On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul
Abstract
Featured Application
Abstract
1. Introduction
2. Materials and Methods
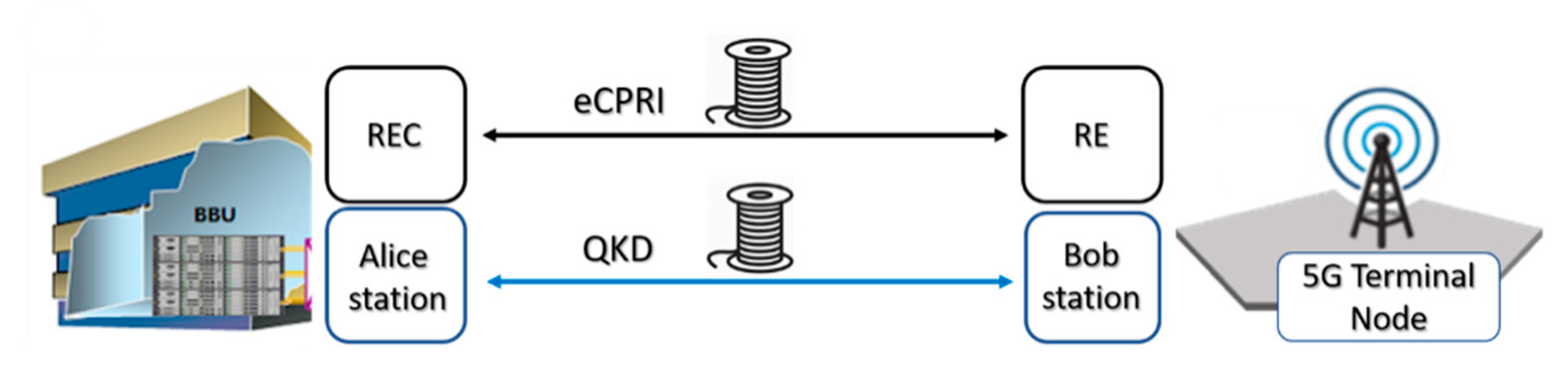
2.1. Dark Fiber Topology
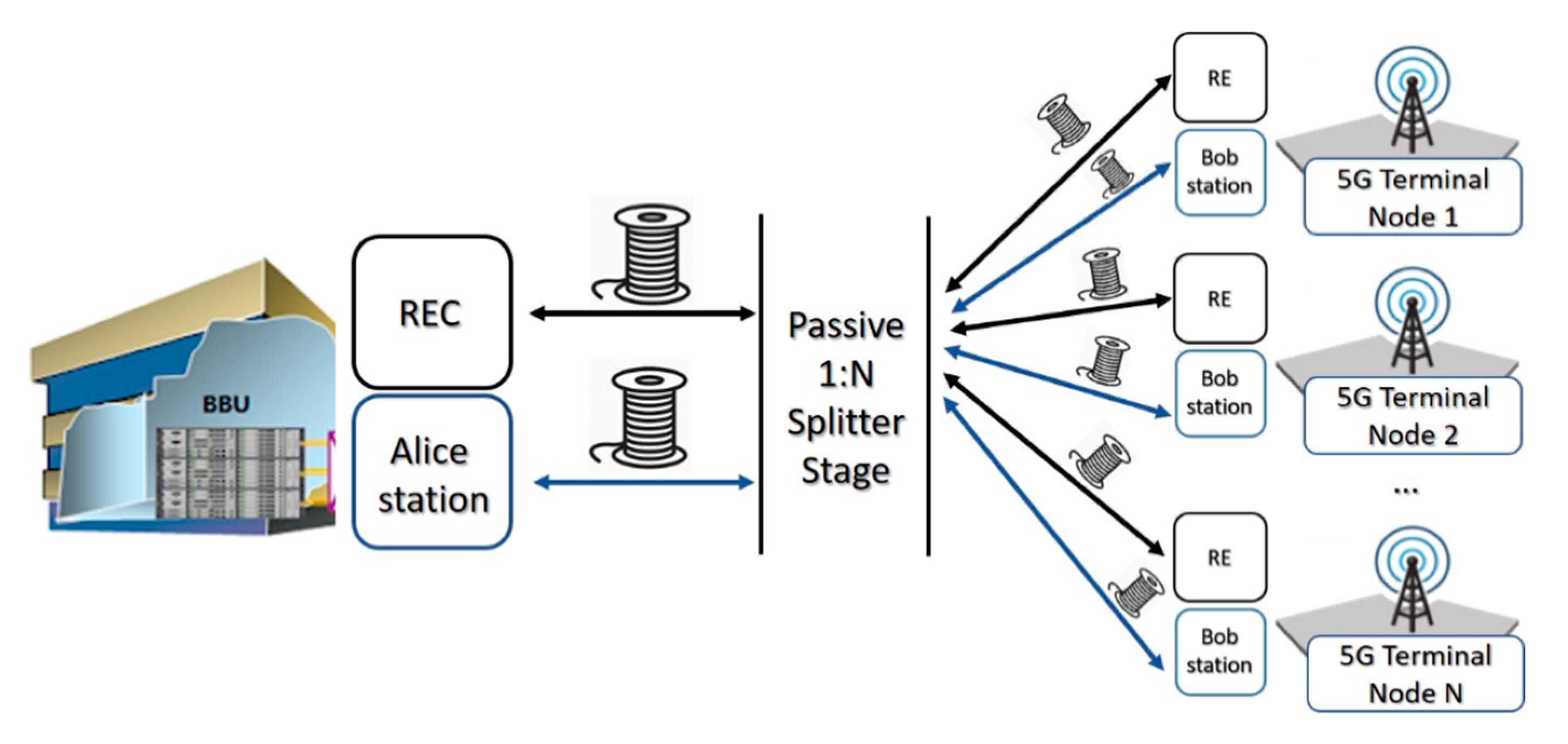
2.2. Shared Fiber Topology
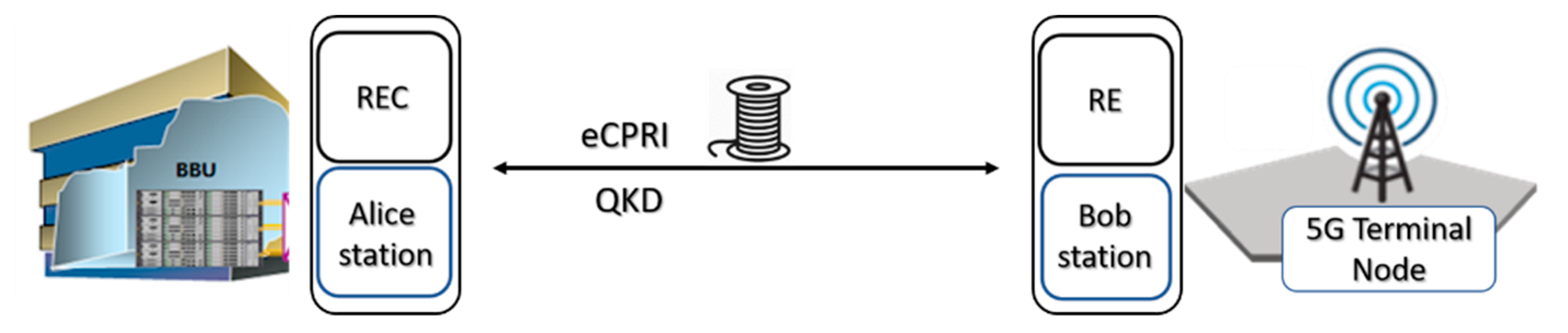
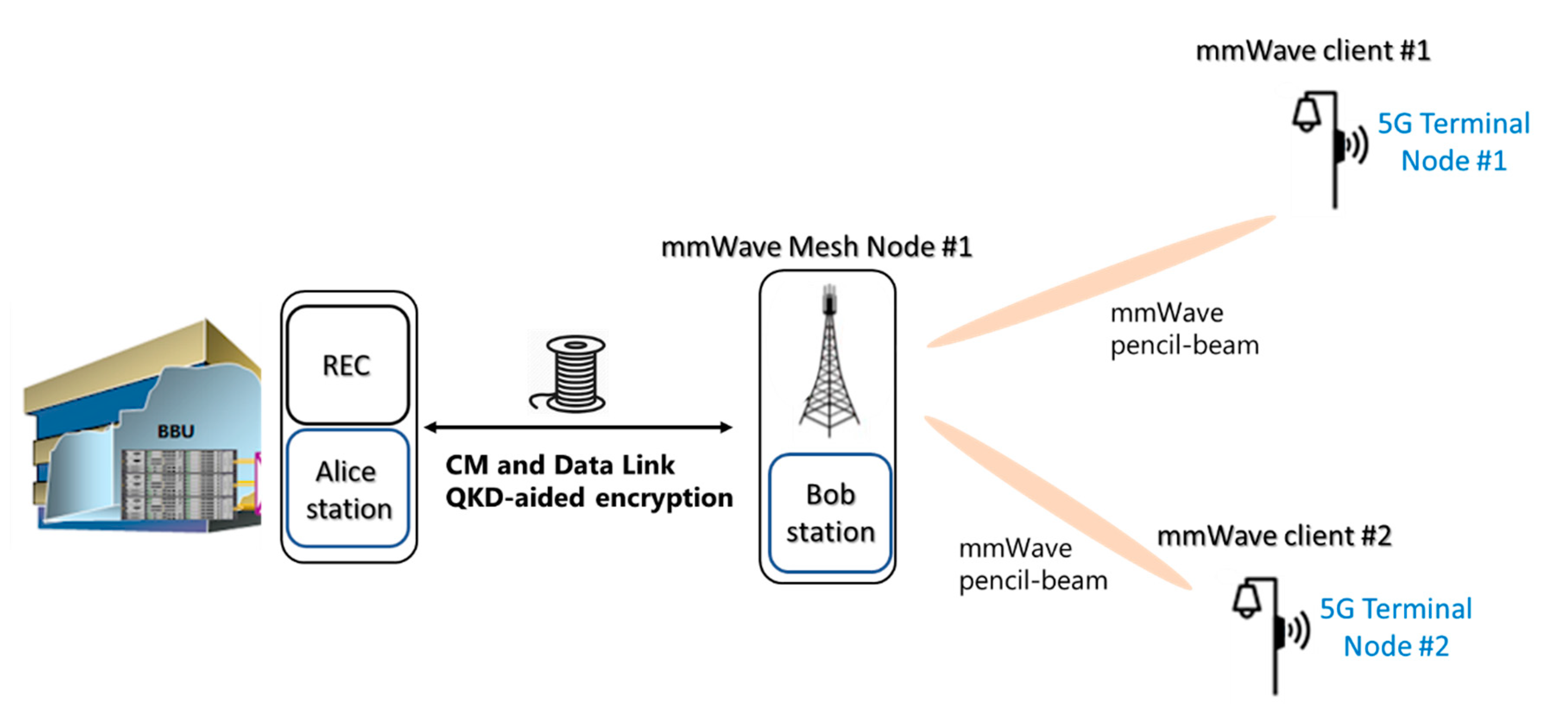
2.3. Fiber-Wireless Topology
3. Results
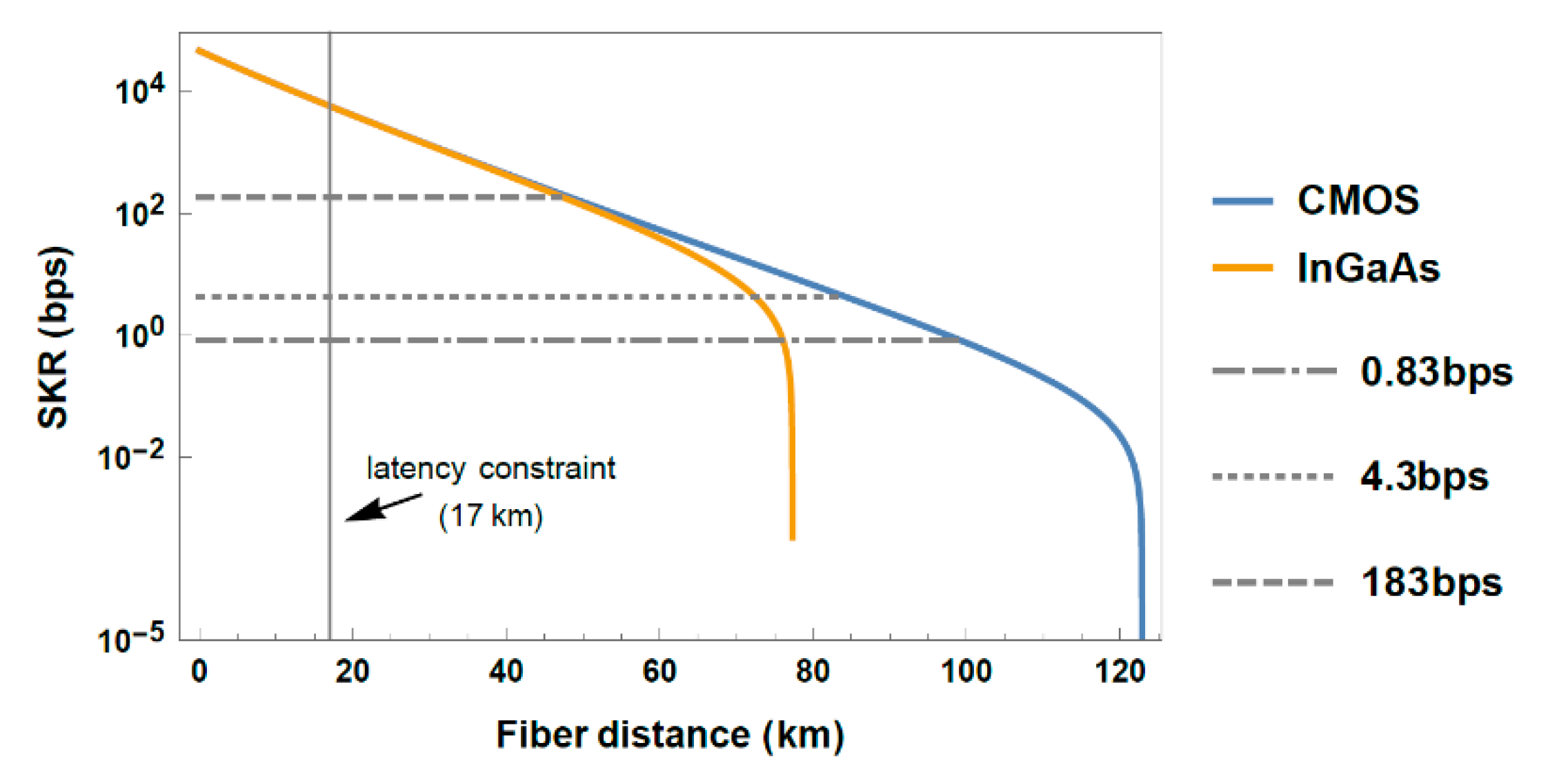
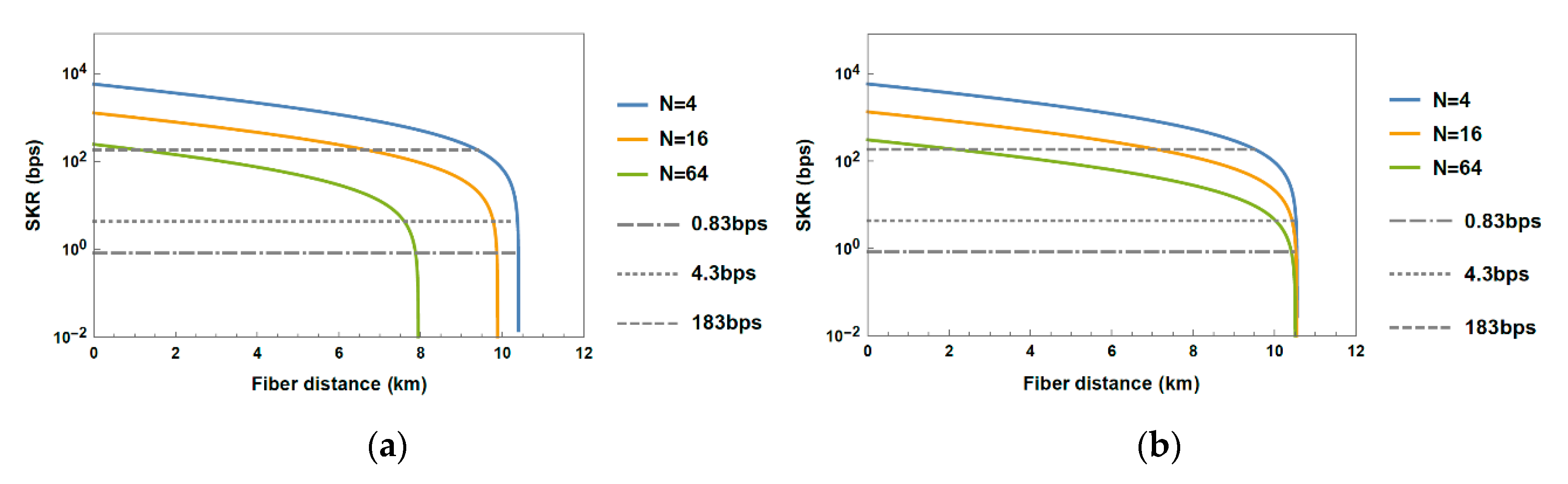
