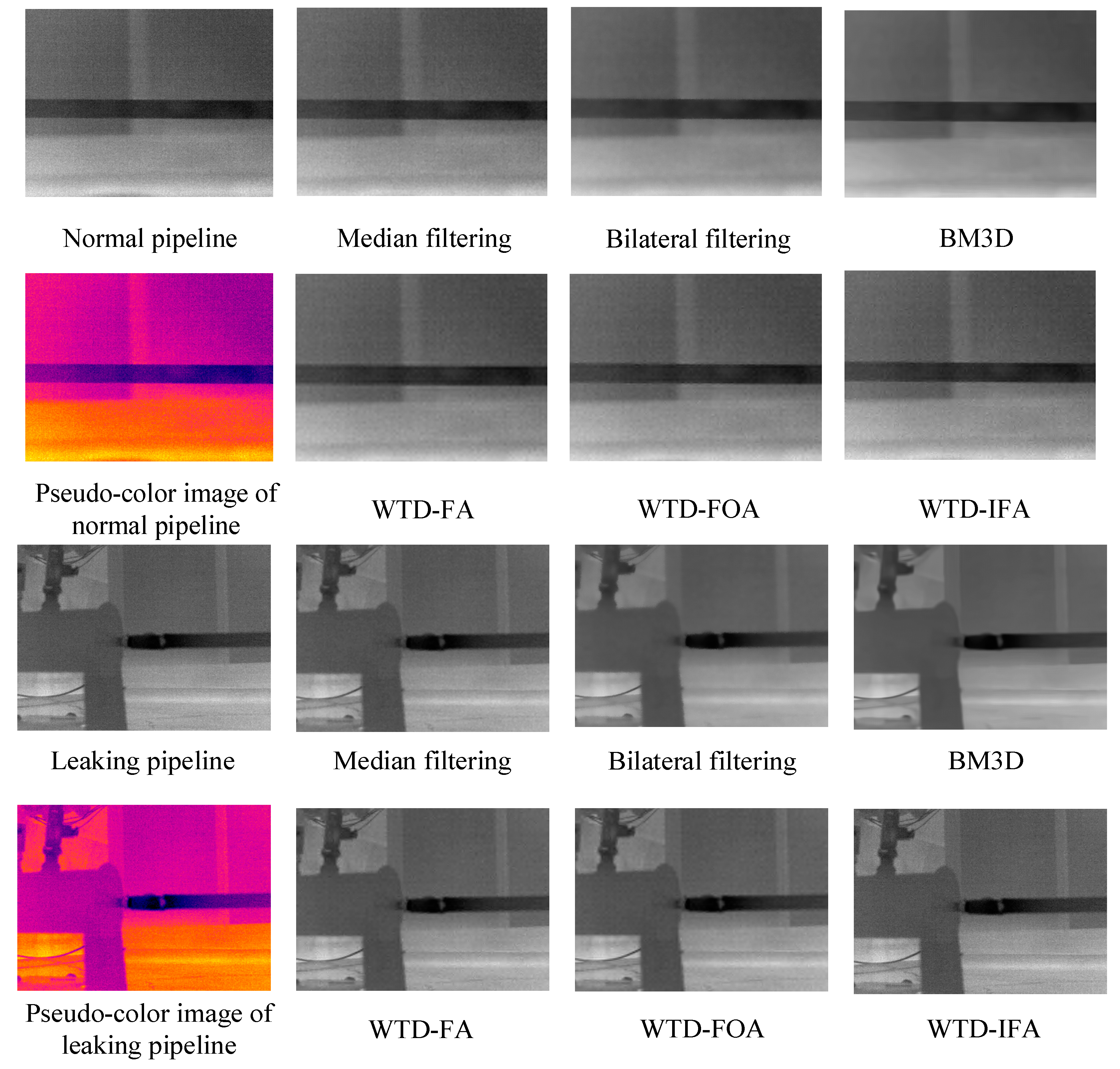
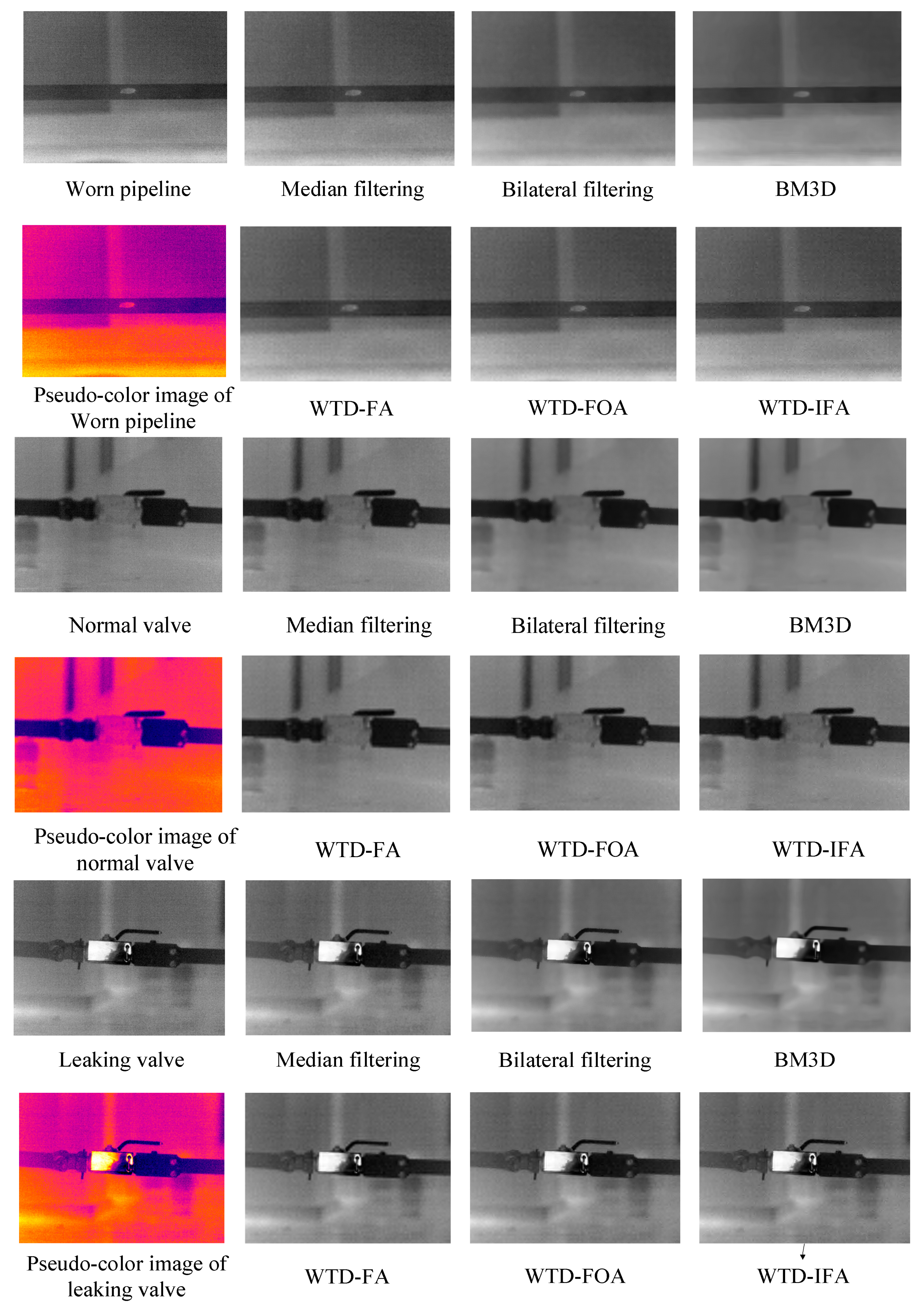
3.2. Infrared Image Denoising Experiments
3.3. SVM Classification Experiment Results
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Bao, C.; Yang, C. Remote On-line Monitoring System for Air Compressor Used for Mine Based on Configuration Technology. Coal Mine Mach. 2012, 7, 236–238. [Google Scholar]
- Jian-zhang, L.U. Compressed Air Self Rescue System in Underground Mine. Coal Sci. Technol. 2010, 12, 4–6. [Google Scholar]
- Maolin, C. Modern Pneumatic Technology and Practice Lecture 10: Energy-Saving in Pneumatic System. Hydraul. Pneum. Seals 2008, 28, 59–63. [Google Scholar]
- Šešlija, D.; Ignjatović, I.; Dudić, S.; Lagod, B. Potential energy savings in compressed air systems in Serbia. Afr. J. Bus. Manag. 2011, 5, 5637–5645. [Google Scholar]
- Kreith, F.; Goswami, D.Y. Energy Management and Conservation Handbook; CRC Press: Boca Raton, FL, USA, 2007. [Google Scholar]
- Madding, R.; Benson, R. Detecting SF6 insulating gas leaks with an IR imaging camera. Electr. Today 2007, 19, 9–15. [Google Scholar]
- Dudić, S.; Ignjatović, I.; Šešlija, D.; Blagojević, V.; Stojiljković, M. Leakage quantification of compressed air using ultrasound and infrared thermography. Measurement 2012, 45, 1689–1694. [Google Scholar] [CrossRef]
- Meng, L.; Yuxing, L.; Wuchang, W.; Juntao, F. Experimental study on leak detection and location for gas pipeline based on acoustic method. J. Loss Prev. Proc. 2012, 25, 90–102. [Google Scholar] [CrossRef]
- Chis, T. Pipeline leak detection techniques. Ann. Comput. Sci. 2009, 5, 25–34. [Google Scholar]
