Cross-Site Scripting Guardian: A Static XSS Detector Based on Data Stream Input-Output Association Mining
Abstract
1. Introduction
Contributions
- (1)
- Cross-Scripting Guardian: A novel PHP source code vulnerability detector. According to our experimental evaluation, this detector performs better in vulnerability identification compared with related methods. It has guiding significance for the follow-up research of machine learning applied to XSS code audits.
- (2)
- Algorithms for input-output pattern mining: We analyzed the I/O patterns in XSS-related PHP source code and design an algorithm to identify the specific path of the data stream. With this algorithm, it will be more efficient to mine the I/O context and build the precise and consistent TOKEN sequence for representation.
- (3)
- A novel adapted open-sourced PHP code parsing tool [5]: We modify the source code of the VLD to enable it to output richer and more structured parsing information of the PHP source code, which can facilitate the work of parsing and serializing PHP source code.
2. Research Background and Significance
2.1. Background
2.2. Related Work
2.2.1. Code Auditing with Machine Learning
2.2.2. XSS Vulnerability Detection
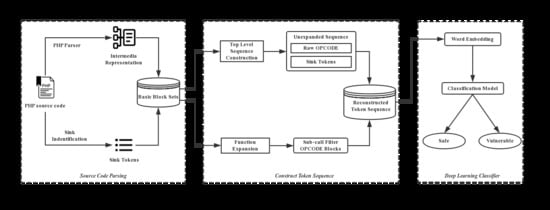
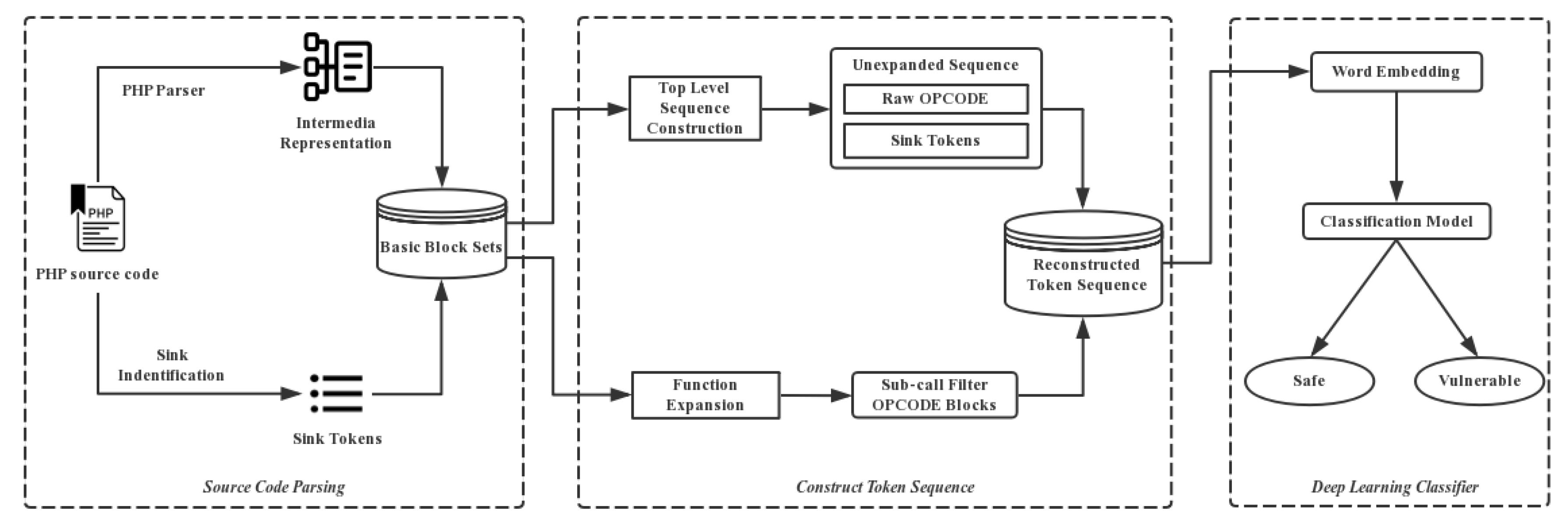
3. Methodology
3.1. Overview of This Section
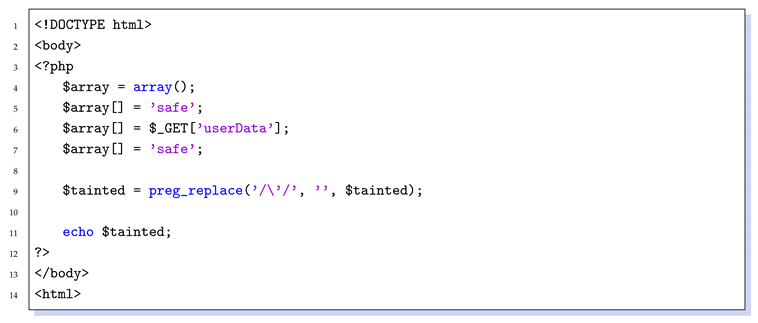
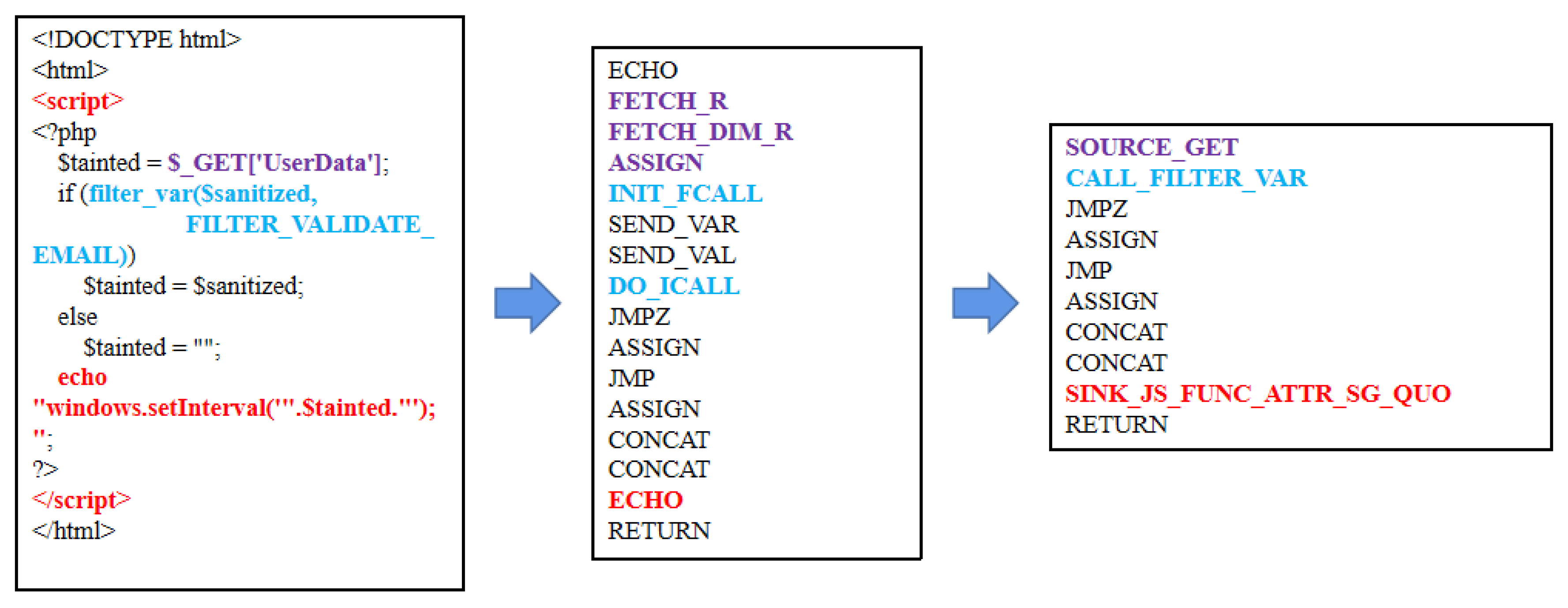
3.2. XSS Triggering in Source Code
| Listing 1: A simple PHP example. |
 |
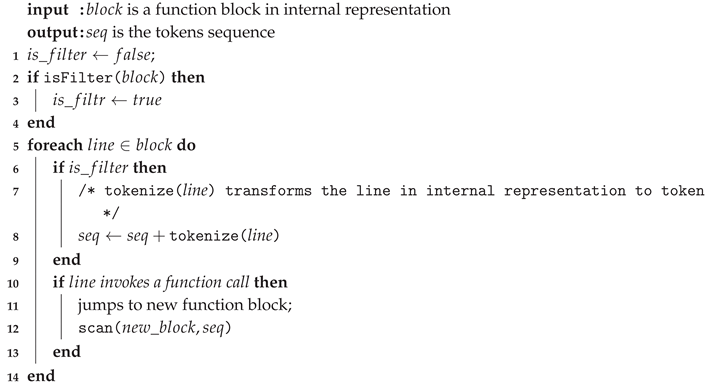
3.3. OPCODE Sequence Clipping and Optimization
| Algorithm 1: isFilter. |
| input: is a function block in internal representation |
| output: or |
| 1 if contains encoding or escapingthen |
| 2 | return |
| 3 else if contains filtering or replacementthen |
| 4 | return |
| 5 else if contains type conversionthen |
| 6 | return |
| 7 else |
| 8 | return |
| 9 end |
- (1)