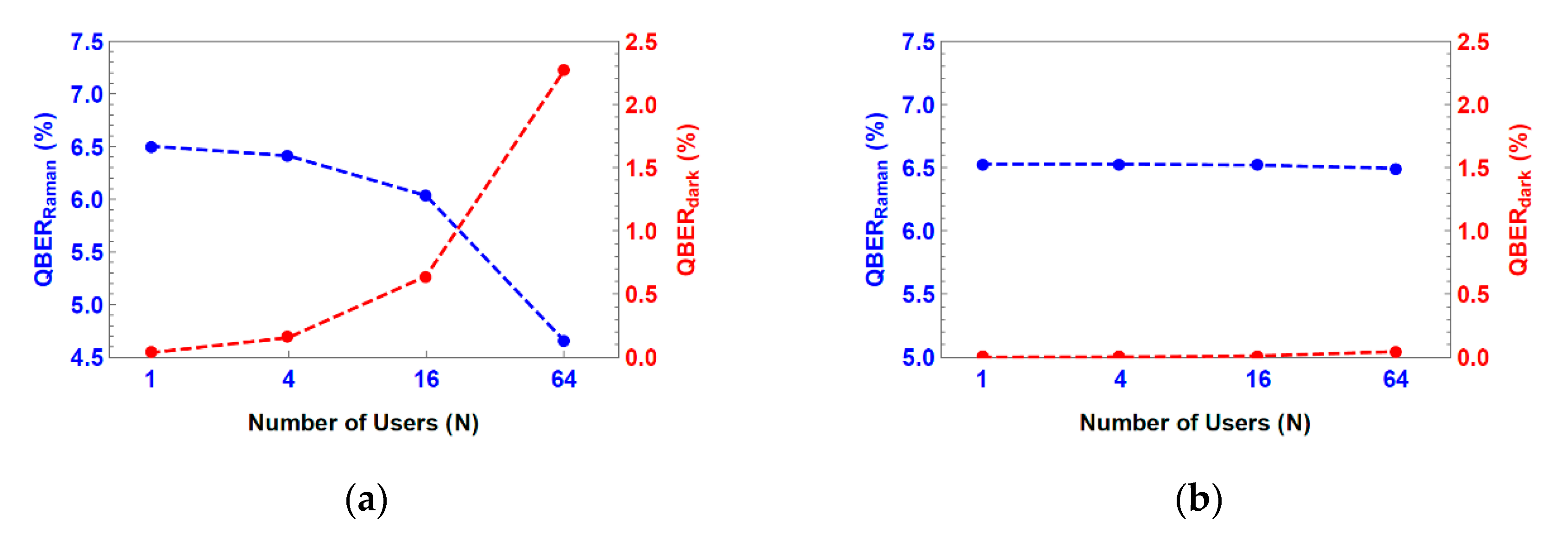
3.1. Performance Evaluation of Dark Fiber Topology
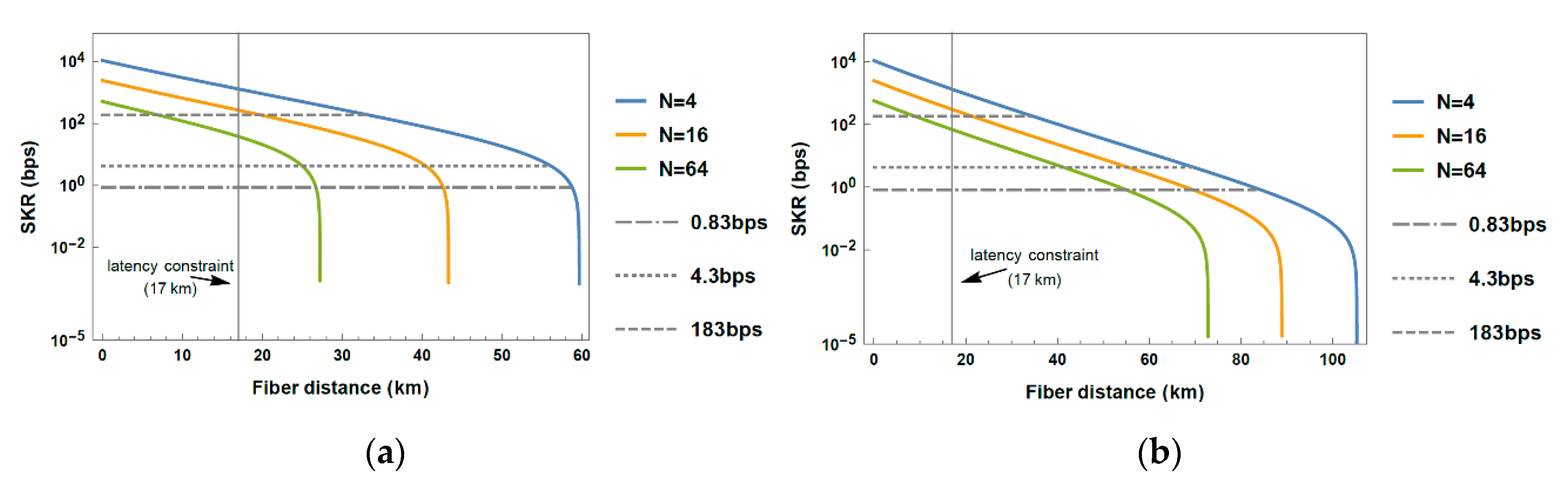
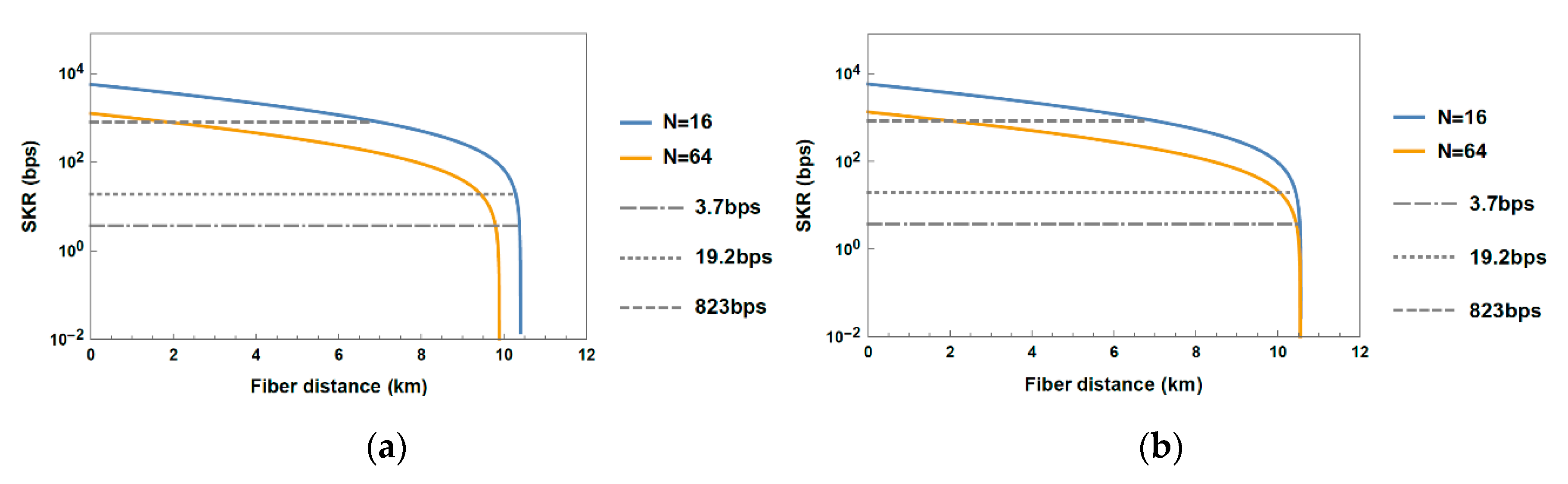
3.2. Performance Evaluation of Shared Fiber Topology
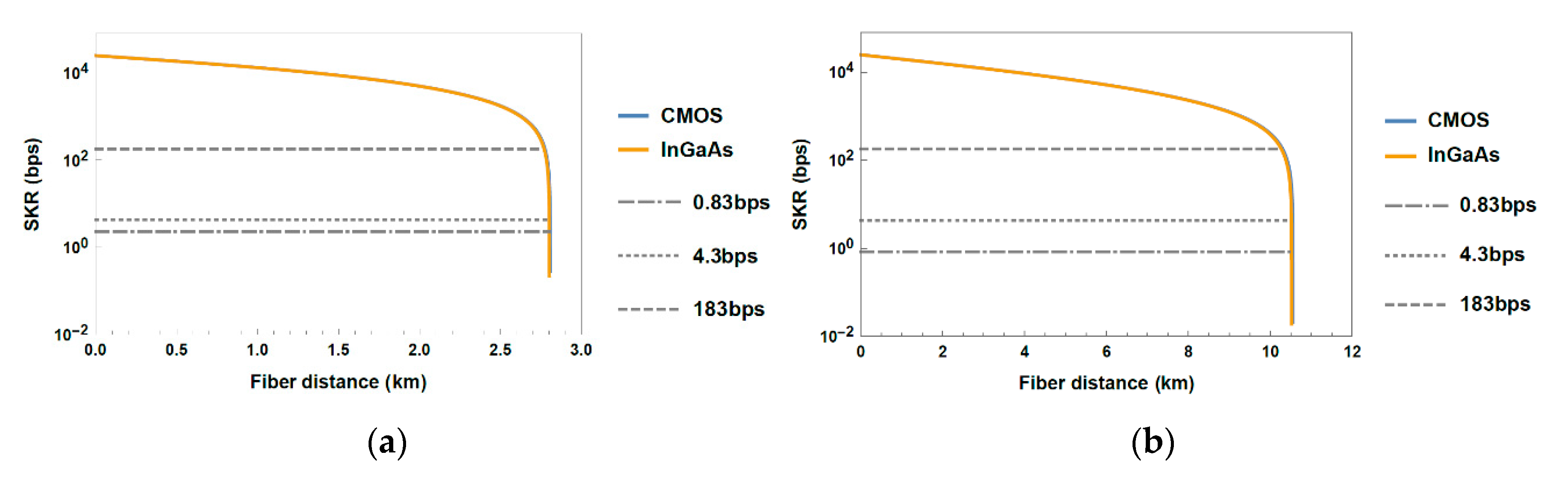
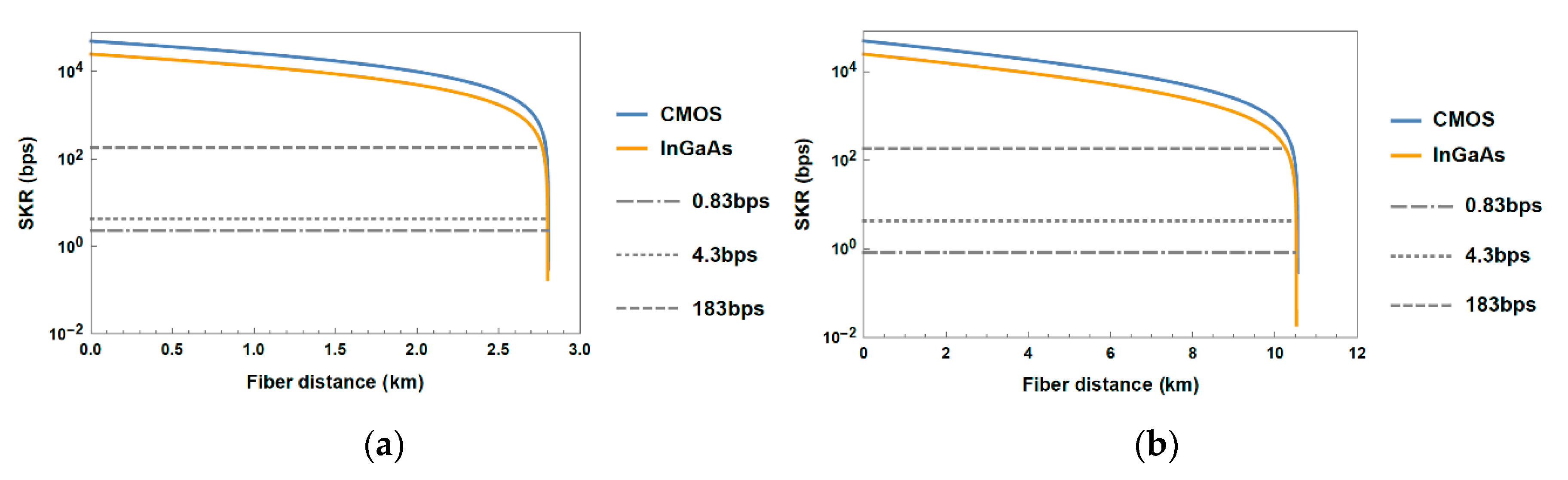
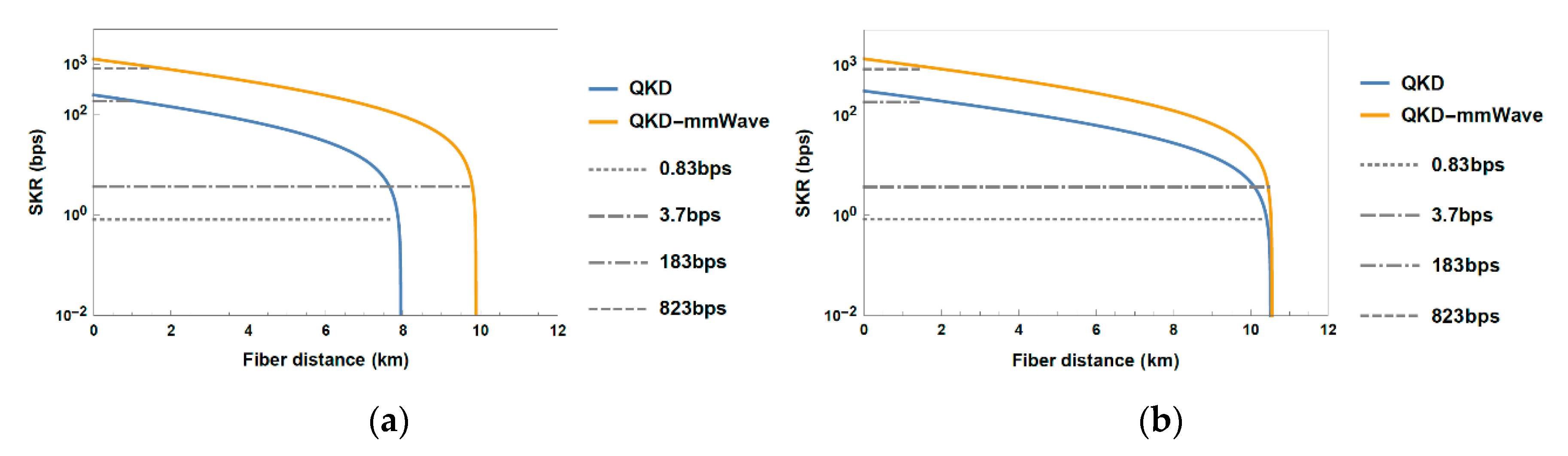
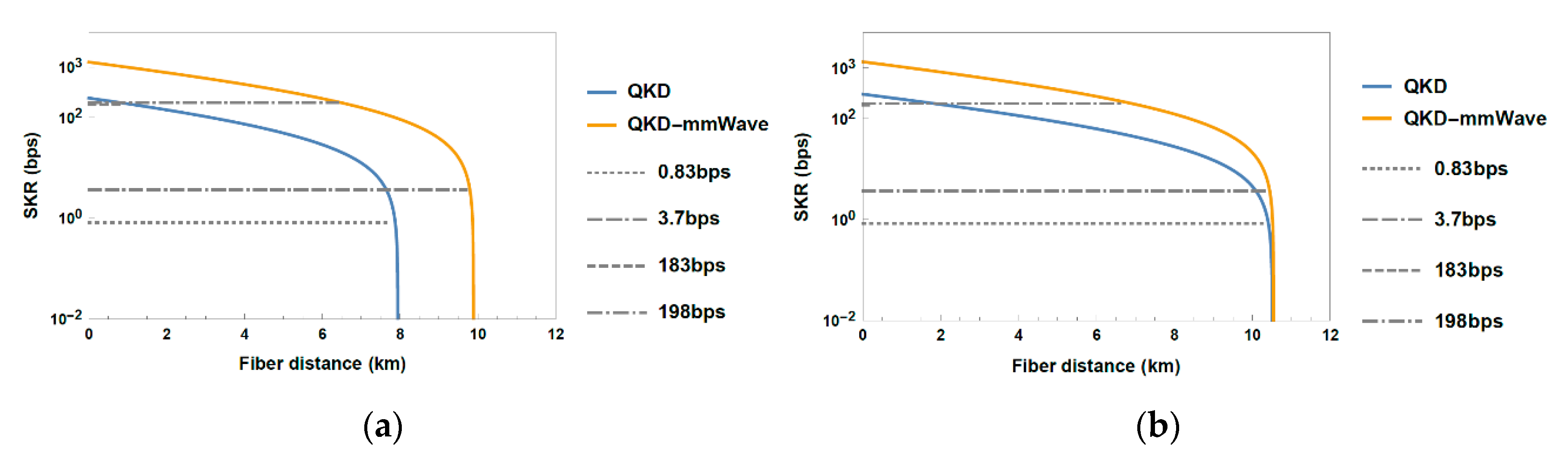
3.3. Performance Evaluation of Fiber-Wireless Topology
4. Discussion