- Wang, Y. Application and research of DSP in the portable air-leakage detector. Machinery 2005, 3, 56–59. [Google Scholar]
- Jin, H.; Zhang, L.; Liang, W.; Ding, Q. Integrated leakage detection and localization model for gas pipelines based on the acoustic wave method. J. Loss Prev. Proc. 2014, 27, 74–88. [Google Scholar] [CrossRef]
- Salisbury, J.W.; D’Aria, D.M. Emissivity of terrestrial materials in the 8–14 μm atmospheric window. Remote Sens. Environ. 1992, 42, 83–106. [Google Scholar] [CrossRef]
- Yang, X. Firefly algorithm. In Nature-Inspired Metaheuristic Algorithms; Elsevier: Amsterdam, The Netherlands, 2014; Volume 20, pp. 111–127. [Google Scholar]
- Hassanzadeh, T.; Kanan, H.R. Fuzzy FA: A modified firefly algorithm. Appl. Artif. Intell. 2014, 28, 47–65. [Google Scholar] [CrossRef]
- Haji, V.H.; Monje, C.A. Fractional-order PID control of a chopper-fed DC motor drive using a novel firefly algorithm with dynamic control mechanism. Soft Comput. 2018, 22, 6135–6146. [Google Scholar] [CrossRef]
- Kumar, S.V.; Nagaraju, C. FFBF: Cluster-based Fuzzy Firefly Bayes Filter for noise identification and removal from grayscale images. Clust. Comput. 2019, 22, 1–23. [Google Scholar] [CrossRef]
- Mo, Y.; Ma, Y.; Zheng, Q. Optimal choice of parameters for firefly algorithm. In 2013 Fourth International Conference on Digital Manufacturing and Automation; IEEE: Piscataway, NJ, USA, 2013; pp. 887–892. [Google Scholar]
- Soto, C.; Valdez, F.; Castillo, O. A review of dynamic parameter adaptation methods for the firefly algorithm. In Nature-Inspired Design of Hybrid Intelligent Systems; Springer: Cham, Switzerland, 2017; pp. 285–295. [Google Scholar]