- Encoding/Escaping: The malicious payloads in most XSS attacks are constructed to add extra tags or attributes to HTML documents, then perform specific operations. In this case, ensuring that payloads from untrusted sources will be output as normal document content is the primary idea. PHP provides a series of builtin functions for this type of work [36]. By encoding or escaping string data, these functions are intended to make them normal text rather than executable code. For example, the function htmlentities converts characters to HTML entities, and the function addslashes add backslashes before symbols such as quotation marks and slashes. Besides, in different scenarios, urlencode, htmlspecialchars can also play this role [37].
- (2)
- Filtering/Replacement: Some developers prefer to use some rules set by themselves to filter or replace the XSS payload that may exist in the input data. For example, the function filter_var is a filter function commonly used by developers. It can match the specified content through specific expressions. The regular replacement represented by the function preg_replace is also a common method to remove XSS vulnerabilities. Such functions are called filtering functions. Analyzing these functions in the code can further audit the effectiveness of the filtering process.
- (3)
- Type conversion: In the major of cases, the program expects user input to be specific datatype to ensure its safety. Thus, function like intval will be used to compulsorily receive a numeric. However, using this method to force data type conversion of input may drop appropriate input, which is similar to a whitelist strategy.
| Algorithm 2: scan. |
 |
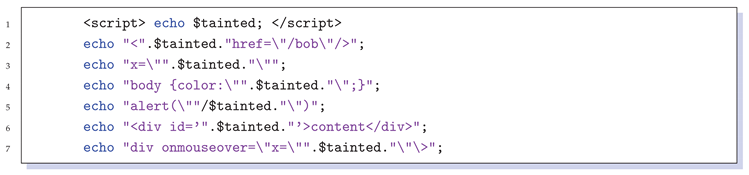
3.4. Proposed Theory of Sink Identification
- (1)
- User input is output without any filtering. This is the most likely scenario to trigger an XSS vulnerability.
- (2)
- User input is filtered to some extent, but the filtering is insufficient or the filtering function is used incorrectly. Sometimes this approach can prevent part of the XSS attacks, but if the attacker uses an advanced bypass method, it can bypass the restriction of filter function and trigger XSS vulnerability.