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A. Maximum Fiber Fronthaul Distance Corresponding to Round-Trip Latency Barrier
References
- Sim, D.-H. Quantum Safe Communication—Preparing for the Next Era. In Proceedings of the Presentation in ITU Workshop on Quantum Information Technology, Shanghai, China, 5–7 June 2019. [Google Scholar]
- Tomkos, I.; Klonidis, D.; Pikasis, E.; Theodoridis, S. Toward the 6G network era: Opportunities and challenges. IT Prof. 2020, 22, 34–38. [Google Scholar] [CrossRef]
- Bernstein, D.J. Introduction to post-quantum cryptography. In Post-Quantum Cryptography; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–14. [Google Scholar]
- Diamanti, E.; Lo, H.K.; Qi, B.; Yuan, Z. Practical challenges in quantum key distribution. NPJ Quantum Inf. 2016, 2, 1–12. [Google Scholar] [CrossRef]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Modern Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Liao, S.-K.; Cai, W.-Q.; Handsteiner, J.; Liu, B.; Yin, J.; Zhang, L.; Rauch, D.; Fink, M.; Ren, J.-G.; Liu, W.; et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett. 2018, 120, 030501. [Google Scholar] [CrossRef] [PubMed]
- Community Response to the NCSC 2020 Quantum Security Technologies White Paper. Available online: https://www.quantumcommshub.net/wp-content/src/Response-to-NCSC-QSC-WP-Issue-1.1-27_5_2020.pdf (accessed on 24 June 2020).