- Liu, Q.; Jiang, Z.; Shi, H. Maximum Entropy Image Segmentation Method Based On Improved Firefly Algorithm. In Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2019; p. 032023. [Google Scholar]
- Hidalgopaniagua, A.; Vegarodriguez, M.A.; Ferruz, J.; Pavon, N. Solving the multi-objective path planning problem in mobile robotics with a firefly-based approach. Soft Comput. 2017, 4, 949–964. [Google Scholar] [CrossRef]
- Sadhu, A.K.; Konar, A.; Bhattacharjee, T.; Das, S. Synergism of Firefly Algorithm and Q-Learning for Robot Arm Path Planning. Swarm Evol. Comput. 2018, 43, 50–68. [Google Scholar] [CrossRef]
- Yang, X. Firefly algorithm, Levy flights and global optimization. In Research and Development in Intelligent Systems XXVI; Springer: London, UK, 2010; pp. 209–218. [Google Scholar]
- Abdullah, A.; Deris, S.; Mohamad, M.S.; Hashim, S.Z.M. A new hybrid firefly algorithm for complex and nonlinear problem. In Distributed Computing and Artificial Intelligence; Springer: Berlin/Heidelberg, Germany, 2012; pp. 673–680. [Google Scholar]
- Yang, Q.; Tan, K.; Ahuja, N. Real-time O (1) bilateral filtering. In 2009 IEEE Computer Society Conference on Computer Vision and Pattern Recognition; IEEE: Piscataway, NJ, USA, 2009; pp. 557–564. [Google Scholar]
- Feruglio, P.F.; Vinegoni, C.; Gros, J.; Sbarbati, A.; Weissleder, R. Block matching 3D random noise filtering for absorption optical projection tomography. Phys. Med. Biol. 2010, 55, 5401–5415. [Google Scholar] [CrossRef]