- (3)
- The code fully considers all the filtering conditions of the relevant output and sets excessively strict filtering functions. In this case, it is impossible for an attacker to trigger an XSS vulnerability. However, this kind of situation is very rare in real web applications.
| Listing 2: Examples of sinks. |
 |
3.5. OPCODE Sequence Embedding
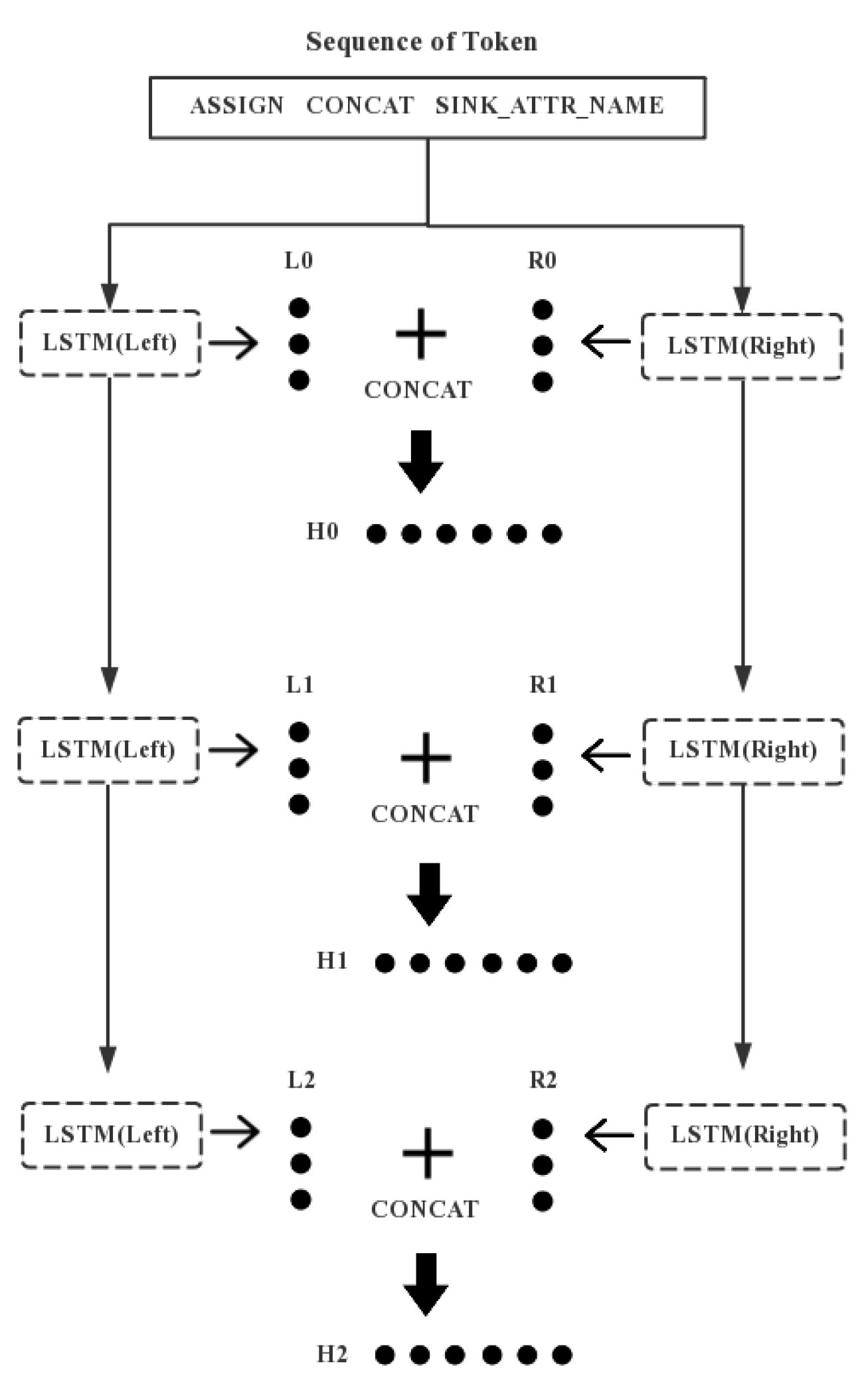
3.6. Bi-LSTM Classifier Construction
4. Experiments and Performances