- Dowling, B.; Hansen, T.B.; Paterson, K.G. Many a Mickle Makes a Muckle: A Framework for Provably Quantum-Secure Hybrid Key Exchange. In Proceedings of the International Conference on Post-Quantum Cryptography, Paris, France, 15–17 April 2020; pp. 483–502. [Google Scholar]
- Post-Quantum Cryptography. Workshops and Timeline. Available online: https://csrc.nist.gov/Projects/post-quantum-cryptography/workshops-and-timeline (accessed on 24 June 2020).
- ADVA achieves world-first 100G Quantum-Safe Transport Over 2800 km. Available online: https://www.adva.com/en/newsroom/press-releases/20180613-adva-achieves-world-first-100g-quantum-safe-transport-over-2800km (accessed on 24 June 2020).
- Bonnetain, X.; Naya-Plasencia, M.; Schrottenloher, A. Quantum Security Analysis of AES. IACR Trans. Symmetric Cryptol. 2019, 2, 55–93. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 1999, 283, 2050–2056. [Google Scholar] [CrossRef]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef]
- Mayers, D. Unconditional security in quantum cryptography. J. ACM 2001, 48, 351–406. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Tamaki, K. Secure quantum key distribution. Nat. Photonics 2014, 8, 595–604. [Google Scholar] [CrossRef]
- Wright, P.; White, C.; Parker, R.C.; Pegon, J.-S.; Menchetti, M.; Pearse, J.; Bahrami, A.; Moroz, A.; Wonfor, A.; Penty, R.V.; et al. 5G Network Slicing with QKD and Quantum-Safe Security. arXiv Preprint 2020, arXiv:2007.03377. [Google Scholar]
- OIDA. OIDA Quantum Photonics Roadmap: Every Photon Counts. OIDA Report, 3; OSA Industry Development Associates (OIDA). 2020. Available online: https://www.osapublishing.org/abstract.cfm?uri=OIDA-2020-3 (accessed on 10 June 2020).
- Chen, J.-P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.-L.; Guan, J.-Y.; Yu, Z.-W.; Xu, H.; Lin, J.; et al. Sending-or-Not-Sending with Independent Lasers: Secure Twin-Field Quantum Key Distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef]
- UNIQORN Objectives. Available online: https://quantum-uniqorn.eu/home/technology-lines/saftey-security-design-methods/ (accessed on 23 June 2020).
- Eriksson, T.A.; Hirano, T.; Puttnam, B.J.; Rademacher, G.; Luís, R.S.; Fujiwara, M.; Namiki, R.; Awaji, Y.; Takeoka, M.; Wada, N.; et al. Wavelength division multiplexing of continuous variable quantum key distribution and 18.3 Tbit/s data channels. Commun. Phys. 2019, 2, 1–8. [Google Scholar] [CrossRef]
- Lai, J.S.; Lin, X.Y.; Qian, Y.; Liu, L.; Zhao, W.Y.; Zhang, H.Y. Deployment-oriented integration of DV-QKD and 100 G optical transmission system. In Proceedings of the Asia Communications and Photonics Conference, Optical Society of America. Chengdu, China, 2–5 November 2019; p. T2H-1. [Google Scholar]
- Aleksic, S.; Winkler, D.; Franzl, G.; Poppe, A.; Schrenk, B.; Hipp, F. Quantum key distribution over optical access networks. In Proceedings of the 2013 18th European Conference on Network and Optical Communications & 2013 8th Conference on Optical Cabling and Infrastructure (NOC-OC&I), Graz, Austria, 10–12 July 2013; pp. 11–18. [Google Scholar]
- Qi, B.; Zhu, W.; Qian, L.; Lo, H.K. Feasibility of quantum key distribution through a dense wavelength division multiplexing network. New J. Phys. 2010, 12, 103042. [Google Scholar] [CrossRef]
- Choi, I.; Zhou, Y.R.; Dynes, J.F.; Yuan, Z.; Klar, A.; Sharpe, A.; Plews, A.; Lucamarini, M.; Radig, C.; Neubert, J.; et al. Field trial of a quantum secured 10 Gb/s DWDM transmission system over a single installed fiber. Opt. Express 2014, 22, 23121–23128. [Google Scholar] [CrossRef]
- Wang, R.; Wang, Q.; Kanellos, G.T.; Nejabati, R.; Simeonidou, D.; Tessinari, R.S.; Hugues-Salas, E.; Bravalheri, A.; Uniyal, N.; Muqaddas, A.S.; et al. End-to-End Quantum Secured Inter-Domain 5G Service Orchestration Over Dynamically Switched Flex-Grid Optical Networks Enabled by a q-ROADM. J. Light. Technol. 2020, 38, 139–149. [Google Scholar] [CrossRef]
- Kong, W.; Sun, Y.; Cai, C.; Ji, Y. Impact of Modulation Formats and Bandwidth on Quantum Secured 5G Optical Fronthaul over Multicore Fiber. In Proceedings of the CLEO 2020, Washington, DC, USA, 10–15 May 2020. [Google Scholar]
- Hugues-Salas, E.; Alia, O.; Wang, R.; Rajkumar, K.; Kanellos, G.T.; Nejabati, R.; Simeonidou, D. 11.2 Tb/s Classical Channel Coexistence with DV-QKD over a 7-Core Multicore Fiber. J. Light. Technol. 2020, 1. [Google Scholar] [CrossRef]
- Cho, J.Y.; Sergeev, A.; Zou, J. Securing Ethernet-based Optical Fronthaul for 5G Network. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; pp. 1–6. [Google Scholar]
- Common Public Radio Interface: ECPRI Interface Specification v1.2. Available online: http://www.cpri.info/spec.html (accessed on 26 June 2020).