- Deng, G.; Liu, Z. A wavelet image denoising based on the new threshold function. In 2015 11th International Conference on Computational Intelligence and Security (CIS); IEEE: Piscataway, NJ, USA, 2015; pp. 158–161. [Google Scholar]
- Otsu, N. A threshold selection method from gray-level histograms. IEEE Trans. Syst. Man Cybern. 1979, 9, 62–66. [Google Scholar] [CrossRef]
- Rother, C.; Kolmogorov, V.; Blake, A. Interactive foreground extraction using iterated graph cuts. ACM Trans. Graph. 2004, 3, 309–314. [Google Scholar] [CrossRef]
- Haralick, R.M.; Shanmugam, K.; Dinstein, I.H. Textural features for image classification. IEEE Trans. Syst. Man Cybern. 1973, 6, 610–621. [Google Scholar] [CrossRef]
- Chen, J.; Yin, Y.; Han, L.; Zhao, F. Optimization Approaches for Parameters of SVM. In Proceedings of the 11th International Conference on Modelling, Identification and Control, Tianjin, China, 13–15 July 2019; Springer: Berlin/Heidelberg, Germany, 2020; pp. 575–583. [Google Scholar]
- Maulik, U.; Bandyopadhyay, S. Genetic algorithm-based clustering technique. Pattern Recogn. 2000, 33, 1455–1465. [Google Scholar] [CrossRef]
- Demidova, L.A.; Egin, M.M.; Tishkin, R.V. A Self-tuning Multiobjective Genetic Algorithm with Application in the SVM Classification. Procedia Comput. Sci. 2019, 150, 503–510. [Google Scholar] [CrossRef]
- Zhou, C.; Gao, H.B.; Gao, L.; Zhang, W. Particle Swarm Optimization (PSO) Algorithm. Appl. Res. Comput. 2003, 12, 7–11. [Google Scholar]
- Raj, S.; Ray, K.C. ECG Signal Analysis Using DCT-Based DOST and PSO Optimized SVM. IEEE Trans. Instrum. Meas. 2017, 66, 470–478. [Google Scholar] [CrossRef]