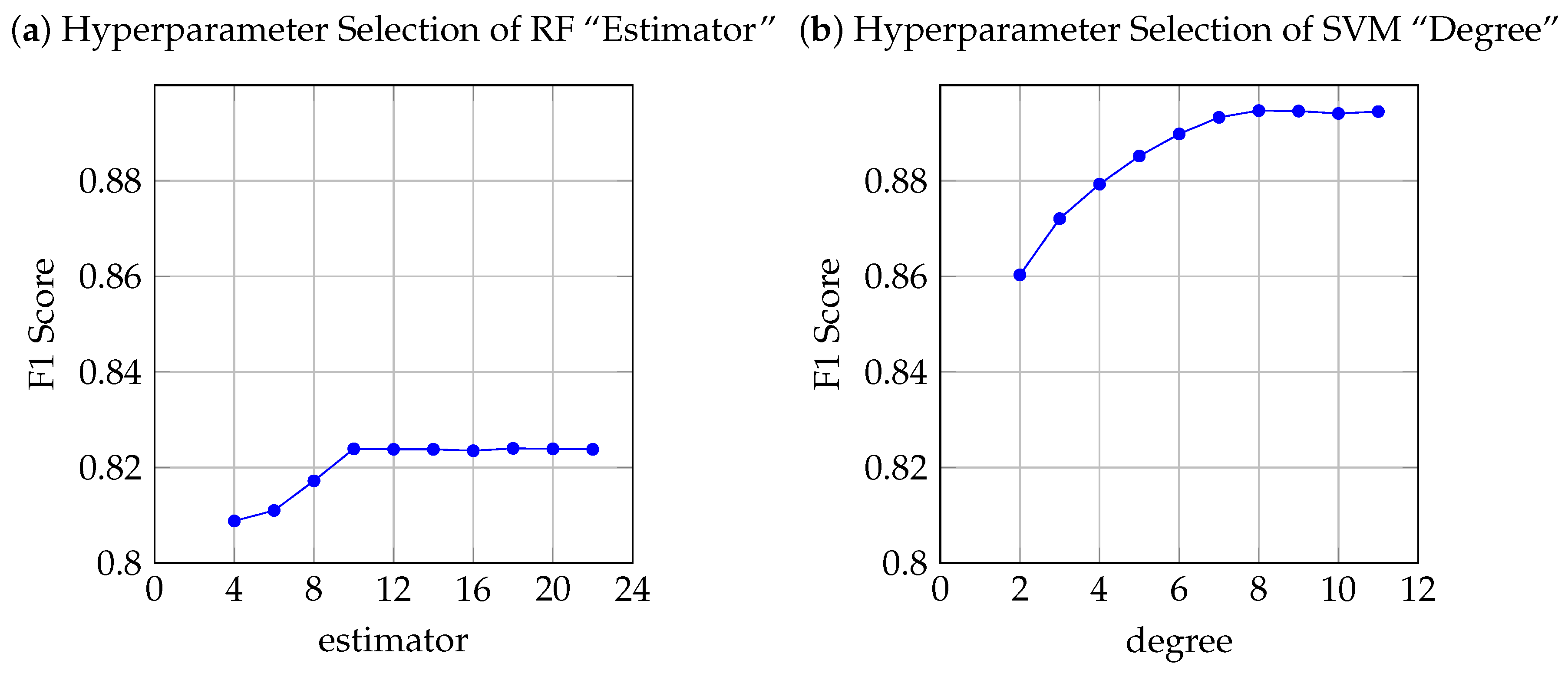
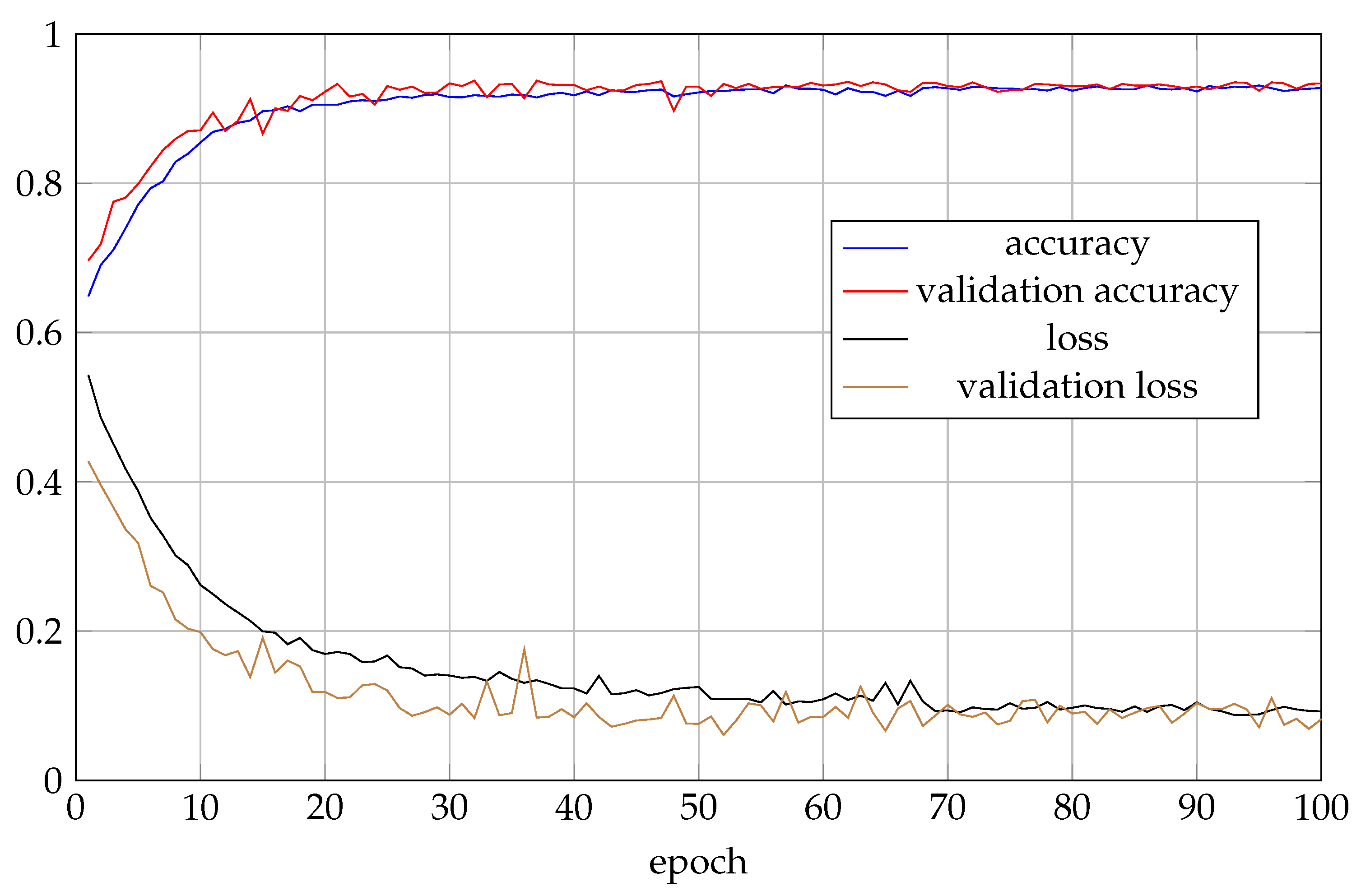
4.1. Experiments Setup
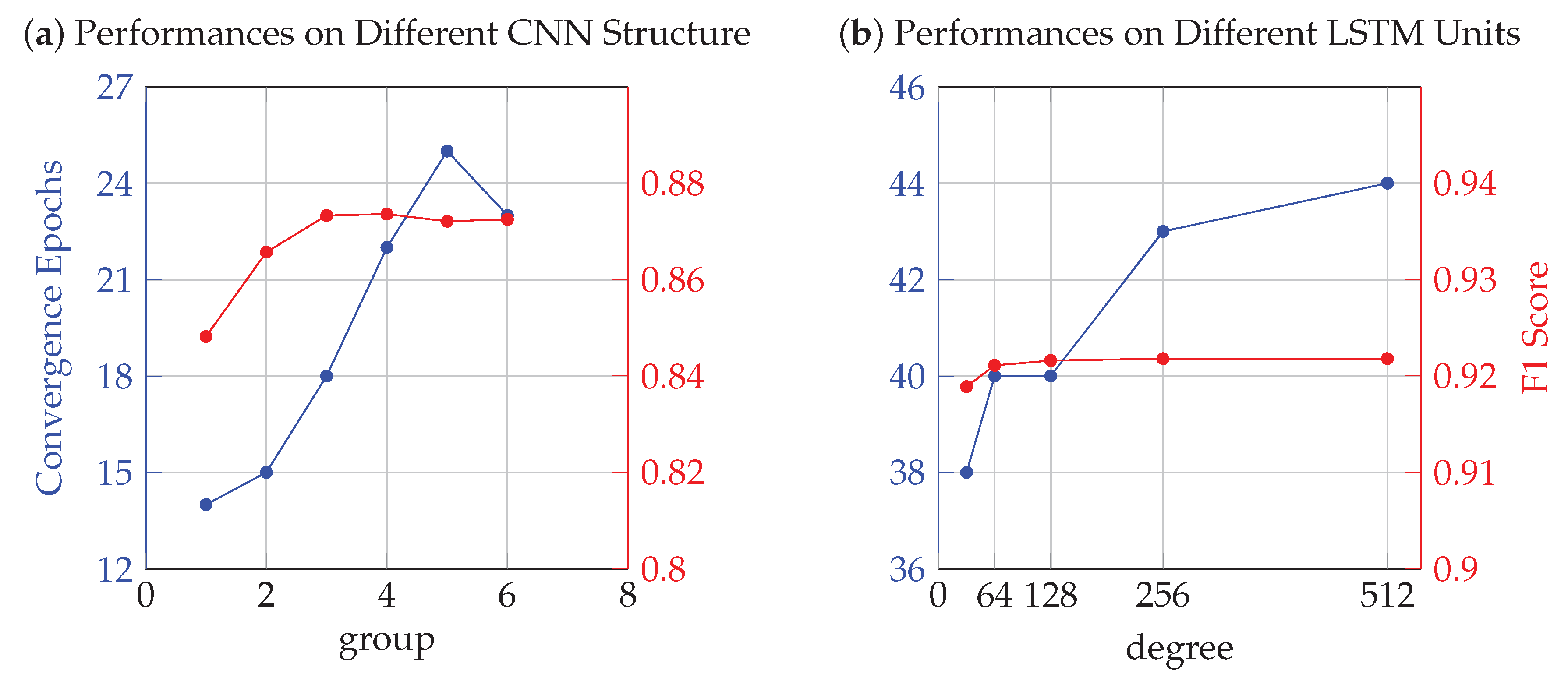
4.2. Comparative Experiment under Different Factors
4.2.1. Comparison of Different TOKEN Sequences
4.2.2. Comparison of Different Classifiers
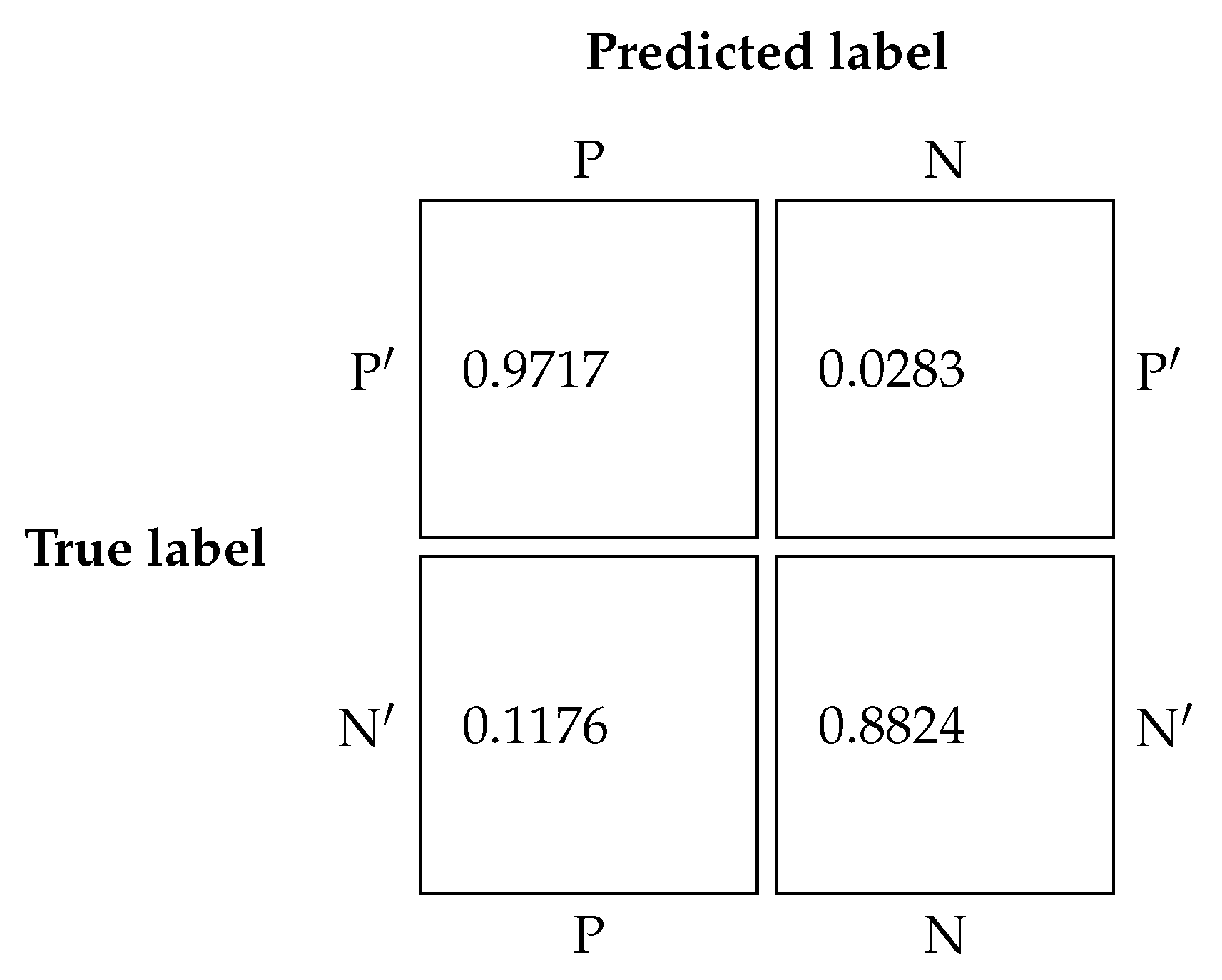
4.3. Generalization Capability Assessment
4.3.1. Evaluation on the Test Dataset
4.3.2. Comparison with Similar Studies
5. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Nirmal, K.; Janet, B.; Kumar, R. It’s More Than Stealing Cookies-Exploitability of XSS. In Proceedings of the 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 14–15 June 2018; pp. 490–493. [Google Scholar]
- Web Applications Vulnerabilities and Threats: Statistics for 2019. Available online: https://www.ptsecurity.com/ww-en/analytics/web-vulnerabilities-2020/ (accessed on 20 February 2020).