- Pérez, G.O.; López, D.L.; Hernández, J.A. 5G new radio fronthaul network design for eCPRI-IEEE 802.1 CM and extreme latency percentiles. IEEE Access 2019, 7, 82218–82230. [Google Scholar] [CrossRef]
- IEEE Standard for Local and Metropolitan Area Networks-IEEE Time Sensitive Networking for Fronthaul, IEEE Standard 802.1cm. 2018. Available online: http://www.ieee802.org/1/pages/802.1cm.html (accessed on 26 June 2020).
- Kong, L.; Li, Z.; Li, C.; Cao, L.; Xing, Z.; Cao, J.; Wang, Y.; Cai, X.; Zhou, X. Photonic integrated quantum key distribution receiver for multiple users. Opt. Express 2020, 28, 18449–18455. [Google Scholar] [CrossRef]
- Hübel, H. All you Need to Know about UNIQORN. Available online: https://quantum-uniqorn.eu/wp-content/uploads/2019/02/UNIQORN-summary-EQTC-Grenoble.pdf (accessed on 27 June 2020).
- Townsend, P.D. Quantum cryptography on multiuser optical fibre networks. Nature 1997, 385, 47–49. [Google Scholar] [CrossRef]
- Eraerds, P.; Walenta, N.; Legré, M.; Gisin, N.; Zbinden, H. Quantum key distribution and 1 Gbps data encryption over a single fibre. New J. Phys. 2010, 12, 063027. [Google Scholar] [CrossRef]
- Jain, N. Security of Practical Quantum Key Distribution Systems. PhD Thesis, Friedrich-Alexander-Universität Erlangen-Nürnberg, Bavaria, Germany, 2015. [Google Scholar]
- idQuantique. Available online: www.idQuantique.com (accessed on 18 June 2020).
- Mlejnek, M.; Kaliteevskiy, N.A.; Nolan, D.A. Reducing spontaneous Raman scattering noise in high quantum bit rate QKD systems over optical fiber. arXiv Preprint 2017, arXiv:1712.05891. [Google Scholar]
- Aurea Technology Single Photon Counting Module: SPD_A_NIR Datasheet. Available online: http://www.aureatechnology.com/images/produits/AUREA_Datasheet_SPD_A_NIR_V1.1_2018_light.pdf (accessed on 26 June 2020).
- Ma, F.; Liang, L.-Y.; Chen, J.-P.; Gao, Y.; Zheng, M.-Y.; Xie, X.-P.; Liu, H.; Zhang, Q.; Pan, J.-W. Upconversion single-photon detectors based on integrated periodically poled lithium niobate waveguides [Invited]. J. Opt. Soc. Am. B 2018, 35, 2096–2101. [Google Scholar] [CrossRef]
- Niederberger, A.; Scarani, V.; Gisin, N. Photon-number-splitting versus cloning attacks in practical implementations of the Bennett-Brassard 1984 protocol for quantum cryptography. Phys. Rev. A 2005, 71, 042316. [Google Scholar] [CrossRef]
- Shields, A. Performance Limits for Quantum Key Distribution Networks. In Proceedings of the Presentation in ITU Workshop on Quantum Information Technology, Shanghai, China, 5–7 June 2019. [Google Scholar]
- Dynes, J.F.; Wonfor, A.; Tam, W.W.-S.; Sharpe, A.W.; Takahashi, R.; Lucamarini, M.; Plews, A.; Yuan, Z.; Dixon, A.R.; Cho, J.; et al. Cambridge quantum network. npj Quantum Inf. 2019, 5, 1–8. [Google Scholar] [CrossRef]
- Luykx, A.; Paterson, K.G. Limits on Authenticated Encryption Use in TLS. 2015. Available online: https://www.isg.rhul.ac.uk/~kp/TLS-AEbounds.pdf (accessed on 26 June 2020).
- Kumar, R.; Qin, H.; Alléaume, R. Coexistence of continuous variable QKD with intense DWDM classical channels. New J. Phys. 2015, 17, 043027. [Google Scholar] [CrossRef]
- Patel, K.A.; Dynes, J.F.; Choi, I.; Sharpe, A.W.; Dixon, A.R.; Yuan, Z.L.; Penty, R.V.; Shields, A.J. Coexistence of High-Bit-Rate Quantum Key Distribution and Data on Optical Fiber. Phys. Rev. X 2012, 2, 041010. [Google Scholar] [CrossRef]
- Fröhlich, B.; Dynes, J.F.; Lucamarini, M.; Sharpe, A.W.; Tam, S.W.B.; Yuan, Z.; Shields, A.J. Quantum secured gigabit optical access networks. Sci. Rep. 2015, 5, 1–7. [Google Scholar] [CrossRef]
- Zavitsanos, D.; Giannoulis, G.; Raptakis, A.; Papapanos, C.; Setaki, F.; Theodoropoulou, E.; Lyberopoulos, G.; Kouloumentas, C.; Avramopoulos, H. Coexistence of Discrete-Variable QKD with WDM classical signals in the C-band for fiber access environments. In Proceedings of the 2019 21st International Conference on Transparent Optical Networks (ICTON), Université d’Angers, France, 9–13 July 2019; pp. 1–5. [Google Scholar]
- Peters, N.A.; Toliver, P.; Chapuran, T.E.; Runser, R.J.; McNown, S.R.; Peterson, C.G.; Rosenberg, D.; Dallmann, N.; Hughes, R.J.; McCabe, K.P.; et al. Dense wavelength multiplexing of 1550 nm QKD with strong classical channels in reconfigurable networking environments. New J. Phys. 2009, 11, 045012. [Google Scholar] [CrossRef]
- Runser, R.J.; Chapuran, T.; Toliver, P.; Peters, N.A.; Goodman, M.S.; Kosloski, J.T.; Nweke, N.; McNown, S.R.; Hughes, R.J.; Rosenberg, D.; et al. Progress toward quantum communications networks: Opportunities and challenges. In Optoelectronic Integrated Circuits IX; International Society for Optics and Photonics: San Jose, CA, USA, 2007; Volume 6476, p. 64760I. [Google Scholar]
- Yan, C.; Yong, S.; Guang-Zhao, T.; Hong-Xin, Z. Impact of cross-phase modulation induced by classical channels on the CV-QKD in a hybrid system. Chin. Phys. Lett. 2013, 30, 110302. [Google Scholar]
- Kingfisher International. Optical Loss & Testing Overview. Available online: https://kingfisherfiber.com/application-notes/optical-loss-testing-overview/ (accessed on 22 June 2020).