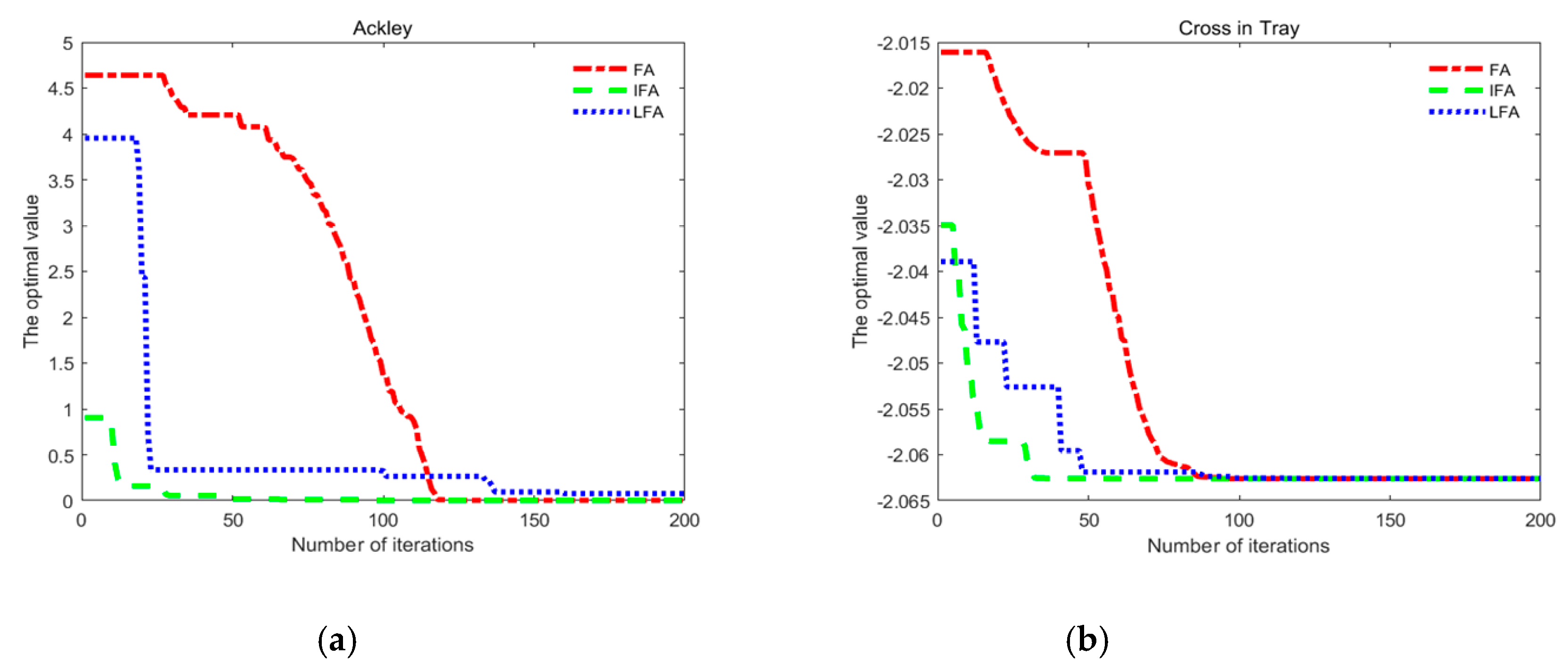
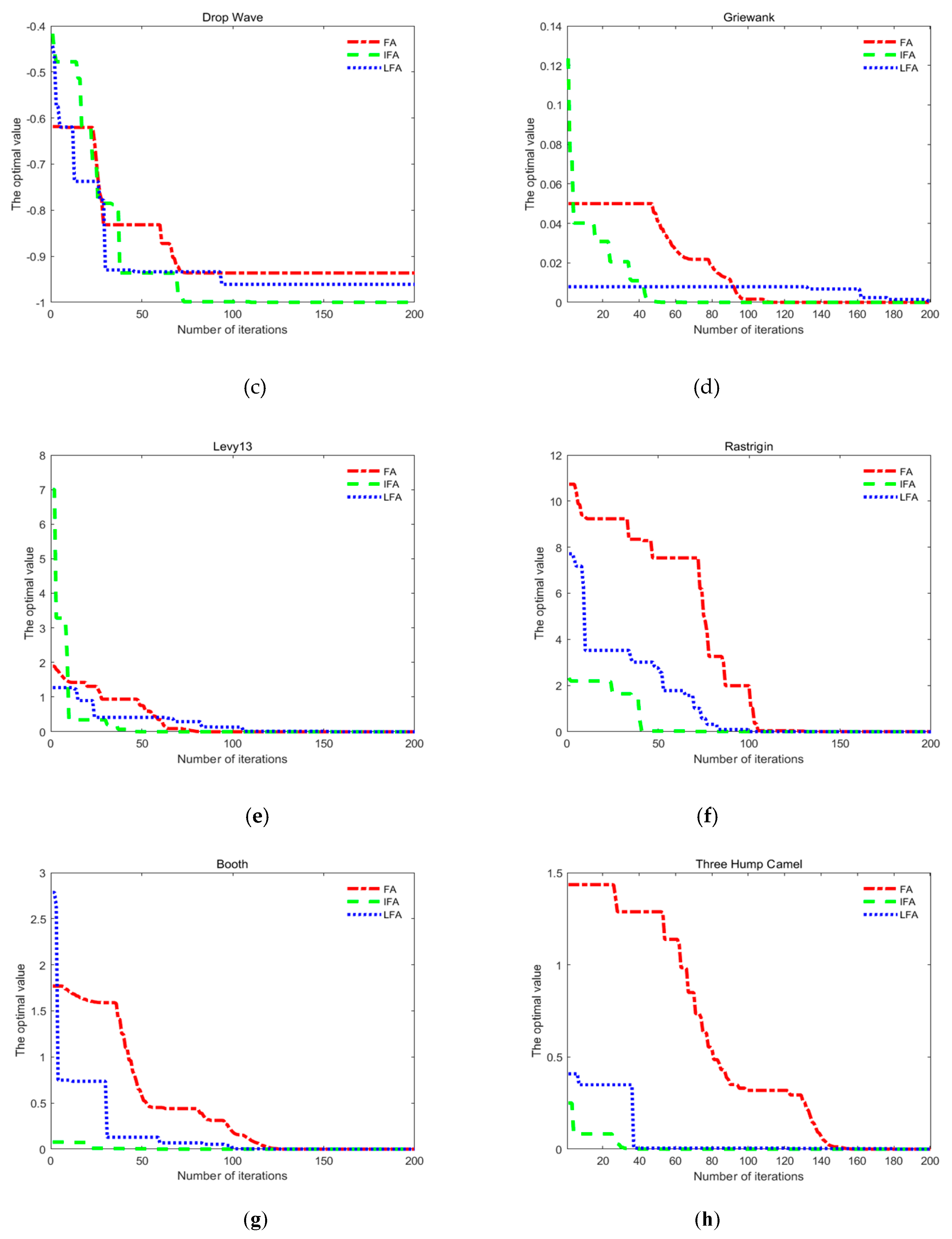
| Function Name | Dimension | Independent Variable Value Range | Function Formula | Theoretical Value | |
|---|---|---|---|---|---|
| f1 | Ackley | 2 | [−32.768, 32.768] | fmin = 0 | |
| f2 | Cross in Tray | 2 | [−10, 10] | fmin = −2.06261 | |
| f3 | Drop Wave | 2 | [−5.12, 5.12] | fmin = −1 | |
| f4 | Griewank | 2 | [−600, 600] | fmin = 0 | |
| f5 | Levy 13 | 2 | [−10, 10] | fmin = 0 | |
| f6 | Rastrigin | 2 | [−5.12, 5.12] | fmin = 0 | |
| f7 | Booth | 2 | [−10, 10] | fmin = 0 | |
| f8 | Three Hump Camel | 2 | [−5, 5] | fmin = 0 |
| Parameter | Optimal Value | Optimal Value Variance | |||||
|---|---|---|---|---|---|---|---|
| Function | FA | LFA | IFA | FA | LFA | IFA | |
| f1 | 1.02 × 10−4 | 0.00452104 | 5.92 × 10−4 | 0.97116936 | 0.13558556 | 1.83 × 10−5 | |
| f2 | −2.06261 | −2.06261 | −2.06261 | 6.21 × 10−6 | 2.18 × 10−7 | 3.43 × 10−13 | |
| f3 | −1.00 | −0.999951 | −0.999984 | 0.0280539 | 8.28 × 10−4 | 9.32 × 10−4 | |
| f4 | 7.79× 10−8 | 2.45× 10−5 | 7.11 × 10−8 | 1.37 × 10−5 | 1.33 × 10−5 | 1.36 × 10−5 | |
| f5 | 1.83 × 10−7 | 3.24 × 10−5 | 2.80 × 10−8 | 0.858863 | 9.74 × 10−4 | 2.31 × 10−11 | |
| f6 | 7.60 × 10−5 | 0.001572 | 1.94 × 10−7 | 1.33 | 0.15732 | 0.0329 | |
| f7 | 2.80 × 10−8 | 3.57 × 10−5 | 1.73 × 10−7 | 0.010723 | 0.006544 | 2.11 × 10−11 | |
| f8 | 6.35 × 10−8 | 8.27 × 10−6 | 3.36 × 10−7 | 0.005363 | 3.27 × 10−6 | 1.42 × 10−8 | |
| Parameter | The Average Operation Time (s) | |||
|---|---|---|---|---|
| Function | FA | LFA | IFA | |