- Chen, H.; Huang, B.; Chen, W.; Liu, F. Machine Learning Principles and Applications; University of Electronic Science and Technology Press: Chengdu, China, 2017. [Google Scholar]
- Chen, X.; Li, M.; Jiang, Y.; Sun, Y. A Comparison of Machine Learning Algorithms for Detecting XSS Attacks. In Proceedings of the International Conference on Artificial Intelligence and Security, New York, NY, USA, 26–28 July 2019; pp. 214–224. [Google Scholar]
- Miao, C. VLD with JSON Format Output Support. Available online: https://github.com/ChanthMiao/vld (accessed on 20 February 2020).
- Top 10 Web Application Security Risks. Available online: https://owasp.org/www-project-top-ten/ (accessed on 20 February 2020).
- Aghaei, S.; Nematbakhsh, M.A.; Farsani, H.K. Evolution of the world wide web: From WEB 1.0 TO WEB 4.0. Int. J. Web Semant. Technol. 2012, 3, 1–10. [Google Scholar] [CrossRef]
- Gupta, K.; Singh, R.R.; Dixit, M. Cross site scripting (XSS) attack detection using intrustion detection system. In Proceedings of the 2017 International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 15–16 June 2017; pp. 199–203. [Google Scholar]
- Yamaguchi, F.; Lindner, F.; Rieck, K. Vulnerability extrapolation: Assisted discovery of vulnerabilities using machine learning. In Proceedings of the 5th USENIX Conference on Offensive Technologies, San Francisco, CA, USA, 8 August 2011; p. 13. [Google Scholar]
- Lingzi, X.; Zhi, L. An Overview of Source Code Audit. In Proceedings of the 2015 International Conference on Industrial Informatics-Computing Technology, Intelligent Technology, Industrial Information Integration, Wuhan, China, 3–4 December 2015; pp. 26–29. [Google Scholar]
- Choi, Y.H.; Liu, P.; Shang, Z.; Wang, H.; Wang, Z.; Zhang, L.; Zhou, J.; Zou, Q. Using Deep Learning to Solve Computer Security Challenges: A Survey. arXiv 2019, arXiv:1912.05721. [Google Scholar]
- Liu, S.; Lin, G.; Han, Q.; Wen, S.; Zhang, J.; Xiang, Y. DeepBalance: Deep-Learning and Fuzzy Oversampling for Vulnerability Detection. IEEE Trans. Fuzzy Syst. 2019, 28, 1329–1343. [Google Scholar] [CrossRef]
- Alon, U.; Zilberstein, M.; Levy, O.; Yahav, E. code2vec: Learning distributed representations of code. Proc. ACM Program. Lang. 2019, 3, 1–29. [Google Scholar] [CrossRef]
- Dahse, J.; Schwenk, J. RIPS-A static source code analyser for vulnerabilities in PHP scripts. In Seminar Work (Seminer Çalismasi); Horst Görtz Institute Ruhr-University Bochum: Bochum, Germany, 2010. [Google Scholar]
- Source Code Security Audit. Available online: https://github.com/WhaleShark-Team/cobra (accessed on 20 February 2020).
- WordPress Version 1.5. Available online: https://github.com/WordPress/WordPress/tree/1.5-branch (accessed on 20 February 2020).