- Schrenk, B.; Hentschel, M.; Hübel, H. O-band differential phase-shift quantum key distribution in 52-channel C/L-band loaded passive optical network. In Proceedings of the 2019 Optical Fiber Communications Conference and Exhibition (OFC), San Diego Convention Center, CA, USA, 3–7 March 2019; pp. 1–3. [Google Scholar]
- Oughton, E.J.; Frias, Z. The cost, coverage and rollout implications of 5G infrastructure in Britain. Telecommun. Policy 2018, 42, 636–652. [Google Scholar] [CrossRef]
- Du, J.; Chizhik, D.; Feick, R.; Rodriguez, M.; Castro, G.; Valenzuela, R.A. Suburban fixed wireless access channel measurements and models at 28 GHz for 90% outdoor coverage. IEEE Trans. Antennas Propag. 2019, 68, 411–420. [Google Scholar] [CrossRef]
- Kanta, K.; Pagano, A.; Ruggeri, E.; Agus, M.; Stratakos, I.; Mercinelli, R.; Vagionas, C.; Toumasis, P.; Kalfas, G.; Giannoulis, G.; et al. Analog fiber-wireless downlink transmission of IFoF/mmWave over in-field deployed legacy PON infrastructure for 5G fronthauling. IEEE/OSA J. Optical Commun. Netw. 2020, 12, D57–D65. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, H.; Hou, S.; Zhao, Z.; Xu, H.; Wu, X.; Wu, Q.; Zhang, R. A Survey on 5G Millimeter Wave Communications for UAV-Assisted Wireless Networks. IEEE Access 2019, 7, 117460–117504. [Google Scholar] [CrossRef]
- Butnaru, S. Siklu Announces the Multi-Gigabit MultiHaul™ Mesh Node N360. Available online: https://www.siklu.com/press-release/siklu-announces-the-multi-gigabit-multihaul-mesh-node-n360/ (accessed on 28 June 2020).
- Siklu. Encryption & Etherhaul 7xx, Edition B1. Available online: https://www.siklu.com/wp-content/uploads/2018/12/2018-12-EH-7xx-and-Encryption-Ed.-B1.pdf (accessed on 24 June 2020).
- Siklu. mmWave Wireless Fiber Frequently Asked Questions. Available online: https://www.siklu.com/mmwave-wireless-fiber-faq/ (accessed on 24 June 2020).
- Benslama, M.; Benslama, A.; Aris, S. Quantum Communications in New Telecommunications Systems; John Wiley & Sons: Hoboken, NJ, USA, 2017. [Google Scholar]
- Revealed: 5G Rollout is Being Stalled by Rows over Lampposts. Available online: https://www.theguardian.com/technology/2019/may/19/revealed-5g-rollout-is-being-stalled-by-rows-over-lampposts (accessed on 27 June 2020).
- Giannoulis, G.; Tokas, K.; Poulopoulos, G.; Kanakis, G.; Toumasis, P.; Kanta, K.; Apostolopoulos, D.; Avramopoulos, H. Integrated Photonic Filters in Support of Converged 5G Mobile Fronthaul & Midhaul Transport Layers. Fiber Integr. Opt. 2019, 38, 333–348. [Google Scholar]
- Bidkar, S.; Galaro, J.; Pfeiffer, T. First demonstration of an ultra-low-latency fronthaul transport over a commercial TDM-PON platform. In Proceedings of the 2018 Optical Fiber Communications Conference and Exposition (OFC), San Diego Convention Center, CA, USA, 11–15 March 2018; pp. 1–3. [Google Scholar]
- Vokić, N.; Milovančev, D.; Schrenk, B.; Hentschel, M.; Hübel, H. Differential Phase-Shift QKD in a 2: 16-Split Lit PON with 19 Carrier-Grade Channels. IEEE J. Sel. Top. Quantum Electron. 2020, 26, 1–9. [Google Scholar] [CrossRef]
- 5G-COMPLETE. Available online: https://5gcomplete.eu/ (accessed on 27 June 2020).
- Paoloni, C.; Krozer, V.; Magne, F.; Le, Q.T.; Basu, R.; Rao, J.; Yacob, H. D-band Point to Multi-Point Deployment with G-Band Transport. In Proceedings of the EuCNC 2020, Dubrovnik, Croatia, 16–17 June 2020. [Google Scholar]
- Federici, J.; Moeller, L. Review of terahertz and subterahertz wireless communications. J. Appl. Phys. 2010, 107, 6. [Google Scholar] [CrossRef]
- Wehner, S.; Elkouss, D.; Hanson, R. Quantum internet: A vision for the road ahead. Science 2018, 362, eaam9288. [Google Scholar] [CrossRef]
- Pirker, A.; Wallnöfer, J.; Dür, W. Modular architectures for quantum networks. New J. Phys. 2018, 20, 053054. [Google Scholar] [CrossRef]
- Elshaari, A.W.; Pernice, W.H.P.; Srinivasan, K.; Benson, O.; Zwiller, V. Hybrid integrated quantum photonic circuits. Nat. Photon 2020, 14, 285–298. [Google Scholar] [CrossRef]
- Lu, H.; Huang, C.-Y.; Li, Z.-D.; Yin, X.-F.; Zhang, R.; Liao, T.-L.; Chen, Y.-A.; Li, C.-M.; Pan, J.-W. Counting Classical Nodes in Quantum Networks. Phys. Rev. Lett. 2020, 124, 180503. [Google Scholar] [CrossRef]
- Yuan, Z.; Murakami, A.; Kujiraoka, M.; Lucamarini, M.; Tanizawa, Y.; Sato, H.; Shields, A.J.; Plews, A.; Takahashi, R.; Doi, K.; et al. 10-Mb/s quantum key distribution. J. Light. Technol. 2018, 36, 3427–3433. [Google Scholar] [CrossRef]

| Latency Components | |
|---|---|
| Round-Trip Delay Components | Typical Time |
| Propagation fiber delay | 10 μs/km |
| Radio Frequency (RF) overhead | 40 μs |
| eCPRI overhead | 10 μs |
| BBU | 2700 μs |
| Fronthaul equipment processing delay | 4 μs |
| One-way encryption/decryption | 34 μs |
| QKD post-processing | 11 μs |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zavitsanos, D.; Ntanos, A.; Giannoulis, G.; Avramopoulos, H. On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul. Appl. Sci. 2020, 10, 5193. https://doi.org/10.3390/app10155193
Zavitsanos D, Ntanos A, Giannoulis G, Avramopoulos H. On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul. Applied Sciences. 2020; 10(15):5193. https://doi.org/10.3390/app10155193
Chicago/Turabian StyleZavitsanos, Dimitris, Argiris Ntanos, Giannis Giannoulis, and Hercules Avramopoulos. 2020. "On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul" Applied Sciences 10, no. 15: 5193. https://doi.org/10.3390/app10155193
APA StyleZavitsanos, D., Ntanos, A., Giannoulis, G., & Avramopoulos, H. (2020). On the QKD Integration in Converged Fiber/Wireless Topologies for Secured, Low-Latency 5G/B5G Fronthaul. Applied Sciences, 10(15), 5193. https://doi.org/10.3390/app10155193