| f1 | 0.2729 | 0.2769 | 0.2608 | |
| f2 | 0.2659 | 0.2631 | 0.240933 | |
| f3 | 0.24796 | 0.2591667 | 0.2313333 | |
| f4 | 0.258367 | 0.252167 | 0.247967 | |
| f5 | 0.255033 | 0.2588 | 0.230233 | |
| f6 | 0.261667 | 0.269767 | 0.233567 | |
| f7 | 0.2536 | 0.259767 | 0.2281 | |
| f8 | 0.270467 | 0.258633 | 0.2308 | |
| Type | Parameter |
|---|---|
| System | Windows10 (64bit) |
| Central processing unit (CPU) | AMD Ryzen 5 3500 u 2.10 GHz |
| Random access memory (RAM) | 16 GB |
| Read only memory (ROM) | SSD (512 GB) |
| Matlab version | 2019b |
| Type | Parameter |
|---|---|
| Infrared camera brand Detector type | Juge Electronics Uncooled focal plane |
| Wavelength range | 7.5–14 μm |
| Pixels | 384 × 288 |
| Frame rate | 50 Hz |
| Operating temperature | −30~60 °C |
| Temperature measurement range | 0–300 °C |
| Temperature measurement accuracy | 2 °C |
| focal length | 10 mm |
| Angle of view | 37.4° × 28° |
| Angular resolution | 1.7 mrad |
| Parameter | Image Information Entropy | |||||
|---|---|---|---|---|---|---|
| Method | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
| Noisy image | 6.70 | 6.39 | 6.56 | 5.99 | 6.53 | |
| Median filtering | 6.55 | 6.25 | 6.42 | 5.82 | 6.39 | |
| Bilateral filtering | 7.04 | 6.76 | 6.98 | 6.33 | 6.87 | |
| BM3D | 7.92 | 7.69 | 7.88 | 7.34 | 7.77 | |
| WTD-FA | 7.08 | 6.82 | 7.02 | 6.38 | 6.92 | |
| WTD-FOA | 7.08 | 6.82 | 7.03 | 6.38 | 6.91 | |
| WTD-IFA | 7.10 | 6.83 | 7.04 | 6.39 | 6.92 | |
| Parameter | Image Information Entropy | |||||
|---|---|---|---|---|---|---|
| Method | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