- Guo, N.; Li, X.; Yin, H.; Gao, Y. VulHunter: An Automated Vulnerability Detection System Based on Deep Learning and Bytecode. In Proceedings of the International Conference on Information and Communications Security; Beijing, China, 15–17 December 2019, Springer: Berlin/Heidelberg, Germany, 2019; pp. 199–218. [Google Scholar]
- Fang, Y.; Han, S.; Huang, C.; Wu, R. TAP: A static analysis model for PHP vulnerabilities based on token and deep learning technology. PLoS ONE 2019, 14, e0225196. [Google Scholar] [CrossRef] [PubMed]
- Liu, S.; Lin, G.; Qu, L.; Zhang, J.; De Vel, O.; Montague, P.; Xiang, Y. CD-VulD: Cross-Domain Vulnerability Discovery based on Deep Domain Adaptation. IEEE Trans. Dependable Secur. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Gupta, M.K.; Govil, M.C.; Singh, G. Predicting Cross-Site Scripting (XSS) security vulnerabilities in web applications. In Proceedings of the 2015 12th International Joint Conference on Computer Science and Software Engineering (JCSSE), Songkhla, Thailand, 22–24 July 2015; pp. 162–167. [Google Scholar]
- Yan, F.; Qiao, T. Study on the Detection of Cross-Site Scripting Vulnerabilities Based on Reverse Code Audit. In Proceedings of the International Conference on Intelligent Data Engineering and Automated Learning; Yangzhou, China, 12–14 October 2016, Springer: Berlin/Heidelberg, Germany, 2016; pp. 154–163. [Google Scholar]
- Steffens, M.; Rossow, C.; Johns, M.; Stock, B. Don’t Trust The Locals: Investigating the Prevalence of Persistent Client-Side Cross-Site Scripting in the Wild. In Proceedings of the NDSS Symposium, San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Bisht, P.; Venkatakrishnan, V. XSS-GUARD: Precise dynamic prevention of cross-site scripting attacks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment; Paris, France, 10–11 July 2008, Springer: Berlin/Heidelberg, Germany, 2008; pp. 23–43. [Google Scholar]
- Di Mauro, M.; Di Sarno, C. A framework for Internet data real-time processing: A machine-learning approach. In Proceedings of the 2014 International Carnahan Conference on Security Technology (ICCST), Rome, Italy, 13–16 October 2014; pp. 1–6. [Google Scholar]
- Batyuk, A.; Voityshyn, V. Apache storm based on topology for real-time processing of streaming data from social networks. In Proceedings of the 2016 IEEE First International Conference on Data Stream Mining & Processing (DSMP), Lviv, Ukraine, 23–27 August 2016; pp. 345–349. [Google Scholar]
- Rodriguez, G.; Torres, J.; Flores, P.; Benavides, E.; Nuñez-Agurto, D. XSStudent: Proposal to Avoid Cross-Site Scripting (XSS) Attacks in Universities. In Proceedings of the 2019 3rd Cyber Security in Networking Conference (CSNet), Quito, Ecuador, 23–25 October 2019; pp. 142–149. [Google Scholar]
- Manès, V.J.M.; Han, H.; Han, C.; Cha, S.K.; Egele, M.; Schwartz, E.J.; Woo, M. The art, science, and engineering of fuzzing: A survey. IEEE Trans. Softw. Eng. 2019. [Google Scholar] [CrossRef]
- Falana, O.J.; Ebo, I.O.; Tinubu, C.O.; Adejimi, O.A.; Ntuk, A. Detection of Cross-Site Scripting Attacks using Dynamic Analysis and Fuzzy Inference System. In Proceedings of the 2020 International Conference in Mathematics, Computer Engineering and Computer Science (ICMCECS), Ayobo, Ipaja, Lagos, Nigeria, 18–21 March 2020; pp. 1–6. [Google Scholar]
- Li, Y.; Ji, S.; Lv, C.; Chen, Y.; Chen, J.; Gu, Q.; Wu, C. V-fuzz: Vulnerability-oriented evolutionary fuzzing. arXiv 2019, arXiv:1901.01142. [Google Scholar]
- Marashdih, A.W.; Zaaba, Z.F.; Suwais, K.; Mohd, N.A. Web Application Security: An Investigation on Static Analysis with other Algorithms to Detect Cross Site Scripting. Procedia Comput. Sci. 2019, 161, 1173–1181. [Google Scholar] [CrossRef]
- Li, J.; Zhao, B.; Zhang, C. Fuzzing: A survey. Cybersecurity 2018, 1, 6. [Google Scholar] [CrossRef]
- Yusof, I.; Pathan, A.S.K. Preventing persistent Cross-Site Scripting (XSS) attack by applying pattern filtering approach. In Proceedings of the The 5th International Conference on Information and Communication Technology for The Muslim World (ICT4M), Kuching, Malaysia, 17–18 November 2014; pp. 1–6. [Google Scholar]
- Mohammadi, M.; Chu, B.; Lipford, H.R. Automated Repair of Cross-Site Scripting Vulnerabilities through Unit Testing. In Proceedings of the 2019 IEEE International Symposium on Software Reliability Engineering Workshops (ISSREW), Berlin, Germany, 27–30 October 2019; pp. 370–377. [Google Scholar]
- Yan, X.X.; Wang, Q.X.; Ma, H.T. Path sensitive static analysis of taint-style vulnerabilities in PHP code. In Proceedings of the 2017 IEEE 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 1382–1386. [Google Scholar]
- Elkhodr, M.; Patel, J.K.; Mahdavi, M.; Gide, E. Prevention of Cross-Site Scripting Attacks in Web Applications. In Proceedings of the Workshops of the International Conference on Advanced Information Networking and Applications; Caserta, Italy, 15–17 April 2020, Springer: Berlin/Heidelberg, Germany, 2020; pp. 1077–1086. [Google Scholar]
- Zubarev, D.; Skarga-Bandurova, I. Cross-Site Scripting for Graphic Data: Vulnerabilities and Prevention. In Proceedings of the 2019 10th International Conference on Dependable Systems, Services and Technologies (DESSERT), Leeds, UK, 5–7 June 2019; pp. 154–160. [Google Scholar]
- Papagiannis, I.; Migliavacca, M.; Pietzuch, P. PHP Aspis: Using partial taint tracking to protect against injection attacks. In Proceedings of the 2nd USENIX Conference on Web Application Development, Portland, OR, USA, 15–16 June 2011; Volume 13. [Google Scholar]
- CWE-79: Improper Neutralization of Input During Web Page Generation (Cross-site Scripting). Available online: https://cwe.mitre.org/data/definitions/79.html (accessed on 20 February 2020).