| Noisy image | 20.37 | 21.18 | 20.02 | 21.91 | 21.21 | |
| Median filtering | 22.96 | 22.81 | 22.74 | 23.86 | 22.95 | |
| Bilateral filtering | 25.84 | 24.91 | 25.59 | 25.67 | 24.67 | |
| BM3D | 26.34 | 25.95 | 26.00 | 25.84 | 25.84 | |
| WTD-FA | 24.04 | 23.39 | 23.97 | 23.96 | 23.52 | |
| WTD-FOA | 23.99 | 23.35 | 23.90 | 24.33 | 23.45 | |
| WTD-IFA | 25.44 | 24.26 | 24.15 | 24.44 | 24.20 | |
| Parameter | Image Information Entropy | |||||
|---|---|---|---|---|---|---|
| Method | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
| Median filtering | 1.0989 | 1.0479 | 1.0426 | 1.0575 | 1.0632 | |
| Bilateral filtering | 1.8838 | 2.0553 | 2.1209 | 2.0259 | 2.2391 | |
| BM3D | 14.7613 | 17.3301 | 17.3533 | 15.0779 | 17.3111 | |
| WTD-FA | 1.0848 | 1.1081 | 1.2193 | 1.1766 | 1.2209 | |
| WTD-FOA | 1.1856 | 1.2467 | 1.2375 | 1.2531 | 1.2738 | |
| WTD-IFA | 1.0839 | 1.1192 | 1.1205 | 1.1784 | 1.3218 | |
| Prediction | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
|---|---|---|---|---|---|---|
| Reality | ||||||
| Normal pipeline | 19 | 0 | 1 | 0 | 0 | |
| Leaking pipeline | 1 | 15 | 4 | 0 | 0 | |
| Worn pipeline | 0 | 1 | 19 | 0 | 0 | |
| Normal valve | 0 | 0 | 0 | 20 | 0 | |
| Leaking valve | 0 | 0 | 0 | 2 | 18 | |
| Prediction | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
|---|---|---|---|---|---|---|
| Reality | ||||||
| Normal pipeline | 19 | 0 | 1 | 0 | 0 | |
| Leaking pipeline | 0 | 17 | 3 | 0 | 0 | |
| Worn pipeline | 0 | 2 | 18 | 0 | 0 | |
| Normal valve | 0 | 0 | 0 | 20 | 0 | |
| Leaking valve | 0 | 0 | 0 | 1 | 19 | |
| Prediction | Normal Pipeline | Leaking Pipeline | Worn Pipeline | Normal Valve | Leaking Valve | |
|---|---|---|---|---|---|---|
| Reality | ||||||
| Normal pipeline | 20 | 0 | 0 | 0 | 0 | |
| Leaking pipeline | 0 | 18 | 2 | 0 | 0 | |
| Worn pipeline | 0 | 1 | 19 | 0 | 0 | |
| Normal valve | 0 | 0 | 0 | 20 | 0 | |
| Leaking valve | 0 | 0 | 0 | 1 | 19 | |
| Intelligent Algorithm | Image Classification Prediction Accuracy | Single Image Processing Average Time |
|---|---|---|
| Genetic algorithm | 91.00% | 2.2068 |
| Particle swarm optimization | 93.00% | 2.5009 |
| IFA | 96.00% | 2.3518 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tong, K.; Wang, Z.; Si, L.; Tan, C.; Li, P. A Novel Pipeline Leak Recognition Method of Mine Air Compressor Based on Infrared Thermal Image Using IFA and SVM. Appl. Sci. 2020, 10, 5991. https://doi.org/10.3390/app10175991
Tong K, Wang Z, Si L, Tan C, Li P. A Novel Pipeline Leak Recognition Method of Mine Air Compressor Based on Infrared Thermal Image Using IFA and SVM. Applied Sciences. 2020; 10(17):5991. https://doi.org/10.3390/app10175991
Chicago/Turabian StyleTong, Kuangwei, Zhongbin Wang, Lei Si, Chao Tan, and Peiyang Li. 2020. "A Novel Pipeline Leak Recognition Method of Mine Air Compressor Based on Infrared Thermal Image Using IFA and SVM" Applied Sciences 10, no. 17: 5991. https://doi.org/10.3390/app10175991
APA StyleTong, K., Wang, Z., Si, L., Tan, C., & Li, P. (2020). A Novel Pipeline Leak Recognition Method of Mine Air Compressor Based on Infrared Thermal Image Using IFA and SVM. Applied Sciences, 10(17), 5991. https://doi.org/10.3390/app10175991