- Gupta, S.; Gupta, B. A robust server-side javascript feature injection-based design for JSP web applications against XSS vulnerabilities. In Cyber Security; Springer: Berlin/Heidelberg, Germany, 2018; pp. 459–465. [Google Scholar]
- Mikolov, T.; Chen, K.; Corrado, G.; Dean, J. Efficient estimation of word representations in vector space. arXiv 2013, arXiv:1301.3781. [Google Scholar]
- Calzavara, S.; Conti, M.; Focardi, R.; Rabitti, A.; Tolomei, G. Machine Learning for Web Vulnerability Detection: The Case of Cross-Site Request Forgery. IEEE Secur. Priv. 2020, 18, 8–16. [Google Scholar] [CrossRef]
- Graves, A.; Schmidhuber, J. Framewise phoneme classification with bidirectional LSTM and other neural network architectures. Neural Netw. 2005, 18, 602–610. [Google Scholar] [CrossRef] [PubMed]
| Authors | Features | Vulnerabilities | Algorithm | Performance |
|---|---|---|---|---|
| Shar et al. | Static/Dynamic code attributes | SQL, XSS | Logistic regression, MLP | |
| Roccardo et al. | Unique-words, Uni_tokens | General | NB, Radom Forest, SVM et al. | |
| Mukesh et al. | Proposed_tokens | XSS | Random Forest, SVM, J48 et al | |
| Yong Fang et al. | TAP_tokens | XSS, SQL | LSTM |
| Super Global Variable | Description |
|---|---|
| $_GET | An associative array of variables passed to the current script via the URL parameters |
| $_POST | An associative array of variables passed to the current script via the HTTP POST method when using application/x-www-form-urlencoded or multipart/form-data as the HTTP Content-Typein the request |
| $_COOKIE | An associative array of variables passed to the current script via HTTP Cookies |
| $_REQUEST | An associative array that by default contains the contents of $_GET, $_POST and $_COOKIE |
| $_FILES | An associative array of items uploaded to the current script via the HTTP POST method |
| $_HTTP_RAW_POST_DATA | A global variable that contains the raw POST data |
| Example | Description | OPCODE |
|---|---|---|
| <script>$output_var</script> | Output directly in the content part of the script tag | DATA_SCRIPT |
| <div $output_var=......> | Output variable as attribute name of tag | ATTR_NAME |
| <$output_var attr=......> | Output variable as tag name | TAG_NAME |
| <div id=$output_var>content</div> | Numeric attribute value | ATTR_VAL_NO_QUO |
| <div attr=’$output_var’>content</div> | Single quote closed attribute value | ATTR_VAL_SG_QUO |
| <div attr="$output_var">content</div> | Double quote closed attribute value | ATTR_VAL_DB_QUO |
| body{attr:$output_var;} | Numeric attribute value in CSS block | CSS_PROP_VAL_NO_QUO |
| body{attr:’$output_var’;} | Single quote closed attribute value in CSS block | CSS_PROP_VAL_SG_QUO |
| body{attr:"$output_var";} | Double quote closed attribute value in CSS block | CSS_PROP_VAL_DB_QUO |
| js_function($output_var); | Bare parameter in JavaScript function | JS_FUNC_ATTR_NO_QUO |
| js_function(’$output_var’); | Numeric quote closed parameter in JavaScript function | JS_FUNC_ATTR_SG_QUO |
| js_function("$output_var"); | Double quote closed parameter in JavaScript function | JS_FUNC_ATTR_DB_QUO |
| <div onclick="$output_var"> | Event handler variable | EVENT_HANDLER_DB_QUO |
| <span style="$output_var">; | Inline css style | CSS_INLINE_STYLE |
| Experiments | Precision | Recall | Macro F1 | Mean AUC | ||
|---|---|---|---|---|---|---|
| Safe | Vulnerable | Safe | Vulnerable | |||
| OPCODE | 0.9402 | 0.6211 | 0.5348 | 0.9493 | 0.7146 | 0.7615 |
| OPCODE+SOURCE | 0.9408 | 0.6209 | 0.5345 | 0.9495 | 0.7148 | 0.7633 |
| OPCODE+SOURCE+FILTER | 0.9435 | 0.6968 | 0.7062 | 0.9236 | 0.7991 | 0.8483 |
| OPCODE+SOURCE+FILTER+SINK | 0.9813 | 0.8659 | 0.8739 | 0.9785 | 0.9216 | 0.9726 |
| Algorithm | AUC | F1 | Precision | Recall | Vulnerability Recall |
|---|---|---|---|---|---|
| Random Forest | 0.86 | 0.82 | 0.83 | 0.82 | 0.90 |
| SVM | 0.94 | 0.89 | 0.88 | 0.89 | 0.94 |
| CNN | 0.93 | 0.87 | 0.87 | 0.86 | 0.87 |
| LSTM | 0.95 | 0.90 | 0.89 | 0.90 | 0.95 |
| Bi-LSTM | 0.97 | 0.92 | 0.92 | 0.92 | 0.98 |
| Method | Precision | Recall | F1 | Accuracy |
|---|---|---|---|---|
| Mukesh’s method | 0.8870 | 0.8300 | 0.8590 | 0.8890 |
| XSS Guardian | 0.9200 | 0.9232 | 0.9216 | 0.9237 |
| Improvements |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, C.; Wang, Y.; Miao, C.; Huang, C. Cross-Site Scripting Guardian: A Static XSS Detector Based on Data Stream Input-Output Association Mining. Appl. Sci. 2020, 10, 4740. https://doi.org/10.3390/app10144740
Li C, Wang Y, Miao C, Huang C. Cross-Site Scripting Guardian: A Static XSS Detector Based on Data Stream Input-Output Association Mining. Applied Sciences. 2020; 10(14):4740. https://doi.org/10.3390/app10144740
Chicago/Turabian StyleLi, Chenghao, Yiding Wang, Changwei Miao, and Cheng Huang. 2020. "Cross-Site Scripting Guardian: A Static XSS Detector Based on Data Stream Input-Output Association Mining" Applied Sciences 10, no. 14: 4740. https://doi.org/10.3390/app10144740
APA StyleLi, C., Wang, Y., Miao, C., & Huang, C. (2020). Cross-Site Scripting Guardian: A Static XSS Detector Based on Data Stream Input-Output Association Mining. Applied Sciences, 10(14), 4740. https://doi.org/10.3390/app10144740